3de1888d74398634c5f14dfdbd14d0dc.ppt
- Количество слайдов: 131
 Wireless LAN Overview Wi-Fi Technology • Wireless Fidelity (Wi-Fi) • Channels • Basic Security&Practices • Vulnerabilities • WAP • 802. 11 i
Wireless LAN Overview Wi-Fi Technology • Wireless Fidelity (Wi-Fi) • Channels • Basic Security&Practices • Vulnerabilities • WAP • 802. 11 i
 Wireless LAN Overview EAP and 802. 1 x • 802. 1 x • EAP – Definition – Process Flow • EAP Types and Flow
Wireless LAN Overview EAP and 802. 1 x • 802. 1 x • EAP – Definition – Process Flow • EAP Types and Flow
 Wi-Fi Technology
Wi-Fi Technology
 Wi-Fi • Wi-Fi (short for “Wireless Fidelity") is the popular term for a high-frequency wireless local area network (WLAN) – Promoted by the Wi-Fi Alliance (Formerly WECA - Wireless Ethernet Carriers Association) • Used generically when referring to any type of 802. 11 network, whether 802. 11 a, 802. 11 b, 802. 11 g, dualband, etc. The term is promulgated by the Wi-Fi Alliance
Wi-Fi • Wi-Fi (short for “Wireless Fidelity") is the popular term for a high-frequency wireless local area network (WLAN) – Promoted by the Wi-Fi Alliance (Formerly WECA - Wireless Ethernet Carriers Association) • Used generically when referring to any type of 802. 11 network, whether 802. 11 a, 802. 11 b, 802. 11 g, dualband, etc. The term is promulgated by the Wi-Fi Alliance
 Wi-Fi • Wi-Fi standards use the Ethernet protocol and CSMA/CA (carrier sense multiple access with collision avoidance) for path sharing • The 802. 11 b (Wi-Fi) technology operates in the 2. 4 GHz range offering data speeds up to 11 megabits per second. The modulation used in 802. 11 has historically been phase-shift keying (PSK). – Note, unless adequately protected, a Wi-Fi wireless LAN is easily accessible by unauthorized users
Wi-Fi • Wi-Fi standards use the Ethernet protocol and CSMA/CA (carrier sense multiple access with collision avoidance) for path sharing • The 802. 11 b (Wi-Fi) technology operates in the 2. 4 GHz range offering data speeds up to 11 megabits per second. The modulation used in 802. 11 has historically been phase-shift keying (PSK). – Note, unless adequately protected, a Wi-Fi wireless LAN is easily accessible by unauthorized users
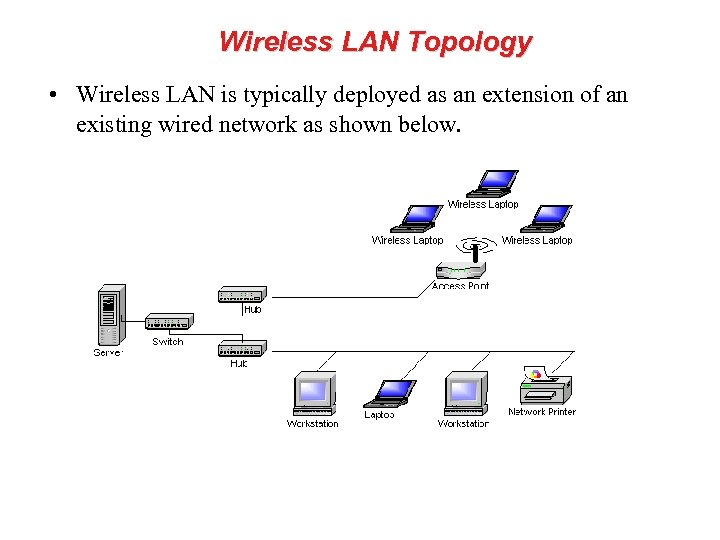 Wireless LAN Topology • Wireless LAN is typically deployed as an extension of an existing wired network as shown below.
Wireless LAN Topology • Wireless LAN is typically deployed as an extension of an existing wired network as shown below.
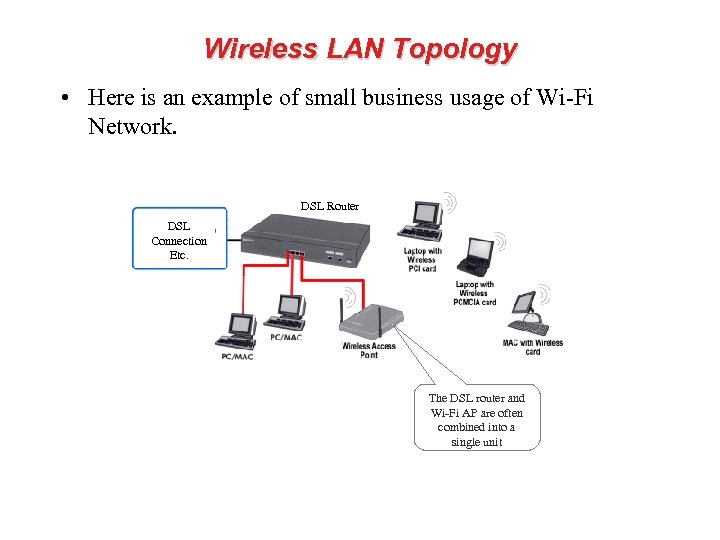 Wireless LAN Topology • Here is an example of small business usage of Wi-Fi Network. DSL Router DSL Connection Etc. The DSL router and Wi-Fi AP are often combined into a single unit
Wireless LAN Topology • Here is an example of small business usage of Wi-Fi Network. DSL Router DSL Connection Etc. The DSL router and Wi-Fi AP are often combined into a single unit
 What is 802. 11? • 802. 11 refers to a family of specifications developed by the IEEE for wireless LAN technology. 802. 11 specifies an over-the-air interface between a wireless client and a base station or between two wireless clients. • The IEEE accepted the specification in 1997.
What is 802. 11? • 802. 11 refers to a family of specifications developed by the IEEE for wireless LAN technology. 802. 11 specifies an over-the-air interface between a wireless client and a base station or between two wireless clients. • The IEEE accepted the specification in 1997.
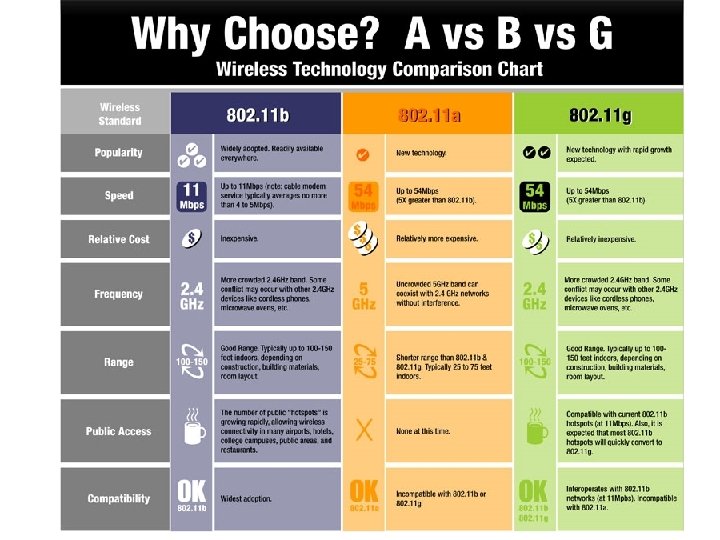
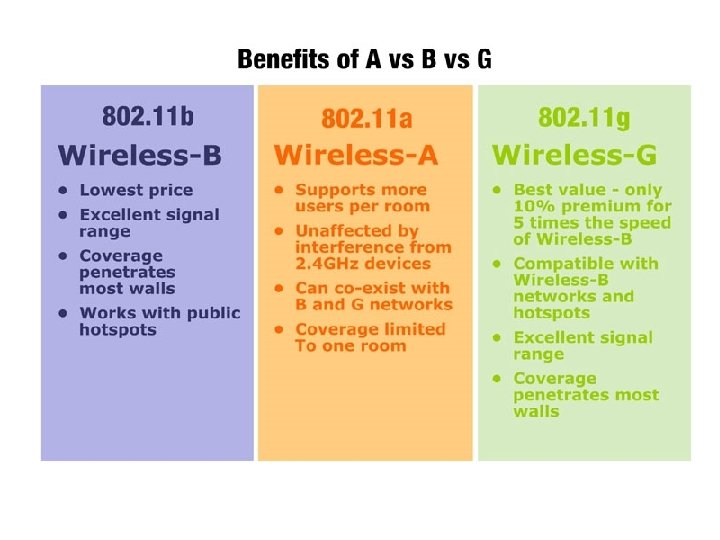
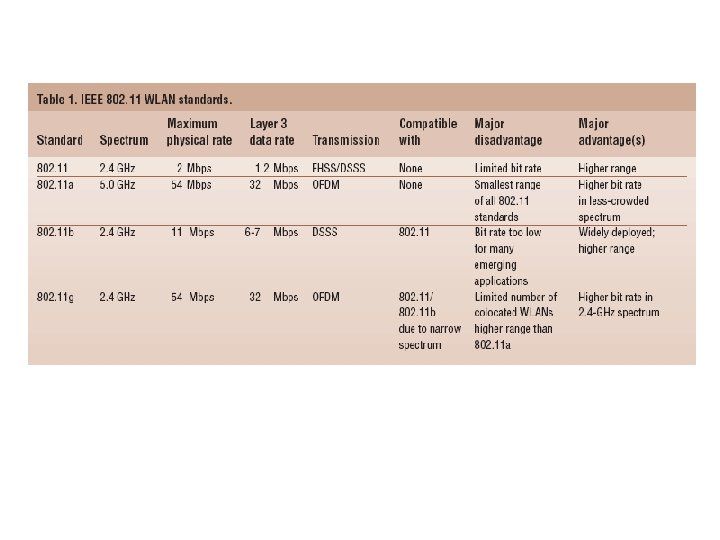
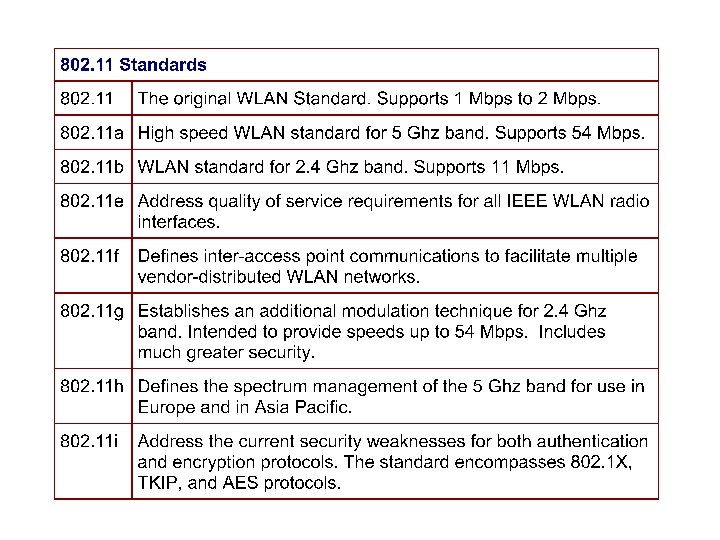
 802. 11 Family Members • There are several specifications in the 802. 11 family: • 802. 11 – Applies to wireless LANs and provides 1 or 2 Mbps transmission in the 2. 4 GHz band using either frequency hopping spread spectrum (FHSS) or direct sequence spread spectrum (DSSS). • 802. 11 a – An extension to 802. 11 that applies to wireless LANs and provides up to 54 Mbps in the 5 GHz band. 802. 11 a uses an orthogonal frequency division multiplexing encoding scheme rather than FHSS or DSSS. • 802. 11 b – (also referred to as 802. 11 High Rate or Wi-Fi) is an extension to 802. 11 that applies to wireless LANs and provides 11 Mbps transmission (with a fallback to 5. 5, 2 and 1 Mbps) in the 2. 4 GHz band. 802. 11 b uses only DSSS. 802. 11 b was a 1999 ratification to the original 802. 11 standard, allowing wireless functionality comparable to Ethernet. • 802. 11 g – Applies to wireless LANs and provides 20+ Mbps in the 2. 4 GHz band.
802. 11 Family Members • There are several specifications in the 802. 11 family: • 802. 11 – Applies to wireless LANs and provides 1 or 2 Mbps transmission in the 2. 4 GHz band using either frequency hopping spread spectrum (FHSS) or direct sequence spread spectrum (DSSS). • 802. 11 a – An extension to 802. 11 that applies to wireless LANs and provides up to 54 Mbps in the 5 GHz band. 802. 11 a uses an orthogonal frequency division multiplexing encoding scheme rather than FHSS or DSSS. • 802. 11 b – (also referred to as 802. 11 High Rate or Wi-Fi) is an extension to 802. 11 that applies to wireless LANs and provides 11 Mbps transmission (with a fallback to 5. 5, 2 and 1 Mbps) in the 2. 4 GHz band. 802. 11 b uses only DSSS. 802. 11 b was a 1999 ratification to the original 802. 11 standard, allowing wireless functionality comparable to Ethernet. • 802. 11 g – Applies to wireless LANs and provides 20+ Mbps in the 2. 4 GHz band.
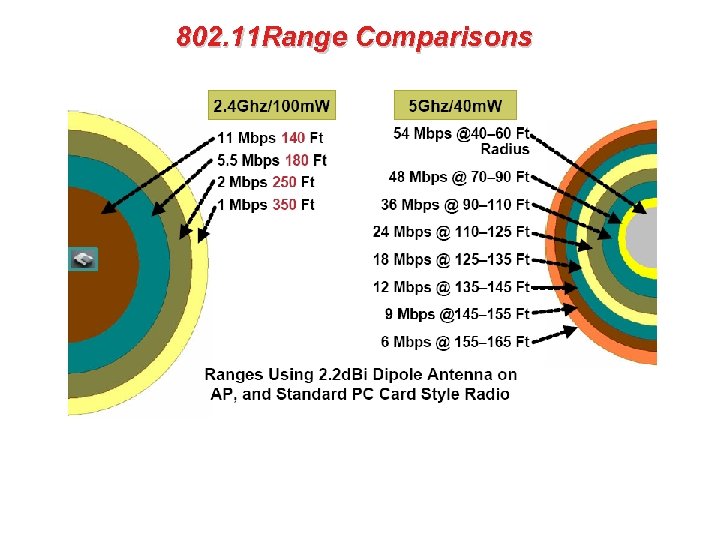 802. 11 Range Comparisons
802. 11 Range Comparisons
 • 802. 11 Authentication The 802. 11 standard defines several services that govern how two 802. 11 devices communicate. The following events must occur before an 802. 11 station can communicate with an Ethernet network through a wireless access point provides: 1. 2. 3. 4. 5. 6. 7. Turn on the wireless Client listens for messages from any access points (AP) that are in range Client finds a message from an AP that has a matching SSID Client sends an authentication request to the AP AP authenticates the station Client sends an association request to the AP AP associates with the station 8. Client can now communicate with the Ethernet network thru the AP
• 802. 11 Authentication The 802. 11 standard defines several services that govern how two 802. 11 devices communicate. The following events must occur before an 802. 11 station can communicate with an Ethernet network through a wireless access point provides: 1. 2. 3. 4. 5. 6. 7. Turn on the wireless Client listens for messages from any access points (AP) that are in range Client finds a message from an AP that has a matching SSID Client sends an authentication request to the AP AP authenticates the station Client sends an association request to the AP AP associates with the station 8. Client can now communicate with the Ethernet network thru the AP
 What Exactly Is 802. 1 x? • Standard set by the IEEE 802. 1 working group. • Describes a standard link layer protocol used for transporting higher-level authentication protocols. • Works between the Supplicant (Client Software) and the Authenticator (Network Device). • Maintains backend communication to an Authentication (Typically RADIUS) Server.
What Exactly Is 802. 1 x? • Standard set by the IEEE 802. 1 working group. • Describes a standard link layer protocol used for transporting higher-level authentication protocols. • Works between the Supplicant (Client Software) and the Authenticator (Network Device). • Maintains backend communication to an Authentication (Typically RADIUS) Server.
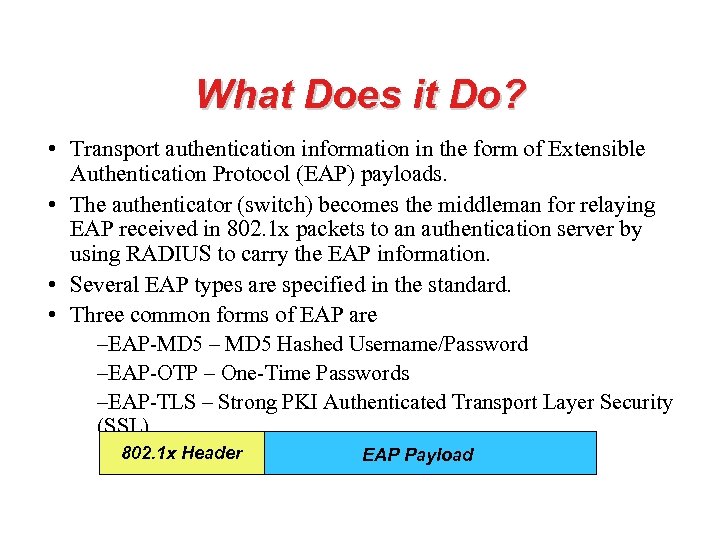 What Does it Do? • Transport authentication information in the form of Extensible Authentication Protocol (EAP) payloads. • The authenticator (switch) becomes the middleman for relaying EAP received in 802. 1 x packets to an authentication server by using RADIUS to carry the EAP information. • Several EAP types are specified in the standard. • Three common forms of EAP are –EAP-MD 5 – MD 5 Hashed Username/Password –EAP-OTP – One-Time Passwords –EAP-TLS – Strong PKI Authenticated Transport Layer Security (SSL) 802. 1 x Header EAP Payload
What Does it Do? • Transport authentication information in the form of Extensible Authentication Protocol (EAP) payloads. • The authenticator (switch) becomes the middleman for relaying EAP received in 802. 1 x packets to an authentication server by using RADIUS to carry the EAP information. • Several EAP types are specified in the standard. • Three common forms of EAP are –EAP-MD 5 – MD 5 Hashed Username/Password –EAP-OTP – One-Time Passwords –EAP-TLS – Strong PKI Authenticated Transport Layer Security (SSL) 802. 1 x Header EAP Payload
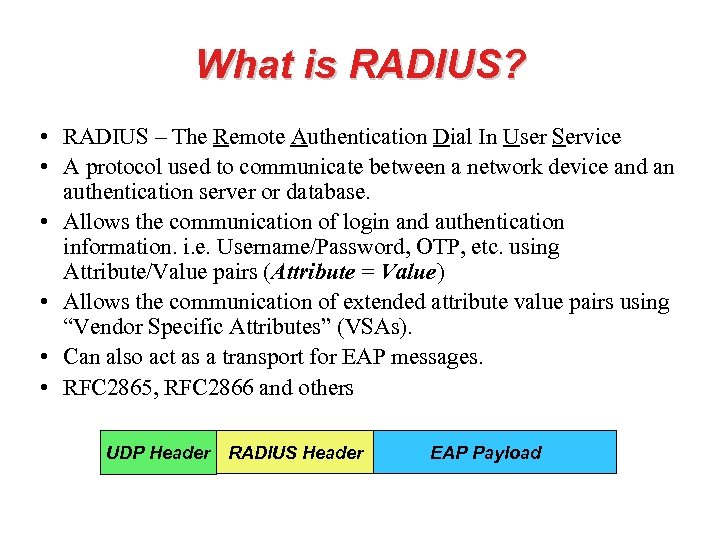 What is RADIUS? • RADIUS – The Remote Authentication Dial In User Service • A protocol used to communicate between a network device and an authentication server or database. • Allows the communication of login and authentication information. i. e. Username/Password, OTP, etc. using Attribute/Value pairs (Attribute = Value) • Allows the communication of extended attribute value pairs using “Vendor Specific Attributes” (VSAs). • Can also act as a transport for EAP messages. • RFC 2865, RFC 2866 and others UDP Header RADIUS Header EAP Payload
What is RADIUS? • RADIUS – The Remote Authentication Dial In User Service • A protocol used to communicate between a network device and an authentication server or database. • Allows the communication of login and authentication information. i. e. Username/Password, OTP, etc. using Attribute/Value pairs (Attribute = Value) • Allows the communication of extended attribute value pairs using “Vendor Specific Attributes” (VSAs). • Can also act as a transport for EAP messages. • RFC 2865, RFC 2866 and others UDP Header RADIUS Header EAP Payload
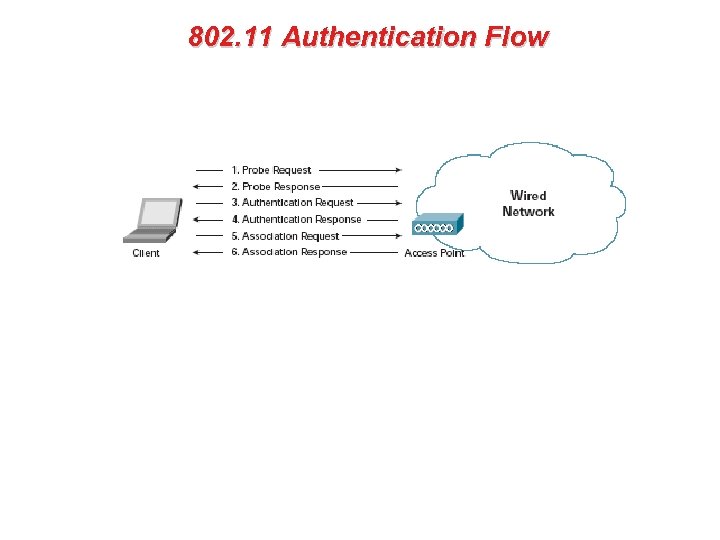 802. 11 Authentication Flow
802. 11 Authentication Flow
 Wi-Fi Channels • Wireless LAN communications are based on the use of radio signals to exchange information through an association between a wireless LAN card and a nearby access point. • Each access point in an 802. 11 b/g network is configured to use one radio frequency (RF) channel. • Although the 802. 11 b/g specifications indicate that there are fourteen (14) channels that can be utilized for wireless communications, in the U. S. , there are only eleven channels allowed for AP use. In addition, since there is frequency overlap among many of the channels, there must be 22 MHz separation between any two channels in use.
Wi-Fi Channels • Wireless LAN communications are based on the use of radio signals to exchange information through an association between a wireless LAN card and a nearby access point. • Each access point in an 802. 11 b/g network is configured to use one radio frequency (RF) channel. • Although the 802. 11 b/g specifications indicate that there are fourteen (14) channels that can be utilized for wireless communications, in the U. S. , there are only eleven channels allowed for AP use. In addition, since there is frequency overlap among many of the channels, there must be 22 MHz separation between any two channels in use.
 Wi-Fi Channels • In a multi-access point installation, where overlapping channels can cause interference, dead-spots and other problems, Channels 1, 6 and 11 are generally regarded as the only safe channels to use. Since there are 5 5 MHz channels between 1 and 6, and between 6 and 11, or 25 MHz of total bandwidth, that leaves three MHz of buffer zone between channels. • In practice, this constraint limits the number of useable channels to three (channels 1, 6, and 11). 802. 11 a wireless networks have eight non-overlapping channels which provide more flexibility in terms of channel assignment.
Wi-Fi Channels • In a multi-access point installation, where overlapping channels can cause interference, dead-spots and other problems, Channels 1, 6 and 11 are generally regarded as the only safe channels to use. Since there are 5 5 MHz channels between 1 and 6, and between 6 and 11, or 25 MHz of total bandwidth, that leaves three MHz of buffer zone between channels. • In practice, this constraint limits the number of useable channels to three (channels 1, 6, and 11). 802. 11 a wireless networks have eight non-overlapping channels which provide more flexibility in terms of channel assignment.
 Wi-Fi Channels • For example, 802. 11 a - An extension to the IEEE 802. 11 standard that applies to wireless LANs and provides up to 54 Mbps in the 5 GHz band. – For the North American users, equipment available today operates between 5. 15 and 5. 35 GHz. – This bandwidth supports eight separate, non-overlapping 200 MHz channels. • These channels allow users to install up to eight access points set to different channels without interference, making access point channel assignment much easier and significantly increasing the level of throughput the wireless LAN can deliver within a given area.
Wi-Fi Channels • For example, 802. 11 a - An extension to the IEEE 802. 11 standard that applies to wireless LANs and provides up to 54 Mbps in the 5 GHz band. – For the North American users, equipment available today operates between 5. 15 and 5. 35 GHz. – This bandwidth supports eight separate, non-overlapping 200 MHz channels. • These channels allow users to install up to eight access points set to different channels without interference, making access point channel assignment much easier and significantly increasing the level of throughput the wireless LAN can deliver within a given area.
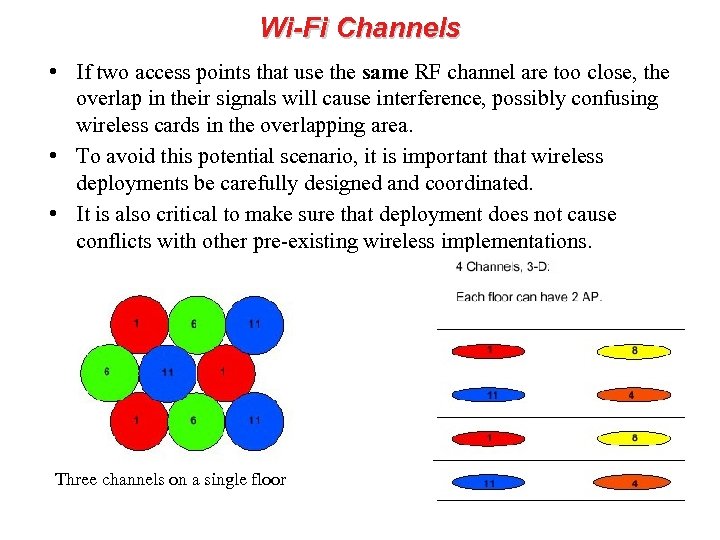 Wi-Fi Channels • If two access points that use the same RF channel are too close, the overlap in their signals will cause interference, possibly confusing wireless cards in the overlapping area. • To avoid this potential scenario, it is important that wireless deployments be carefully designed and coordinated. • It is also critical to make sure that deployment does not cause conflicts with other pre-existing wireless implementations. Three channels on a single floor
Wi-Fi Channels • If two access points that use the same RF channel are too close, the overlap in their signals will cause interference, possibly confusing wireless cards in the overlapping area. • To avoid this potential scenario, it is important that wireless deployments be carefully designed and coordinated. • It is also critical to make sure that deployment does not cause conflicts with other pre-existing wireless implementations. Three channels on a single floor
 Basic 802. 11 Security • SSID (Service Set Identifier) or ESSID (Extended Service Set Identifier) – Each AP has an SSID that it uses to identify itself. Network configuration requires each wireless client to know the SSID of the AP to which it wants to connect. – SSID provides a very modest amount of control. It keeps a client from accidentally connecting to a neighboring AP only. It does not keep an attacker out.
Basic 802. 11 Security • SSID (Service Set Identifier) or ESSID (Extended Service Set Identifier) – Each AP has an SSID that it uses to identify itself. Network configuration requires each wireless client to know the SSID of the AP to which it wants to connect. – SSID provides a very modest amount of control. It keeps a client from accidentally connecting to a neighboring AP only. It does not keep an attacker out.
 SSID • SSID (Service Set Identifier) or ESSID (Extended Service Set Identifier) – The SSID is a token that identifies an 802. 11 network. The SSID is a secret key that is set by the network administrator. Clients must know the SSID to join an 802. 11 network; however, network sniffing can discover the SSID. – The fact that the SSID is a secret key instead of a public key creates a management problem for the network administrator. • Every user of the network must configure the SSID into their system. If the network administrator seeks to lock a user out of the network, the administrator must change the SSID of the network, which requires reconfiguration of every network node. Some 802. 11 NICs allow you to configure several SSIDs at one time.
SSID • SSID (Service Set Identifier) or ESSID (Extended Service Set Identifier) – The SSID is a token that identifies an 802. 11 network. The SSID is a secret key that is set by the network administrator. Clients must know the SSID to join an 802. 11 network; however, network sniffing can discover the SSID. – The fact that the SSID is a secret key instead of a public key creates a management problem for the network administrator. • Every user of the network must configure the SSID into their system. If the network administrator seeks to lock a user out of the network, the administrator must change the SSID of the network, which requires reconfiguration of every network node. Some 802. 11 NICs allow you to configure several SSIDs at one time.
 Basic 802. 11 Security • MAC filters – Some APs provide the capability for checking the MAC address of the client before allowing it to connect to the network. – Using MAC filters is considered to be very weak security because with many Wi-Fi client implementations it is possible to change the MAC address by reconfiguring the card. – An attacker could sniff a valid MAC address from the wireless network traffic.
Basic 802. 11 Security • MAC filters – Some APs provide the capability for checking the MAC address of the client before allowing it to connect to the network. – Using MAC filters is considered to be very weak security because with many Wi-Fi client implementations it is possible to change the MAC address by reconfiguring the card. – An attacker could sniff a valid MAC address from the wireless network traffic.
 Basic 802. 11 Security • Static WEP keys – Wired Equivalent Privacy (WEP) is part of the 802. 11 specification. – Static WEP key operation requires keys on the client and AP that are used to encrypt data sent between them. With WEP encryption, sniffing is eliminated and session hijacking is difficult (or impossible). – Client and AP are configured with a set of 4 keys, and when decrypting each are used in turn until decryption is successful. This allows keys to be changed dynamically. – Keys are the same in all clients and AP. This means that there is a “community” key shared by everyone using the same AP. The danger is that if any one in the community is compromised, the community key, and hence the network and everyone else using it, is at risk.
Basic 802. 11 Security • Static WEP keys – Wired Equivalent Privacy (WEP) is part of the 802. 11 specification. – Static WEP key operation requires keys on the client and AP that are used to encrypt data sent between them. With WEP encryption, sniffing is eliminated and session hijacking is difficult (or impossible). – Client and AP are configured with a set of 4 keys, and when decrypting each are used in turn until decryption is successful. This allows keys to be changed dynamically. – Keys are the same in all clients and AP. This means that there is a “community” key shared by everyone using the same AP. The danger is that if any one in the community is compromised, the community key, and hence the network and everyone else using it, is at risk.
 Authentication Type • An access point must authenticate a station before the station can associate with the access point or communicate with the network. The IEEE 802. 11 standard defines two types of authentication: – Open System Authentication – Shared Key Authentication
Authentication Type • An access point must authenticate a station before the station can associate with the access point or communicate with the network. The IEEE 802. 11 standard defines two types of authentication: – Open System Authentication – Shared Key Authentication
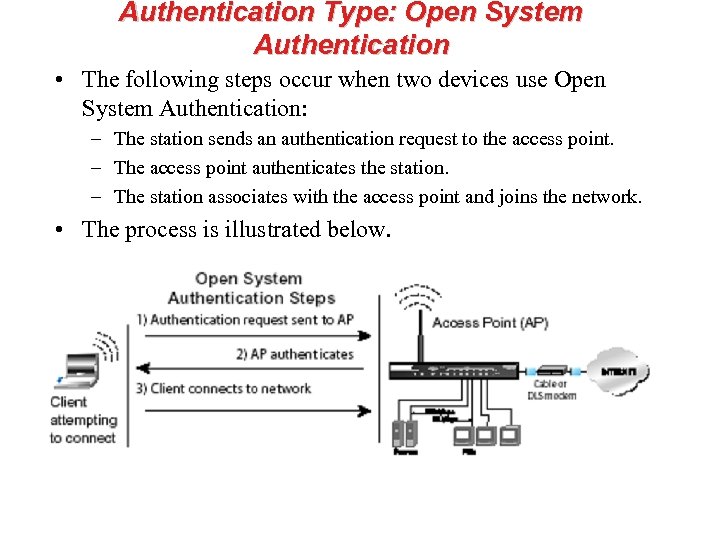 Authentication Type: Open System Authentication • The following steps occur when two devices use Open System Authentication: – The station sends an authentication request to the access point. – The access point authenticates the station. – The station associates with the access point and joins the network. • The process is illustrated below.
Authentication Type: Open System Authentication • The following steps occur when two devices use Open System Authentication: – The station sends an authentication request to the access point. – The access point authenticates the station. – The station associates with the access point and joins the network. • The process is illustrated below.
 Authentication Type: Shared Key Authentication • The following steps occur when two devices use Shared Key Authentication: 1. 2. 3. 4. 5. 6. The station sends an authentication request to the access point. The access point sends challenge text to the station. The station uses its configured 64 -bit or 128 -bit default key to encrypt the challenge text, and sends the encrypted text to the access point. The access point decrypts the encrypted text using its configured WEP Key that corresponds to the station’s default key. The access point compares the decrypted text with the original challenge text. If the decrypted text matches the original challenge text, then the access point and the station share the same WEP Key and the access point authenticates the station. The station connects to the network.
Authentication Type: Shared Key Authentication • The following steps occur when two devices use Shared Key Authentication: 1. 2. 3. 4. 5. 6. The station sends an authentication request to the access point. The access point sends challenge text to the station. The station uses its configured 64 -bit or 128 -bit default key to encrypt the challenge text, and sends the encrypted text to the access point. The access point decrypts the encrypted text using its configured WEP Key that corresponds to the station’s default key. The access point compares the decrypted text with the original challenge text. If the decrypted text matches the original challenge text, then the access point and the station share the same WEP Key and the access point authenticates the station. The station connects to the network.
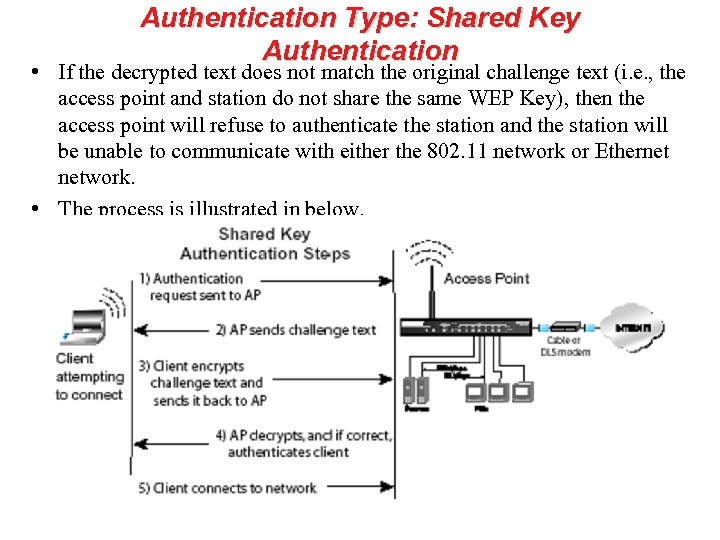 Authentication Type: Shared Key Authentication • If the decrypted text does not match the original challenge text (i. e. , the access point and station do not share the same WEP Key), then the access point will refuse to authenticate the station and the station will be unable to communicate with either the 802. 11 network or Ethernet network. • The process is illustrated in below.
Authentication Type: Shared Key Authentication • If the decrypted text does not match the original challenge text (i. e. , the access point and station do not share the same WEP Key), then the access point will refuse to authenticate the station and the station will be unable to communicate with either the 802. 11 network or Ethernet network. • The process is illustrated in below.
 Overview of WEP Parameters • Before enabling WEP on an 802. 11 network, you must first consider what type of encryption you require and the key size you want to use. Typically, there are three WEP Encryption options available for 802. 11 products: – Do Not Use WEP: The 802. 11 network does not encrypt data. For authentication purposes, the network uses Open System Authentication. – Use WEP for Encryption: A transmitting 802. 11 device encrypts the data portion of every packet it sends using a configured WEP Key. The receiving device decrypts the data using the same WEP Key. For authentication purposes, the wireless network uses Open System Authentication. – Use WEP for Authentication and Encryption: A transmitting 802. 11 device encrypts the data portion of every packet it sends using a configured WEP Key. The receiving 802. 11 device decrypts the data using the same WEP Key. For authentication purposes, the 802. 11 network uses Shared Key Authentication. • Note: Some 802. 11 access points also support Use WEP for Authentication Only (Shared Key Authentication without data encryption).
Overview of WEP Parameters • Before enabling WEP on an 802. 11 network, you must first consider what type of encryption you require and the key size you want to use. Typically, there are three WEP Encryption options available for 802. 11 products: – Do Not Use WEP: The 802. 11 network does not encrypt data. For authentication purposes, the network uses Open System Authentication. – Use WEP for Encryption: A transmitting 802. 11 device encrypts the data portion of every packet it sends using a configured WEP Key. The receiving device decrypts the data using the same WEP Key. For authentication purposes, the wireless network uses Open System Authentication. – Use WEP for Authentication and Encryption: A transmitting 802. 11 device encrypts the data portion of every packet it sends using a configured WEP Key. The receiving 802. 11 device decrypts the data using the same WEP Key. For authentication purposes, the 802. 11 network uses Shared Key Authentication. • Note: Some 802. 11 access points also support Use WEP for Authentication Only (Shared Key Authentication without data encryption).
 Recommended 802. 11 Security Practices • • Change the default password for the Admin account SSID • • • Enable MAC Address Filtering Enable WEP 128 -bit Data Encryption. Please note that this will reduce your network performance • • • Change the default Disable Broadcast Make it unique If possible, Change it often Use the highest level of encryption possible Use a “Shared” Key Use multiple WEP keys Change it regularly Turn off DHCP Refrain from using the default IP subnet
Recommended 802. 11 Security Practices • • Change the default password for the Admin account SSID • • • Enable MAC Address Filtering Enable WEP 128 -bit Data Encryption. Please note that this will reduce your network performance • • • Change the default Disable Broadcast Make it unique If possible, Change it often Use the highest level of encryption possible Use a “Shared” Key Use multiple WEP keys Change it regularly Turn off DHCP Refrain from using the default IP subnet
 Vulnerabilities
Vulnerabilities
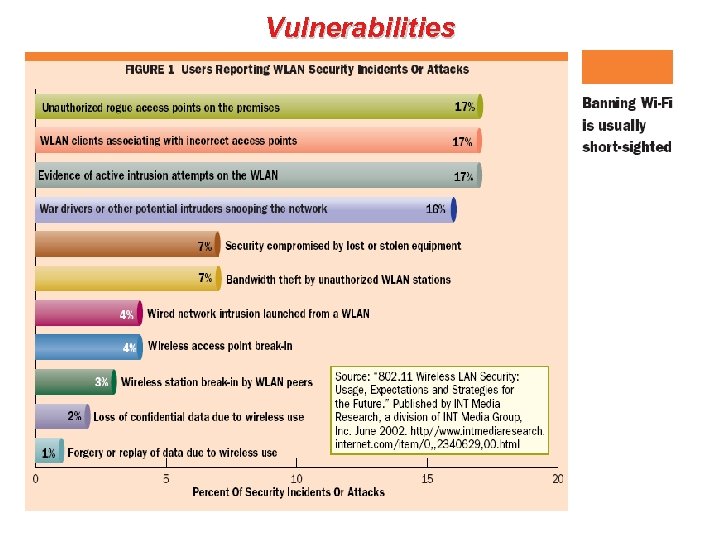
 Vulnerabilities • There are several known types of wireless attacks that must be protected against: – – – SSID (network name) sniffing WEP encryption key recovery attacks ARP poisoning (“man in the middle attacks”) MAC address spoofing Access Point management password and SNMP attacks – Wireless end user (station) attacks – Rogue AP attacks (AP impersonation) – DOS (denial of service) wireless attacks
Vulnerabilities • There are several known types of wireless attacks that must be protected against: – – – SSID (network name) sniffing WEP encryption key recovery attacks ARP poisoning (“man in the middle attacks”) MAC address spoofing Access Point management password and SNMP attacks – Wireless end user (station) attacks – Rogue AP attacks (AP impersonation) – DOS (denial of service) wireless attacks
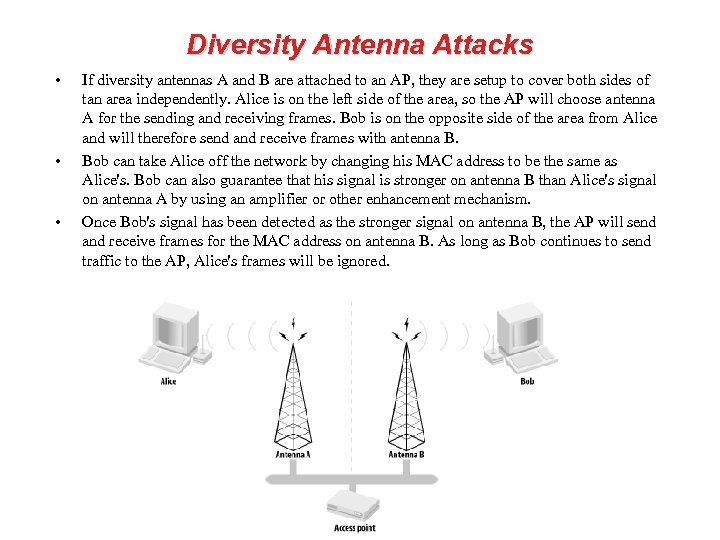 Diversity Antenna Attacks • • • If diversity antennas A and B are attached to an AP, they are setup to cover both sides of tan area independently. Alice is on the left side of the area, so the AP will choose antenna A for the sending and receiving frames. Bob is on the opposite side of the area from Alice and will therefore send and receive frames with antenna B. Bob can take Alice off the network by changing his MAC address to be the same as Alice's. Bob can also guarantee that his signal is stronger on antenna B than Alice's signal on antenna A by using an amplifier or other enhancement mechanism. Once Bob's signal has been detected as the stronger signal on antenna B, the AP will send and receive frames for the MAC address on antenna B. As long as Bob continues to send traffic to the AP, Alice's frames will be ignored.
Diversity Antenna Attacks • • • If diversity antennas A and B are attached to an AP, they are setup to cover both sides of tan area independently. Alice is on the left side of the area, so the AP will choose antenna A for the sending and receiving frames. Bob is on the opposite side of the area from Alice and will therefore send and receive frames with antenna B. Bob can take Alice off the network by changing his MAC address to be the same as Alice's. Bob can also guarantee that his signal is stronger on antenna B than Alice's signal on antenna A by using an amplifier or other enhancement mechanism. Once Bob's signal has been detected as the stronger signal on antenna B, the AP will send and receive frames for the MAC address on antenna B. As long as Bob continues to send traffic to the AP, Alice's frames will be ignored.
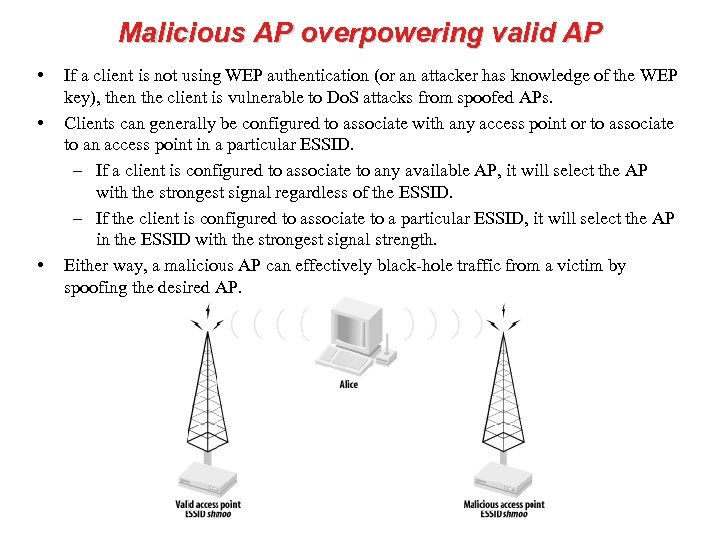 Malicious AP overpowering valid AP • • • If a client is not using WEP authentication (or an attacker has knowledge of the WEP key), then the client is vulnerable to Do. S attacks from spoofed APs. Clients can generally be configured to associate with any access point or to associate to an access point in a particular ESSID. – If a client is configured to associate to any available AP, it will select the AP with the strongest signal regardless of the ESSID. – If the client is configured to associate to a particular ESSID, it will select the AP in the ESSID with the strongest signal strength. Either way, a malicious AP can effectively black-hole traffic from a victim by spoofing the desired AP.
Malicious AP overpowering valid AP • • • If a client is not using WEP authentication (or an attacker has knowledge of the WEP key), then the client is vulnerable to Do. S attacks from spoofed APs. Clients can generally be configured to associate with any access point or to associate to an access point in a particular ESSID. – If a client is configured to associate to any available AP, it will select the AP with the strongest signal regardless of the ESSID. – If the client is configured to associate to a particular ESSID, it will select the AP in the ESSID with the strongest signal strength. Either way, a malicious AP can effectively black-hole traffic from a victim by spoofing the desired AP.
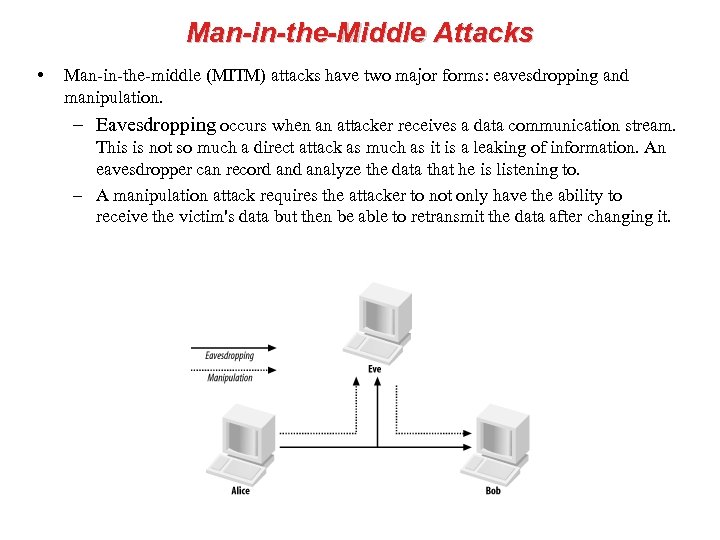 Man-in-the-Middle Attacks • Man-in-the-middle (MITM) attacks have two major forms: eavesdropping and manipulation. – Eavesdropping occurs when an attacker receives a data communication stream. This is not so much a direct attack as much as it is a leaking of information. An eavesdropper can record analyze the data that he is listening to. – A manipulation attack requires the attacker to not only have the ability to receive the victim's data but then be able to retransmit the data after changing it.
Man-in-the-Middle Attacks • Man-in-the-middle (MITM) attacks have two major forms: eavesdropping and manipulation. – Eavesdropping occurs when an attacker receives a data communication stream. This is not so much a direct attack as much as it is a leaking of information. An eavesdropper can record analyze the data that he is listening to. – A manipulation attack requires the attacker to not only have the ability to receive the victim's data but then be able to retransmit the data after changing it.
 WEP – What? • WEP (Wired Equivalent Privacy) referring to the intent to provide a privacy service to wireless LAN users similar to that provided by the physical security inherent in a wired LAN. • WEP is the privacy protocol specified in IEEE 802. 11 to provide wireless LAN users protection against casual eavesdropping.
WEP – What? • WEP (Wired Equivalent Privacy) referring to the intent to provide a privacy service to wireless LAN users similar to that provided by the physical security inherent in a wired LAN. • WEP is the privacy protocol specified in IEEE 802. 11 to provide wireless LAN users protection against casual eavesdropping.
 IV Key Hashing/Temporal Key WEP Encryption Today IV BASE KEY PLAINTEXT DATA RC 4 XOR STREAM CIPHERTEXT DATA
IV Key Hashing/Temporal Key WEP Encryption Today IV BASE KEY PLAINTEXT DATA RC 4 XOR STREAM CIPHERTEXT DATA
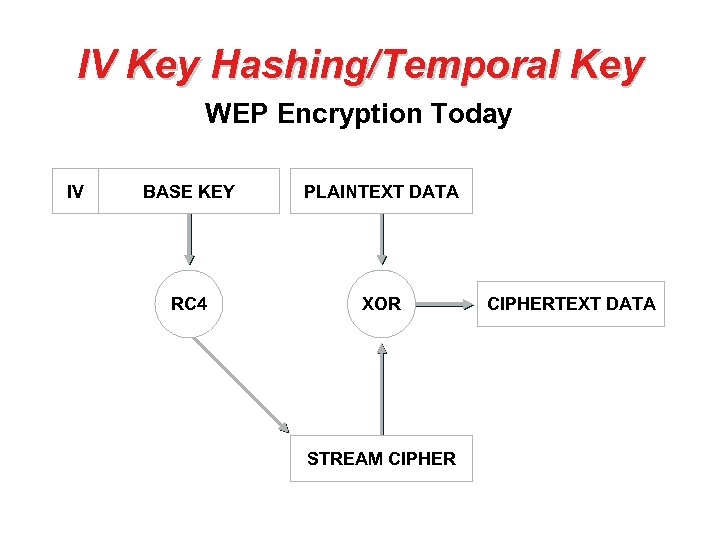
 WEP – How? • When WEP is active in a wireless LAN, each 802. 11 packet is encrypted separately with a RC 4 cipher stream generated by a 64 bit RC 4 key. This key is composed of a 24 bit initialization vector (IV) and a 40 bit WEP key. • The encrypted packet is generated with a bit-wise exclusive OR (XOR) of the original packet and the RC 4 stream. • The IV is chosen by the sender and should be changed so that every packet won't be encrypted with the same cipher stream. • The IV is sent in the clear with each packet. • An additional 4 byte Integrity Check Value (ICV) is computed on the original packet using the CRC-32 checksum algorithm and appended to the end. • The ICV (be careful not to confuse this with the IV) is also encrypted with the RC 4 cipher stream.
WEP – How? • When WEP is active in a wireless LAN, each 802. 11 packet is encrypted separately with a RC 4 cipher stream generated by a 64 bit RC 4 key. This key is composed of a 24 bit initialization vector (IV) and a 40 bit WEP key. • The encrypted packet is generated with a bit-wise exclusive OR (XOR) of the original packet and the RC 4 stream. • The IV is chosen by the sender and should be changed so that every packet won't be encrypted with the same cipher stream. • The IV is sent in the clear with each packet. • An additional 4 byte Integrity Check Value (ICV) is computed on the original packet using the CRC-32 checksum algorithm and appended to the end. • The ICV (be careful not to confuse this with the IV) is also encrypted with the RC 4 cipher stream.
 WEP - Weaknesses • Key Management and Key Size – Key management is not specified in the WEP standard, and therefore is one of its weaknesses, because without interoperable key management, keys will tend to be long-lived and of poor quality. • The Initialization Vector (IV) is Too Small – WEP’s IV size of 24 bits provides for 16, 777, 216 different RC 4 cipher streams for a given WEP key, for any key size. Remember that the RC 4 cipher stream is XOR-ed with the original packet to give the encrypted packet which is transmitted, and the IV is sent in the clear with each packet. • The Integrity Check Value (ICV) algorithm is not appropriate – The WEP ICV is based on CRC-32, an algorithm for detecting noise and common errors in transmission. CRC-32 is an excellent checksum for detecting errors, but an awful choice for a cryptographic hash.
WEP - Weaknesses • Key Management and Key Size – Key management is not specified in the WEP standard, and therefore is one of its weaknesses, because without interoperable key management, keys will tend to be long-lived and of poor quality. • The Initialization Vector (IV) is Too Small – WEP’s IV size of 24 bits provides for 16, 777, 216 different RC 4 cipher streams for a given WEP key, for any key size. Remember that the RC 4 cipher stream is XOR-ed with the original packet to give the encrypted packet which is transmitted, and the IV is sent in the clear with each packet. • The Integrity Check Value (ICV) algorithm is not appropriate – The WEP ICV is based on CRC-32, an algorithm for detecting noise and common errors in transmission. CRC-32 is an excellent checksum for detecting errors, but an awful choice for a cryptographic hash.
 WEP - Weaknesses • WEP’s use of RC 4 is weak – RC 4 in its implementation in WEP has been found to have weak keys. Having a weak key means that there is more correlation between the key and the output than there should be for good security. Determining which packets were encrypted with weak keys is easy because the first three bytes of the key are taken from the IV that is sent unencrypted in each packet. – This weakness can be exploited by a passive attack. All the attacker needs to do is be within a hundred feet or so of the AP. • Authentication Messages can be easily forged – 802. 11 defines two forms of authentication: • Open System (no authentication) and • Shared Key authentication. – These are used to authenticate the client to the access point. • The idea was that authentication would be better than no authentication because the user has to prove knowledge of the shared WEP key, in effect, authenticating himself.
WEP - Weaknesses • WEP’s use of RC 4 is weak – RC 4 in its implementation in WEP has been found to have weak keys. Having a weak key means that there is more correlation between the key and the output than there should be for good security. Determining which packets were encrypted with weak keys is easy because the first three bytes of the key are taken from the IV that is sent unencrypted in each packet. – This weakness can be exploited by a passive attack. All the attacker needs to do is be within a hundred feet or so of the AP. • Authentication Messages can be easily forged – 802. 11 defines two forms of authentication: • Open System (no authentication) and • Shared Key authentication. – These are used to authenticate the client to the access point. • The idea was that authentication would be better than no authentication because the user has to prove knowledge of the shared WEP key, in effect, authenticating himself.
 WPA • Wi-Fi Protected Access (WPA) is a new security guideline issued by the Wi-Fi Alliance. • The goal is to strengthen security over the current WEP standards by including mechanisms from the emerging 802. 11 i standard for both data encryption and network access control. • Path: WEP -> WPA -> 802. 11 i • WPA = TKIP(Temporal Key Integrity Protocol) + IEEE 802. 1 x – For encryption, WPA has TKIP, which uses the same encryption algorithm as WEP, but constructs keys in a different way. – For access control, WPA will use the IEEE 802. 1 x protocol.
WPA • Wi-Fi Protected Access (WPA) is a new security guideline issued by the Wi-Fi Alliance. • The goal is to strengthen security over the current WEP standards by including mechanisms from the emerging 802. 11 i standard for both data encryption and network access control. • Path: WEP -> WPA -> 802. 11 i • WPA = TKIP(Temporal Key Integrity Protocol) + IEEE 802. 1 x – For encryption, WPA has TKIP, which uses the same encryption algorithm as WEP, but constructs keys in a different way. – For access control, WPA will use the IEEE 802. 1 x protocol.
 802. 11 i – Future Wireless Security Standard • Task group "i" within the IEEE 802. 11 is responsible for developing a new standard for WLAN security to replace the weak WEP (Wired Equivalent Privacy). • The IEEE 802. 11 i standard utilizes the authentication schemes of 802. 1 x and EAP(Extensible Authentication Protocol) in addition to a new encryption scheme – AES (Advanced Encryption Standard) and dynamic key distribution scheme - TKIP(Temporal Key Integrity Protocol). • 802. 11 i = TKIP + IEEE 802. 1 x + AES
802. 11 i – Future Wireless Security Standard • Task group "i" within the IEEE 802. 11 is responsible for developing a new standard for WLAN security to replace the weak WEP (Wired Equivalent Privacy). • The IEEE 802. 11 i standard utilizes the authentication schemes of 802. 1 x and EAP(Extensible Authentication Protocol) in addition to a new encryption scheme – AES (Advanced Encryption Standard) and dynamic key distribution scheme - TKIP(Temporal Key Integrity Protocol). • 802. 11 i = TKIP + IEEE 802. 1 x + AES
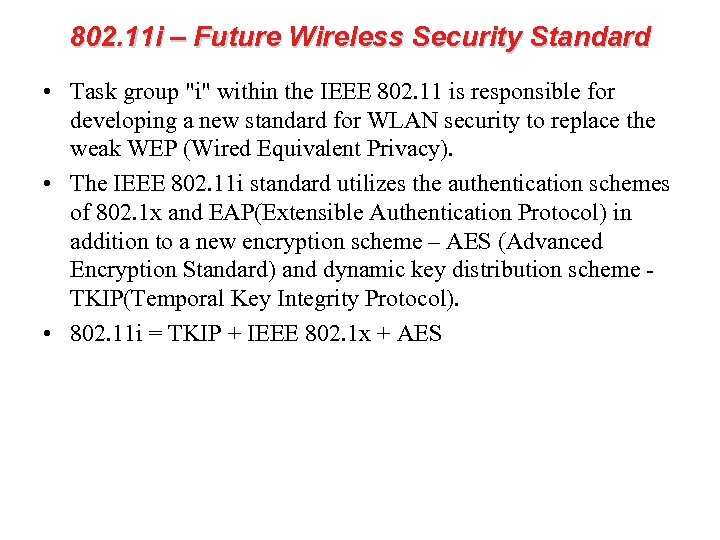
 802. 11 i – Future Wireless Security Standard • Temporal Key Integrity Protocol (TKIP) – The Temporal Key Integrity Protocol is part of the IEEE 802. 11 i encryption standard for wireless LANs. TKIP is the next generation of WEP, the Wired Equivalency Protocol, which is used to secure 802. 11 wireless LANs. TKIP provides per-packet key mixing, a message integrity check and a re-keying mechanism, thus fixing the flaws of WEP.
802. 11 i – Future Wireless Security Standard • Temporal Key Integrity Protocol (TKIP) – The Temporal Key Integrity Protocol is part of the IEEE 802. 11 i encryption standard for wireless LANs. TKIP is the next generation of WEP, the Wired Equivalency Protocol, which is used to secure 802. 11 wireless LANs. TKIP provides per-packet key mixing, a message integrity check and a re-keying mechanism, thus fixing the flaws of WEP.
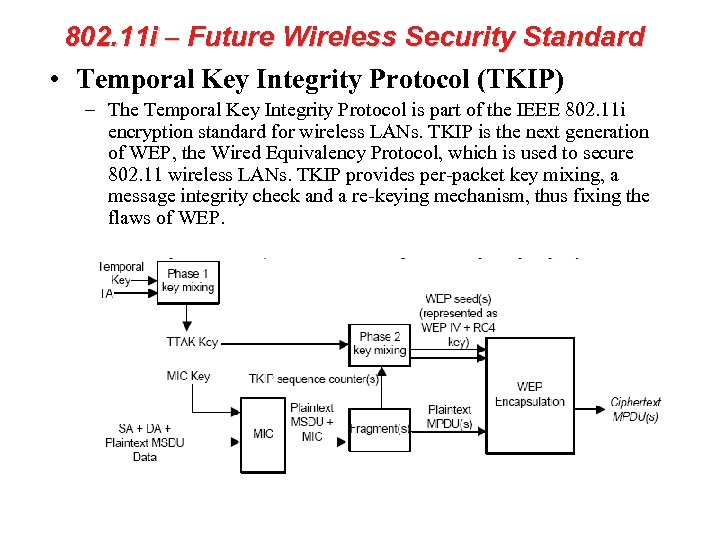
 802. 11 i – Future Wireless Security Standard • Advanced Encryption Standard (AES) – AES is the U. S. government's next-generation cryptography algorithm, which will replace DES and 3 DES.
802. 11 i – Future Wireless Security Standard • Advanced Encryption Standard (AES) – AES is the U. S. government's next-generation cryptography algorithm, which will replace DES and 3 DES.
 EAP and 802. 1 x
EAP and 802. 1 x
 802. 1 x • IEEE 802. 1 x is the denotation of a standard that is titled “Port Based Network Access Control”, which indicates that the emphasis of the standard is to provide a control mechanism to connect physically to a LAN. • The standard does not define the authentication methods, but it does provide a framework that allows the application of this standard in combination with any chosen authentication method. • It adds to the flexibility as current and future authentication methods can be used without having to adapt the standard.
802. 1 x • IEEE 802. 1 x is the denotation of a standard that is titled “Port Based Network Access Control”, which indicates that the emphasis of the standard is to provide a control mechanism to connect physically to a LAN. • The standard does not define the authentication methods, but it does provide a framework that allows the application of this standard in combination with any chosen authentication method. • It adds to the flexibility as current and future authentication methods can be used without having to adapt the standard.
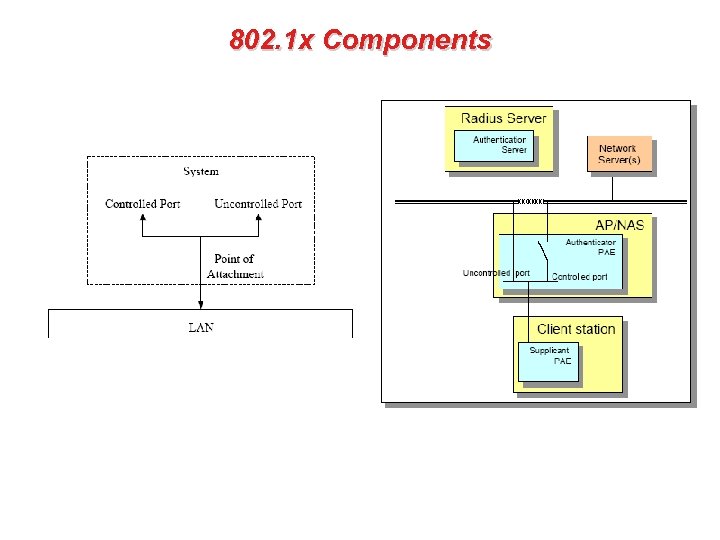
 802. 1 x Components • The 802. 1 x standard recognizes the following concepts: – Port Access Entity (PAE) • which refers to the mechanism (algorithms and protocols) associated with a LAN port (residing in either a Bridge or a Station) – Supplicant PAE • which refers to the entity that requires authentication before getting access to the LAN (typically in the client station) – Authenticator PAE • which refers to the entity facilitating authentication of a supplicant (typically in bridge or AP) – Authentication server • which refers to the entity that provides authentication service to the Authenticators in the LAN (could be a RADIUS server)
802. 1 x Components • The 802. 1 x standard recognizes the following concepts: – Port Access Entity (PAE) • which refers to the mechanism (algorithms and protocols) associated with a LAN port (residing in either a Bridge or a Station) – Supplicant PAE • which refers to the entity that requires authentication before getting access to the LAN (typically in the client station) – Authenticator PAE • which refers to the entity facilitating authentication of a supplicant (typically in bridge or AP) – Authentication server • which refers to the entity that provides authentication service to the Authenticators in the LAN (could be a RADIUS server)
 802. 1 x Components
802. 1 x Components
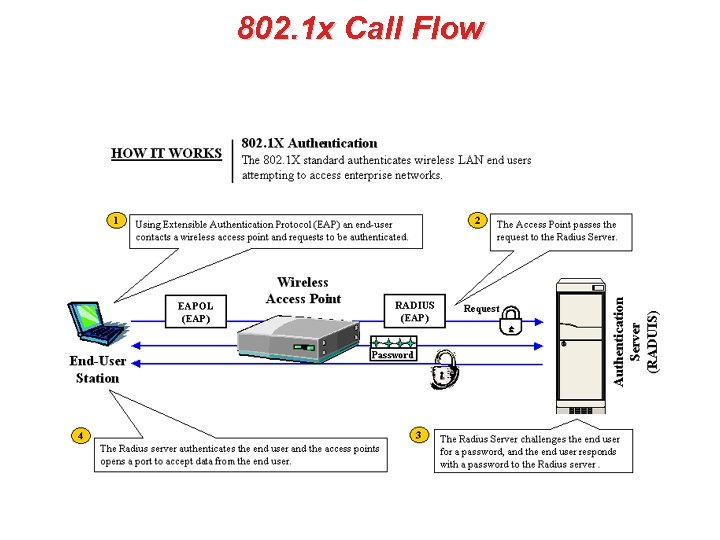
 802. 1 x Call Flow
802. 1 x Call Flow
 802. 1 x Call Flow
802. 1 x Call Flow
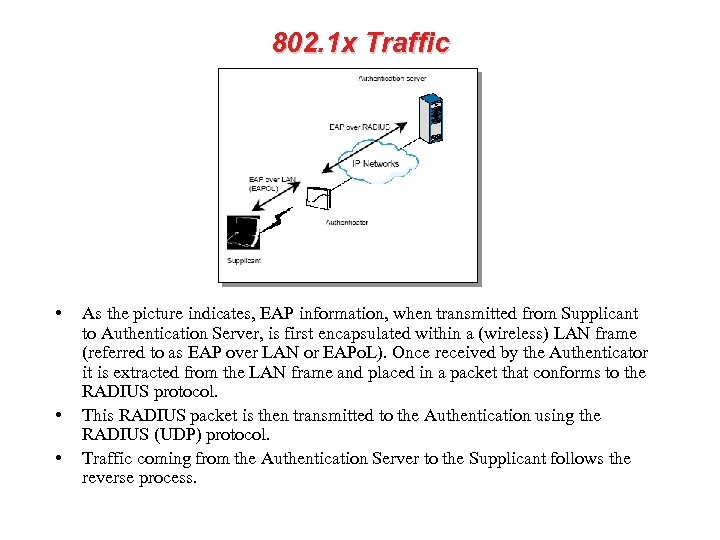 802. 1 x Traffic • • • As the picture indicates, EAP information, when transmitted from Supplicant to Authentication Server, is first encapsulated within a (wireless) LAN frame (referred to as EAP over LAN or EAPo. L). Once received by the Authenticator it is extracted from the LAN frame and placed in a packet that conforms to the RADIUS protocol. This RADIUS packet is then transmitted to the Authentication using the RADIUS (UDP) protocol. Traffic coming from the Authentication Server to the Supplicant follows the reverse process.
802. 1 x Traffic • • • As the picture indicates, EAP information, when transmitted from Supplicant to Authentication Server, is first encapsulated within a (wireless) LAN frame (referred to as EAP over LAN or EAPo. L). Once received by the Authenticator it is extracted from the LAN frame and placed in a packet that conforms to the RADIUS protocol. This RADIUS packet is then transmitted to the Authentication using the RADIUS (UDP) protocol. Traffic coming from the Authentication Server to the Supplicant follows the reverse process.
 EAP • EAP was originally designed as part of the PPP (Point-to-Point Protocol) – The PPP Extensible Authentication Protocol (EAP) is a general protocol for PPP authentication which supports multiple authentication mechanisms. It was developed in response to an increasing demand for remote access user authentication that uses other security devices. • By using EAP, support for a number of authentication schemes may be added by defining EAP-Types. Support might include token cards, one-time passwords, public key authentication using smart card, certificates, and others. • EAP hides the details of the authentication scheme from those network elements that need not know – For example in PPP, the client and the AAA server only need to know the EAP type, and the Network Access Server does not
EAP • EAP was originally designed as part of the PPP (Point-to-Point Protocol) – The PPP Extensible Authentication Protocol (EAP) is a general protocol for PPP authentication which supports multiple authentication mechanisms. It was developed in response to an increasing demand for remote access user authentication that uses other security devices. • By using EAP, support for a number of authentication schemes may be added by defining EAP-Types. Support might include token cards, one-time passwords, public key authentication using smart card, certificates, and others. • EAP hides the details of the authentication scheme from those network elements that need not know – For example in PPP, the client and the AAA server only need to know the EAP type, and the Network Access Server does not
 EAP • RFC 2284 defines PPP Extensible Authentication Protocol. • EAP does not select a specific authentication mechanism at Link Control Phase, but rather postpones this until the Authentication Phase. – This allows the authenticator to request more information before determining the specific authentication mechanism. – This also permits the use of a "back-end" server which actually implements the various mechanisms while the PPP authenticator merely passes through the authentication exchange.
EAP • RFC 2284 defines PPP Extensible Authentication Protocol. • EAP does not select a specific authentication mechanism at Link Control Phase, but rather postpones this until the Authentication Phase. – This allows the authenticator to request more information before determining the specific authentication mechanism. – This also permits the use of a "back-end" server which actually implements the various mechanisms while the PPP authenticator merely passes through the authentication exchange.
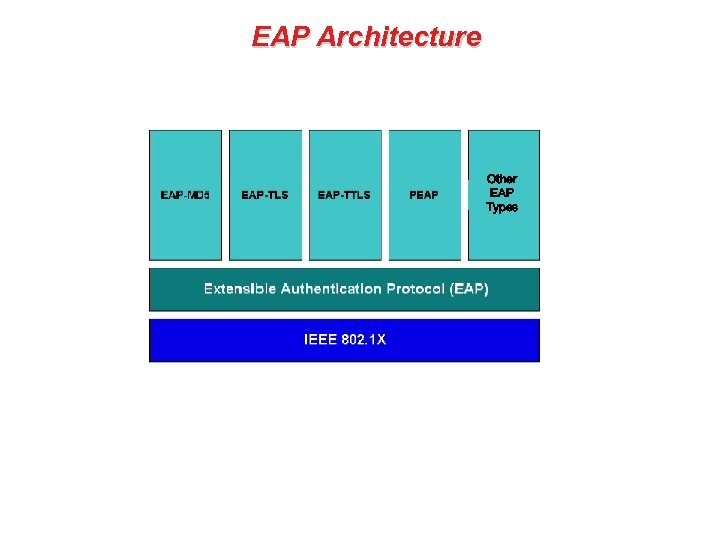 EAP Architecture Other EAP Types
EAP Architecture Other EAP Types
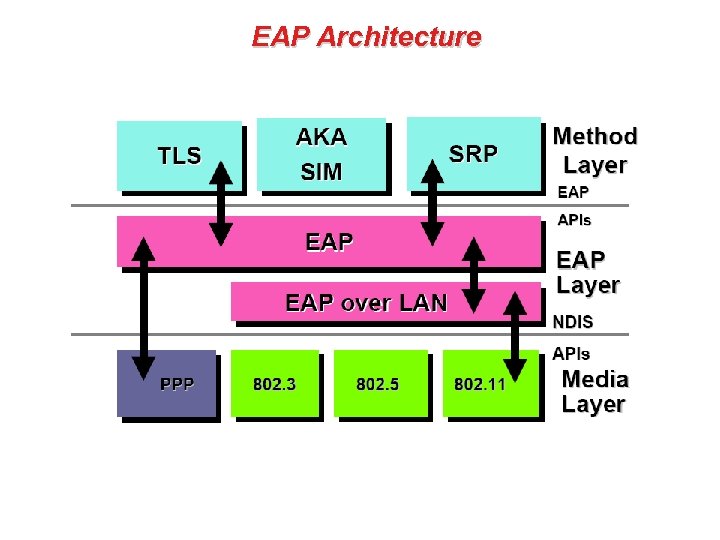 EAP Architecture
EAP Architecture
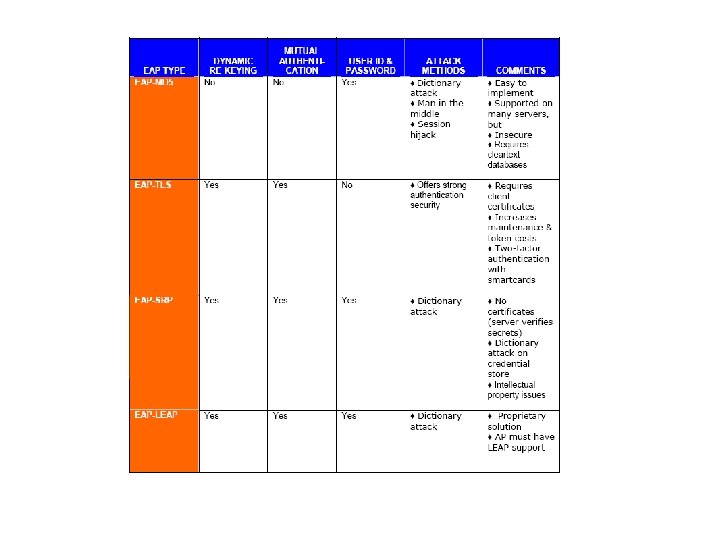
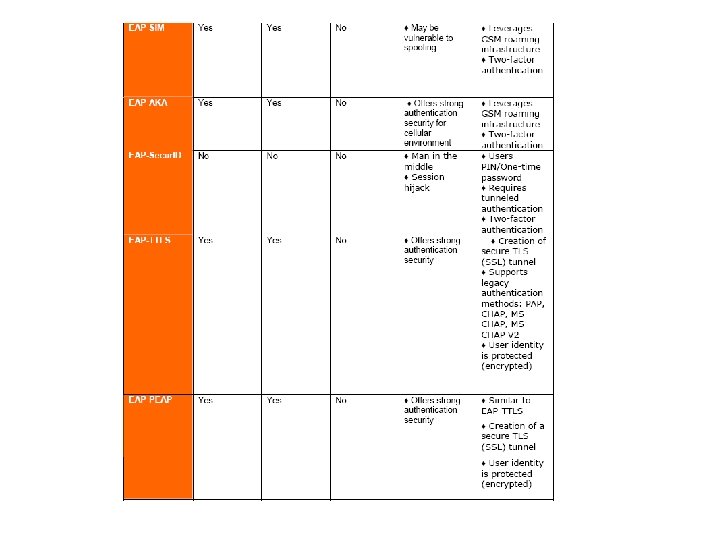
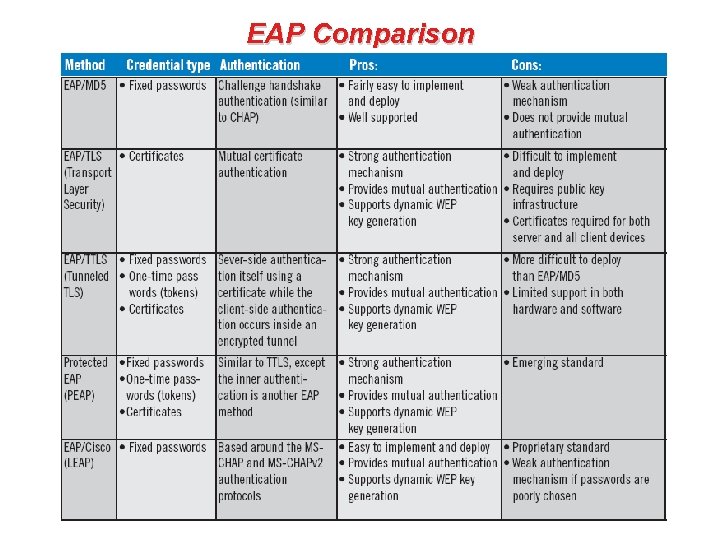 EAP Comparison
EAP Comparison
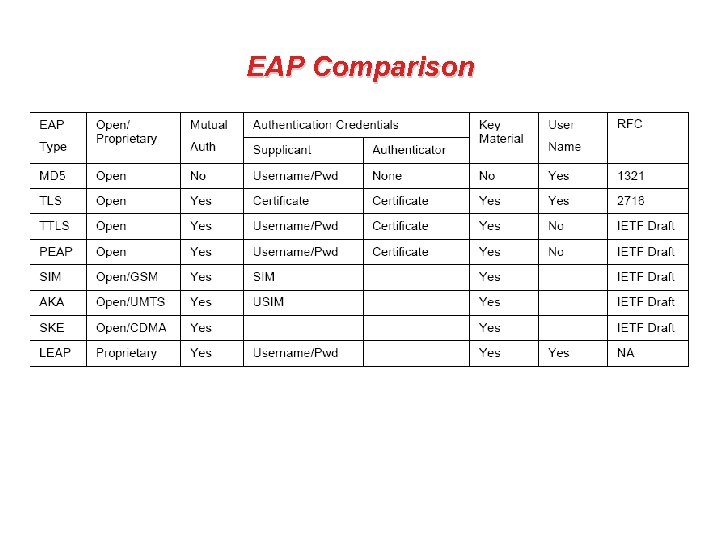 EAP Comparison
EAP Comparison
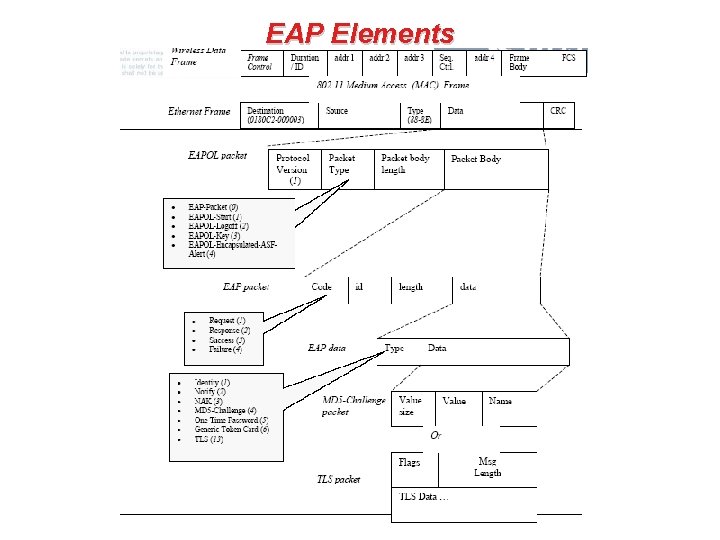
 EAP Elements • EAP basically consists of four different protocol elements: – – Request packets (from Authenticator [AP] to client [Supplicant]) Response packets (from Client to Authenticator) Success packet May originate from an AAA server Failure packet {
EAP Elements • EAP basically consists of four different protocol elements: – – Request packets (from Authenticator [AP] to client [Supplicant]) Response packets (from Client to Authenticator) Success packet May originate from an AAA server Failure packet {
 EAP Elements
EAP Elements
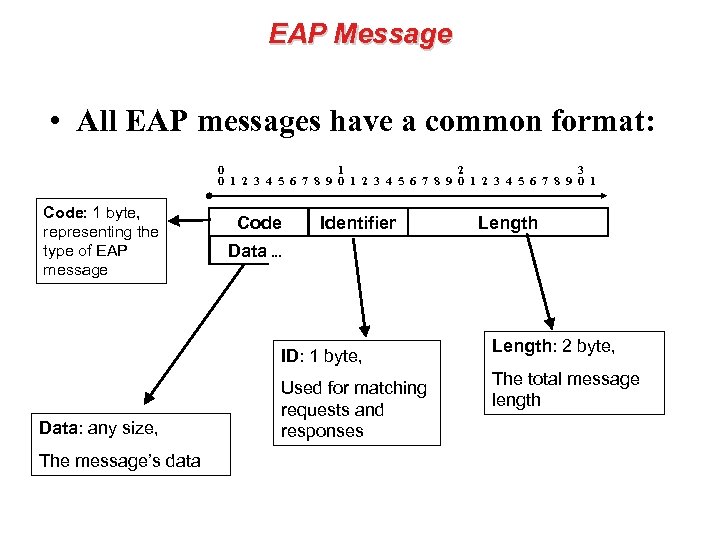 EAP Message • All EAP messages have a common format: 0 1 2 3 4 5 6 7 8 9 0 1 Code: 1 byte, representing the type of EAP message Code Identifier Data. . . ID: 1 byte, Data: any size, The message’s data Length Used for matching requests and responses Length: 2 byte, The total message length
EAP Message • All EAP messages have a common format: 0 1 2 3 4 5 6 7 8 9 0 1 Code: 1 byte, representing the type of EAP message Code Identifier Data. . . ID: 1 byte, Data: any size, The message’s data Length Used for matching requests and responses Length: 2 byte, The total message length
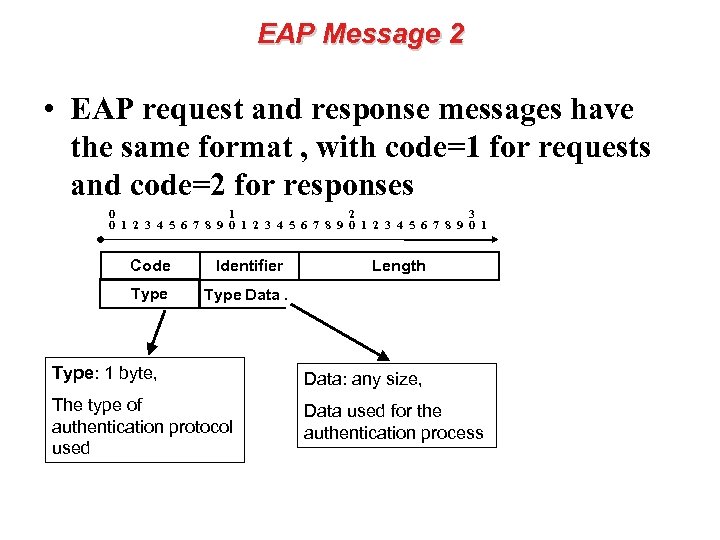 EAP Message 2 • EAP request and response messages have the same format , with code=1 for requests and code=2 for responses 0 1 2 3 4 5 6 7 8 9 0 1 Code Identifier Type Length Type Data. Type: 1 byte, Data: any size, The type of authentication protocol used Data used for the authentication process
EAP Message 2 • EAP request and response messages have the same format , with code=1 for requests and code=2 for responses 0 1 2 3 4 5 6 7 8 9 0 1 Code Identifier Type Length Type Data. Type: 1 byte, Data: any size, The type of authentication protocol used Data used for the authentication process
 EAP Message 3 • EAP Success messages are EAP messages with code 3 and no data. – A success message means that the authentication concluded successfully. • EAP failure messages are EAP messages with code 4 and no data. – A Failure message means that the authentication has failed.
EAP Message 3 • EAP Success messages are EAP messages with code 3 and no data. – A success message means that the authentication concluded successfully. • EAP failure messages are EAP messages with code 4 and no data. – A Failure message means that the authentication has failed.
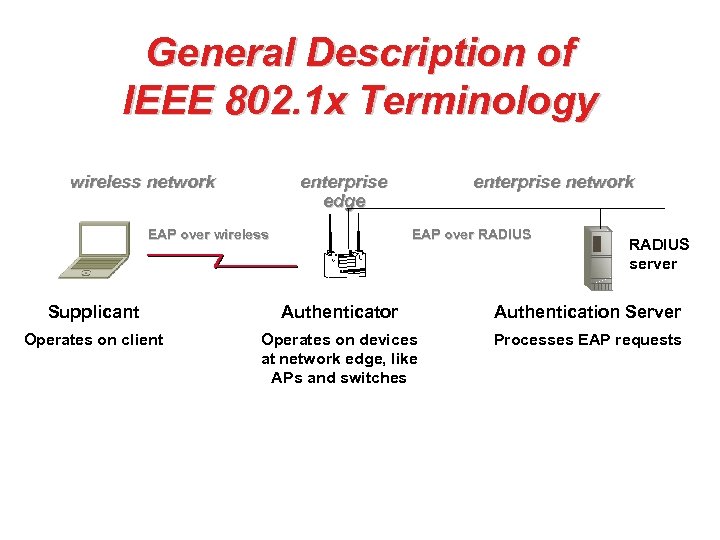 General Description of IEEE 802. 1 x Terminology wireless network enterprise edge EAP over wireless enterprise network EAP over RADIUS server Supplicant Authenticator Authentication Server Operates on client Operates on devices at network edge, like APs and switches Processes EAP requests
General Description of IEEE 802. 1 x Terminology wireless network enterprise edge EAP over wireless enterprise network EAP over RADIUS server Supplicant Authenticator Authentication Server Operates on client Operates on devices at network edge, like APs and switches Processes EAP requests
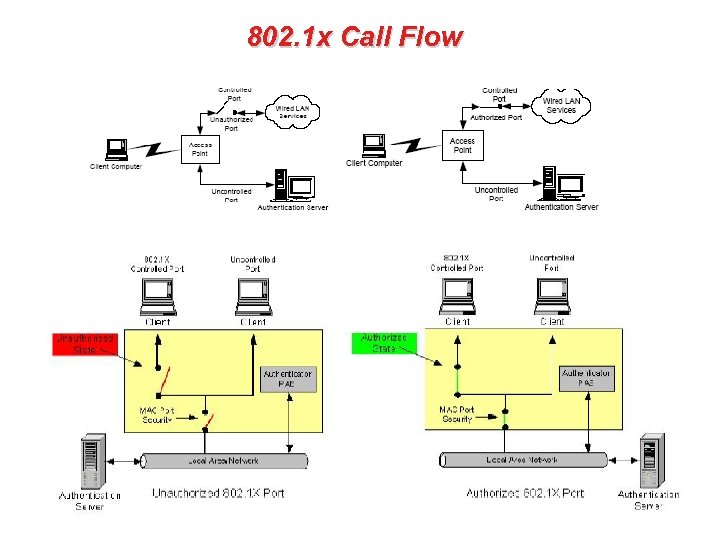
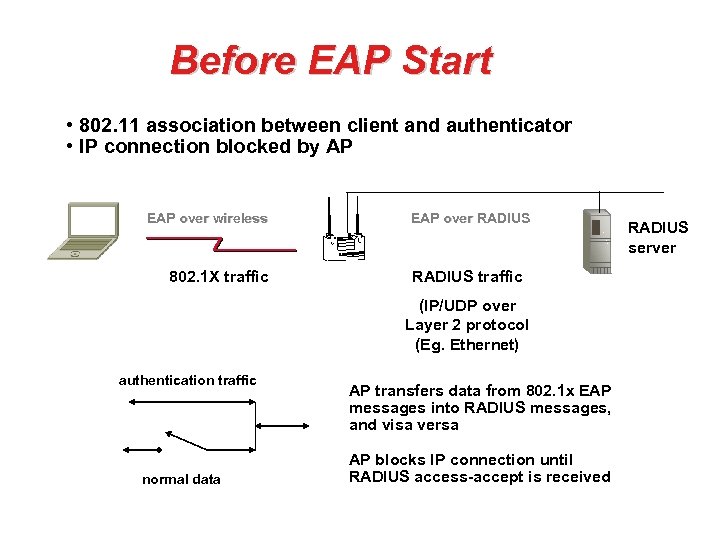 Before EAP Start • 802. 11 association between client and authenticator • IP connection blocked by AP EAP over wireless 802. 1 X traffic EAP over RADIUS traffic (IP/UDP over Layer 2 protocol (Eg. Ethernet) authentication traffic normal data AP transfers data from 802. 1 x EAP messages into RADIUS messages, and visa versa AP blocks IP connection until RADIUS access-accept is received RADIUS server
Before EAP Start • 802. 11 association between client and authenticator • IP connection blocked by AP EAP over wireless 802. 1 X traffic EAP over RADIUS traffic (IP/UDP over Layer 2 protocol (Eg. Ethernet) authentication traffic normal data AP transfers data from 802. 1 x EAP messages into RADIUS messages, and visa versa AP blocks IP connection until RADIUS access-accept is received RADIUS server
 802. 1 x Call Flow
802. 1 x Call Flow
 EAP Flow • After the Link Establishment phase is complete, the authenticator sends one or more Requests to authenticate the peer. • The Request has a type field to indicate what is being requested. Examples of Request types include Identity, MD 5 challenge, One-Time Passwords, Generic Token Card, etc. – The MD 5 -challenge type corresponds closely to the CHAP authentication protocol. • Typically, the authenticator will send an initial Identity Request followed by one or more Requests for authentication information. However, an initial Identity Request is not required, and MAY be bypassed in cases where the identity is presumed (leased lines, dedicated dial-ups, etc. ).
EAP Flow • After the Link Establishment phase is complete, the authenticator sends one or more Requests to authenticate the peer. • The Request has a type field to indicate what is being requested. Examples of Request types include Identity, MD 5 challenge, One-Time Passwords, Generic Token Card, etc. – The MD 5 -challenge type corresponds closely to the CHAP authentication protocol. • Typically, the authenticator will send an initial Identity Request followed by one or more Requests for authentication information. However, an initial Identity Request is not required, and MAY be bypassed in cases where the identity is presumed (leased lines, dedicated dial-ups, etc. ).
 EAP Flow • The peer sends a Response packet in reply to each Request. As with the Request packet, the Response packet contains a type field which corresponds to the type field of the Request. • The authenticator ends the authentication phase with a Success or Failure packet.
EAP Flow • The peer sends a Response packet in reply to each Request. As with the Request packet, the Response packet contains a type field which corresponds to the type field of the Request. • The authenticator ends the authentication phase with a Success or Failure packet.
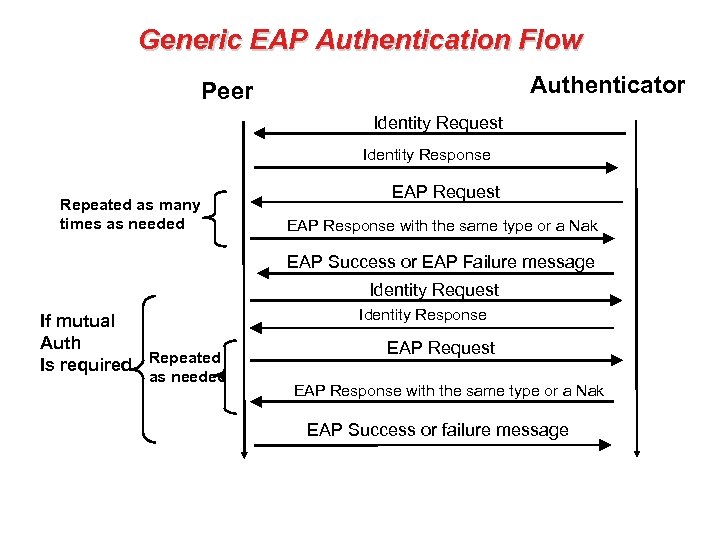 Generic EAP Authentication Flow Authenticator Peer Identity Request Identity Response Repeated as many times as needed EAP Request EAP Response with the same type or a Nak EAP Success or EAP Failure message Identity Request If mutual Auth Is required Repeated as needed Identity Response EAP Request EAP Response with the same type or a Nak EAP Success or failure message
Generic EAP Authentication Flow Authenticator Peer Identity Request Identity Response Repeated as many times as needed EAP Request EAP Response with the same type or a Nak EAP Success or EAP Failure message Identity Request If mutual Auth Is required Repeated as needed Identity Response EAP Request EAP Response with the same type or a Nak EAP Success or failure message
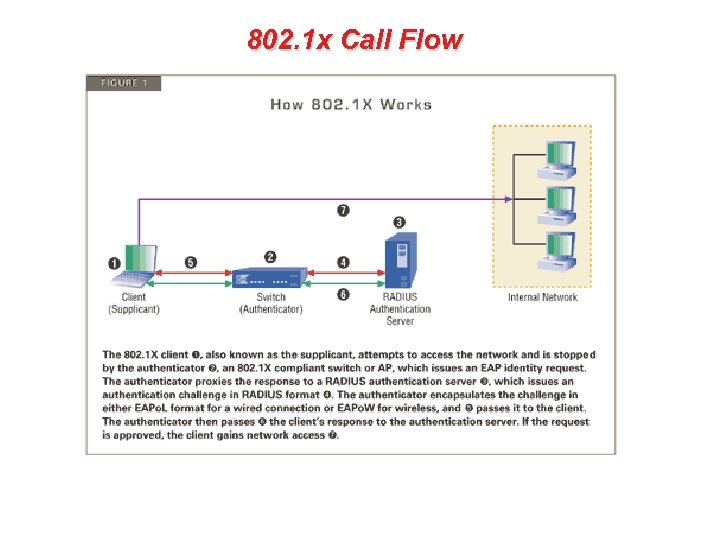
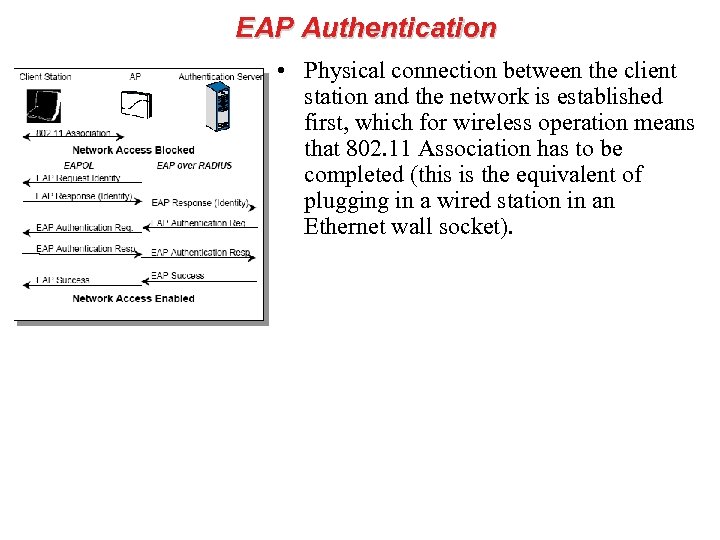 EAP Authentication • Physical connection between the client station and the network is established first, which for wireless operation means that 802. 11 Association has to be completed (this is the equivalent of plugging in a wired station in an Ethernet wall socket).
EAP Authentication • Physical connection between the client station and the network is established first, which for wireless operation means that 802. 11 Association has to be completed (this is the equivalent of plugging in a wired station in an Ethernet wall socket).
 EAP Authentication • After Association the 802. 1 x authentication commences, initiated by the Authenticator (i. e. the AP or NAS), which sends an EAP Request to the Supplicant (i. e. the client station) asking for its credentials. These credentials could be machine name or user name, depending on the authentication method that is used.
EAP Authentication • After Association the 802. 1 x authentication commences, initiated by the Authenticator (i. e. the AP or NAS), which sends an EAP Request to the Supplicant (i. e. the client station) asking for its credentials. These credentials could be machine name or user name, depending on the authentication method that is used.
 EAP Authentication • The Supplicant transmits identity information as part of an EAP response to the Authenticator, which takes the packet from the LAN frame and encapsulates it in a RADIUS protocol message for transmission to the Authentication Server.
EAP Authentication • The Supplicant transmits identity information as part of an EAP response to the Authenticator, which takes the packet from the LAN frame and encapsulates it in a RADIUS protocol message for transmission to the Authentication Server.
 EAP Authentication • At this point a sequence of exchanges will take place between the Authentication Server and the Supplicant (via the Authenticator), of which the exact details depend on the Authentication method used. The ultimate result of the complete sequence is either a positive result, where the supplicant is successfully authenticated, or a negative one where the authentication has failed. In the first case the “door” to network is opened and all network resources are now available for the client device, while in the second case the network access remains blocked.
EAP Authentication • At this point a sequence of exchanges will take place between the Authentication Server and the Supplicant (via the Authenticator), of which the exact details depend on the Authentication method used. The ultimate result of the complete sequence is either a positive result, where the supplicant is successfully authenticated, or a negative one where the authentication has failed. In the first case the “door” to network is opened and all network resources are now available for the client device, while in the second case the network access remains blocked.
 EAP Authentication Methods – MD 5 • EAP-Message Digest 5 uses the same challenge handshake protocol as PPP-based CHAP, but the challenges and responses are sent as EAP messages. – MD 5 can be considered as the “lowest common denominator” EAP type. – EAP-MD 5 does not support the use of per session WEP keys, or mutual authentication of Access Point and client. – It also does not support encrypted links for user data, so cannot be used in an 802. 11 i environment. • The EAP-MD 5 authentication algorithm provides one-way password based network authentication of the client.
EAP Authentication Methods – MD 5 • EAP-Message Digest 5 uses the same challenge handshake protocol as PPP-based CHAP, but the challenges and responses are sent as EAP messages. – MD 5 can be considered as the “lowest common denominator” EAP type. – EAP-MD 5 does not support the use of per session WEP keys, or mutual authentication of Access Point and client. – It also does not support encrypted links for user data, so cannot be used in an 802. 11 i environment. • The EAP-MD 5 authentication algorithm provides one-way password based network authentication of the client.
 EAP Authentication Methods – MD 5 • This algorithm can also be used for wireless applications with less stringent wireless LAN security requirements. – Advantage of using EAP-MD 5 is that it is simple to administer for an operator, re-using the database of usernames and passwords which may exist currently. – Disadvantage of using EAP-MD 5 in wireless LAN applications is that no encryption keys are generated. Also, while the protocol can be used by the client to authenticate the network, it is typically used only for the network to authenticate the client.
EAP Authentication Methods – MD 5 • This algorithm can also be used for wireless applications with less stringent wireless LAN security requirements. – Advantage of using EAP-MD 5 is that it is simple to administer for an operator, re-using the database of usernames and passwords which may exist currently. – Disadvantage of using EAP-MD 5 in wireless LAN applications is that no encryption keys are generated. Also, while the protocol can be used by the client to authenticate the network, it is typically used only for the network to authenticate the client.
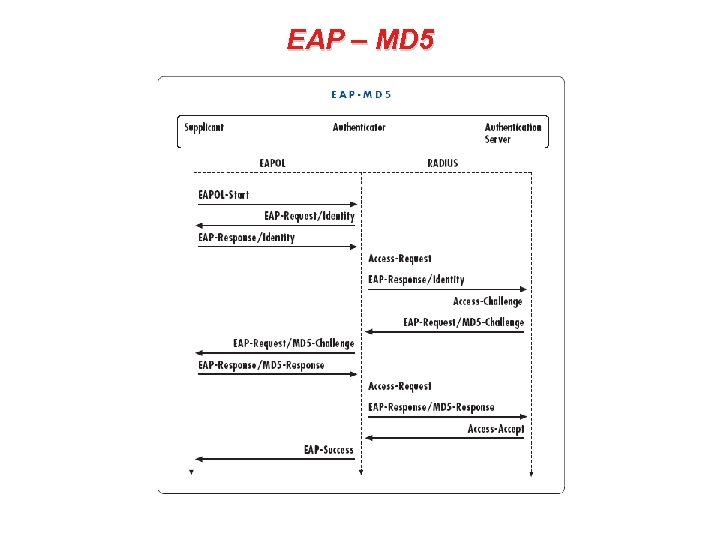
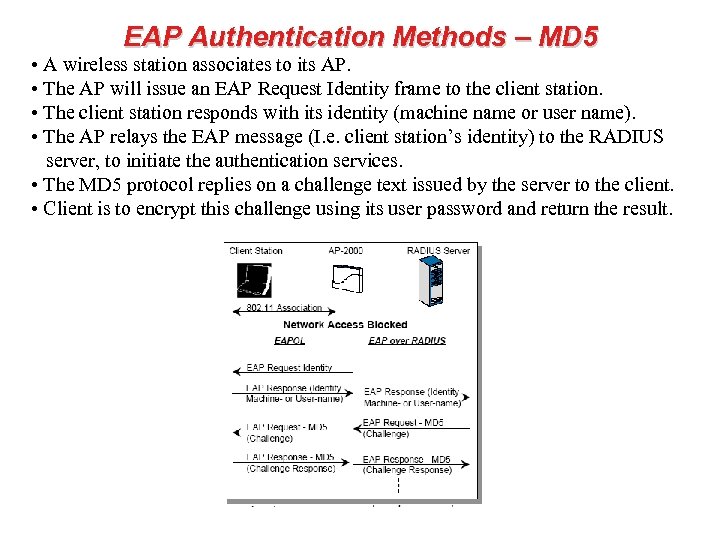 EAP Authentication Methods – MD 5 • A wireless station associates to its AP. • The AP will issue an EAP Request Identity frame to the client station. • The client station responds with its identity (machine name or user name). • The AP relays the EAP message (I. e. client station’s identity) to the RADIUS server, to initiate the authentication services. • The MD 5 protocol replies on a challenge text issued by the server to the client. • Client is to encrypt this challenge using its user password and return the result.
EAP Authentication Methods – MD 5 • A wireless station associates to its AP. • The AP will issue an EAP Request Identity frame to the client station. • The client station responds with its identity (machine name or user name). • The AP relays the EAP message (I. e. client station’s identity) to the RADIUS server, to initiate the authentication services. • The MD 5 protocol replies on a challenge text issued by the server to the client. • Client is to encrypt this challenge using its user password and return the result.
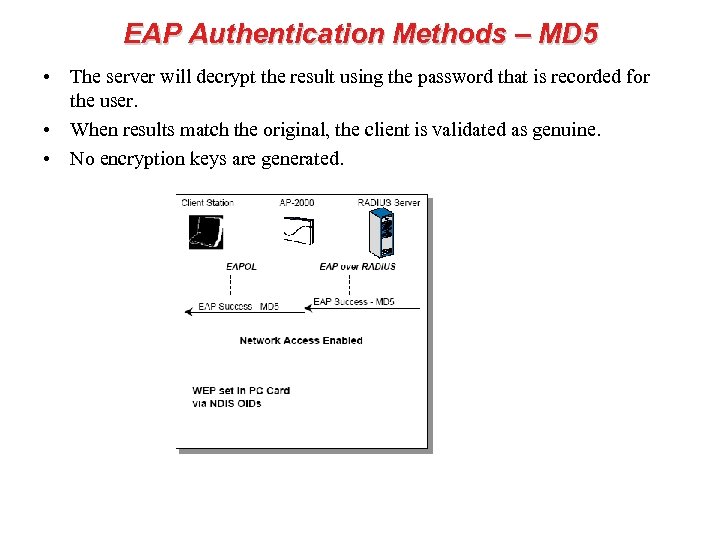 EAP Authentication Methods – MD 5 • The server will decrypt the result using the password that is recorded for the user. • When results match the original, the client is validated as genuine. • No encryption keys are generated.
EAP Authentication Methods – MD 5 • The server will decrypt the result using the password that is recorded for the user. • When results match the original, the client is validated as genuine. • No encryption keys are generated.
 EAP – MD 5
EAP – MD 5
 EAP Authentication Methods – TLS • Transport Layer Security (TLS) is a certificate based authentication protocol. RFC 2716 provides mutual authentication and supports per-session WEP keys. • Certificate based authentication provides a highly secure digital equivalent of ID cards used by both the client and network so they can authenticate each other. Public Key Infrastructure (PKI) digital signature techniques are used to prove each party’s authenticity.
EAP Authentication Methods – TLS • Transport Layer Security (TLS) is a certificate based authentication protocol. RFC 2716 provides mutual authentication and supports per-session WEP keys. • Certificate based authentication provides a highly secure digital equivalent of ID cards used by both the client and network so they can authenticate each other. Public Key Infrastructure (PKI) digital signature techniques are used to prove each party’s authenticity.
 EAP Authentication Methods – TLS • A digital certificate is comprised of the following fields: – – – – – a version certificate serial number signature algorithm identifier name of the issuer validity period name public key optional unique identifiers a signature value.
EAP Authentication Methods – TLS • A digital certificate is comprised of the following fields: – – – – – a version certificate serial number signature algorithm identifier name of the issuer validity period name public key optional unique identifiers a signature value.
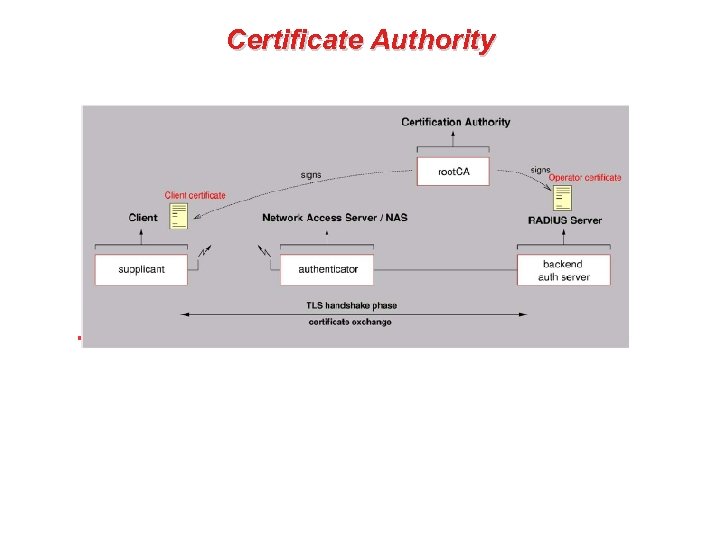 Certificate Authority
Certificate Authority
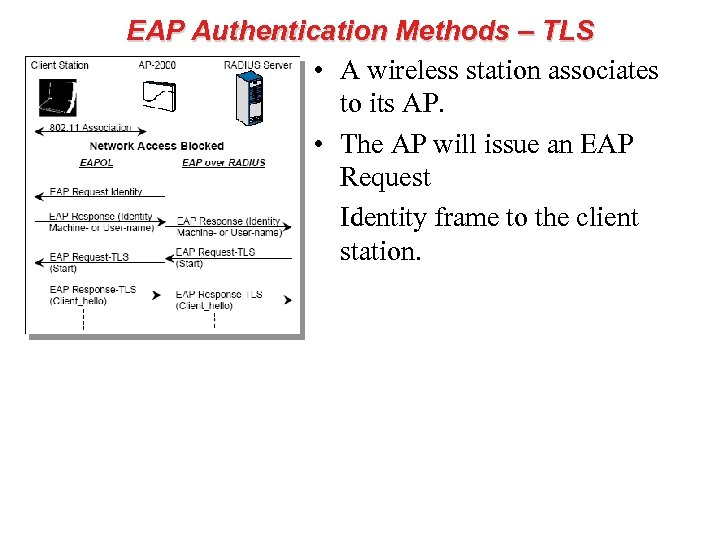 EAP Authentication Methods – TLS • A wireless station associates to its AP. • The AP will issue an EAP Request Identity frame to the client station.
EAP Authentication Methods – TLS • A wireless station associates to its AP. • The AP will issue an EAP Request Identity frame to the client station.
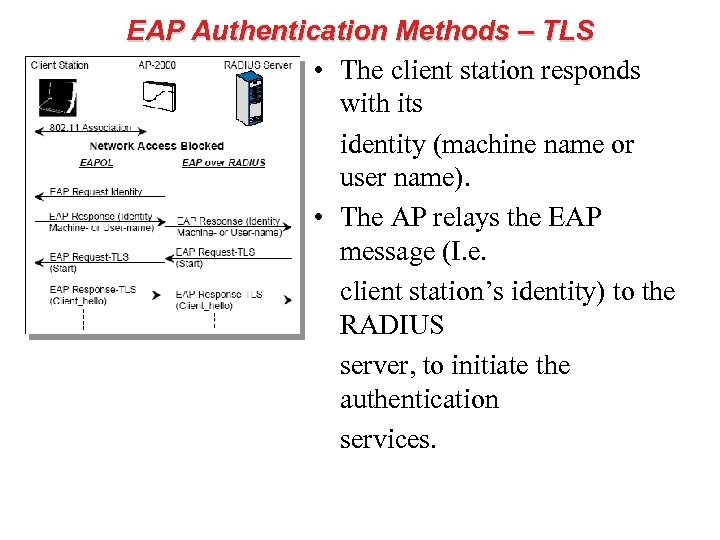 EAP Authentication Methods – TLS • The client station responds with its identity (machine name or user name). • The AP relays the EAP message (I. e. client station’s identity) to the RADIUS server, to initiate the authentication services.
EAP Authentication Methods – TLS • The client station responds with its identity (machine name or user name). • The AP relays the EAP message (I. e. client station’s identity) to the RADIUS server, to initiate the authentication services.
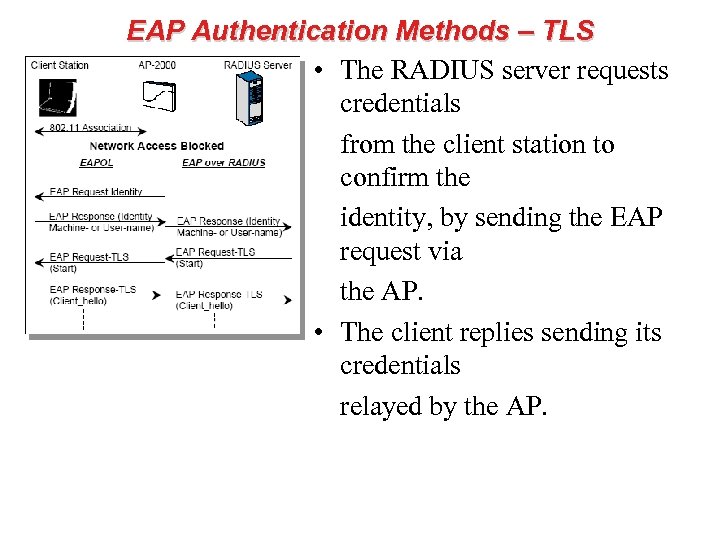 EAP Authentication Methods – TLS • The RADIUS server requests credentials from the client station to confirm the identity, by sending the EAP request via the AP. • The client replies sending its credentials relayed by the AP.
EAP Authentication Methods – TLS • The RADIUS server requests credentials from the client station to confirm the identity, by sending the EAP request via the AP. • The client replies sending its credentials relayed by the AP.
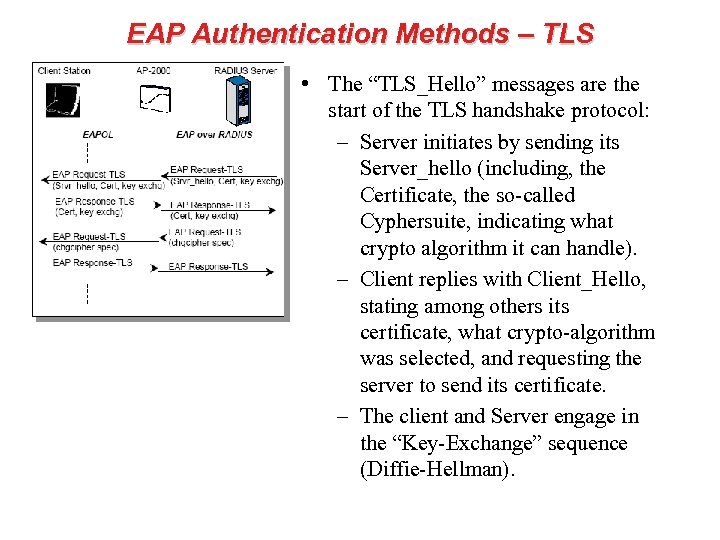 EAP Authentication Methods – TLS • The “TLS_Hello” messages are the start of the TLS handshake protocol: – Server initiates by sending its Server_hello (including, the Certificate, the so-called Cyphersuite, indicating what crypto algorithm it can handle). – Client replies with Client_Hello, stating among others its certificate, what crypto-algorithm was selected, and requesting the server to send its certificate. – The client and Server engage in the “Key-Exchange” sequence (Diffie-Hellman).
EAP Authentication Methods – TLS • The “TLS_Hello” messages are the start of the TLS handshake protocol: – Server initiates by sending its Server_hello (including, the Certificate, the so-called Cyphersuite, indicating what crypto algorithm it can handle). – Client replies with Client_Hello, stating among others its certificate, what crypto-algorithm was selected, and requesting the server to send its certificate. – The client and Server engage in the “Key-Exchange” sequence (Diffie-Hellman).
 EAP Authentication Methods – TLS • On completion of the DH Key exchange between server and client, the server transmits keys to the AP. • To encrypt subsequent IEEE 802. 11 frames exchanged between the AP and the client, a WEP key pair is used, that is generated by the AP, and is the same for all clients associated to this particular AP. • The AP will transmit this key pair to the client and uses the key received from the server to encrypt this message. • Once the client received the WEP keys it will pass them to the PC card via the NDIS interface and the driver. • Station and AP will use these WEP keys until station logs off or until reauthentication timer has expired (for period re-authentication). • When station roams to another AP a re-authentication is required and new WEP keys are established.
EAP Authentication Methods – TLS • On completion of the DH Key exchange between server and client, the server transmits keys to the AP. • To encrypt subsequent IEEE 802. 11 frames exchanged between the AP and the client, a WEP key pair is used, that is generated by the AP, and is the same for all clients associated to this particular AP. • The AP will transmit this key pair to the client and uses the key received from the server to encrypt this message. • Once the client received the WEP keys it will pass them to the PC card via the NDIS interface and the driver. • Station and AP will use these WEP keys until station logs off or until reauthentication timer has expired (for period re-authentication). • When station roams to another AP a re-authentication is required and new WEP keys are established.
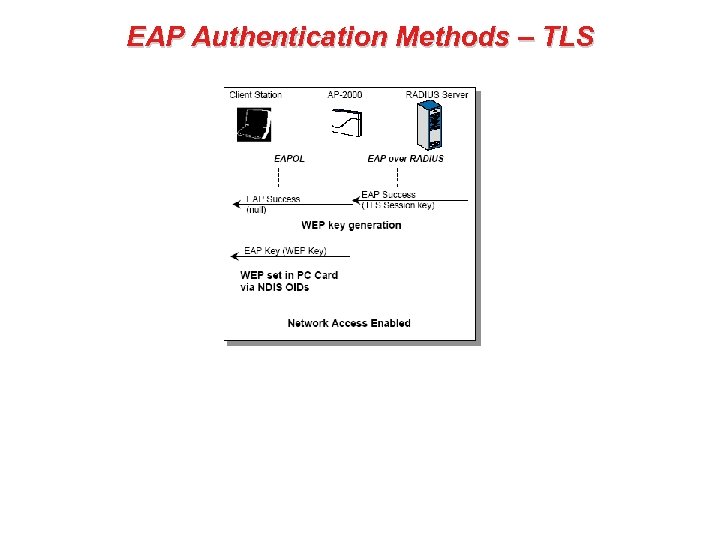 EAP Authentication Methods – TLS
EAP Authentication Methods – TLS
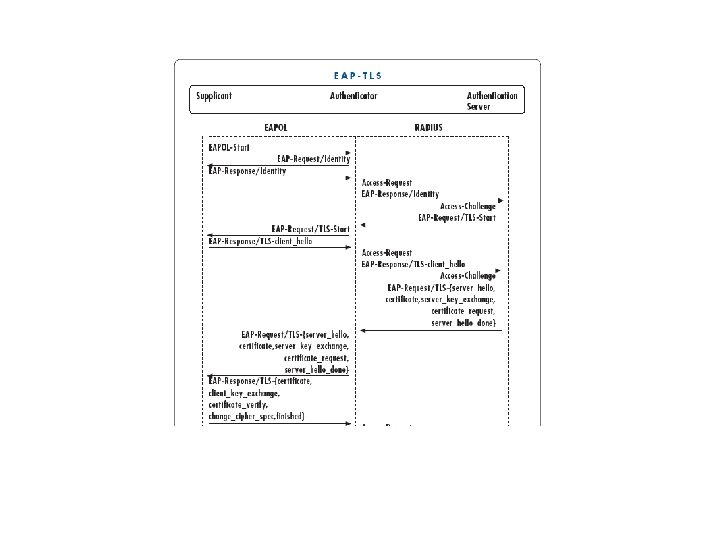
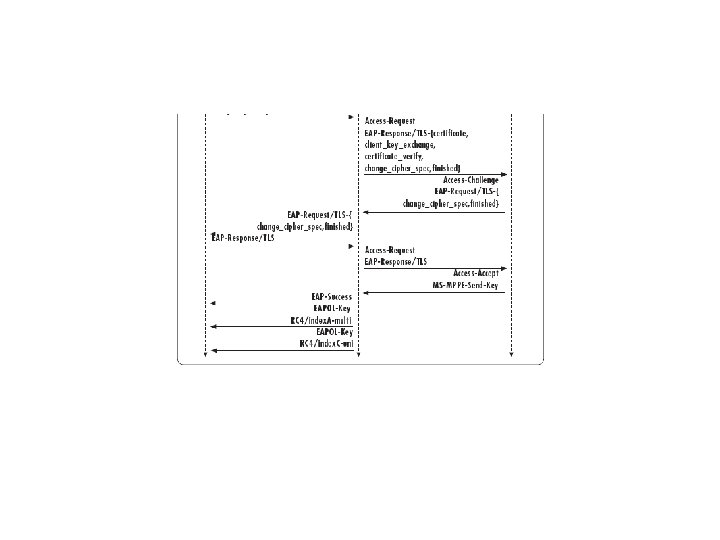
 EAP Authentication Methods – TTLS • • Tunneled Transport Layer Security (TTLS) and Protected Extensible Authentication Protocol (PEAP) are similar in operation and support both secure username/password and mutual authentication. EAP-TTLS a combination of both EAP-TLS, and traditional password-based methods such as Challenge Handshake Authentication Protocol (CHAP), and One Time Password (OTP). On the client side merely passwords are required instead of digital certificates, which relieves the administrator of the systems to manage and distribute certificates. On the authentication server side a certificate is required. Certificates do not have to be installed in each client device. This is because PKI techniques are used to first allow the client to authenticate the server (via a certificate installed on the server) and form a secured connection between client and server. Then the server authenticates the client over the secured connection with the user providing a username and password pair. This principle is much like the way in which browser based commerce takes place today over web browsers. Secure connections are established before the user’s authentication information is exchanged. Users see this typically as a padlock symbol in their browsers.
EAP Authentication Methods – TTLS • • Tunneled Transport Layer Security (TTLS) and Protected Extensible Authentication Protocol (PEAP) are similar in operation and support both secure username/password and mutual authentication. EAP-TTLS a combination of both EAP-TLS, and traditional password-based methods such as Challenge Handshake Authentication Protocol (CHAP), and One Time Password (OTP). On the client side merely passwords are required instead of digital certificates, which relieves the administrator of the systems to manage and distribute certificates. On the authentication server side a certificate is required. Certificates do not have to be installed in each client device. This is because PKI techniques are used to first allow the client to authenticate the server (via a certificate installed on the server) and form a secured connection between client and server. Then the server authenticates the client over the secured connection with the user providing a username and password pair. This principle is much like the way in which browser based commerce takes place today over web browsers. Secure connections are established before the user’s authentication information is exchanged. Users see this typically as a padlock symbol in their browsers.
 EAP Authentication Methods – TTLS • In EAP-TTLS a secure TLS tunnel is first established between the supplicant and the authentication server. • The client authenticates the network to which it is connecting by authenticating the digital certificate provided by the TTLS server. This is exactly analogous to the techniques used to connect to a secure web server. Once an authenticated “tunnel” is established, the authentication of the end user occurs. • EAP-TTLS has the added benefit of protecting the identity of the end user from view over the wireless medium. In this way anonymity of the end user, a desirable attribute is provided. • EAP-TTLS also enables existing end-user authentication systems to be reused. Two key advantages of EAP-TTLS are that anonymity of the end user is provided, and that any existing RADIUS server and its associated database can be re-used. • EAP-TTLS is the only EAP type to date which provides end user anonymity.
EAP Authentication Methods – TTLS • In EAP-TTLS a secure TLS tunnel is first established between the supplicant and the authentication server. • The client authenticates the network to which it is connecting by authenticating the digital certificate provided by the TTLS server. This is exactly analogous to the techniques used to connect to a secure web server. Once an authenticated “tunnel” is established, the authentication of the end user occurs. • EAP-TTLS has the added benefit of protecting the identity of the end user from view over the wireless medium. In this way anonymity of the end user, a desirable attribute is provided. • EAP-TTLS also enables existing end-user authentication systems to be reused. Two key advantages of EAP-TTLS are that anonymity of the end user is provided, and that any existing RADIUS server and its associated database can be re-used. • EAP-TTLS is the only EAP type to date which provides end user anonymity.
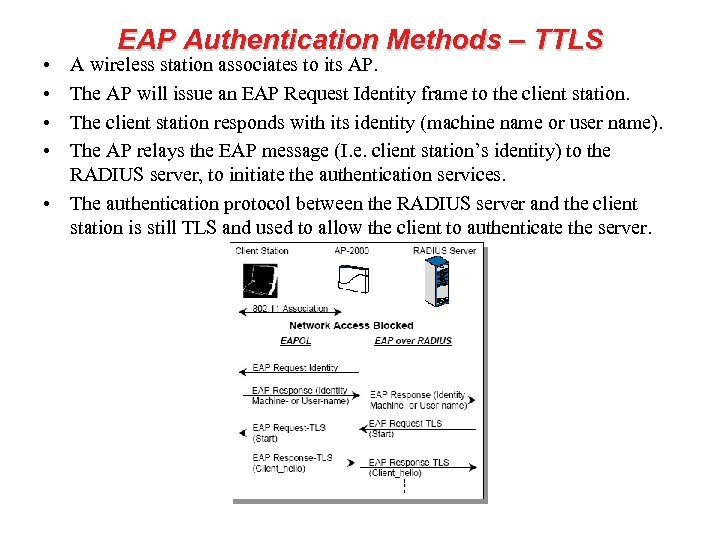 • • EAP Authentication Methods – TTLS A wireless station associates to its AP. The AP will issue an EAP Request Identity frame to the client station. The client station responds with its identity (machine name or user name). The AP relays the EAP message (I. e. client station’s identity) to the RADIUS server, to initiate the authentication services. • The authentication protocol between the RADIUS server and the client station is still TLS and used to allow the client to authenticate the server.
• • EAP Authentication Methods – TTLS A wireless station associates to its AP. The AP will issue an EAP Request Identity frame to the client station. The client station responds with its identity (machine name or user name). The AP relays the EAP message (I. e. client station’s identity) to the RADIUS server, to initiate the authentication services. • The authentication protocol between the RADIUS server and the client station is still TLS and used to allow the client to authenticate the server.
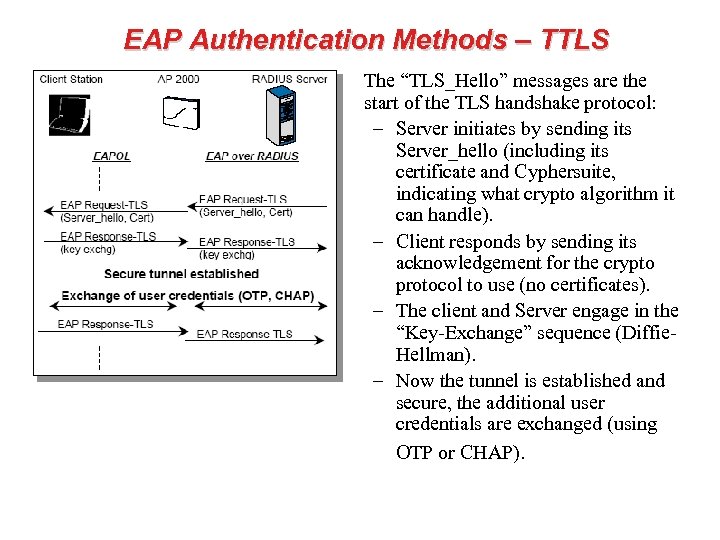 EAP Authentication Methods – TTLS • The “TLS_Hello” messages are the start of the TLS handshake protocol: – Server initiates by sending its Server_hello (including its certificate and Cyphersuite, indicating what crypto algorithm it can handle). – Client responds by sending its acknowledgement for the crypto protocol to use (no certificates). – The client and Server engage in the “Key-Exchange” sequence (Diffie. Hellman). – Now the tunnel is established and secure, the additional user credentials are exchanged (using OTP or CHAP).
EAP Authentication Methods – TTLS • The “TLS_Hello” messages are the start of the TLS handshake protocol: – Server initiates by sending its Server_hello (including its certificate and Cyphersuite, indicating what crypto algorithm it can handle). – Client responds by sending its acknowledgement for the crypto protocol to use (no certificates). – The client and Server engage in the “Key-Exchange” sequence (Diffie. Hellman). – Now the tunnel is established and secure, the additional user credentials are exchanged (using OTP or CHAP).
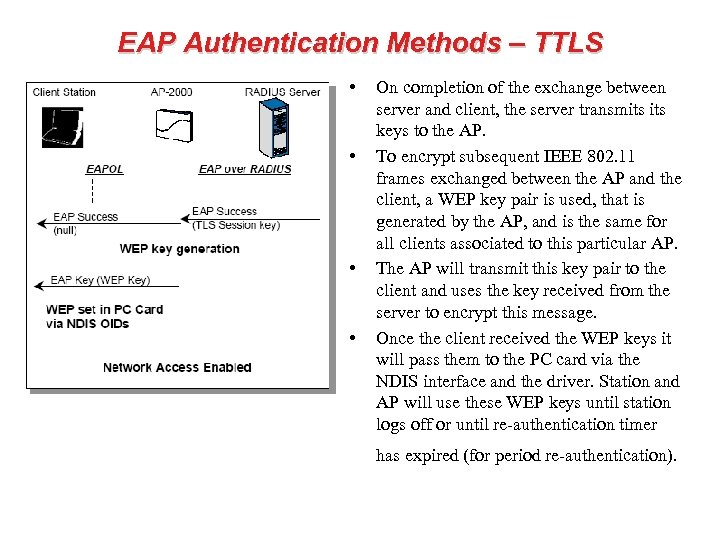 EAP Authentication Methods – TTLS • • On completion of the exchange between server and client, the server transmits keys to the AP. To encrypt subsequent IEEE 802. 11 frames exchanged between the AP and the client, a WEP key pair is used, that is generated by the AP, and is the same for all clients associated to this particular AP. The AP will transmit this key pair to the client and uses the key received from the server to encrypt this message. Once the client received the WEP keys it will pass them to the PC card via the NDIS interface and the driver. Station and AP will use these WEP keys until station logs off or until re-authentication timer has expired (for period re-authentication).
EAP Authentication Methods – TTLS • • On completion of the exchange between server and client, the server transmits keys to the AP. To encrypt subsequent IEEE 802. 11 frames exchanged between the AP and the client, a WEP key pair is used, that is generated by the AP, and is the same for all clients associated to this particular AP. The AP will transmit this key pair to the client and uses the key received from the server to encrypt this message. Once the client received the WEP keys it will pass them to the PC card via the NDIS interface and the driver. Station and AP will use these WEP keys until station logs off or until re-authentication timer has expired (for period re-authentication).
 EAP Authentication Methods – TTLS
EAP Authentication Methods – TTLS
 EAP Authentication Methods – SRP • SRP (Secure Remote Password) is a secure password-based authentication and key-exchange protocol. • It solves the problem of authenticating clients to servers securely, in cases where the user of the client software must memorize a small secret (like a password) and carries no other secret information. • The server stores a verifier for each user, which allows it to authenticate the client but which, if compromised, would not allow the attacker to impersonate the client. SRP also exchanges a cryptographically-strong secret as a byproduct of successful authentication, which enables the two parties to communicate securely. • A key advantage of SRP is that the user’s password need not be stored in the RADIUS database. SRP is also a completely password based authentication system. No certificates are required.
EAP Authentication Methods – SRP • SRP (Secure Remote Password) is a secure password-based authentication and key-exchange protocol. • It solves the problem of authenticating clients to servers securely, in cases where the user of the client software must memorize a small secret (like a password) and carries no other secret information. • The server stores a verifier for each user, which allows it to authenticate the client but which, if compromised, would not allow the attacker to impersonate the client. SRP also exchanges a cryptographically-strong secret as a byproduct of successful authentication, which enables the two parties to communicate securely. • A key advantage of SRP is that the user’s password need not be stored in the RADIUS database. SRP is also a completely password based authentication system. No certificates are required.
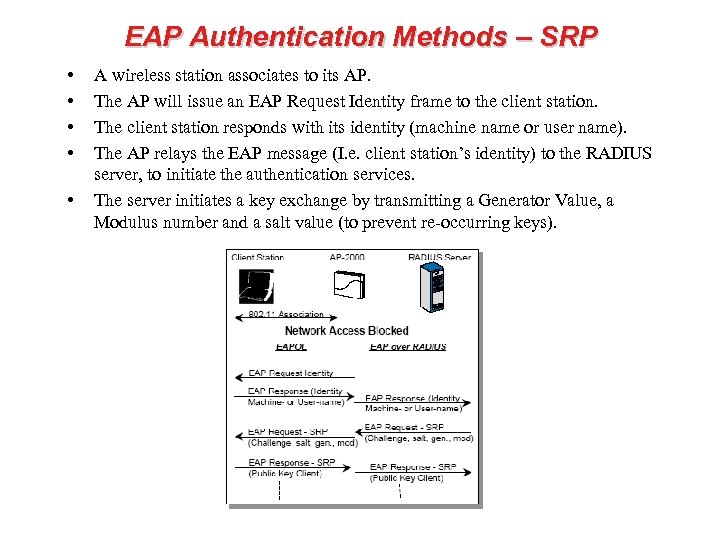 EAP Authentication Methods – SRP • • • A wireless station associates to its AP. The AP will issue an EAP Request Identity frame to the client station. The client station responds with its identity (machine name or user name). The AP relays the EAP message (I. e. client station’s identity) to the RADIUS server, to initiate the authentication services. The server initiates a key exchange by transmitting a Generator Value, a Modulus number and a salt value (to prevent re-occurring keys).
EAP Authentication Methods – SRP • • • A wireless station associates to its AP. The AP will issue an EAP Request Identity frame to the client station. The client station responds with its identity (machine name or user name). The AP relays the EAP message (I. e. client station’s identity) to the RADIUS server, to initiate the authentication services. The server initiates a key exchange by transmitting a Generator Value, a Modulus number and a salt value (to prevent re-occurring keys).
 EAP Authentication Methods – SRP • The client calculates its Public Key as: • K(client) = ga (mod N), where “a” is randomly chosen (client’s private key). • The Server executes a similar procedure and calculates its Public Key as: • K(Server) = (v+gb) (mod N), where “b” is randomly chosen (Server’s private key), and is a stored verifier from the database. • With key’s in place, the client and server mutually validate each other.
EAP Authentication Methods – SRP • The client calculates its Public Key as: • K(client) = ga (mod N), where “a” is randomly chosen (client’s private key). • The Server executes a similar procedure and calculates its Public Key as: • K(Server) = (v+gb) (mod N), where “b” is randomly chosen (Server’s private key), and is a stored verifier from the database. • With key’s in place, the client and server mutually validate each other.
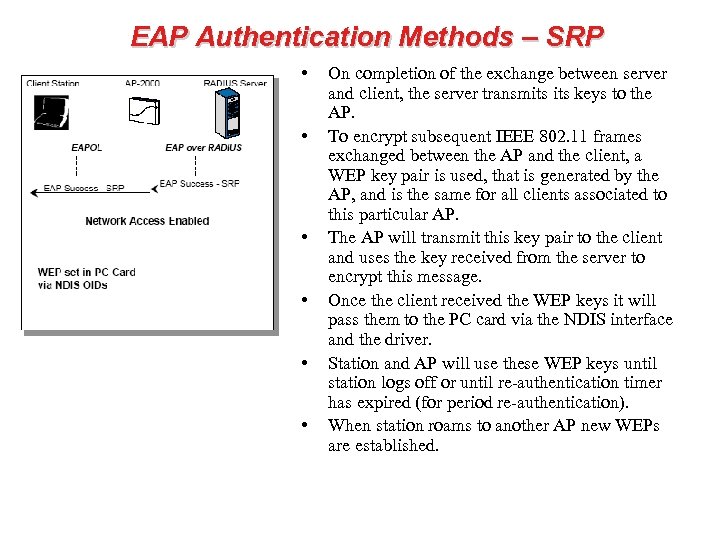 EAP Authentication Methods – SRP • • • On completion of the exchange between server and client, the server transmits keys to the AP. To encrypt subsequent IEEE 802. 11 frames exchanged between the AP and the client, a WEP key pair is used, that is generated by the AP, and is the same for all clients associated to this particular AP. The AP will transmit this key pair to the client and uses the key received from the server to encrypt this message. Once the client received the WEP keys it will pass them to the PC card via the NDIS interface and the driver. Station and AP will use these WEP keys until station logs off or until re-authentication timer has expired (for period re-authentication). When station roams to another AP new WEPs are established.
EAP Authentication Methods – SRP • • • On completion of the exchange between server and client, the server transmits keys to the AP. To encrypt subsequent IEEE 802. 11 frames exchanged between the AP and the client, a WEP key pair is used, that is generated by the AP, and is the same for all clients associated to this particular AP. The AP will transmit this key pair to the client and uses the key received from the server to encrypt this message. Once the client received the WEP keys it will pass them to the PC card via the NDIS interface and the driver. Station and AP will use these WEP keys until station logs off or until re-authentication timer has expired (for period re-authentication). When station roams to another AP new WEPs are established.
 EAP Authentication Methods – LEAP • Cisco delivers a special version of EAP (Extensible Authentication Protocol), known as LEAP (where the “L” stands for lightweight). • Though the Cisco systems can be configured to operate with other EAP protocols (and as such are capable of communicating with off the shelf Radius implementations that support IEEE 802. 1 x), this proprietary version is promoted by Cisco in order to offer a complete Cisco solution. • LEAP also is known to have significant flaws: – The key used for encryption between client and Access Point is derived from the username and password stored at the Authentication server and used by the client station during log-in. The method used in this case is MSCHAP v 1, and known in the industry to be vulnerable and hack-able by existing hack tools. – The EAP exchange between client and authentication server is not encrypted, as the key is not yet determined. The username is transmitted in the clear and the only the password is protected by an MSCHAP v 1 hash, which is relatively easy to hack.
EAP Authentication Methods – LEAP • Cisco delivers a special version of EAP (Extensible Authentication Protocol), known as LEAP (where the “L” stands for lightweight). • Though the Cisco systems can be configured to operate with other EAP protocols (and as such are capable of communicating with off the shelf Radius implementations that support IEEE 802. 1 x), this proprietary version is promoted by Cisco in order to offer a complete Cisco solution. • LEAP also is known to have significant flaws: – The key used for encryption between client and Access Point is derived from the username and password stored at the Authentication server and used by the client station during log-in. The method used in this case is MSCHAP v 1, and known in the industry to be vulnerable and hack-able by existing hack tools. – The EAP exchange between client and authentication server is not encrypted, as the key is not yet determined. The username is transmitted in the clear and the only the password is protected by an MSCHAP v 1 hash, which is relatively easy to hack.
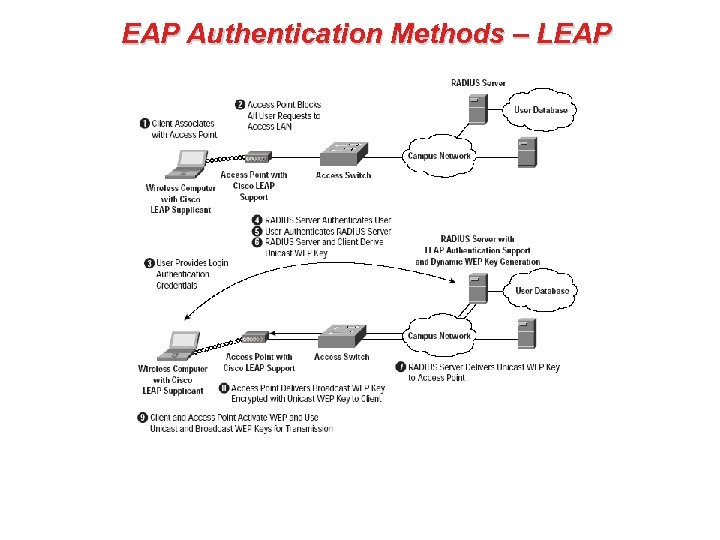 EAP Authentication Methods – LEAP
EAP Authentication Methods – LEAP
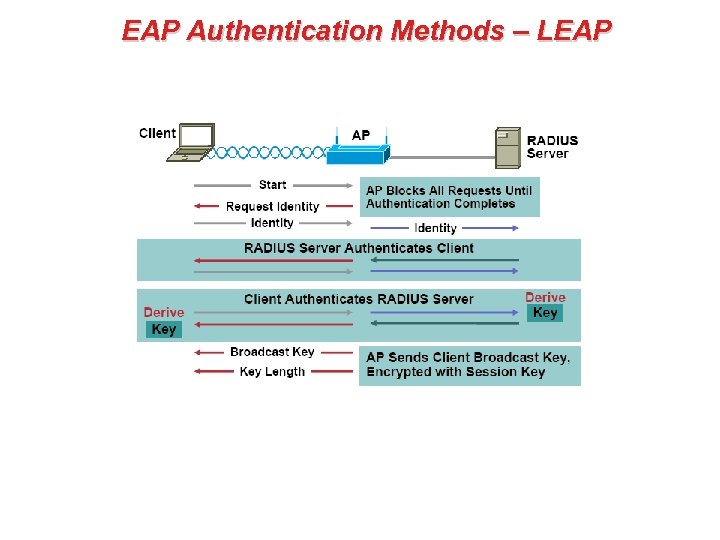 EAP Authentication Methods – LEAP
EAP Authentication Methods – LEAP
 EAP Authentication Methods – PEAP • Protected EAP (PEAP): A version of EAP developed by Microsoft, Cisco, and RSA Security that offers two implementation options. • The first uses the Microsoft Challenge-Handshake Authentication Protocol Version 2 (MS-CHAPv 2) for mutual authentication and does not require client digital certificates. • The second implementation uses TLS for mutual authentication and requires digital certificates on all the clients (very similar to EAP-TLS).
EAP Authentication Methods – PEAP • Protected EAP (PEAP): A version of EAP developed by Microsoft, Cisco, and RSA Security that offers two implementation options. • The first uses the Microsoft Challenge-Handshake Authentication Protocol Version 2 (MS-CHAPv 2) for mutual authentication and does not require client digital certificates. • The second implementation uses TLS for mutual authentication and requires digital certificates on all the clients (very similar to EAP-TLS).
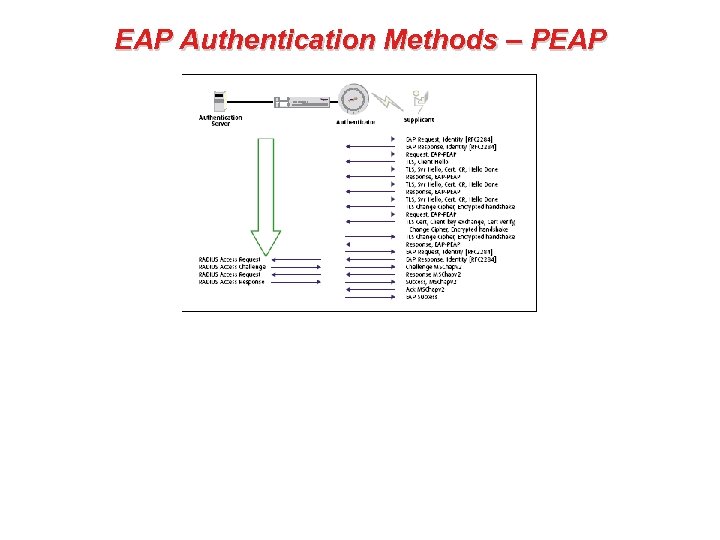 EAP Authentication Methods – PEAP
EAP Authentication Methods – PEAP
 PEAP w MS-CHAPv 2 • • The PEAP authentication process occurs in two parts. The first part is the use of EAP and the PEAP type to create an encrypted TLS channel. The second part is the use of EAP and a different EAP type to authenticate network access. The following examines PEAP with MS-CHAP v 2 operation, using as an example, a wireless client that attempts to authenticate to a wireless access point (AP) that uses a RADIUS server for authentication and authorization.
PEAP w MS-CHAPv 2 • • The PEAP authentication process occurs in two parts. The first part is the use of EAP and the PEAP type to create an encrypted TLS channel. The second part is the use of EAP and a different EAP type to authenticate network access. The following examines PEAP with MS-CHAP v 2 operation, using as an example, a wireless client that attempts to authenticate to a wireless access point (AP) that uses a RADIUS server for authentication and authorization.
 PEAP w MS-CHAPv 2 • PEAP Part 1 -Creating the TLS Channel – The following steps are used to create the PEAP TLS channel: • After creating the logical link, the wireless AP sends an EAPRequest/Identity message to the wireless client. • The wireless client responds with an EAP-Response/Identity message that contains the identity (user or computer name) of the wireless client. • The EAP-Response/Identity message is sent by the wireless AP to the RADIUS server. From this point on, the logical communication occurs between the RADIUS server and the wireless client, using the wireless AP as a pass-through device. • The RADIUS server sends an EAP-Request/Start PEAP message to the wireless client. • The wireless client and the RADIUS server exchange a series of TLS messages through which the cipher suite for the TLS channel is negotiated and the RADIUS server sends a certificate chain to the wireless client for authentication. – At the end of the PEAP negotiation, the RADIUS server has authenticated itself to the wireless client. Both nodes have determined mutual encryption and signing keys (using public key cryptography, not passwords) for the TLS channel.
PEAP w MS-CHAPv 2 • PEAP Part 1 -Creating the TLS Channel – The following steps are used to create the PEAP TLS channel: • After creating the logical link, the wireless AP sends an EAPRequest/Identity message to the wireless client. • The wireless client responds with an EAP-Response/Identity message that contains the identity (user or computer name) of the wireless client. • The EAP-Response/Identity message is sent by the wireless AP to the RADIUS server. From this point on, the logical communication occurs between the RADIUS server and the wireless client, using the wireless AP as a pass-through device. • The RADIUS server sends an EAP-Request/Start PEAP message to the wireless client. • The wireless client and the RADIUS server exchange a series of TLS messages through which the cipher suite for the TLS channel is negotiated and the RADIUS server sends a certificate chain to the wireless client for authentication. – At the end of the PEAP negotiation, the RADIUS server has authenticated itself to the wireless client. Both nodes have determined mutual encryption and signing keys (using public key cryptography, not passwords) for the TLS channel.
![EAP Authentication Methods – PEAP EAP-Request / Identity EAP- Response / Identity [My Domain] EAP Authentication Methods – PEAP EAP-Request / Identity EAP- Response / Identity [My Domain]](https://present5.com/presentation/3de1888d74398634c5f14dfdbd14d0dc/image-111.jpg) EAP Authentication Methods – PEAP EAP-Request / Identity EAP- Response / Identity [My Domain] EAP-Request (Type = PEAP, start) Client TLS Handshake EAP- Response (empty) PEAP Server
EAP Authentication Methods – PEAP EAP-Request / Identity EAP- Response / Identity [My Domain] EAP-Request (Type = PEAP, start) Client TLS Handshake EAP- Response (empty) PEAP Server
 PEAP w MS-CHAPv 2 • PEAP Part 2 -Authenticating With MS-CHAP v 2 – After the PEAP TLS channel is created, the following steps are used to authenticate the wireless client credentials with MS-CHAP v 2: • The RADIUS server sends an EAP-Request/Identity message. • The wireless client responds with an EAP-Response/Identity message that contains the identity (user or computer name) of the wireless client. • The RADIUS server sends an EAP-Request/EAP-MS-CHAP-V 2 Challenge message that contains a challenge string. • The wireless client responds with an EAP-Response/EAP-MS-CHAP-V 2 Response message that contains both the response to the RADIUS server challenge string and a challenge string for the RADIUS server. • The RADIUS server sends an EAP-Request/EAP-MS-CHAP-V 2 Success message, which indicates that the wireless client response was correct and contains the response to the wireless client challenge string. • The wireless client responds with an EAP-Response/EAP-MS-CHAP-V 2 Ack message, indicating that the RADIUS server response was correct. • The RADIUS server sends an EAP-Success message. – At the end of this mutual authentication exchange, the wireless client has provided proof of knowledge of the correct password (the response to the RADIUS server challenge string), and the RADIUS server has provided proof of knowledge of the correct password (the response to the wireless client challenge string). The entire exchange is encrypted through the TLS channel created in PEAP part 1.
PEAP w MS-CHAPv 2 • PEAP Part 2 -Authenticating With MS-CHAP v 2 – After the PEAP TLS channel is created, the following steps are used to authenticate the wireless client credentials with MS-CHAP v 2: • The RADIUS server sends an EAP-Request/Identity message. • The wireless client responds with an EAP-Response/Identity message that contains the identity (user or computer name) of the wireless client. • The RADIUS server sends an EAP-Request/EAP-MS-CHAP-V 2 Challenge message that contains a challenge string. • The wireless client responds with an EAP-Response/EAP-MS-CHAP-V 2 Response message that contains both the response to the RADIUS server challenge string and a challenge string for the RADIUS server. • The RADIUS server sends an EAP-Request/EAP-MS-CHAP-V 2 Success message, which indicates that the wireless client response was correct and contains the response to the wireless client challenge string. • The wireless client responds with an EAP-Response/EAP-MS-CHAP-V 2 Ack message, indicating that the RADIUS server response was correct. • The RADIUS server sends an EAP-Success message. – At the end of this mutual authentication exchange, the wireless client has provided proof of knowledge of the correct password (the response to the RADIUS server challenge string), and the RADIUS server has provided proof of knowledge of the correct password (the response to the wireless client challenge string). The entire exchange is encrypted through the TLS channel created in PEAP part 1.
![EAP Authentication Methods – PEAP EAP-Request / Identity EAP-Response / Identity [My ID] EAP-Request EAP Authentication Methods – PEAP EAP-Request / Identity EAP-Response / Identity [My ID] EAP-Request](https://present5.com/presentation/3de1888d74398634c5f14dfdbd14d0dc/image-113.jpg) EAP Authentication Methods – PEAP EAP-Request / Identity EAP-Response / Identity [My ID] EAP-Request / Type = X (MD 5, OTP, etc) Establish EAP method and Perform authentication Client EAP-Success / EAP-Failure PEAP Server Transfer of the generated key from the PEAP server to the NAS if on different machines
EAP Authentication Methods – PEAP EAP-Request / Identity EAP-Response / Identity [My ID] EAP-Request / Type = X (MD 5, OTP, etc) Establish EAP method and Perform authentication Client EAP-Success / EAP-Failure PEAP Server Transfer of the generated key from the PEAP server to the NAS if on different machines
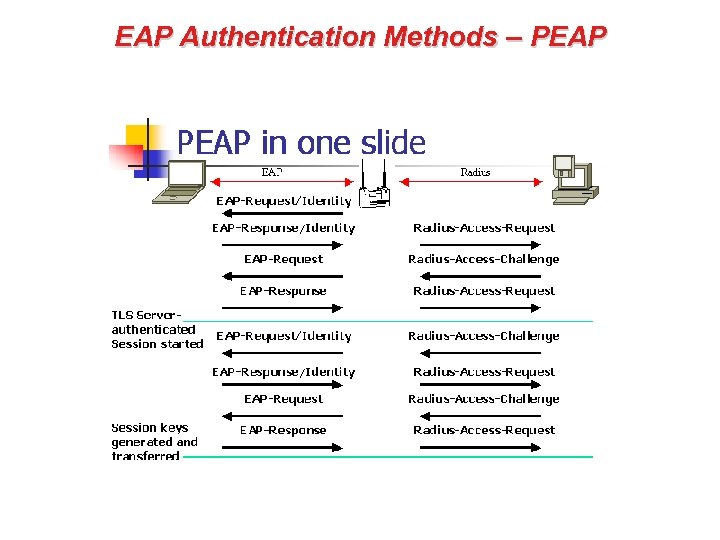 EAP Authentication Methods – PEAP
EAP Authentication Methods – PEAP
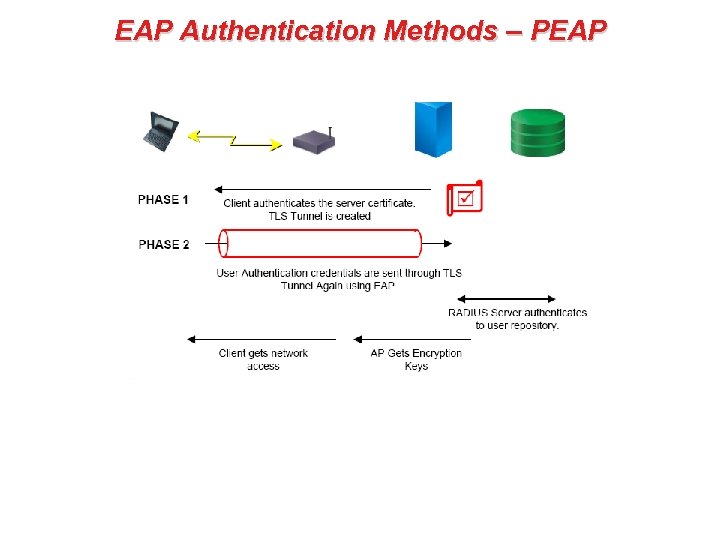 EAP Authentication Methods – PEAP
EAP Authentication Methods – PEAP
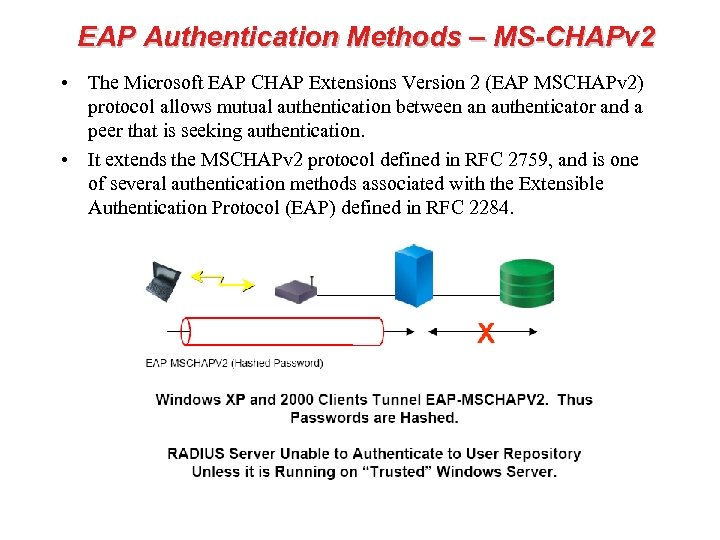 EAP Authentication Methods – MS-CHAPv 2 • The Microsoft EAP CHAP Extensions Version 2 (EAP MSCHAPv 2) protocol allows mutual authentication between an authenticator and a peer that is seeking authentication. • It extends the MSCHAPv 2 protocol defined in RFC 2759, and is one of several authentication methods associated with the Extensible Authentication Protocol (EAP) defined in RFC 2284.
EAP Authentication Methods – MS-CHAPv 2 • The Microsoft EAP CHAP Extensions Version 2 (EAP MSCHAPv 2) protocol allows mutual authentication between an authenticator and a peer that is seeking authentication. • It extends the MSCHAPv 2 protocol defined in RFC 2759, and is one of several authentication methods associated with the Extensible Authentication Protocol (EAP) defined in RFC 2284.
 MS-CHAPv 2, What is? • Peer authentication using MS-CHAPv 2. Following stages take place after a PPTP tunnel is established and the setup for the PPP connection has started. – The client requests an authenticator challenge from the server. – The server sends back a 16 -bytes random authenticator challenge. – The client generates the response: • The client generates 16 -bytes random peer challenge. • The client generates the challenge by hashing the authenticator challenge, the peer challenge, and the user's login using SHA. • The client generates the NT password hash from the user's password. • The 16 -byte NT password hash from step (c) is padded with 5 bytes of zero. From these 21 bytes three 7 -byte DES keys are derived. • The first 8 bytes of the hash generated in step (b) (these 8 bytes are later referred to as the challenge) are encrypted using DES with each of the three keys generated in step (d). • The 24 bytes resulting from step (e), the 16 -byte random peer challenge, and the user's login are sent back to the server as response.
MS-CHAPv 2, What is? • Peer authentication using MS-CHAPv 2. Following stages take place after a PPTP tunnel is established and the setup for the PPP connection has started. – The client requests an authenticator challenge from the server. – The server sends back a 16 -bytes random authenticator challenge. – The client generates the response: • The client generates 16 -bytes random peer challenge. • The client generates the challenge by hashing the authenticator challenge, the peer challenge, and the user's login using SHA. • The client generates the NT password hash from the user's password. • The 16 -byte NT password hash from step (c) is padded with 5 bytes of zero. From these 21 bytes three 7 -byte DES keys are derived. • The first 8 bytes of the hash generated in step (b) (these 8 bytes are later referred to as the challenge) are encrypted using DES with each of the three keys generated in step (d). • The 24 bytes resulting from step (e), the 16 -byte random peer challenge, and the user's login are sent back to the server as response.
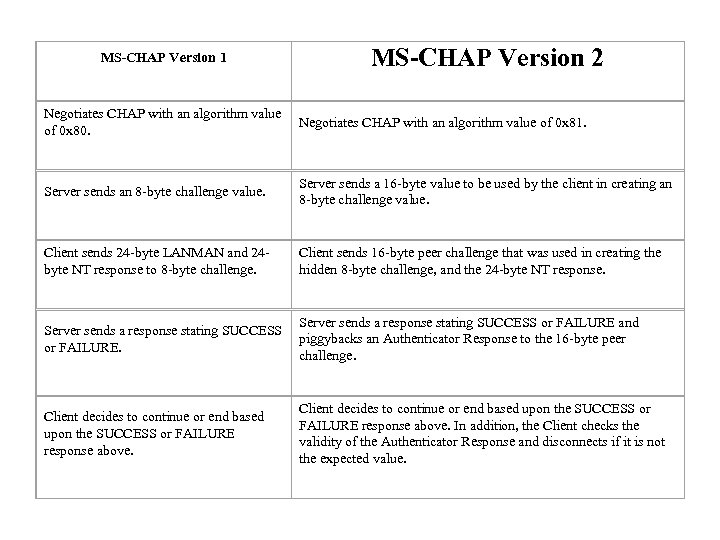 MS-CHAP Version 1 MS-CHAP Version 2 Negotiates CHAP with an algorithm value of 0 x 80. Negotiates CHAP with an algorithm value of 0 x 81. Server sends an 8 -byte challenge value. Server sends a 16 -byte value to be used by the client in creating an 8 -byte challenge value. Client sends 24 -byte LANMAN and 24 byte NT response to 8 -byte challenge. Client sends 16 -byte peer challenge that was used in creating the hidden 8 -byte challenge, and the 24 -byte NT response. Server sends a response stating SUCCESS or FAILURE and Server sends a response stating SUCCESS piggybacks an Authenticator Response to the 16 -byte peer or FAILURE. challenge. Client decides to continue or end based upon the SUCCESS or FAILURE response above. In addition, the Client checks the validity of the Authenticator Response and disconnects if it is not the expected value.
MS-CHAP Version 1 MS-CHAP Version 2 Negotiates CHAP with an algorithm value of 0 x 80. Negotiates CHAP with an algorithm value of 0 x 81. Server sends an 8 -byte challenge value. Server sends a 16 -byte value to be used by the client in creating an 8 -byte challenge value. Client sends 24 -byte LANMAN and 24 byte NT response to 8 -byte challenge. Client sends 16 -byte peer challenge that was used in creating the hidden 8 -byte challenge, and the 24 -byte NT response. Server sends a response stating SUCCESS or FAILURE and Server sends a response stating SUCCESS piggybacks an Authenticator Response to the 16 -byte peer or FAILURE. challenge. Client decides to continue or end based upon the SUCCESS or FAILURE response above. In addition, the Client checks the validity of the Authenticator Response and disconnects if it is not the expected value.
 EAP Authentication Methods – MS-CHAPv 2 – – – – The server decrypts the response with the hashed password of the client that is stored in a database. If the decrypted response matches the challenge, the server sends a positive authenticator response: The server hashes the NT password hash using MD 4 to generate a password-hash. The server generates a hash using SHA from the clients response, the password-hash, and the literal constant ``Magic server to client signing constant''. The server generates another hash using SHA from the 20 -byte output of step (c), the 8 -byte challenge (see step 3 (b)), and the literal constant ``Pad to make it do more than one iteration''. The resulting 20 bytes are send back to the client in the form ``S= upper-case ASCII representation of the byte values ''. The client uses the same procedure to generate the 20 bytes and compares them to the servers authenticator response. If they match, both the client and the server are authenticated.
EAP Authentication Methods – MS-CHAPv 2 – – – – The server decrypts the response with the hashed password of the client that is stored in a database. If the decrypted response matches the challenge, the server sends a positive authenticator response: The server hashes the NT password hash using MD 4 to generate a password-hash. The server generates a hash using SHA from the clients response, the password-hash, and the literal constant ``Magic server to client signing constant''. The server generates another hash using SHA from the 20 -byte output of step (c), the 8 -byte challenge (see step 3 (b)), and the literal constant ``Pad to make it do more than one iteration''. The resulting 20 bytes are send back to the client in the form ``S= upper-case ASCII representation of the byte values ''. The client uses the same procedure to generate the 20 bytes and compares them to the servers authenticator response. If they match, both the client and the server are authenticated.
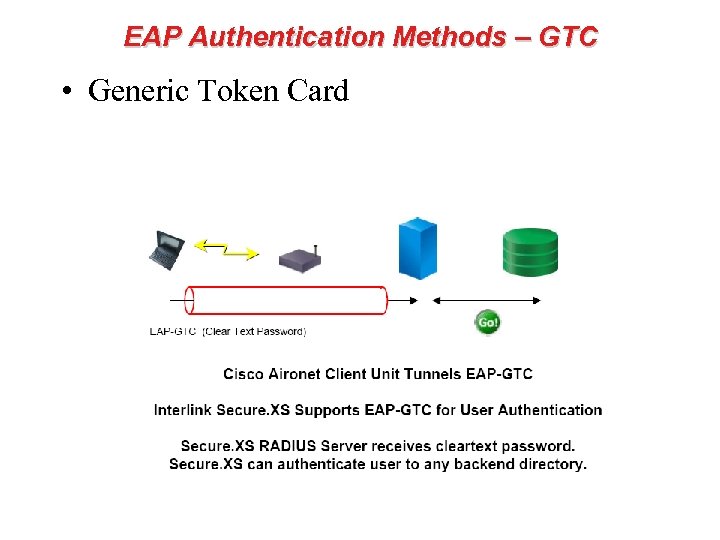 EAP Authentication Methods – GTC • Generic Token Card
EAP Authentication Methods – GTC • Generic Token Card
 Difference between Ms. CHAPv 2 and GTC • What is the difference between EAP-MSCHAPv 2 and EAP -GTC PEAP supplicants? Both supplicants support PEAP, but each supports different methods of client authentication through the TLS tunnel. The Microsoft PEAP supplicant supports client authentication by only MSCHAPv 2. This limits user databases to those that support MSCHAPv 2, such as Windows NT Domain and Active Directory. The Cisco PEAP supplicant (based on EAP-GTC) supports client authentication by one-time passwords and logon passwords. This enables support for one-time password databases from vendors such as RSA Security and Secure Computing Corporation and logon password databases such as LDAP and NDS as well as Microsoft Novell Directory Service (NDS) databases. In addition, the EAP-GTC implementation includes the ability to hide username identities until the TLS encrypted tunnel is established, which provides additional confidentiality that usernames are not being broadcasted during the authentication phase. Starting in version 3. 2, Cisco Secure ACS will support both EAPMSCHAPv 2 and EAP-GTC PEAP supplicants.
Difference between Ms. CHAPv 2 and GTC • What is the difference between EAP-MSCHAPv 2 and EAP -GTC PEAP supplicants? Both supplicants support PEAP, but each supports different methods of client authentication through the TLS tunnel. The Microsoft PEAP supplicant supports client authentication by only MSCHAPv 2. This limits user databases to those that support MSCHAPv 2, such as Windows NT Domain and Active Directory. The Cisco PEAP supplicant (based on EAP-GTC) supports client authentication by one-time passwords and logon passwords. This enables support for one-time password databases from vendors such as RSA Security and Secure Computing Corporation and logon password databases such as LDAP and NDS as well as Microsoft Novell Directory Service (NDS) databases. In addition, the EAP-GTC implementation includes the ability to hide username identities until the TLS encrypted tunnel is established, which provides additional confidentiality that usernames are not being broadcasted during the authentication phase. Starting in version 3. 2, Cisco Secure ACS will support both EAPMSCHAPv 2 and EAP-GTC PEAP supplicants.
 EAP methods based on GSM credentials • Support for SIM and USIM (AKA) credentials • Uses standard SIM (Subscriber Identity Module) and USIM(UMTS Subscriber Identity Module) cards – Wireless phone SIM cards as a way of obtaining authentication • using SIM Extensible Authentication Protocol for GSM (EAP-SIM) • Using USIM Extensible Authentication and Key Agreement Protocol (EAP-AKA) for UMTS. • Generates 128 bit keys, has optional fast reconnect and identity privacy support
EAP methods based on GSM credentials • Support for SIM and USIM (AKA) credentials • Uses standard SIM (Subscriber Identity Module) and USIM(UMTS Subscriber Identity Module) cards – Wireless phone SIM cards as a way of obtaining authentication • using SIM Extensible Authentication Protocol for GSM (EAP-SIM) • Using USIM Extensible Authentication and Key Agreement Protocol (EAP-AKA) for UMTS. • Generates 128 bit keys, has optional fast reconnect and identity privacy support
 EAP Authentication Methods – SIM • • EAP SIM (Subscriber Identity Module) Authentication for GSM EAP SIM authentication is based on Nokia’s EAP Server Technology. This provides an interface between the GSM Authentication Center and one or more wireless LANs and uses the Extensible Authentication Protocol (EAP) in order to allow it to pass traffic securely over any Wide Area Network – e. g. a Telco’s internal data network or the Internet. It permits authentication to be performed by WLAN clients that have an 802. 11 interface and access to a GSM SIM card, with or without GSM air interface capabilities. This authentication procedure is designed to provide mutual authentication between a wireless LAN client and an AAA server. Typically the EAP server is implemented on the AAA server (e. g. RADIUS) and has an interface to the GSM network, so it operates as a gateway between the Internet AAA network and the GSM authentication infrastructure. The system allows GSM mobile operators to reuse their existing authentication infrastructure for providing access to wireless networks. EAP SIM combines the data from several GSM “triplets” (RAND, SRES, Kc), obtained from an Authentication Centre (Au. C), to generate a more secure session encryption key. EAP SIM also enhances the basic GSM authentication mechanism by providing for mutual authentication between the client and the RADIUS server.
EAP Authentication Methods – SIM • • EAP SIM (Subscriber Identity Module) Authentication for GSM EAP SIM authentication is based on Nokia’s EAP Server Technology. This provides an interface between the GSM Authentication Center and one or more wireless LANs and uses the Extensible Authentication Protocol (EAP) in order to allow it to pass traffic securely over any Wide Area Network – e. g. a Telco’s internal data network or the Internet. It permits authentication to be performed by WLAN clients that have an 802. 11 interface and access to a GSM SIM card, with or without GSM air interface capabilities. This authentication procedure is designed to provide mutual authentication between a wireless LAN client and an AAA server. Typically the EAP server is implemented on the AAA server (e. g. RADIUS) and has an interface to the GSM network, so it operates as a gateway between the Internet AAA network and the GSM authentication infrastructure. The system allows GSM mobile operators to reuse their existing authentication infrastructure for providing access to wireless networks. EAP SIM combines the data from several GSM “triplets” (RAND, SRES, Kc), obtained from an Authentication Centre (Au. C), to generate a more secure session encryption key. EAP SIM also enhances the basic GSM authentication mechanism by providing for mutual authentication between the client and the RADIUS server.
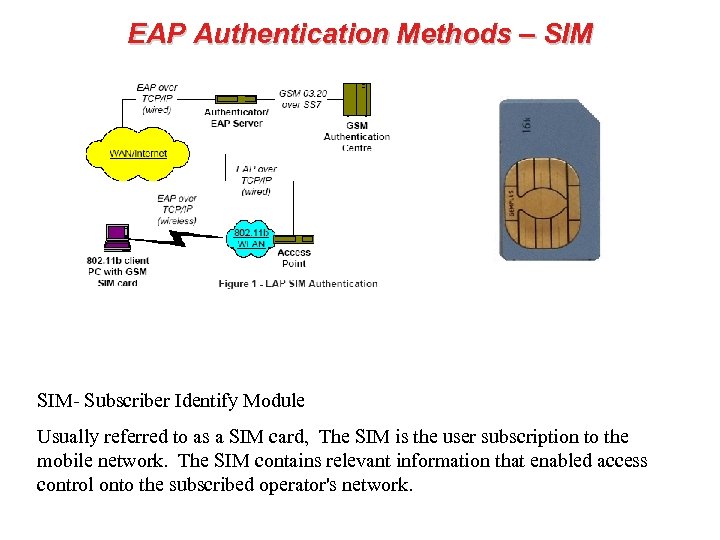 EAP Authentication Methods – SIM- Subscriber Identify Module Usually referred to as a SIM card, The SIM is the user subscription to the mobile network. The SIM contains relevant information that enabled access control onto the subscribed operator's network.
EAP Authentication Methods – SIM- Subscriber Identify Module Usually referred to as a SIM card, The SIM is the user subscription to the mobile network. The SIM contains relevant information that enabled access control onto the subscribed operator's network.
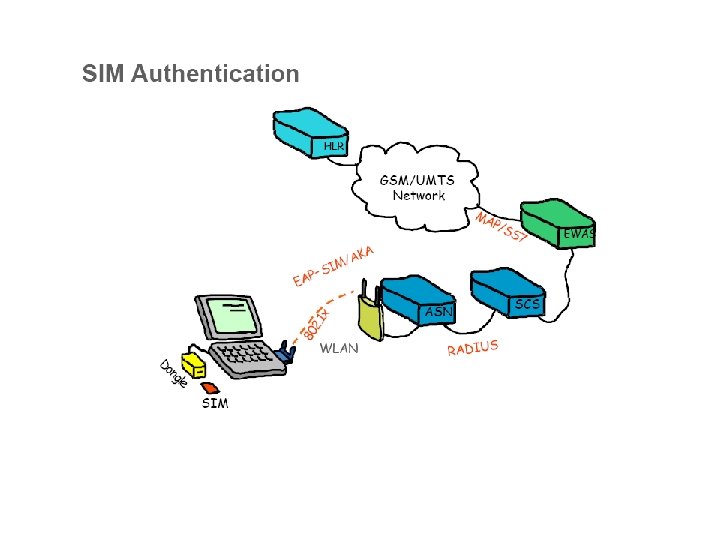
 EAP Authentication Methods – SIM • The EAP SIM authentication proceeds as follows: – The client receives an EAP Identity Request from the access point (AP). – The client responds to the AP’s request with an EAP Identity Response message containing the user’s network identity which is stored on the SIM (either the user's International Mobile Subscriber Identity (IMSI) or a temporary identity (pseudonym)). – The AP transmits this message to the RADIUS server, which in turn forwards it to the Authentication Center of the GSM network. – From the Au. C the RADIUS server obtains GSM triplets and passes the RAND to the client. The SIM calculates the signed response (SRES) which is returned to the RADIUS server. The SIM also calculates cryptographic keying material, using a secure hash function on the user identity and the GSM encryption keys, for the derivation of session encryption keys. – When the AAA server receives the client’s Authentication response, it calculates its own XRES and compares it to the one received from the client. If both match, the client is authenticated and the AAA server calculates the session encryption keys. – It then sends a RADIUS ACCEPT message to the AP, which contains an encapsulated EAP Success message and the (encrypted) client session key. – The AP installs the session key for the encryption and forwards the EAP Success message to the client which is now able to access the network.
EAP Authentication Methods – SIM • The EAP SIM authentication proceeds as follows: – The client receives an EAP Identity Request from the access point (AP). – The client responds to the AP’s request with an EAP Identity Response message containing the user’s network identity which is stored on the SIM (either the user's International Mobile Subscriber Identity (IMSI) or a temporary identity (pseudonym)). – The AP transmits this message to the RADIUS server, which in turn forwards it to the Authentication Center of the GSM network. – From the Au. C the RADIUS server obtains GSM triplets and passes the RAND to the client. The SIM calculates the signed response (SRES) which is returned to the RADIUS server. The SIM also calculates cryptographic keying material, using a secure hash function on the user identity and the GSM encryption keys, for the derivation of session encryption keys. – When the AAA server receives the client’s Authentication response, it calculates its own XRES and compares it to the one received from the client. If both match, the client is authenticated and the AAA server calculates the session encryption keys. – It then sends a RADIUS ACCEPT message to the AP, which contains an encapsulated EAP Success message and the (encrypted) client session key. – The AP installs the session key for the encryption and forwards the EAP Success message to the client which is now able to access the network.
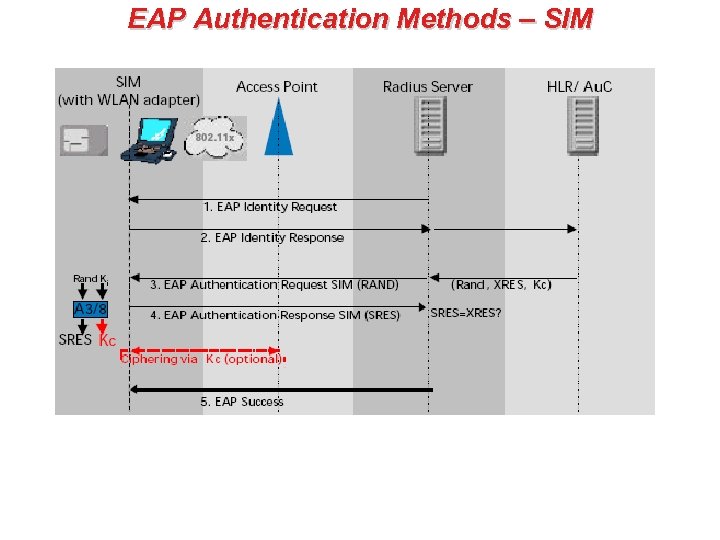 EAP Authentication Methods – SIM
EAP Authentication Methods – SIM
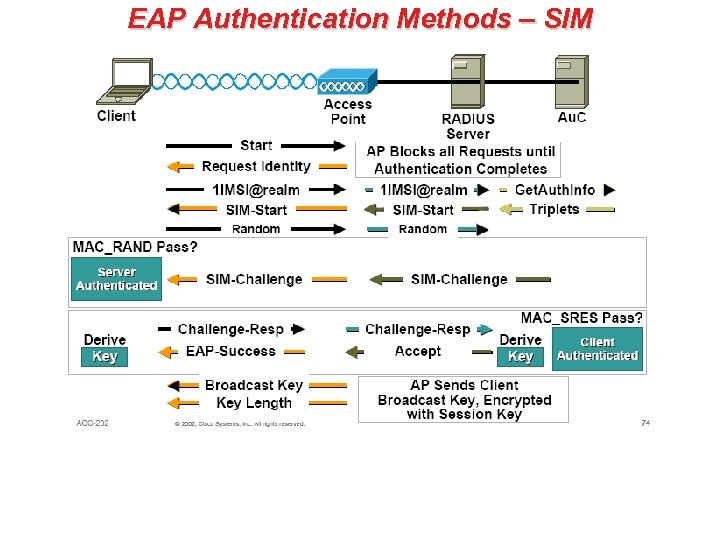 EAP Authentication Methods – SIM
EAP Authentication Methods – SIM
 EAP Authentication Methods – AKA • EAP AKA (authentication and key agreement) is for UMTS • For a W-LAN-3 G-inter-working the EAP AKA protocols have been developed. • The basic difference in the security of the EAP SIM and EAP AKA protocols is that, while both provide mutual authentication, the network-touser authentication of EAP SIM is implicitly based on the derived key Kc , whereas the network-to-user authentication is integral part of EAP/AKA procedure. • EAP/AKA is an EAP type for the UMTS Authentication and Key Agreement (AKA) • EAP/AKA supports all the UMTS AKA scenarios – basic authentication, sequence number synchronization etc. • Similar IMSI privacy support as in EAP/SIM • EAP/AKA includes GSM compatible mode – basic GSM authentication without the enhancements of EAP/SIM – The home server knows if this particular user has been given an old GSM SIM or a newer UMTS USIM – Client can refuse GSM-only authentication
EAP Authentication Methods – AKA • EAP AKA (authentication and key agreement) is for UMTS • For a W-LAN-3 G-inter-working the EAP AKA protocols have been developed. • The basic difference in the security of the EAP SIM and EAP AKA protocols is that, while both provide mutual authentication, the network-touser authentication of EAP SIM is implicitly based on the derived key Kc , whereas the network-to-user authentication is integral part of EAP/AKA procedure. • EAP/AKA is an EAP type for the UMTS Authentication and Key Agreement (AKA) • EAP/AKA supports all the UMTS AKA scenarios – basic authentication, sequence number synchronization etc. • Similar IMSI privacy support as in EAP/SIM • EAP/AKA includes GSM compatible mode – basic GSM authentication without the enhancements of EAP/SIM – The home server knows if this particular user has been given an old GSM SIM or a newer UMTS USIM – Client can refuse GSM-only authentication
 EAP Authentication Methods – AKA • AKA is based on challenge-response mechanisms and symmetric cryptography. • AKA typically runs in a UMTS Subscriber Identity Module (USIM), a smart card like device. However, the applicability of AKA is not limited to client devices with smart cards, but the AKA mechanisms could also be implemented in host software. • Compared to the GSM mechanism, AKA provides substantially longer key lengths and the authentication of the server side as well as the client side.
EAP Authentication Methods – AKA • AKA is based on challenge-response mechanisms and symmetric cryptography. • AKA typically runs in a UMTS Subscriber Identity Module (USIM), a smart card like device. However, the applicability of AKA is not limited to client devices with smart cards, but the AKA mechanisms could also be implemented in host software. • Compared to the GSM mechanism, AKA provides substantially longer key lengths and the authentication of the server side as well as the client side.
 EAP Authentication Methods – AKA Client Authenticator | | EAP-Request/Identity | |<---------------------------| | | EAP-Response/Identity | | (Includes user's NAI) | |--------------------------->| | +---------------+ | | Server runs UMTS algorithms, | | | generates RAND and AUTN. | | +---------------+ | | EAP-Request/AKA-Challenge | | (RAND, AUTN) | |<---------------------------| | +-------------------+ | | Client runs UMTS algorithms on USIM, | | | verifies AUTN, derives RES | | and session key | +-------------------+ | | EAP-Response/AKA-Challenge | | (RES) | |--------------------------->| | +---------------+ | | Server checks the given RES, | | | and finds it correct. | | +---------------+ | | EAP-Success | |<---------------------------|
EAP Authentication Methods – AKA Client Authenticator | | EAP-Request/Identity | |<---------------------------| | | EAP-Response/Identity | | (Includes user's NAI) | |--------------------------->| | +---------------+ | | Server runs UMTS algorithms, | | | generates RAND and AUTN. | | +---------------+ | | EAP-Request/AKA-Challenge | | (RAND, AUTN) | |<---------------------------| | +-------------------+ | | Client runs UMTS algorithms on USIM, | | | verifies AUTN, derives RES | | and session key | +-------------------+ | | EAP-Response/AKA-Challenge | | (RES) | |--------------------------->| | +---------------+ | | Server checks the given RES, | | | and finds it correct. | | +---------------+ | | EAP-Success | |<---------------------------|


