3d58ffc1ab3ca5b11e5e9ad0cd98a479.ppt
- Количество слайдов: 19

Work. Safe. BC’s Wireless LAN Implementation …with a focus on security UBC October 2, 2008 Allan Alton, BSc, CISA, CISSP

Agenda • Goals • Functional • Security • Architecture Overview • Challenges • Futures

Goals - Functional From: • Head Office and 17 area offices/work centres • Meeting rooms • Common areas (lobby, atrium, lounge, cafeteria) • Parking lot edge (drive-by downloading)

Goals - Functional To: • Employee access to internal network • Guest access to Internet • Broader Public Sector (BPS) employee access to Internet

Goals - Functional Using: • existing built-in client adapters • PC Card adapter for exceptions • Windows XP client software • standardized client for easier support • 802. 11 g and 802. 11 a only • no 802. 11 b due to performance penalty
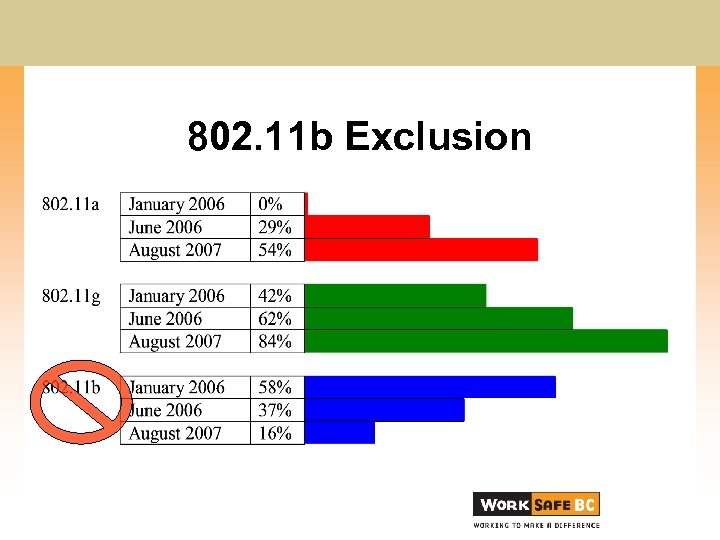
802. 11 b Exclusion
Goals - Security • Tip for success: Work with your security group from the beginning Network Services & IS Security

Goals - Security • • Wi-Fi Protected Access 2 (WPA 2) only Firewall separation from internal network SSID not broadcast (except for guest) Integration with Active Directory Wireless intrusion detection Intrusion detection at wired network entry Access Points physically hidden
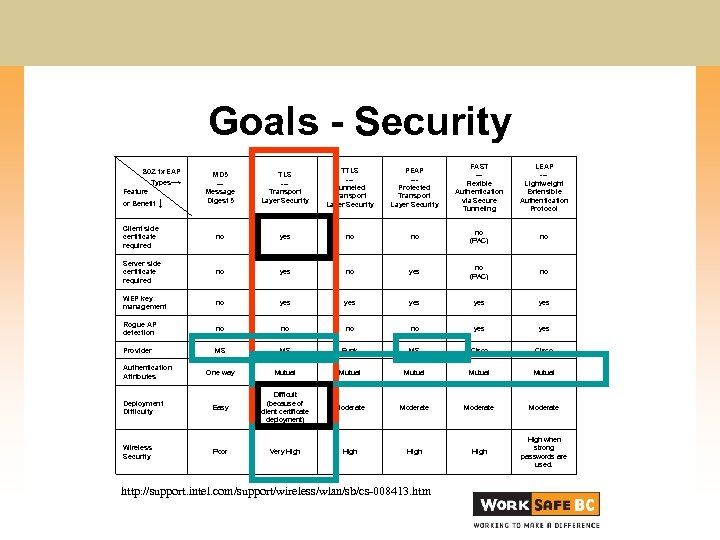
Goals - Security MD 5 --Message Digest 5 TLS --Transport Layer Security TTLS --Tunneled Transport Layer Security PEAP --Protected Transport Layer Security FAST --Flexible Authentication via Secure Tunneling LEAP --Lightweight Extensible Authentication Protocol Client side certificate required no yes no no no (PAC) no Server side certificate required no yes no (PAC) no WEP key management no yes yes yes Rogue AP detection no no yes Provider MS MS Funk MS Cisco One way Mutual Mutual Deployment Difficulty Easy Difficult (because of client certificate deployment) Moderate Wireless Security Poor Very High High when strong passwords are used. 802. 1 x EAP Types→ Feature or Benefit ↓ Authentication Attributes http: //support. intel. com/support/wireless/wlan/sb/cs-008413. htm
Architecture Overview • Centralized controller model • Redundancy measures: • • Secondary / Tertiary controller assignment for APs Under-load AP/controller ratio for controller failure 802. 3 ad Link Aggregation for cable failures Switch stacks for switch failure Multiple paths to multiple core switches HSRP for router failure Firewall cluster in active/standby mode
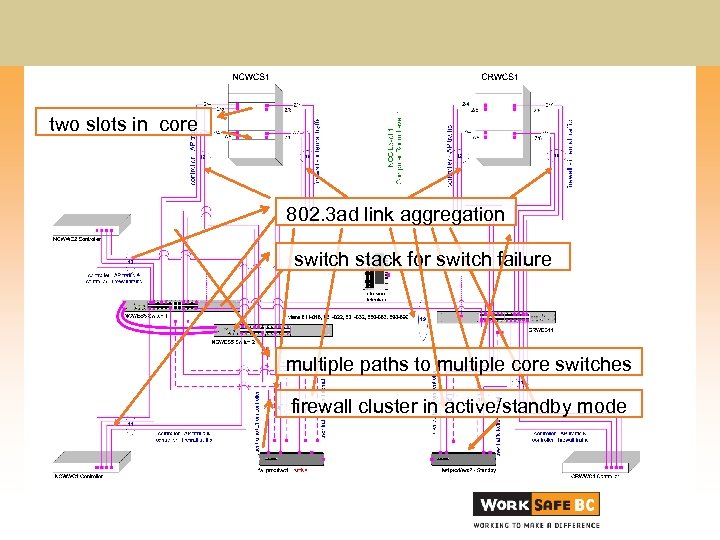
two slots in core 802. 3 ad link aggregation switch stack for switch failure multiple paths to multiple core switches firewall cluster in active/standby mode
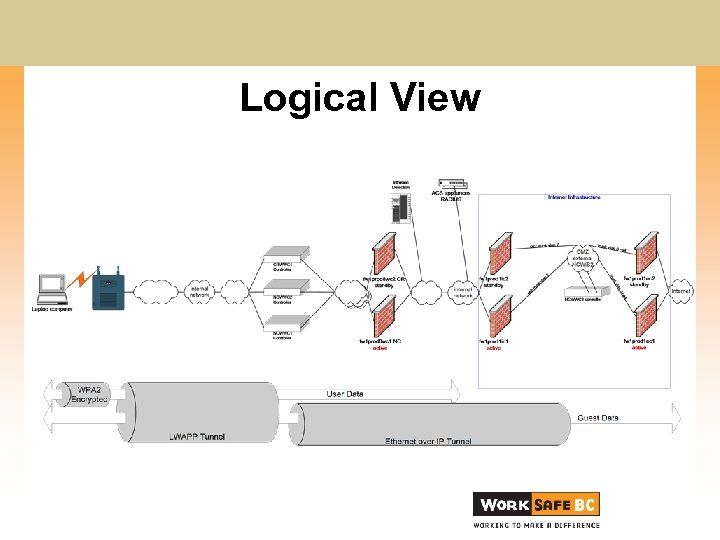
Logical View

Guest Access • Separate SSID (broadcast) • Ethernet over IP tunnel to Internet DMZ • Authentication models wired guest access • Secur. ID token held by Help Desk • Web page authentication
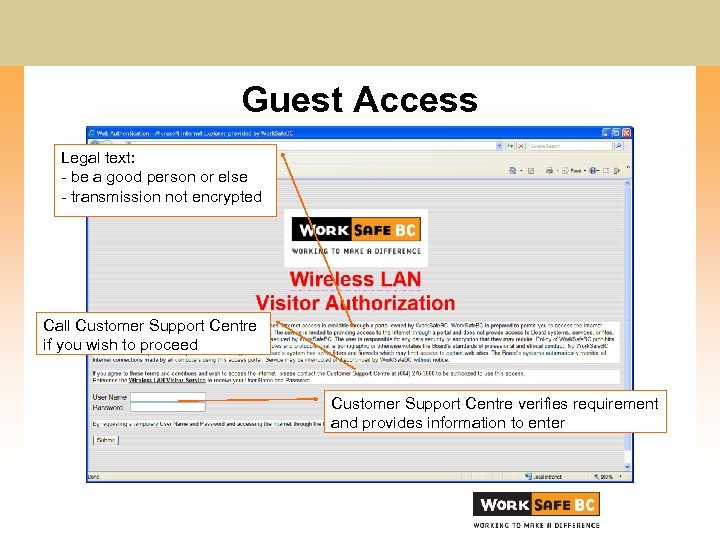
Guest Access Legal text: - be a good person or else - transmission not encrypted Call Customer Support Centre if you wish to proceed Customer Support Centre verifies requirement and provides information to enter

Challenges • Sorting out rogues (on vs. off network) • Problems in remote offices • Interference, rogues, security attacks

Futures • • • Broader Public Sector access Location: Will explore these capabilities 802. 11 n: No real requirement Non-workstation devices: will consider Voice over WLAN • No plans, Vo. IP experimental on wired side • Did site survey for voice coverage

First phase installation Additional for voice

Antenna Research • Greater RF gain needed • Users are mobile • Integration with personal protective gear • Sophisticated look – coolness factor

Questions ? ? ? ? ? ?
3d58ffc1ab3ca5b11e5e9ad0cd98a479.ppt