fe6135d12872d180d7b9e9418adc7b71.ppt
- Количество слайдов: 50
 WWW and Security CS 587 x Lecture Department of Computer Science Iowa State University
WWW and Security CS 587 x Lecture Department of Computer Science Iowa State University
 Internet Security Issues A TCP/IP packet could go through many intermediate computers and separate networks Possible ways for communication interference Eavesdropping n w Information remains intact, but its privacy is compromised. For example, someone could learn your credit card number, etc. Tampering n w Information in transit is changed or replaced and then sent on to the recipient. For example, someone could alter an order of goods Impersonation n w Information passes to a person who poses as the intended recipient. For example, a person can pretend to have the email address jdoe@mozilla. com or a computer can identify itself as www. mozilla. com while it is not
Internet Security Issues A TCP/IP packet could go through many intermediate computers and separate networks Possible ways for communication interference Eavesdropping n w Information remains intact, but its privacy is compromised. For example, someone could learn your credit card number, etc. Tampering n w Information in transit is changed or replaced and then sent on to the recipient. For example, someone could alter an order of goods Impersonation n w Information passes to a person who poses as the intended recipient. For example, a person can pretend to have the email address jdoe@mozilla. com or a computer can identify itself as www. mozilla. com while it is not
 Public-Key Cryptography The goals of developing this standard n Encryption and decryption w Allow two communication parties to disguise information they send to each other n Tamper detection w Allows the recipient of information to verify that it has not been modified in transit n Authentication w Allows the recipient of information to determine its origin, i. e. , confirm the sender’s identity n Nonrepudiation w Prevents the sender of information from claiming at a later date that the information was never sent
Public-Key Cryptography The goals of developing this standard n Encryption and decryption w Allow two communication parties to disguise information they send to each other n Tamper detection w Allows the recipient of information to verify that it has not been modified in transit n Authentication w Allows the recipient of information to determine its origin, i. e. , confirm the sender’s identity n Nonrepudiation w Prevents the sender of information from claiming at a later date that the information was never sent
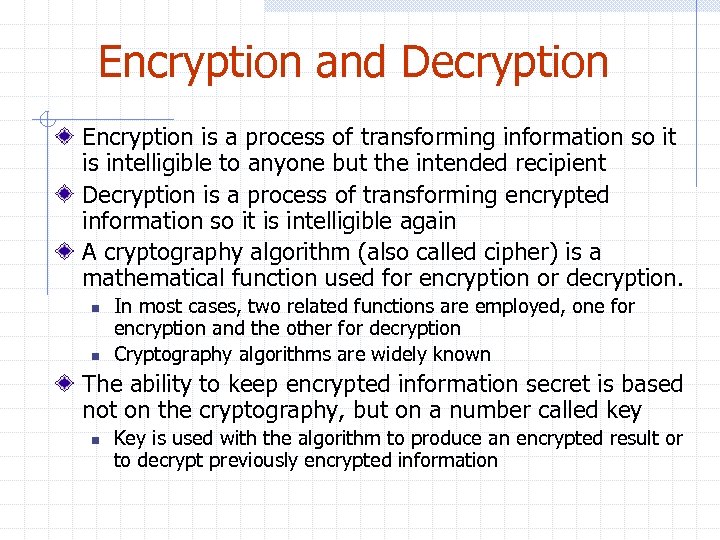 Encryption and Decryption Encryption is a process of transforming information so it is intelligible to anyone but the intended recipient Decryption is a process of transforming encrypted information so it is intelligible again A cryptography algorithm (also called cipher) is a mathematical function used for encryption or decryption. n n In most cases, two related functions are employed, one for encryption and the other for decryption Cryptography algorithms are widely known The ability to keep encrypted information secret is based not on the cryptography, but on a number called key n Key is used with the algorithm to produce an encrypted result or to decrypt previously encrypted information
Encryption and Decryption Encryption is a process of transforming information so it is intelligible to anyone but the intended recipient Decryption is a process of transforming encrypted information so it is intelligible again A cryptography algorithm (also called cipher) is a mathematical function used for encryption or decryption. n n In most cases, two related functions are employed, one for encryption and the other for decryption Cryptography algorithms are widely known The ability to keep encrypted information secret is based not on the cryptography, but on a number called key n Key is used with the algorithm to produce an encrypted result or to decrypt previously encrypted information
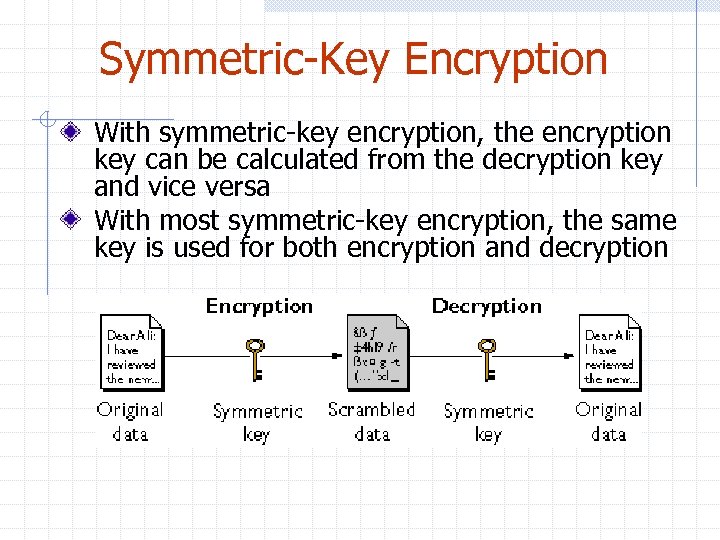 Symmetric-Key Encryption With symmetric-key encryption, the encryption key can be calculated from the decryption key and vice versa With most symmetric-key encryption, the same key is used for both encryption and decryption
Symmetric-Key Encryption With symmetric-key encryption, the encryption key can be calculated from the decryption key and vice versa With most symmetric-key encryption, the same key is used for both encryption and decryption
 Symmetric-Key Encryption Advantages n Highly efficient implementation w n fast encryption and decryption Provides some degree of authentication w information encrypted with one symmetric key cannot be decrypted with any other symmetric key. Disadvantages n n Effective only if the key is kept secret by the two parties involved If anyone else discovers the key, it affects both confidentiality and authentication w The person not only can decrypt messages sent with that key, but can encrypt new messages and send them as if they came from one of the two parties who were originally using the key
Symmetric-Key Encryption Advantages n Highly efficient implementation w n fast encryption and decryption Provides some degree of authentication w information encrypted with one symmetric key cannot be decrypted with any other symmetric key. Disadvantages n n Effective only if the key is kept secret by the two parties involved If anyone else discovers the key, it affects both confidentiality and authentication w The person not only can decrypt messages sent with that key, but can encrypt new messages and send them as if they came from one of the two parties who were originally using the key
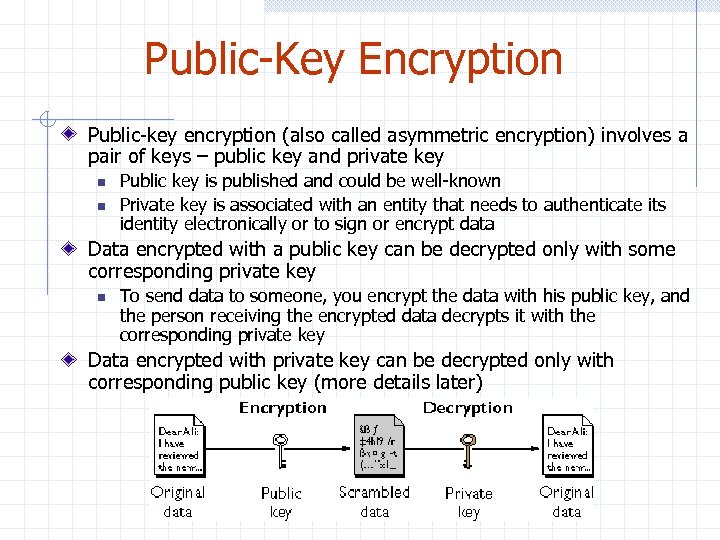 Public-Key Encryption Public-key encryption (also called asymmetric encryption) involves a pair of keys – public key and private key n n Public key is published and could be well-known Private key is associated with an entity that needs to authenticate its identity electronically or to sign or encrypt data Data encrypted with a public key can be decrypted only with some corresponding private key n To send data to someone, you encrypt the data with his public key, and the person receiving the encrypted data decrypts it with the corresponding private key Data encrypted with private key can be decrypted only with corresponding public key (more details later)
Public-Key Encryption Public-key encryption (also called asymmetric encryption) involves a pair of keys – public key and private key n n Public key is published and could be well-known Private key is associated with an entity that needs to authenticate its identity electronically or to sign or encrypt data Data encrypted with a public key can be decrypted only with some corresponding private key n To send data to someone, you encrypt the data with his public key, and the person receiving the encrypted data decrypts it with the corresponding private key Data encrypted with private key can be decrypted only with corresponding public key (more details later)
 Public-Key Encryption Advantage n n Allow to freely distribute public key to the sender Private key can be kept in secret Disadvantage n Compared with symmetric-key encryption, public-key encryption requires more computation and is therefore not always appropriate for large amounts of data The way to leverage the advantage and minimize the disadvantage n Use public-key encryption to send a symmetric key, which can be then be used to encrypt additional data. This is the approach used by the SSL protocol
Public-Key Encryption Advantage n n Allow to freely distribute public key to the sender Private key can be kept in secret Disadvantage n Compared with symmetric-key encryption, public-key encryption requires more computation and is therefore not always appropriate for large amounts of data The way to leverage the advantage and minimize the disadvantage n Use public-key encryption to send a symmetric key, which can be then be used to encrypt additional data. This is the approach used by the SSL protocol
 Temper Detection Encryption and decryption solves only the problem of eavesdropping The problem of tampering and impersonation remains n n Tamper detection is done by using public-key encryption for digital signature Impersonation can be addressed by certification and authentication
Temper Detection Encryption and decryption solves only the problem of eavesdropping The problem of tampering and impersonation remains n n Tamper detection is done by using public-key encryption for digital signature Impersonation can be addressed by certification and authentication
 Digital Signature Tamer detection replies on a mathematical function called a one-way hash (also called a message digest) A one-way hash is a number of fixed length with the following characteristics n n Ideally, the value of the hash is unique for the hashed data. Any change in the data, even deleting or altering a single character, results in different value The content of the hashed data cannot, for all practical purposes, be deduced from the hash – which is why it is called “one-way”
Digital Signature Tamer detection replies on a mathematical function called a one-way hash (also called a message digest) A one-way hash is a number of fixed length with the following characteristics n n Ideally, the value of the hash is unique for the hashed data. Any change in the data, even deleting or altering a single character, results in different value The content of the hashed data cannot, for all practical purposes, be deduced from the hash – which is why it is called “one-way”
 Digital Signature Public-key encryption allows you to use your private key for encryption and your public key for decryption This feature can be used to digitally signing any data n n The signing software creates a one-way hash of the data, then uses your private key to encrypt the hash The encrypted hash, along with other information, such as the hashing algorithm, is known as a digital signature
Digital Signature Public-key encryption allows you to use your private key for encryption and your public key for decryption This feature can be used to digitally signing any data n n The signing software creates a one-way hash of the data, then uses your private key to encrypt the hash The encrypted hash, along with other information, such as the hashing algorithm, is known as a digital signature
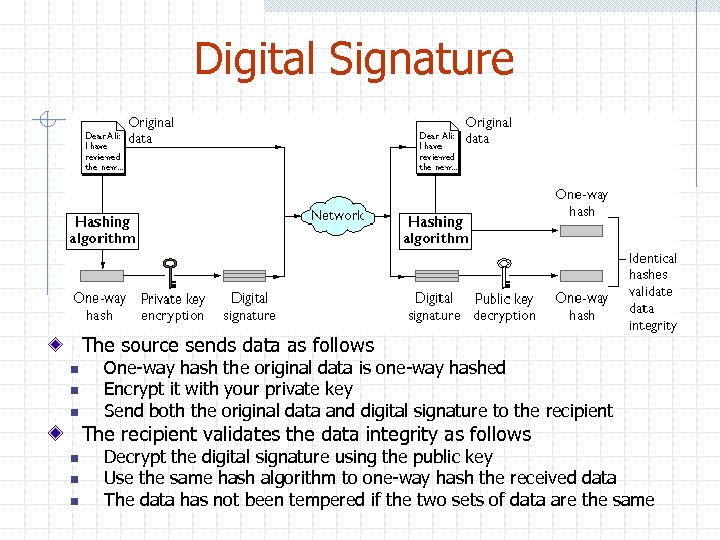 Digital Signature The source sends data as follows n n n One-way hash the original data is one-way hashed Encrypt it with your private key Send both the original data and digital signature to the recipient The recipient validates the data integrity as follows n n n Decrypt the digital signature using the public key Use the same hash algorithm to one-way hash the received data The data has not been tempered if the two sets of data are the same
Digital Signature The source sends data as follows n n n One-way hash the original data is one-way hashed Encrypt it with your private key Send both the original data and digital signature to the recipient The recipient validates the data integrity as follows n n n Decrypt the digital signature using the public key Use the same hash algorithm to one-way hash the received data The data has not been tempered if the two sets of data are the same
 A Certificate Identifies an Entity What is certificate? n A certificate is an electronic document used to identify an individual, a server, a company, or some other entity w Just like a driver license identifies a person Who issues certificate? n Certificate Authorities (CA) w can be either independent third party or organizations running their certificate-issuing server software n Before issuing a certificate, CA must go through certain verification procedures, depending on the CA’s policies
A Certificate Identifies an Entity What is certificate? n A certificate is an electronic document used to identify an individual, a server, a company, or some other entity w Just like a driver license identifies a person Who issues certificate? n Certificate Authorities (CA) w can be either independent third party or organizations running their certificate-issuing server software n Before issuing a certificate, CA must go through certain verification procedures, depending on the CA’s policies
 Certificate Content Each certificate always n binds a particular public key to the certified entity w Only the public key certified by the certificate will work with the corresponding private key possessed by the owner of the certificate n includes the digital signature of the issuing CA w For tempering detection - you cannot change a certificate w The signature allows the certificate to function as a “letter of introduction” for users who know and trust the CA but don’t know the entity identified by the certificate Of course, a certificate also includes the name of the entity it identifies, an expiration date, the name the of CA that issued the certificate
Certificate Content Each certificate always n binds a particular public key to the certified entity w Only the public key certified by the certificate will work with the corresponding private key possessed by the owner of the certificate n includes the digital signature of the issuing CA w For tempering detection - you cannot change a certificate w The signature allows the certificate to function as a “letter of introduction” for users who know and trust the CA but don’t know the entity identified by the certificate Of course, a certificate also includes the name of the entity it identifies, an expiration date, the name the of CA that issued the certificate
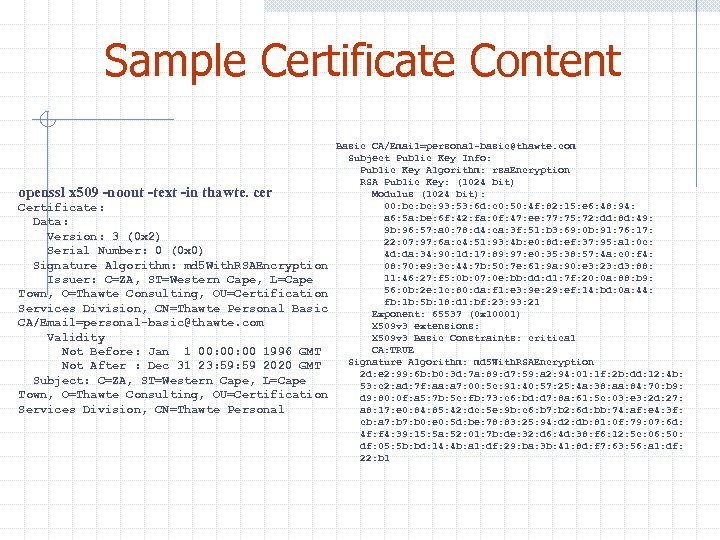 Sample Certificate Content openssl x 509 -noout -text -in thawte. cer Certificate: Data: Version: 3 (0 x 2) Serial Number: 0 (0 x 0) Signature Algorithm: md 5 With. RSAEncryption Issuer: C=ZA, ST=Western Cape, L=Cape Town, O=Thawte Consulting, OU=Certification Services Division, CN=Thawte Personal Basic CA/Email=personal-basic@thawte. com Validity Not Before: Jan 1 00: 00 1996 GMT Not After : Dec 31 23: 59 2020 GMT Subject: C=ZA, ST=Western Cape, L=Cape Town, O=Thawte Consulting, OU=Certification Services Division, CN=Thawte Personal Basic CA/Email=personal-basic@thawte. com Subject Public Key Info: Public Key Algorithm: rsa. Encryption RSA Public Key: (1024 bit) Modulus (1024 bit): 00: bc: 93: 53: 6 d: c 0: 50: 4 f: 82: 15: e 6: 48: 94: a 6: 5 a: be: 6 f: 42: fa: 0 f: 47: ee: 77: 75: 72: dd: 8 d: 49: 9 b: 96: 57: a 0: 78: d 4: ca: 3 f: 51: b 3: 69: 0 b: 91: 76: 17: 22: 07: 97: 6 a: c 4: 51: 93: 4 b: e 0: 8 d: ef: 37: 95: a 1: 0 c: 4 d: da: 34: 90: 1 d: 17: 89: 97: e 0: 35: 38: 57: 4 a: c 0: f 4: 08: 70: e 9: 3 c: 44: 7 b: 50: 7 e: 61: 9 a: 90: e 3: 23: d 3: 88: 11: 46: 27: f 5: 0 b: 07: 0 e: bb: dd: d 1: 7 f: 20: 0 a: 88: b 9: 56: 0 b: 2 e: 1 c: 80: da: f 1: e 3: 9 e: 29: ef: 14: bd: 0 a: 44: fb: 1 b: 5 b: 18: d 1: bf: 23: 93: 21 Exponent: 65537 (0 x 10001) X 509 v 3 extensions: X 509 v 3 Basic Constraints: critical CA: TRUE Signature Algorithm: md 5 With. RSAEncryption 2 d: e 2: 99: 6 b: b 0: 3 d: 7 a: 89: d 7: 59: a 2: 94: 01: 1 f: 2 b: dd: 12: 4 b: 53: c 2: ad: 7 f: aa: a 7: 00: 5 c: 91: 40: 57: 25: 4 a: 38: aa: 84: 70: b 9: d 9: 80: 0 f: a 5: 7 b: 5 c: fb: 73: c 6: bd: d 7: 8 a: 61: 5 c: 03: e 3: 2 d: 27: a 8: 17: e 0: 84: 85: 42: dc: 5 e: 9 b: c 6: b 7: b 2: 6 d: bb: 74: af: e 4: 3 f: cb: a 7: b 0: e 0: 5 d: be: 78: 83: 25: 94: d 2: db: 81: 0 f: 79: 07: 6 d: 4 f: f 4: 39: 15: 5 a: 52: 01: 7 b: de: 32: d 6: 4 d: 38: f 6: 12: 5 c: 06: 50: df: 05: 5 b: bd: 14: 4 b: a 1: df: 29: ba: 3 b: 41: 8 d: f 7: 63: 56: a 1: df: 22: b 1
Sample Certificate Content openssl x 509 -noout -text -in thawte. cer Certificate: Data: Version: 3 (0 x 2) Serial Number: 0 (0 x 0) Signature Algorithm: md 5 With. RSAEncryption Issuer: C=ZA, ST=Western Cape, L=Cape Town, O=Thawte Consulting, OU=Certification Services Division, CN=Thawte Personal Basic CA/Email=personal-basic@thawte. com Validity Not Before: Jan 1 00: 00 1996 GMT Not After : Dec 31 23: 59 2020 GMT Subject: C=ZA, ST=Western Cape, L=Cape Town, O=Thawte Consulting, OU=Certification Services Division, CN=Thawte Personal Basic CA/Email=personal-basic@thawte. com Subject Public Key Info: Public Key Algorithm: rsa. Encryption RSA Public Key: (1024 bit) Modulus (1024 bit): 00: bc: 93: 53: 6 d: c 0: 50: 4 f: 82: 15: e 6: 48: 94: a 6: 5 a: be: 6 f: 42: fa: 0 f: 47: ee: 77: 75: 72: dd: 8 d: 49: 9 b: 96: 57: a 0: 78: d 4: ca: 3 f: 51: b 3: 69: 0 b: 91: 76: 17: 22: 07: 97: 6 a: c 4: 51: 93: 4 b: e 0: 8 d: ef: 37: 95: a 1: 0 c: 4 d: da: 34: 90: 1 d: 17: 89: 97: e 0: 35: 38: 57: 4 a: c 0: f 4: 08: 70: e 9: 3 c: 44: 7 b: 50: 7 e: 61: 9 a: 90: e 3: 23: d 3: 88: 11: 46: 27: f 5: 0 b: 07: 0 e: bb: dd: d 1: 7 f: 20: 0 a: 88: b 9: 56: 0 b: 2 e: 1 c: 80: da: f 1: e 3: 9 e: 29: ef: 14: bd: 0 a: 44: fb: 1 b: 5 b: 18: d 1: bf: 23: 93: 21 Exponent: 65537 (0 x 10001) X 509 v 3 extensions: X 509 v 3 Basic Constraints: critical CA: TRUE Signature Algorithm: md 5 With. RSAEncryption 2 d: e 2: 99: 6 b: b 0: 3 d: 7 a: 89: d 7: 59: a 2: 94: 01: 1 f: 2 b: dd: 12: 4 b: 53: c 2: ad: 7 f: aa: a 7: 00: 5 c: 91: 40: 57: 25: 4 a: 38: aa: 84: 70: b 9: d 9: 80: 0 f: a 5: 7 b: 5 c: fb: 73: c 6: bd: d 7: 8 a: 61: 5 c: 03: e 3: 2 d: 27: a 8: 17: e 0: 84: 85: 42: dc: 5 e: 9 b: c 6: b 7: b 2: 6 d: bb: 74: af: e 4: 3 f: cb: a 7: b 0: e 0: 5 d: be: 78: 83: 25: 94: d 2: db: 81: 0 f: 79: 07: 6 d: 4 f: f 4: 39: 15: 5 a: 52: 01: 7 b: de: 32: d 6: 4 d: 38: f 6: 12: 5 c: 06: 50: df: 05: 5 b: bd: 14: 4 b: a 1: df: 29: ba: 3 b: 41: 8 d: f 7: 63: 56: a 1: df: 22: b 1
 Authentication Confirms an Identity Password-based authentication 1. 2. A client submits user name and password Server checks database to see if name and password match Certificate-based authentication 1. A client digitally signs some piece of data, which are randomly generated based on the input from server and client w 2. 3. Both client and server must know exactly the data to be signed The client sends both the certificate and the signed data to the server The server uses the public key in the certificate to decode the signed data w The signed data is an “evidence” used to verify if the client owns the private key corresponding to the public key stored in its certificate
Authentication Confirms an Identity Password-based authentication 1. 2. A client submits user name and password Server checks database to see if name and password match Certificate-based authentication 1. A client digitally signs some piece of data, which are randomly generated based on the input from server and client w 2. 3. Both client and server must know exactly the data to be signed The client sends both the certificate and the signed data to the server The server uses the public key in the certificate to decode the signed data w The signed data is an “evidence” used to verify if the client owns the private key corresponding to the public key stored in its certificate
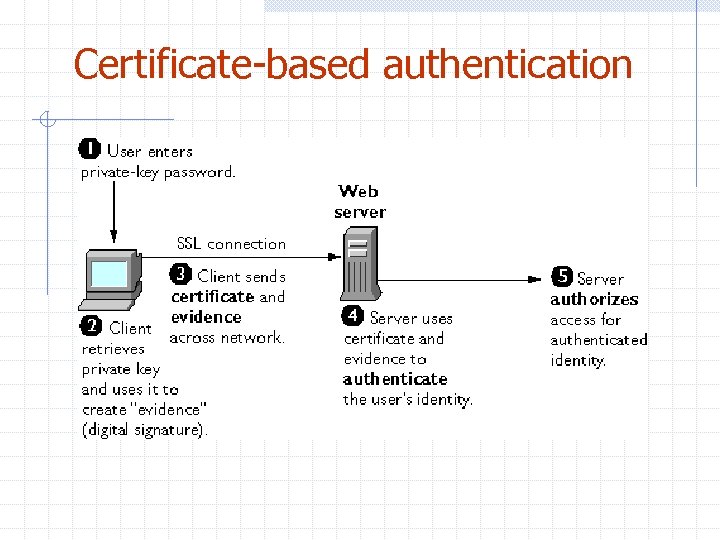 Certificate-based authentication
Certificate-based authentication
 Types of Certificates Client/server certificates n Used to authenticate client/server via SSL S/MIMI certificates n Used for signed and encrypted email Object certificates n Used to identify signers of Java code or other signed files CA certificates n Used to identify Certificate Authorities that can be trusted
Types of Certificates Client/server certificates n Used to authenticate client/server via SSL S/MIMI certificates n Used for signed and encrypted email Object certificates n Used to identify signers of Java code or other signed files CA certificates n Used to identify Certificate Authorities that can be trusted
 Establishing trust through CA Certificates Any client/server software that supports certificates maintains a collection of trusted CA certificates It is possible to delegate certificate-issuing responsibility to subordinate CAs, thus, creating CA hierarchies n n n The root CA’s certificate is a self-signed certificates, i. e. , it is digitally signed by the same entity The CAs that are directly subordinate to the root CA have CA certificate signed by the root CA CAs under the subordinate CAs in the hierarchy have their CA signed the higher-level subordinate CAs
Establishing trust through CA Certificates Any client/server software that supports certificates maintains a collection of trusted CA certificates It is possible to delegate certificate-issuing responsibility to subordinate CAs, thus, creating CA hierarchies n n n The root CA’s certificate is a self-signed certificates, i. e. , it is digitally signed by the same entity The CAs that are directly subordinate to the root CA have CA certificate signed by the root CA CAs under the subordinate CAs in the hierarchy have their CA signed the higher-level subordinate CAs
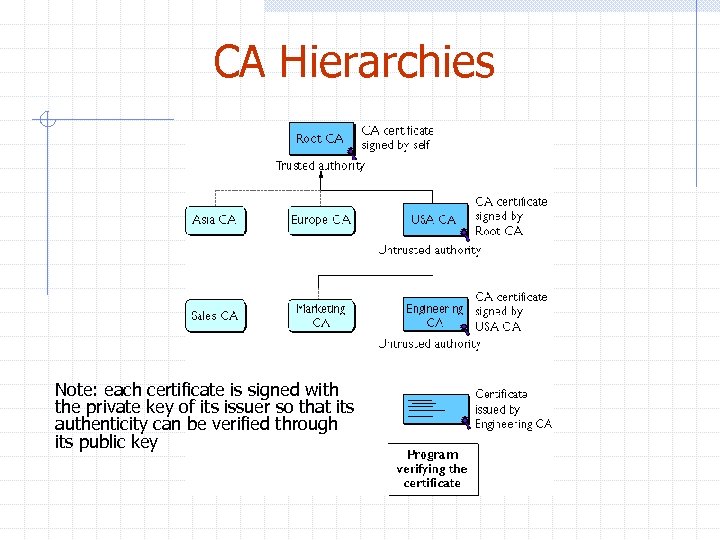 CA Hierarchies Note: each certificate is signed with the private key of its issuer so that its authenticity can be verified through its public key
CA Hierarchies Note: each certificate is signed with the private key of its issuer so that its authenticity can be verified through its public key
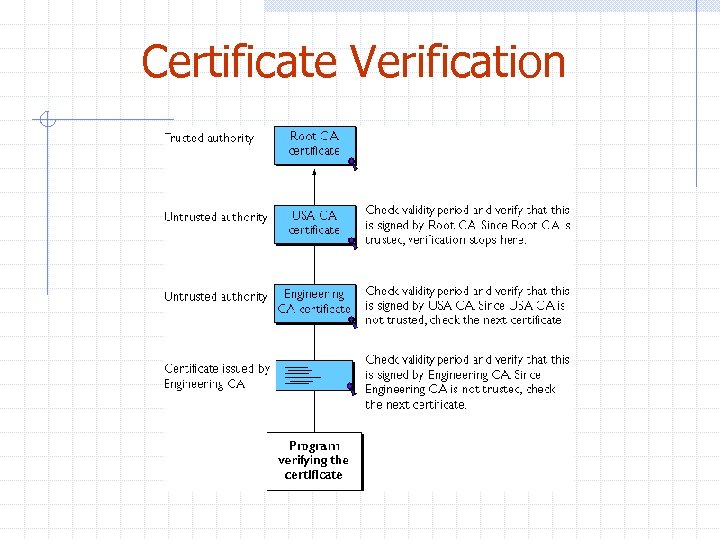 Certificate Verification
Certificate Verification
 Certificate Standards X. 509 Standard n n n Created to provide credentials for X. 500 directory objects V 1 published as part of X. 500 directory recommendations V 3 (1996) added much flexibility w added provisions for “extension” fields (“V 3 extensions”) n V 3 use pretty much universal for Internet applications w supports mail, c/s, IPsec w alternatives limited to special purposes, e. g PGP certificates
Certificate Standards X. 509 Standard n n n Created to provide credentials for X. 500 directory objects V 1 published as part of X. 500 directory recommendations V 3 (1996) added much flexibility w added provisions for “extension” fields (“V 3 extensions”) n V 3 use pretty much universal for Internet applications w supports mail, c/s, IPsec w alternatives limited to special purposes, e. g PGP certificates
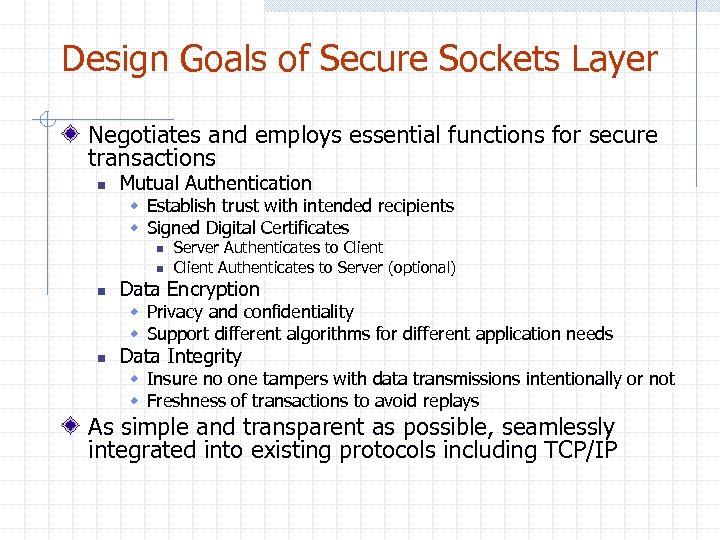 Design Goals of Secure Sockets Layer Negotiates and employs essential functions for secure transactions n Mutual Authentication w Establish trust with intended recipients w Signed Digital Certificates n n n Server Authenticates to Client Authenticates to Server (optional) Data Encryption w Privacy and confidentiality w Support different algorithms for different application needs n Data Integrity w Insure no one tampers with data transmissions intentionally or not w Freshness of transactions to avoid replays As simple and transparent as possible, seamlessly integrated into existing protocols including TCP/IP
Design Goals of Secure Sockets Layer Negotiates and employs essential functions for secure transactions n Mutual Authentication w Establish trust with intended recipients w Signed Digital Certificates n n n Server Authenticates to Client Authenticates to Server (optional) Data Encryption w Privacy and confidentiality w Support different algorithms for different application needs n Data Integrity w Insure no one tampers with data transmissions intentionally or not w Freshness of transactions to avoid replays As simple and transparent as possible, seamlessly integrated into existing protocols including TCP/IP
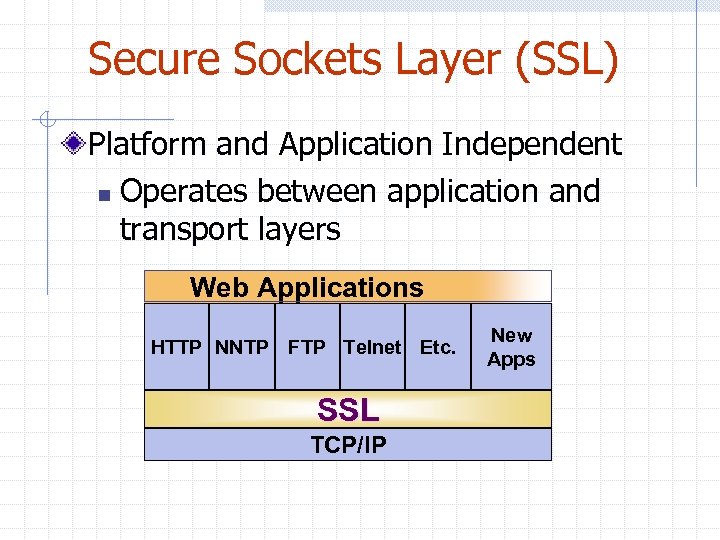 Secure Sockets Layer (SSL) Platform and Application Independent n Operates between application and transport layers Web Applications HTTP NNTP FTP Telnet Etc. SSL TCP/IP New Apps
Secure Sockets Layer (SSL) Platform and Application Independent n Operates between application and transport layers Web Applications HTTP NNTP FTP Telnet Etc. SSL TCP/IP New Apps
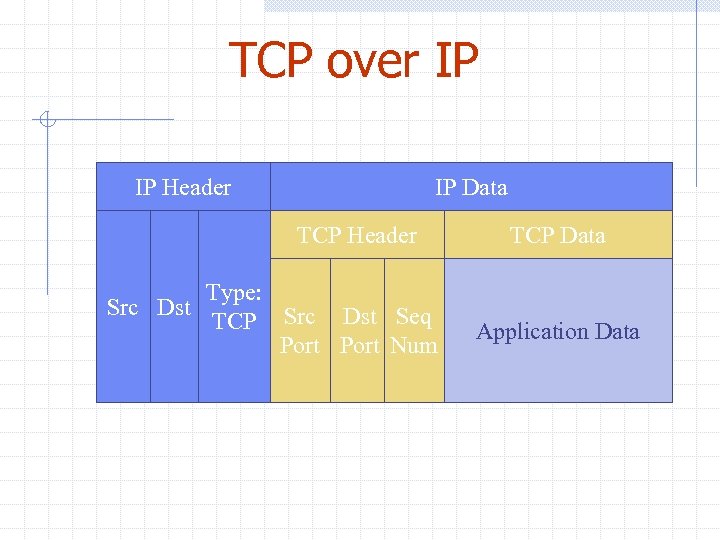 TCP over IP IP Header IP Data TCP Header Src Dst Type: TCP Src Dst Seq Port Num TCP Data Application Data
TCP over IP IP Header IP Data TCP Header Src Dst Type: TCP Src Dst Seq Port Num TCP Data Application Data
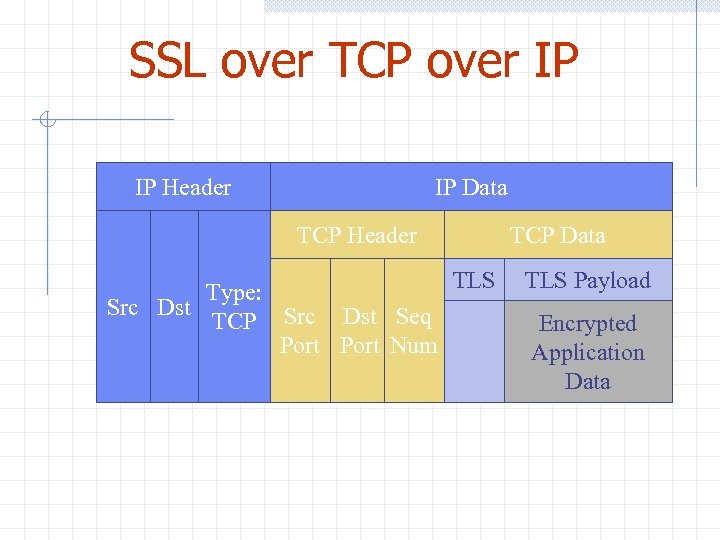 SSL over TCP over IP IP Header IP Data TCP Header Src Dst Type: TCP Src Dst Seq Port Num TCP Data TLS Payload Encrypted Application Data
SSL over TCP over IP IP Header IP Data TCP Header Src Dst Type: TCP Src Dst Seq Port Num TCP Data TLS Payload Encrypted Application Data
 SSL 3. 0 Layers Record Layer n n Fragmentation Compression Message Authentication (MAC) Encryption Alert Layer n n close errors message sequence errors bad MACs certificate errors Handshake Layer* n n n All messages are MAC’d Message order is absolute Negotiation messages are created here and handed to record layer
SSL 3. 0 Layers Record Layer n n Fragmentation Compression Message Authentication (MAC) Encryption Alert Layer n n close errors message sequence errors bad MACs certificate errors Handshake Layer* n n n All messages are MAC’d Message order is absolute Negotiation messages are created here and handed to record layer
 SSL Handshake SSL protocol uses a combination of public-key and symmetric key encryption n n Symmetric key encryption is much faster than public -key encryption Public-key encryption provides better authentication techniques Each SSL session always begin with an exchange of messages called SSL handshake n n Allows the server to authenticate itself to the client using public-key techniques Allows the client and the server to cooperate in the creation of symmetric keys used for rapid encryption, decryption, and tamper detection during the session that follows
SSL Handshake SSL protocol uses a combination of public-key and symmetric key encryption n n Symmetric key encryption is much faster than public -key encryption Public-key encryption provides better authentication techniques Each SSL session always begin with an exchange of messages called SSL handshake n n Allows the server to authenticate itself to the client using public-key techniques Allows the client and the server to cooperate in the creation of symmetric keys used for rapid encryption, decryption, and tamper detection during the session that follows
 Handshake Protocol 1. The client sends the server 2. The server sends the client 3. The client and the server selects a common cipher the client’s SSL version number, cipher settings, randomly generated data, etc. The server’s own certificate Request for the client’s certificate if the client is requesting a server resource that requires client authentication Allows use of multiple ciphers because: n – – Strong ciphers may require too much computational overhead – n Some countries disallow the use of strong ciphers Some communications must be secured with a strong cipher SSL uses strongest commonly-allowed cipher suite
Handshake Protocol 1. The client sends the server 2. The server sends the client 3. The client and the server selects a common cipher the client’s SSL version number, cipher settings, randomly generated data, etc. The server’s own certificate Request for the client’s certificate if the client is requesting a server resource that requires client authentication Allows use of multiple ciphers because: n – – Strong ciphers may require too much computational overhead – n Some countries disallow the use of strong ciphers Some communications must be secured with a strong cipher SSL uses strongest commonly-allowed cipher suite
 Handshake Protocol Summary 4. 5. 6. The client uses some of the information sent by the server to authenticate the server If the authentication fails, terminate the connection The client creates the premaster secret for the session, using the data generated during the handshake so far The secret is sent to the server after encrypted with the server’s public key (obtained from the server’s certificate) Only the corresponding private key can correctly decrypts the secret, so the client has some assurance that it is talking to the authentic server If the server requests client authentication (optional), the client also signs another piece of data and sends it with the client’s certificate The data must be unique to this handshake and known by both the client and the server (why? ) Terminate the connection if authentication fails
Handshake Protocol Summary 4. 5. 6. The client uses some of the information sent by the server to authenticate the server If the authentication fails, terminate the connection The client creates the premaster secret for the session, using the data generated during the handshake so far The secret is sent to the server after encrypted with the server’s public key (obtained from the server’s certificate) Only the corresponding private key can correctly decrypts the secret, so the client has some assurance that it is talking to the authentic server If the server requests client authentication (optional), the client also signs another piece of data and sends it with the client’s certificate The data must be unique to this handshake and known by both the client and the server (why? ) Terminate the connection if authentication fails
 SSL Handshake Protocol 7. Both the server and client follow the same steps to generate the master secret from the same premaster secret If the server does not have the right private key, it cannot generate the right master secret 8. Both the client and the server use the master secret to generate the session keys, which are symmetric keys used to encrypt and decrypt information exchanged during the SSL session verify data integrity, i. e. , detect any changes in the data between the time it was sent and the time it was received 9. Finishing handshake The client and the server send each other a message informing that future messages from will be encrypted with the session key
SSL Handshake Protocol 7. Both the server and client follow the same steps to generate the master secret from the same premaster secret If the server does not have the right private key, it cannot generate the right master secret 8. Both the client and the server use the master secret to generate the session keys, which are symmetric keys used to encrypt and decrypt information exchanged during the SSL session verify data integrity, i. e. , detect any changes in the data between the time it was sent and the time it was received 9. Finishing handshake The client and the server send each other a message informing that future messages from will be encrypted with the session key
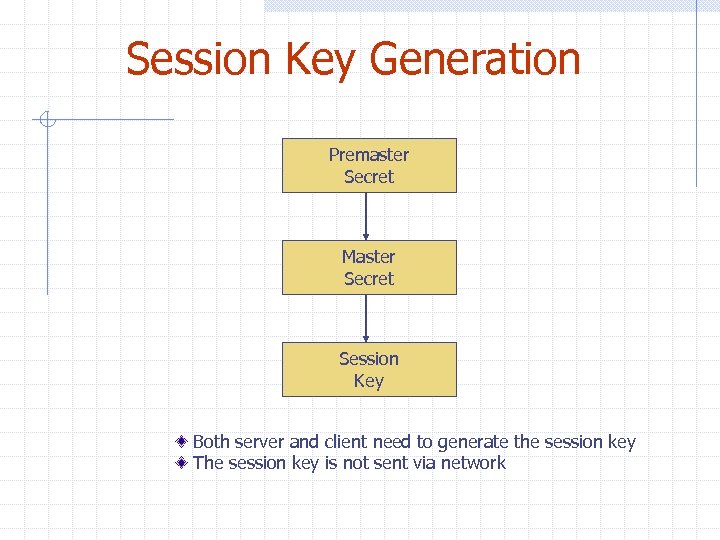 Session Key Generation Premaster Secret Master Secret Session Key Both server and client need to generate the session key The session key is not sent via network
Session Key Generation Premaster Secret Master Secret Session Key Both server and client need to generate the session key The session key is not sent via network
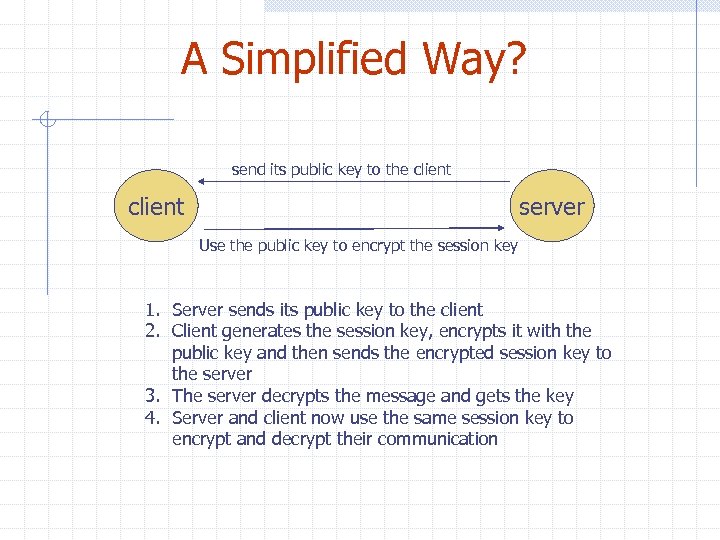 A Simplified Way? send its public key to the client server Use the public key to encrypt the session key 1. Server sends its public key to the client 2. Client generates the session key, encrypts it with the public key and then sends the encrypted session key to the server 3. The server decrypts the message and gets the key 4. Server and client now use the same session key to encrypt and decrypt their communication
A Simplified Way? send its public key to the client server Use the public key to encrypt the session key 1. Server sends its public key to the client 2. Client generates the session key, encrypts it with the public key and then sends the encrypted session key to the server 3. The server decrypts the message and gets the key 4. Server and client now use the same session key to encrypt and decrypt their communication
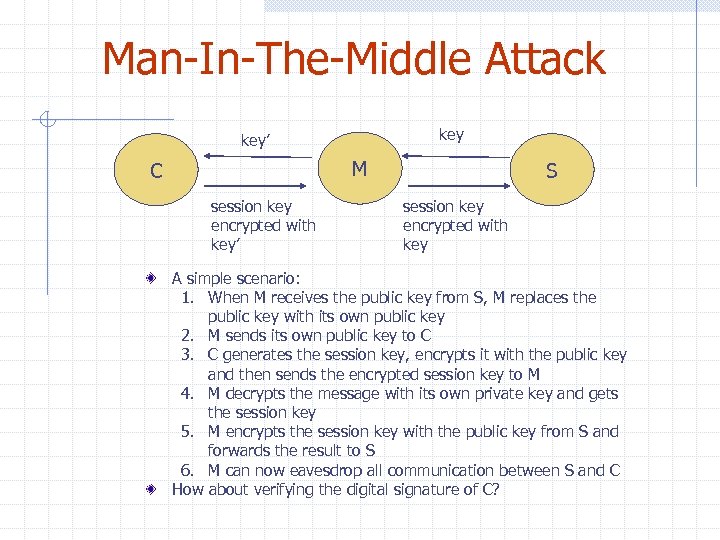 Man-In-The-Middle Attack key’ M C session key encrypted with key’ S session key encrypted with key A simple scenario: 1. When M receives the public key from S, M replaces the public key with its own public key 2. M sends its own public key to C 3. C generates the session key, encrypts it with the public key and then sends the encrypted session key to M 4. M decrypts the message with its own private key and gets the session key 5. M encrypts the session key with the public key from S and forwards the result to S 6. M can now eavesdrop all communication between S and C How about verifying the digital signature of C?
Man-In-The-Middle Attack key’ M C session key encrypted with key’ S session key encrypted with key A simple scenario: 1. When M receives the public key from S, M replaces the public key with its own public key 2. M sends its own public key to C 3. C generates the session key, encrypts it with the public key and then sends the encrypted session key to M 4. M decrypts the message with its own private key and gets the session key 5. M encrypts the session key with the public key from S and forwards the result to S 6. M can now eavesdrop all communication between S and C How about verifying the digital signature of C?
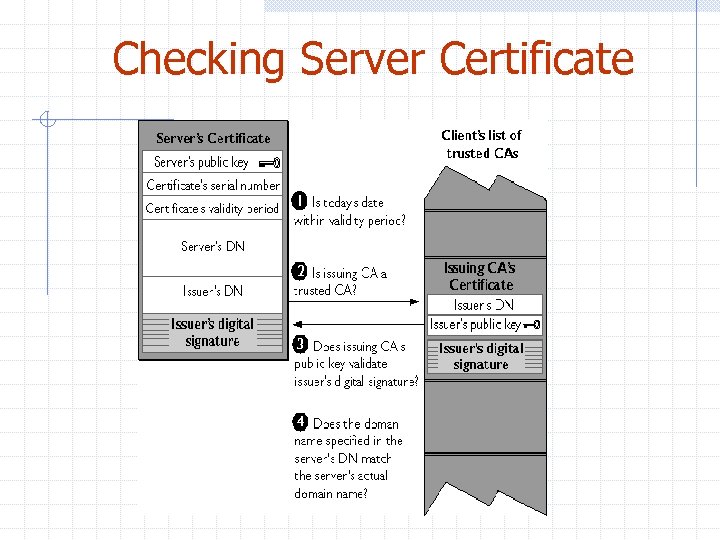 Checking Server Certificate
Checking Server Certificate
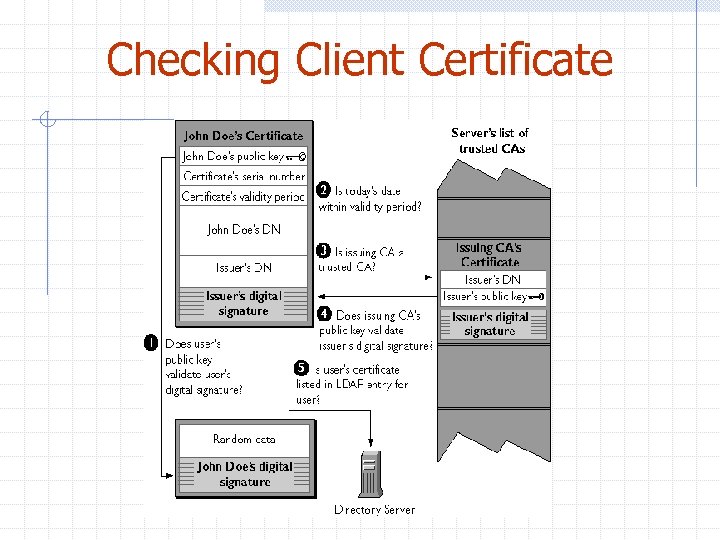 Checking Client Certificate
Checking Client Certificate
 Java SSL Java 1. 4 includes Java Secure Socket Extention (JSSE) n JSSE can be downloaded and installed into previous versions of Java Obtain SSLSocket or SSLServer. Socket objects via javax. net. ssl's SSLServer. Socket. Factory and SSLSocket. Factory classes
Java SSL Java 1. 4 includes Java Secure Socket Extention (JSSE) n JSSE can be downloaded and installed into previous versions of Java Obtain SSLSocket or SSLServer. Socket objects via javax. net. ssl's SSLServer. Socket. Factory and SSLSocket. Factory classes
 JSSE API: Client Socket Factory Methods javax. net. ssl. SSLSocket. Factory methods: n n n n static Socket. Factory get. Default() Socket create. Socket(String host, int port, Inet. Address local. Host, int local. Port) Socket create. Socket(Inet. Address host, int port, Inet. Address local. Host, int local. Port) Socket create. Socket(Socket socket, String host, int port, boolean auto. Close) String[] get. Default. Cipher. Suite() String[] get. Supported. Cipher. Suites()
JSSE API: Client Socket Factory Methods javax. net. ssl. SSLSocket. Factory methods: n n n n static Socket. Factory get. Default() Socket create. Socket(String host, int port, Inet. Address local. Host, int local. Port) Socket create. Socket(Inet. Address host, int port, Inet. Address local. Host, int local. Port) Socket create. Socket(Socket socket, String host, int port, boolean auto. Close) String[] get. Default. Cipher. Suite() String[] get. Supported. Cipher. Suites()
 JSSE API: Client Socket Methods javax. net. ssl. SSLSocket methods (extends Socket): n n n Supported SSL cipher suites: w String[] get. Enabled. Cipher. Suites() w String[] get. Supported. Cipher. Suites() w void set. Enabled. Cipher. Suites(String[] suites) SSL session creation enabled? w boolean get. Enable. Session. Creation() w void set. Enable. Session. Creation(boolean flag) SSL client authentication required? w boolean get. Need. Client. Auth() w void set. Need. Client. Auth(boolean need)
JSSE API: Client Socket Methods javax. net. ssl. SSLSocket methods (extends Socket): n n n Supported SSL cipher suites: w String[] get. Enabled. Cipher. Suites() w String[] get. Supported. Cipher. Suites() w void set. Enabled. Cipher. Suites(String[] suites) SSL session creation enabled? w boolean get. Enable. Session. Creation() w void set. Enable. Session. Creation(boolean flag) SSL client authentication required? w boolean get. Need. Client. Auth() w void set. Need. Client. Auth(boolean need)
 JSSE API: Client Socket Methods (2) n n n Change from SSL client to SSL server mode: w boolean get. Use. Client. Mode() w void set. Use. Client. Mode(boolean mode) Initiate the SSL handshake protocol: w void start. Handshake() Add/remove SSL handshake listener (notified when SSL handshake operations complete on the socket) w void add. Handshake. Completed. Listener (Handshare. Completed. Listener listener) w void remove. Handshake. Completed. Listener (Handshare. Completed. Listener listener)
JSSE API: Client Socket Methods (2) n n n Change from SSL client to SSL server mode: w boolean get. Use. Client. Mode() w void set. Use. Client. Mode(boolean mode) Initiate the SSL handshake protocol: w void start. Handshake() Add/remove SSL handshake listener (notified when SSL handshake operations complete on the socket) w void add. Handshake. Completed. Listener (Handshare. Completed. Listener listener) w void remove. Handshake. Completed. Listener (Handshare. Completed. Listener listener)
 JSSE API: Server Socket Factory Methods javax. net. ssl. SSLServer. Socket. Factory methods: n n n static Server. Socket. Factory get. Default() Server. Socket create. Server. Socket(int port, int LQsize) Server. Socket create. Server. Socket(int port, int LQsize, Inet. Address local. Address) String[] get. Default. Cipher. Suites() String[] get. Supported. Cipher. Suites()
JSSE API: Server Socket Factory Methods javax. net. ssl. SSLServer. Socket. Factory methods: n n n static Server. Socket. Factory get. Default() Server. Socket create. Server. Socket(int port, int LQsize) Server. Socket create. Server. Socket(int port, int LQsize, Inet. Address local. Address) String[] get. Default. Cipher. Suites() String[] get. Supported. Cipher. Suites()
 JSSE API: Server Socket Methods javax. net. ssl. SSLServer. Socket methods: n n Supported SSL cipher suites: w String[] get. Enabled. Cipher. Suites() w String[] get. Supported. Cipher. Suites() w void set. Enabled. Cipher. Suites(String[] suites) SSL session creation enabled? w boolean get. Enable. Session. Creation() w void set. Enable. Session. Creation(boolean flag) SSL client authentication required on accepted sockets? w boolean get. Need. Client. Auth() w void set. Need. Client. Auth(boolean need) Switch accepted sockets from SSL client mode to SSL server mode w boolean get. Use. Client. Mode() w void set. Use. Client. Mode(boolean mode)
JSSE API: Server Socket Methods javax. net. ssl. SSLServer. Socket methods: n n Supported SSL cipher suites: w String[] get. Enabled. Cipher. Suites() w String[] get. Supported. Cipher. Suites() w void set. Enabled. Cipher. Suites(String[] suites) SSL session creation enabled? w boolean get. Enable. Session. Creation() w void set. Enable. Session. Creation(boolean flag) SSL client authentication required on accepted sockets? w boolean get. Need. Client. Auth() w void set. Need. Client. Auth(boolean need) Switch accepted sockets from SSL client mode to SSL server mode w boolean get. Use. Client. Mode() w void set. Use. Client. Mode(boolean mode)
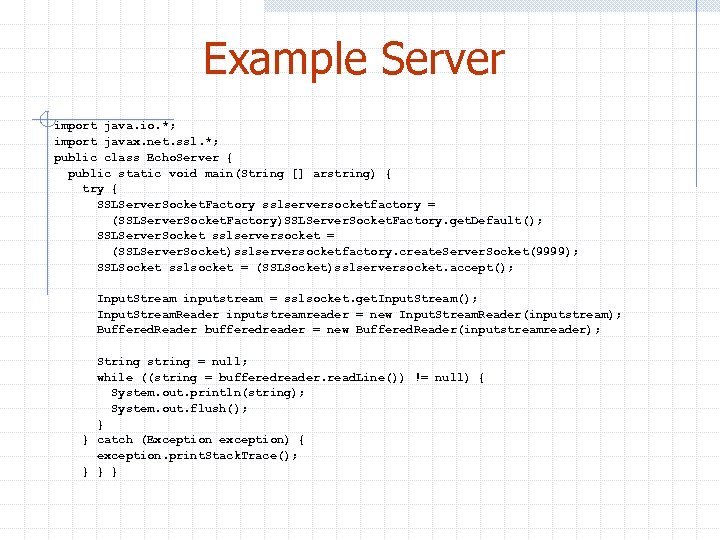 Example Server import java. io. *; import javax. net. ssl. *; public class Echo. Server { public static void main(String [] arstring) { try { SSLServer. Socket. Factory sslserversocketfactory = (SSLServer. Socket. Factory)SSLServer. Socket. Factory. get. Default(); SSLServer. Socket sslserversocket = (SSLServer. Socket)sslserversocketfactory. create. Server. Socket(9999); SSLSocket sslsocket = (SSLSocket)sslserversocket. accept(); Input. Stream inputstream = sslsocket. get. Input. Stream(); Input. Stream. Reader inputstreamreader = new Input. Stream. Reader(inputstream); Buffered. Reader bufferedreader = new Buffered. Reader(inputstreamreader); String string = null; while ((string = bufferedreader. read. Line()) != null) { System. out. println(string); System. out. flush(); } } catch (Exception exception) { exception. print. Stack. Trace(); } } }
Example Server import java. io. *; import javax. net. ssl. *; public class Echo. Server { public static void main(String [] arstring) { try { SSLServer. Socket. Factory sslserversocketfactory = (SSLServer. Socket. Factory)SSLServer. Socket. Factory. get. Default(); SSLServer. Socket sslserversocket = (SSLServer. Socket)sslserversocketfactory. create. Server. Socket(9999); SSLSocket sslsocket = (SSLSocket)sslserversocket. accept(); Input. Stream inputstream = sslsocket. get. Input. Stream(); Input. Stream. Reader inputstreamreader = new Input. Stream. Reader(inputstream); Buffered. Reader bufferedreader = new Buffered. Reader(inputstreamreader); String string = null; while ((string = bufferedreader. read. Line()) != null) { System. out. println(string); System. out. flush(); } } catch (Exception exception) { exception. print. Stack. Trace(); } } }
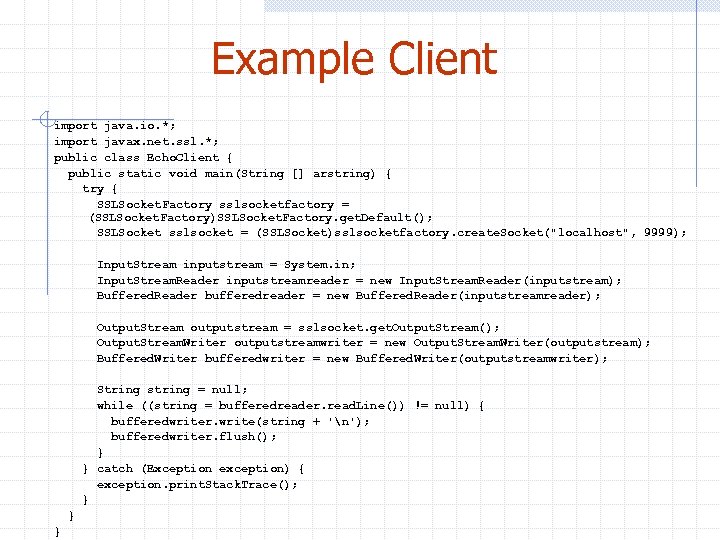 Example Client import java. io. *; import javax. net. ssl. *; public class Echo. Client { public static void main(String [] arstring) { try { SSLSocket. Factory sslsocketfactory = (SSLSocket. Factory)SSLSocket. Factory. get. Default(); SSLSocket sslsocket = (SSLSocket)sslsocketfactory. create. Socket("localhost", 9999); Input. Stream inputstream = System. in; Input. Stream. Reader inputstreamreader = new Input. Stream. Reader(inputstream); Buffered. Reader bufferedreader = new Buffered. Reader(inputstreamreader); Output. Stream outputstream = sslsocket. get. Output. Stream(); Output. Stream. Writer outputstreamwriter = new Output. Stream. Writer(outputstream); Buffered. Writer bufferedwriter = new Buffered. Writer(outputstreamwriter); String string = null; while ((string = bufferedreader. read. Line()) != null) { bufferedwriter. write(string + 'n'); bufferedwriter. flush(); } } catch (Exception exception) { exception. print. Stack. Trace(); } } }
Example Client import java. io. *; import javax. net. ssl. *; public class Echo. Client { public static void main(String [] arstring) { try { SSLSocket. Factory sslsocketfactory = (SSLSocket. Factory)SSLSocket. Factory. get. Default(); SSLSocket sslsocket = (SSLSocket)sslsocketfactory. create. Socket("localhost", 9999); Input. Stream inputstream = System. in; Input. Stream. Reader inputstreamreader = new Input. Stream. Reader(inputstream); Buffered. Reader bufferedreader = new Buffered. Reader(inputstreamreader); Output. Stream outputstream = sslsocket. get. Output. Stream(); Output. Stream. Writer outputstreamwriter = new Output. Stream. Writer(outputstream); Buffered. Writer bufferedwriter = new Buffered. Writer(outputstreamwriter); String string = null; while ((string = bufferedreader. read. Line()) != null) { bufferedwriter. write(string + 'n'); bufferedwriter. flush(); } } catch (Exception exception) { exception. print. Stack. Trace(); } } }
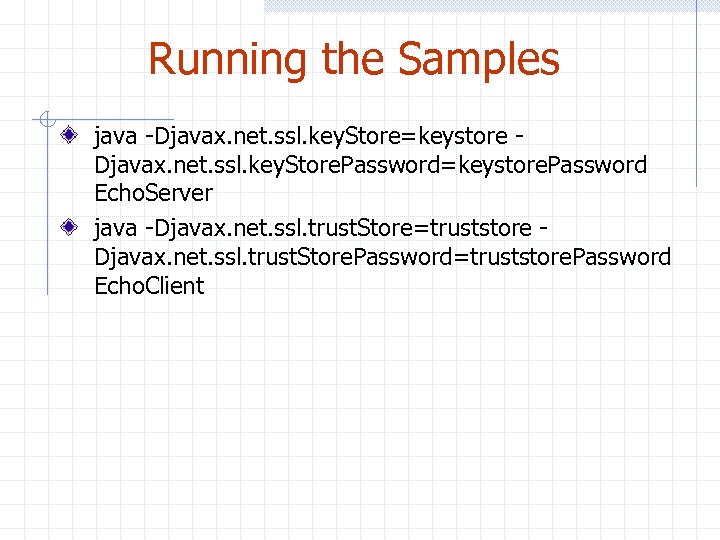 Running the Samples java -Djavax. net. ssl. key. Store=keystore Djavax. net. ssl. key. Store. Password=keystore. Password Echo. Server java -Djavax. net. ssl. trust. Store=truststore Djavax. net. ssl. trust. Store. Password=truststore. Password Echo. Client
Running the Samples java -Djavax. net. ssl. key. Store=keystore Djavax. net. ssl. key. Store. Password=keystore. Password Echo. Server java -Djavax. net. ssl. trust. Store=truststore Djavax. net. ssl. trust. Store. Password=truststore. Password Echo. Client
 Java Certificate Classes java. security. cert n n n Certificate (abstract class) CRL (abstract class) Certificate. Factory w To obtain instances of Certificates and CRLs n n X 509 Certificate extends Certificate X 509 CRL extends CRL
Java Certificate Classes java. security. cert n n n Certificate (abstract class) CRL (abstract class) Certificate. Factory w To obtain instances of Certificates and CRLs n n X 509 Certificate extends Certificate X 509 CRL extends CRL
 Certificate. Factory Class public static Certificate. Factory get. Instance(String string. Type) n Type is, e. g. , “X. 509” public static Certificate. Factory get. Instance(String string. Type, String string. Provider) public final Certificate generate. Certificate(Input. Stream inputstream) public final Collection generate. Certificates(Input. Stream inputstream) public final CRL generate. CRL(Input. Stream inputstream) public final Collection generate. CRLs(Input. Stream inputstream)
Certificate. Factory Class public static Certificate. Factory get. Instance(String string. Type) n Type is, e. g. , “X. 509” public static Certificate. Factory get. Instance(String string. Type, String string. Provider) public final Certificate generate. Certificate(Input. Stream inputstream) public final Collection generate. Certificates(Input. Stream inputstream) public final CRL generate. CRL(Input. Stream inputstream) public final Collection generate. CRLs(Input. Stream inputstream)
![Certificate Interface public String abstract Public. Key get. Public. Key() abstract byte [] get. Certificate Interface public String abstract Public. Key get. Public. Key() abstract byte [] get.](https://present5.com/presentation/fe6135d12872d180d7b9e9418adc7b71/image-48.jpg) Certificate Interface public String abstract Public. Key get. Public. Key() abstract byte [] get. Encoded() abstract void verify(Public. Key publickey, string. Provider)
Certificate Interface public String abstract Public. Key get. Public. Key() abstract byte [] get. Encoded() abstract void verify(Public. Key publickey, string. Provider)
![X. 509 Certificate Interface public abstract byte [] get. Encoded() n Returns certificate encoded X. 509 Certificate Interface public abstract byte [] get. Encoded() n Returns certificate encoded](https://present5.com/presentation/fe6135d12872d180d7b9e9418adc7b71/image-49.jpg) X. 509 Certificate Interface public abstract byte [] get. Encoded() n Returns certificate encoded in DER format public abstract int get. Version() public abstract Principal get. Subject. DN() public abstract Principal get. Issuer. DN() public abstract Date get. Not. Before() public abstract Date get. Not. After() public abstract Big. Integer get. Serial. Number() public abstract String get. Sig. Alg. Name() public abstract String get. Sig. Alg. OID() public abstract int get. Basic. Constraints() public abstract boolean [] get. Key. Usage() public Set get. Critical. Extension. OIDs() public Set get. Non. Critical. Extension. OIDs()
X. 509 Certificate Interface public abstract byte [] get. Encoded() n Returns certificate encoded in DER format public abstract int get. Version() public abstract Principal get. Subject. DN() public abstract Principal get. Issuer. DN() public abstract Date get. Not. Before() public abstract Date get. Not. After() public abstract Big. Integer get. Serial. Number() public abstract String get. Sig. Alg. Name() public abstract String get. Sig. Alg. OID() public abstract int get. Basic. Constraints() public abstract boolean [] get. Key. Usage() public Set get. Critical. Extension. OIDs() public Set get. Non. Critical. Extension. OIDs()
 Summary Introduction to cryptography n n n Symmetric key and public key encryption/decryption Digital signature Certificate Secure Sockets Layer n SSL handshake Java Secure Sockets Extensions n n Socket factories SSLSockets and SSLServer. Sockets Sample client and server
Summary Introduction to cryptography n n n Symmetric key and public key encryption/decryption Digital signature Certificate Secure Sockets Layer n SSL handshake Java Secure Sockets Extensions n n Socket factories SSLSockets and SSLServer. Sockets Sample client and server


