e457d39fbe7c2f5b3cd19326ce77d492.ppt
- Количество слайдов: 40
 www. intracom. dk Risk Management within the Context of Integrated Border Management – Some Considerations WCO ICT Conference - Seoul, 25. April 2008 Copyright © 2008 Intracom IT Services. All rights reserved. 1
www. intracom. dk Risk Management within the Context of Integrated Border Management – Some Considerations WCO ICT Conference - Seoul, 25. April 2008 Copyright © 2008 Intracom IT Services. All rights reserved. 1
 Albert Menashe CEO Intracom IT Services Denmark Copyright © 2008 Intracom IT Services. All rights reserved. 2
Albert Menashe CEO Intracom IT Services Denmark Copyright © 2008 Intracom IT Services. All rights reserved. 2
 Intracom IT Services • Formerly Compliance Solutions Department of WMdata • Recently acquired by Intracom IT Services • Considerable experience (more than 19 years) in compliance and enforcement domain • Complete business solution and methodology for compliance and enforcement • Considerable customs experience in general, inter alia, as one of the main suppliers to EU Customs Directorate (DG TAXUD) • Key player in other customs areas (e. g. NCTS) Copyright © 2008 Intracom IT Services. All rights reserved. 3
Intracom IT Services • Formerly Compliance Solutions Department of WMdata • Recently acquired by Intracom IT Services • Considerable experience (more than 19 years) in compliance and enforcement domain • Complete business solution and methodology for compliance and enforcement • Considerable customs experience in general, inter alia, as one of the main suppliers to EU Customs Directorate (DG TAXUD) • Key player in other customs areas (e. g. NCTS) Copyright © 2008 Intracom IT Services. All rights reserved. 3
 Intracom IT Services References ü more than 30 customers in over 25 countries on 5 continents ü both customs and tax ü from small administrations to very large administrations ü from single applications to comprehensive, integrated compliance solutions ü from basically compliant cultures to highly non-compliant cultures Copyright © 2008 Intracom IT Services. All rights reserved. 4
Intracom IT Services References ü more than 30 customers in over 25 countries on 5 continents ü both customs and tax ü from small administrations to very large administrations ü from single applications to comprehensive, integrated compliance solutions ü from basically compliant cultures to highly non-compliant cultures Copyright © 2008 Intracom IT Services. All rights reserved. 4
 Integrated Border Management - is IT it essential? Copyright © 2008 Intracom IT Services. All rights reserved. 5
Integrated Border Management - is IT it essential? Copyright © 2008 Intracom IT Services. All rights reserved. 5
 Integrated Border Management What is it? • • Across/between countries Across/between agencies Across regimes - people and goods Across/between processes – before, – At, – and beyond the border Copyright © 2008 Intracom IT Services. All rights reserved. 6
Integrated Border Management What is it? • • Across/between countries Across/between agencies Across regimes - people and goods Across/between processes – before, – At, – and beyond the border Copyright © 2008 Intracom IT Services. All rights reserved. 6
 Integrated Border Management And what does it that imply? • Combining organisations • Combining functions (goods + people) • Integrating processes • Sharing and/or integrating systems (Single Window) • Sharing and/or integrating data • Sharing knowledge Copyright © 2008 Intracom IT Services. All rights reserved. 7
Integrated Border Management And what does it that imply? • Combining organisations • Combining functions (goods + people) • Integrating processes • Sharing and/or integrating systems (Single Window) • Sharing and/or integrating data • Sharing knowledge Copyright © 2008 Intracom IT Services. All rights reserved. 7
 Integrated Border Management But what does it really mean? • Managing the RISK in the light of the prevailing circumstances – Inceasing (and more highly organised) • threats to security • avoidance & evasion – Ever more pressing need to facilitate trade • In an integrated manner Copyright © 2008 Intracom IT Services. All rights reserved. 8
Integrated Border Management But what does it really mean? • Managing the RISK in the light of the prevailing circumstances – Inceasing (and more highly organised) • threats to security • avoidance & evasion – Ever more pressing need to facilitate trade • In an integrated manner Copyright © 2008 Intracom IT Services. All rights reserved. 8
 IBM = IRM Copyright © 2008 Intracom IT Services. All rights reserved. 9
IBM = IRM Copyright © 2008 Intracom IT Services. All rights reserved. 9
 Risk Management of the total risk faced by the organisation Copyright © 2008 Intracom IT Services. All rights reserved. 10
Risk Management of the total risk faced by the organisation Copyright © 2008 Intracom IT Services. All rights reserved. 10
 The ESKORT Approach to Risk Managment Management of anything but the total risk is equivalent to not managing the risk at all Copyright © 2008 Intracom IT Services. All rights reserved. 11
The ESKORT Approach to Risk Managment Management of anything but the total risk is equivalent to not managing the risk at all Copyright © 2008 Intracom IT Services. All rights reserved. 11
 Integrated Risk Management What are the barriers to implementing IRM • The potential scope • Laws (e. g. protection of the individual’s rights) • Budget • Unwillingness to cooperate – political level – operational level • Lack of capacity • Lack of expertise • Limited vision Copyright © 2008 Intracom IT Services. All rights reserved. 12
Integrated Risk Management What are the barriers to implementing IRM • The potential scope • Laws (e. g. protection of the individual’s rights) • Budget • Unwillingness to cooperate – political level – operational level • Lack of capacity • Lack of expertise • Limited vision Copyright © 2008 Intracom IT Services. All rights reserved. 12
 Integrated Risk Management Limited Vision • too much focus on clearance • data ’bandwidth’ is too narrow • too much focus on known risk factors (e. g. risk profiles) • risk management as only ”identifying and quantifying” risk Copyright © 2008 Intracom IT Services. All rights reserved. 13
Integrated Risk Management Limited Vision • too much focus on clearance • data ’bandwidth’ is too narrow • too much focus on known risk factors (e. g. risk profiles) • risk management as only ”identifying and quantifying” risk Copyright © 2008 Intracom IT Services. All rights reserved. 13
 Integrated Risk Managment • Recognising and understanding potential sources/areas of risk • Determining policy for addressing risk • Identifying risk (within these areas) • Quantifying risk • Addressing the risk (in a prioritised fashion and in conformance with the policy) • Monitoring the effect Strategic Level Operational Level (Risk Analysis) Management of the total risk faced by the organisation Copyright © 2008 Intracom IT Services. All rights reserved. 14
Integrated Risk Managment • Recognising and understanding potential sources/areas of risk • Determining policy for addressing risk • Identifying risk (within these areas) • Quantifying risk • Addressing the risk (in a prioritised fashion and in conformance with the policy) • Monitoring the effect Strategic Level Operational Level (Risk Analysis) Management of the total risk faced by the organisation Copyright © 2008 Intracom IT Services. All rights reserved. 14
 Integrated Risk Management So where does that leave us • Be pragmatic – start small and proceed incrementally but in relation to an overall strategy • Must consider all the steps • Start internally and proceed outwards • Work simultaneously at level of: – business processes (before, at and beyond the border) – data (enhanced availability and access) – systems (to support the procedures and optimise use of data) Copyright © 2008 Intracom IT Services. All rights reserved. 15
Integrated Risk Management So where does that leave us • Be pragmatic – start small and proceed incrementally but in relation to an overall strategy • Must consider all the steps • Start internally and proceed outwards • Work simultaneously at level of: – business processes (before, at and beyond the border) – data (enhanced availability and access) – systems (to support the procedures and optimise use of data) Copyright © 2008 Intracom IT Services. All rights reserved. 15
 Strategic Level Copyright © 2008 Intracom IT Services. All rights reserved. 16
Strategic Level Copyright © 2008 Intracom IT Services. All rights reserved. 16
 Recognising and Understanding Risk Causes of Risk • Laws • Administrative procedures • Socio/economic situation • Political situation • Attitudes • . . . Copyright © 2008 Intracom IT Services. All rights reserved. 17
Recognising and Understanding Risk Causes of Risk • Laws • Administrative procedures • Socio/economic situation • Political situation • Attitudes • . . . Copyright © 2008 Intracom IT Services. All rights reserved. 17
 Recognising and Understanding Risk Where do we encounter risk • At any stage of the interaction with the trader (or passenger) – – – In the goods clearance process During audit During collections Coincidentally (ad-hoc) Directly Indirectly Copyright © 2008 Intracom IT Services. All rights reserved. 18
Recognising and Understanding Risk Where do we encounter risk • At any stage of the interaction with the trader (or passenger) – – – In the goods clearance process During audit During collections Coincidentally (ad-hoc) Directly Indirectly Copyright © 2008 Intracom IT Services. All rights reserved. 18
 Recognising and Undestanding Risk How do we encounter risk • Incorrect reporting – False/erroneous – Partial reporting – Under-reporting • Non-payment • Interaction with other agencies • Suspicious activities • Coincidentally • In other connections Copyright © 2008 Intracom IT Services. All rights reserved. 19
Recognising and Undestanding Risk How do we encounter risk • Incorrect reporting – False/erroneous – Partial reporting – Under-reporting • Non-payment • Interaction with other agencies • Suspicious activities • Coincidentally • In other connections Copyright © 2008 Intracom IT Services. All rights reserved. 19
 Recognising and Understanding Risk management is directed at: • the voluntarily compliant – informative (pro-actively help them to avoid mistakes) – corrective (re-actively helping them to understand correct unintended errors) • the non-compliant – preventive (keep them from deviating by sending a strong signal) – corrective (taking punitive action based on targeted identification) Copyright © 2008 Intracom IT Services. All rights reserved. 20
Recognising and Understanding Risk management is directed at: • the voluntarily compliant – informative (pro-actively help them to avoid mistakes) – corrective (re-actively helping them to understand correct unintended errors) • the non-compliant – preventive (keep them from deviating by sending a strong signal) – corrective (taking punitive action based on targeted identification) Copyright © 2008 Intracom IT Services. All rights reserved. 20
 Determining Policy for Risk Depends on organisational strategy • • Maximise revenue Reduce crime Reduce corruption Improve security Improve voluntary compliance Improve service (trade facilitation) Etc. Copyright © 2008 Intracom IT Services. All rights reserved. 21
Determining Policy for Risk Depends on organisational strategy • • Maximise revenue Reduce crime Reduce corruption Improve security Improve voluntary compliance Improve service (trade facilitation) Etc. Copyright © 2008 Intracom IT Services. All rights reserved. 21
 Determining Policy for Risk How Do We Organise Against Risk • Internationally/Nationally • Centrally/Regionally • Separately within domains (excise, security, clearance, post clearance, intelligence, goods, passengers) • Integrated across domains • … Copyright © 2008 Intracom IT Services. All rights reserved. 22
Determining Policy for Risk How Do We Organise Against Risk • Internationally/Nationally • Centrally/Regionally • Separately within domains (excise, security, clearance, post clearance, intelligence, goods, passengers) • Integrated across domains • … Copyright © 2008 Intracom IT Services. All rights reserved. 22
 Determining Policy for Risk How Do We Eliminate/Reduce Risk • • • Coercion Service (making it easier) Incentives Information and education (of the public) Psychology Increasing the likelihood of detection Competence building Collaboration Technology Copyright © 2008 Intracom IT Services. All rights reserved. 23
Determining Policy for Risk How Do We Eliminate/Reduce Risk • • • Coercion Service (making it easier) Incentives Information and education (of the public) Psychology Increasing the likelihood of detection Competence building Collaboration Technology Copyright © 2008 Intracom IT Services. All rights reserved. 23
 Operational Level - is IT essential? Copyright © 2008 Intracom IT Services. All rights reserved. 24
Operational Level - is IT essential? Copyright © 2008 Intracom IT Services. All rights reserved. 24
 Risk Analysis ”Risk analysis without IT is like drilling for oil with a corkscrew” Copyright © 2008 Intracom IT Services. All rights reserved. 25
Risk Analysis ”Risk analysis without IT is like drilling for oil with a corkscrew” Copyright © 2008 Intracom IT Services. All rights reserved. 25
 Risk Analysis At the operational level risk management involves: • identifying the risks • evaluating the degree of risk • determining the necessary corrective actions to address the risk and the appropriate level of resources necessary to do so • confirming the risk • monitoring the efficacy of the actions Copyright © 2008 Intracom IT Services. All rights reserved. 26
Risk Analysis At the operational level risk management involves: • identifying the risks • evaluating the degree of risk • determining the necessary corrective actions to address the risk and the appropriate level of resources necessary to do so • confirming the risk • monitoring the efficacy of the actions Copyright © 2008 Intracom IT Services. All rights reserved. 26
 Identifying and Quantifying the Risk • Start by developing an overall risk model • And ensure an approach that: – Adresses all the different occurences of risk – At every level of interaction with the trader, broker, passenger, … – Is integrated across points of contact – Is quantifiable and objective – Is flexible – Has a high degree of granularity (segment orientation) – Can be integrated into the overall IT environment Copyright © 2008 Intracom IT Services. All rights reserved. 27
Identifying and Quantifying the Risk • Start by developing an overall risk model • And ensure an approach that: – Adresses all the different occurences of risk – At every level of interaction with the trader, broker, passenger, … – Is integrated across points of contact – Is quantifiable and objective – Is flexible – Has a high degree of granularity (segment orientation) – Can be integrated into the overall IT environment Copyright © 2008 Intracom IT Services. All rights reserved. 27
 Indentifying and Quantifying the Risk To get the answers that knowledge workers need, the risk management systems must have: 4 The right data (within constraints of the law) 4 Proper data structure 4 Enough detail data 4 Enough computer horsepower Copyright © 2008 Intracom IT Services. All rights reserved. 28
Indentifying and Quantifying the Risk To get the answers that knowledge workers need, the risk management systems must have: 4 The right data (within constraints of the law) 4 Proper data structure 4 Enough detail data 4 Enough computer horsepower Copyright © 2008 Intracom IT Services. All rights reserved. 28
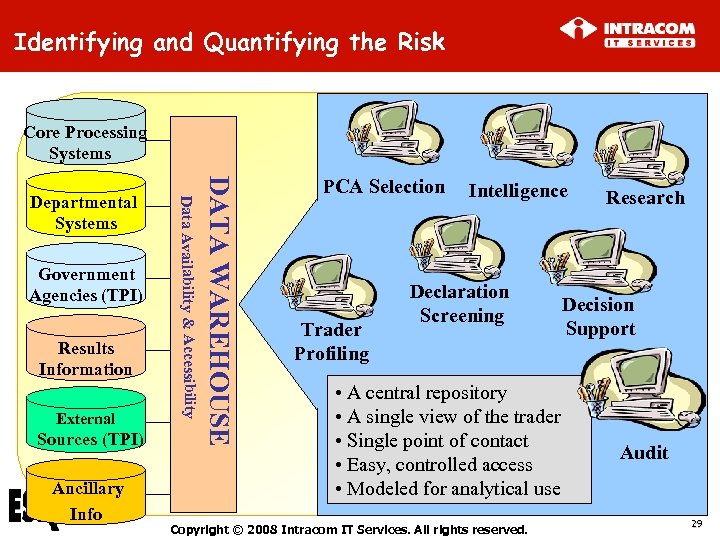 Identifying and Quantifying the Risk Core Processing Systems Results Information External Sources (TPI) Ancillary Info DATA WAREHOUSE Government Agencies (TPI) Data Availability & Accessibility Departmental Systems PCA Selection Trader Profiling Intelligence Declaration Screening • A central repository • A single view of the trader • Single point of contact • Easy, controlled access • Modeled for analytical use Copyright © 2008 Intracom IT Services. All rights reserved. Research Decision Support Audit 29
Identifying and Quantifying the Risk Core Processing Systems Results Information External Sources (TPI) Ancillary Info DATA WAREHOUSE Government Agencies (TPI) Data Availability & Accessibility Departmental Systems PCA Selection Trader Profiling Intelligence Declaration Screening • A central repository • A single view of the trader • Single point of contact • Easy, controlled access • Modeled for analytical use Copyright © 2008 Intracom IT Services. All rights reserved. Research Decision Support Audit 29
 Identifying and Quantifying the Risk • Data is only the first step - the question is how to get the most out of the data • A number of different analytical tools and methods are available • The choice of tools must match the needs of the application area - certain tools are suitable for certain types of analysis but not for others Copyright © 2008 Intracom IT Services. All rights reserved. 30
Identifying and Quantifying the Risk • Data is only the first step - the question is how to get the most out of the data • A number of different analytical tools and methods are available • The choice of tools must match the needs of the application area - certain tools are suitable for certain types of analysis but not for others Copyright © 2008 Intracom IT Services. All rights reserved. 30
 Identifying and Quantifying Risk We need to be able to support both transactional and behavioural risk analysis • Transactional risk analysis (real time) – – Declaration screening • import/export/transit declarations • pre-arrival information (manifest etc. ) Passenger screening Screening of suspicious activity reports etc. • Behavioural risk analysis (batch-oriented) – – – General risk profiling (traders, passengers) • certification (AEO, etc. ) • case selection (post clearance audit, criminal investigations) Risk analysis of financial information (during audit) etc. Copyright © 2008 Intracom IT Services. All rights reserved. 32
Identifying and Quantifying Risk We need to be able to support both transactional and behavioural risk analysis • Transactional risk analysis (real time) – – Declaration screening • import/export/transit declarations • pre-arrival information (manifest etc. ) Passenger screening Screening of suspicious activity reports etc. • Behavioural risk analysis (batch-oriented) – – – General risk profiling (traders, passengers) • certification (AEO, etc. ) • case selection (post clearance audit, criminal investigations) Risk analysis of financial information (during audit) etc. Copyright © 2008 Intracom IT Services. All rights reserved. 32
 Identifying and Quantifying Risk Methods • Data Mining - for detection of hitherto unknown patterns and hypothesis generation • Knowledge-based Analysis – for identification and quantification of the risk - reasons on the basis of a set of rules which are derived from both human knowledge and experience and from the output of data mining • Need a formalised approach for verifying and transforming the hypotheses of the data mining approach to the grammar of the knowledge-based system Copyright © 2008 Intracom IT Services. All rights reserved. 33
Identifying and Quantifying Risk Methods • Data Mining - for detection of hitherto unknown patterns and hypothesis generation • Knowledge-based Analysis – for identification and quantification of the risk - reasons on the basis of a set of rules which are derived from both human knowledge and experience and from the output of data mining • Need a formalised approach for verifying and transforming the hypotheses of the data mining approach to the grammar of the knowledge-based system Copyright © 2008 Intracom IT Services. All rights reserved. 33
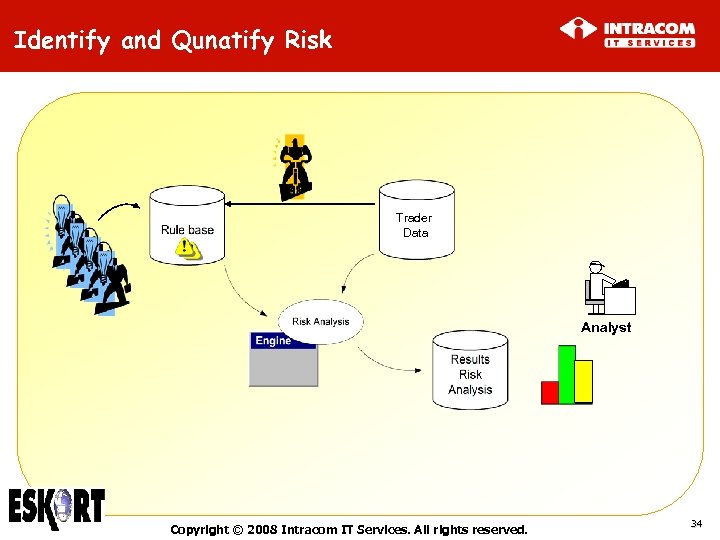 Identify and Qunatify Risk Trader Data Analyst Copyright © 2008 Intracom IT Services. All rights reserved. 34
Identify and Qunatify Risk Trader Data Analyst Copyright © 2008 Intracom IT Services. All rights reserved. 34
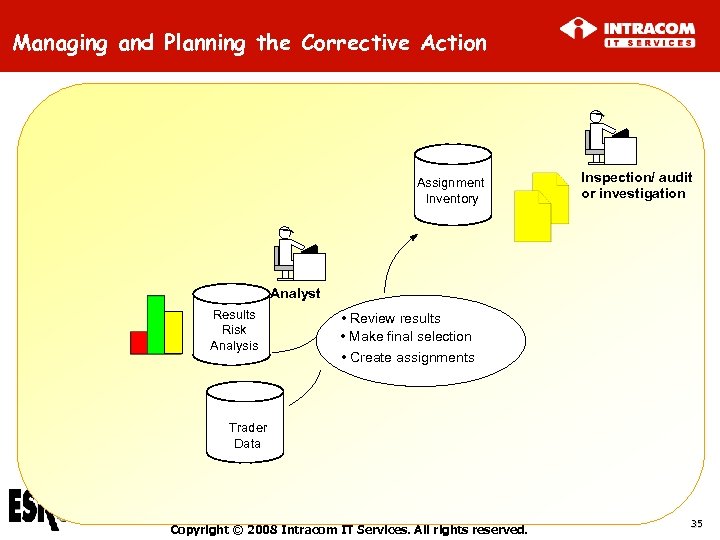 Managing and Planning the Corrective Action Assignment Inventory Inspection/ audit or investigation Analyst Results Risk Analysis • Review results • Make final selection • Create assignments Trader Data Copyright © 2008 Intracom IT Services. All rights reserved. 35
Managing and Planning the Corrective Action Assignment Inventory Inspection/ audit or investigation Analyst Results Risk Analysis • Review results • Make final selection • Create assignments Trader Data Copyright © 2008 Intracom IT Services. All rights reserved. 35
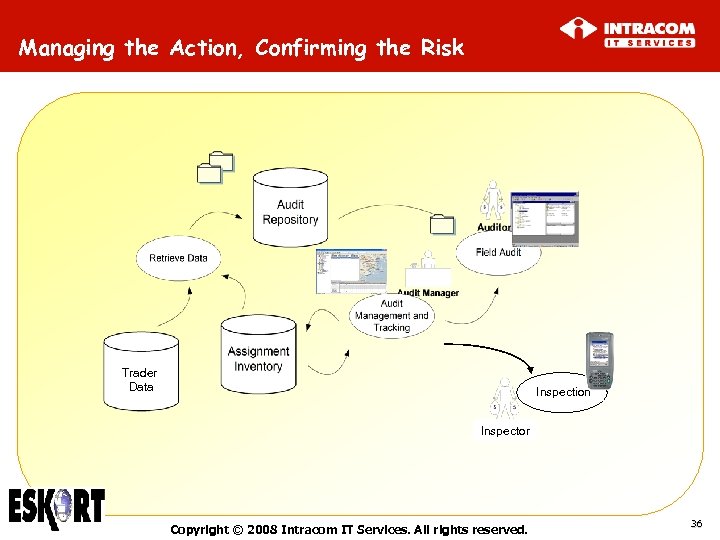 Managing the Action, Confirming the Risk Trader Data Inspection Inspector Copyright © 2008 Intracom IT Services. All rights reserved. 36
Managing the Action, Confirming the Risk Trader Data Inspection Inspector Copyright © 2008 Intracom IT Services. All rights reserved. 36
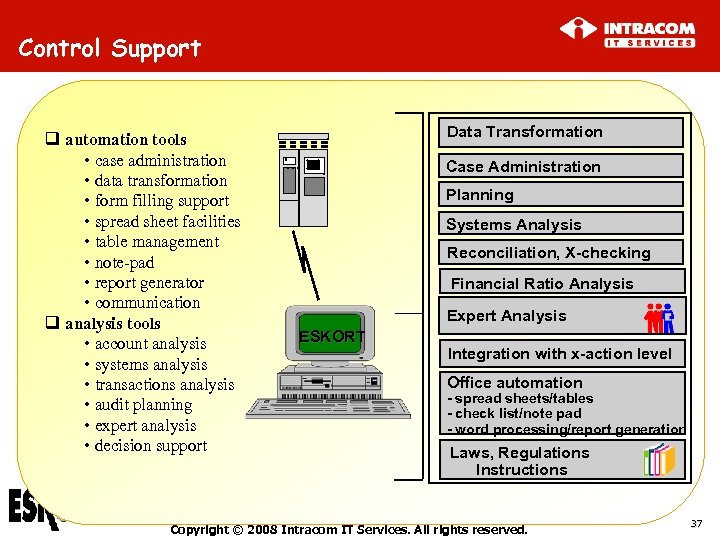 Control Support q automation tools • case administration • data transformation • form filling support • spread sheet facilities • table management • note-pad • report generator • communication q analysis tools • account analysis • systems analysis • transactions analysis • audit planning • expert analysis • decision support Data Transformation . . Case Administration Planning Systems Analysis Reconciliation, X-checking Financial Ratio Analysis Expert Analysis ESKORT Integration with x-action level Office automation - spread sheets/tables - check list/note pad - word processing/report generation Laws, Regulations Instructions Copyright © 2008 Intracom IT Services. All rights reserved. 37
Control Support q automation tools • case administration • data transformation • form filling support • spread sheet facilities • table management • note-pad • report generator • communication q analysis tools • account analysis • systems analysis • transactions analysis • audit planning • expert analysis • decision support Data Transformation . . Case Administration Planning Systems Analysis Reconciliation, X-checking Financial Ratio Analysis Expert Analysis ESKORT Integration with x-action level Office automation - spread sheets/tables - check list/note pad - word processing/report generation Laws, Regulations Instructions Copyright © 2008 Intracom IT Services. All rights reserved. 37
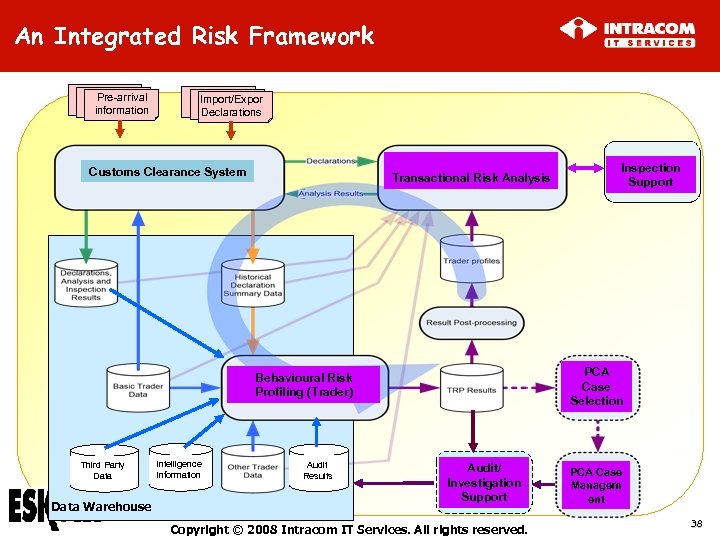 An Integrated Risk Framework Pre-arrival information Import/Expor Declarations Customs Clearance System Transactional Risk Analysis PCA Case Selection Behavioural Risk Profiling (Trader) Third Party Data Warehouse Intelligence Information Audit Results Inspection Support Audit/ Investigation Support Copyright © 2008 Intracom IT Services. All rights reserved. PCA Case Managem ent 38
An Integrated Risk Framework Pre-arrival information Import/Expor Declarations Customs Clearance System Transactional Risk Analysis PCA Case Selection Behavioural Risk Profiling (Trader) Third Party Data Warehouse Intelligence Information Audit Results Inspection Support Audit/ Investigation Support Copyright © 2008 Intracom IT Services. All rights reserved. PCA Case Managem ent 38
 The Process • Parallel Streams – Process stream – Data stream – Systems stream – Knowledge content stream Copyright © 2008 Intracom IT Services. All rights reserved. 40
The Process • Parallel Streams – Process stream – Data stream – Systems stream – Knowledge content stream Copyright © 2008 Intracom IT Services. All rights reserved. 40
 The Next Step – A vision What next: developing a common language and grammar for expressing risk • developing a mechanism for transmitting risk information between shareholders • Developing a collaborative working model for risk – A risk clearing house? – Defining jurisdictions (international/ agency/ central/ local) • Copyright © 2008 Intracom IT Services. All rights reserved. 41
The Next Step – A vision What next: developing a common language and grammar for expressing risk • developing a mechanism for transmitting risk information between shareholders • Developing a collaborative working model for risk – A risk clearing house? – Defining jurisdictions (international/ agency/ central/ local) • Copyright © 2008 Intracom IT Services. All rights reserved. 41
 Questions and Answers Copyright © 2008 Intracom IT Services. All rights reserved. 42
Questions and Answers Copyright © 2008 Intracom IT Services. All rights reserved. 42


