2c74f08a5eff43d0217a5c89a8a0ae59.ppt
- Количество слайдов: 129
 Wireless Sensor Networking (Understanding the radio, MAC, & routing protocols) Romit Roy Choudhury 1 1
Wireless Sensor Networking (Understanding the radio, MAC, & routing protocols) Romit Roy Choudhury 1 1
 Sensor Networking – Why ? ? n Data Collection – A basic need § Will the volcano erupt? Need temperature/gas signatures § How much Global Warming? Need ocean current data § How many enemy tanks crossed? n Human monitoring possible/feasible ? § Often risky, impenetrable, costly, … n But science has collected data for centuries … § Manual (wired) placement, periodic human visits § Wireless data transmitters § Community accepted barriers/defiiencies 2 2
Sensor Networking – Why ? ? n Data Collection – A basic need § Will the volcano erupt? Need temperature/gas signatures § How much Global Warming? Need ocean current data § How many enemy tanks crossed? n Human monitoring possible/feasible ? § Often risky, impenetrable, costly, … n But science has collected data for centuries … § Manual (wired) placement, periodic human visits § Wireless data transmitters § Community accepted barriers/defiiencies 2 2
 New Opportunities n Device miniaturization § Moore’s law § Processors envisioned as smart dust n Innovations in wireless communication § Low power communication § Antenna sizes smaller with high frequency Device + RF + sensors - A new breakthrough: Scattered sensor motes self-organize themselves forming a network. Sensed data aggregated, processed, and transported to base station. Low risk, low cost, and heavy penetration 3 3
New Opportunities n Device miniaturization § Moore’s law § Processors envisioned as smart dust n Innovations in wireless communication § Low power communication § Antenna sizes smaller with high frequency Device + RF + sensors - A new breakthrough: Scattered sensor motes self-organize themselves forming a network. Sensed data aggregated, processed, and transported to base station. Low risk, low cost, and heavy penetration 3 3
 Plethora of Applications 4 4
Plethora of Applications 4 4
 Plethora of Challenges n Devices § Reducing energy consumption § Heavy programming constraints (16 KB RAM) n Wireless Radio Network § § § Reliable low power communication Medium access control (MAC) Network wide energy conservation Routing Aggregation, compression, suppression … 5 5
Plethora of Challenges n Devices § Reducing energy consumption § Heavy programming constraints (16 KB RAM) n Wireless Radio Network § § § Reliable low power communication Medium access control (MAC) Network wide energy conservation Routing Aggregation, compression, suppression … 5 5
 Today’s Talk n Understanding the wireless channel § The departure from wireline § The key challenges n Medium access control § Protocol design § Energy-awareness (coordinated sleeping) n Routing § Unicast (Diffusion) § Broadcast (Gossip) 6 6
Today’s Talk n Understanding the wireless channel § The departure from wireline § The key challenges n Medium access control § Protocol design § Energy-awareness (coordinated sleeping) n Routing § Unicast (Diffusion) § Broadcast (Gossip) 6 6
 The Wireless Channel 7 7
The Wireless Channel 7 7
 Many Motivations for Wireless n Unrestricted mobility / deployability § Unplugged from power outlet n Significantly lower cost § No cable layout, service provision § Low maintenance n Ease § Direct communication with minimum infratructure 8 8
Many Motivations for Wireless n Unrestricted mobility / deployability § Unplugged from power outlet n Significantly lower cost § No cable layout, service provision § Low maintenance n Ease § Direct communication with minimum infratructure 8 8
 From Links to Networks n Variety of architectures § Single hop networks § Multi-hop networks 9 9
From Links to Networks n Variety of architectures § Single hop networks § Multi-hop networks 9 9
 The Wireless Future … Internet 10 10
The Wireless Future … Internet 10 10
 No Free Lunch n Numerous challenges § § § Channel fluctuation Lower bandwidth Limited Battery power Disconnection due to mobility Security … 11 11
No Free Lunch n Numerous challenges § § § Channel fluctuation Lower bandwidth Limited Battery power Disconnection due to mobility Security … 11 11
 Question Is … Can’t we use the rich “wireline” knowledge ? In solving the wireless challenges 12 12
Question Is … Can’t we use the rich “wireline” knowledge ? In solving the wireless challenges 12 12
 The Answer Wireless channel: A dispersive medium The PHY and MAC layer completely dissimilar The whole game changes 13 13
The Answer Wireless channel: A dispersive medium The PHY and MAC layer completely dissimilar The whole game changes 13 13
 On Our Agenda n Quick Glimpse § Medium Access Control • Wired • Wireless § The emergence of 802. 11 § Evolution of sensor network MAC protocols • Energy awareness 14 14
On Our Agenda n Quick Glimpse § Medium Access Control • Wired • Wireless § The emergence of 802. 11 § Evolution of sensor network MAC protocols • Energy awareness 14 14
 Medium Access Control 15 15
Medium Access Control 15 15
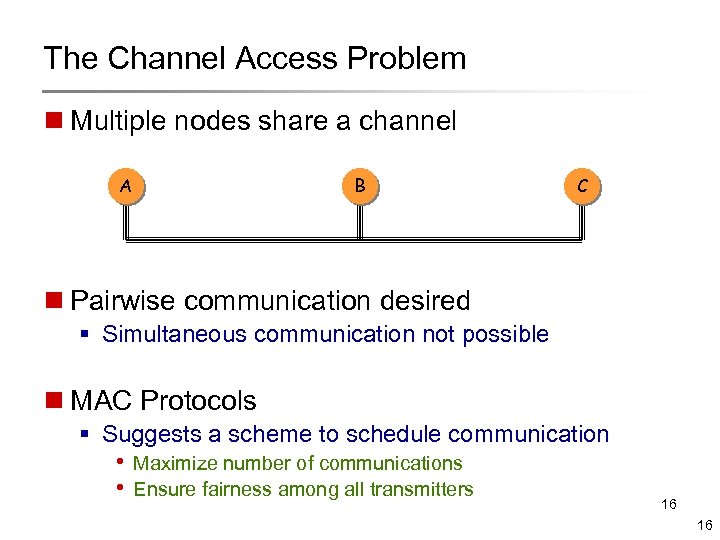 The Channel Access Problem n Multiple nodes share a channel A B C n Pairwise communication desired § Simultaneous communication not possible n MAC Protocols § Suggests a scheme to schedule communication • Maximize number of communications • Ensure fairness among all transmitters 16 16
The Channel Access Problem n Multiple nodes share a channel A B C n Pairwise communication desired § Simultaneous communication not possible n MAC Protocols § Suggests a scheme to schedule communication • Maximize number of communications • Ensure fairness among all transmitters 16 16
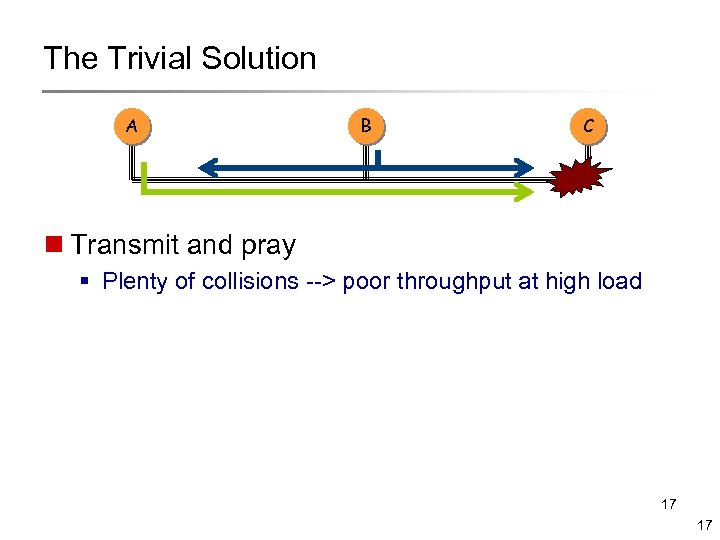 The Trivial Solution A B C n Transmit and pray § Plenty of collisions --> poor throughput at high load 17 17
The Trivial Solution A B C n Transmit and pray § Plenty of collisions --> poor throughput at high load 17 17
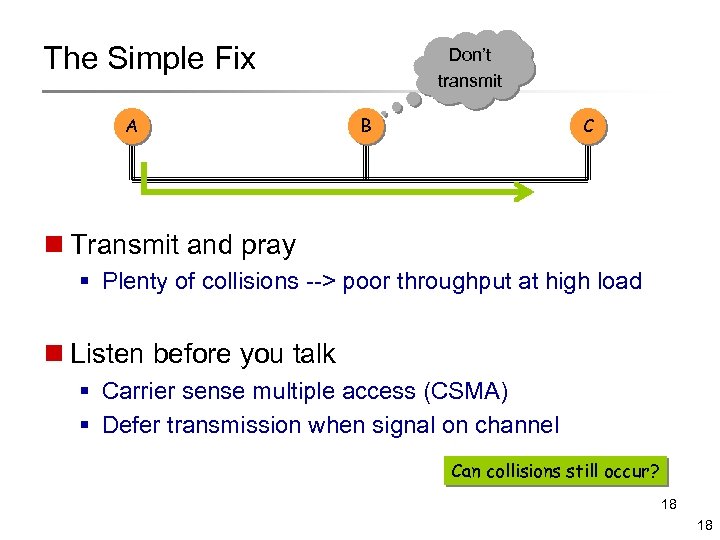 The Simple Fix A Don’t transmit B C n Transmit and pray § Plenty of collisions --> poor throughput at high load n Listen before you talk § Carrier sense multiple access (CSMA) § Defer transmission when signal on channel Can collisions still occur? 18 18
The Simple Fix A Don’t transmit B C n Transmit and pray § Plenty of collisions --> poor throughput at high load n Listen before you talk § Carrier sense multiple access (CSMA) § Defer transmission when signal on channel Can collisions still occur? 18 18
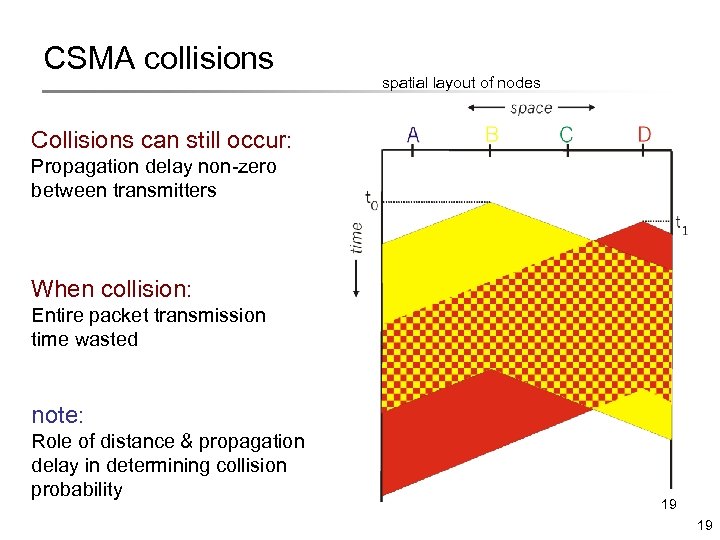 CSMA collisions spatial layout of nodes Collisions can still occur: Propagation delay non-zero between transmitters When collision: Entire packet transmission time wasted note: Role of distance & propagation delay in determining collision probability 19 19
CSMA collisions spatial layout of nodes Collisions can still occur: Propagation delay non-zero between transmitters When collision: Entire packet transmission time wasted note: Role of distance & propagation delay in determining collision probability 19 19
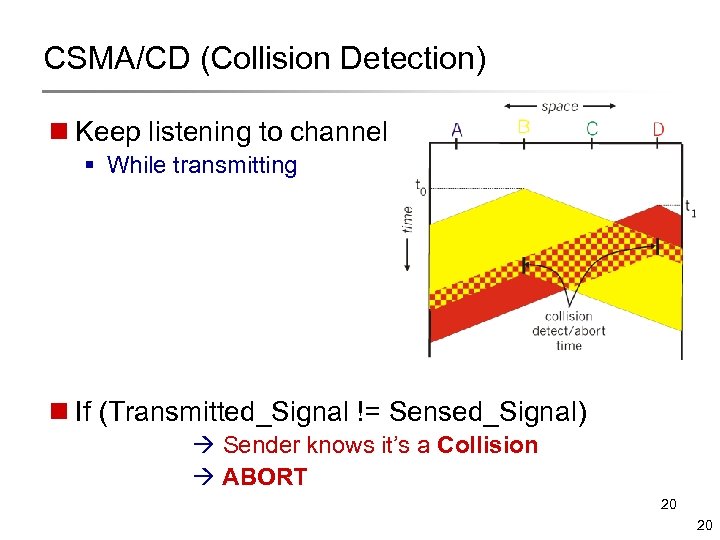 CSMA/CD (Collision Detection) n Keep listening to channel § While transmitting n If (Transmitted_Signal != Sensed_Signal) Sender knows it’s a Collision ABORT 20 20
CSMA/CD (Collision Detection) n Keep listening to channel § While transmitting n If (Transmitted_Signal != Sensed_Signal) Sender knows it’s a Collision ABORT 20 20
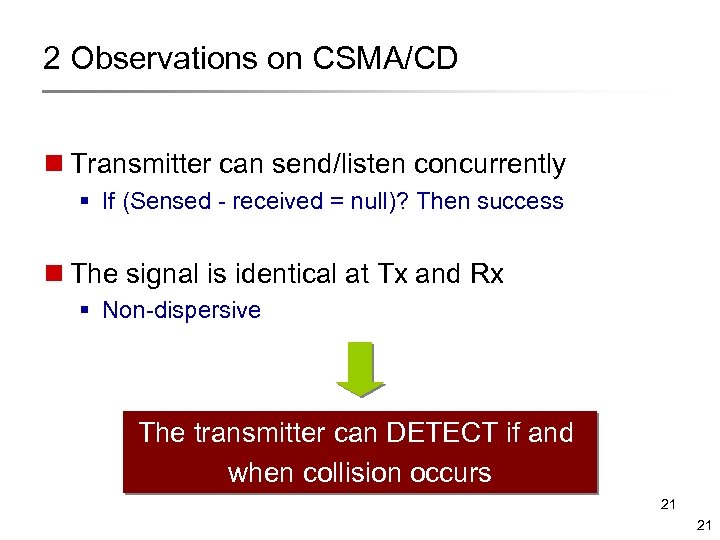 2 Observations on CSMA/CD n Transmitter can send/listen concurrently § If (Sensed - received = null)? Then success n The signal is identical at Tx and Rx § Non-dispersive The transmitter can DETECT if and when collision occurs 21 21
2 Observations on CSMA/CD n Transmitter can send/listen concurrently § If (Sensed - received = null)? Then success n The signal is identical at Tx and Rx § Non-dispersive The transmitter can DETECT if and when collision occurs 21 21
 Unfortunately … Both observations do not hold for wireless Leading to … 22 22
Unfortunately … Both observations do not hold for wireless Leading to … 22 22
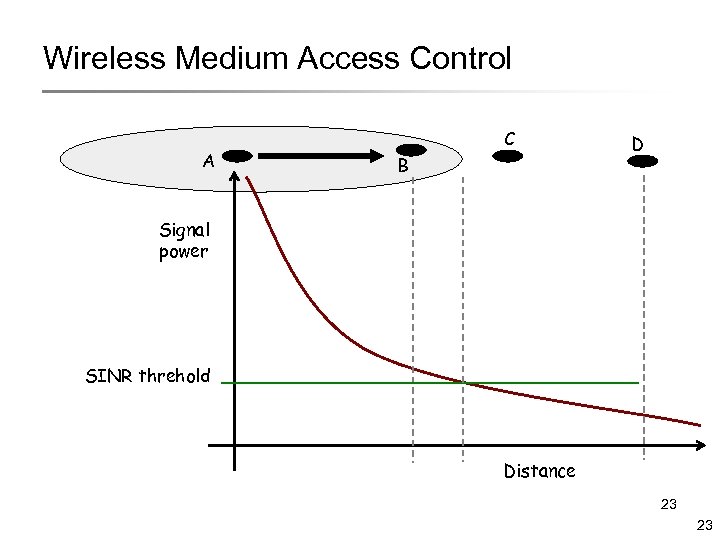 Wireless Medium Access Control A C B D Signal power SINR threhold Distance 23 23
Wireless Medium Access Control A C B D Signal power SINR threhold Distance 23 23
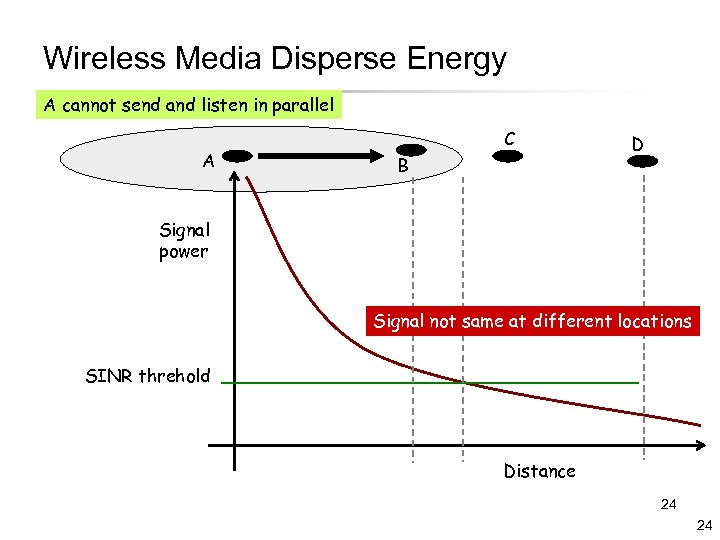 Wireless Media Disperse Energy A cannot send and listen in parallel A C B D Signal power Signal not same at different locations SINR threhold Distance 24 24
Wireless Media Disperse Energy A cannot send and listen in parallel A C B D Signal power Signal not same at different locations SINR threhold Distance 24 24
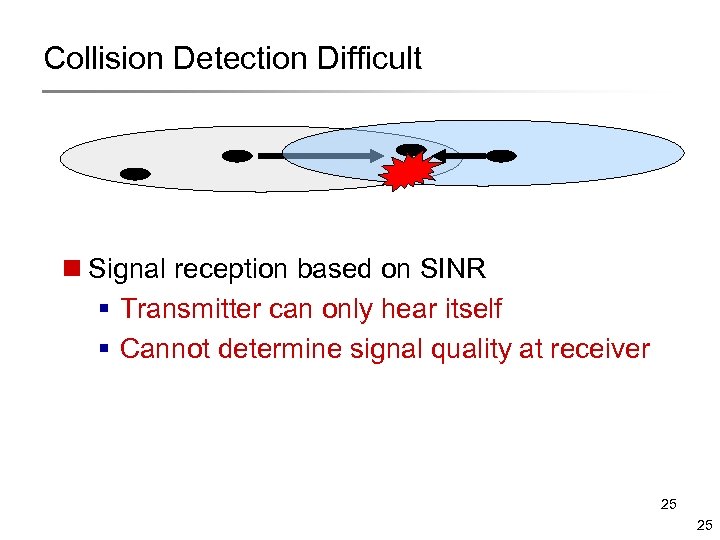 Collision Detection Difficult n Signal reception based on SINR § Transmitter can only hear itself § Cannot determine signal quality at receiver 25 25
Collision Detection Difficult n Signal reception based on SINR § Transmitter can only hear itself § Cannot determine signal quality at receiver 25 25
 Calculating SINR A B C 26 26
Calculating SINR A B C 26 26
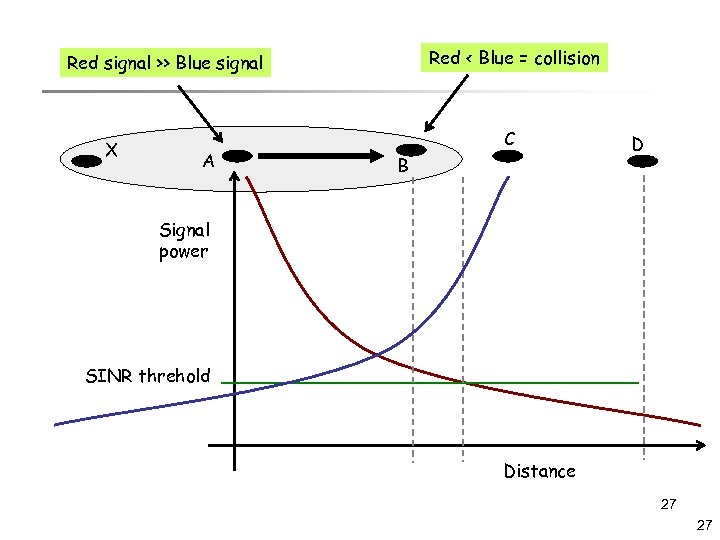 Red < Blue = collision Red signal >> Blue signal X A C B D Signal power SINR threhold Distance 27 27
Red < Blue = collision Red signal >> Blue signal X A C B D Signal power SINR threhold Distance 27 27
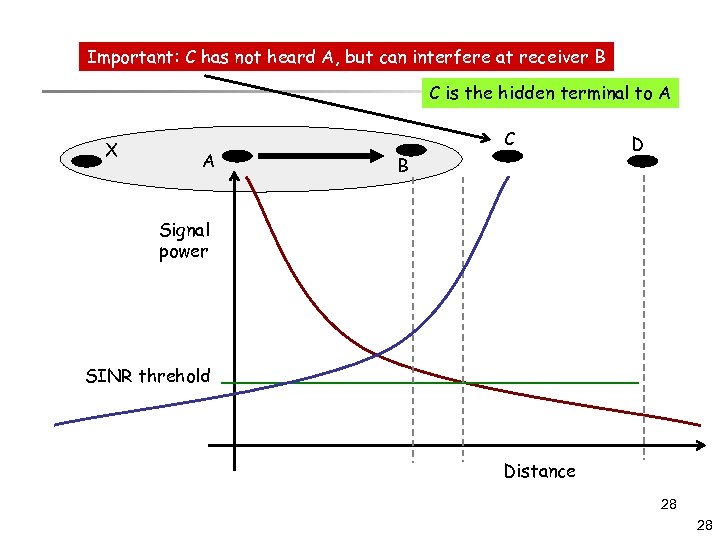 Important: C has not heard A, but can interfere at receiver B C is the hidden terminal to A X A C B D Signal power SINR threhold Distance 28 28
Important: C has not heard A, but can interfere at receiver B C is the hidden terminal to A X A C B D Signal power SINR threhold Distance 28 28
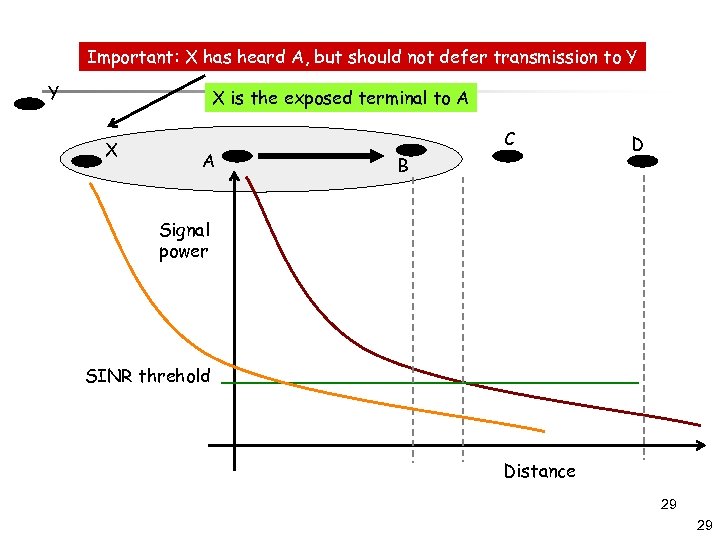 Important: X has heard A, but should not defer transmission to Y Y X is the exposed terminal to A X A C B D Signal power SINR threhold Distance 29 29
Important: X has heard A, but should not defer transmission to Y Y X is the exposed terminal to A X A C B D Signal power SINR threhold Distance 29 29
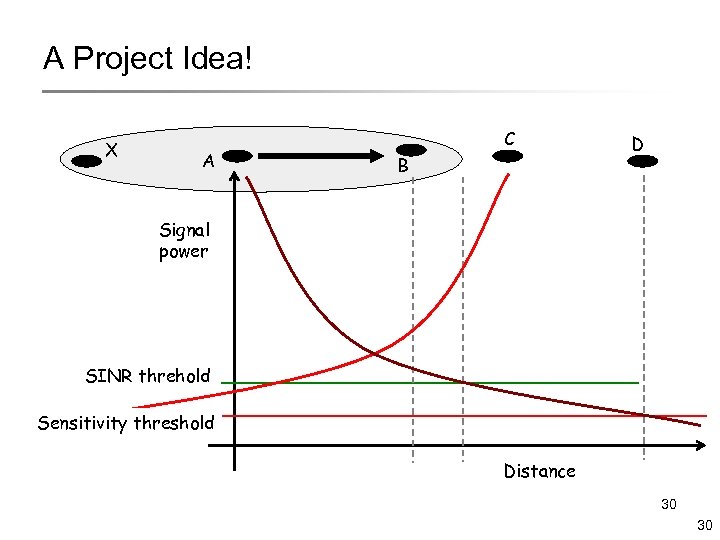 A Project Idea! X A C B D Signal power SINR threhold Sensitivity threshold Distance 30 30
A Project Idea! X A C B D Signal power SINR threhold Sensitivity threshold Distance 30 30
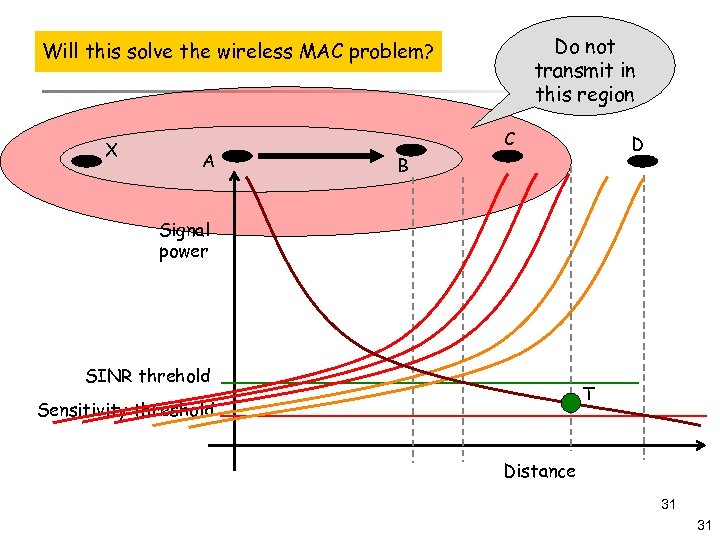 A Project Idea! Do not transmit in this region Will this solve the wireless MAC problem? X A C D B Signal power SINR threhold T Sensitivity threshold Distance 31 31
A Project Idea! Do not transmit in this region Will this solve the wireless MAC problem? X A C D B Signal power SINR threhold T Sensitivity threshold Distance 31 31
 The Emergence of 802. 11 n Wireless MAC proved to be non-trivial n 1992 - research by Karn (MACA) n 1994 - research by Bhargavan (MACAW) n Led to IEEE 802. 11 committee § The standard was ratified in 1999 32 32
The Emergence of 802. 11 n Wireless MAC proved to be non-trivial n 1992 - research by Karn (MACA) n 1994 - research by Bhargavan (MACAW) n Led to IEEE 802. 11 committee § The standard was ratified in 1999 32 32
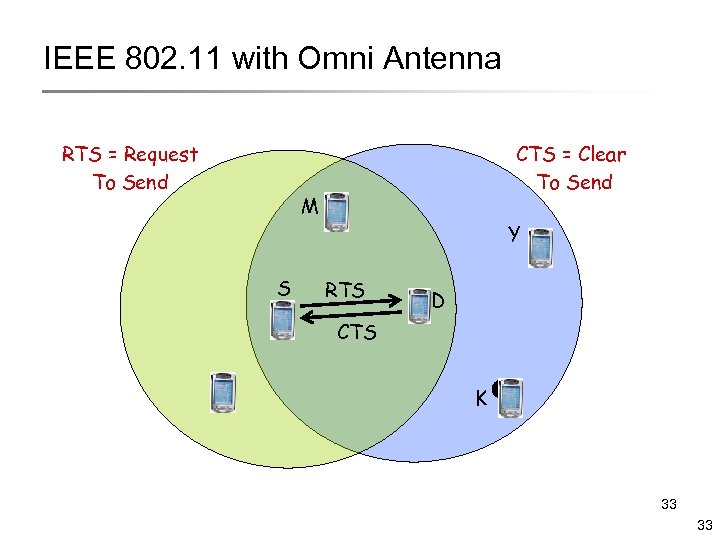 IEEE 802. 11 with Omni Antenna RTS = Request To Send CTS = Clear To Send M S Y RTS D CTS K 33 33
IEEE 802. 11 with Omni Antenna RTS = Request To Send CTS = Clear To Send M S Y RTS D CTS K 33 33
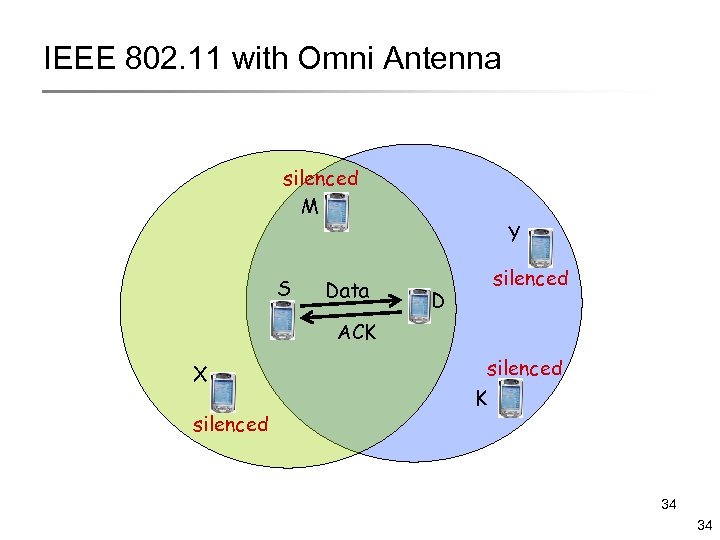 IEEE 802. 11 with Omni Antenna silenced M S Data Y D silenced ACK X silenced K 34 34
IEEE 802. 11 with Omni Antenna silenced M S Data Y D silenced ACK X silenced K 34 34
 But is that enough? 35 35
But is that enough? 35 35
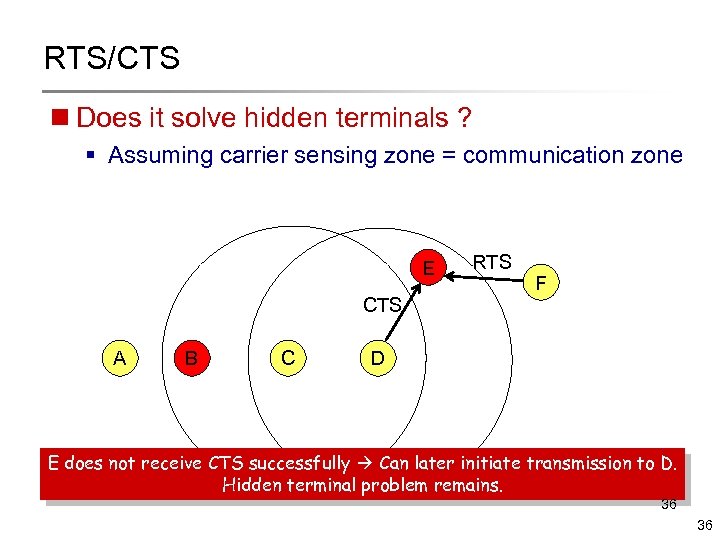 RTS/CTS n Does it solve hidden terminals ? § Assuming carrier sensing zone = communication zone E RTS F CTS A B C D E does not receive CTS successfully Can later initiate transmission to D. Hidden terminal problem remains. 36 36
RTS/CTS n Does it solve hidden terminals ? § Assuming carrier sensing zone = communication zone E RTS F CTS A B C D E does not receive CTS successfully Can later initiate transmission to D. Hidden terminal problem remains. 36 36
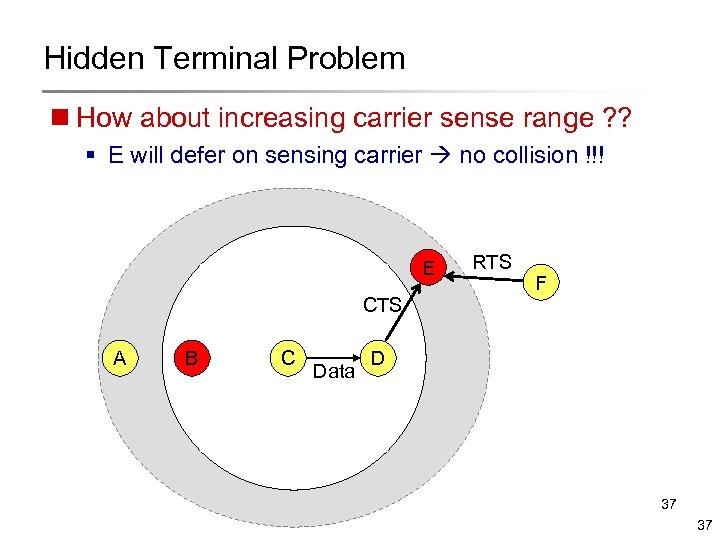 Hidden Terminal Problem n How about increasing carrier sense range ? ? § E will defer on sensing carrier no collision !!! E RTS F CTS A B C Data D 37 37
Hidden Terminal Problem n How about increasing carrier sense range ? ? § E will defer on sensing carrier no collision !!! E RTS F CTS A B C Data D 37 37
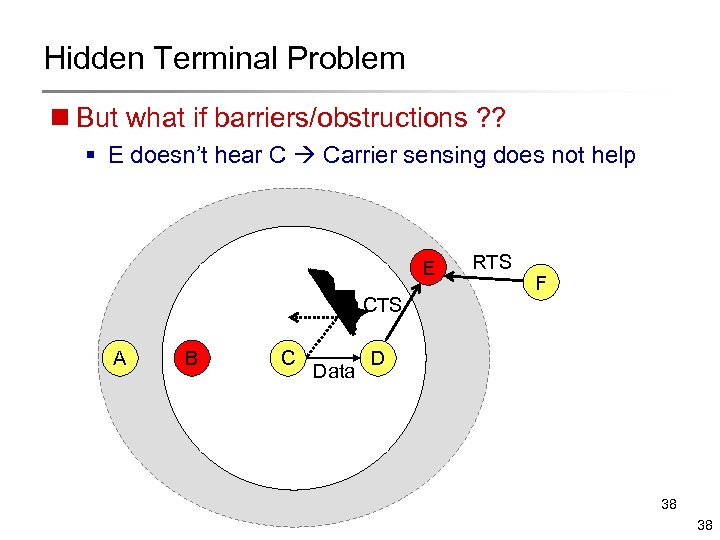 Hidden Terminal Problem n But what if barriers/obstructions ? ? § E doesn’t hear C Carrier sensing does not help E RTS F CTS A B C Data D 38 38
Hidden Terminal Problem n But what if barriers/obstructions ? ? § E doesn’t hear C Carrier sensing does not help E RTS F CTS A B C Data D 38 38
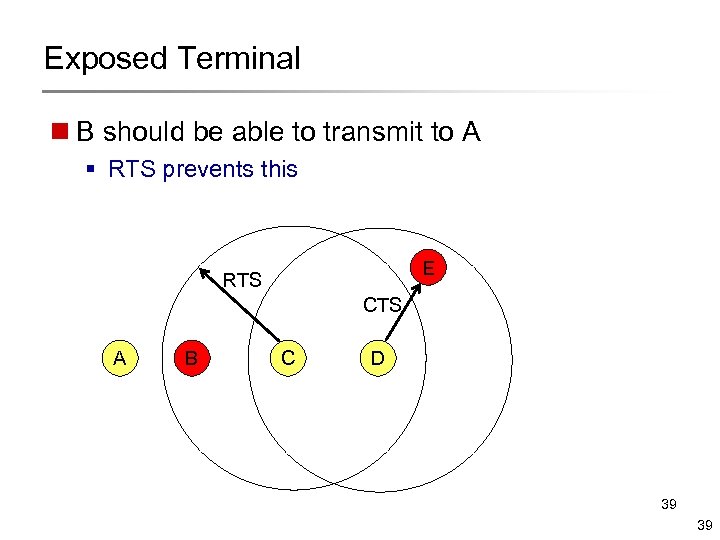 Exposed Terminal n B should be able to transmit to A § RTS prevents this E RTS CTS A B C D 39 39
Exposed Terminal n B should be able to transmit to A § RTS prevents this E RTS CTS A B C D 39 39
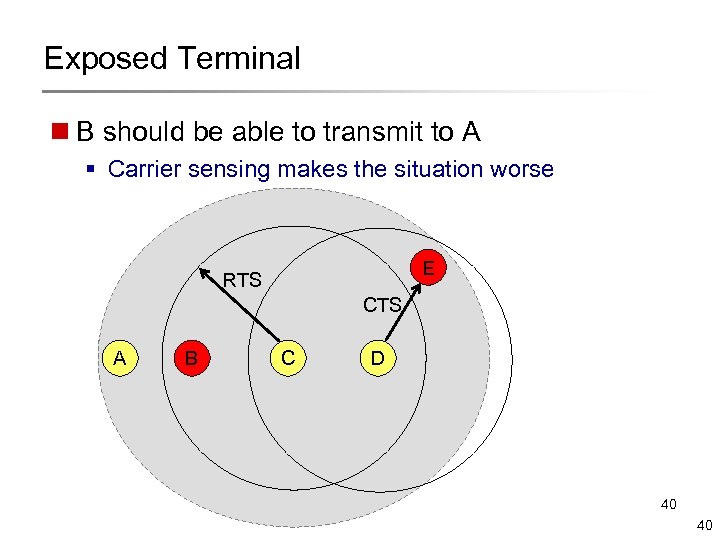 Exposed Terminal n B should be able to transmit to A § Carrier sensing makes the situation worse E RTS CTS A B C D 40 40
Exposed Terminal n B should be able to transmit to A § Carrier sensing makes the situation worse E RTS CTS A B C D 40 40
 Thoughts ! n 802. 11 does not solve HT/ET completely § Only alleviates the problem through RTS/CTS and recommends larger CS zone n Large CS zone aggravates exposed terminals § Spatial reuse reduces A tradeoff § RTS/CTS packets also consume bandwidth § Moreover, backing off mechanism is also wasteful The search for the best MAC protocol is still on. However, 802. 11 is being optimized too. Thus, wireless MAC research still alive 41 41
Thoughts ! n 802. 11 does not solve HT/ET completely § Only alleviates the problem through RTS/CTS and recommends larger CS zone n Large CS zone aggravates exposed terminals § Spatial reuse reduces A tradeoff § RTS/CTS packets also consume bandwidth § Moreover, backing off mechanism is also wasteful The search for the best MAC protocol is still on. However, 802. 11 is being optimized too. Thus, wireless MAC research still alive 41 41
 Questions? 42 42
Questions? 42 42
 Energy-Awareness n 802. 11 optimizes for throughput/latency § Energy savings is second priority n Unattended sensor networks § Operate on AA batteries § Yet, expected to last for months or years n Energy-awareness is the key § Throughput and latency is secondary 43 43
Energy-Awareness n 802. 11 optimizes for throughput/latency § Energy savings is second priority n Unattended sensor networks § Operate on AA batteries § Yet, expected to last for months or years n Energy-awareness is the key § Throughput and latency is secondary 43 43
 An Energy-Efficient MAC Protocol for Wireless Sensor Networks (S-MAC) Wei Ye, John Heidemann, Deborah Estrin 44 44
An Energy-Efficient MAC Protocol for Wireless Sensor Networks (S-MAC) Wei Ye, John Heidemann, Deborah Estrin 44 44
 Major source of energy waste n Collision n Overhearing n Control Overhead n Idle Listening § Listening to possible traffic that is not sent § 50%-100% energy drain compared with receiving 45 45
Major source of energy waste n Collision n Overhearing n Control Overhead n Idle Listening § Listening to possible traffic that is not sent § 50%-100% energy drain compared with receiving 45 45
 Avenues to Reduce Energy Consumption (1) Periodic listen and sleep (2) Collision avoidance (3) Overhearing avoidance (4) Message passing 46 46
Avenues to Reduce Energy Consumption (1) Periodic listen and sleep (2) Collision avoidance (3) Overhearing avoidance (4) Message passing 46 46
 (1) Periodic Listen and Sleep n The main idea § Put nodes to sleep periodically § Called “Duty Cycles” § However, ensure that sleep/wake-up is synchronous 47 47
(1) Periodic Listen and Sleep n The main idea § Put nodes to sleep periodically § Called “Duty Cycles” § However, ensure that sleep/wake-up is synchronous 47 47
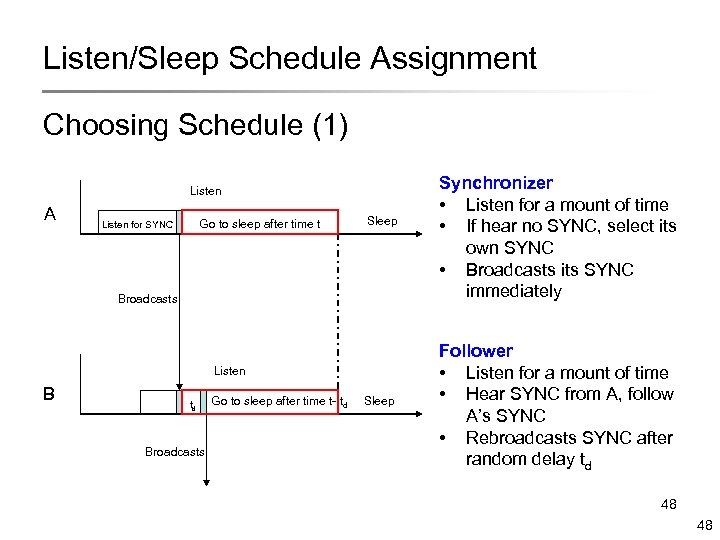 Listen/Sleep Schedule Assignment Choosing Schedule (1) Listen A Go to sleep after time t Listen for SYNC Sleep Broadcasts Listen B td Broadcasts Go to sleep after time t- td Sleep Synchronizer • Listen for a mount of time • If hear no SYNC, select its own SYNC • Broadcasts its SYNC immediately Follower • Listen for a mount of time • Hear SYNC from A, follow A’s SYNC • Rebroadcasts SYNC after random delay td 48 48
Listen/Sleep Schedule Assignment Choosing Schedule (1) Listen A Go to sleep after time t Listen for SYNC Sleep Broadcasts Listen B td Broadcasts Go to sleep after time t- td Sleep Synchronizer • Listen for a mount of time • If hear no SYNC, select its own SYNC • Broadcasts its SYNC immediately Follower • Listen for a mount of time • Hear SYNC from A, follow A’s SYNC • Rebroadcasts SYNC after random delay td 48 48
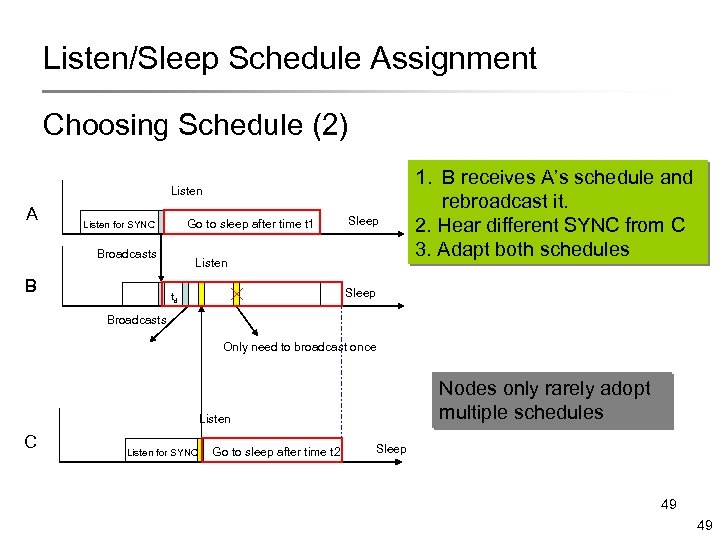 Listen/Sleep Schedule Assignment Choosing Schedule (2) Listen A Go to sleep after time t 1 Listen for SYNC Broadcasts B Sleep Listen 1. B receives A’s schedule and rebroadcast it. 2. Hear different SYNC from C 3. Adapt both schedules Sleep td Broadcasts Only need to broadcast once Nodes only rarely adopt multiple schedules Listen C Listen for SYNC Go to sleep after time t 2 Sleep 49 49
Listen/Sleep Schedule Assignment Choosing Schedule (2) Listen A Go to sleep after time t 1 Listen for SYNC Broadcasts B Sleep Listen 1. B receives A’s schedule and rebroadcast it. 2. Hear different SYNC from C 3. Adapt both schedules Sleep td Broadcasts Only need to broadcast once Nodes only rarely adopt multiple schedules Listen C Listen for SYNC Go to sleep after time t 2 Sleep 49 49
 Keeping Clocks in SYNC packets must not collide § Reserve separate time window for SYNC transmission 50 50
Keeping Clocks in SYNC packets must not collide § Reserve separate time window for SYNC transmission 50 50
 (2) Collision Avoidance n Identical to 802. 11 § RTS/CTS § Virtual carrier sense (NAV) § Physical carrier sense 51 51
(2) Collision Avoidance n Identical to 802. 11 § RTS/CTS § Virtual carrier sense (NAV) § Physical carrier sense 51 51
 (3) Overhearing Avoidance Neighbors go to sleepon overhearing RTS/CTS A is talking to B D receives CTS from B -> sleep • D’s transmission will collide B’s C receives RTS from A -> sleep • C cannot receive CTS/DATA from E All immediate neighbours of transmitting node sleep How long should they sleep? C and D update their NAV Keeping sleeping until NAV count down to zero 52 52
(3) Overhearing Avoidance Neighbors go to sleepon overhearing RTS/CTS A is talking to B D receives CTS from B -> sleep • D’s transmission will collide B’s C receives RTS from A -> sleep • C cannot receive CTS/DATA from E All immediate neighbours of transmitting node sleep How long should they sleep? C and D update their NAV Keeping sleeping until NAV count down to zero 52 52
 (4) Message Passing n How to transmit long message? § § Transmitting one long message is inefficient Many small packets with RTS/CTS/ACK for each n S-MAC: Divide into fragments, transmit in burst § § • RTS/CTS reserve medium for the entire sequence Fragment-errors recovery with ACK no control packets for fragments 53 53
(4) Message Passing n How to transmit long message? § § Transmitting one long message is inefficient Many small packets with RTS/CTS/ACK for each n S-MAC: Divide into fragments, transmit in burst § § • RTS/CTS reserve medium for the entire sequence Fragment-errors recovery with ACK no control packets for fragments 53 53
 Acknowledgment to Pro. Jun Yang Neighbors can sleep for whole message 54 54
Acknowledgment to Pro. Jun Yang Neighbors can sleep for whole message 54 54
 Message Passing Advantages: n Energy saving: § Neighbors go to sleep when sense transmissions § Reduces control overhead by sending multiple ACK Disadvantage: n Node-to-node fairness reduces However, message-level latency reduces 55 55
Message Passing Advantages: n Energy saving: § Neighbors go to sleep when sense transmissions § Reduces control overhead by sending multiple ACK Disadvantage: n Node-to-node fairness reduces However, message-level latency reduces 55 55
 Experiment Listen time: 300 ms Sleeping time: 1 s SYNC: every 13 s (10 listen/sleep period) A, B, C use the same schedule 56 56
Experiment Listen time: 300 ms Sleeping time: 1 s SYNC: every 13 s (10 listen/sleep period) A, B, C use the same schedule 56 56
 Energy save due to 802. 11 periodic sleep Energy save due to avoiding overhearing by using message passing OA SMAC Heavy Traffic Light Traffic 57 57
Energy save due to 802. 11 periodic sleep Energy save due to avoiding overhearing by using message passing OA SMAC Heavy Traffic Light Traffic 57 57
 OA: In light traffic status, nodes keep listening for quite a long time 58 58
OA: In light traffic status, nodes keep listening for quite a long time 58 58
 SYNC overhead Overhearing avoidance still benefit Heavy Traffic Light Traffic 59 59
SYNC overhead Overhearing avoidance still benefit Heavy Traffic Light Traffic 59 59
 Questions? 60 60
Questions? 60 60
 Studied MAC protocols till now Another important challenge: How does a packet get transported end to end i. e. , How do you perform Routing 61 61
Studied MAC protocols till now Another important challenge: How does a packet get transported end to end i. e. , How do you perform Routing 61 61
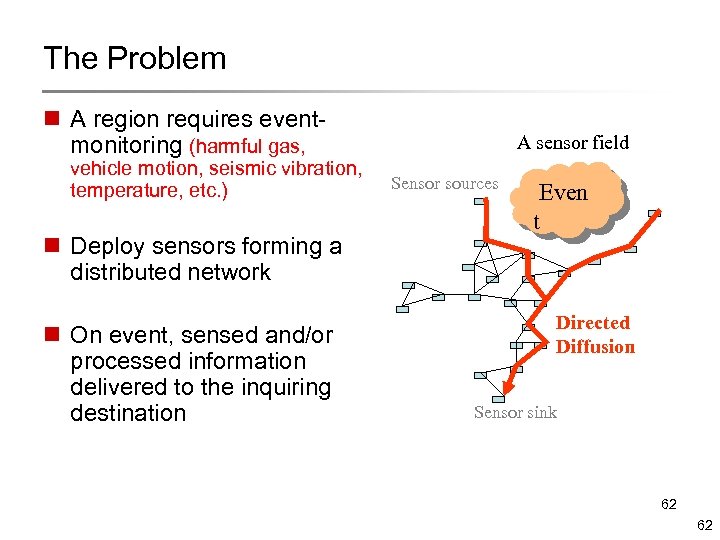 The Problem n A region requires eventmonitoring (harmful gas, vehicle motion, seismic vibration, temperature, etc. ) n Deploy sensors forming a distributed network n On event, sensed and/or processed information delivered to the inquiring destination A sensor field Sensor sources Even t Directed Diffusion Sensor sink 62 62
The Problem n A region requires eventmonitoring (harmful gas, vehicle motion, seismic vibration, temperature, etc. ) n Deploy sensors forming a distributed network n On event, sensed and/or processed information delivered to the inquiring destination A sensor field Sensor sources Even t Directed Diffusion Sensor sink 62 62
 Directed Diffusion 63 63
Directed Diffusion 63 63
 The Proposal n Proposes an application-aware paradigm to facilitate efficient aggregation, and delivery of sensed data to inquiring destination n Challenges: § § Scalability Energy efficiency Robustness / Fault tolerance in outdoor areas Efficient routing (multiple source destination pairs) 64 64
The Proposal n Proposes an application-aware paradigm to facilitate efficient aggregation, and delivery of sensed data to inquiring destination n Challenges: § § Scalability Energy efficiency Robustness / Fault tolerance in outdoor areas Efficient routing (multiple source destination pairs) 64 64
 IP or not to IP n IP is the pivot of wired/wireless networks § All networking protocol over and below IP n Should we stick to this model? Comments ? 65 65
IP or not to IP n IP is the pivot of wired/wireless networks § All networking protocol over and below IP n Should we stick to this model? Comments ? 65 65
 Directed Diffusion n Typical IP based networks § Requires unique host ID addressing § Application is end-to-end, routers unaware n Directed diffusion – uses publish/subscribe § Inquirer expresses an interest, I, using attribute values § Sensor sources that can service I, reply with data 66 66
Directed Diffusion n Typical IP based networks § Requires unique host ID addressing § Application is end-to-end, routers unaware n Directed diffusion – uses publish/subscribe § Inquirer expresses an interest, I, using attribute values § Sensor sources that can service I, reply with data 66 66
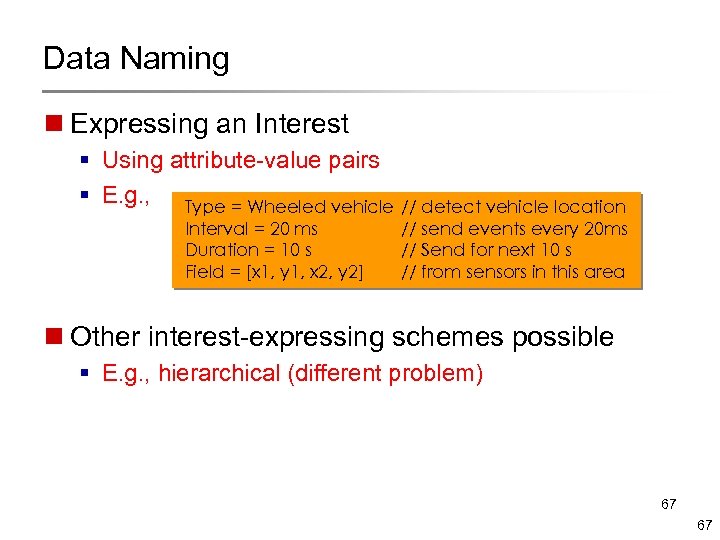 Data Naming n Expressing an Interest § Using attribute-value pairs § E. g. , Type = Wheeled vehicle // detect vehicle location Interval = 20 ms Duration = 10 s Field = [x 1, y 1, x 2, y 2] // send events every 20 ms // Send for next 10 s // from sensors in this area n Other interest-expressing schemes possible § E. g. , hierarchical (different problem) 67 67
Data Naming n Expressing an Interest § Using attribute-value pairs § E. g. , Type = Wheeled vehicle // detect vehicle location Interval = 20 ms Duration = 10 s Field = [x 1, y 1, x 2, y 2] // send events every 20 ms // Send for next 10 s // from sensors in this area n Other interest-expressing schemes possible § E. g. , hierarchical (different problem) 67 67
 Gradient Set Up n Inquirer (sink) broadcasts exploratory interest, i 1 § Intended to discover routes between source and sink n Neighbors update interest-cache and forwards i 1 n Gradient for i 1 set up to upstream neighbor § No source routes § Gradient – a weighted reverse link § Low gradient Few packets per unit time needed 68 68
Gradient Set Up n Inquirer (sink) broadcasts exploratory interest, i 1 § Intended to discover routes between source and sink n Neighbors update interest-cache and forwards i 1 n Gradient for i 1 set up to upstream neighbor § No source routes § Gradient – a weighted reverse link § Low gradient Few packets per unit time needed 68 68
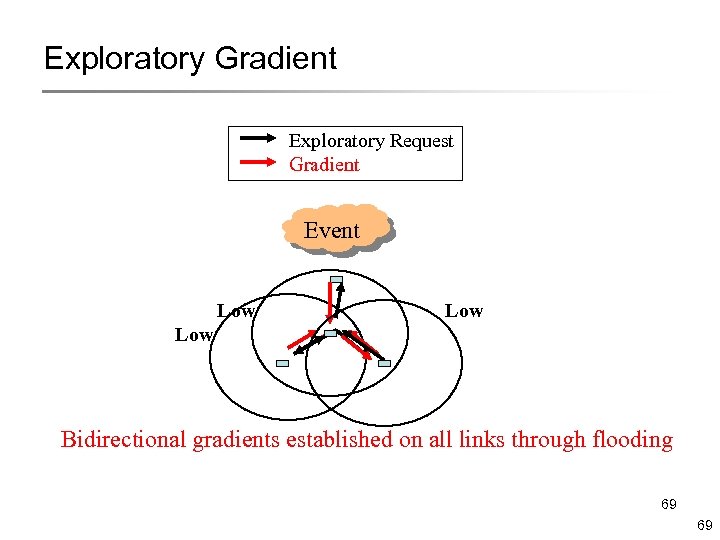 Exploratory Gradient Exploratory Request Gradient Event Low Low Bidirectional gradients established on all links through flooding 69 69
Exploratory Gradient Exploratory Request Gradient Event Low Low Bidirectional gradients established on all links through flooding 69 69
 Event-data propagation n Event e 1 occurs, matches i 1 in sensor cache § e 1 identified based on waveform pattern matching n Interest reply diffused down gradient (unicast) § Diffusion initially exploratory (low packet-rate) n Cache filters suppress previously seen data § Problem of bidirectional gradient avoided 70 70
Event-data propagation n Event e 1 occurs, matches i 1 in sensor cache § e 1 identified based on waveform pattern matching n Interest reply diffused down gradient (unicast) § Diffusion initially exploratory (low packet-rate) n Cache filters suppress previously seen data § Problem of bidirectional gradient avoided 70 70
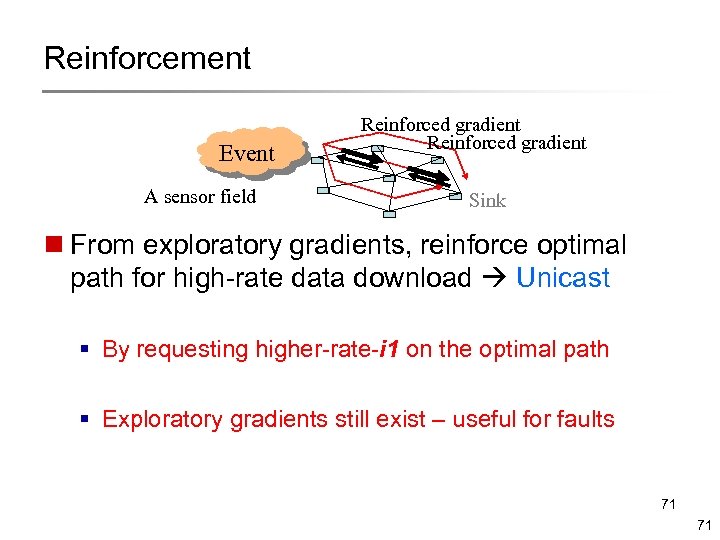 Reinforcement Event A sensor field Reinforced gradient Sink n From exploratory gradients, reinforce optimal path for high-rate data download Unicast § By requesting higher-rate-i 1 on the optimal path § Exploratory gradients still exist – useful for faults 71 71
Reinforcement Event A sensor field Reinforced gradient Sink n From exploratory gradients, reinforce optimal path for high-rate data download Unicast § By requesting higher-rate-i 1 on the optimal path § Exploratory gradients still exist – useful for faults 71 71
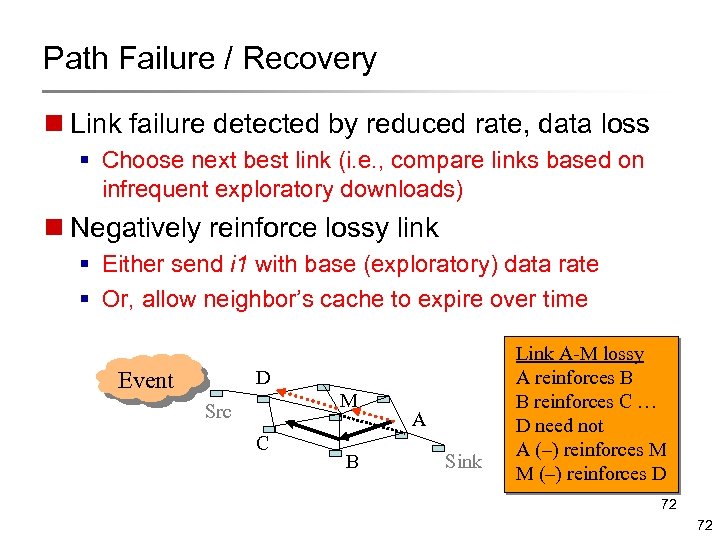 Path Failure / Recovery n Link failure detected by reduced rate, data loss § Choose next best link (i. e. , compare links based on infrequent exploratory downloads) n Negatively reinforce lossy link § Either send i 1 with base (exploratory) data rate § Or, allow neighbor’s cache to expire over time D Event M Src C B A Sink Link A-M lossy A reinforces B B reinforces C … D need not A (–) reinforces M M (–) reinforces D 72 72
Path Failure / Recovery n Link failure detected by reduced rate, data loss § Choose next best link (i. e. , compare links based on infrequent exploratory downloads) n Negatively reinforce lossy link § Either send i 1 with base (exploratory) data rate § Or, allow neighbor’s cache to expire over time D Event M Src C B A Sink Link A-M lossy A reinforces B B reinforces C … D need not A (–) reinforces M M (–) reinforces D 72 72
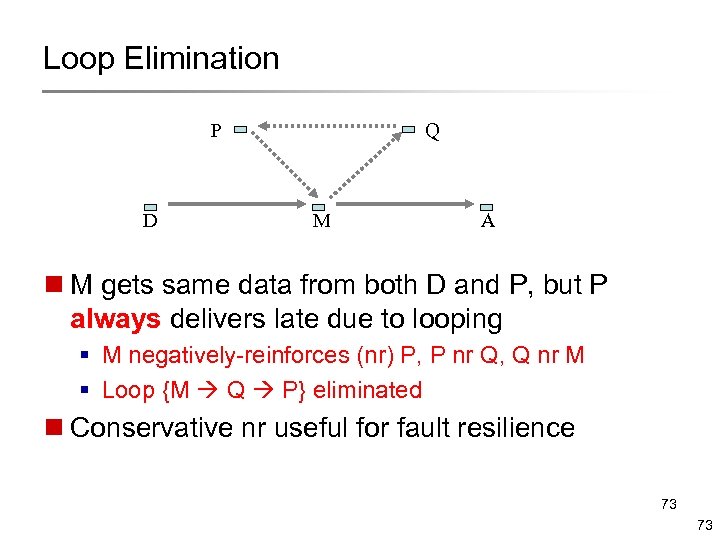 Loop Elimination P D Q M A n M gets same data from both D and P, but P always delivers late due to looping § M negatively-reinforces (nr) P, P nr Q, Q nr M § Loop {M Q P} eliminated n Conservative nr useful for fault resilience 73 73
Loop Elimination P D Q M A n M gets same data from both D and P, but P always delivers late due to looping § M negatively-reinforces (nr) P, P nr Q, Q nr M § Loop {M Q P} eliminated n Conservative nr useful for fault resilience 73 73
 Simulation Setup & Metrics n ns 2, 50 nodes in 160 x 160 sqm. , range 40 m § Node density maintained, 802. 11 MAC n Random 5 sources in 70 x 70, random 5 sinks n Average Dissipated Energy § Per node energy dissipation / # events seen by sinks n Average Delay § Latency of event transmission to reception at sink n Distinct event delivery ratio § Ratio of # events sent to # events received by sink 74 74
Simulation Setup & Metrics n ns 2, 50 nodes in 160 x 160 sqm. , range 40 m § Node density maintained, 802. 11 MAC n Random 5 sources in 70 x 70, random 5 sinks n Average Dissipated Energy § Per node energy dissipation / # events seen by sinks n Average Delay § Latency of event transmission to reception at sink n Distinct event delivery ratio § Ratio of # events sent to # events received by sink 74 74
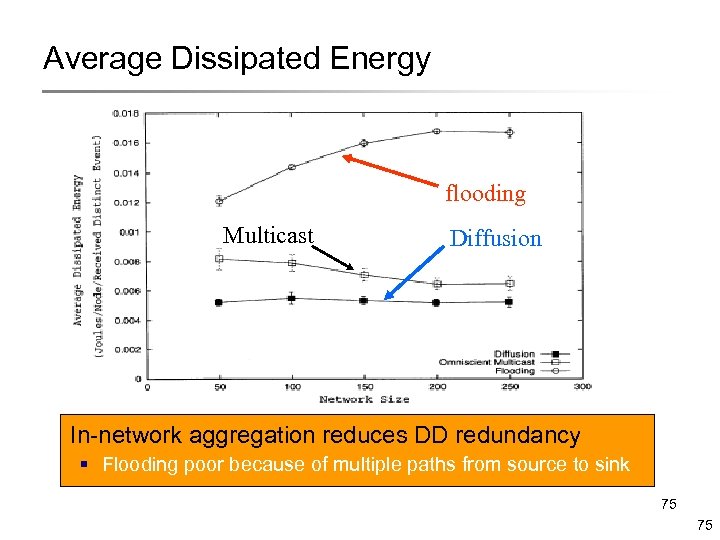 Average Dissipated Energy flooding Multicast Diffusion In-network aggregation reduces DD redundancy § Flooding poor because of multiple paths from source to sink 75 75
Average Dissipated Energy flooding Multicast Diffusion In-network aggregation reduces DD redundancy § Flooding poor because of multiple paths from source to sink 75 75
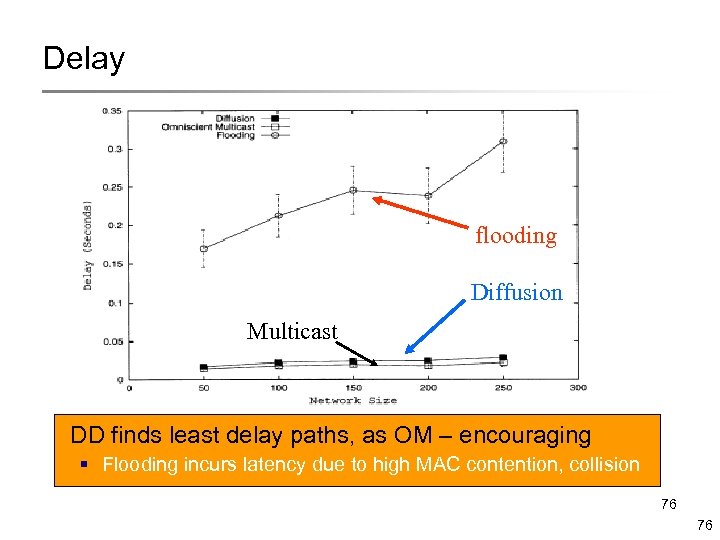 Delay flooding Diffusion Multicast DD finds least delay paths, as OM – encouraging § Flooding incurs latency due to high MAC contention, collision 76 76
Delay flooding Diffusion Multicast DD finds least delay paths, as OM – encouraging § Flooding incurs latency due to high MAC contention, collision 76 76
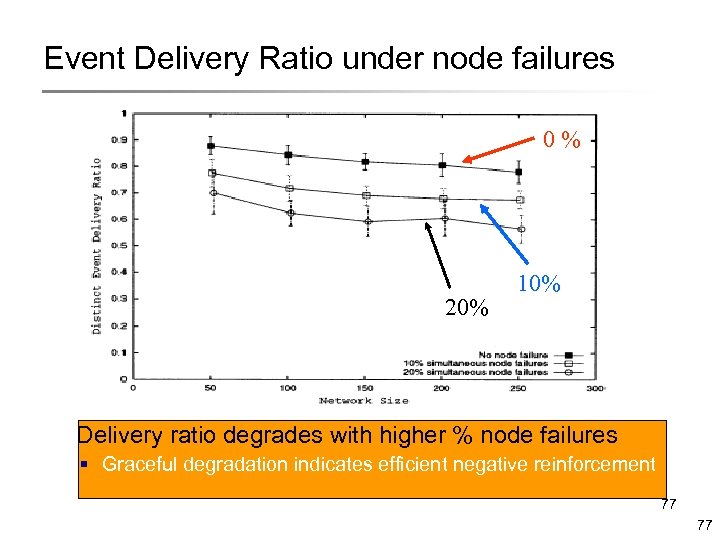 Event Delivery Ratio under node failures 0% 20% 10% Delivery ratio degrades with higher % node failures § Graceful degradation indicates efficient negative reinforcement 77 77
Event Delivery Ratio under node failures 0% 20% 10% Delivery ratio degrades with higher % node failures § Graceful degradation indicates efficient negative reinforcement 77 77
 Conclusion n Directed diffusion, a paradigm proposed for event monitoring sensor networks n Energy efficiency achievable n Diffusion mechanism resilient to fault tolerance § Conservative negative reinforcements proves useful n A careful MAC protocol, designed for such specifics, can yield further performance gains 78 78
Conclusion n Directed diffusion, a paradigm proposed for event monitoring sensor networks n Energy efficiency achievable n Diffusion mechanism resilient to fault tolerance § Conservative negative reinforcements proves useful n A careful MAC protocol, designed for such specifics, can yield further performance gains 78 78
 Rumor Routing LEACH SPIN Some other proposals for sensor routing 79 79
Rumor Routing LEACH SPIN Some other proposals for sensor routing 79 79
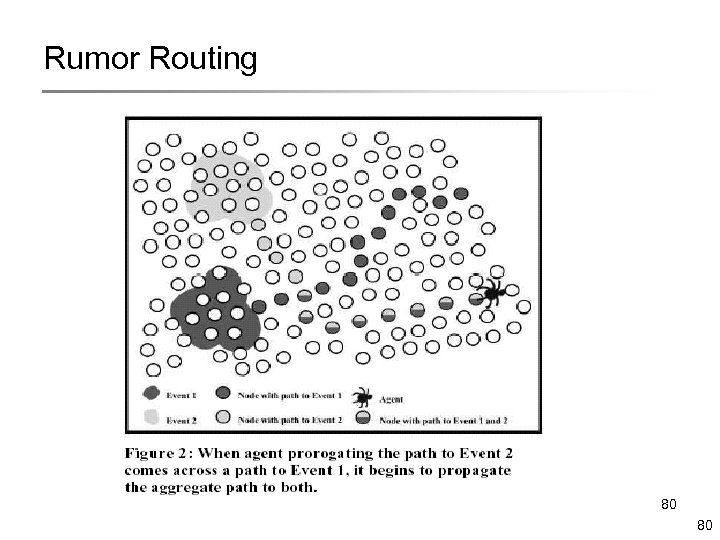 Rumor Routing 80 80
Rumor Routing 80 80
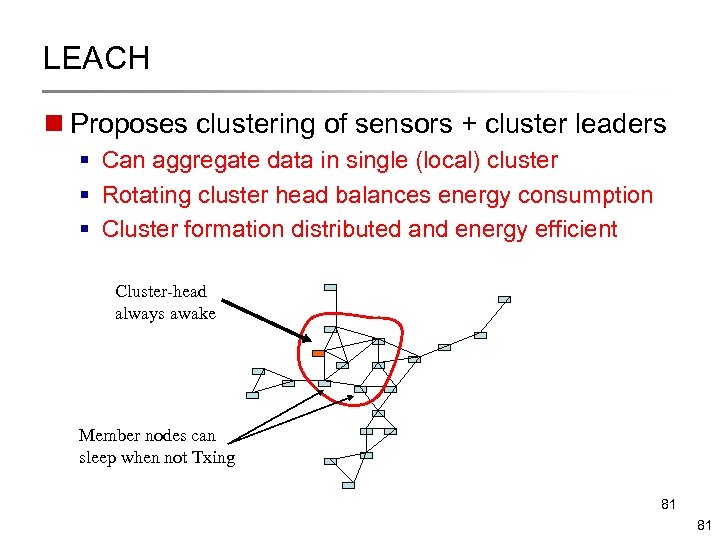 LEACH n Proposes clustering of sensors + cluster leaders § Can aggregate data in single (local) cluster § Rotating cluster head balances energy consumption § Cluster formation distributed and energy efficient Cluster-head always awake Member nodes can sleep when not Txing 81 81
LEACH n Proposes clustering of sensors + cluster leaders § Can aggregate data in single (local) cluster § Rotating cluster head balances energy consumption § Cluster formation distributed and energy efficient Cluster-head always awake Member nodes can sleep when not Txing 81 81
 LEACH – The Protocol n Time is divided into rounds n A node self-elects itself as the cluster head § § § Higher residual energy, higher probability to be head Close-by sensors join this cluster-head Cluster head does TDMA scheduling and gathers data Gathered data compressed based on spatial correlation Transmits data to Base Station (@ higher power) n In the next round, another cluster head elected § Probabilistic load balancing § Network lifetime can increase manifolds 82 82
LEACH – The Protocol n Time is divided into rounds n A node self-elects itself as the cluster head § § § Higher residual energy, higher probability to be head Close-by sensors join this cluster-head Cluster head does TDMA scheduling and gathers data Gathered data compressed based on spatial correlation Transmits data to Base Station (@ higher power) n In the next round, another cluster head elected § Probabilistic load balancing § Network lifetime can increase manifolds 82 82
 SPIN: Information Via Negotiation n Flooding many sensors transmit same data § Redundant n Make sensors disseminate spatially/temporally disjoint data sets § Name data with meta-data to define space/time property § Sensors compare overheard data with self-sensed data § Combine data to minimize overlap n Make sensors resource-adaptive § When low battery perform minimum activities 83 83
SPIN: Information Via Negotiation n Flooding many sensors transmit same data § Redundant n Make sensors disseminate spatially/temporally disjoint data sets § Name data with meta-data to define space/time property § Sensors compare overheard data with self-sensed data § Combine data to minimize overlap n Make sensors resource-adaptive § When low battery perform minimum activities 83 83
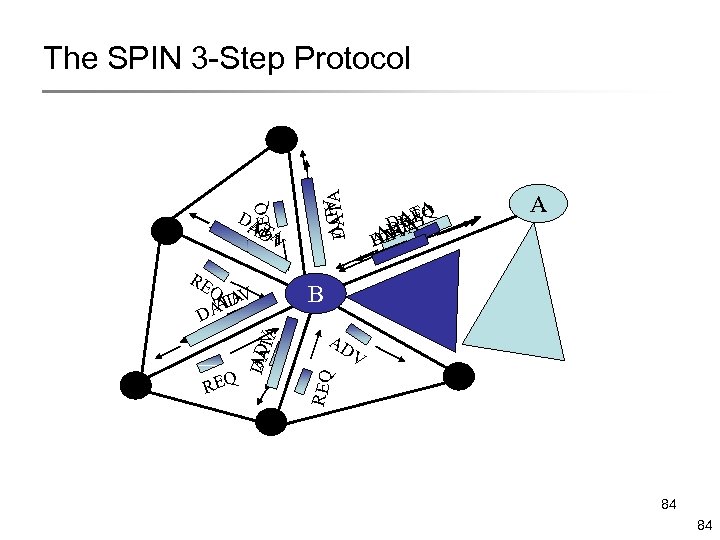 RE REQ AD DAT V A Q V A AD AT D DATA R Q DTEE VQ R AD A AA V DD A B AD V REQ DA AT DV A ADV REQ The SPIN 3 -Step Protocol 84 84
RE REQ AD DAT V A Q V A AD AT D DATA R Q DTEE VQ R AD A AA V DD A B AD V REQ DA AT DV A ADV REQ The SPIN 3 -Step Protocol 84 84
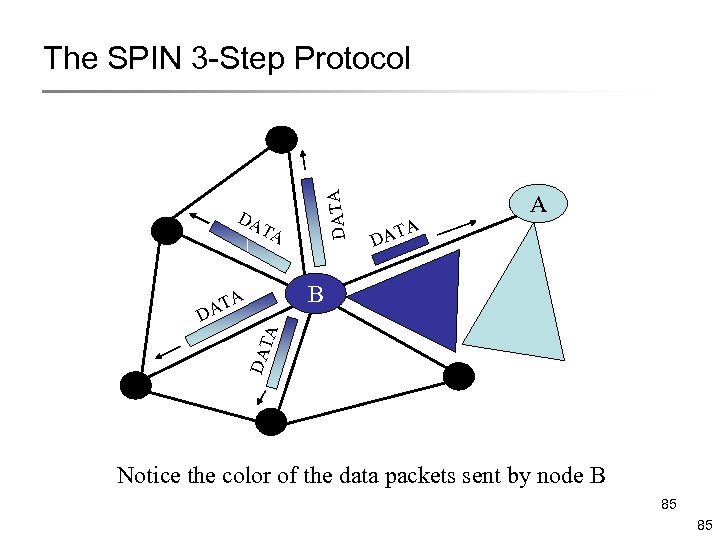 DATA The SPIN 3 -Step Protocol DA TA A DA TA B A DAT A T DA Notice the color of the data packets sent by node B 85 85
DATA The SPIN 3 -Step Protocol DA TA A DA TA B A DAT A T DA Notice the color of the data packets sent by node B 85 85
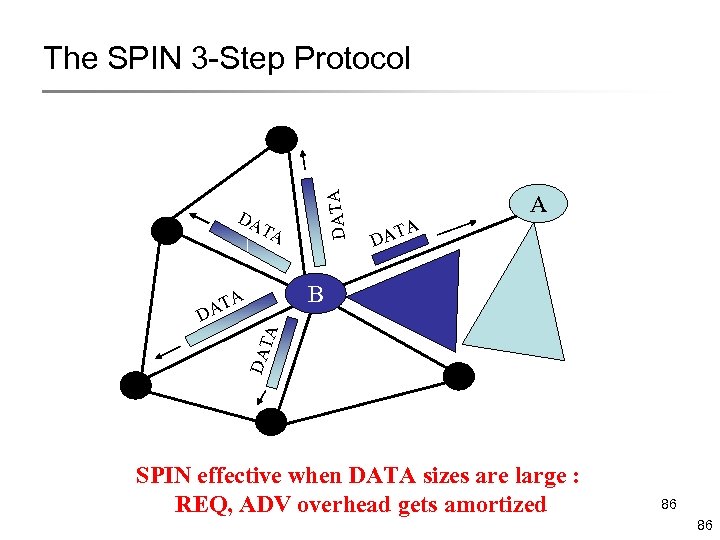 DATA The SPIN 3 -Step Protocol DA TA A DA TA B A DAT A T DA SPIN effective when DATA sizes are large : REQ, ADV overhead gets amortized 86 86
DATA The SPIN 3 -Step Protocol DA TA A DA TA B A DAT A T DA SPIN effective when DATA sizes are large : REQ, ADV overhead gets amortized 86 86
 Smart. Gossip: A Reliable Broadcast Service for Wireless Sensor Networks Romit Roy Choudhury Dept. of ECE, Duke University Joint work with Pradeep Kyasanur (Google) Indranil Gupta (UIUC) 87 87
Smart. Gossip: A Reliable Broadcast Service for Wireless Sensor Networks Romit Roy Choudhury Dept. of ECE, Duke University Joint work with Pradeep Kyasanur (Google) Indranil Gupta (UIUC) 87 87
 Problem n Broadcast in Sensor Networks § A widely used service § Network layer functions heavily depend on it § Examples: • Directed Diffusion • Unicast or multicast routing • Instruction / code dissemination • Query propagation 88 88
Problem n Broadcast in Sensor Networks § A widely used service § Network layer functions heavily depend on it § Examples: • Directed Diffusion • Unicast or multicast routing • Instruction / code dissemination • Query propagation 88 88
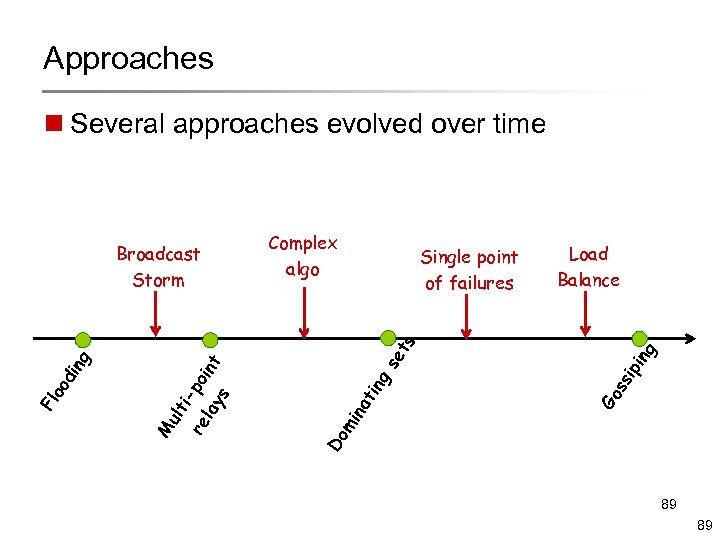 Approaches n Several approaches evolved over time Complex algo Single point of failures Load Balance ng sip i Go s se t g tin Do mi na i re -poi lay nt s ult M Fl oo di ng s Broadcast Storm 89 89
Approaches n Several approaches evolved over time Complex algo Single point of failures Load Balance ng sip i Go s se t g tin Do mi na i re -poi lay nt s ult M Fl oo di ng s Broadcast Storm 89 89
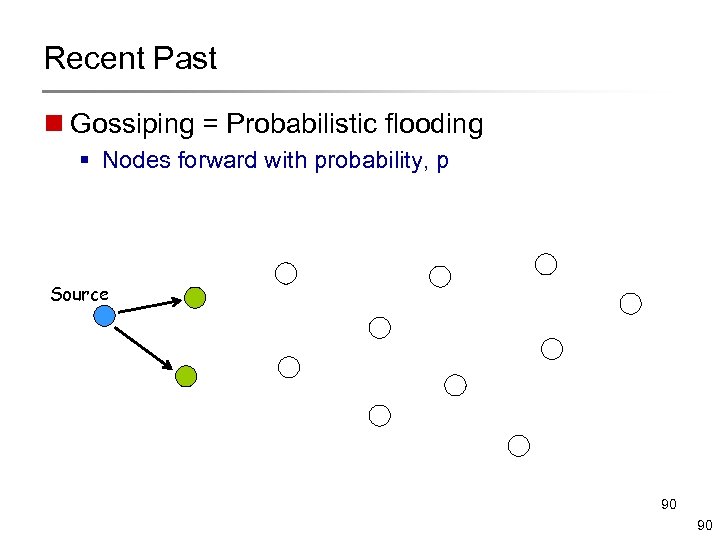 Recent Past n Gossiping = Probabilistic flooding § Nodes forward with probability, p Source 90 90
Recent Past n Gossiping = Probabilistic flooding § Nodes forward with probability, p Source 90 90
 Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads 91 91
Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads 91 91
 Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads 92 92
Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads 92 92
 Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads 93 93
Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads 93 93
 Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads 94 94
Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads 94 94
 Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads Tails 95 95
Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads Tails 95 95
 Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads Tails 96 96
Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads Tails 96 96
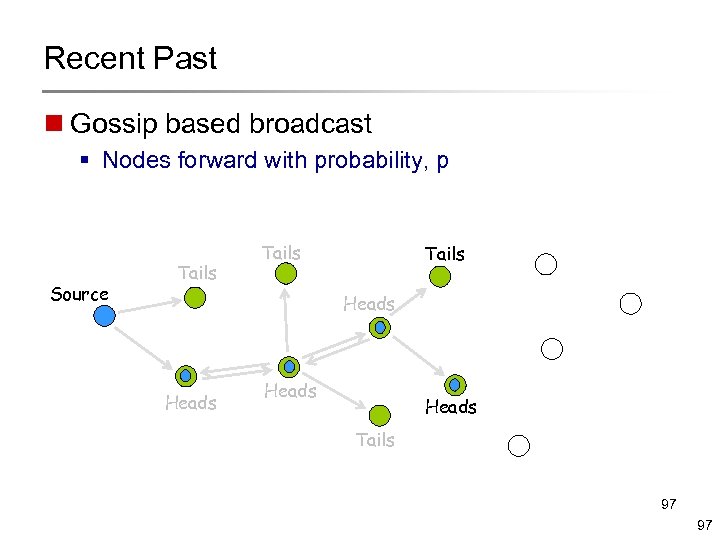 Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads Tails 97 97
Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads Tails 97 97
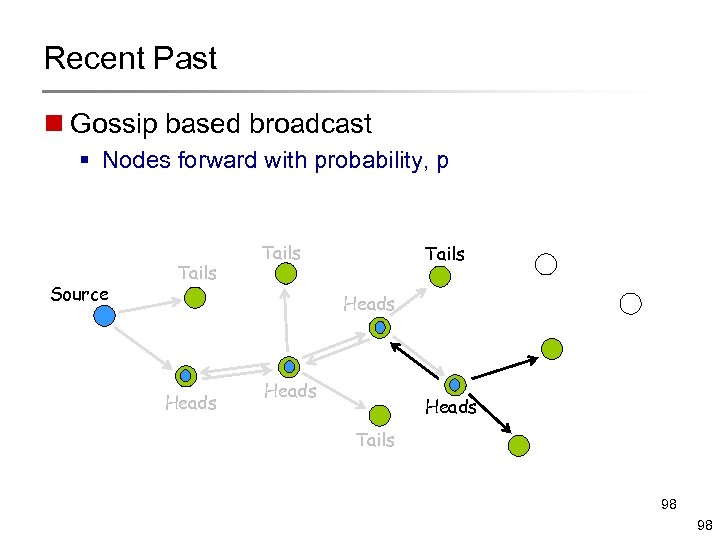 Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads Tails 98 98
Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads Tails 98 98
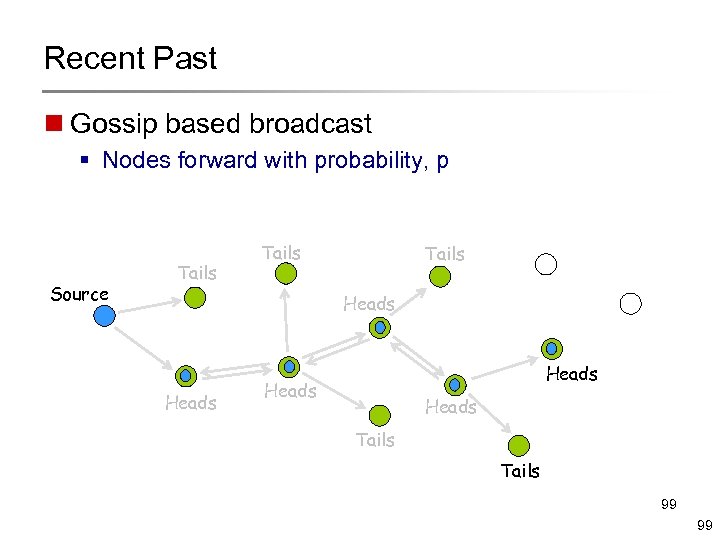 Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads Heads Tails 99 99
Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads Heads Tails 99 99
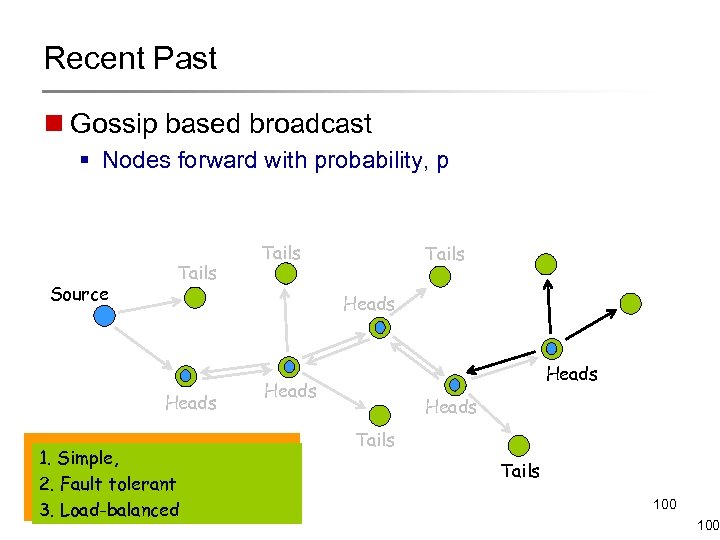 Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads For carefully chosen ‘p’ 1. Simple, the. Fault tolerant 2. message reaches all nodes in minimal transmissions 3. Load-balanced Heads Tails 100
Recent Past n Gossip based broadcast § Nodes forward with probability, p Source Tails Heads For carefully chosen ‘p’ 1. Simple, the. Fault tolerant 2. message reaches all nodes in minimal transmissions 3. Load-balanced Heads Tails 100
 We Ask … n Given some topology deployment § How do we choose a suitable value of “p” ? But, for is to simulate One option this example, simulation result will be the gossip offline, p=1 and determine “p” 101
We Ask … n Given some topology deployment § How do we choose a suitable value of “p” ? But, for is to simulate One option this example, simulation result will be the gossip offline, p=1 and determine “p” 101
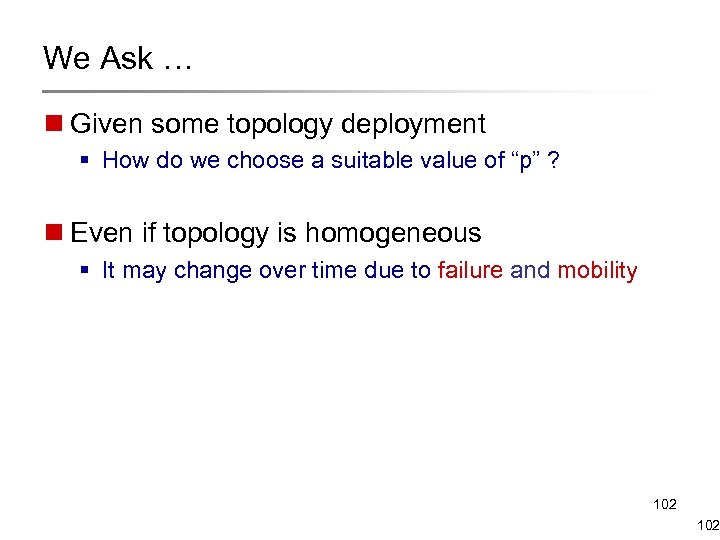 We Ask … n Given some topology deployment § How do we choose a suitable value of “p” ? n Even if topology is homogeneous § It may change over time due to failure and mobility 102
We Ask … n Given some topology deployment § How do we choose a suitable value of “p” ? n Even if topology is homogeneous § It may change over time due to failure and mobility 102
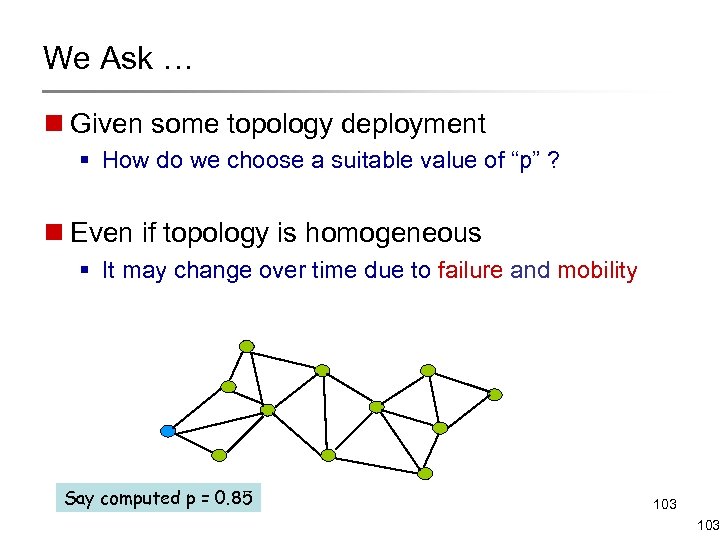 We Ask … n Given some topology deployment § How do we choose a suitable value of “p” ? n Even if topology is homogeneous § It may change over time due to failure and mobility Say computed p = 0. 85 103
We Ask … n Given some topology deployment § How do we choose a suitable value of “p” ? n Even if topology is homogeneous § It may change over time due to failure and mobility Say computed p = 0. 85 103
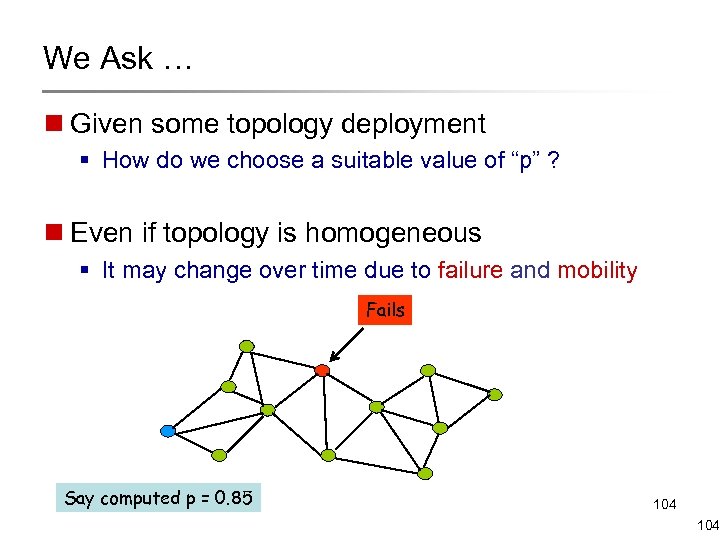 We Ask … n Given some topology deployment § How do we choose a suitable value of “p” ? n Even if topology is homogeneous § It may change over time due to failure and mobility Fails Say computed p = 0. 85 104
We Ask … n Given some topology deployment § How do we choose a suitable value of “p” ? n Even if topology is homogeneous § It may change over time due to failure and mobility Fails Say computed p = 0. 85 104
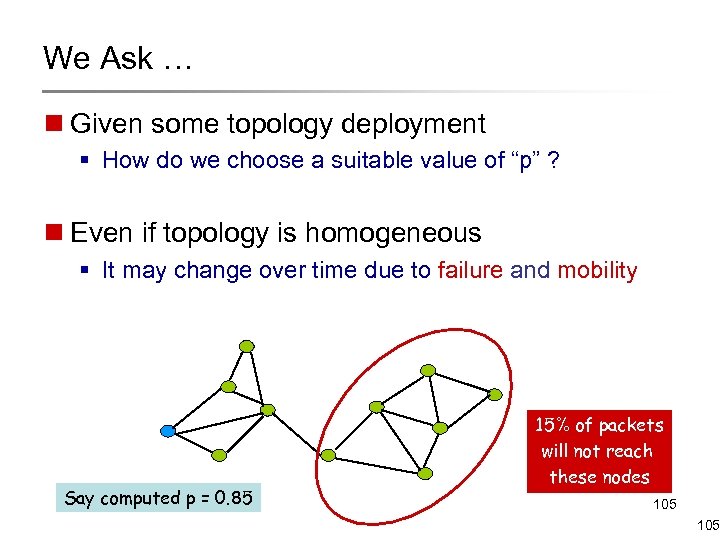 We Ask … n Given some topology deployment § How do we choose a suitable value of “p” ? n Even if topology is homogeneous § It may change over time due to failure and mobility Say computed p = 0. 85 15% of packets will not reach these nodes 105
We Ask … n Given some topology deployment § How do we choose a suitable value of “p” ? n Even if topology is homogeneous § It may change over time due to failure and mobility Say computed p = 0. 85 15% of packets will not reach these nodes 105
 We Ask … n Given some topology deployment § How do we choose a suitable value of “p” ? n Even if topology is homogeneous § It may change over time due to failure and mobility n Finally, what if topology is not known a priori ? § How can you choose “p” ? 106
We Ask … n Given some topology deployment § How do we choose a suitable value of “p” ? n Even if topology is homogeneous § It may change over time due to failure and mobility n Finally, what if topology is not known a priori ? § How can you choose “p” ? 106
 We Argue … A broadcast service necessary that customizes itself to the underlying topology and repairs itself with failures and mobility 107
We Argue … A broadcast service necessary that customizes itself to the underlying topology and repairs itself with failures and mobility 107
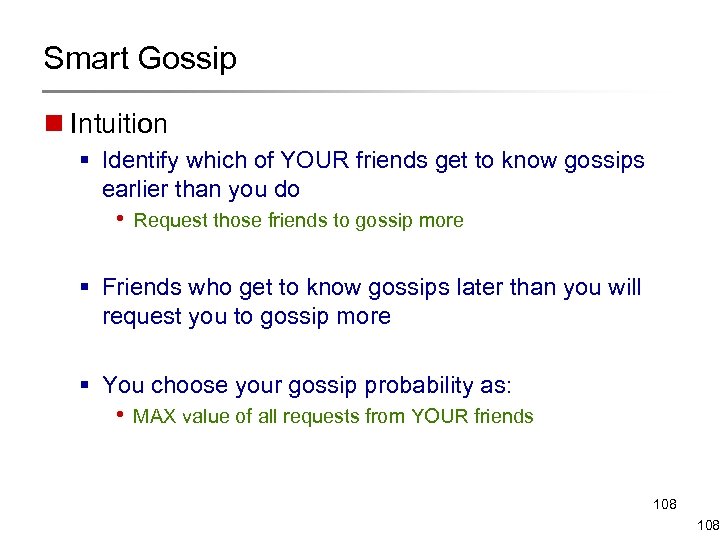 Smart Gossip n Intuition § Identify which of YOUR friends get to know gossips earlier than you do • Request those friends to gossip more § Friends who get to know gossips later than you will request you to gossip more § You choose your gossip probability as: • MAX value of all requests from YOUR friends 108
Smart Gossip n Intuition § Identify which of YOUR friends get to know gossips earlier than you do • Request those friends to gossip more § Friends who get to know gossips later than you will request you to gossip more § You choose your gossip probability as: • MAX value of all requests from YOUR friends 108
 For Example … n When H spreads a gossip § F gets gossip only from G § F asks G to always gossip § Thus, p. G = 1. 0 § B receives gossip from A, C, D, E, F § B also observes that A, C, D, E received gossip from F • Indicates that B must depend only on F (parent) • A, C, D, E and B are independent (siblings) § B asks F to always gossip, thus p. F = 1. 0 109
For Example … n When H spreads a gossip § F gets gossip only from G § F asks G to always gossip § Thus, p. G = 1. 0 § B receives gossip from A, C, D, E, F § B also observes that A, C, D, E received gossip from F • Indicates that B must depend only on F (parent) • A, C, D, E and B are independent (siblings) § B asks F to always gossip, thus p. F = 1. 0 109
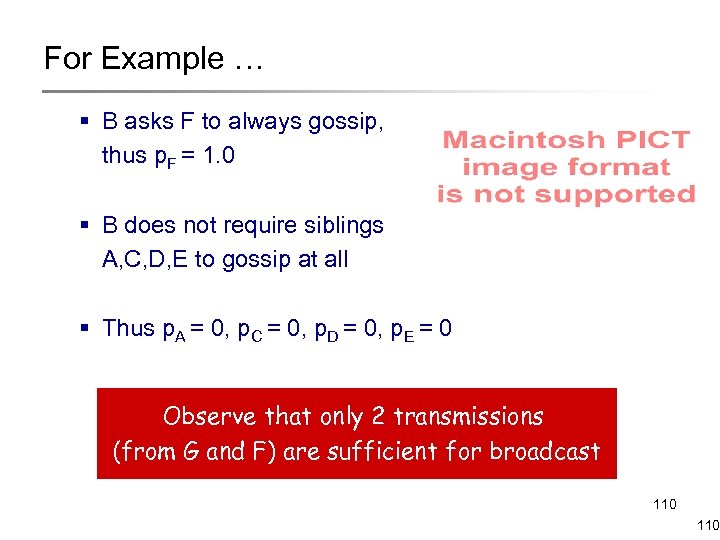 For Example … § B asks F to always gossip, thus p. F = 1. 0 § B does not require siblings A, C, D, E to gossip at all § Thus p. A = 0, p. C = 0, p. D = 0, p. E = 0 Observe that only 2 transmissions (from G and F) are sufficient for broadcast 110
For Example … § B asks F to always gossip, thus p. F = 1. 0 § B does not require siblings A, C, D, E to gossip at all § Thus p. A = 0, p. C = 0, p. D = 0, p. E = 0 Observe that only 2 transmissions (from G and F) are sufficient for broadcast 110
 Protocol Details n For first gossip pkt, nodes transmit with p=1 § Enables nodes to deduce neighbor dependences § Transmitters piggyback pkt with parent-id from which it received the pkt § Nodes record transmitter-id, and its parent-id, and deduce parent, child, sibling relationships … … see next slide 111
Protocol Details n For first gossip pkt, nodes transmit with p=1 § Enables nodes to deduce neighbor dependences § Transmitters piggyback pkt with parent-id from which it received the pkt § Nodes record transmitter-id, and its parent-id, and deduce parent, child, sibling relationships … … see next slide 111
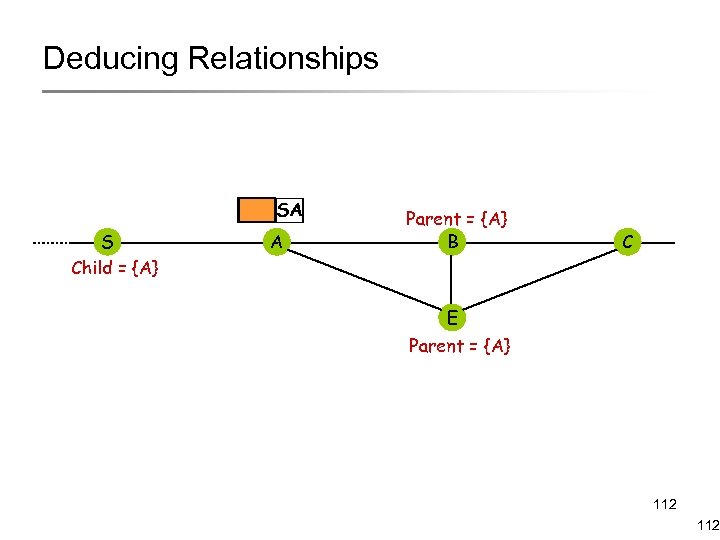 Deducing Relationships SA S Child = {A} A Parent = {A} B C E Parent = {A} 112
Deducing Relationships SA S Child = {A} A Parent = {A} B C E Parent = {A} 112
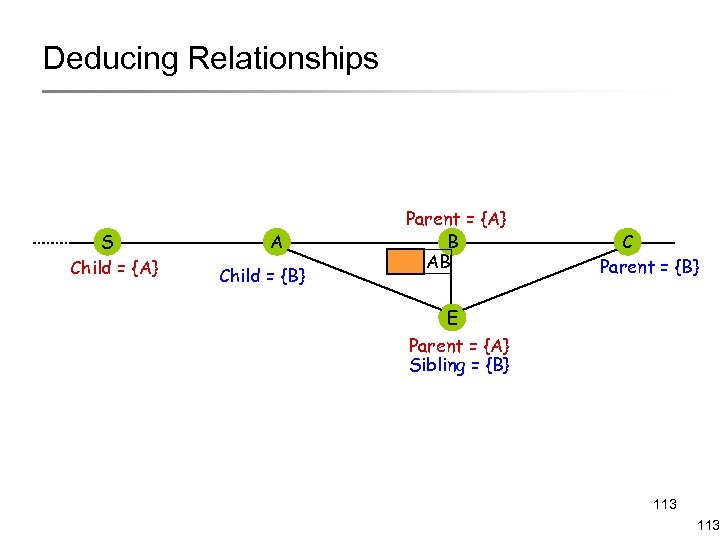 Deducing Relationships S Child = {A} A Child = {B} Parent = {A} B AB C Parent = {B} E Parent = {A} Sibling = {B} 113
Deducing Relationships S Child = {A} A Child = {B} Parent = {A} B AB C Parent = {B} E Parent = {A} Sibling = {B} 113
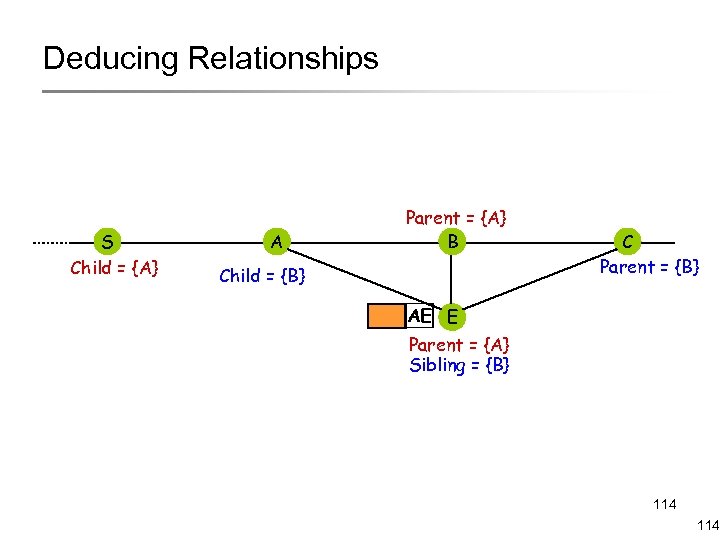 Deducing Relationships S Child = {A} A Parent = {A} B Child = {B} C Parent = {B} AE E Parent = {A} Sibling = {B} 114
Deducing Relationships S Child = {A} A Parent = {A} B Child = {B} C Parent = {B} AE E Parent = {A} Sibling = {B} 114
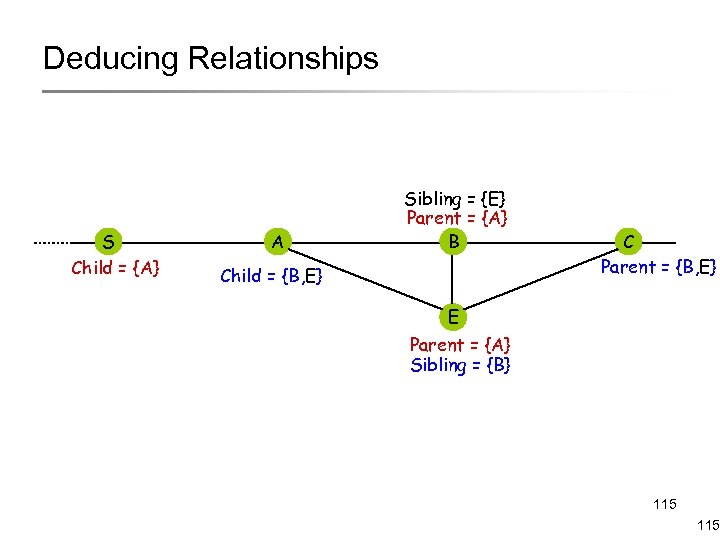 Deducing Relationships S Child = {A} A Sibling = {E} Parent = {A} B Child = {B, E} C Parent = {B, E} E Parent = {A} Sibling = {B} 115
Deducing Relationships S Child = {A} A Sibling = {E} Parent = {A} B Child = {B, E} C Parent = {B, E} E Parent = {A} Sibling = {B} 115
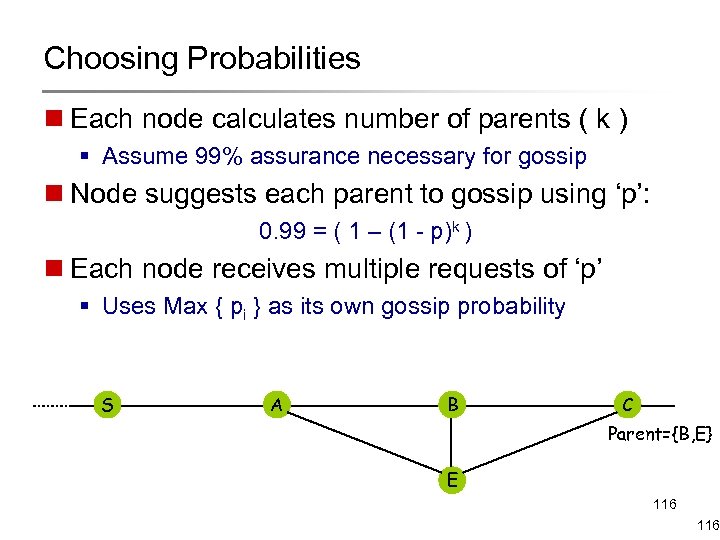 Choosing Probabilities n Each node calculates number of parents ( k ) § Assume 99% assurance necessary for gossip n Node suggests each parent to gossip using ‘p’: 0. 99 = ( 1 – (1 - p)k ) n Each node receives multiple requests of ‘p’ § Uses Max { pi } as its own gossip probability S A B C Parent={B, E} E 116
Choosing Probabilities n Each node calculates number of parents ( k ) § Assume 99% assurance necessary for gossip n Node suggests each parent to gossip using ‘p’: 0. 99 = ( 1 – (1 - p)k ) n Each node receives multiple requests of ‘p’ § Uses Max { pi } as its own gossip probability S A B C Parent={B, E} E 116
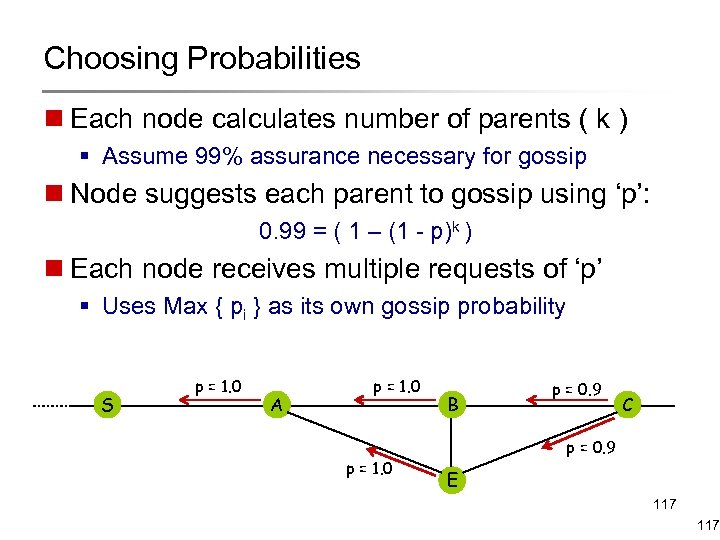 Choosing Probabilities n Each node calculates number of parents ( k ) § Assume 99% assurance necessary for gossip n Node suggests each parent to gossip using ‘p’: 0. 99 = ( 1 – (1 - p)k ) n Each node receives multiple requests of ‘p’ § Uses Max { pi } as its own gossip probability S p = 1. 0 A p = 1. 0 B p = 0. 9 C p = 0. 9 E 117
Choosing Probabilities n Each node calculates number of parents ( k ) § Assume 99% assurance necessary for gossip n Node suggests each parent to gossip using ‘p’: 0. 99 = ( 1 – (1 - p)k ) n Each node receives multiple requests of ‘p’ § Uses Max { pi } as its own gossip probability S p = 1. 0 A p = 1. 0 B p = 0. 9 C p = 0. 9 E 117
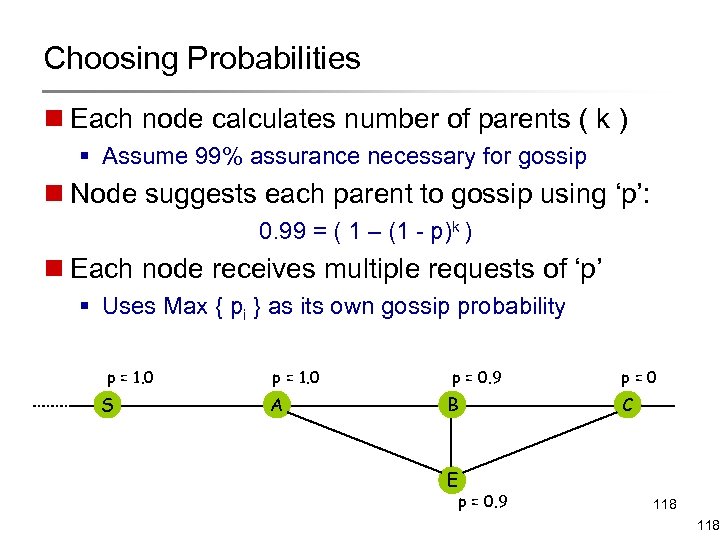 Choosing Probabilities n Each node calculates number of parents ( k ) § Assume 99% assurance necessary for gossip n Node suggests each parent to gossip using ‘p’: 0. 99 = ( 1 – (1 - p)k ) n Each node receives multiple requests of ‘p’ § Uses Max { pi } as its own gossip probability p = 1. 0 S p = 1. 0 A p = 0. 9 B E p=0 C p = 0. 9 118
Choosing Probabilities n Each node calculates number of parents ( k ) § Assume 99% assurance necessary for gossip n Node suggests each parent to gossip using ‘p’: 0. 99 = ( 1 – (1 - p)k ) n Each node receives multiple requests of ‘p’ § Uses Max { pi } as its own gossip probability p = 1. 0 S p = 1. 0 A p = 0. 9 B E p=0 C p = 0. 9 118
 The Bigger Picture Src 119
The Bigger Picture Src 119
 Reliability (Details in paper) n Node Failures § Node failures affect broadcast § Source node flags packet periodically (p=1) § Allows for updating dependences n Link Losses § Node requests upstream nodes to retransmit • We require each node to buffer few packets § Children overhear this request § Children do not request retransmissions themselves 120
Reliability (Details in paper) n Node Failures § Node failures affect broadcast § Source node flags packet periodically (p=1) § Allows for updating dependences n Link Losses § Node requests upstream nodes to retransmit • We require each node to buffer few packets § Children overhear this request § Children do not request retransmissions themselves 120
 Evaluation n Qualnet Simulator, ver 3. 7 (Currently implementing on Moteiv tmotes + Tiny. OS) n Metrics used § Average Reception Percentage § Average Forwarding Percentage § Resilience to link/node failures 121
Evaluation n Qualnet Simulator, ver 3. 7 (Currently implementing on Moteiv tmotes + Tiny. OS) n Metrics used § Average Reception Percentage § Average Forwarding Percentage § Resilience to link/node failures 121
 Percolation Smart Gossip Adaptive Overhead Adaptive Neighbor 122
Percolation Smart Gossip Adaptive Overhead Adaptive Neighbor 122
 Forwarding Overhead 123
Forwarding Overhead 123
 Adaption to Node Failures Nodes gossip more to compensate for other failing nodes 124
Adaption to Node Failures Nodes gossip more to compensate for other failing nodes 124
 Conclusion n Broadcast is an important problem § Gossip is good – but not practical for sensor nets § Need to adapt gossip based on topology / failures n Smart Gossip § Form dependence graphs using distributed protocol § Dependence relations suggest suitable probability n Results § Overheads are low, and yet good percolation § Robust to node and link failures 125
Conclusion n Broadcast is an important problem § Gossip is good – but not practical for sensor nets § Need to adapt gossip based on topology / failures n Smart Gossip § Form dependence graphs using distributed protocol § Dependence relations suggest suitable probability n Results § Overheads are low, and yet good percolation § Robust to node and link failures 125
 Questions? 126
Questions? 126
 Percolation Smart Gossip Adaptive Overhead Adaptive Neighbor 127
Percolation Smart Gossip Adaptive Overhead Adaptive Neighbor 127
 Wireless Routing n Link instability causes many routing issues § § Shortest hop routing often worst choice Scarce bandwidth makes overhead conspicuous Battery power a concern Security and misbehavior … n If that’s not bad enough § Add node mobility • Note: Routes may break, and reconnect later 128
Wireless Routing n Link instability causes many routing issues § § Shortest hop routing often worst choice Scarce bandwidth makes overhead conspicuous Battery power a concern Security and misbehavior … n If that’s not bad enough § Add node mobility • Note: Routes may break, and reconnect later 128
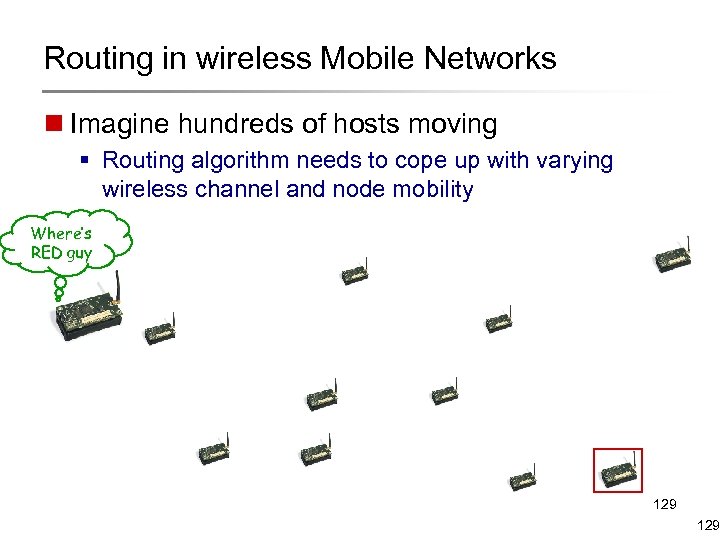 Routing in wireless Mobile Networks n Imagine hundreds of hosts moving § Routing algorithm needs to cope up with varying wireless channel and node mobility Where’s RED guy 129
Routing in wireless Mobile Networks n Imagine hundreds of hosts moving § Routing algorithm needs to cope up with varying wireless channel and node mobility Where’s RED guy 129


