fdf6609e3dcb29dbcf2b693922830f9f.ppt
- Количество слайдов: 55
 Wireless Network Security Nate Arnold GE Transportation MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Network Security Nate Arnold GE Transportation MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Wireless Networks What are they? • A Wireless Network is a system of physically separated devices which communicate via electronic waves in order to share information. MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Networks What are they? • A Wireless Network is a system of physically separated devices which communicate via electronic waves in order to share information. MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Wireless Networks What’s out there? • Approximately 50 different types of wireless networks • Examples – Cell Phones (GSM, 3 GS) – UPS & Fed Ex sending messages using GPRS and CDMA – 802. 11 IEEE standards for WLAN – Satellites (Corporate networks, GPS, Iridium) MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Networks What’s out there? • Approximately 50 different types of wireless networks • Examples – Cell Phones (GSM, 3 GS) – UPS & Fed Ex sending messages using GPRS and CDMA – 802. 11 IEEE standards for WLAN – Satellites (Corporate networks, GPS, Iridium) MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
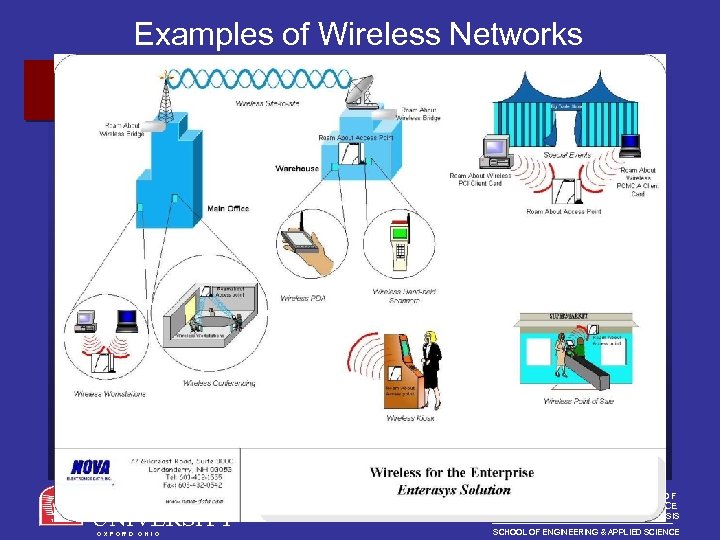 Examples of Wireless Networks MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Examples of Wireless Networks MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Wireless Networks What we will focus on • 802. 11 IEEE – Current standards – Security – New and future standards – Examples • Alternate Wireless Network Standards MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Networks What we will focus on • 802. 11 IEEE – Current standards – Security – New and future standards – Examples • Alternate Wireless Network Standards MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Wireless Networks The Business Case • Why go wireless? – Do the benefits outweigh the risks? MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Networks The Business Case • Why go wireless? – Do the benefits outweigh the risks? MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Wireless Networks The Business Case • Does wireless networking provide business value? Soft Benefits vs. Hard Benefits MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Networks The Business Case • Does wireless networking provide business value? Soft Benefits vs. Hard Benefits MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Wireless Networks The Business Case Soft Benefits of a WLAN: • • Increased flexibility Faster decision making Higher employee satisfaction Greater accuracy of information MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Networks The Business Case Soft Benefits of a WLAN: • • Increased flexibility Faster decision making Higher employee satisfaction Greater accuracy of information MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Wireless Networks The Business Case Real world examples of Soft Benefits • University of Illinois at Chicago Medical Center – – 507 beds, Outpatient Care Center, 715 physicians Originally 5 different terminals to carry out jobs Difficult for IT Dept. to support multiple devices Server based WLAN, and wireless computers improved the quality of the care given to patients MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Networks The Business Case Real world examples of Soft Benefits • University of Illinois at Chicago Medical Center – – 507 beds, Outpatient Care Center, 715 physicians Originally 5 different terminals to carry out jobs Difficult for IT Dept. to support multiple devices Server based WLAN, and wireless computers improved the quality of the care given to patients MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Wireless Networks The Business Case Real world examples of Soft Benefits • AOT Financial Services (The Netherlands) – Amsterdam Options Exchange introduces new electronic trading with wireless access – AOT provided its traders the with wireless devices and so the ability to make a trade or access market information at the touch of a button – Results in a 300 percent increase in the speed of trading – 300 percent increase in profits? MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Networks The Business Case Real world examples of Soft Benefits • AOT Financial Services (The Netherlands) – Amsterdam Options Exchange introduces new electronic trading with wireless access – AOT provided its traders the with wireless devices and so the ability to make a trade or access market information at the touch of a button – Results in a 300 percent increase in the speed of trading – 300 percent increase in profits? MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Wireless Networks The Business Case Problems with Soft Benefits • Difficult if not impossible to quantify • Hard to justify expenditure MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Networks The Business Case Problems with Soft Benefits • Difficult if not impossible to quantify • Hard to justify expenditure MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Wireless Networks The Business Case Hard Benefits • Dollar amount of cost savings • Measurable increases in productivity MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Networks The Business Case Hard Benefits • Dollar amount of cost savings • Measurable increases in productivity MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
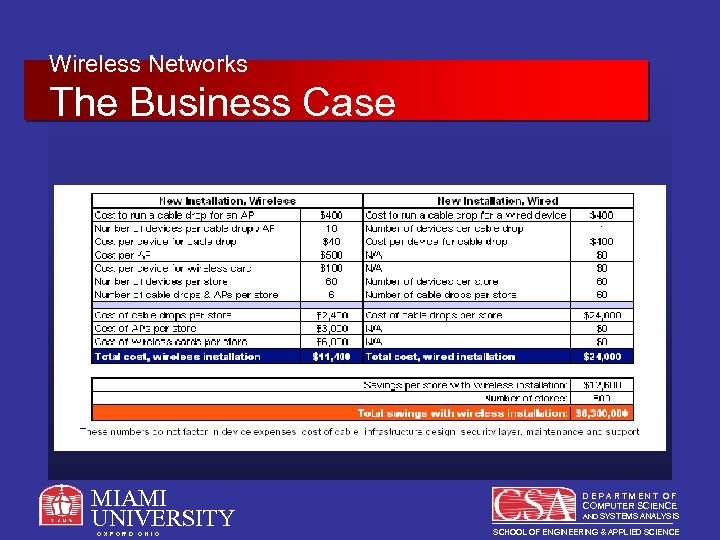
 Wireless Networks The Business Case Hard Benefits – Cost savings • Case study of a major national retail chain with more than 500 stores • Focuses on total cost of ownership of wireless vs. wired networks in stores • Initial installation, and store reconfigurations both considered MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Networks The Business Case Hard Benefits – Cost savings • Case study of a major national retail chain with more than 500 stores • Focuses on total cost of ownership of wireless vs. wired networks in stores • Initial installation, and store reconfigurations both considered MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Wireless Networks The Business Case MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Networks The Business Case MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Wireless Networks The Business Case Hard Benefits - Productivity Gains • Intel IT and Intel Finance collaboration • ROI based model based on the standard discounted cash flow methodology ROI = (Productivity benefits – Start-up costs – Sustaining costs) MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Networks The Business Case Hard Benefits - Productivity Gains • Intel IT and Intel Finance collaboration • ROI based model based on the standard discounted cash flow methodology ROI = (Productivity benefits – Start-up costs – Sustaining costs) MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Wireless Networks The Business Case Hard Benefits – Productivity Gains • Startup costs and Sustaining costs both relatively easy to measure • Converting the perceived value to actual ROI is much more difficult MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Networks The Business Case Hard Benefits – Productivity Gains • Startup costs and Sustaining costs both relatively easy to measure • Converting the perceived value to actual ROI is much more difficult MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Wireless Networks The Business Case Hard Benefits – Productivity Gains • Method to measure productivity benefits – WLAN Pilot • Determine data points • Establish a baseline • Segment the users • Set expectations MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Networks The Business Case Hard Benefits – Productivity Gains • Method to measure productivity benefits – WLAN Pilot • Determine data points • Establish a baseline • Segment the users • Set expectations MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
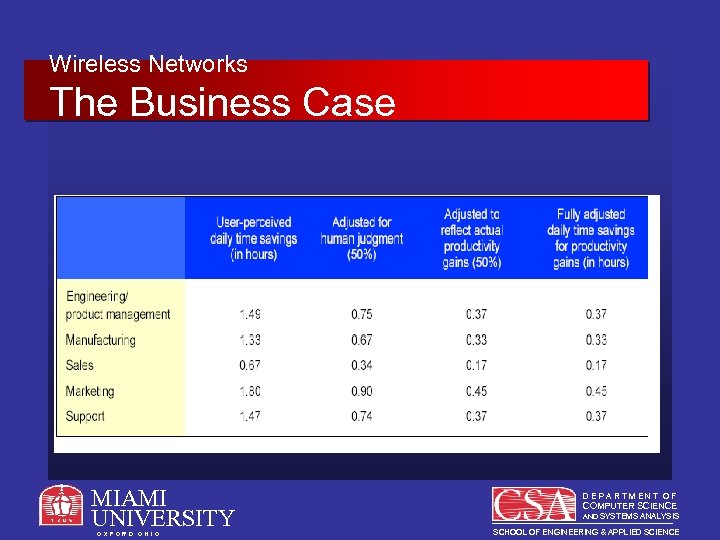
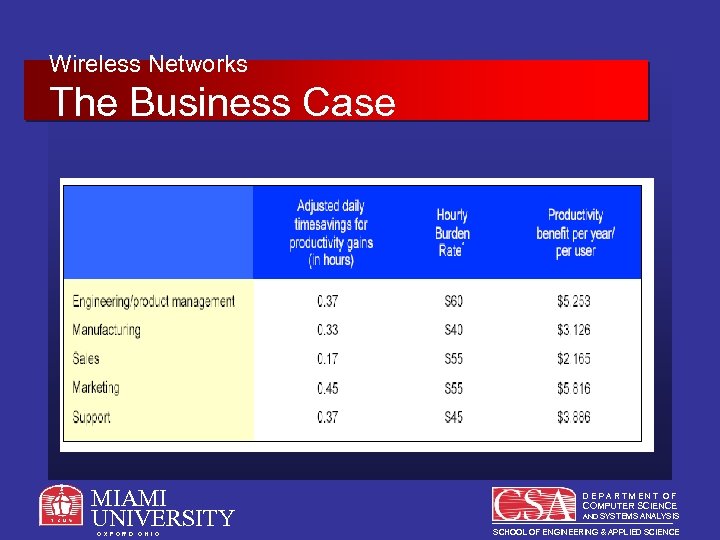
 Wireless Networks The Business Case Hard Benefits – Productivity Gains • Timesavings = Productivity • Measuring Timesavings – Intel IT asked users how much time they saved by using the WLAN and took 25 percent of those estimates to use in its ROI equations. MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Networks The Business Case Hard Benefits – Productivity Gains • Timesavings = Productivity • Measuring Timesavings – Intel IT asked users how much time they saved by using the WLAN and took 25 percent of those estimates to use in its ROI equations. MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Wireless Networks The Business Case MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Networks The Business Case MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Wireless Networks The Business Case MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Networks The Business Case MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
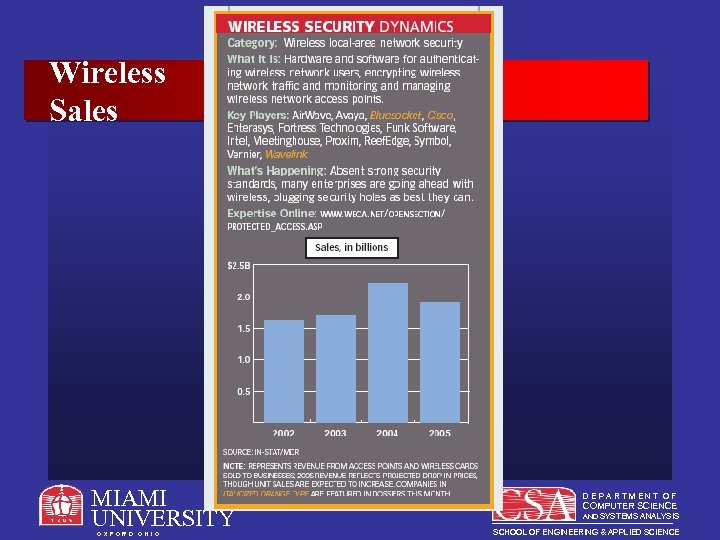 Wireless Sales MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wireless Sales MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 7 Security Problems of Wireless Networks • • Easy Access Rogue Access Points Unauthorized Use of Service and Performance Constraints MAC Spoofing and Session Hi-jacking Traffic Analysis and Eavesdropping Higher Level of Attacks MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
7 Security Problems of Wireless Networks • • Easy Access Rogue Access Points Unauthorized Use of Service and Performance Constraints MAC Spoofing and Session Hi-jacking Traffic Analysis and Eavesdropping Higher Level of Attacks MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
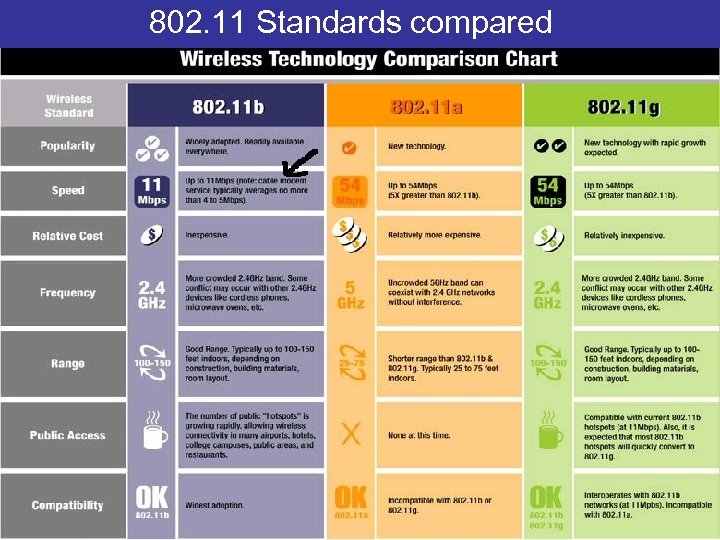 802. 11 Standards compared MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
802. 11 Standards compared MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Security Goals of 802. 11 • To protect wireless transmissions that travel over the open radio frequencies. – Confidentiality: protect data from being intercepted – Access Control: protect access to private networks – Data Integrity: prevent tampering with transmitted messages MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Security Goals of 802. 11 • To protect wireless transmissions that travel over the open radio frequencies. – Confidentiality: protect data from being intercepted – Access Control: protect access to private networks – Data Integrity: prevent tampering with transmitted messages MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 802. 11 WEP Design Flaws • Weak Authentication • Weak Encryption – Open System Authentication – Shared Key Authentication – MAC Address Filtering MIAMI UNIVERSITY O X F O R D O H I O – Keystream Reuse – Improper Key Management – Short Encryption Keys – WEP Packet Checksums are not Secure – WEP is Turned off by Default DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
802. 11 WEP Design Flaws • Weak Authentication • Weak Encryption – Open System Authentication – Shared Key Authentication – MAC Address Filtering MIAMI UNIVERSITY O X F O R D O H I O – Keystream Reuse – Improper Key Management – Short Encryption Keys – WEP Packet Checksums are not Secure – WEP is Turned off by Default DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Solution for Securing 802. 11 • 802. 1 X – Mutual Authentication using Extensible Authentication Protocols (EAP) • Wi-Fi Protected Access (WPA) – Enhanced encryption that replaces WEP MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Solution for Securing 802. 11 • 802. 1 X – Mutual Authentication using Extensible Authentication Protocols (EAP) • Wi-Fi Protected Access (WPA) – Enhanced encryption that replaces WEP MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 What is EAP? • EAP stands for Extensible Authentication Protocol that is based on a process rather than an algorithm • EAP is a one sided authentication protocol • EAP allows for mutual authentication by running the protocol in both directions • It is a request-response protocol • It reduces exposure to key attacks MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
What is EAP? • EAP stands for Extensible Authentication Protocol that is based on a process rather than an algorithm • EAP is a one sided authentication protocol • EAP allows for mutual authentication by running the protocol in both directions • It is a request-response protocol • It reduces exposure to key attacks MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
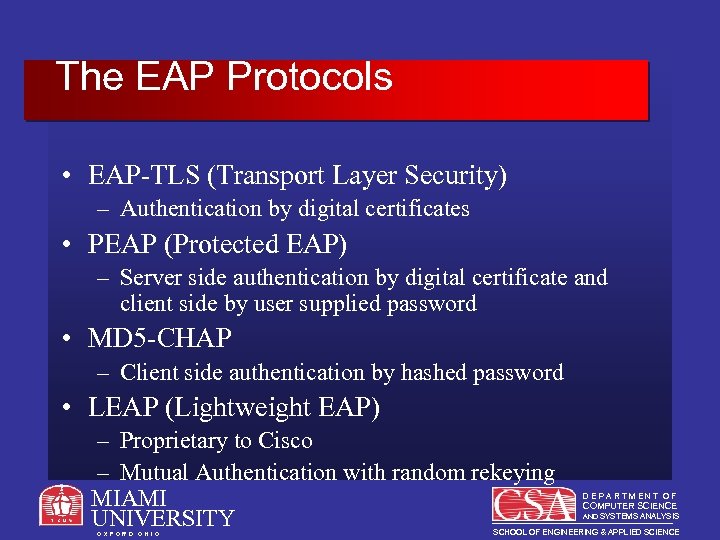 The EAP Protocols • EAP-TLS (Transport Layer Security) – Authentication by digital certificates • PEAP (Protected EAP) – Server side authentication by digital certificate and client side by user supplied password • MD 5 -CHAP – Client side authentication by hashed password • LEAP (Lightweight EAP) – Proprietary to Cisco – Mutual Authentication with random rekeying MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
The EAP Protocols • EAP-TLS (Transport Layer Security) – Authentication by digital certificates • PEAP (Protected EAP) – Server side authentication by digital certificate and client side by user supplied password • MD 5 -CHAP – Client side authentication by hashed password • LEAP (Lightweight EAP) – Proprietary to Cisco – Mutual Authentication with random rekeying MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
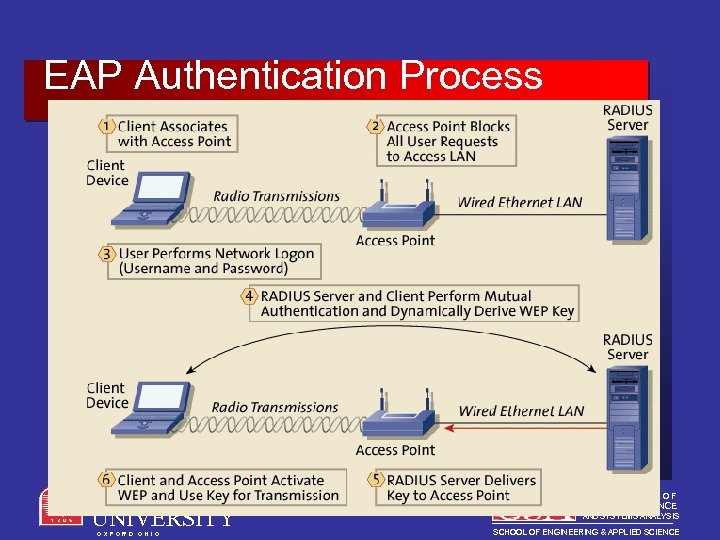 EAP Authentication Process MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
EAP Authentication Process MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Wi-Fi Protected Access (WPA) • Specification accepted early part of 2003 • Secure implementations of WPA involve – 802. 1 x infrastructure • EAP protocol + RADIUS server – Software upgrades for clients and Access Points MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Wi-Fi Protected Access (WPA) • Specification accepted early part of 2003 • Secure implementations of WPA involve – 802. 1 x infrastructure • EAP protocol + RADIUS server – Software upgrades for clients and Access Points MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 WPA Security Enhancements • 802. 1 x – EAP Authentication • Temporal Key Integrity Protocol (TKIP) – Encryption method using 128 bit rekeying – Allows different client stations to use different keys to encrypt data – Key generating function that encrypts every data packet with it own unique key • Message Integrity Code (MIC) – Checksum that prevents message tampering MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
WPA Security Enhancements • 802. 1 x – EAP Authentication • Temporal Key Integrity Protocol (TKIP) – Encryption method using 128 bit rekeying – Allows different client stations to use different keys to encrypt data – Key generating function that encrypts every data packet with it own unique key • Message Integrity Code (MIC) – Checksum that prevents message tampering MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 802. 11 i Standard • Approved in August 2004 • It incorporates the 802. 1 x specification • It adds security features – Temporary Key Integrity Protocol (TKIP) – Advanced Encryption Standard (AES) • Replacement for WEP • Mathematical ciphering algorithm that uses variable key lengths (128, 192, 256) making it almost impossible to decipher MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
802. 11 i Standard • Approved in August 2004 • It incorporates the 802. 1 x specification • It adds security features – Temporary Key Integrity Protocol (TKIP) – Advanced Encryption Standard (AES) • Replacement for WEP • Mathematical ciphering algorithm that uses variable key lengths (128, 192, 256) making it almost impossible to decipher MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Newer Standards • 802. 16 or Wi-Fi Max – Enables a single base station to support fixed and mobile devices (30 mile radius/70 mbps) – DSL providers can use this standard to provide last mile delivery of broadband to homes • 802. 20 (MBWA) Mobile Broadband Wireless Access – IEEE may ratify by the end of this year – Offers blanket coverage to a large city sized area at speeds of 1. 5 mbps – Requires special hardware at cell transmission sites and client devices containing specialized chips MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Newer Standards • 802. 16 or Wi-Fi Max – Enables a single base station to support fixed and mobile devices (30 mile radius/70 mbps) – DSL providers can use this standard to provide last mile delivery of broadband to homes • 802. 20 (MBWA) Mobile Broadband Wireless Access – IEEE may ratify by the end of this year – Offers blanket coverage to a large city sized area at speeds of 1. 5 mbps – Requires special hardware at cell transmission sites and client devices containing specialized chips MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Newer Standards (2) • 802. 11 n “mesh networking” - home use – IEEE expected to ratify this standard late 2005 – Wireless transmissions hop from device to device - Leaps could reach 100 -200 mbps – The first TV to accept this standard is expected to be released in 2006 MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Newer Standards (2) • 802. 11 n “mesh networking” - home use – IEEE expected to ratify this standard late 2005 – Wireless transmissions hop from device to device - Leaps could reach 100 -200 mbps – The first TV to accept this standard is expected to be released in 2006 MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 New Networks • Ultrawideband (UWB) for home use – Expected to be ratified by IEEE in 2005 – Data transmission rates of 1 gbps – Shorter transmit range than current Wi-Fi • Freedom Link by SBC – Combines Wi-Fi and new cellular-data networks • Voice Over Wi-Fi by Nortel Networks – Makes it possible to use Wi-Fi to make phone calls over the Web MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
New Networks • Ultrawideband (UWB) for home use – Expected to be ratified by IEEE in 2005 – Data transmission rates of 1 gbps – Shorter transmit range than current Wi-Fi • Freedom Link by SBC – Combines Wi-Fi and new cellular-data networks • Voice Over Wi-Fi by Nortel Networks – Makes it possible to use Wi-Fi to make phone calls over the Web MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 WLAN Security Best Practices 1. 2. 3. 4. 5. 6. 7. 8. Educate Employees Personal Firewalls on Mobile Machines Scan for Rogue APs (ex: Netstumbler) Change Default Passwords on APs Turn on and use WEP Avoid Placing APs near walls or windows Reduce Broadcast Strength Use VPN with secondary authentication MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
WLAN Security Best Practices 1. 2. 3. 4. 5. 6. 7. 8. Educate Employees Personal Firewalls on Mobile Machines Scan for Rogue APs (ex: Netstumbler) Change Default Passwords on APs Turn on and use WEP Avoid Placing APs near walls or windows Reduce Broadcast Strength Use VPN with secondary authentication MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
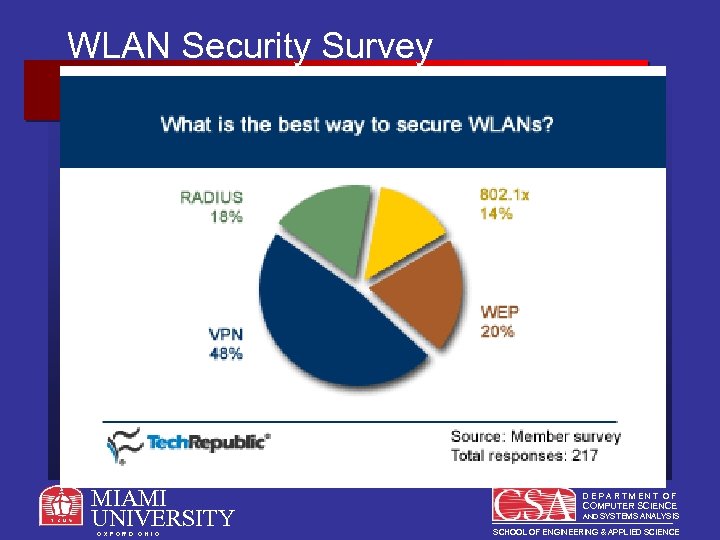 WLAN Security Survey MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
WLAN Security Survey MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
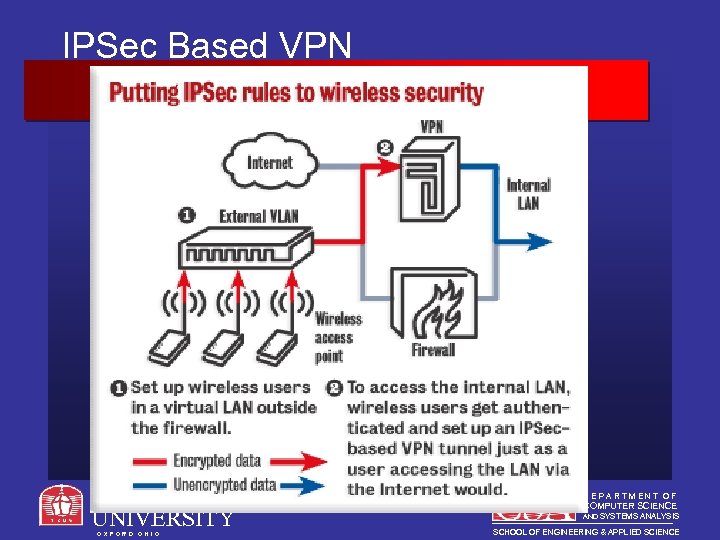 IPSec Based VPN MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
IPSec Based VPN MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
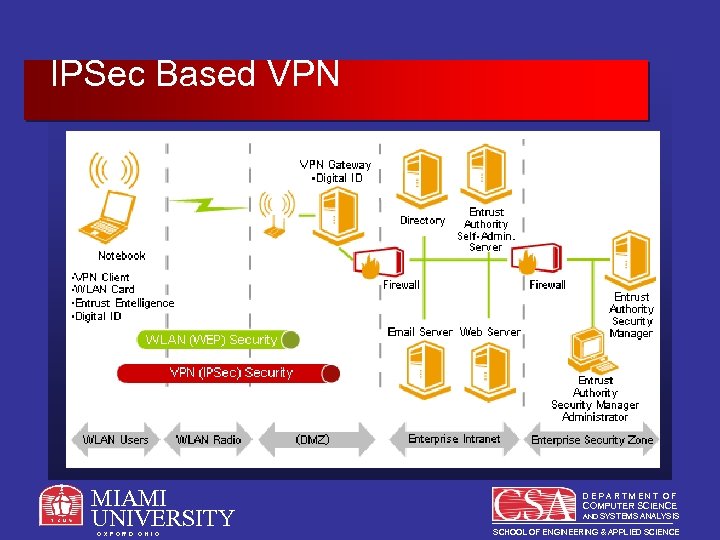 IPSec Based VPN MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
IPSec Based VPN MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 MU Campus MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
MU Campus MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 MUnet Wireless LAN – IT Services will install a university-wide 802. 11 infrastructure over 75% of most heavily trafficked student areas (e. g. , study areas, classrooms, and instructional spaces) and over 90% of office and conference areas by June 2005. The residence halls will be the first area to receive the 802. 11 infrastructure, with coverage planned for Fall 2004. – Wireless networking, even with WEP encryption, is inherently insecure. Sensitive data should not be transmitted on a wireless network unless encrypted by the application (e. g. SSL or SSH) or through use of MU's VPN service (see Related Items). MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
MUnet Wireless LAN – IT Services will install a university-wide 802. 11 infrastructure over 75% of most heavily trafficked student areas (e. g. , study areas, classrooms, and instructional spaces) and over 90% of office and conference areas by June 2005. The residence halls will be the first area to receive the 802. 11 infrastructure, with coverage planned for Fall 2004. – Wireless networking, even with WEP encryption, is inherently insecure. Sensitive data should not be transmitted on a wireless network unless encrypted by the application (e. g. SSL or SSH) or through use of MU's VPN service (see Related Items). MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 MU Wi. Fi Security Use the MUVPN http: //software. muohio. edu/ MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
MU Wi. Fi Security Use the MUVPN http: //software. muohio. edu/ MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
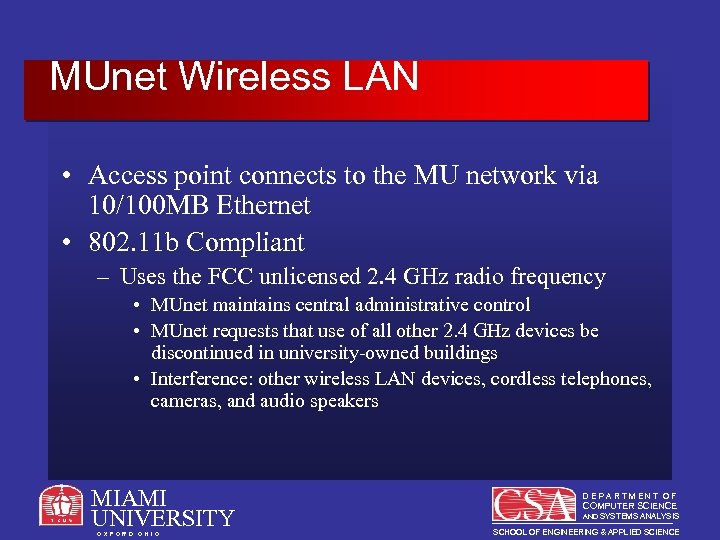 MUnet Wireless LAN • Access point connects to the MU network via 10/100 MB Ethernet • 802. 11 b Compliant – Uses the FCC unlicensed 2. 4 GHz radio frequency • MUnet maintains central administrative control • MUnet requests that use of all other 2. 4 GHz devices be discontinued in university-owned buildings • Interference: other wireless LAN devices, cordless telephones, cameras, and audio speakers MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
MUnet Wireless LAN • Access point connects to the MU network via 10/100 MB Ethernet • 802. 11 b Compliant – Uses the FCC unlicensed 2. 4 GHz radio frequency • MUnet maintains central administrative control • MUnet requests that use of all other 2. 4 GHz devices be discontinued in university-owned buildings • Interference: other wireless LAN devices, cordless telephones, cameras, and audio speakers MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 More MU Wi. Fi Info Mymiami. muohio. edu MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
More MU Wi. Fi Info Mymiami. muohio. edu MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 What is Netstumbler? • A Windows utility for 802. 11 b based wireless network auditing – Compatible with Windows 9 x, 2000, and XP • Mini. Stumbler – Pocket PC 3. 0 and 2002. Supports ARM, MIPS and SH 3 CPU types • More info at netstumbler. com MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
What is Netstumbler? • A Windows utility for 802. 11 b based wireless network auditing – Compatible with Windows 9 x, 2000, and XP • Mini. Stumbler – Pocket PC 3. 0 and 2002. Supports ARM, MIPS and SH 3 CPU types • More info at netstumbler. com MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Who might use Netstumbler? • Security team wanting to check that their corporate LAN isn't wide open • Systems admins wanting to check coverage of their Wireless LAN • Gatherers of demographic information about 802. 11 popularity • Drive-by snoopers • Overly curious bystanders MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Who might use Netstumbler? • Security team wanting to check that their corporate LAN isn't wide open • Systems admins wanting to check coverage of their Wireless LAN • Gatherers of demographic information about 802. 11 popularity • Drive-by snoopers • Overly curious bystanders MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
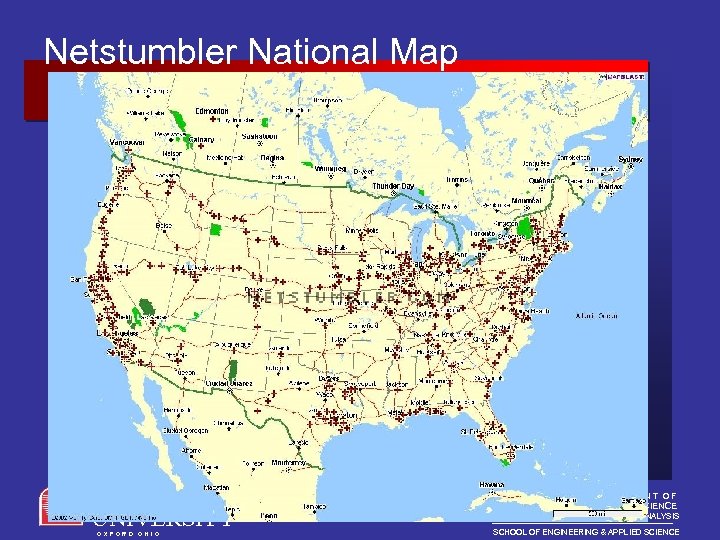 Netstumbler National Map MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Netstumbler National Map MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
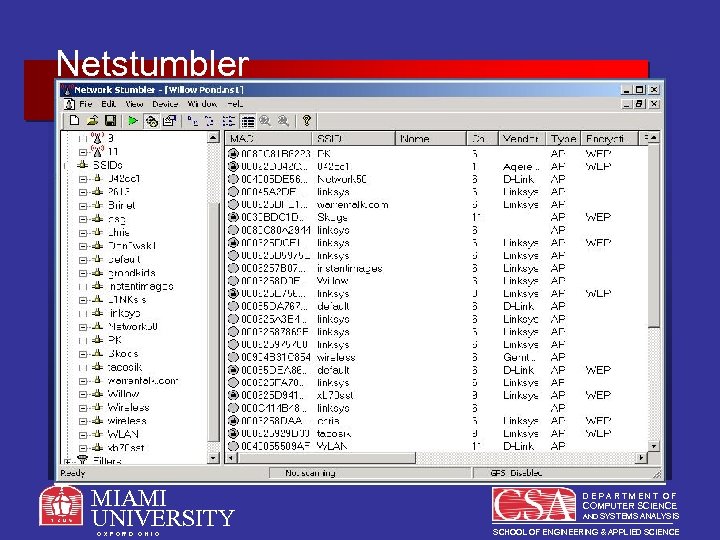 Netstumbler MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Netstumbler MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Questions? MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Questions? MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 The following slides include references and extra material MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
The following slides include references and extra material MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Reference Materials • Securing WI-FI Wireless Networks with Today’s Technologies; WI-FI Alliance, 02/06/03, www. wifi. org • Enterprise Solutions for Wireless Lan Security; WI-FI Alliance, 02/06/03, – www. wi-fi. org • Intercepting Mobile Communications: The Insecurity of 802. 11 –DRAFT-; Nikita Borisov and David Wagner. UC Berkley, Ian Goldberg Zero Knowledge Systems. • Wireless Security: The Gaps and How to Fill Them; Jeff Moad, Larry Seltzer, Craig Ellison, Gary Bolles, Eweek Enterprise News & Reviews REPORT, 11/25/03 – http: //www. eweek. com/article 2/0, 4149, 1507241, 00. asp • WPA Wireless Security Offers Multiple Advantages over WEP; Brien M. Posey, 08/20/03, www. techrepublic. com • How the Wi-Fi Future Might Look; Olga Kharif, Business Week Online, 02/18/04 • Then There’s UWB, WIMAX, w. Oz. Net…; Olga Kharif, Business Week Online, 02/18/04 • Carnival sees world's largest public Wi-Fi network; Anthony Newman, 02/20/04 MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Reference Materials • Securing WI-FI Wireless Networks with Today’s Technologies; WI-FI Alliance, 02/06/03, www. wifi. org • Enterprise Solutions for Wireless Lan Security; WI-FI Alliance, 02/06/03, – www. wi-fi. org • Intercepting Mobile Communications: The Insecurity of 802. 11 –DRAFT-; Nikita Borisov and David Wagner. UC Berkley, Ian Goldberg Zero Knowledge Systems. • Wireless Security: The Gaps and How to Fill Them; Jeff Moad, Larry Seltzer, Craig Ellison, Gary Bolles, Eweek Enterprise News & Reviews REPORT, 11/25/03 – http: //www. eweek. com/article 2/0, 4149, 1507241, 00. asp • WPA Wireless Security Offers Multiple Advantages over WEP; Brien M. Posey, 08/20/03, www. techrepublic. com • How the Wi-Fi Future Might Look; Olga Kharif, Business Week Online, 02/18/04 • Then There’s UWB, WIMAX, w. Oz. Net…; Olga Kharif, Business Week Online, 02/18/04 • Carnival sees world's largest public Wi-Fi network; Anthony Newman, 02/20/04 MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 Reference Materials • The CIO’s Guide to Mobile Wireless Computing; Citrix; White Paper; 2002 (16) • Wireless LANs – Linking productivity gains to return on investment; Intel Information Technology; White Paper; December, 2002 (9) • Assessing the Total Cost of Ownership for Wireless Versus Wired LAN; Syntegra; White Paper; 2003 (6) • David Spence. Personal Interview. 2/12/04 • Kevin Kessler. Personal Interview. 2/17/04 • http: //ucit. uc. edu/, 2/17/04 • http: //www. netstumbler. com/, 2/17/04 • http: //www. nova-data. com/images/, 2/18/04 MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
Reference Materials • The CIO’s Guide to Mobile Wireless Computing; Citrix; White Paper; 2002 (16) • Wireless LANs – Linking productivity gains to return on investment; Intel Information Technology; White Paper; December, 2002 (9) • Assessing the Total Cost of Ownership for Wireless Versus Wired LAN; Syntegra; White Paper; 2003 (6) • David Spence. Personal Interview. 2/12/04 • Kevin Kessler. Personal Interview. 2/17/04 • http: //ucit. uc. edu/, 2/17/04 • http: //www. netstumbler. com/, 2/17/04 • http: //www. nova-data. com/images/, 2/18/04 MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
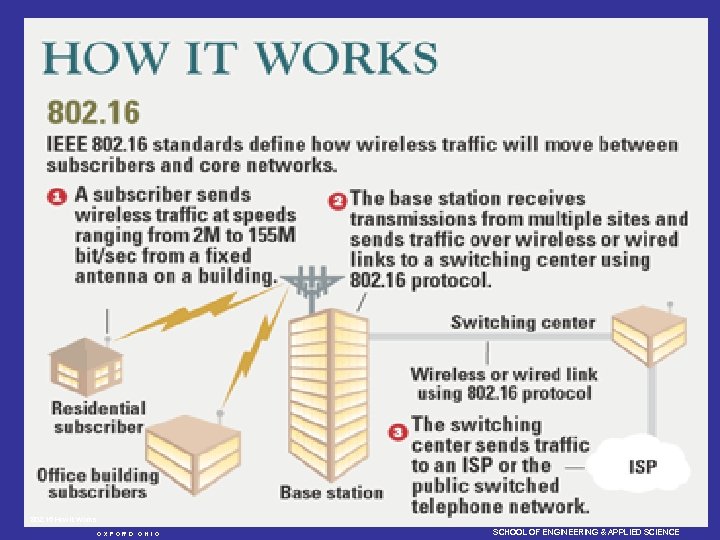 MIAMI UNIVERSITY 802. 16 How It Works O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
MIAMI UNIVERSITY 802. 16 How It Works O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 IEEE 802. 16 Progress Work on 802. 16 started in July 1999. Four years into its mission, the IEEE 802. 16 Working Group on Broadband Wireless Access has delivered a base and three follow-on standards. IEEE 802. 16 (“Air Interface for Fixed Broadband Wireless Access Systems”) was approved in December 2001. This standard is for wireless MANs operating at frequencies between 10 and 66 GHz. IEEE 802. 16. 2, published in 2001, specifies a “recommended practice” to address the operation of multiple, different broadband systems in the 10 -66 GHz frequency range. In January of this year, the IEEE approved an amendment to 802. 16, called 802. 16 a, which adds to the original standard operation in licensed and unlicensed frequency bands from 2 -11 GHz. 802. 16 c, which was approved in December 2002, is aimed at improving interoperability by specifying system profiles in the 10 -66 GHz range. MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
IEEE 802. 16 Progress Work on 802. 16 started in July 1999. Four years into its mission, the IEEE 802. 16 Working Group on Broadband Wireless Access has delivered a base and three follow-on standards. IEEE 802. 16 (“Air Interface for Fixed Broadband Wireless Access Systems”) was approved in December 2001. This standard is for wireless MANs operating at frequencies between 10 and 66 GHz. IEEE 802. 16. 2, published in 2001, specifies a “recommended practice” to address the operation of multiple, different broadband systems in the 10 -66 GHz frequency range. In January of this year, the IEEE approved an amendment to 802. 16, called 802. 16 a, which adds to the original standard operation in licensed and unlicensed frequency bands from 2 -11 GHz. 802. 16 c, which was approved in December 2002, is aimed at improving interoperability by specifying system profiles in the 10 -66 GHz range. MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
 IEEE 802. 20 Mission and Project Scope On 11 December 2002, the IEEE Standards Board approved the establishment of IEEE 802. 20, the Mobile Broadband Wireless Access (MBWA) Working Group. • Mission • The mission of IEEE 802. 20 is to develop the specification for an efficient packet based air interface that is optimized for the transport of IP based services. The goal is to enable worldwide deployment of affordable, ubiquitous, always-on and interoperable multi-vendor mobile broadband wireless access networks that meet the needs of business and residential end user markets. MBWA Scope • Specification of physical and medium access control layers of an air interface for interoperable mobile broadband wireless access systems, operating in licensed bands below 3. 5 GHz, optimized for IP-data transport, with peak data rates per user in excess of 1 Mbps. It supports various vehicular mobility classes up to 250 Km/h in a MAN environment and targets spectral efficiencies, sustained user data rates and numbers of active users that are all significantly higher than achieved by existing mobile systems MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE
IEEE 802. 20 Mission and Project Scope On 11 December 2002, the IEEE Standards Board approved the establishment of IEEE 802. 20, the Mobile Broadband Wireless Access (MBWA) Working Group. • Mission • The mission of IEEE 802. 20 is to develop the specification for an efficient packet based air interface that is optimized for the transport of IP based services. The goal is to enable worldwide deployment of affordable, ubiquitous, always-on and interoperable multi-vendor mobile broadband wireless access networks that meet the needs of business and residential end user markets. MBWA Scope • Specification of physical and medium access control layers of an air interface for interoperable mobile broadband wireless access systems, operating in licensed bands below 3. 5 GHz, optimized for IP-data transport, with peak data rates per user in excess of 1 Mbps. It supports various vehicular mobility classes up to 250 Km/h in a MAN environment and targets spectral efficiencies, sustained user data rates and numbers of active users that are all significantly higher than achieved by existing mobile systems MIAMI UNIVERSITY O X F O R D O H I O DEPARTMENT OF COMPUTER SCIENCE AND SYSTEMS ANALYSIS SCHOOL OF ENGINEERING & APPLIED SCIENCE


