3848c2312becf598bc67f37b18af27d3.ppt
- Количество слайдов: 31

Wirtualizacja i optymalizacja infrastruktury Zbigniew Skurczyński Dyrektor regionalny EE F 5 Networks
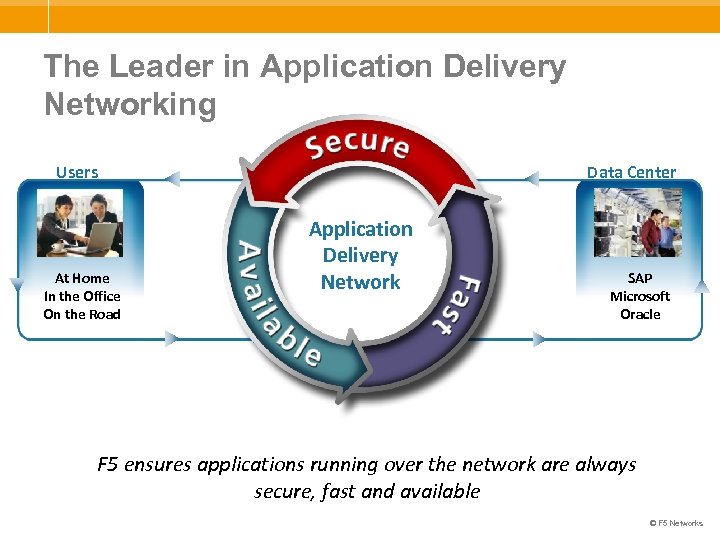
The Leader in Application Delivery Networking Users At Home In the Office On the Road Data Center Application Delivery Network SAP Microsoft Oracle F 5 ensures applications running over the network are always secure, fast and available © F 5 Networks
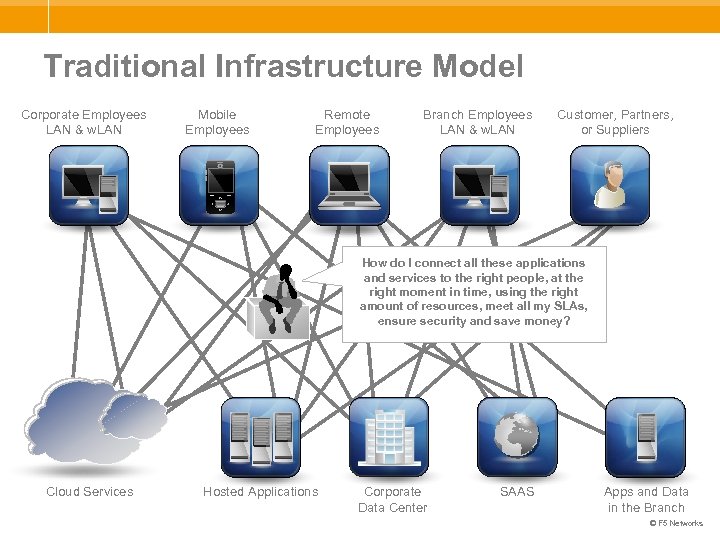
Traditional Infrastructure Model Corporate Employees LAN & w. LAN Mobile Employees Remote Employees Branch Employees LAN & w. LAN Customer, Partners, or Suppliers How do I connect all these applications and services to the right people, at the right moment in time, using the right amount of resources, meet all my SLAs, ensure security and save money? Cloud Services Hosted Applications Corporate Data Center SAAS Apps and Data in the Branch © F 5 Networks
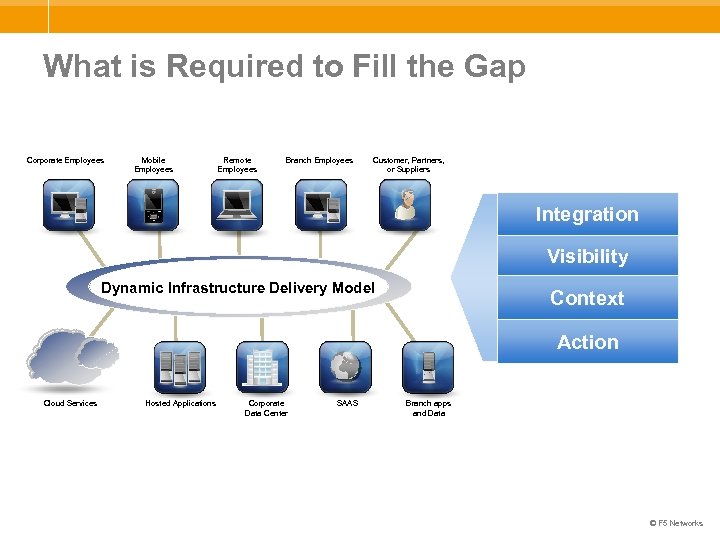
What is Required to Fill the Gap Corporate Employees Mobile Employees Remote Employees Branch Employees Customer, Partners, or Suppliers Integration Visibility Dynamic Infrastructure Delivery Model Context Action Cloud Services Hosted Applications Corporate Data Center SAAS Branch apps and Data © F 5 Networks
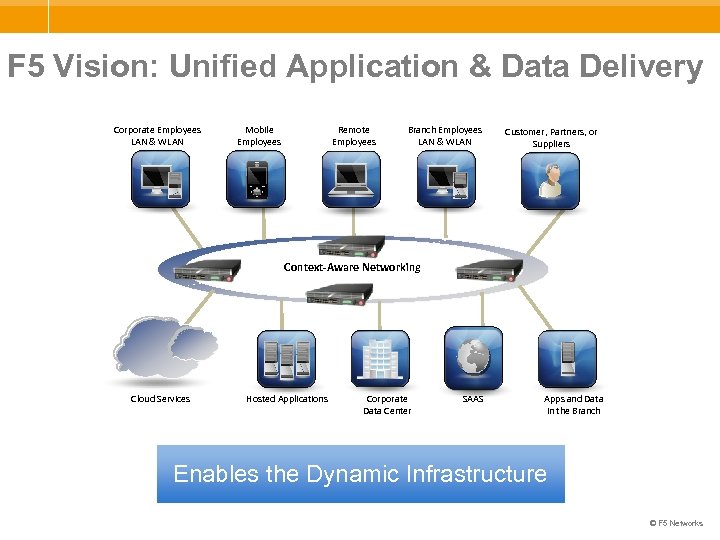
F 5 Vision: Unified Application & Data Delivery Corporate Employees LAN & WLAN Mobile Employees Remote Employees Branch Employees LAN & WLAN Customer, Partners, or Suppliers Context-Aware Networking Cloud Services Hosted Applications Corporate Data Center SAAS Apps and Data in the Branch Enables the Dynamic Infrastructure © F 5 Networks

Consolidation by Virtualisation Web Server App. Server File Storage Virtualization Web Server Virtualization Remote - WAN Data Center & Link Virtualization PC - Home Application Server Virtualization Web Server Cell Web Server PC - LAN Net. App EMC Windows file storage App. Server Web Server WLAN GTM & LC LTM ARX © F 5 Networks
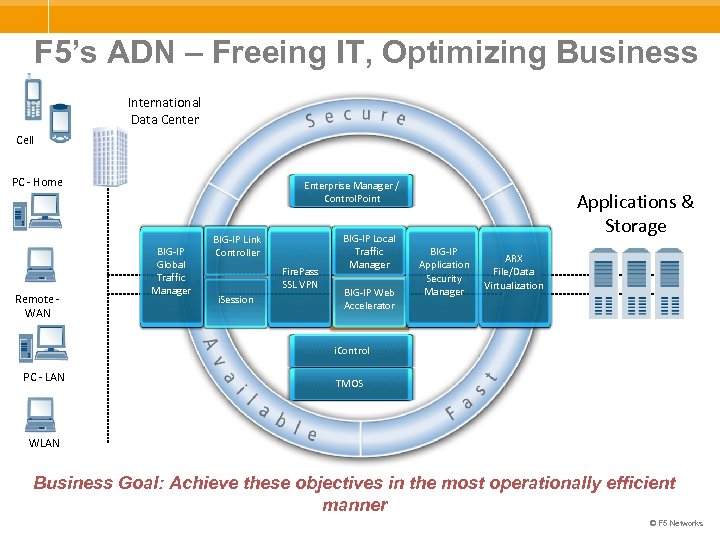
F 5’s ADN – Freeing IT, Optimizing Business International Data Center Cell PC - Home Remote - WAN Enterprise Manager / Control. Point BIG-IP Global Traffic Manager BIG-IP Link Controller Fire. Pass SSL VPN i. Session BIG-IP Local Traffic Manager BIG-IP Web Accelerator Applications & Storage BIG-IP Application Security Manager ARX File/Data Virtualization i. Control PC - LAN TMOS WLAN Business Goal: Achieve these objectives in the most operationally efficient manner © F 5 Networks

Wirtualizacja ośrodków obliczeniowych © F 5 Networks
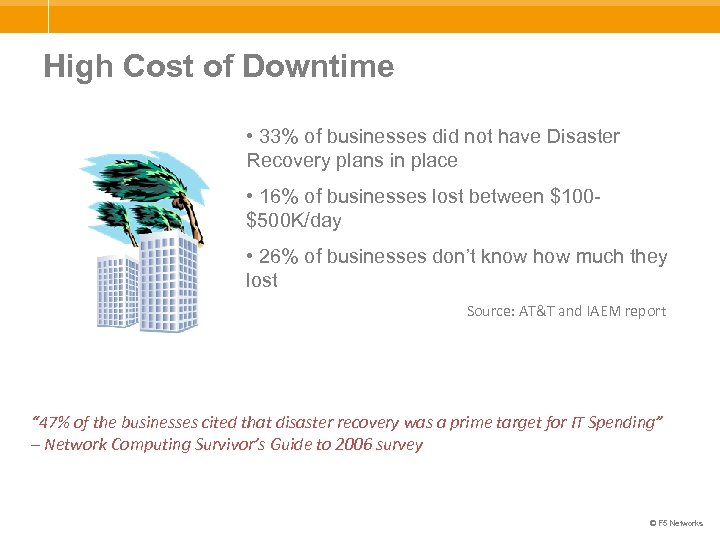
High Cost of Downtime • 33% of businesses did not have Disaster Recovery plans in place • 16% of businesses lost between $100$500 K/day • 26% of businesses don’t know how much they lost Source: AT&T and IAEM report “ 47% of the businesses cited that disaster recovery was a prime target for IT Spending” – Network Computing Survivor’s Guide to 2006 survey © F 5 Networks

Getting Users to the Best Available Data Centre Client L-DNS Site 1 (Primary) Site 2 (Back up) Router BIG-IP GTM BIG-IP LTM Corporate Servers © F 5 Networks
SOA Application Management Delivering unique flexibility and intelligence to meet emerging application challenges Sydney Data Centre Singapore Data Centre High availability Persistence Ease of maintenance © F 5 Networks

Wirtualizacja wewnątrz ośrodków obliczeniowych © F 5 Networks
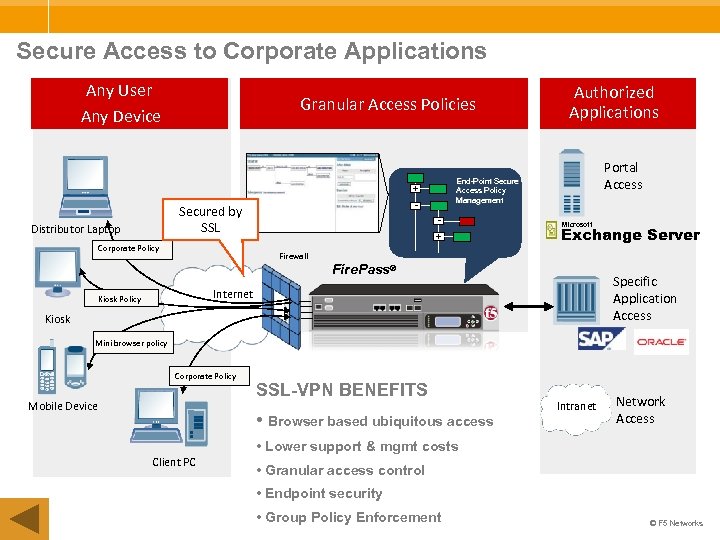
Secure Access to Corporate Applications Any User Any Device Granular Access Policies Distributor Laptop Corporate Policy Portal Access End-Point Secure Access Policy Management + - Secured by SSL Authorized Applications + Microsoft Exchange Server Firewall Fire. Pass® Specific Application Access Internet Kiosk Policy Kiosk Mini browser policy Corporate Policy Mobile Device SSL-VPN BENEFITS • Browser based ubiquitous access Intranet Network Access • Lower support & mgmt costs Client PC • Granular access control • Endpoint security • Group Policy Enforcement © F 5 Networks
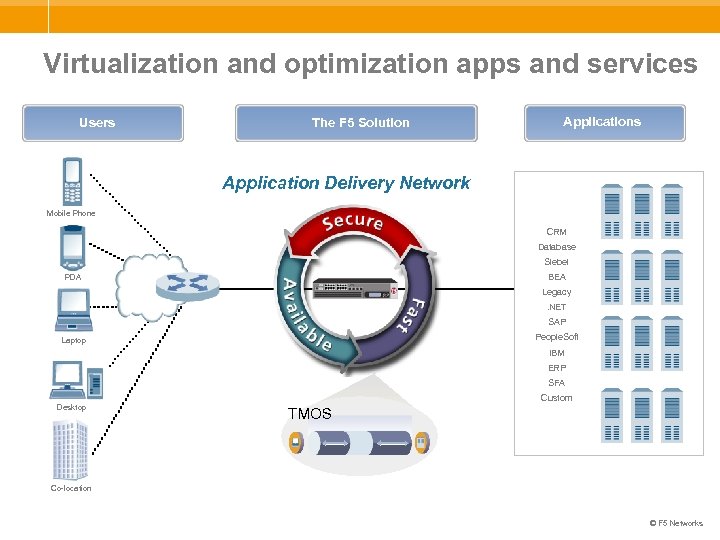
Virtualization and optimization apps and services Users The F 5 Solution Applications Application Delivery Network Mobile Phone CRM Database Siebel BEA PDA Legacy. NET SAP People. Soft Laptop IBM ERP SFA Desktop Custom TMOS Co-location © F 5 Networks
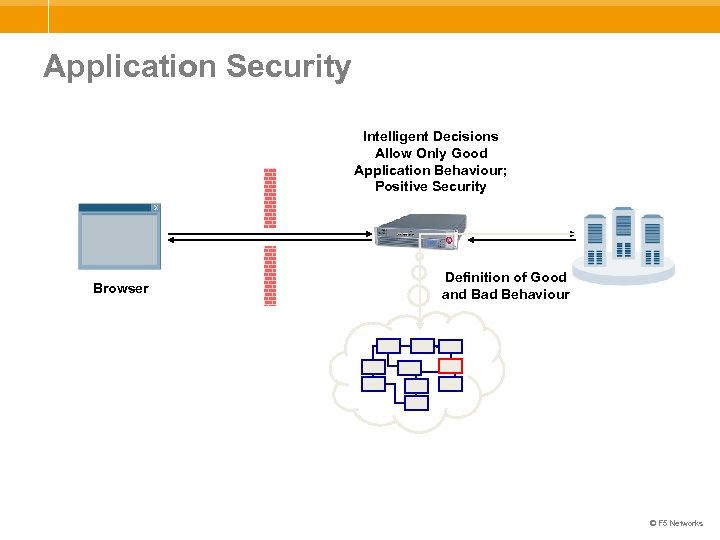
Application Security Intelligent Decisions Allow Only Good Application Behaviour; Positive Security Browser Definition of Good and Bad Behaviour © F 5 Networks
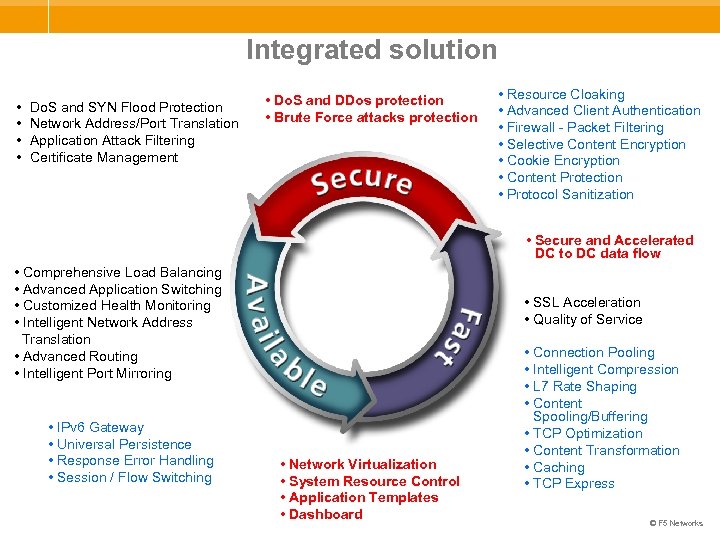
Integrated solution • • Do. S and SYN Flood Protection Network Address/Port Translation Application Attack Filtering Certificate Management • Do. S and DDos protection • Brute Force attacks protection • Resource Cloaking • Advanced Client Authentication • Firewall - Packet Filtering • Selective Content Encryption • Cookie Encryption • Content Protection • Protocol Sanitization • Secure and Accelerated DC to DC data flow • Comprehensive Load Balancing • Advanced Application Switching • Customized Health Monitoring • Intelligent Network Address Translation • Advanced Routing • Intelligent Port Mirroring • IPv 6 Gateway • Universal Persistence • Response Error Handling • Session / Flow Switching • SSL Acceleration • Quality of Service • Network Virtualization • System Resource Control • Application Templates • Dashboard • Connection Pooling • Intelligent Compression • L 7 Rate Shaping • Content Spooling/Buffering • TCP Optimization • Content Transformation • Caching • TCP Express © F 5 Networks
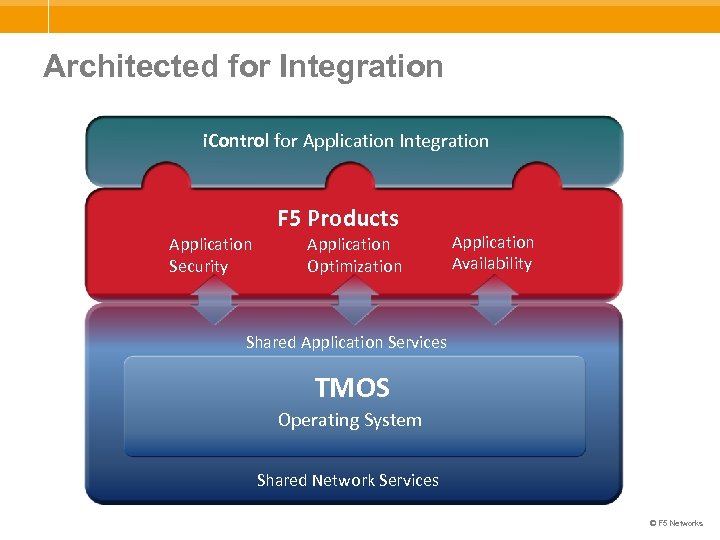
Architected for Integration i. Control for Application Integration F 5 Products Application Security Application Optimization Application Availability Shared Application Services TMOS Operating System Shared Network Services © F 5 Networks

BIG-IP Hardware Line-up Price BIG-IP 8900 BIG-IP 6900 BIG-IP 3600 BIG-IP 1600 Dual core CPU 4 10/1000 + 2 x 1 GB SFP 1 x 160 GB HD 4 GB memory SSL @ 5 K TPS / 1 Gb Bulk 1 Gbps max software compression Dual core CPU 8 10/1000 + 2 x 1 GB SFP 1 x 160 GB HD + 8 GB CF 4 GB memory SSL @ 10 K TPS / 2 Gb bulk 1 Gbps max software compression 2 x Dual core CPU 16 10/1000 + 8 x 1 GB SFP 2 x 320 GB HD (S/W RAID) + 8 GB CF 8 GB memory SSL @ 25 K TPS / 4 Gb bulk 5 Gbps max hardware compression 2 x Quad core CPU 16 10/1000 + 8 x 1 GB SFP 2 x 320 GB HD (S/W RAID) + 8 GB CF 16 GB memory SSL @ 58 K TPS / 9. 6 Gb bulk 6 Gbps max hardware compression 12 Gbps Traffic Multiple Product Modules 6 Gbps Traffic Multiple Product Modules 2 Gbps Traffic 1 Advanced Product Module 1 Gbps Traffic 1 Basic Product Module Function / Performance © F 5 Networks

On-Demand & Dynamic Application Security fic l Traf Loca G-IP r + BIG-IP BI ge rity Mana tion Secu ca Appli anager M Leading Value • World’s first on-demand scaling Web Application Firewall • Advanced security • Integrated security performance • Application insight/visibility Better security 2 x+ performance! © F 5 Networks

Ultimate Reliability Client Server Multi-Level Redundancy • Blade failure will not cause chassis failure • Redundant and hot swappable components Always Available © F 5 Networks

On Demand – Zero Reconfiguration Virtual Machines Servers Physical Servers • Automatic addition of power • No need to overprovision • Fixed and predictable opex Virtual Machines Physical Servers © F 5 Networks

WIRTUALIZACJA STORAGE’U © F 5 Networks
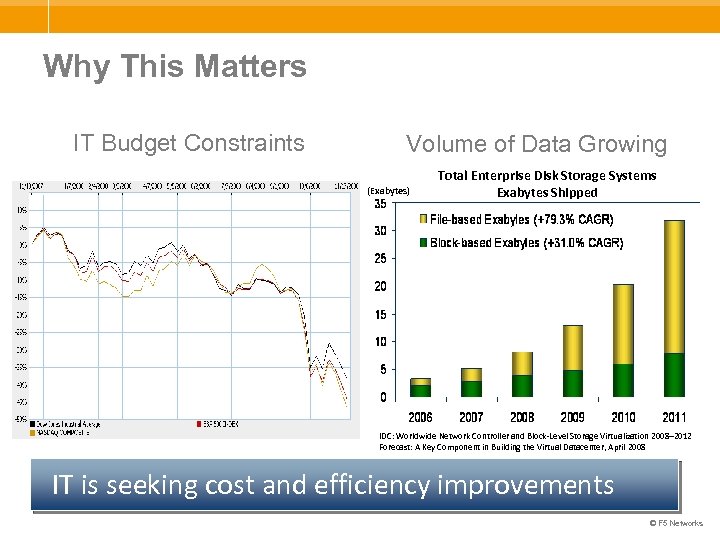
Why This Matters IT Budget Constraints Volume of Data Growing (Exabytes) Total Enterprise Disk Storage Systems Exabytes Shipped IDC: Worldwide Network Controller and Block-Level Storage Virtualization 2008– 2012 Forecast: A Key Component in Building the Virtual Datacenter, April 2008 IT is seeking cost and efficiency improvements © F 5 Networks
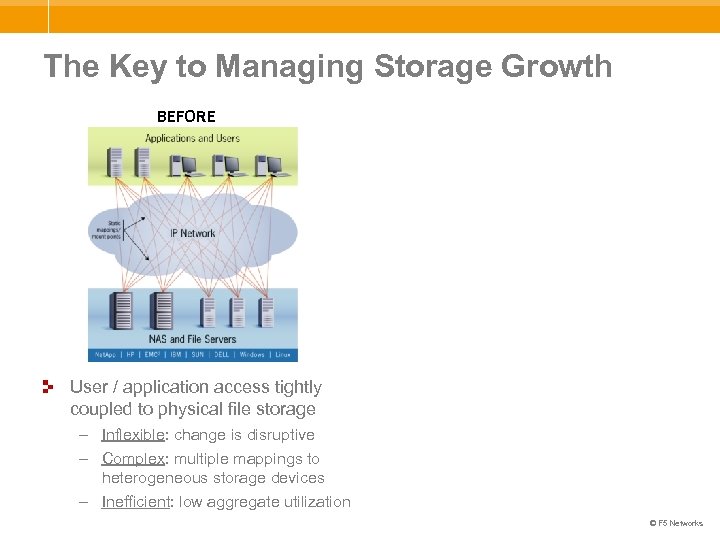
The Key to Managing Storage Growth BEFORE User / application access tightly coupled to physical file storage – Inflexible: change is disruptive – Complex: multiple mappings to heterogeneous storage devices – Inefficient: low aggregate utilization © F 5 Networks

The Key to Managing Storage Growth BEFORE AFTER User / application access tightly coupled to physical file storage – Inflexible: change is disruptive – Complex: multiple mappings to heterogeneous storage devices – Inefficient: low aggregate utilization File access decoupled from physical storage location – Flexible: change is non-disruptive – Simple: single mapping to unified storage pool – Efficient: maximize utilization © F 5 Networks

What Does F 5 ARX Do? • Decouples access from physical file location • Presents a Global Namespace view of the data – a federation of the underlying file systems • Masks changes to underlying storage systems from users and applications • Automates common storage management tasks – Migration – Storage Tiering – Load Balancing • These tasks now take place without affecting access to the file data or requiring client re-configuration © F 5 Networks
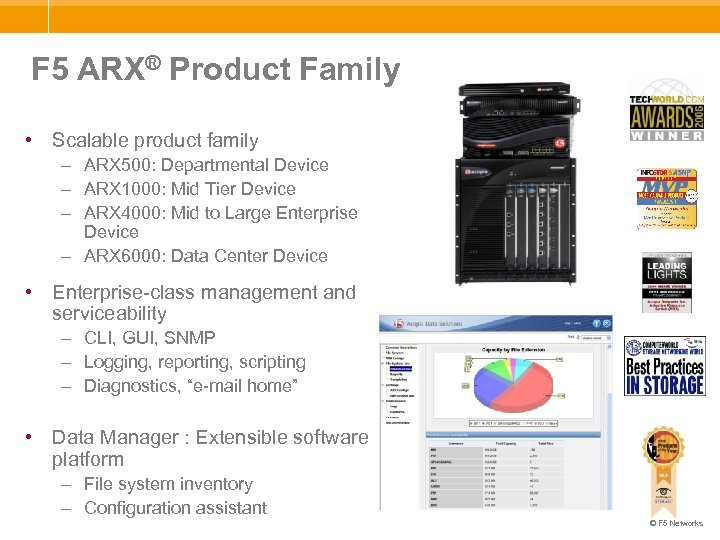
F 5 ARX® Product Family • Scalable product family – ARX 500: Departmental Device – ARX 1000: Mid Tier Device – ARX 4000: Mid to Large Enterprise Device – ARX 6000: Data Center Device • Enterprise-class management and serviceability – CLI, GUI, SNMP – Logging, reporting, scripting – Diagnostics, “e-mail home” • Data Manager : Extensible software platform – File system inventory – Configuration assistant © F 5 Networks
Podsumowanie © F 5 Networks
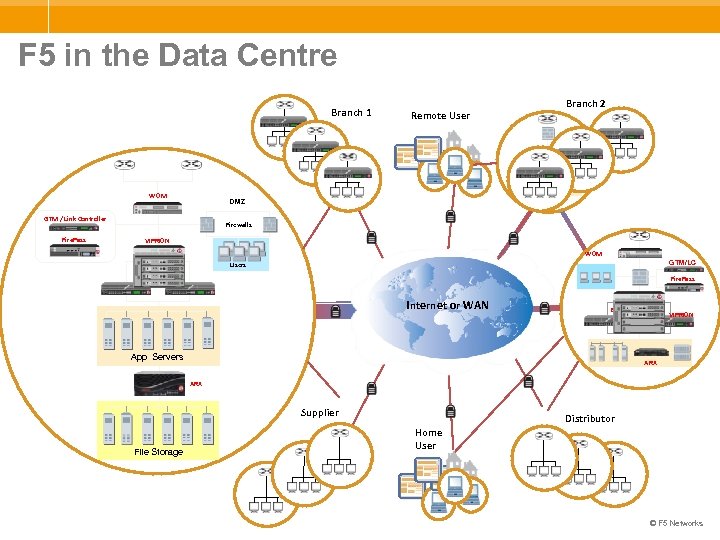
F 5 in the Data Centre Branch 1 Branch 2 Remote User Munich WOM DMZ GTM / Link Controller Fire. Pass Firewalls VIPRION WOM GTM/LC Users BIG-IP LTM Web. Accelerator Fire. Pass Internet or WAN BIG-IP LTM / WA Munich App Servers VIPRION ARX Supplier File Storage Distributor Home User © F 5 Networks

The Leader in Application Delivery Networking Users At Home In the Office On the Road Data Center Application Delivery Network SAP Microsoft Oracle F 5 ensures applications running over the network are always secure, fast and available © F 5 Networks

3848c2312becf598bc67f37b18af27d3.ppt