6a16fe191e794386b2718d8bab2ada4c.ppt
- Количество слайдов: 43
 Wireless LAN Security Yen-Cheng Chen Department of Information Management National Chi Nan University ycchen@ncnu. edu. tw
Wireless LAN Security Yen-Cheng Chen Department of Information Management National Chi Nan University ycchen@ncnu. edu. tw
 Outline 1. 2. 3. 4. 5. Introduction WLAN Authentication WEP (Wired Equivalent Privacy) IEEE 802. 1 x Conclusion
Outline 1. 2. 3. 4. 5. Introduction WLAN Authentication WEP (Wired Equivalent Privacy) IEEE 802. 1 x Conclusion
 1. Introduction n n Increasing popularity of IEEE 802. 11 Wireless LANs (WLANs) More laptops and PDAs equipped with WLAN interface. (Intel Centrinotm) n n By 2005, over 80 percent of professional notebook PCs will have an WLAN interface. Public Wireless LAN Hotspots n ISPs provide WLAN access services at airports, coffee shops, conference centers, shopping malls, …
1. Introduction n n Increasing popularity of IEEE 802. 11 Wireless LANs (WLANs) More laptops and PDAs equipped with WLAN interface. (Intel Centrinotm) n n By 2005, over 80 percent of professional notebook PCs will have an WLAN interface. Public Wireless LAN Hotspots n ISPs provide WLAN access services at airports, coffee shops, conference centers, shopping malls, …
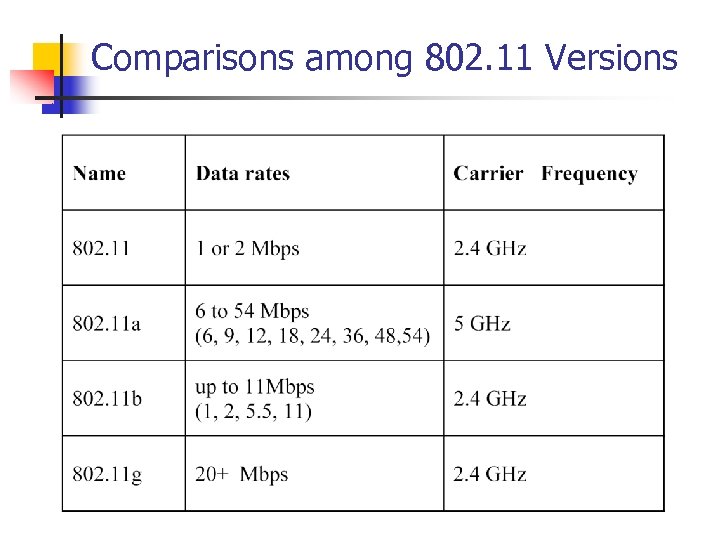 Comparisons among 802. 11 Versions
Comparisons among 802. 11 Versions
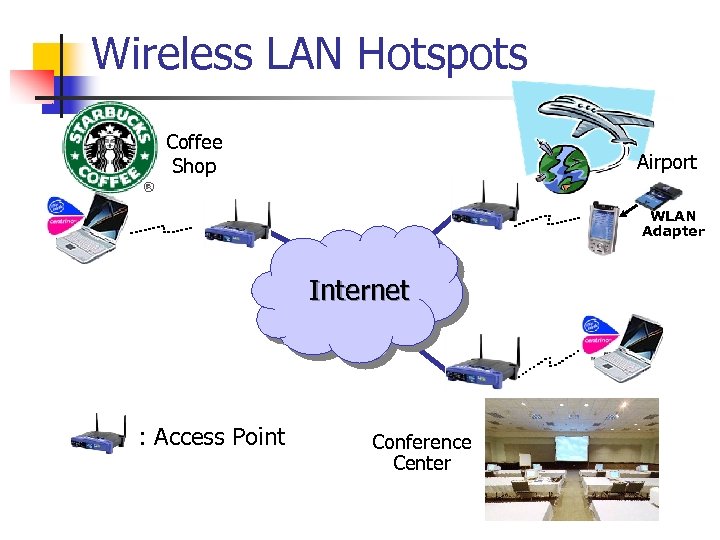 Wireless LAN Hotspots Coffee Shop Airport WLAN Adapter Internet : Access Point Conference Center
Wireless LAN Hotspots Coffee Shop Airport WLAN Adapter Internet : Access Point Conference Center
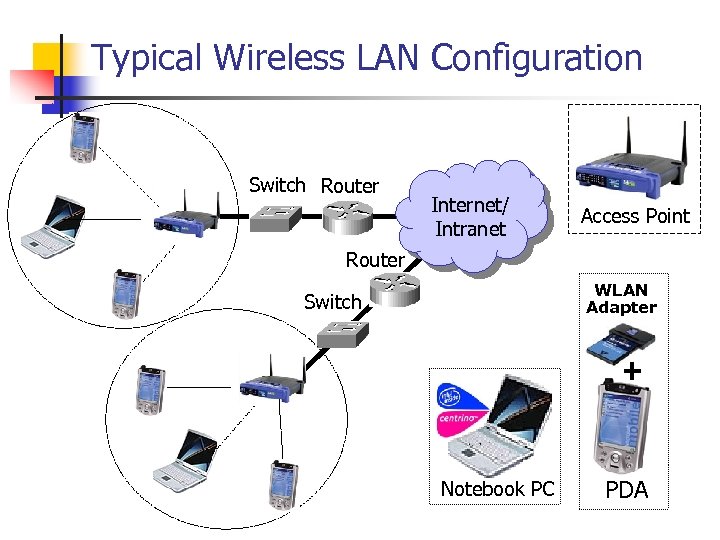 Typical Wireless LAN Configuration Switch Router Internet/ Intranet Access Point Router WLAN Adapter Switch + Notebook PC PDA
Typical Wireless LAN Configuration Switch Router Internet/ Intranet Access Point Router WLAN Adapter Switch + Notebook PC PDA
 IEEE 802. 11 Association Services n Three association services defined in 802. 11 n Association Service: Service n n Reassociation Service: Service n n Before a mobile client is allowed to send a data message via an AP, it shall first become associated with the AP. The reassociation service is invoked to “move” a current association from one AP to another. Disassociation Service: Service n The disassociation service is invoked whenever an existing association is to be terminated.
IEEE 802. 11 Association Services n Three association services defined in 802. 11 n Association Service: Service n n Reassociation Service: Service n n Before a mobile client is allowed to send a data message via an AP, it shall first become associated with the AP. The reassociation service is invoked to “move” a current association from one AP to another. Disassociation Service: Service n The disassociation service is invoked whenever an existing association is to be terminated.
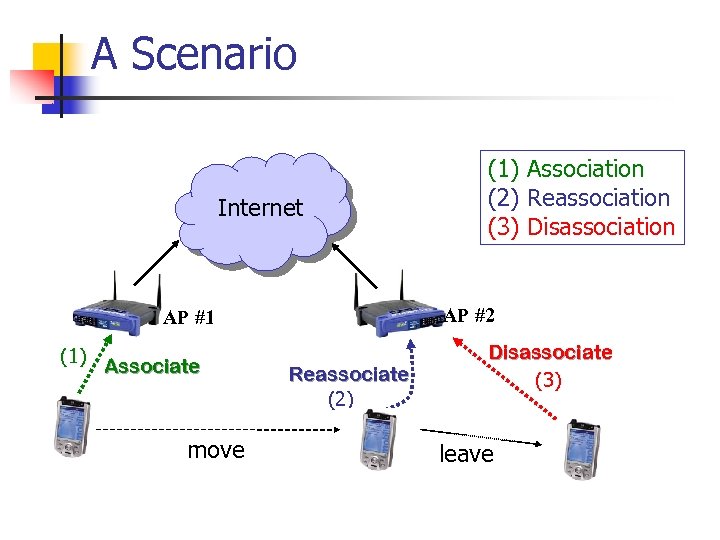 A Scenario Internet AP #2 AP #1 (1) Associate move (1) Association (2) Reassociation (3) Disassociation Reassociate (2) Disassociate (3) leave
A Scenario Internet AP #2 AP #1 (1) Associate move (1) Association (2) Reassociation (3) Disassociation Reassociate (2) Disassociate (3) leave
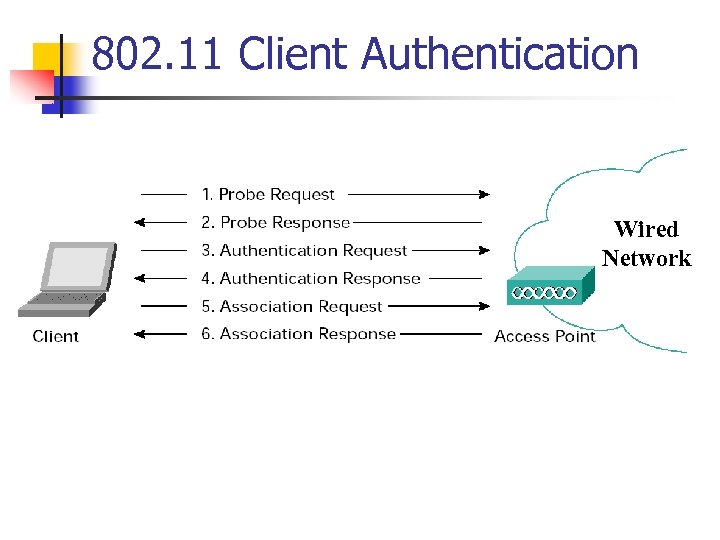 802. 11 Client Authentication Wired Network
802. 11 Client Authentication Wired Network
 802. 11 Client Authentication 1. Client broadcasts a probe request frame on every channel 2. Access points within range respond with a probe response frame 3. The client decides which access point (AP) is the best for access and sends an authentication request 4. The access point will send an authentication reply 5. Upon successful authentication, the client will send an association request frame to the access point 6. The access point will reply with an association response 7. The client is now able to pass traffic to the access point
802. 11 Client Authentication 1. Client broadcasts a probe request frame on every channel 2. Access points within range respond with a probe response frame 3. The client decides which access point (AP) is the best for access and sends an authentication request 4. The access point will send an authentication reply 5. Upon successful authentication, the client will send an association request frame to the access point 6. The access point will reply with an association response 7. The client is now able to pass traffic to the access point
 Security Threats n n n Data transmitted can be easily intercepted. Signal coverage area cannot be well limited. Intentional and non-intentional interference. n n User authentication to prevent unauthorized access to network resources Data privacy to protect the integrity and privacy of transmitted data
Security Threats n n n Data transmitted can be easily intercepted. Signal coverage area cannot be well limited. Intentional and non-intentional interference. n n User authentication to prevent unauthorized access to network resources Data privacy to protect the integrity and privacy of transmitted data
 2. WLAN Authentication n SSIDs (Service Set IDs) n Open Authentication n Shared Key Authentication n MAC Address Authentication
2. WLAN Authentication n SSIDs (Service Set IDs) n Open Authentication n Shared Key Authentication n MAC Address Authentication
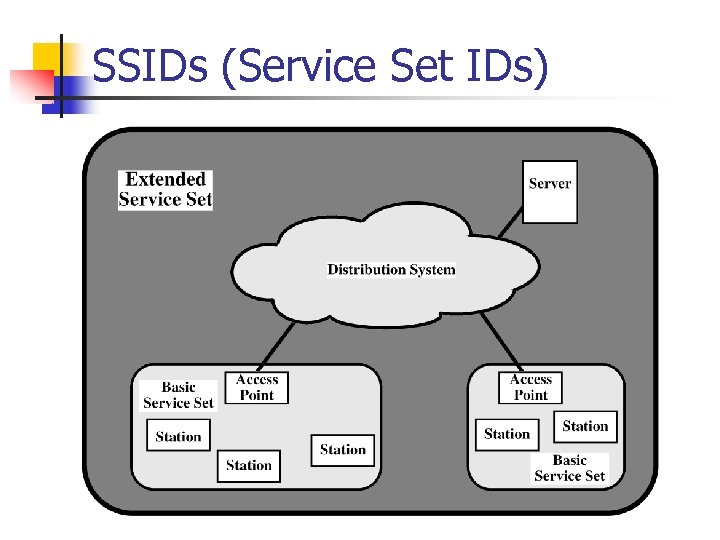 SSIDs (Service Set IDs)
SSIDs (Service Set IDs)
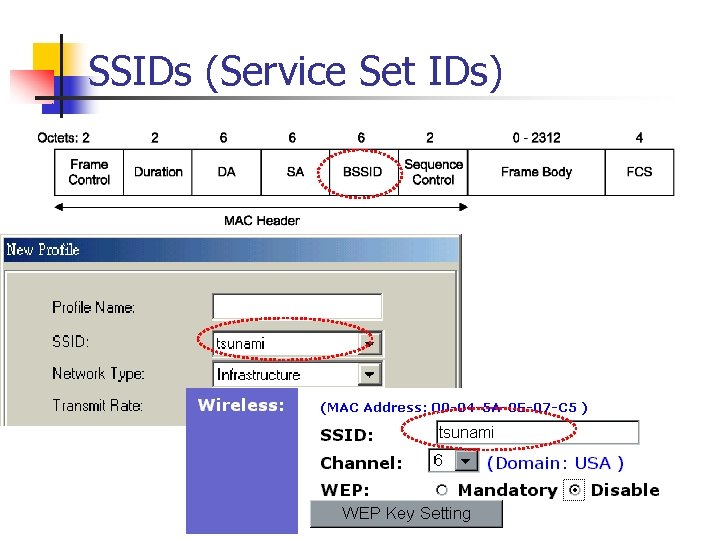 SSIDs (Service Set IDs)
SSIDs (Service Set IDs)
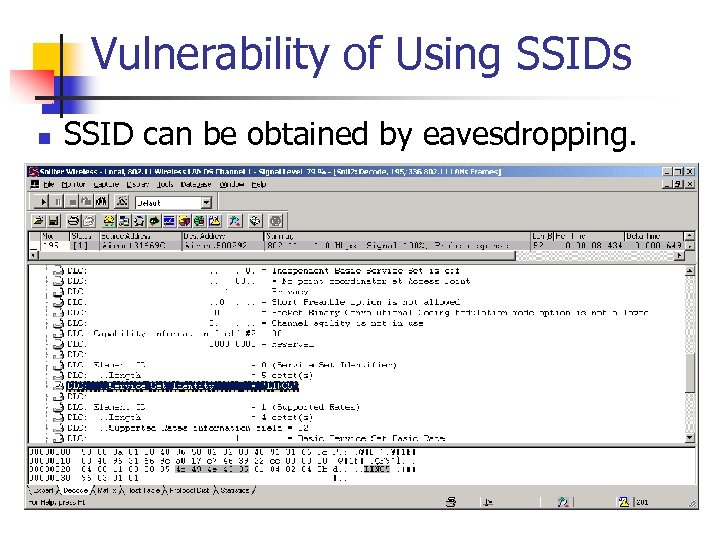 Vulnerability of Using SSIDs n SSID can be obtained by eavesdropping.
Vulnerability of Using SSIDs n SSID can be obtained by eavesdropping.
 Open Authentication n Null authentication Some hand-held devices do not have capabilities for complex authentication algorithms. Any device that knows the SSID can gain access to the WLAN.
Open Authentication n Null authentication Some hand-held devices do not have capabilities for complex authentication algorithms. Any device that knows the SSID can gain access to the WLAN.
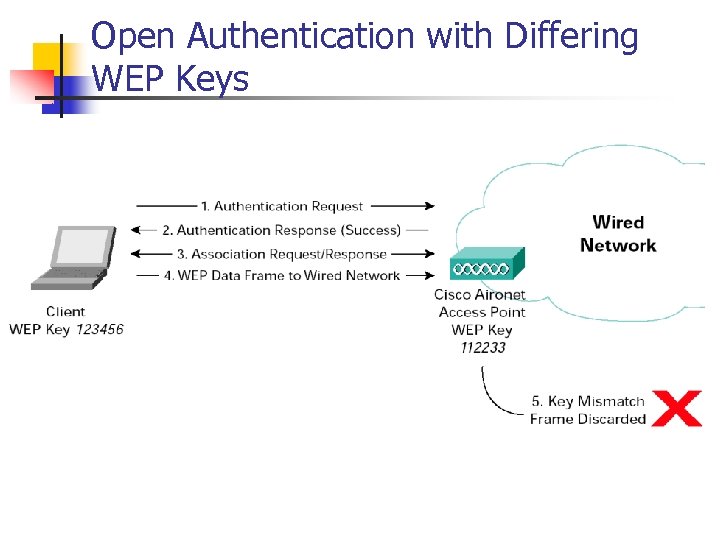 Open Authentication with Differing WEP Keys
Open Authentication with Differing WEP Keys
 Shared Key Authentication 1. The client sends an authentication request to the access point requesting shared key authentication 2. The access point responds with an authentication response containing challenge text 3. The client uses its locally configured WEP key to encrypt the challenge text and reply with a subsequent authentication request 4. If the access point can decrypt the authentication request and retrieve the original challenge text, then it responds with an authentication response that grants the client access
Shared Key Authentication 1. The client sends an authentication request to the access point requesting shared key authentication 2. The access point responds with an authentication response containing challenge text 3. The client uses its locally configured WEP key to encrypt the challenge text and reply with a subsequent authentication request 4. If the access point can decrypt the authentication request and retrieve the original challenge text, then it responds with an authentication response that grants the client access
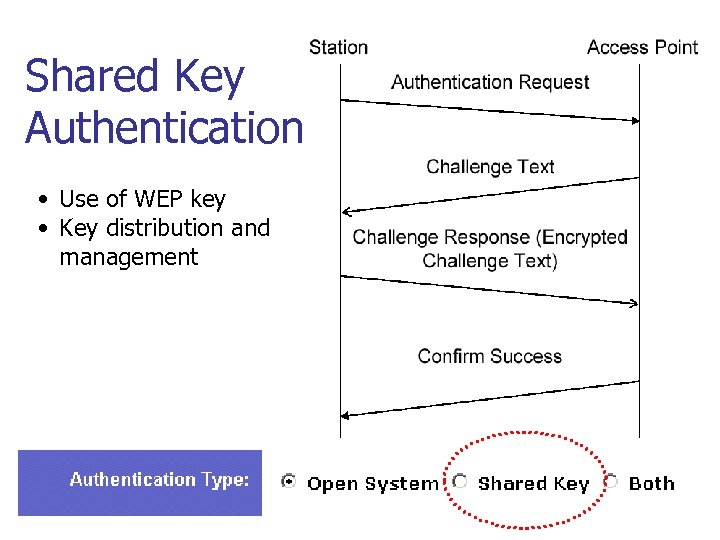 Shared Key Authentication • Use of WEP key • Key distribution and management
Shared Key Authentication • Use of WEP key • Key distribution and management
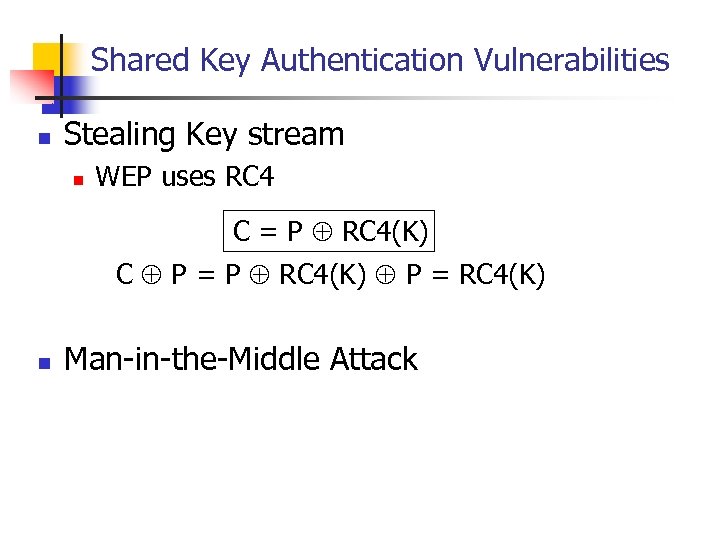 Shared Key Authentication Vulnerabilities n Stealing Key stream n WEP uses RC 4 C = P RC 4(K) C P = P RC 4(K) P = RC 4(K) n Man-in-the-Middle Attack
Shared Key Authentication Vulnerabilities n Stealing Key stream n WEP uses RC 4 C = P RC 4(K) C P = P RC 4(K) P = RC 4(K) n Man-in-the-Middle Attack
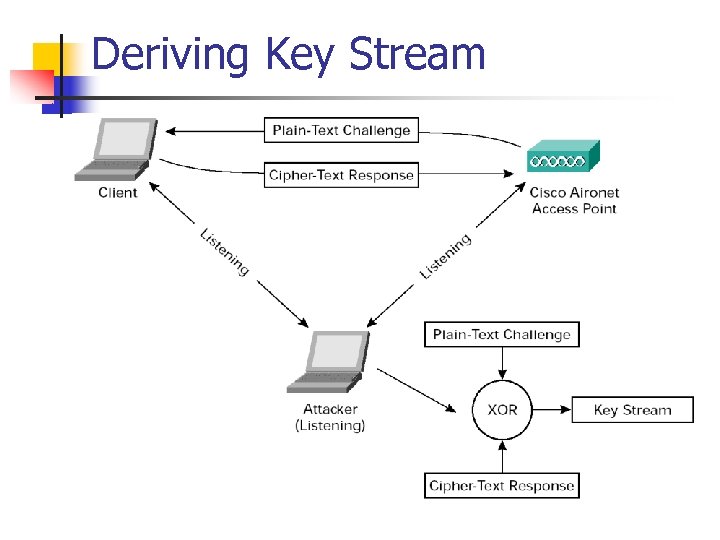 Deriving Key Stream
Deriving Key Stream
 MAC Address Authentication n Not specified in 802. 11 Many AP products support MAC address authentication verifies the client’s MAC address against a locally configured list of allowed addresses or against an external authentication server.
MAC Address Authentication n Not specified in 802. 11 Many AP products support MAC address authentication verifies the client’s MAC address against a locally configured list of allowed addresses or against an external authentication server.
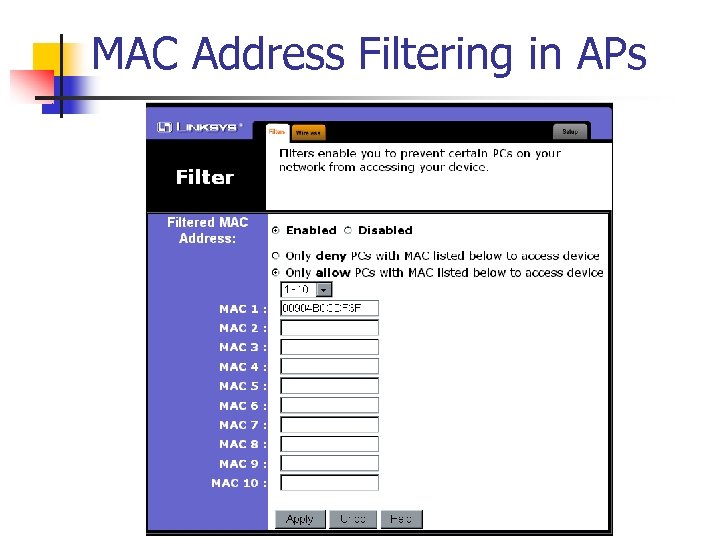 MAC Address Filtering in APs
MAC Address Filtering in APs
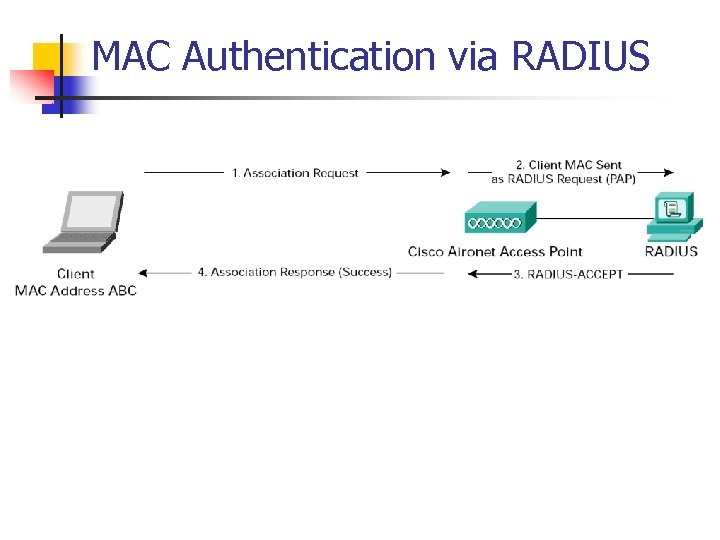 MAC Authentication via RADIUS
MAC Authentication via RADIUS
 MAC Address Authentication Vulnerabilities n MAC Address Spoofing n n Valid MAC addresses can be observed by a protocol analyzer. The MACs of some WLAN NICs can be overwritten.
MAC Address Authentication Vulnerabilities n MAC Address Spoofing n n Valid MAC addresses can be observed by a protocol analyzer. The MACs of some WLAN NICs can be overwritten.
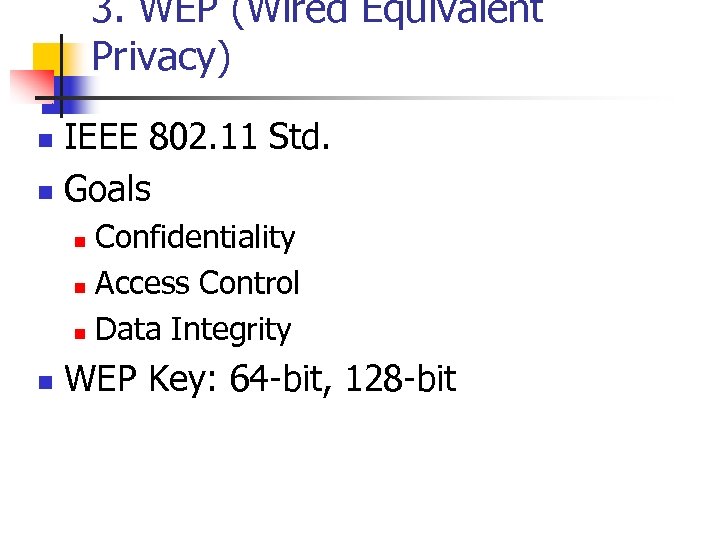 3. WEP (Wired Equivalent Privacy) IEEE 802. 11 Std. n Goals n Confidentiality n Access Control n Data Integrity n n WEP Key: 64 -bit, 128 -bit
3. WEP (Wired Equivalent Privacy) IEEE 802. 11 Std. n Goals n Confidentiality n Access Control n Data Integrity n n WEP Key: 64 -bit, 128 -bit
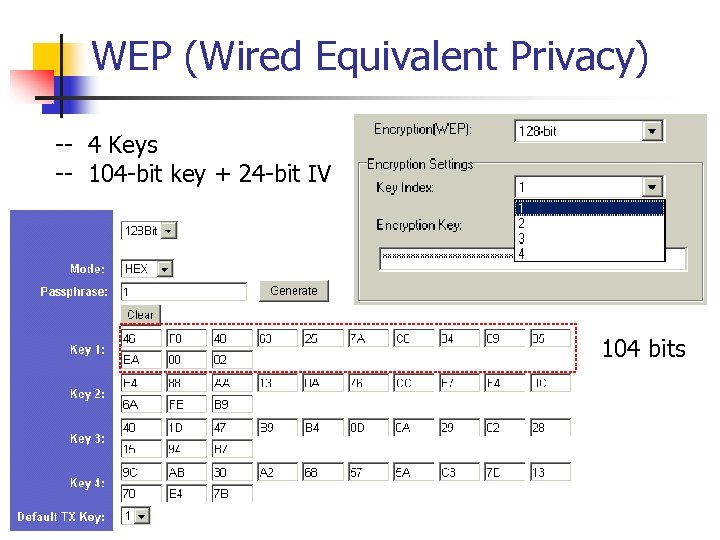 WEP (Wired Equivalent Privacy) -- 4 Keys -- 104 -bit key + 24 -bit IV 104 bits
WEP (Wired Equivalent Privacy) -- 4 Keys -- 104 -bit key + 24 -bit IV 104 bits
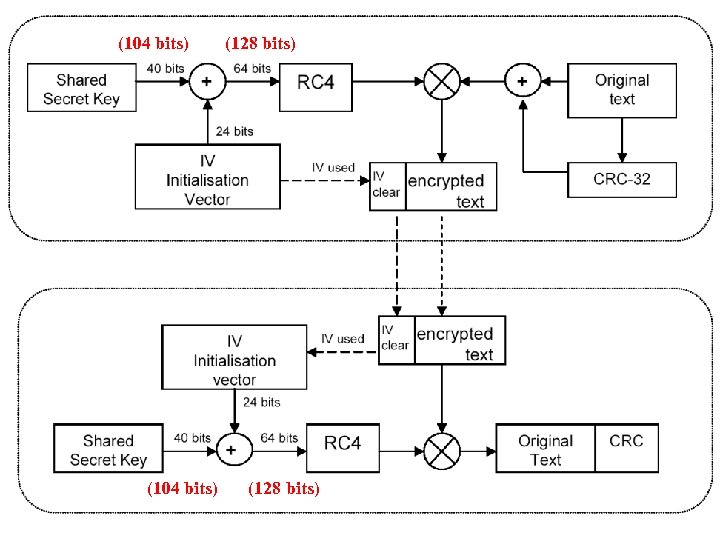 (104 bits) (128 bits)
(104 bits) (128 bits)
 WEP Vulnerabilities n Key attacks n n n Statistical key derivation – Several IVs can reveal key bytes after statistical analysis. Secret key problems Confidentiality attacks Integrity attacks Authentication attack
WEP Vulnerabilities n Key attacks n n n Statistical key derivation – Several IVs can reveal key bytes after statistical analysis. Secret key problems Confidentiality attacks Integrity attacks Authentication attack
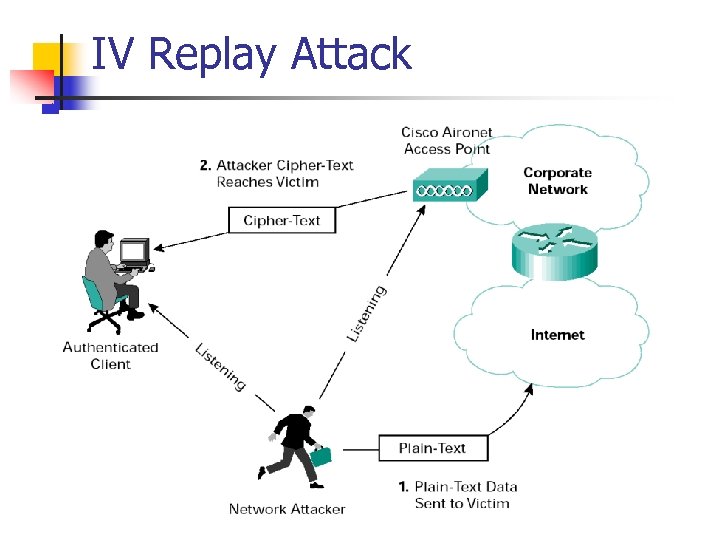 IV Replay Attack
IV Replay Attack
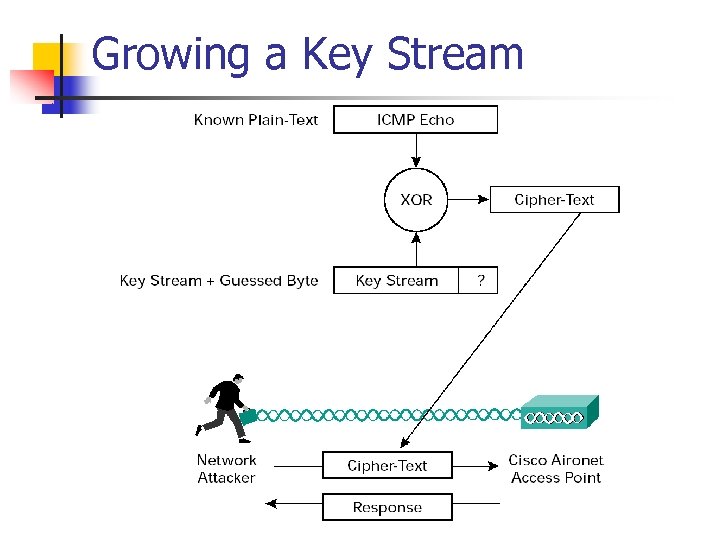 Growing a Key Stream
Growing a Key Stream
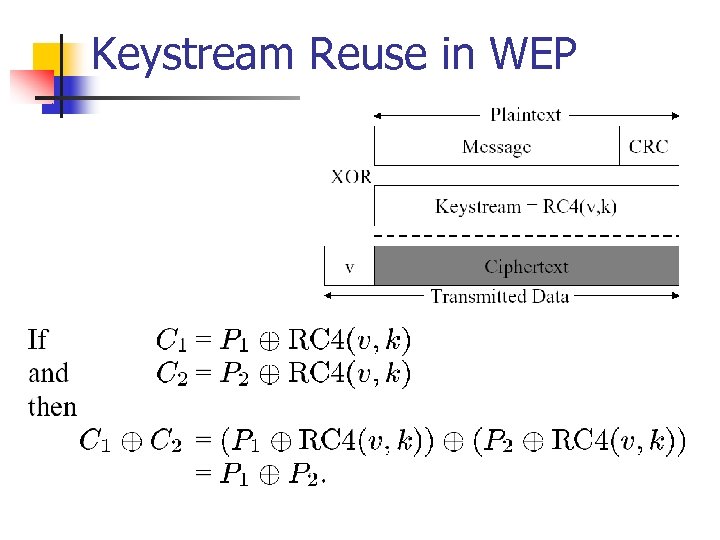 Keystream Reuse in WEP
Keystream Reuse in WEP
 Keystream Reuse in WEP n n n WEP standard recommends that IV be changed after every packet. Many WLAN cards reset the IV to 0 each time they were re-initialized, and then incremented the IV by one after each packet transmitted. IV is only 24 bits wide. 1500 byte packets, 5 Mbps bandwidth half of a day
Keystream Reuse in WEP n n n WEP standard recommends that IV be changed after every packet. Many WLAN cards reset the IV to 0 each time they were re-initialized, and then incremented the IV by one after each packet transmitted. IV is only 24 bits wide. 1500 byte packets, 5 Mbps bandwidth half of a day
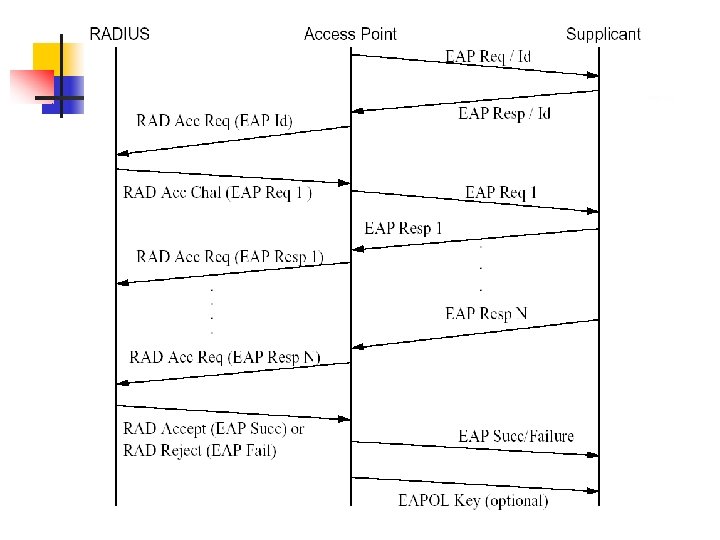
 4. IEEE 802. 1 X n n Port-Based Network Access Control To provide a means of authenticating and authorizing devices attached to a LAN port that has point-to-point connection characteristics To prevent access to that port in cases in which the authentication and authorization process fails. 802. 1 X requires three entities: n n n The supplicant—resides on the wireless LAN client The authenticator—resides on the access point The authentication server—EAP server, mostly RADIUS server
4. IEEE 802. 1 X n n Port-Based Network Access Control To provide a means of authenticating and authorizing devices attached to a LAN port that has point-to-point connection characteristics To prevent access to that port in cases in which the authentication and authorization process fails. 802. 1 X requires three entities: n n n The supplicant—resides on the wireless LAN client The authenticator—resides on the access point The authentication server—EAP server, mostly RADIUS server
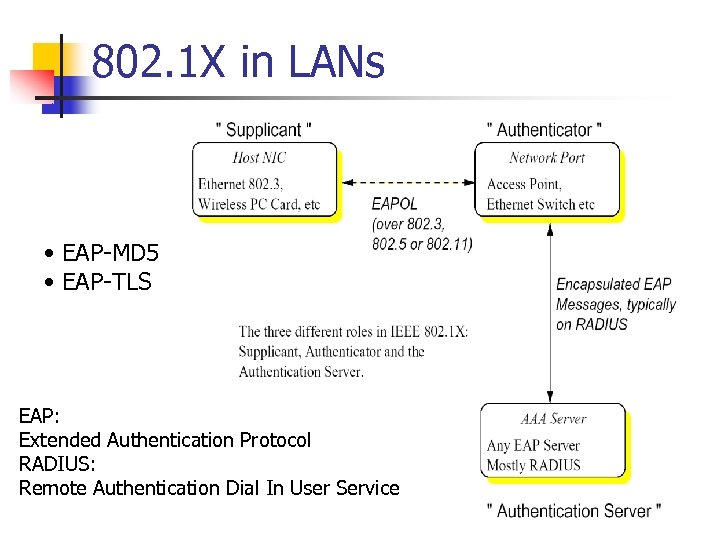 802. 1 X in LANs • EAP-MD 5 • EAP-TLS EAP: Extended Authentication Protocol RADIUS: Remote Authentication Dial In User Service
802. 1 X in LANs • EAP-MD 5 • EAP-TLS EAP: Extended Authentication Protocol RADIUS: Remote Authentication Dial In User Service
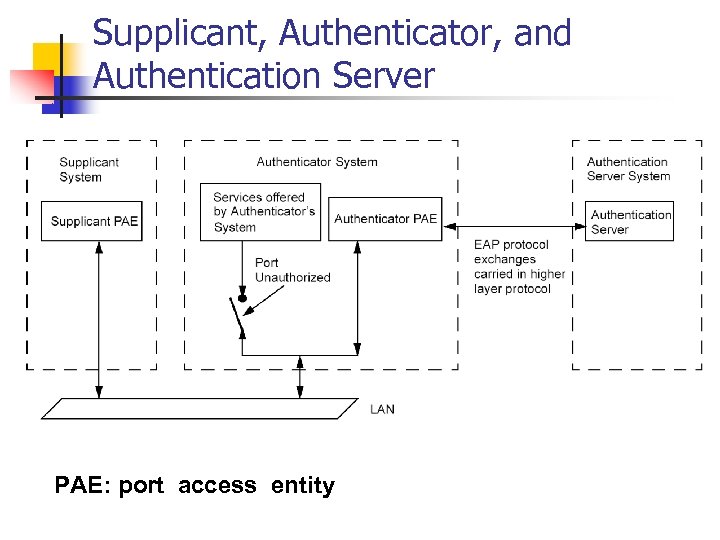 Supplicant, Authenticator, and Authentication Server PAE: port access entity
Supplicant, Authenticator, and Authentication Server PAE: port access entity
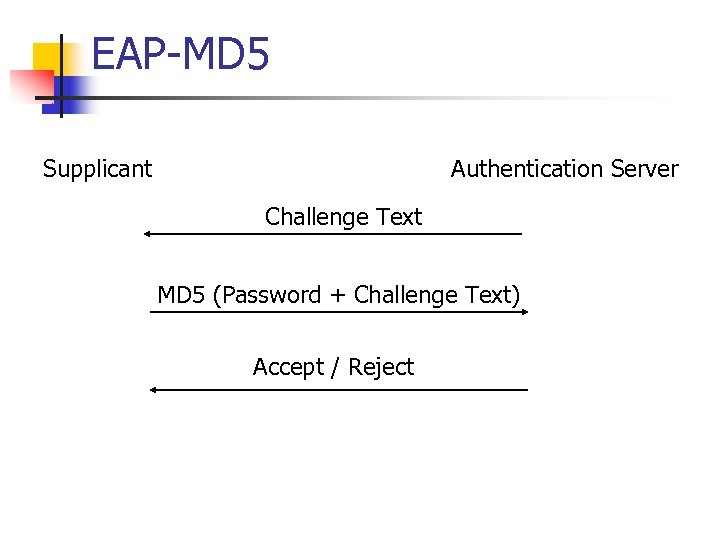 EAP-MD 5 Supplicant Authentication Server Challenge Text MD 5 (Password + Challenge Text) Accept / Reject
EAP-MD 5 Supplicant Authentication Server Challenge Text MD 5 (Password + Challenge Text) Accept / Reject
 EAP-TLS n n TLS: Transport Layer Security Use TLS public key certification mechanism within EAP. Digital certificate signed by CA Mutual Authentication n Client Certificate Server Certificate Key exchange / Dynamic session key
EAP-TLS n n TLS: Transport Layer Security Use TLS public key certification mechanism within EAP. Digital certificate signed by CA Mutual Authentication n Client Certificate Server Certificate Key exchange / Dynamic session key
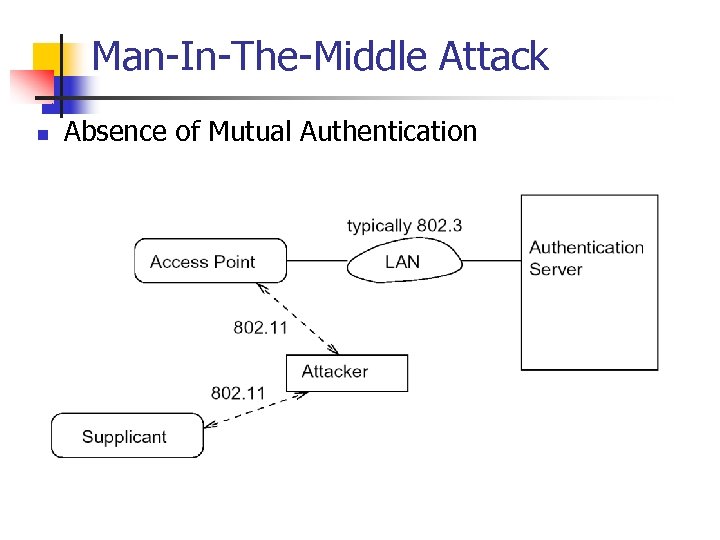 Man-In-The-Middle Attack n Absence of Mutual Authentication
Man-In-The-Middle Attack n Absence of Mutual Authentication
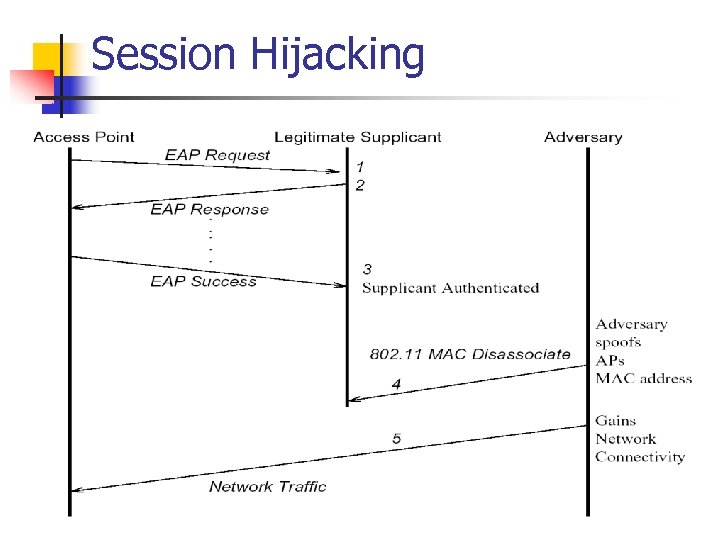 Session Hijacking
Session Hijacking
 5. Conclusion n IEEE 802. 11 i n n n Certificate based authentication n n TKIP: Temporal Key Integrity Protocol AES: Advanced Encryption Standard EAP-TLS, EAP-TTLS, PEAP Password authentication n n LEAP, Diffie-Hellman exchange, SPEKE: ZKPP(Zero Knowledge Password Proof)
5. Conclusion n IEEE 802. 11 i n n n Certificate based authentication n n TKIP: Temporal Key Integrity Protocol AES: Advanced Encryption Standard EAP-TLS, EAP-TTLS, PEAP Password authentication n n LEAP, Diffie-Hellman exchange, SPEKE: ZKPP(Zero Knowledge Password Proof)
 Reference “A Comprehensive Review of 802. 11 Wireless LAN Security and the Cisco Wireless Security Suite” http: //www. cisco. com/warp/public/cc/pd/witc/ao 1200 ap/prodlit/wswpf_wp. pdf “Intercepting Mobile Communications: the Insecurity of 802. 11”, 802. 11” Borisov, N. , Goldberg, I. , and Wagner, D. , Proc. Of the 7 th ACM International Conference on Mobile Computing and Networking, Rome, July 2001. “An Initial Analysis of the IEEE 802. 1 X Standard”, Standard” Mishra, A. , Arbaugh, W. A. , University of Maryland, February 2002. “IEEE Std 802. 11 Wireless LAN Medium Access Control and Physical Layer Specifications” IEEE, 1999
Reference “A Comprehensive Review of 802. 11 Wireless LAN Security and the Cisco Wireless Security Suite” http: //www. cisco. com/warp/public/cc/pd/witc/ao 1200 ap/prodlit/wswpf_wp. pdf “Intercepting Mobile Communications: the Insecurity of 802. 11”, 802. 11” Borisov, N. , Goldberg, I. , and Wagner, D. , Proc. Of the 7 th ACM International Conference on Mobile Computing and Networking, Rome, July 2001. “An Initial Analysis of the IEEE 802. 1 X Standard”, Standard” Mishra, A. , Arbaugh, W. A. , University of Maryland, February 2002. “IEEE Std 802. 11 Wireless LAN Medium Access Control and Physical Layer Specifications” IEEE, 1999


