db89848d7dd710ca0278e0d95455794b.ppt
- Количество слайдов: 46

Windows Server 2008 安全功能-NAP Welcome
Network Access Protection in Windows Server 2008

Overview Network Policies Access Protection Enforcement Options Network Access Protection Scenarios

Lesson 1: Network Policies Access Protection Why Use Network Access Protection? Network Protection Services Overview Network Access Protection Solution NAP Architecture Overview Network Layer Protection with NAP Host Layer Protection with NAP
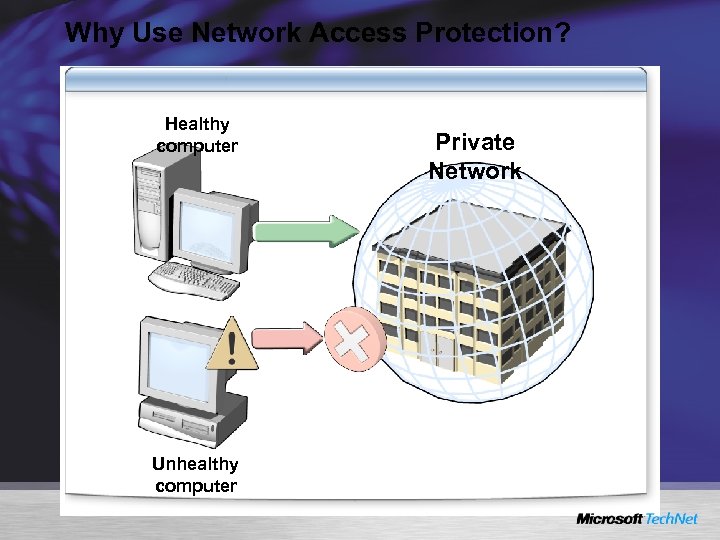
Why Use Network Access Protection? Healthy computer Unhealthy computer Private Network
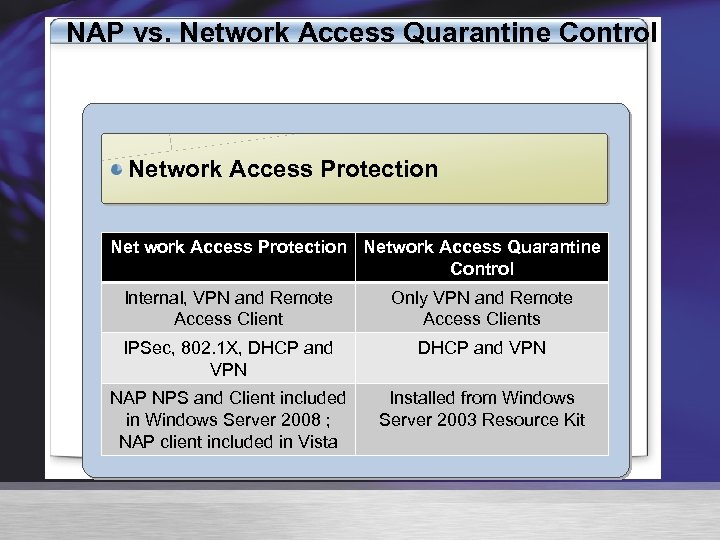
NAP vs. Network Access Quarantine Control Network Access Protection Network Access Quarantine Control Internal, VPN and Remote Access Client Only VPN and Remote Access Clients IPSec, 802. 1 X, DHCP and VPN NAP NPS and Client included in Windows Server 2008 ; NAP client included in Vista Installed from Windows Server 2003 Resource Kit
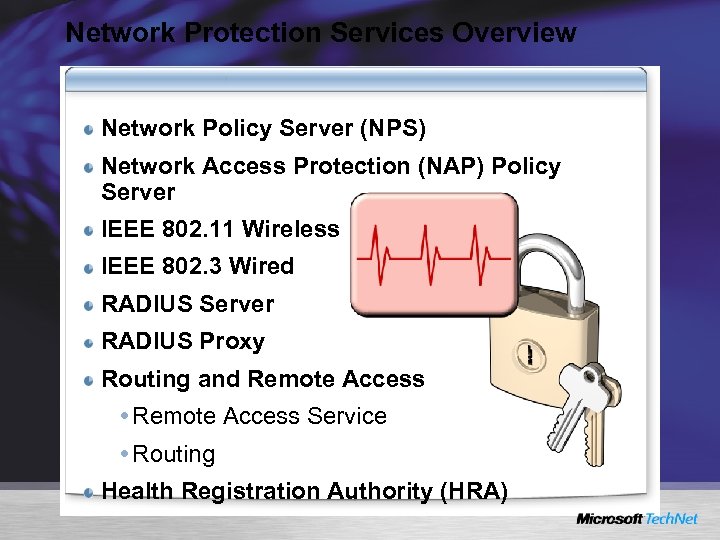
Network Protection Services Overview Network Policy Server (NPS) Network Access Protection (NAP) Policy Server IEEE 802. 11 Wireless IEEE 802. 3 Wired RADIUS Server RADIUS Proxy Routing and Remote Access Service Routing Health Registration Authority (HRA)
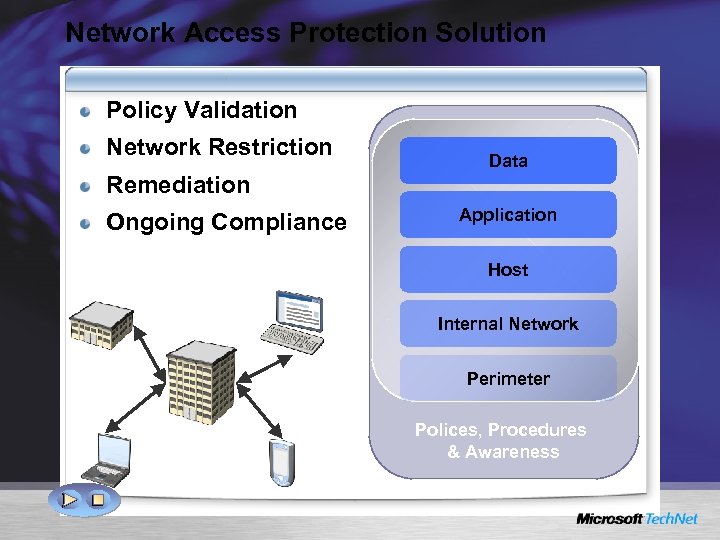
Network Access Protection Solution Policy Validation Network Restriction Remediation Ongoing Compliance Data Application Host Internal Network Perimeter Polices, Procedures & Awareness
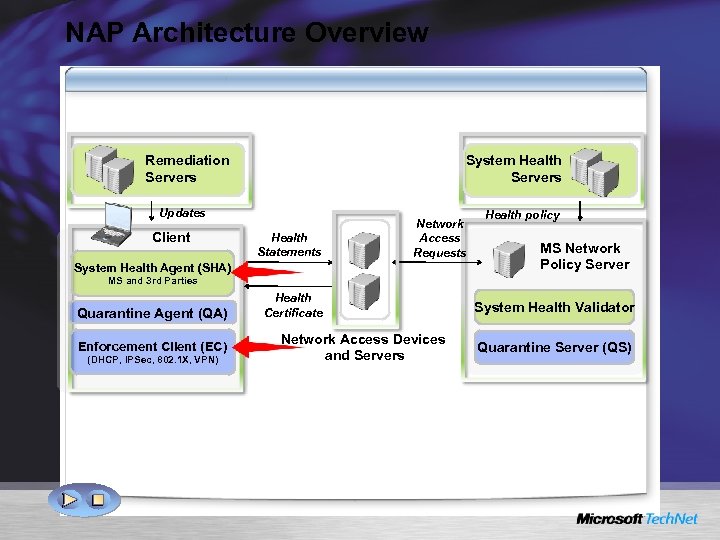
NAP Architecture Overview Remediation Servers System Health Servers Updates Client Health Statements Network Access Requests System Health Agent (SHA) Health policy MS Network Policy Server MS and 3 rd Parties Quarantine Agent (QA) Enforcement Client (EC) (DHCP, IPSec, 802. 1 X, VPN) Health Certificate Network Access Devices and Servers System Health Validator Quarantine Server (QS)
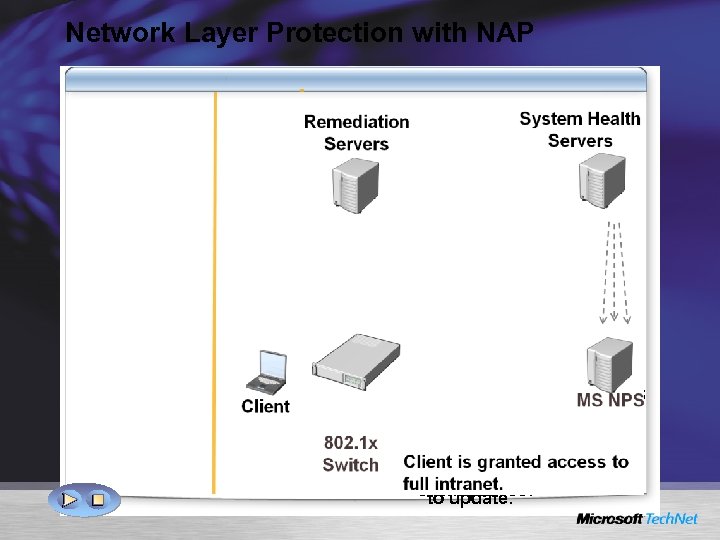
Network Layer Protection with NAP Restricted Network Remediation Servers System Health Servers Here you go. Can I have updates? Ongoing policy updates to Network Policy Server Should this client May I have access? Requesting access. Here’s my current Here’s my new health status. Client You are given restricted access until fix-up. be restricted based on its health? 802. 1 x Switch According to MS NPS According to policy, the client policy, the to date. is not up client is. Quarantine up to date. Client is granted access to fullclient, request it intranet. Grant access. to update.
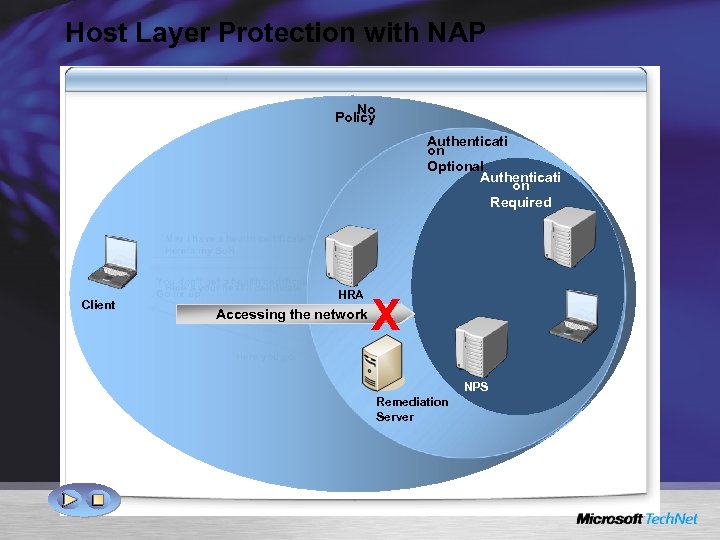
Host Layer Protection with NAP No Policy Authenticati on Optional Authenticati on Required May I have a health certificate? Here’s my So. H. Client You don’t get a health certificate. Here’s your health certificate. Go fix up. I need updates. Client ok? HRA Accessing the network Yes. Issue No. Needs fix-up. health certificate. X Here you go. NPS Remediation Server
Technical Background NAP Infrastructure NAP Platform Architecture NAP Enforcement Methods NAP Client Architecture NAP Server Architecture Component Communication

NAP Infrastructure Automatic Remediation Health Policy Validation Health Policy Compliance Limited Access
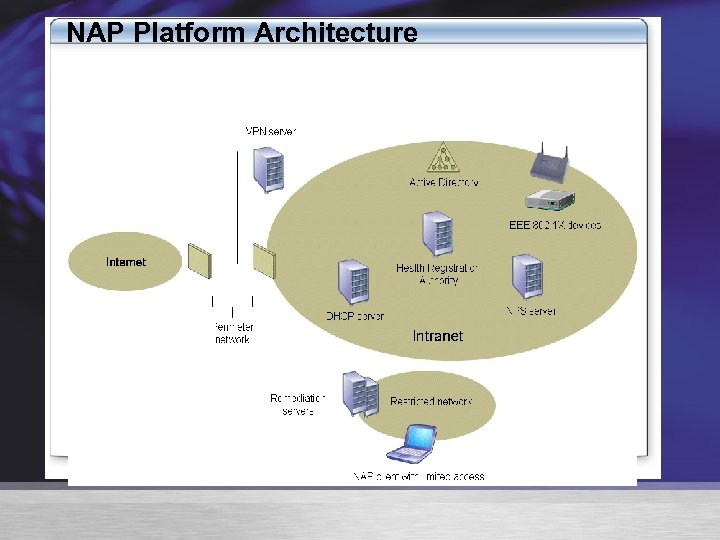
NAP Platform Architecture
Network Access Protection Components (1 of 5) NAP Clients IPSec, 802. 1 X, VPN, DHCP NAP Servers-determine the System Health of any NAP Client Windows Server 2008 + Network Policy Server Remediation action are required for computers that are not compliant Health Registration Authority VPN Server DHCP Server
Network Access Protection Components (2 of 5) NAP Clients IPSec, 802. 1 X, VPN, DHCP NAP Servers-determine the SH of any NAP Client Windows Server 2008 + Network Policy Server Remediation action are required for computers that are not compliant Health Registration Authority VPN Server DHCP Server
Network Access Protection Components (3 of 5) NPS Servers Replacement for the Internet Authentication Service (IAS) Windows server 2008 + Validate System Health Policy Active Directory Service Group Policy Setting for IPSec 802. 1 X credential are stored in directory service
Network Access Protection Components (4 of 5) Restricted Network Separate network segment (logical/physical) Contains the Remediation Servers Remediation Server Bring NAP Client into compliance with health policy System Health Agent (SHA) Check for particular health parameter Send a Statement of Health (So. H) to System Health Validator (SHV)
Network Access Protection Components (5 of 5) System Health Validator Compare the System of Health (So. H) sent from a System Health Agent (SHA) Statement of Health (So. H) So. H is response sent by a System Health Agent to a System Health Validator
Misconception Quarantine network is anything but empty SMS Server form within Quarantine Mode For starters, must have a DNS Server Don’t be a primary DNS server Finally, the DHCP and IAS server (VPN Quarantine Mode only) must accessable. Otherwise, a client would never be able to get out of Quarantine Mode after its Statement of Health has been update.

Lesson 2: Enforcement Options NAP – Enforcement Options NAP with DHCP IPsec-based Communication NAP with RRAS
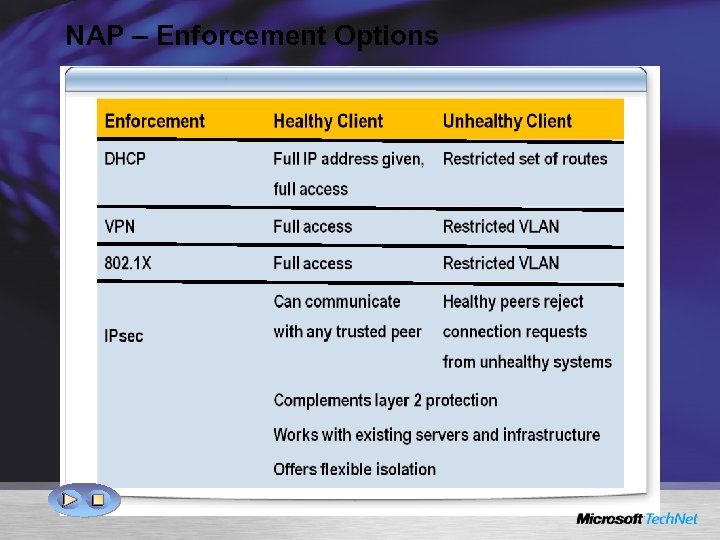
NAP – Enforcement Options
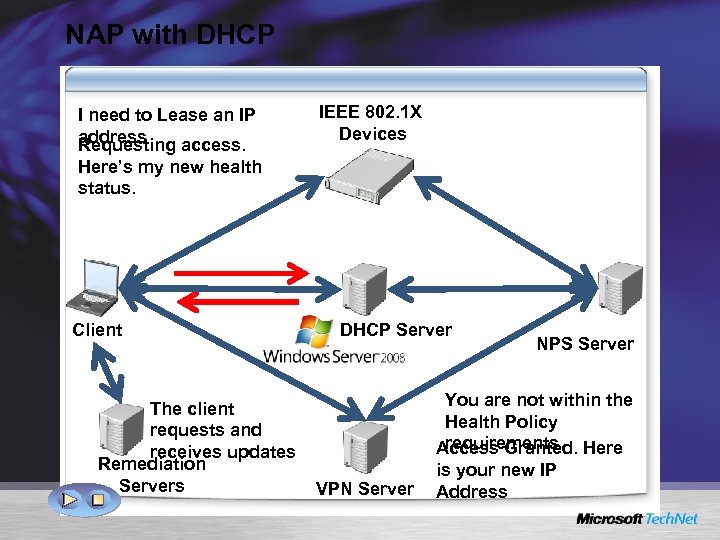
NAP with DHCP I need to Lease an IP address Requesting access. IEEE 802. 1 X Devices Here’s my new health status. Client The client requests and receives updates Remediation Servers DHCP Server VPN Server NPS Server You are not within the Health Policy requirements Access Granted. Here is your new IP Address
Demo 1: Using Network Access Protection Exercise 1: Configuring Network Access Protection for DHCP
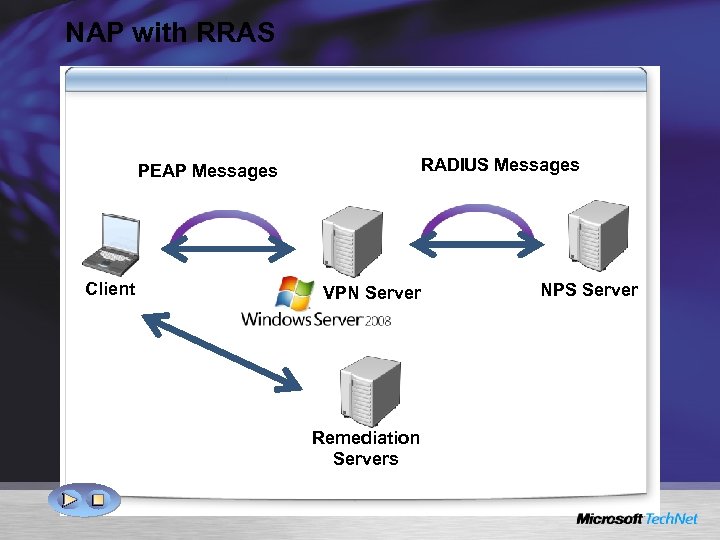
NAP with RRAS RADIUS Messages PEAP Messages Client VPN Server Remediation Servers NPS Server

Demo 2: Using Network Access Protection Exercise 1: Configuring Network Access Protection for VPN
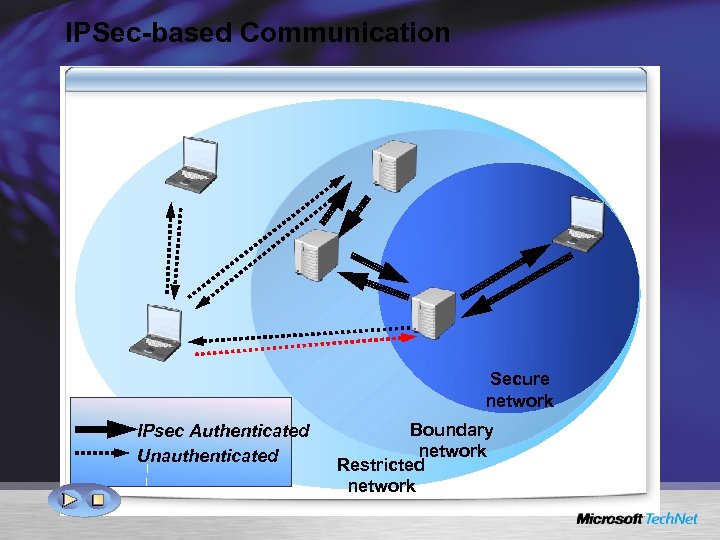
IPSec-based Communication Secure network IPsec Authenticated Unauthenticated Boundary network Restricted network
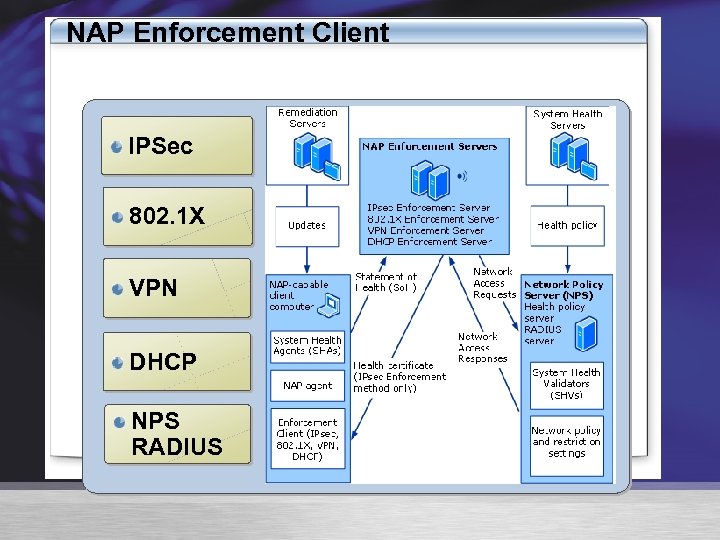
NAP Enforcement Client IPSec 802. 1 X VPN DHCP NPS RADIUS
How NAP Works Logical Networks IPSec Enforcement IEEE 802. 1 X Remote Access VPNs DHCP
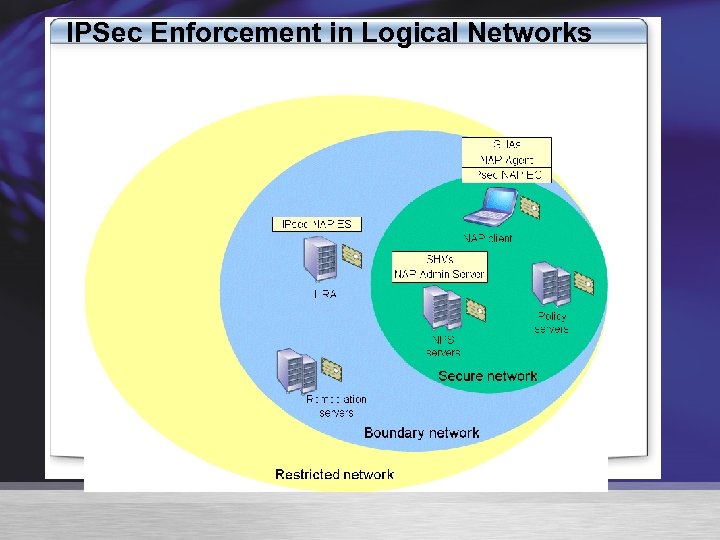
IPSec Enforcement in Logical Networks
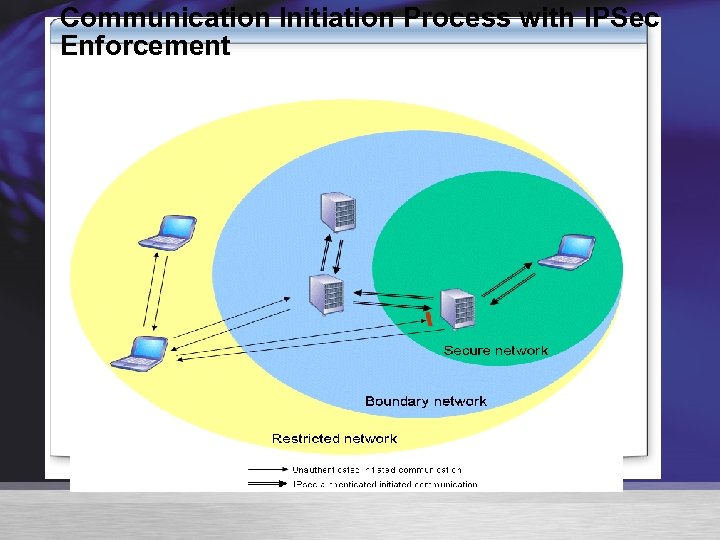
Communication Initiation Process with IPSec Enforcement
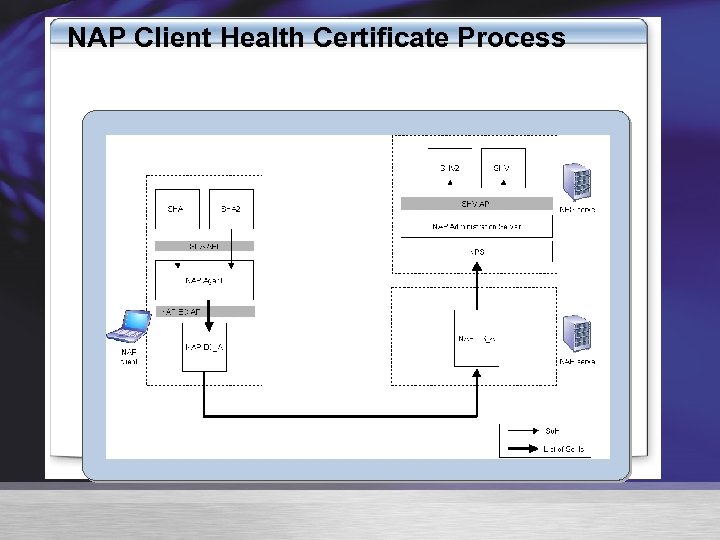
NAP Client Health Certificate Process
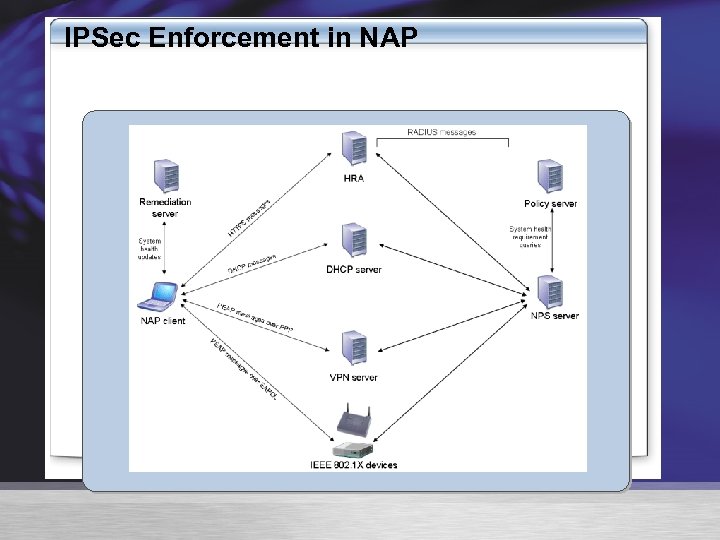
IPSec Enforcement in NAP

IPSec Reviewing IPSec functionality OSI 7 Layer - Layer 3 Authentication methods for IPSec Pre-share Key Kerberos Certificate

Certificate Reviewing What’s Digital Certificate What’s Certificate Authority Digital Certificate for what? Identity user, computer, service Digital Certificate for IPSec
Demo 3: Network Access Protection - IPSec • Create a Certificate Template for NAP Exemptions • Enable Certificate Auto. Enrollment • Config NAP to Issue Health Certificates • Config Health Registration Authority to request Certificate from subordinate CA • Add System Health Validation Certificate to NPS • Config GPO to Ensure Client are Configured to Implement NAP • Verify Network Access Protection
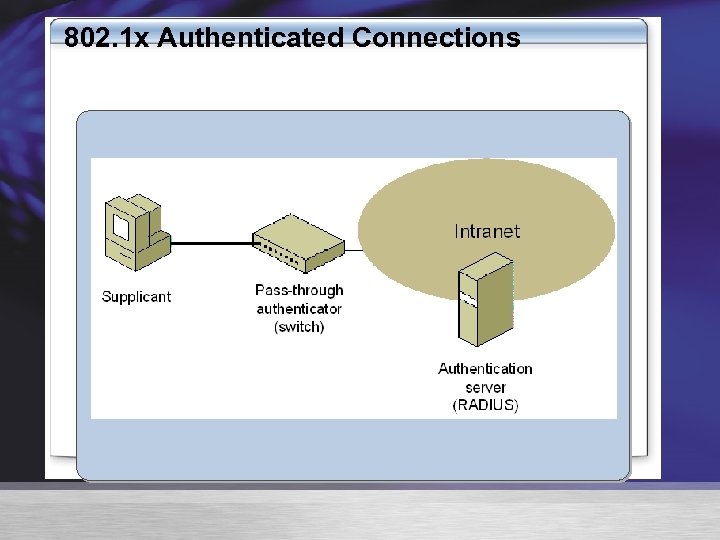
802. 1 x Authenticated Connections
Lesson 3: Network Access Protection Scenarios Scenario 1: Roaming Laptops Scenario 2: Health of Desktop Computers Scenario 3: Health of Visiting Laptops Scenario 4: Unmanaged Home Computers
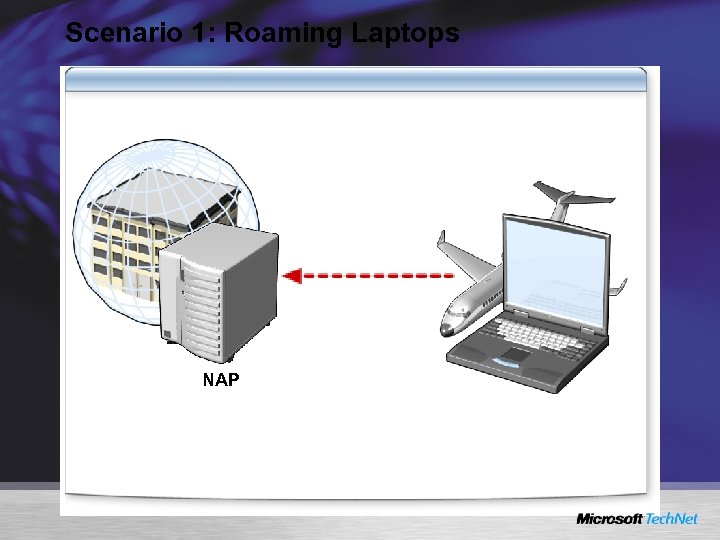
Scenario 1: Roaming Laptops NAP
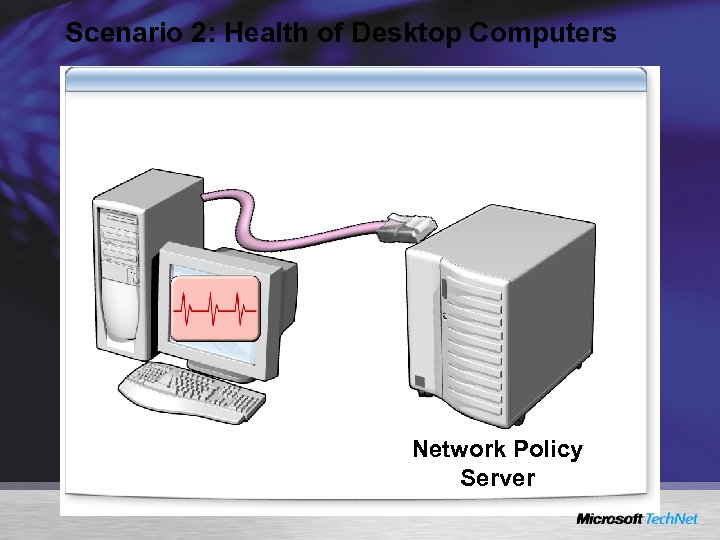
Scenario 2: Health of Desktop Computers Network Policy Server
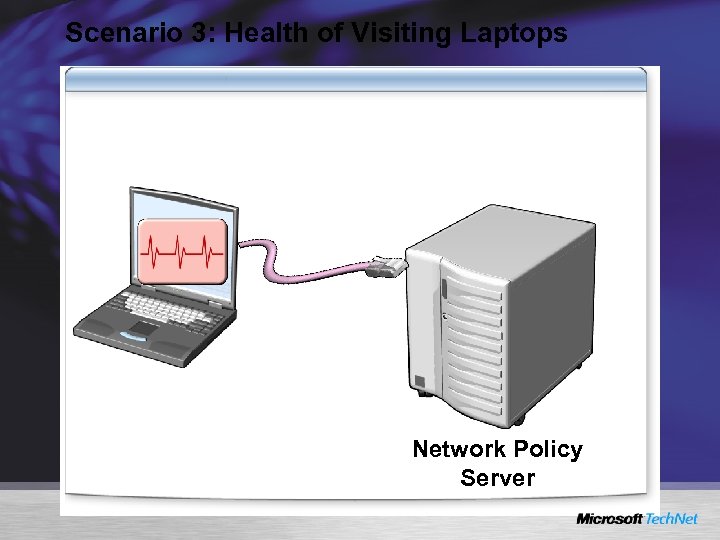
Scenario 3: Health of Visiting Laptops Network Policy Server
Scenario 4: Unmanaged Home Computers
NAP Authentication Process Background Authentication Process Network Access Protection Settings Authorization Policies
Implementation/Usage Scenarios Checking the Health and Status of Roaming Laptops Ensuring the Health of Corporate Desktops Determining the Health of Visiting Laptops Verify the Compliance of Home Computers
Summary Network Access Protection: Secures Remote Computers before accessing the Network Has Client and Server Components Can Use One or More of Several methods for Enforcement IPSec 802. 1 X VPN DHCP Provides Support for Third Party Software
What Next? Windows Server 2008 Beta: https: //connect. microsoft. com Home Page: http: //www. microsoft. com/windowsserver/longhorn/default. mspx Webcasts: http: //www. microsoft. com/windowsserver/longhorn/webcasts. mspx Forums: http: //forums. microsoft. com/Tech. Net/default. aspx? Forum. Group. ID=161&Site. ID=17 Network Access Protection • Home Page: http: //www. microsoft. com/nap Introduction to Network Access Protection: • Network Access Protection Platform Architecture: • Network Access Protection Frequently Asked Questions: • IPSec: http: //www. microsoft. com/ipsec Server and Domain Isolation: • • http: //go. microsoft. com/fwlink/? Link. Id=49884 http: //go. microsoft. com/fwlink/? Link. Id=49885 http: //go. microsoft. com/fwlink/? Link. Id=49886 http: //www. microsoft. com/technet/network/sdiso/default. mspx
db89848d7dd710ca0278e0d95455794b.ppt