7178200effb563cb5c4ba329a4dcc9a1.ppt
- Количество слайдов: 42

XML Encryption and Authentication March 30, 2006 Robert Richards

Digital Signatures and Encryption Canonicalization – A standard form of data Digital Signatures – Provides proof of identity and authenticity which the sender cannot deny. Encryption – Protection of data from being accessed by unauthorized parties.

Existing Tools/Technologies Secure Sockets Layer (SSL) Transport Layer Security (TLS) Pretty Good Privacy (PGP) GNU Privacy Guard (Gnu. PG) Open. PGP S/MIME x. 509

XML Security Standards Canonical XML http: //www. w 3. org/TR/xml-c 14 n/ Exclusive XML Canonicalization http: //www. w 3. org/TR/xml-exc-c 14 n/ XML Signature http: //www. w 3. org/TR/xmldsig-core/ XML Encryption http: //www. w 3. org/TR/xmlenc-core/ XML Key Management http: //www. w 3. org/TR/xkms 2/
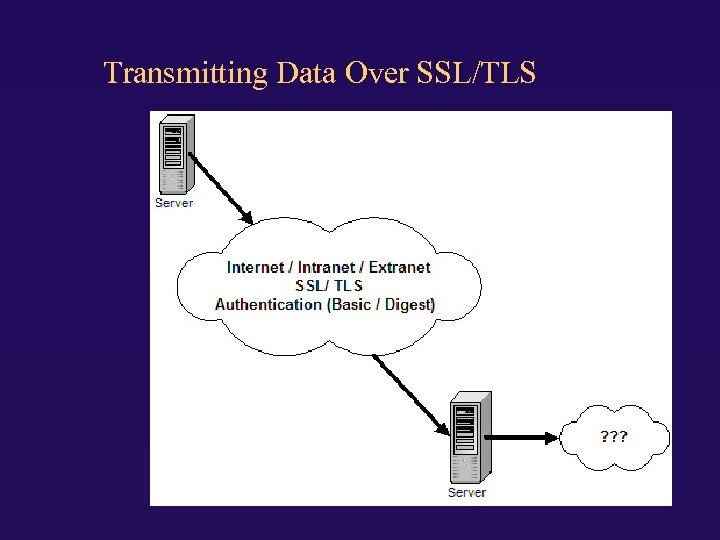
Transmitting Data Over SSL/TLS
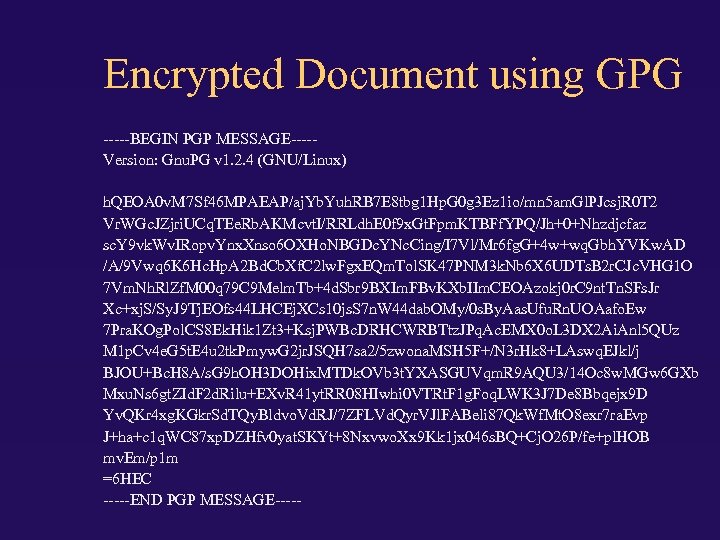
Encrypted Document using GPG -----BEGIN PGP MESSAGE----Version: Gnu. PG v 1. 2. 4 (GNU/Linux) h. QEOA 0 v. M 7 Sf 46 MPAEAP/aj. Yb. Yuh. RB 7 E 8 tbg 1 Hp. G 0 g 3 Ez 1 io/mn 5 am. Gl. PJcsj. R 0 T 2 Vr. WGc. JZjri. UCq. TEe. Rb. AKMcvt. I/RRLdh. E 0 f 9 x. Gt. Fpm. KTBFf. YPQ/Jh+0+Nhzdjcfaz sc. Y 9 vk. Wv. IRopv. Ynx. Xnso 6 OXHo. NBGDc. YNc. Cing/I 7 Vl/Mr 6 fg. G+4 w+wq. Gbh. YVKw. AD /A/9 Vwq 6 K 6 Hc. Hp. A 2 Bd. Cb. Xf. C 2 lw. Fgx. EQm. Tol. SK 47 PNM 3 k. Nb 6 X 6 UDTs. B 2 r. CJc. VHG 1 O 7 Vm. Nh. Rl. Zf. M 00 q 79 C 9 Melm. Tb+4 d. Sbr 9 BXIm. FBv. KXb. IIm. CEOAzokj 0 r. C 9 nt. Tn. SFs. Jr Xc+xj. S/Sy. J 9 Tj. EOfs 44 LHCEj. XCs 10 js. S 7 n. W 44 dab. OMy/0 s. By. Aas. Ufu. Rn. UOAafo. Ew 7 Pra. KOg. Pol. CS 8 Ek. Hik 1 Zt 3+Ksj. PWBc. DRHCWRBTtz. JPq. Ac. EMX 0 o. L 3 DX 2 Ai. Anl 5 QUz M 1 p. Cv 4 e. G 5 t. E 4 u 2 tk. Pmyw. G 2 jr. JSQH 7 sa 2/5 zwona. MSH 5 F+/N 3 r. Hk 8+LAswq. EJkl/j BJOU+Bc. H 8 A/s. G 9 h. OH 3 DOHix. MTDk. OVb 3 t. YXASGUVqm. R 9 AQU 3/14 Oc 8 w. MGw 6 GXb Mxu. Ns 6 gt. ZId. F 2 d. Rilu+EXv. R 41 yt. RR 08 HIwhi 0 VTRt. F 1 g. Foq. LWK 3 J 7 De 8 Bbqejx 9 D Yv. QKr 4 xg. KGkr. Sd. TQy. Bldvo. Vd. RJ/7 ZFLVd. Qyr. VJl. FABeli 87 Qk. Wf. Mt. O 8 exr 7 ra. Evp J+ha+c 1 q. WC 87 xp. DZHfv 0 yat. SKYt+8 Nxvwo. Xx 9 Kk 1 jx 046 s. BQ+Cj. O 26 P/fe+pl. HOB mv. Em/p 1 m =6 HEC -----END PGP MESSAGE-----

Benefits of XML Security Standards XML is a structured format Allows for secure storage of documents Leverages existing technologies Provides granularity
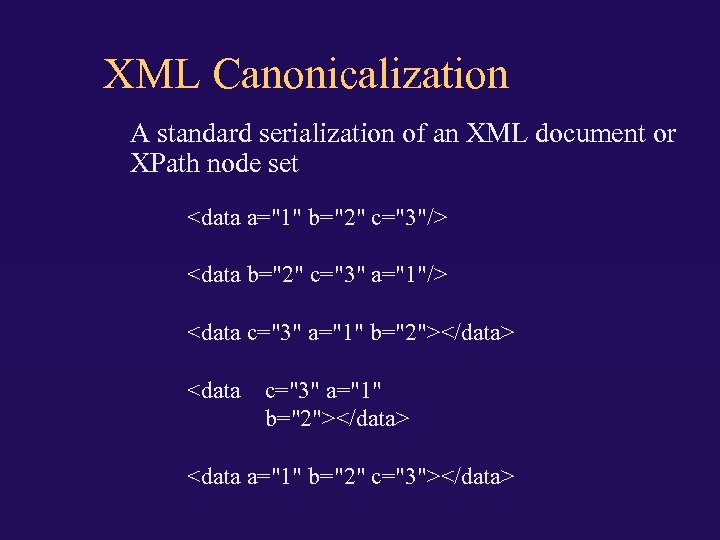
XML Canonicalization A standard serialization of an XML document or XPath node set <data a="1" b="2" c="3"/> <data b="2" c="3" a="1"/> <data c="3" a="1" b="2"></data> <data a="1" b="2" c="3"></data>
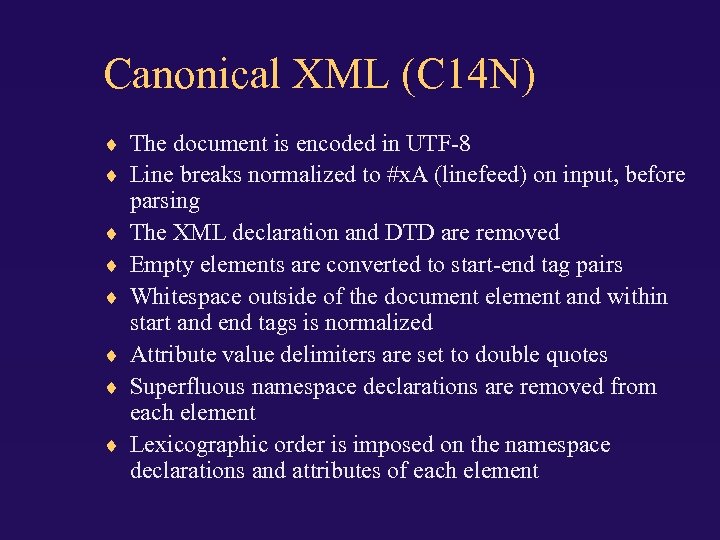
Canonical XML (C 14 N) The document is encoded in UTF-8 Line breaks normalized to #x. A (linefeed) on input, before parsing The XML declaration and DTD are removed Empty elements are converted to start-end tag pairs Whitespace outside of the document element and within start and end tags is normalized Attribute value delimiters are set to double quotes Superfluous namespace declarations are removed from each element Lexicographic order is imposed on the namespace declarations and attributes of each element

Canonical XML Example #1 <? xml version="1. 0" encoding="UTF-8"? > <? xml-stylesheet href="doc. xsl" type="text/xsl" ? > <!-- Comment --> <doc> <e 1 a: attr='out' b: attr='sorted' attr 2='all' attr="I'm" xmlns: b='http: //www. ietf. org' xmlns: a="http: //www. w 3. org" xmlns="http: //example. org"/> <e 2 xmlns="" xmlns: a="http: //www. w 3. org"> <e 3 xmlns="" xmlns: a="http: //www. w 3. org"/> </e 2> </doc> Canonical Form of Document (uncommented) <? xml-stylesheet href="doc. xsl" type="text/xsl" ? > <doc> <e 1 xmlns="http: //example. org" xmlns: a="http: //www. w 3. org" xmlns: b="http: //www. ietf. org" attr="I'm" attr 2="all" b: attr="sorted" a: attr="out"></e 1> <e 2 xmlns: a="http: //www. w 3. org"> <e 3></e 3> </e 2> </doc>

Canonical XML Example #1 <? xml version="1. 0" encoding="UTF-8"? > <? xml-stylesheet href="doc. xsl" type="text/xsl" ? > <!-- Comment --> <doc> <e 1 a: attr='out' b: attr='sorted' attr 2='all' attr="I'm" xmlns: b='http: //www. ietf. org' xmlns: a="http: //www. w 3. org" xmlns="http: //example. org"/> <e 2 xmlns="" xmlns: a="http: //www. w 3. org"> <e 3 xmlns="" xmlns: a="http: //www. w 3. org"/> </e 2> </doc> Canonical Form of Document (uncommented) <? xml-stylesheet href="doc. xsl" type="text/xsl" ? > <doc> <e 1 xmlns="http: //example. org" xmlns: a="http: //www. w 3. org" xmlns: b="http: //www. ietf. org" attr="I'm" attr 2="all" b: attr="sorted" a: attr="out"></e 1> <e 2 xmlns: a="http: //www. w 3. org"> <e 3></e 3> </e 2> </doc>

Canonical XML Example #1 <? xml version="1. 0" encoding="UTF-8"? > <? xml-stylesheet href="doc. xsl" type="text/xsl" ? > <!-- Comment --> <doc> <e 1 a: attr='out' b: attr='sorted' attr 2='all' attr="I'm" xmlns: b='http: //www. ietf. org' xmlns: a="http: //www. w 3. org" xmlns="http: //example. org"/> <e 2 xmlns="" xmlns: a="http: //www. w 3. org"> <e 3 xmlns="" xmlns: a="http: //www. w 3. org"/> </e 2> </doc> Canonical Form of Document (uncommented) <? xml-stylesheet href="doc. xsl" type="text/xsl" ? > <doc> <e 1 xmlns="http: //example. org" xmlns: a="http: //www. w 3. org" xmlns: b="http: //www. ietf. org" attr="I'm" attr 2="all" b: attr="sorted" a: attr="out"></e 1> <e 2 xmlns: a="http: //www. w 3. org"> <e 3></e 3> </e 2> </doc>

Canonical XML Example #1 <? xml version="1. 0" encoding="UTF-8"? > <? xml-stylesheet href="doc. xsl" type="text/xsl" ? > <!-- Comment --> <doc> <e 1 a: attr='out' b: attr='sorted' attr 2='all' attr="I'm" xmlns: b='http: //www. ietf. org' xmlns: a="http: //www. w 3. org" xmlns="http: //example. org"/> <e 2 xmlns="" xmlns: a="http: //www. w 3. org"> <e 3 xmlns="" xmlns: a="http: //www. w 3. org"/> </e 2> </doc> Canonical Form of Document (uncommented) <? xml-stylesheet href="doc. xsl" type="text/xsl" ? > <doc> <e 1 xmlns="http: //example. org" xmlns: a="http: //www. w 3. org" xmlns: b="http: //www. ietf. org" attr="I'm" attr 2="all" b: attr="sorted" a: attr="out"></e 1> <e 2 xmlns: a="http: //www. w 3. org"> <e 3></e 3> </e 2> </doc>

Canonical XML Example #2 <? xml version="1. 0" encoding="UTF-8"? > <doc xmlns: d="http: //www. example. org/d" xmlns: c="http: //www. example. org/c"> <e 1 a: attr="out" b: attr="sorted" attr 2="all" attr="I'm" xmlns: b="http: //www. ietf. org" xmlns: a="http: //www. w 3. org" xmlns="http: //example. org"/> <d: e 2 xmlns="" xmlns: a="http: //www. w 3. org"> <e 3 xmlns="" xmlns: a="http: //www. w 3. org"/> </d: e 2> </doc> Canonical Form of Nodeset (uncommented) (//. | //@* | //namespace: : *)[ancestor-or-self: : d: e 2] <d: e 2 xmlns: a="http: //www. w 3. org" xmlns: c="http: //www. example. org/c" xmlns: d="http: //www. example. org/d"> <e 3></e 3> </d: e 2>

Canonical XML Example #2 <? xml version="1. 0" encoding="UTF-8"? > <doc xmlns: d="http: //www. example. org/d" xmlns: c="http: //www. example. org/c"> <e 1 a: attr="out" b: attr="sorted" attr 2="all" attr="I'm" xmlns: b="http: //www. ietf. org" xmlns: a="http: //www. w 3. org" xmlns="http: //example. org"/> <d: e 2 xmlns="" xmlns: a="http: //www. w 3. org"> <e 3 xmlns="" xmlns: a="http: //www. w 3. org"/> </d: e 2> </doc> Canonical Form of Nodeset (uncommented) (//. | //@* | //namespace: : *)[ancestor-or-self: : d: e 2] <d: e 2 xmlns: a="http: //www. w 3. org" xmlns: c="http: //www. example. org/c" xmlns: d="http: //www. example. org/d"> <e 3></e 3> </d: e 2>

Canonical XML Example #2 <? xml version="1. 0" encoding="UTF-8"? > <doc xmlns: d="http: //www. example. org/d" xmlns: c="http: //www. example. org/c"> <e 1 a: attr="out" b: attr="sorted" attr 2="all" attr="I'm" xmlns: b="http: //www. ietf. org" xmlns: a="http: //www. w 3. org" xmlns="http: //example. org"/> <d: e 2 xmlns="" xmlns: a="http: //www. w 3. org"> <e 3 xmlns="" xmlns: a="http: //www. w 3. org"/> </d: e 2> </doc> Canonical Form of Nodeset (uncommented) (//. | //@* | //namespace: : *)[ancestor-or-self: : d: e 2] <d: e 2 xmlns: a="http: //www. w 3. org" xmlns: c="http: //www. example. org/c" xmlns: d="http: //www. example. org/d"> <e 3></e 3> </d: e 2>

Problem with Re-Enveloping <d: e 2 xmlns: d="http: //www. example. org/d">content</d: e 2> <!-- Document wrapped within ns 0: e 1 element --> <ns 0: e 1 xmlns: ns 0="www. example. org/ns 0"> <d: e 2 xmlns: d="http: //www. example. org/d">content</d: e 2> </ns 0: e 1> <!-- Canonical Form --> <d: e 2 xmlns: d="http: //www. example. org/d" xmlns: ns 0="www. example. org/ns 0">content</d: e 2> <!-- Document wrapped within ns 1: e 1 element --> <ns 1: e 1 xmlns: ns 0="www. example. org/ns 1"> <d: e 2 xmlns: d="http: //www. example. org/d">content</d: e 2> </ns 1: e 1> <!-- Canonical Form --> <d: e 2 xmlns: d="http: //www. example. org/d" xmlns: ns 1="www. example. org/ns 1">content</d: e 2>

Exclusive XML Canonicalization Follows the same rules as Canonical XML, except… Attributes in the xml namespace are not imported into orphan nodes Namespaces not specially told to be added are only added on the starting element for which they are visible and not currently in scope within the output.

Re-Enveloping using Exclusive <d: e 2 xmlns: d="http: //www. example. org/d">content</d: e 2> <!-- Document wrapped within ns 0: e 1 element --> <ns 0: e 1 xmlns: ns 0="www. example. org/ns 0"> <d: e 2 xmlns: d="http: //www. example. org/d">content</d: e 2> </ns 0: e 1> <!-- Canonical Form --> <d: e 2 xmlns: d="http: //www. example. org/d">content</d: e 2> <!-- Document wrapped within ns 1: e 1 element --> <ns 1: e 1 xmlns: ns 0="www. example. org/ns 1"> <d: e 2 xmlns: d="http: //www. example. org/d">content</d: e 2> </ns 1: e 1> <!-- Canonical Form --> <d: e 2 xmlns: d="http: //www. example. org/d">content</d: e 2>

Exclusive Canonical XML Example <? xml version="1. 0" encoding="UTF-8"? > <doc xmlns: d="http: //www. example. org/d" xmlns: c="http: //www. example. org/c"> <e 1 a: attr="out" b: attr="sorted" attr 2="all" attr="I'm" xmlns: b="http: //www. ietf. org" xmlns: a="http: //www. w 3. org" xmlns="http: //example. org"/> <d: e 2 xmlns="" xmlns: a="http: //www. w 3. org"> <e 3 xmlns="" xmlns: a="http: //www. w 3. org"/> </d: e 2> </doc> Exclusive Canonical Form of Nodeset (uncommented) (//. | //@* | //namespace: : *)[ancestor-or-self: : d: e 2] <d: e 2 xmlns: d="http: //www. example. org/d"> <e 3></e 3> </d: e 2>

XML Digital Signature (XMLDSIG) Insure that a message has not been altered or tampered with. (integrity) Protection against attacks that alter a message but maintain integrity. (message authentication) Provide a means for message auditing so that messages may not be repudiated. (signer authenticity)
XML Signature: Types of Signatures Enveloping Signature – Data lives within the XML Signature structure – Good for signing data being packaged within an XML payload Enveloped Signature – Data lives outside of and contains the XML Signature structure – Good for signing an entire XML document Detached Signature – Data lives outside and DOES NOT contain the XML Signature structure – Data may reside at a remote location addressable by URI

Enveloping Signature <? xml version="1. 0"? > <Signature xmlns="http: //www. w 3. org/2000/09/xmldsig#"> <Signed. Info> <Canonicalization. Method Algorithm="http: //www. w 3. org/TR/2001/REC-xml-c 14 n-20010315"/> <Signature. Method Algorithm="http: //www. w 3. org/2000/09/xmldsig#hmac-sha 1"/> <Reference URI="#myobj"> <Digest. Method Algorithm="http: //www. w 3. org/2000/09/xmldsig#sha 1"/> <Digest. Value>C 2 g 9 BLc. Gy. GPCVKu. F 2 by. R 1 Ym+6 p. E=</Digest. Value> </Reference> </Signed. Info> <Signature. Value>+R/XEOHDv. R/jbmmpiu. H 4 Zc. Rq. C 6 c=</Signature. Value> <Object Id="myobj">Hello World!</Object> </Signature>

Enveloped Signature <? xml version="1. 0"? > <Envelope> <Data>content</Data> <Signature xmlns="http: //www. w 3. org/2000/09/xmldsig#"> <Signed. Info> <Canonicalization. Method Algorithm="http: //www. w 3. org/2001/10/xml-exc-c 14 n#"/> <Signature. Method Algorithm="http: //www. w 3. org/2000/09/xmldsig#hmac-sha 1"/> <Reference> <Transforms> <Transform Algorithm="http: //www. w 3. org/2000/09/xmldsig#enveloped-signature"/> </Transforms> <Digest. Method Algorithm="http: //www. w 3. org/2000/09/xmldsig#sha 1"/> <Digest. Value>MMMk. B 0 ZPp 82 Xr. Uv. JMFq. DIEu. Xy 0 o=</Digest. Value> </Reference> </Signed. Info> <Signature. Value>m. VPvfc. VSXi 9 el. KL+Ic. SCAz. D 4 Jbk=</Signature. Value> </Signature></Envelope>

Detached Signature <? xml version="1. 0"? > <Signature xmlns="http: //www. w 3. org/2000/09/xmldsig#"> <Signed. Info> <Canonicalization. Method Algorithm="http: //www. w 3. org/2001/10/xml-exc-c 14 n#"/> <Signature. Method Algorithm="http: //www. w 3. org/2000/09/xmldsig#hmac-sha 1"/> <Reference URI="http: //www. ctindustries. net/text. txt"> <Digest. Method Algorithm="http: //www. w 3. org/2000/09/xmldsig#sha 1"/> <Digest. Value>o. LZZOWc. Lws. AQ 9 NXWo. LPk 5 Fk. Pu. Ss=</Digest. Value> </Reference> </Signed. Info> <Signature. Value>O 9 ykp. FMXmkddz. J 3 Cy. Srpz. HBUW/Q=</Signature. Value> </Signature>

XML Signature Example Hello World! Resulting Enveloping Signature: <? xml version="1. 0"? > <Signature xmlns="http: //www. w 3. org/2000/09/xmldsig#"> <Signed. Info> <Canonicalization. Method Algorithm="http: //www. w 3. org/TR/2001/REC-xml-c 14 n-20010315"/> <Signature. Method Algorithm="http: //www. w 3. org/2000/09/xmldsig#hmac-sha 1"/> <Reference URI="#myobj"> <Digest. Method Algorithm="http: //www. w 3. org/2000/09/xmldsig#sha 1"/> <Digest. Value>C 2 g 9 BLc. Gy. GPCVKu. F 2 by. R 1 Ym+6 p. E=</Digest. Value> </Reference> </Signed. Info> <Signature. Value>+R/XEOHDv. R/jbmmpiu. H 4 Zc. Rq. C 6 c=</Signature. Value> <Object Id="myobj">Hello World!</Object> </Signature>

XML Signature Generation Apply any transforms to the data Calculate the digest value Create the Reference Element Create Signed. Info element with Signature. Method, Canonicalization. Method and Reference elements 5. Canonicalize the Signed. Info element 6. Calculate the Signature. Value over the canonicalized Signed. Info based the Signature. Method 7. Assemble the Signature element 1. 2. 3. 4.
XML Signature Validation 1. Obtain the verification keying information. 2. Apply the Canonicalization. Method to the Signed. Info element. 3. Verify the Signature. Value using the canonical form of the Signature. Method. 4. For each Reference element within Signed. Info: – Obtain the data to be digested. – Digest the data using the Digest. Method within its Referece element. – Compare the computed value to that of the un-encoded value from the Digest. Value element.

XML Encryption (XMLENC) Encrypted data is maintained. All information needed to decrypt a document is contained within the document. Session can be secured on the document level and shared between multiple parties. Sensitive data is easily interchanged between applications.

XML Encryption Example <payment> <order_number>1001</order_number> <customer>Joe Smith</customer> <creditcard> <number>4111 1111</number> <expiration_month>01</expiration_month> <expiration_year>2007</expiration_year> <ccv 2>123</ccv 2> </creditcard> </payment>

XML Encryption Example Element with Shared Secret Key <? xml version="1. 0"? > <payment> <order_number>1001</order_number> <customer>Joe Smith</customer> <Encrypted. Data xmlns="http: //www. w 3. org/2001/04/xmlenc#" Type="http: //www. w 3. org/2001/04/xmlenc#Element"> <Encryption. Method Algorithm="http: //www. w 3. org/2001/04/xmlenc#tripledes-cbc"/> <Cipher. Data> <Cipher. Value>C 5 X 1 I 65 RCX…</Cipher. Value> </Cipher. Data> </Encrypted. Data> </payment>

XML Encryption Example Element Content with Shared Secret Key <? xml version="1. 0"? > <payment> <order_number>1001</order_number> <customer>Joe Smith</customer> <creditcard><Encrypted. Data xmlns="http: //www. w 3. org/2001/04/xmlenc#" Type="http: //www. w 3. org/2001/04/xmlenc#Content"> <Encryption. Method Algorithm="http: //www. w 3. org/2001/04/xmlenc#tripledes-cbc"/> <Cipher. Data> <Cipher. Value>C 5 X 1 I 65 RCX…</Cipher. Value> </Cipher. Data> </Encrypted. Data></creditcard> </payment>

XML Encryption Example Arbitrary Data with Shared Secret Key <? xml version='1. 0'? > <Encrypted. Data xmlns='http: //www. w 3. org/2001/04/xmlenc#' xmlns: ds='http: //www. w 3. org/2000/09/xmldsig#' Mime. Type='text/xml'> <Cipher. Data> <Cipher. Value>. . . C 5 X 1 I 65 RCX. . . </Cipher. Value> </Cipher. Data> </Encrypted. Data>

XML Encryption Example Unsupported <? xml version="1. 0"? > <payment> <order_number>1001</order_number> <customer>Joe Smith</customer> <Encrypted. Data xmlns="http: //www. w 3. org/2001/04/xmlenc#" Type="http: //www. w 3. org/2001/04/xmlenc#Element"> <Encryption. Method Algorithm="http: //www. w 3. org/2001/04/xmlenc#tripledes-cbc"/> <Key. Info xmlns="http: //www. w 3. org/2000/09/xmldsig#"> <Key. Name>mcryptiv</Key. Name> <Key. Value>w 1 Uy 6 Mv. HZNY=</Key. Value> </Key. Info> <Cipher. Data> <Cipher. Value>F 541 I 65 RCX…</Cipher. Value> </Cipher. Data> </Encrypted. Data> </payment>

XML Encryption: Encrypting 1. Select the algorithm (and parameters) to use in encrypting the item. 2. Obtain the key and create ds: Key. Info if necessary 3. Encrypt the data and prepend any appropriate initialization vector (IV). 4. Build Cipher. Data element – If to be stored within Cipher. Value element, then encrypted data is base 64 encoded. – If encrypted data is external, then create Cipher. Reference with URI and any transforms. 5. Build Encrypted. Data or Encrypted. Key structure
XML Encryption: Decrypting 1. Determine encryption algorithm and parameters. 2. Obtain the decryption key information. 3. Obtain the data to decrypt. – If Cipher. Data has a Cipher. Value child then base-64 decode its contents. – If Cipher. Data has a Cipher. Reference child, retrieve the data and apply any Transforms. 4. Depending upon algorithm and parameters, strip any IV from the data to use for decryption. 5. Decrypt the cipher data with the encryption algorithm, parameters, and keying material.

Signing and Encrypting Sign and then Encrypt – Provides signature protection – Allows for encryption algorithm to be changed without affecting signature – Incurs additional overhead as you must decrypt before you can verify Encrypt and then Sign – Immediately know if data has been tampered with – Document can no longer be shared with other parties without revealing decryption key – Sender identity is revealed

XML Signature in WS-Security <env: Envelope xmlns: env="http: //www. w 3. org/2001/12/soap-envelope"> <env: Header> <wsse: Security xmlns: wsse="http: //schemas. xmlsoap. org/ws/2002/04/secext"> <dsig: Signature xmlns: dsig="http: //www. w 3. org/2000/09/xmldsig#"> <dsig: Signed. Info> <dsig: Canonicalization. Method Algorithm="http: //www. w 3. org/2001/10/xml-exc-c 14 n#"/> <dsig: Signature. Method Algorithm="http: //www. w 3. org/2000/09/xmldsig#rsa-sha 1"/> <dsig: Reference URI=""> <dsig: Transforms> …</dsig: Transforms> <Digest. Method Algorithm= "http: //www. w 3. org/2001/04/xmldsigmore#md 5"/> <Digest. Value>q. Zk+Nkc. Gg. Wq 6 Pi. Vxe. FDCb. J==</Digest. Value> </dsig: Reference> </dsig: Signed. Info> <dsig: Signature. Value> <dsig: Key. Info>. . . </dsig: Key. Info> </dsig: Signature> </wsse: Security> </env: Header> <env: Body><payment>. . . </payment></env: Body> </env: Envelope>

XML Encryption in WS-Security <env: Envelope xmlns: env="http: //www. w 3. org/2001/12/soap-envelope" xmlns: xenc="http: //www. w 3. org/2001/04/xmlenc#"> <env: Header> <wsse: Security xmlns: wsse="http: //schemas. xmlsoap. org/ws/2002/04/secext"> <xenc: Reference. List> <xenc: Data. Reference URI="#encrypted. ID"/> </xenc: Reference. List> </wsse: Security> </env: Header> <env: Body> <xenc: Encrypted. Data Id="encrypted. ID"> <xenc: Cipher. Data> <xenc: Cipher. Value>. . . </xenc: Cipher. Value> </xenc: Cipher. Data> </xenc: Encrypted. Data> </env: Body> </env: Envelope>

Questions?
XML Signature using Digital Certificate <Envelope xmlns="urn: envelope"> <Data> Hello, World! </Data> <Signature xmlns="http: //www. w 3. org/2000/09/xmldsig#"> <Signed. Info> <Canonicalization. Method Algorithm="http: //www. w 3. org/2001/10/xml-exc-c 14 n#"/> <Signature. Method Algorithm="http: //www. w 3. org/2000/09/xmldsig#rsa-sha 1"/> <Reference> <Transforms> <Transform Algorithm="http: //www. w 3. org/2000/09/xmldsig#enveloped-signature"/> </Transforms> <Digest. Method Algorithm="http: //www. w 3. org/2000/09/xmldsig#sha 1"/> <Digest. Value>Hj. Y 8 il. ZAIEM 2 t. Bb. Pn 5 m. YO 1 ie. IX 4=</Digest. Value> </Reference> </Signed. Info> <Signature. Value>SIaj/6 KY 3 C. . . </Signature. Value> <Key. Info> <X 509 Data> <X 509 Certificate>MIIE 3 z. CCBEj. AUB 9. . . </X 509 Certificate> </X 509 Data> </Key. Info> </Signature></Envelope>

XML Encryption w/ Digital Certificate <Encrypted. Data xmlns="http: //www. w 3. org/2001/04/xmlenc#" Type="http: //www. w 3. org/2001/04/xmlenc#Element"> <Encryption. Method Algorithm="http: //www. w 3. org/2001/04/xmlenc#tripledes-cbc"/> <Key. Info xmlns="http: //www. w 3. org/2000/09/xmldsig#"> <Encrypted. Key xmlns="http: //www. w 3. org/2001/04/xmlenc#"> <Encryption. Method Algorithm="http: //www. w 3. org/2001/04/xmlenc#rsa-oaep-mgf 1 p"/> <Key. Info xmlns="http: //www. w 3. org/2000/09/xmldsig#"> <Key. Name>rsakey. pem</Key. Name> </Key. Info> <Cipher. Data> <Cipher. Value>IPi. Eu 9 Nv+Es. Gyv. V. . . </Cipher. Value> </Cipher. Data> </Encrypted. Key> </Key. Info> <Cipher. Data> <Cipher. Value>xrf. PSA+BEI+8. . . </Cipher. Value> </Cipher. Data> </Encrypted. Data>
7178200effb563cb5c4ba329a4dcc9a1.ppt