9d04e0504ccdc56cd6d7c9c6d719d6b5.ppt
- Количество слайдов: 19
 Yanchao Zhang, Yuguang Fang Wireless Networks 2006. 6 MMC Lab. 임동혁
Yanchao Zhang, Yuguang Fang Wireless Networks 2006. 6 MMC Lab. 임동혁
 Introduction Network architecture and system models Entity authentication Incontestable billing of mobile users System Analysis Conclusions
Introduction Network architecture and system models Entity authentication Incontestable billing of mobile users System Analysis Conclusions
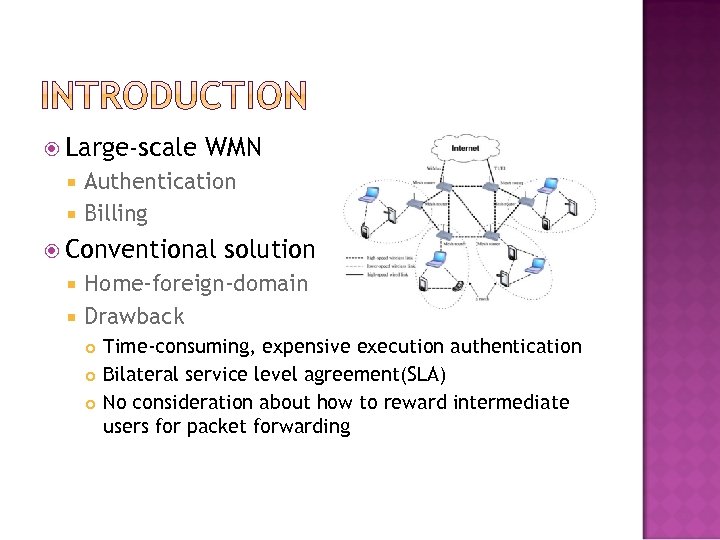 Large-scale WMN Authentication Billing Conventional solution Home-foreign-domain Drawback Time-consuming, expensive execution authentication Bilateral service level agreement(SLA) No consideration about how to reward intermediate users for packet forwarding
Large-scale WMN Authentication Billing Conventional solution Home-foreign-domain Drawback Time-consuming, expensive execution authentication Bilateral service level agreement(SLA) No consideration about how to reward intermediate users for packet forwarding
 UPASS No need SLA between WMN operators Authentication ID-based cryptography(IBC) User vs serving WMN User vs user in the same WMN Certificate-based cryptography(CBC) Universal verifiability of passes Billing Digital signature & one-way hash-chain Realtime micropayment approach
UPASS No need SLA between WMN operators Authentication ID-based cryptography(IBC) User vs serving WMN User vs user in the same WMN Certificate-based cryptography(CBC) Universal verifiability of passes Billing Digital signature & one-way hash-chain Realtime micropayment approach
 Assumptions Mesh router sends packets in one hop to all users in its coverage A mobile user transmits packets multiple hops to a mesh router All communications pass through a mesh router
Assumptions Mesh router sends packets in one hop to all users in its coverage A mobile user transmits packets multiple hops to a mesh router All communications pass through a mesh router
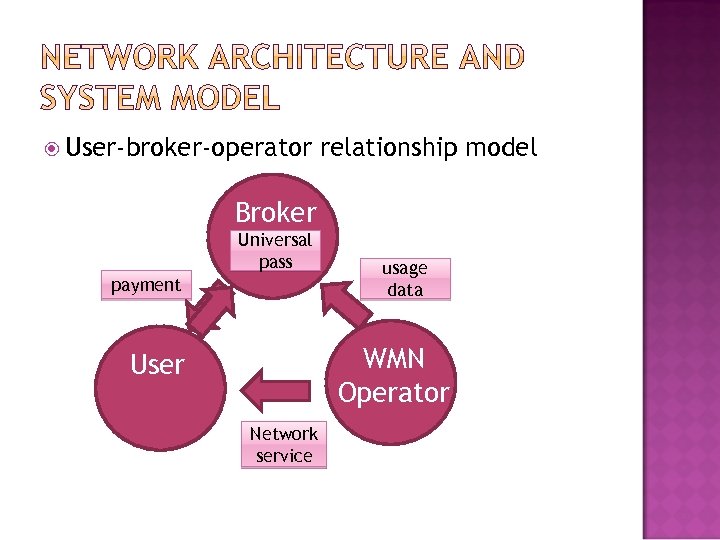 User-broker-operator relationship model Broker Universal pass payment usage data WMN Operator User Network service
User-broker-operator relationship model Broker Universal pass payment usage data WMN Operator User Network service
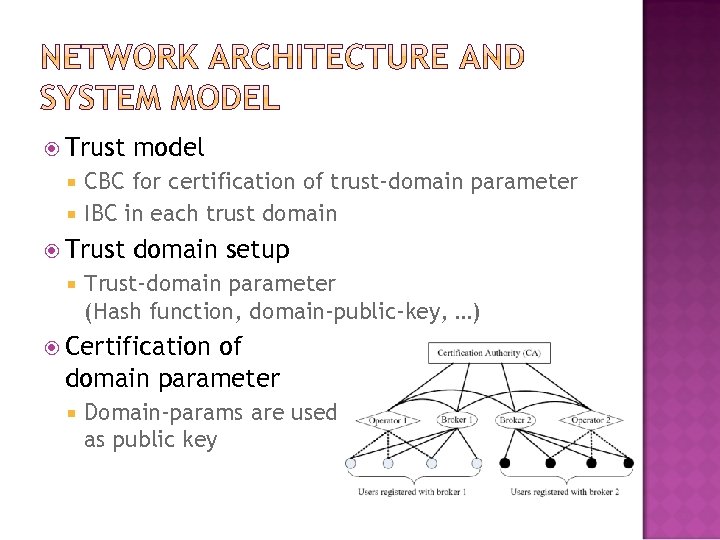 Trust model CBC for certification of trust-domain parameter IBC in each trust domain Trust domain setup Trust-domain parameter (Hash function, domain-public-key, …) Certification of domain parameter Domain-params are used as public key
Trust model CBC for certification of trust-domain parameter IBC in each trust domain Trust domain setup Trust-domain parameter (Hash function, domain-public-key, …) Certification of domain parameter Domain-params are used as public key
 Pass Router model R-NAI : router. ID@operater_domain R-pass : (R-NAI, expiry-date) R-key : k. H 1(R-pass) k : operator’s domain-master-secret (R-pass, R-key): IBC public & private key pair User U-NAI : user. ID@broker_domain U-pass : (U-NAI, expiry-date, other. Terms) U-key : k. H 1(U-pass) k : broker’s domain-master-secret (U-pass, U-key) : IBC public & private key pair
Pass Router model R-NAI : router. ID@operater_domain R-pass : (R-NAI, expiry-date) R-key : k. H 1(R-pass) k : operator’s domain-master-secret (R-pass, R-key): IBC public & private key pair User U-NAI : user. ID@broker_domain U-pass : (U-NAI, expiry-date, other. Terms) U-key : k. H 1(U-pass) k : broker’s domain-master-secret (U-pass, U-key) : IBC public & private key pair
 Pairwise User-router authentication shared key Inter-domain authentication Intra-domain authentication User-user authentication
Pairwise User-router authentication shared key Inter-domain authentication Intra-domain authentication User-user authentication
 Inter-domain authentication U and R possesses each other’s authentic domainparams Procedure (1) (2) (3) (4) (5) shared key :
Inter-domain authentication U and R possesses each other’s authentic domainparams Procedure (1) (2) (3) (4) (5) shared key :
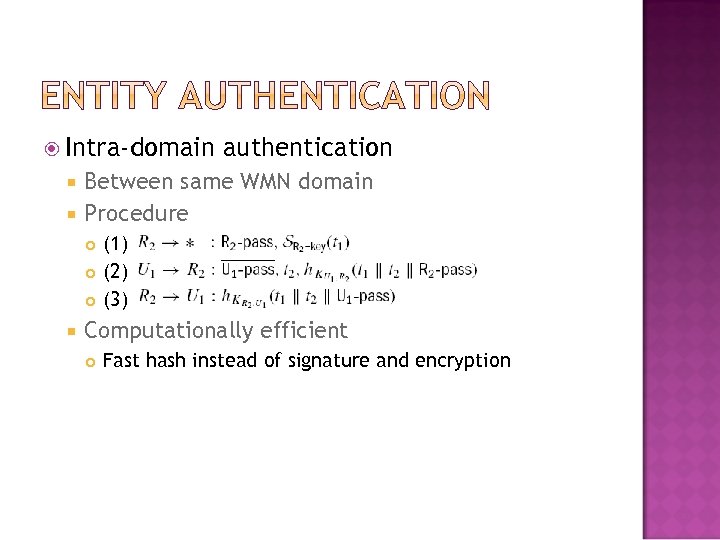 Intra-domain authentication Between same WMN domain Procedure (1) (2) (3) Computationally efficient Fast hash instead of signature and encryption
Intra-domain authentication Between same WMN domain Procedure (1) (2) (3) Computationally efficient Fast hash instead of signature and encryption
 User-user authentication Get paid for his packet forwarding Pairwise shared keys Symmetric-key challenge-response authentication technique U 1 send to U 2 a challenge r 1 encrypted KU 1, U 2 report a correct response, (r 1+1) U 1 declares the authentication of U 2 successful Similarly, U 2 can authenticate U 1
User-user authentication Get paid for his packet forwarding Pairwise shared keys Symmetric-key challenge-response authentication technique U 1 send to U 2 a challenge r 1 encrypted KU 1, U 2 report a correct response, (r 1+1) U 1 declares the authentication of U 2 successful Similarly, U 2 can authenticate U 1
 Billing Intermediate user compensation basics Attaching to forwarded packet a message integrity code(MIC) calculated under its pairwise shared key with R 1 ascertain the user in forwarding packet for U 1 Total payment (m-units per t-unit transmitted)
Billing Intermediate user compensation basics Attaching to forwarded packet a message integrity code(MIC) calculated under its pairwise shared key with R 1 ascertain the user in forwarding packet for U 1 Total payment (m-units per t-unit transmitted)
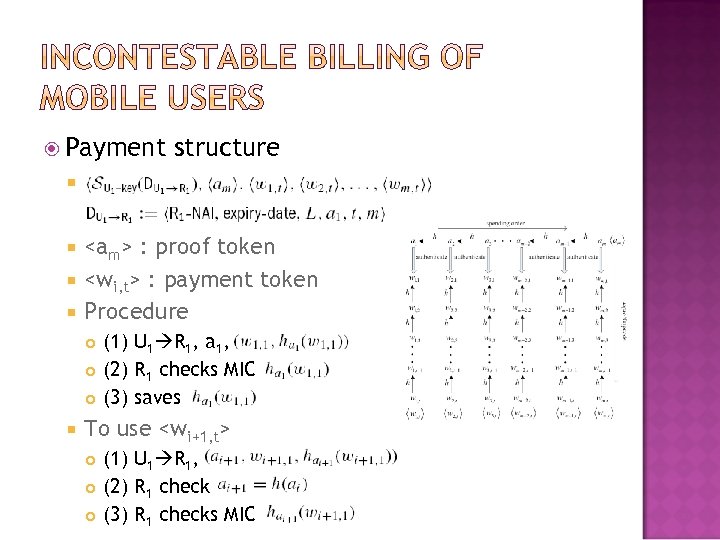 Payment structure
Payment structure
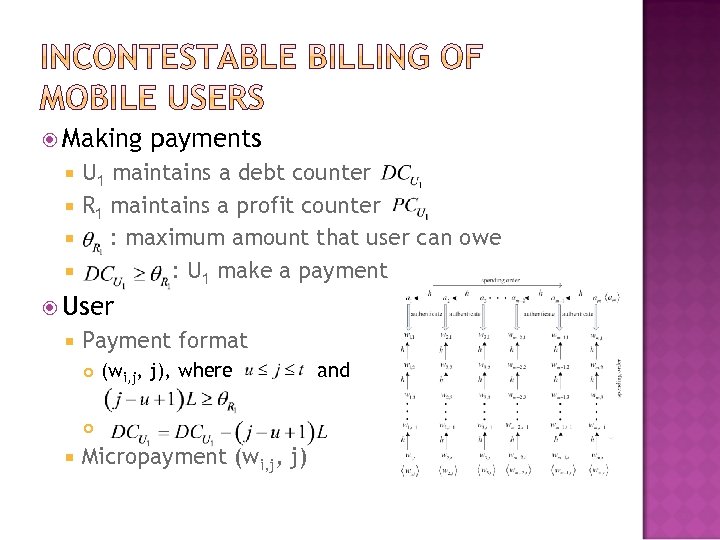 Making payments U 1 maintains a debt counter R 1 maintains a profit counter : maximum amount that user can owe : U 1 make a payment User Payment format (wi, j, j), where Micropayment (wi, j, j) and
Making payments U 1 maintains a debt counter R 1 maintains a profit counter : maximum amount that user can owe : U 1 make a payment User Payment format (wi, j, j), where Micropayment (wi, j, j) and
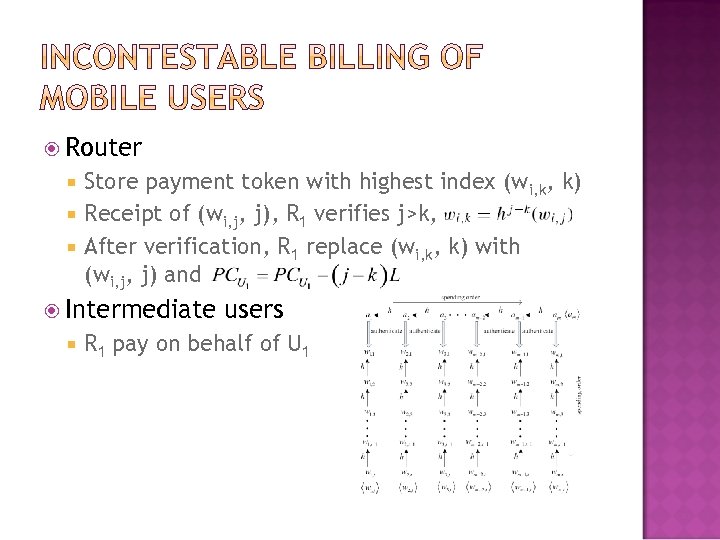 Router Store payment token with highest index (wi, k, k) Receipt of (wi, j, j), R 1 verifies j>k, After verification, R 1 replace (wi, k, k) with (wi, j, j) and Intermediate users R 1 pay on behalf of U 1
Router Store payment token with highest index (wi, k, k) Receipt of (wi, j, j), R 1 verifies j>k, After verification, R 1 replace (wi, k, k) with (wi, j, j) and Intermediate users R 1 pay on behalf of U 1
 Redemption of payment structure Broker VS R 1 Payment record Procedure
Redemption of payment structure Broker VS R 1 Payment record Procedure
 Security A user signs a payment structure digitally Payment structure is both user-specific and router-specific Low Computation Rare public-key operation Fast hash operation Small Storage Communication More efficient than home-foreign-domain model
Security A user signs a payment structure digitally Payment structure is both user-specific and router-specific Low Computation Rare public-key operation Fast hash operation Small Storage Communication More efficient than home-foreign-domain model
 UPASS First known secure authentication and billing architecture for large-scale WMNs Homeless, no need for SLAs Hybrid IBC/CBC trust model Lightweight realtime micropayment approach
UPASS First known secure authentication and billing architecture for large-scale WMNs Homeless, no need for SLAs Hybrid IBC/CBC trust model Lightweight realtime micropayment approach


