05f625aa4a3c99e923567acab0d8b2cf.ppt
- Количество слайдов: 44

Wireless Security (802. 11 b) Mahendran Velauthapillai April 29, 2004

Agenda • • • Introduction to WLAN Communication Security Requirements 802. 11 b Security Architecture Security Issues in 802. 11 b Proposed Solutions for Enhanced Security
Introduction to WLAN • Two modes 1) Infrastructure 2) Adhoc
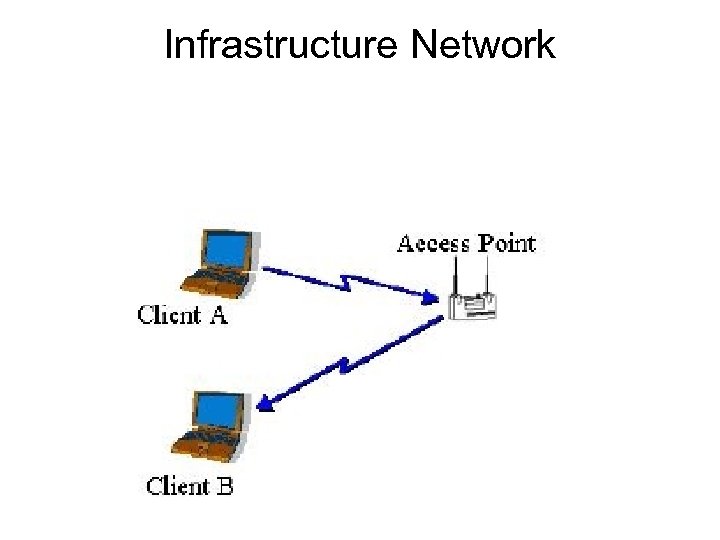
Infrastructure Network
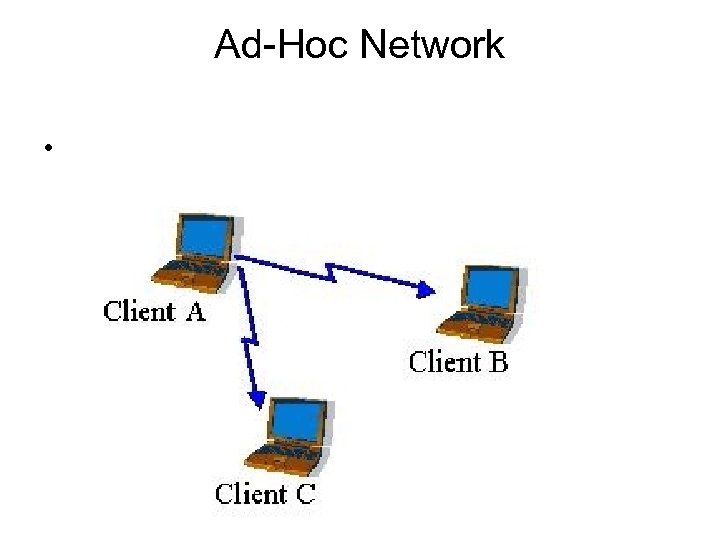
Ad-Hoc Network •

• Prior to communicating data, wireless clients and access points must establish a relationship, or an association. • Only after an association is established can the two wireless stations exchange data.

Infrastructure Mode • clients associate with an access point. • The association process is a two step process involving three states: 1. Unauthenticated and unassociated, 2. Authenticated and unassociated, and 3. Authenticated and associated.

• To transition between the states, the communicating parties exchange messages called management frames. • All access points transmit a beacon management frame at fixed interval. • To associate with an access point and join a BSS, a client listens for beacon messages to identify the access points within range. • The client then selects the BSS to join in a vendor independent manner.

• A client may also send a probe request management frame to find an access point affiliated with a desired SSID. • After identifying an access point, the client and the access point perform a mutual authentication by exchanging several management frames as part of the process. • After successful authentication, the client moves into the second state, authenticated and unassociated. • Moving from the second state to the third and final state, authenticated and associated, involves the client sending an association request frame, and the access point responding with an association response frame.
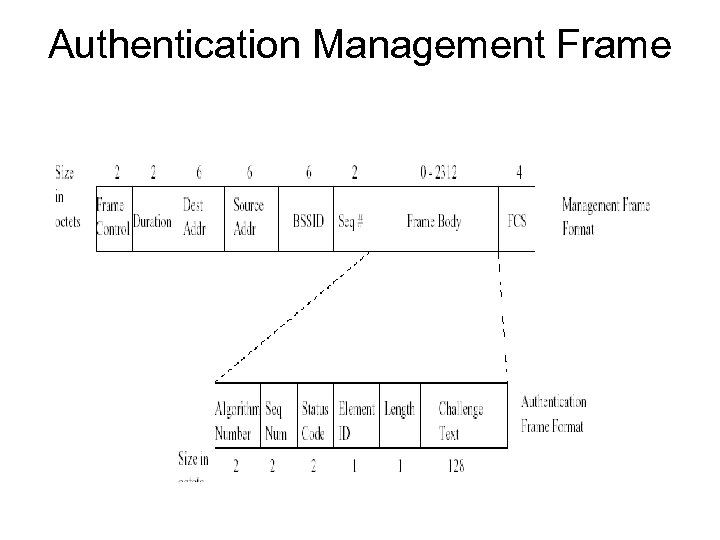
Authentication Management Frame
WEP (encrypted traffic • The industry’s solution: WEP (Wired Equivalent Privacy) • Share a single cryptographic key among all devices • Encrypt all packets sent over the air, using the shared key • Use a checksum to prevent injection of spoofed packets
Communication Security Requirements • Privacy • Data Integrity • Authentication

802. 11 b Security Architecture • Link-layer security protocol Prevent link-layer eavesdropping Control network access WEP (Wired Equivalent Protocol) Essentially, equivalent to wired access point security

WEP Requirements • • • Reasonably Strong (What does this mean? ) Self-synchronizing Computationally efficient Exportable Optional

WEP Data Frame
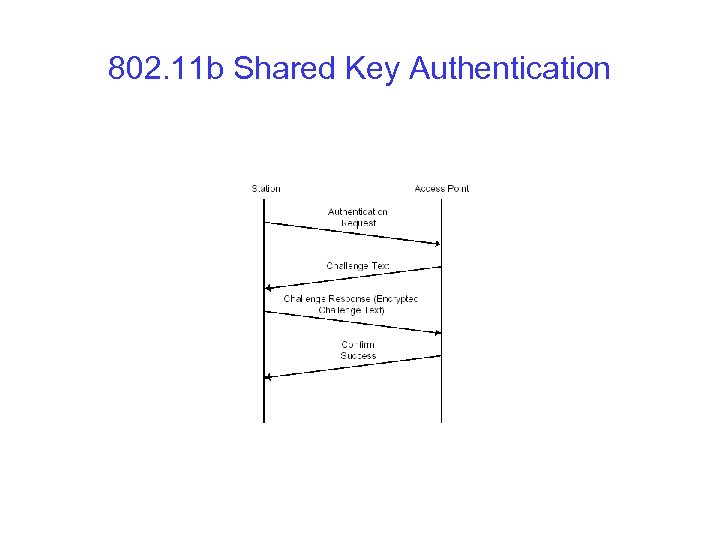
802. 11 b Shared Key Authentication

Security Issues • • • War Driving / Sniffing (Parking Lot attack) Rogue Access Points MAC Address SSID WEP

War Driving • War driving is one of the latest hacker fads – http: //www. wardriving. com/ • Involves driving around and scanning in search of unprotected 802. 11 wireless networks • Several War Driving tools are available – – – Net. Stumbler Airo. Peek Mobile. Manager Sniffer Wireless THC-War. Drive
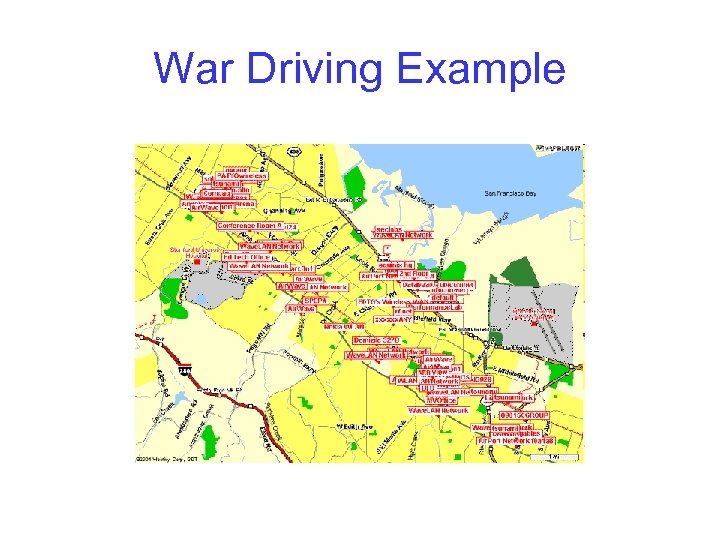
War Driving Example
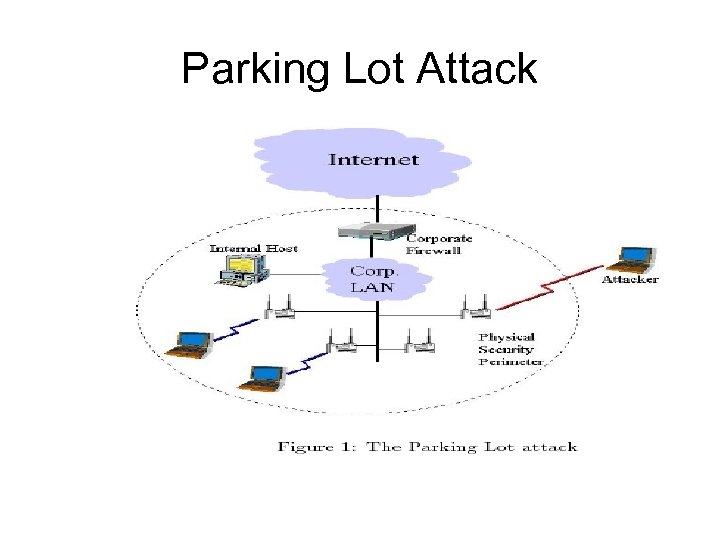
Parking Lot Attack

Unauthorized Access Points • Install access points without permission (Bala!!!!! Shuuuu!) • Security is NOT enabled • The whole Network becomes vulnerable to war driving/sniffing attacks

Using MAC Address • Control access by allowing only valid MAC addresses to access the network • Complicated and difficult to maintain list of valid MAC addresses • Using software, MAC addresses can be spoofed

Service Set ID (SSID) • SSID is the network name given to a wireless network • Can be used to access a specific access point by name • The more people that come to know about the SSID the more likely that it will be misused • Changes in SSID requires communicating it to all people who access the network
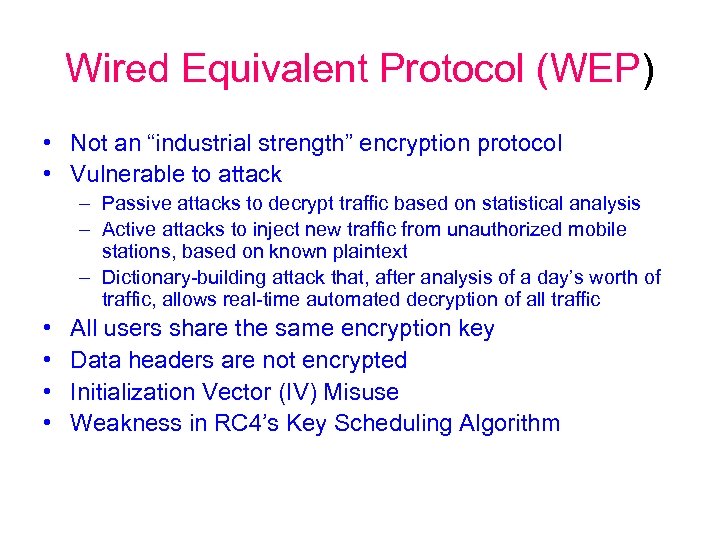
Wired Equivalent Protocol (WEP) • Not an “industrial strength” encryption protocol • Vulnerable to attack – Passive attacks to decrypt traffic based on statistical analysis – Active attacks to inject new traffic from unauthorized mobile stations, based on known plaintext – Dictionary-building attack that, after analysis of a day’s worth of traffic, allows real-time automated decryption of all traffic • • All users share the same encryption key Data headers are not encrypted Initialization Vector (IV) Misuse Weakness in RC 4’s Key Scheduling Algorithm

WEP - A Little More Detail IV, P RC 4(K, IV) • WEP uses the RC 4 stream cipher to encrypt a TCP/IP packet (P) by xor-ing it with keystream (RC 4(K, IV))

A Property of RC 4 • Keystream leaks, under known-plaintext attack – Suppose we intercept a ciphertext C, and suppose we can guess the corresponding plaintext P – Let Z = RC 4(K, IV) be the RC 4 keystream – Since C = P Z, we can derive the RC 4 keystream Z by P C = P (P Z) = Z • This is not a problem. . . unless keystream is reused!
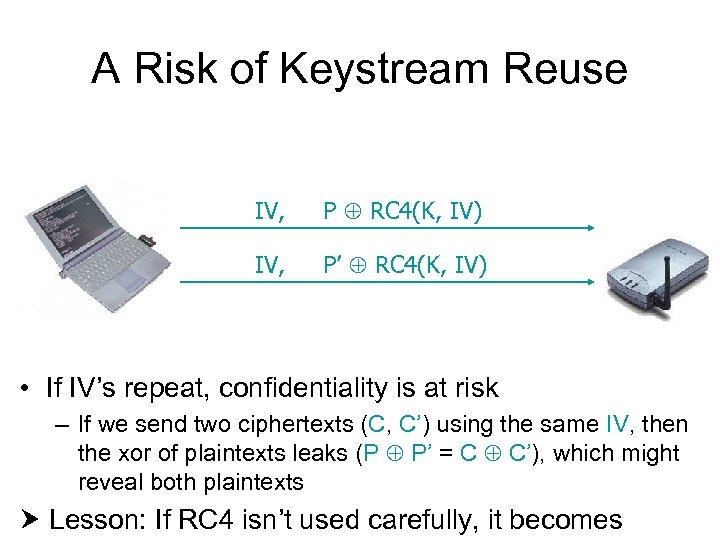
A Risk of Keystream Reuse IV, P RC 4(K, IV) IV, P’ RC 4(K, IV) • If IV’s repeat, confidentiality is at risk – If we send two ciphertexts (C, C’) using the same IV, then the xor of plaintexts leaks (P P’ = C C’), which might reveal both plaintexts Lesson: If RC 4 isn’t used carefully, it becomes

Attack #1: Keystream Reuse • WEP didn’t use RC 4 carefully • The problem: IV’s frequently repeat – The IV is often a counter that starts at zero – Hence, rebooting causes IV reuse – Also, there are only 16 million possible IV’s, so after intercepting enough packets, there are sure to be repeats Attackers can eavesdrop on 802. 11 traffic – An eavesdropper can decrypt intercepted ciphertexts even without knowing the key
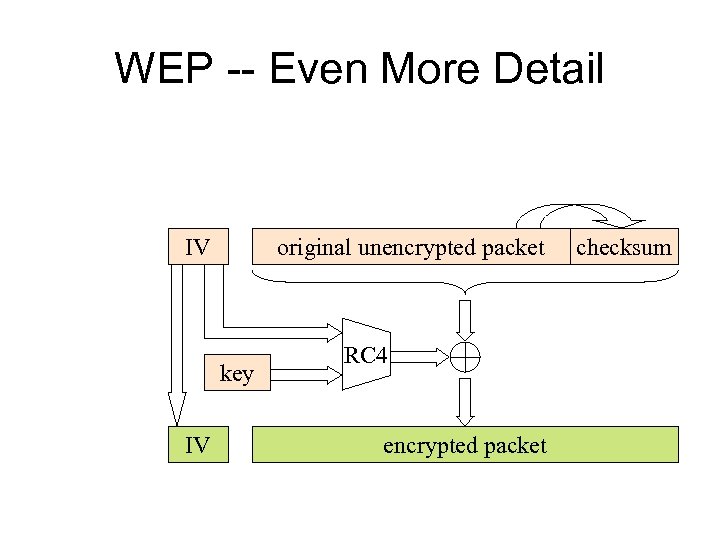
WEP -- Even More Detail IV original unencrypted packet key IV RC 4 encrypted packet checksum

Attack #2: Spoofed Packets • Attackers can inject forged 802. 11 traffic – Learn RC 4(K, IV) using previous attack – Since the checksum is unkeyed, you can then create valid ciphertexts that will be accepted by the receiver Attackers can bypass 802. 11 access control – All computers attached to wireless net are exposed
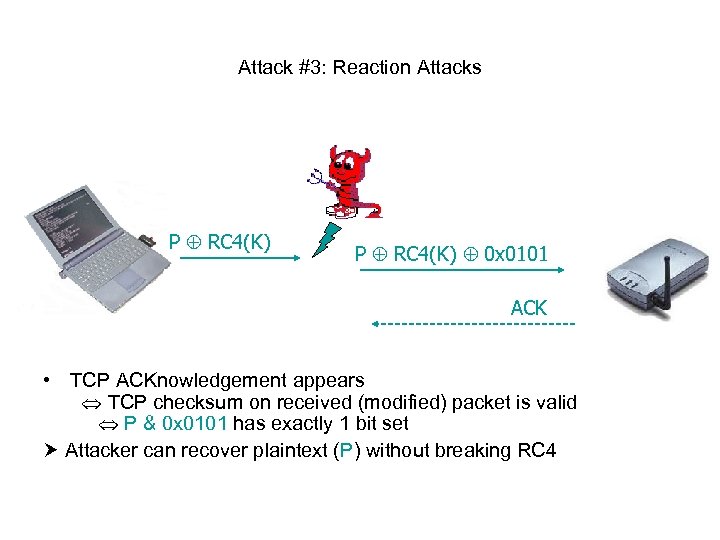
Attack #3: Reaction Attacks P RC 4(K) 0 x 0101 ACK • TCP ACKnowledgement appears TCP checksum on received (modified) packet is valid P & 0 x 0101 has exactly 1 bit set Attacker can recover plaintext (P) without breaking RC 4

Attacks on WEP • Downloadable procedures • To crack the key – Air. Snort: http: //airsnort. sourceforge. net/ – WEPCrack: http: //sourceforge. net/projects/wepcrack/ • To brute force enter into WLAN – THC-RUT: www. thehackerschoice. com/releases. php

Proposed Solutions to Enhance Security • Virtual Private Network (VPN) • Secure LAN (SLAN) • Remote Authentication Dial In User Services (RADIUS) • IPsec • 802. 1 x • Proprietary WEP Implementations

VPN • Enables you to send data between two computers across a shared or public network in a manner that emulates the properties of a pointto-point private link • Provides a scaleable authentication and encryption solution • Does require end user configuration and a strong knowledge of VPN technology • Users must re-authenticate if roaming between VPN servers

Secure LAN (SLAN) • A GPL open-source “VPN” System • Provides server authentication, client authentication, data privacy, and integrity using per session and per user short life keys • Simpler and more cost efficient than a VPN • Support for Windows and Linux • Website: http: //slan. sourceforge. net/
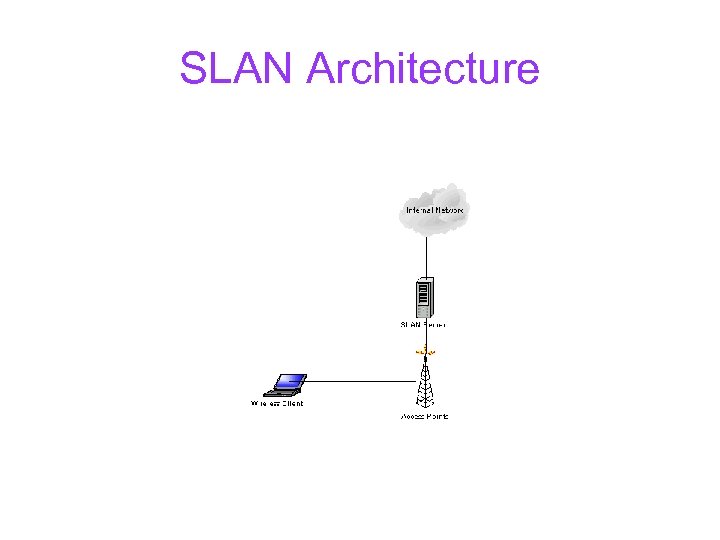
SLAN Architecture

RADIUS • Several 802. 11 access points offer RADIUS authentication • Clients can gain access to the network by supplying a username and password to a separate server • This information is securely sent over the network eliminating the possibility of passive snooping

IPsec • Provides encryption and authentication services at the IP level of the network protocol stack • Can be used to secure nearly any type of Internet traffic • Legacy applications not implementing secure communications can be made secure using IPsec • Examples: – Free S/WAN - http: //www. freeswan. org/

IPsec - Disadvantages • IPsec authenticates machines, not users • IPsec does not stop Denial-of-Service attacks • IPsec is not true end-to-end security • IPsec cannot be secure if your system isn’t

802. 1 x • Provides enhanced security for users of 802. 11 b WLANs • Provides port-level authentication for any wired or wireless Ethernet client system • 802. 1 x was originally designed as a standard for wired Ethernet, but is applicable to WLANs • It leverages many of the security features used with dial-up networking (RADIUS) • Also uses Extensible Authentication Protocol (EAP, RFC 2284) • Built in support in Windows XP
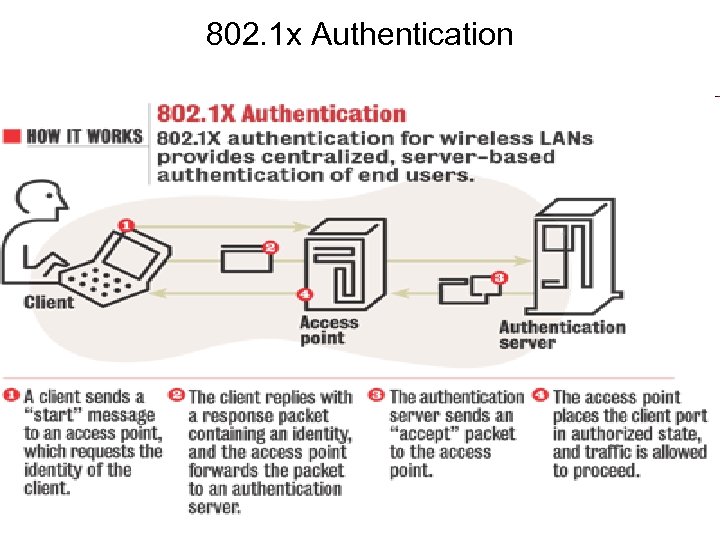
802. 1 x Authentication

Proprietary WEP Security • Dynamic Key Refresh instead of static keys • Use of 3 DES/AES instead of RC 4 (Net. Motion Wireless) • Disadvantages: – Interoperability Issues (non-Wi. Fi Compliant)

Conclusion • Wireless LANs are very useful and convenient, but current security state not ideal for sensitive environments • Care must be taken before sensitive information is made available over Wireless LANs
05f625aa4a3c99e923567acab0d8b2cf.ppt