1946e279ec798b6e15c29373d98caa6c.ppt
- Количество слайдов: 35

Workshop on “Cyber Crime” Wednesday, 18 th June 2010 - Hotel Bristol, M. G. Road, Gurgaon Session II- Overview of Cyber crimes , data thefts and identity thefts By Karnika Seth Managing Partner, SETH ASSOCIATES

Presentation plan p p p This session will examine the effect of e-crimes on businesses and on individuals. It will discuss the nature of cybercrimes, the loopholes , and other pertinent issues Categories of cybercrimes Vulnerabilities in security systems Challenges in identification of accused & prosecution Statistical index of rise of cybercrimes with case studies Recognizing loopholes & planning a techno legal e -security plan
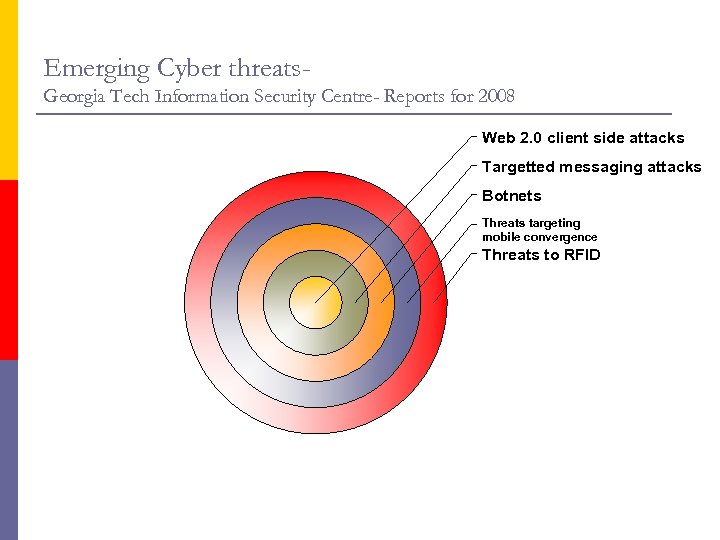
Emerging Cyber threats. Georgia Tech Information Security Centre- Reports for 2008 Web 2. 0 client side attacks Targetted messaging attacks Botnets Threats targeting mobile convergence Threats to RFID
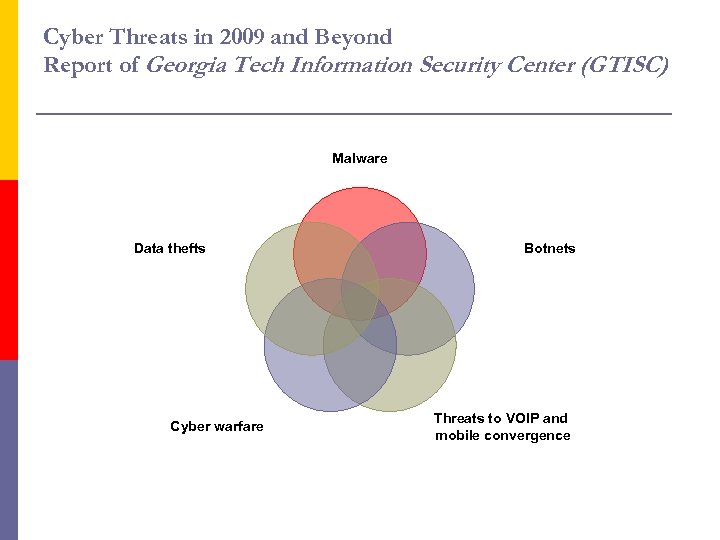
Cyber Threats in 2009 and Beyond Report of Georgia Tech Information Security Center (GTISC) Malware Data thefts Cyber warfare Botnets Threats to VOIP and mobile convergence
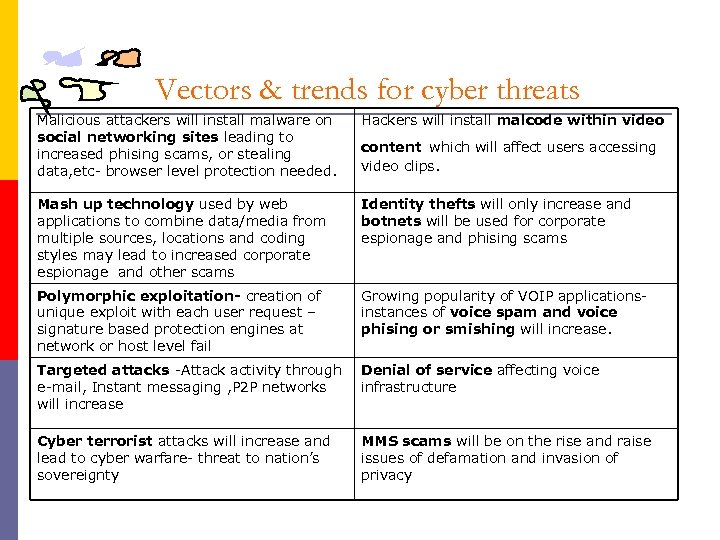
Vectors & trends for cyber threats Malicious attackers will install malware on social networking sites leading to increased phising scams, or stealing data, etc- browser level protection needed. Hackers will install malcode within video Mash up technology used by web applications to combine data/media from multiple sources, locations and coding styles may lead to increased corporate espionage and other scams Identity thefts will only increase and botnets will be used for corporate espionage and phising scams Polymorphic exploitation- creation of unique exploit with each user request – signature based protection engines at network or host level fail Growing popularity of VOIP applicationsinstances of voice spam and voice phising or smishing will increase. Targeted attacks -Attack activity through e-mail, Instant messaging , P 2 P networks will increase Denial of service affecting voice infrastructure Cyber terrorist attacks will increase and lead to cyber warfare- threat to nation’s sovereignty MMS scams will be on the rise and raise issues of defamation and invasion of privacy content which will affect users accessing video clips.
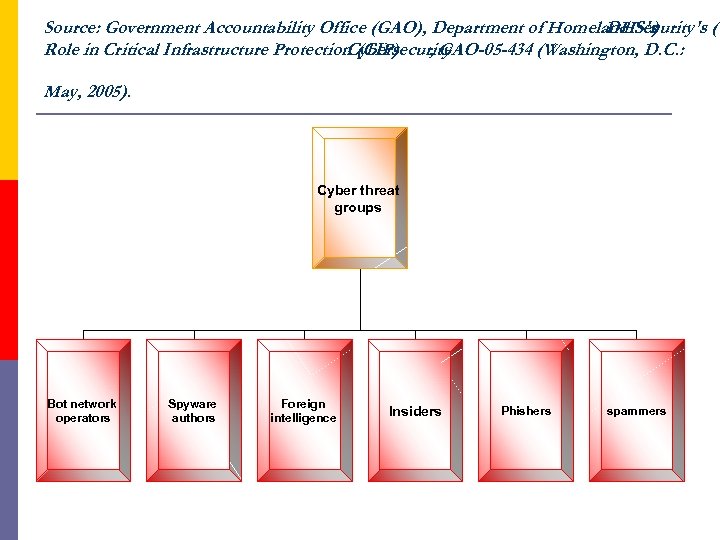
Source: Government Accountability Office (GAO), Department of Homeland Security's ( DHS's ) Role in Critical Infrastructure Protection (CIP) Cybersecurity , GAO-05 -434 (Washington, D. C. : May, 2005). Cyber threat groups Bot network operators Spyware authors Foreign intelligence Insiders Phishers spammers

Categories of hackers

Prevention is proven to be better than cure…. p “Attackers will continue to post malicious links as part of the user’s everyday online activity-at the end of an IM string, hidden in a You Tube Video or embedded in an Excel spreadsheet ” - Paul Judge, Senior Vice President and chief Technology Officer, Secure Computing p “When massive numbers of users are infected, it poses a serious risk to the infrastructure. When the Storm Worm virus broke out last January, it infected 40 to 50 million of some 300 million users connected by broadband. To combat this, network and point –based security solutions need to be invented for the mobile environment . ” -Chris Rouland- Chief Technology Officer, IBM Internet security Systems and IBM Distinguished Engineer

The Storm botnet p p The typical lifecycle of spam that originates from a botnet: (1) Spammer's web site (2) Spammer (3) Spamware (4) Infected computers (5) Virus or trojan (6) Mail servers (7) Users (8) Web traffic The Storm botnet or Storm worm botnet is a remotelycontrolled network of "zombie" computers (or "botnet") that has been linked by the Storm Worm, a Trojan horse spread through email spam. Some have estimated that by September 2007 the Storm botnet was running on anywhere from 1 million to 50 million computer systems. United States Federal Bureau of Investigation considers the botnet a major risk to increased bank fraud, identity theft, and other cybercrimes
The Conficker Worm p p Conficker, also known as Downup, Downadup and Kido, is a computer worm targeting the Microsoft Windows operating system that was first detected in October 2008. Conficker is believed to be the most widespread computer worm infection since SQL Slammer in 2003. The initial rapid spread of the worm has been attributed to the number of Windows PCs (estimated at 30%) which have yet to apply the Microsoft patch for the MS 08 -067 vulnerability. By January 2009, the estimated number of infected computers ranged from almost 9 million to 15 million. Antivirus software vendor Panda Security reported that of the 2 million computers analyzed through Active. Scan, around 115, 000 (6%) were infected with Conficker.
Levels of cyber threats and vulnerabilities Individual sector society State level Global
Cyber Crime mechanisms Network based attacks Hardware based attacks Software based attacks Operation based attacks User authentication

Striking facts! p According to a report compiled by Panda Labs, in 2008, 10 million bot computers were used to distribute spam and malware across the Internet each day. p Annual take by theft-oriented cyber criminals is estimated to be as high as 100 billion dollars and 97 per cent of these offences go undetected, -CBI's Conference on International Police Cooperation against Cyber Crime, March 2009 .

Cyber crime & warfare EMERGING CHALLENGE: SECURITY AND SAFETY IN CYBERSPACE by Richard O. Hundley and Robert H. Anderson in IEEE Technology and Society, pp. 19– 28 (Winter 1995/1996). “In this cyberspace world, the distinction between “crime” and “warfare” in cyberspace also blurs the distinction between police responsibilities, to protect societal interests from criminal acts in cyberspace, and military responsibilities, to protect societal interests from acts of war in cyberspace. ”

Cyber warfare-key attributes Jon Ramsey, chief technology officer for Secure Works attributes increasing cyber warfare activity to the following: p p The low cost to launch cyber attacks The lack of cyber defenses The plausible deniability that the Internet affords The lack of cyber rules of engagement in conflicts between nation states.

Examples of Cyber-terrorism p Attacks that lead to death or bodily injury, explosions, plane crashes, water contamination, or severe economic loss or Serious attacks against critical infrastructures would be examples. p Solar Sunrise- In early 1998 U. S. military systems were subjected to an "electronic assault, " noted as "Solar Sunrise. " The intruders hid their tracks by routing their attack through computer systems in the United Arab Emirates. It was found that two young hackers in California had carried out the attacks under the direction of a hacker in Israel, himself a teenager. They gained privileged access to computers using tools available from a university web site and installed sniffer programs to collect user passwords. They created a backdoor to get back into the system and then used a patch available from another university web site to fix the vulnerability and prevent others from repeating their exploit. p

Examples of Cyber terrorism p Middle East terrorist groups--such as Hizballah, HAMAS, and Usama Bin Ladin's organization--are using computerized files, email, and encryption to support their organizations. p Kurdish separatists in Greece and Turkey, Kashmiri separatists in India, and Zapatista rebels in Mexico have also hacked official government Web pages and posted anti-government propaganda and pictures. Terrorists and extremists already use the Internet to cause destruction, communicate, to raise funds, recruit, and gather intelligence. They may even launch attacks remotely from countries where their actions are not illegal or with whom we have no extradition agreements p

Examples of Cyber terrorism p A group calling themselves the Internet Black Tigers took responsibility for attacks in August 1998 on the email systems of Sri Lankan diplomatic posts around the world, including those in the United States. p Third-country sympathizers of the Mexican Zapatista rebels crashed web pages belonging to Mexican financial institutions. While such attacks did not result in damage to the targets, they were portrayed as successful by the activists and used to generate propaganda and rally supporters. p Distributed Denial of Service (DDo. S) attack on Estonia in May 2007 led to crippling of banking institutions and blocked the connectivity of the offices of President, Prime Minister, Parliament and other governmental agencies bringing the whole system down, crippling government and private institutions p Very recently, China-based cyber spy network has hacked into government and private systems in 103 countries, including those of many Indian embassies and the Dalai lama.

IT Act 2000 and Cyber terrorism p p p p Section 66 of IT Act -Hacking ( punishment upto 3 yrs/fine of 2 lakhs) Section 70 of IT Act - any act to harm protected systems punishable under IT Act 2000 ( punishment upto 10 yrs) Section 121 of IPC -waging war against Government ( punishable with life imprisonment) Section 153 A, 295 A of IPC -promoting enmity between different religious groups is punishable offence( 3 yrs imprisonment/fine/both) Section 66 F of the Indian Information Technology Amendment Bill 2008 specifically deals with issue of cyber terrorism. Covers denial of access, unauthorised access, computer contaminant leading to harm to persons, property, critical infrastructure, disruption of supplies, ‘sensitive data’ thefts Punishable with imprisonment which may extend to imprisonment for life.

Recent amendments in IT Act, 2000 p p To protect interests of sovereignty , integrity of India, public order, security of State , defence of India, friendly relations with foreign states Section 69 -Power of interception, decryption, monitoring of information by Central govt/state govt authorised agencies p Section 69 A -Power to block objectionable websites-to protect interests of sovereignty , integrity of India, public order, security of State , defence of India, friendly relations with foreign states p Section 69 B -Power to authorize to monitor and collect traffic data, or information through any computer resource for cyber security p Section 70 -Protected systems, and Section 70 A Central Govt shall appoint Indian Computer Emergency Response Team to protect its critical infrastructure
Data theft According to the section 2 of Information Technology Act, “Data” means a representation of information, knowledge, facts, concepts or instruction which are being prepared or have been prepared in a formalised manner, and is intended to be processed, is being processed or has been processed in a computer system or computer network, and may be in any form (including computer printouts magnetic or optical storage media, punched cards, punched tapes) or stored internally in the memory of the computer. “Data Theft”- It is the term used when any information in the form of data is illegally copied or taken from a business or other individual without his knowledge or consent.

Glaring Examples – Data thefts p p p The incidents in the recent past involving Cyber Space have highlighted the issues of privacy and data protection in India The Pune scam was the first among the many BPO frauds that made international headlines. In April 2005, five employees of Msourc. E in Pune were arrested for allegedly pulling off a fraud worth nearly 2. 5 crore rupees from the Citibank accounts of four New York-based account holders. In June 2005, the British tabloid Sun, in a sting operation, purchased the bank account details of 1, 000 Britons from Karan Bahree, an employee of Gurgaon-based BPO company Infinity E-Search.

Examples of Data thefts p In June 2006, Nadeem Kashmiri, an employee at HSBC's call center in Bangalore, sold the customer credit card information to a group of scamsters who used the information to siphon off nearly Rs 1. 8 crore from bank accounts of UK-based customers. p An Indian engineer and former Intel employee, Bishwasmohan Pani has been charged as stealing secret information from Intel for its new employer and Intel's rival Advanced Micro Devices (AMD) p Acme Tele Power Private Limited, a Manesar-based IT company, decided to shift its $10 million R&D facility to Australia because of a recent incident of data theft that caused it a loss of Rs 750 crore. Acme had developed a product called Power Interface Unit (PIU) and had it patented by the government of India. The patent was valued at Rs 750 crore by Ernst and Young. One of our employees, Sachidanand Patnaik, worked on the project and leaked the patented software of PIU to Lambda Eastern Telecom Limited. ”

Data theft & the Indian legal Provisions p p p Section 378 of the Indian Penal Code, 1860 defines ‘Theft’ as follows: - “Theft – Whoever, intending to take dishonestly any movable property out of the possession of any person without that person’s consent, moves that property in order to such taking, is said to commit theft. ” Section 22 of I. P. C. , 1860 defines “movable property” as follows: - p “The words “movable property” are intended to include corporeal property of every description, except land things attached to the earth or permanently fastened to anything which is attached to the earth. ” p Since Section 378 I. P. C. , only refers to “Movable Property” i. e. Corporeal Property, and Data by itself is intangible, it is not covered under the definition of "Theft. However, if data is stored in a medium (CD, Pen-drive etc. ) and such medium is stolen, it would be covered under the definition of ‘Theft’, since the medium is a movable property.

Data theft & the Indian legal Provisions p Section 405 of I. P. C. , defines ‘Criminal Breach of Trust ‘ as follows: - p “Criminal Breach of Trust’. - Whoever, being in any manner entrusted with property, or with any dominion over property, dishonestly misappropriates or converts to his own use that property, or dishonestly uses or disposes of that property in violation of any direction of law prescribing the mode in which such trust is to be discharged, or of any legal contract, express or implied, which he has made touching the discharge of such trust, or willfully suffers any other person so to do, commits ‘criminal breach of trust’ ”. p Section 406 I. P. C. punishes Criminal Breach of Trust with punishment of imprisonment upto 3 years, or with fine, or with both

Data theft & the Indian legal Provisions p Section 43 IT Act: - This section provides protection against destruction and unauthorized access of the computer system by imposing heavy penalty up to one crore. The unauthorized downloading, extraction and copying of data are also covered under this section. Clause ‘C’ of this section imposes penalty for unauthorized introduction of computer viruses of contaminants. Clause ‘G’ provides penalties for assisting the unauthorized access. p The Recent IT Amendment Bill 2008 adds stealing of computer source code and destruction/alteration of data within its ambit and removes stipulated upperlimit of one crore to claim compensation. Section 43 A imposes heavy liability on body corporates for failure to protect sensitive personal data or information. Section 66 –Element of mens rea in any acts covered by Section 43 punishment of three years/fine upto 5 lakh or both Section 66 C -punisment for identity thefts-upto three year punishment /upto 1 lakh fine Section 72 A-Punishment for disclosure of information in breach of contract –punishable with imprisonment upto three years, fine upto 5 lakhs/both p p

Data theft & Copyright law p p Indian Copyright Act, 1957 protects “Databases” as ‘literary works’ under Section 13 (1) (a) of the Act which states that Copyright shall subsists throughout India in original literary, dramatic, musical and artistic works. The definition of ‘literary works’ as defined under Section 2(o) of Copyright Act, 1957 includes computer programmes, tables and compilations including computer data bases. p Civil remedies in infringement of copyright is covered by Section 55 of the Copyright Act-injunction, damages, accounts, delivery up of infringing goods. p Section 63 - criminal remedy- punishment not less than 6 months, extend to 3 years and fine upto 2 lakhs

Industry Measures to check data thefts p p p Nasscom launched a National Skills Registry for IT professionals to help employers conduct background checks. Nasscom announced plans to set up an independent, selfregulatory organization to set and monitor data security and privacy best practices by outsourcing service providers in India. Service providers in India are also increasingly adopting compliance programs and comprehensive security audits, including personnel and equipment audits to prevent misuse of sensitive information and data. Compliance programs include training of employees to enhance awareness of confidentiality and of managers with regard to securing computer systems, common threats to information security, access-control techniques, risk assessment and management, intrusion detection, authentication and other issues. Enforcement agencies in India also working with business process outsourcers to conduct workshops aimed at improving employees’ knowledge and skills in the area of the misuse of data.

Email spoofing & Identity theft: p p p Pranab Mitra , former executive of Gujarat Ambuja Cement posed as a woman, Rita Basu, and created a fake e-mail ID through which he contacted one V. R. Ninawe an Abu Dhabi businessmen . After long cyber relationship and emotional massages Mitra sent an e-mail that ‘‘she would commit suicide’’ if Ninawe ended the relationship. He also gave him ‘‘another friend Ruchira Sengupta’s’’ e-mail ID which was in fact his second bogus address. When Ninawe mailed at the other ID he was shocked to learn that Mitra had died and police is searching Ninawe. Mitra extorted few lacs Rupees as advocate fees etc. Mitra even sent e-mails as high court and police officials to extort more money. Ninawe finally came down to Mumbai to lodge a police case.

The Information Technology Act, 2000 and cybercrimes p p The Information Technology Act 2000 came into force in India on 17 October 2000. It extends to whole of India and also applies to any offence or contraventions committed outside India by any person (s 1(2), IT Act 2000). According to s 75 of the Act, the Act applies to any offence or contravention committed outside India by any person irrespective of his nationality, if such act involves a computer, computer system or network located in India.

Cognisability & bailability p p p Most offences introduced by the 2008 amendments prescribe punishment of upto 3 yrs , fine of one lac/2 lac For hacking term of imprisonment remains upto 3 yrs but fine increased from 2 lakhs to 5 lacs In S. 67 imprisonment term reduced from 5 yrs to three yrs. Fine increased from one lac to 5 lacs. Most Offences are cognisable but bailable This is a new challenge for cyberlaw enforcement authorities- need quick action by trained investigators to collect and preserve evidence as probability of tampering increases.

Main Features of IT Act, 2000 Applicable to communications made through cell phones , PDAs p Conferred legal validity and recognition to electronic documents & digital signatures p Legal recognition to e-contracts p Set up Regulatory regime to supervise Certifying Authorities p Laid down civil and criminal liabilities for contravention of provisions of IT Act, 2000 p Created the office of Adjudicating Authority to adjudge contraventions p
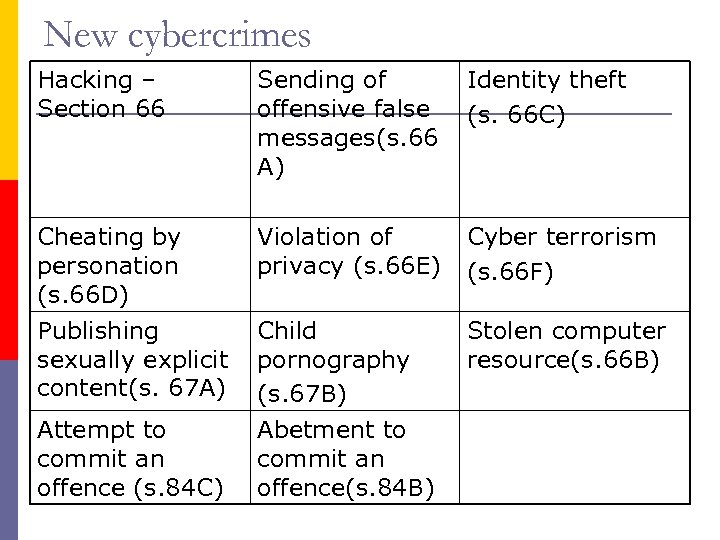
New cybercrimes Hacking – Section 66 Sending of offensive false messages(s. 66 A) Identity theft (s. 66 C) Cheating by personation (s. 66 D) Publishing sexually explicit content(s. 67 A) Violation of privacy (s. 66 E) Cyber terrorism (s. 66 F) Child pornography (s. 67 B) Stolen computer resource(s. 66 B) Attempt to commit an offence (s. 84 C) Abetment to commit an offence(s. 84 B)

Special and General statutes applicable to cybercrimes p p While the IT Act 2000, provides for the specific offences it has to be read with the Indian Penal Code 1860 (IPC) and the Code of Criminal Procedure 1973 (Cr PC) IT Act is a special law, most IT experts are of common consensus that it does not cover or deal specifically with every kind of cyber crime for instance, for defamatory emails reliance is placed on s 500 of IPC, for threatening e-mails, provisions of IPC applicable thereto are criminal intimidation (ch XXII), extortion (ch XVII), for e-mail spoofing, provisions of IPC relating to frauds, cheating by personation (ch XVII) and forgery (ch XVIII) are attracted. Likewise, criminal breach of trust and fraud (ss 405, 406, 408, 409) of the IPC are applicable and for false electronic evidence, s 193 of IPC applies. For cognisability and bailability, reliance is placed on Code of Criminal Procedure which also lays down the specific provisions relating to powers of police to investigate.
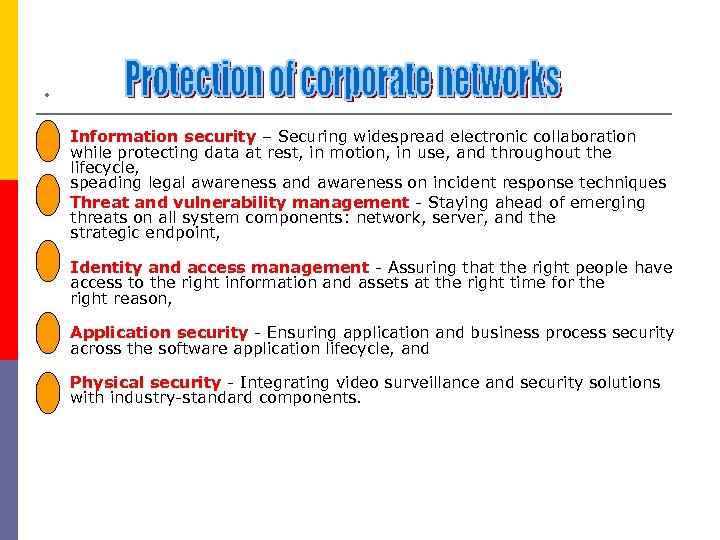
. p p Information security – Securing widespread electronic collaboration while protecting data at rest, in motion, in use, and throughout the lifecycle, speading legal awareness and awareness on incident response techniques Threat and vulnerability management - Staying ahead of emerging threats on all system components: network, server, and the strategic endpoint, p Identity and access management - Assuring that the right people have access to the right information and assets at the right time for the right reason, p Application security - Ensuring application and business process security across the software application lifecycle, and p Physical security - Integrating video surveillance and security solutions with industry-standard components.
1946e279ec798b6e15c29373d98caa6c.ppt