a14455eb1ec2d3b044ee4ac87b461ba0.ppt
- Количество слайдов: 6
X-Road (X-tee) A platform-independent secure standard interface between databases and information systems to connect databases and information systems of the public sector
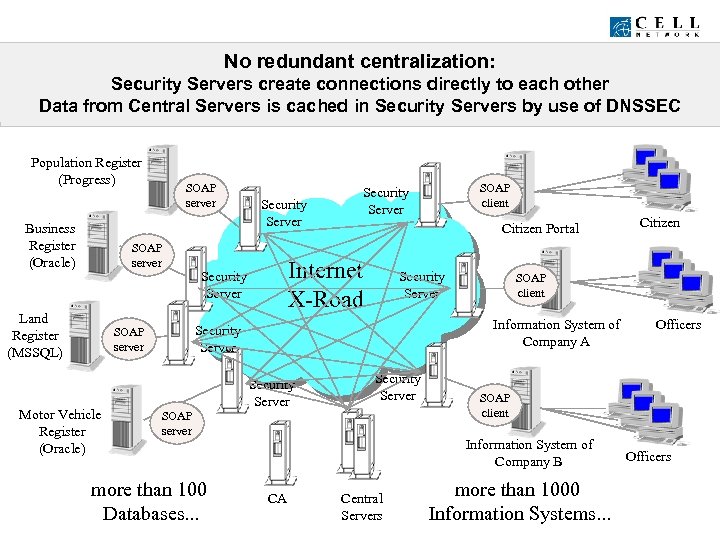
X-Road Database. Server is a every database Security Information standard accesses up is adapted to X-Road by setting No redundant centralization: To platform-independent secure software solution that Certificates are available forfrom. Servers from X-Roadsystemsbetween Trafficare various databases and information X-Road between system, systems encrypted with Central There. Extra interface verification isstandard every PKI. X-Road is a secure the Security each party need: to interface Servers. encrypts/decrypts. Serversvia it’swould havecontains: X-Road rules outgoing/ingoing which directlyof each other Security. XMLRPC client. Security Server filters ingoing messages create connections been to Adapter Server, messages, expensive. . . information systems SOAP different platforms+ understanding. Certification Authority Security Servers databases Servers are duplicated Central and with by X-Road certified need to co-operate. . . in or have to becached in Security Servers by use Data from Central Servers isand logs messages it receives of DNSSEC as a firewall, SOAP or XMLRPC server + X-Road rules Population Register (Progress) Business Register (Oracle) SOAP server Land Register (MSSQL) Citizen Portal Internet X-Road ? Security Server SOAP server Motor Vehicle Register (Oracle) Security Server Security Server Central Servers Officers SOAP client Information System of Company B CA Citizen SOAP client Information System of Company A SOAP server more than 100 Databases. . . SOAP client Security Server more than 1000 Information Systems. . . Officers
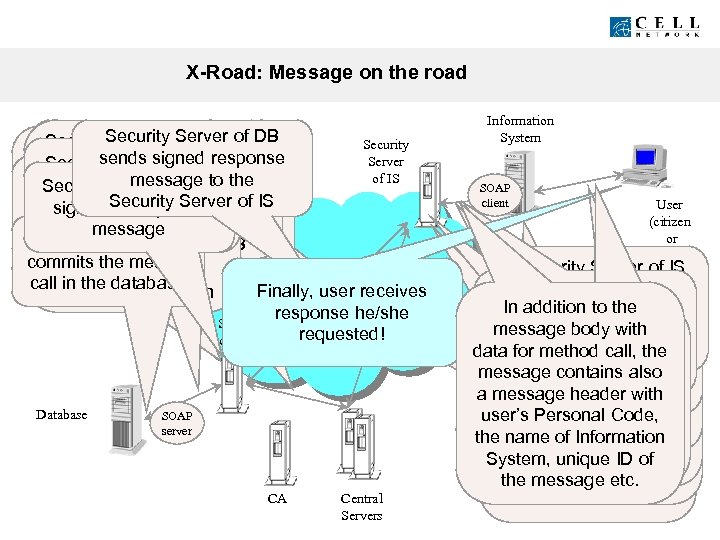
X-Road: Message on the road As secure channel of Security valid, If certificate was. Serverthe Security Server of DB has DB Security Server signed response ISDB opens been created of of other sends of and DB Server Security Server checks whether Security Server the of IS TCP connection DB to Security ofto the. DB party verified, its message Informationdecryptedback System sends Server of DB Securitythecertificate is of Server verifies signature DB Securitycreation Server of verifies Adapter toauthorized for of IS sends finish to the over message. Security thissecure IS signs the response. DNSSEC and sends certificate to of thesigned messagereceived message and the its certificate connection method Server message Adapter start TLS the. DB logs the Server to message Security Server of from commits is theprotocol the method security second This Security Server of IS Internet call in the authorization Finally, user receives level of database X-Road Security response he/she Server requested! of DB Database SOAP server CA Central Servers Information System SOAP client User (citizen or officer) Security Server of IS checks the signature Security Server ofof IS Inof responsethe IS addition to message Security Server sends decrypted message over DNSSEC verifies body with IS logs to As. Whethermessage call userand user is choosesthe The Security Server ofto response Informationmessage datathe certificate. System for method call, the response received identified by (usage of a Information System method ID-card, asks over DNSSEC the. Security Server User user the Thegives authenticatesto messageisfromaccess by password, face or which contains also authorized thehimself/herself Central Server signs methods userofto the else is with asomething header upis DB message Security Server the Information of the for IP address System), authorized to with it’s private keyuse user’s Personal System, the message with method Information Code, a Information System Security Server(s) of DB the call goes. Information name of towards the provided that the way of must be able level to This is first ID of System, uniqueto getof identification is reliable Security Server authorization theknow the proper message etc. Personal Code of user
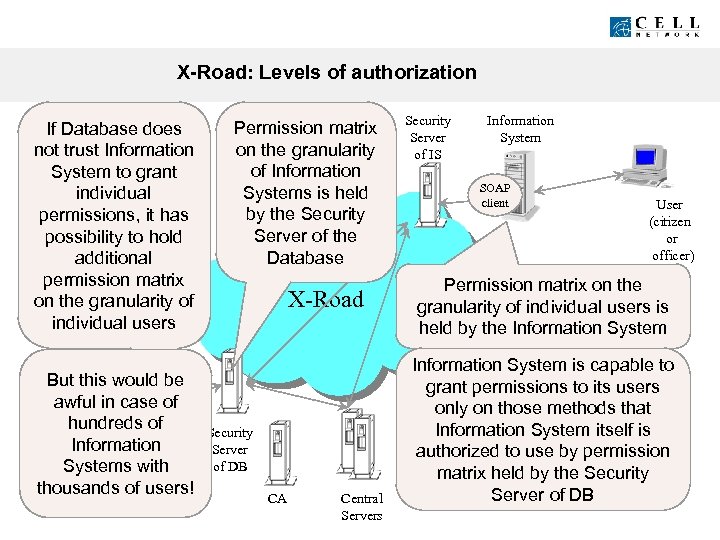
X-Road: Levels of authorization If Database does not trust Information System to grant individual permissions, it has possibility to hold additional permission matrix on the granularity of individual users But this would be awful in case of Database SOAP hundreds ofserver Information Systems with thousands of users! Permission matrix on the granularity of Information Systems is held by the Security Server of the Database Internet X-Road Security Server of DB CA Central Servers Security Server of IS Information System SOAP client User (citizen or officer) Permission matrix on the granularity of individual users is held by the Information System is capable to grant permissions to its users only on those methods that Information System itself is authorized to use by permission matrix held by the Security Server of DB
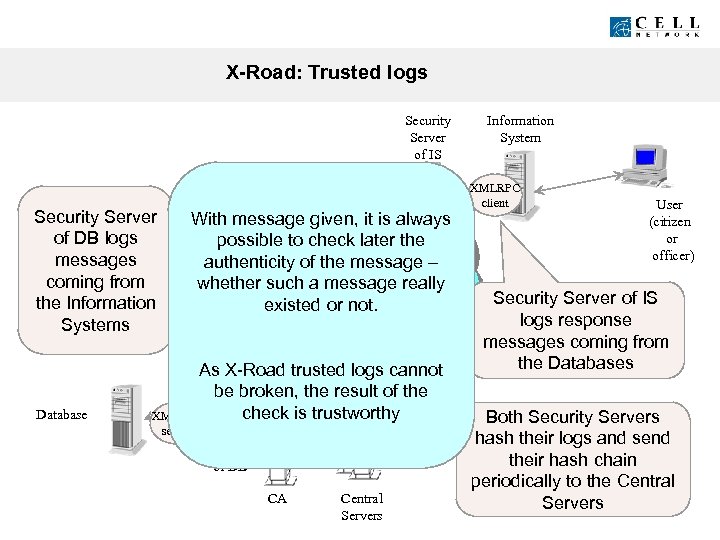
X-Road: Trusted logs Security Server of IS Security Server of DB logs messages coming from the Information Systems Database With. If evil administratoris always message given, it of any possible to check later the Security Server would even authenticity of the message – try to change the local log, Internet whether such a message really the hash in Security Server does existed or not. hash in not. X-Road match the Central Servers any more! As X-Road trusted logs cannot be broken, the result cannot Therefore, the logs of the check be trustworthy is broken XMLRPC server Security Server of DB CA Central Servers Information System XMLRPC client User (citizen or officer) Security Server of IS logs response messages coming from the Databases Both Security Servers hash their logs and send their hash chain periodically to the Central Servers
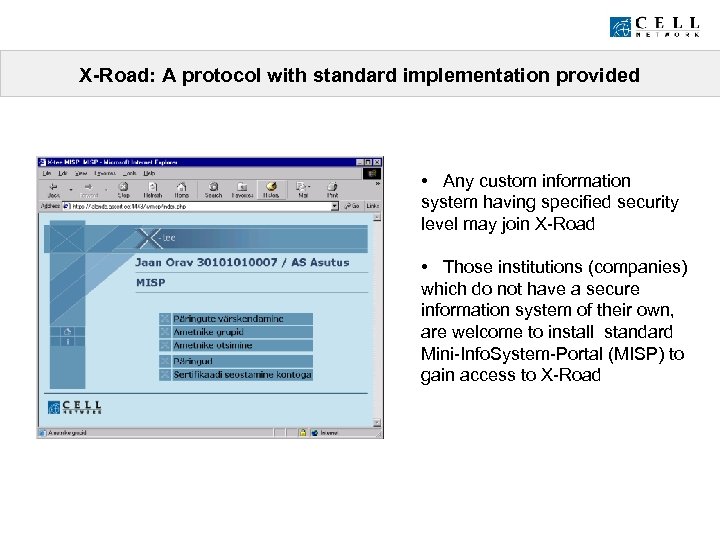
X-Road: A protocol with standard implementation provided • Any custom information system having specified security level may join X-Road • Those institutions (companies) which do not have a secure information system of their own, are welcome to install standard Mini-Info. System-Portal (MISP) to gain access to X-Road
a14455eb1ec2d3b044ee4ac87b461ba0.ppt