3d2380e5df8e06a174a0d0f9371b3264.ppt
- Количество слайдов: 35
 Windows Server 2003 Security Donald E. Hester CISSP, CISA, MCT, MCSE, MCSA, MCDST, Security+, CTT+, MV Maze & Associates San Diego City College Los Medanos College
Windows Server 2003 Security Donald E. Hester CISSP, CISA, MCT, MCSE, MCSA, MCDST, Security+, CTT+, MV Maze & Associates San Diego City College Los Medanos College
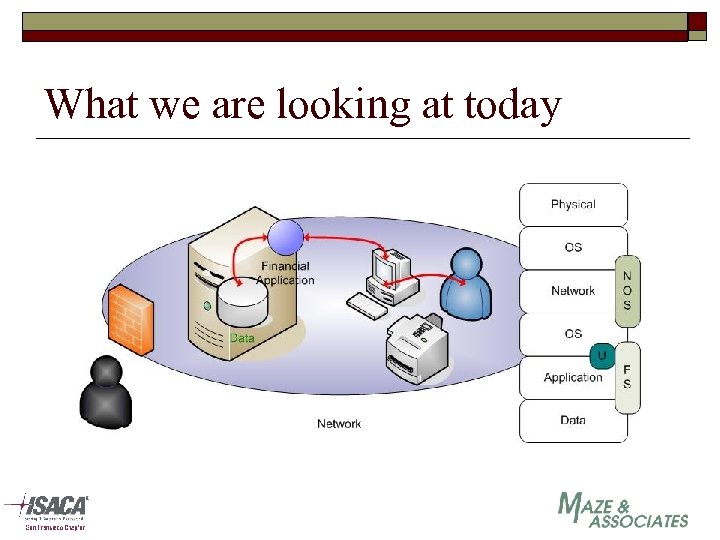 What we are looking at today
What we are looking at today
 Priority Shift o Access was a top priority n n o Open-by-default Start with everything open and then start locking down as needed Control is now a top priority n n Closed-by-default Start with everything closed and open only what is needed
Priority Shift o Access was a top priority n n o Open-by-default Start with everything open and then start locking down as needed Control is now a top priority n n Closed-by-default Start with everything closed and open only what is needed
 Security Enhancements
Security Enhancements
 Server 2003 Defaults o IIS – Internet Information Services n n o o IIS is not installed by default When you install IIS 6 it is locked down More startup services are disabled in 2003 Everyone Group n n No longer has full control it has read and execute No longer includes anonymous users
Server 2003 Defaults o IIS – Internet Information Services n n o o IIS is not installed by default When you install IIS 6 it is locked down More startup services are disabled in 2003 Everyone Group n n No longer has full control it has read and execute No longer includes anonymous users
 Server 2003 Defaults o o Accounts with null passwords are console-bound Software restriction policies n n o o Hash rule Path rule Certificate rule Internet Zone rule Protected EAP (PEAP) Detailed security auditing
Server 2003 Defaults o o Accounts with null passwords are console-bound Software restriction policies n n o o Hash rule Path rule Certificate rule Internet Zone rule Protected EAP (PEAP) Detailed security auditing
 File System o NTFS n n n o Permissions & auditing EFS - Encrypted File System (multiple users) VSS - Volume Shadow Copy (Server 2003) Quotas ABE (Server 2003 SP 1) Future developments Win. FS n Won’t be in Longhorn
File System o NTFS n n n o Permissions & auditing EFS - Encrypted File System (multiple users) VSS - Volume Shadow Copy (Server 2003) Quotas ABE (Server 2003 SP 1) Future developments Win. FS n Won’t be in Longhorn
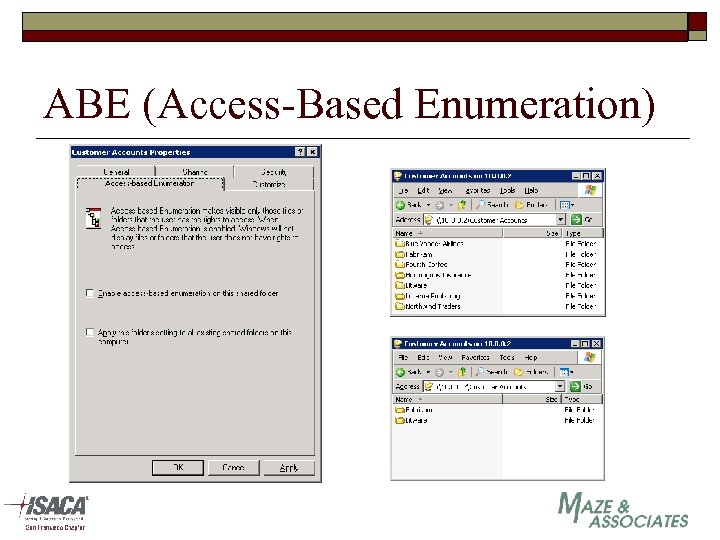 ABE (Access-Based Enumeration)
ABE (Access-Based Enumeration)
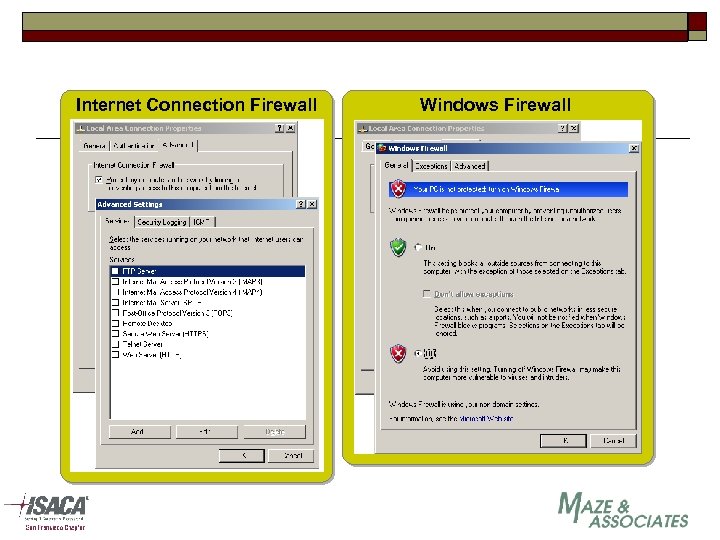 Internet Connection Firewall Windows Firewall
Internet Connection Firewall Windows Firewall
 ICF vs. Windows Firewall o o o o Boot-time Security Global configuration Audit logging Scope restrictions Command-line support Program-based exceptions Multiple Profiles o o Unattended setup support Enhanced multicast and broadcast support IPv 6 support New Group Policy Support
ICF vs. Windows Firewall o o o o Boot-time Security Global configuration Audit logging Scope restrictions Command-line support Program-based exceptions Multiple Profiles o o Unattended setup support Enhanced multicast and broadcast support IPv 6 support New Group Policy Support
 PSSU (Post-Setup Security Updates) o o o Service Pack 1 enhancement Protects the computer until it can update Uses Windows Firewall
PSSU (Post-Setup Security Updates) o o o Service Pack 1 enhancement Protects the computer until it can update Uses Windows Firewall
 DEP (Data Execution Prevention) o o Prevent malicious software rather than error out and potentially crashing the system Hardware-enforced DEP n n n o Protects memory locations The no-execute page-protection (NX) processor feature as defined by AMD. The Execute Disable Bit (XD) feature as defined by Intel. Software-enforced DEP n n Protects system binaries and exception-handling Software built with Safe. SEH
DEP (Data Execution Prevention) o o Prevent malicious software rather than error out and potentially crashing the system Hardware-enforced DEP n n n o Protects memory locations The no-execute page-protection (NX) processor feature as defined by AMD. The Execute Disable Bit (XD) feature as defined by Intel. Software-enforced DEP n n Protects system binaries and exception-handling Software built with Safe. SEH
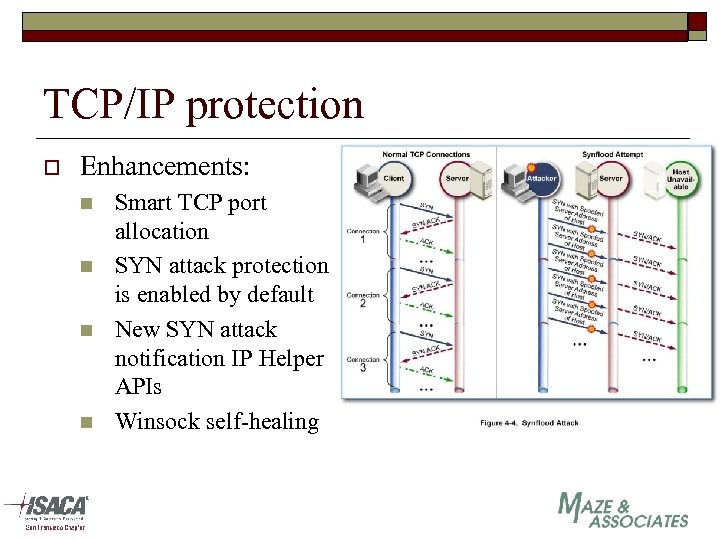 TCP/IP protection o Enhancements: n n Smart TCP port allocation SYN attack protection is enabled by default New SYN attack notification IP Helper APIs Winsock self-healing
TCP/IP protection o Enhancements: n n Smart TCP port allocation SYN attack protection is enabled by default New SYN attack notification IP Helper APIs Winsock self-healing
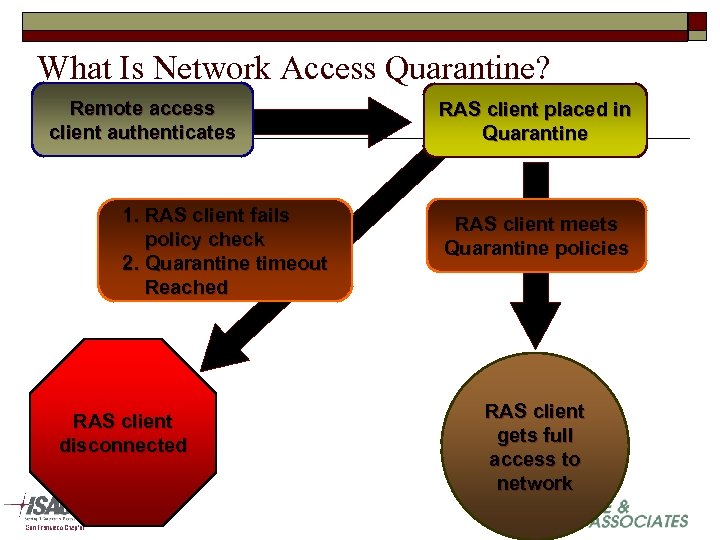 What Is Network Access Quarantine? Remote access client authenticates 1. RAS client fails policy check 2. Quarantine timeout Reached RAS client disconnected RAS client placed in Quarantine RAS client meets Quarantine policies RAS client gets full access to network
What Is Network Access Quarantine? Remote access client authenticates 1. RAS client fails policy check 2. Quarantine timeout Reached RAS client disconnected RAS client placed in Quarantine RAS client meets Quarantine policies RAS client gets full access to network
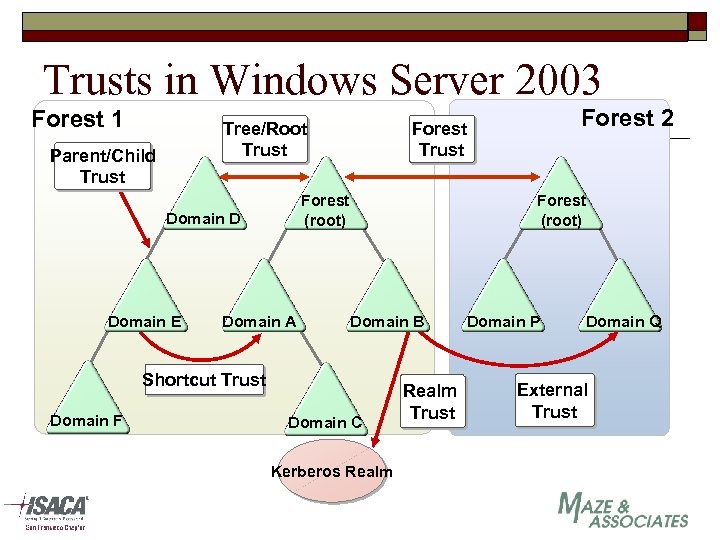 Trusts in Windows Server 2003 Forest 1 Tree/Root Trust Parent/Child Trust Forest (root) Domain D Domain E Domain A Forest (root) Domain B Shortcut Trust Domain F Forest 2 Forest Trust Domain C Kerberos Realm Trust Domain P Domain Q External Trust
Trusts in Windows Server 2003 Forest 1 Tree/Root Trust Parent/Child Trust Forest (root) Domain D Domain E Domain A Forest (root) Domain B Shortcut Trust Domain F Forest 2 Forest Trust Domain C Kerberos Realm Trust Domain P Domain Q External Trust
 Coming Soon: IE 7 o Information Security Magazine (Jan 2006)
Coming Soon: IE 7 o Information Security Magazine (Jan 2006)
 Server Hardening
Server Hardening
 Server Hardening o Appropriate settings for a secure baseline n n n Settings for applications and services Operating system components Permissions and rights Administrative procedures Physical access
Server Hardening o Appropriate settings for a secure baseline n n n Settings for applications and services Operating system components Permissions and rights Administrative procedures Physical access
 Server Hardening - Templates o o o Predefined Security Templates Security Guide Templates Industrial Templates n n o SANS CIAC NSA Do. D Custom Templates
Server Hardening - Templates o o o Predefined Security Templates Security Guide Templates Industrial Templates n n o SANS CIAC NSA Do. D Custom Templates
 Template Deployment o o Test before deployment Periodic analysis n n o Security Configuration and Analysis snap-in Scripting (Secedit. exe) Deployment Methods n n n Group Policy (Active Directory) Security Configuration and Analysis snap-in Scripting (Secedit. exe)
Template Deployment o o Test before deployment Periodic analysis n n o Security Configuration and Analysis snap-in Scripting (Secedit. exe) Deployment Methods n n n Group Policy (Active Directory) Security Configuration and Analysis snap-in Scripting (Secedit. exe)
 Server Hardening o Security Configuration Wizard (SCW) n n n n Comes with Service Pack 1 (Server 2003) Disables unneeded services Blocks unused ports Allows further address or security restrictions for ports that are left open Prohibits unnecessary Internet Information Services (IIS) Web extensions, if applicable Reduces protocol exposure to server message block (SMB), NTLM, Lan. Man, and Lightweight Directory Access Protocol (LDAP) Defines a high signal-to-noise audit policy Best for servers with multiple roles
Server Hardening o Security Configuration Wizard (SCW) n n n n Comes with Service Pack 1 (Server 2003) Disables unneeded services Blocks unused ports Allows further address or security restrictions for ports that are left open Prohibits unnecessary Internet Information Services (IIS) Web extensions, if applicable Reduces protocol exposure to server message block (SMB), NTLM, Lan. Man, and Lightweight Directory Access Protocol (LDAP) Defines a high signal-to-noise audit policy Best for servers with multiple roles
 Security Configuration Wizard o Supports n n n n Rollback Analysis Remote configuration Command-line support Active Directory integration Policy editing Export to Group Policy
Security Configuration Wizard o Supports n n n n Rollback Analysis Remote configuration Command-line support Active Directory integration Policy editing Export to Group Policy
 Security Tools
Security Tools
 Updates o Manual n o Windows Updates n o Automatic process fine for small deployments SUS n o Requires user intervention – labor intensive Updates approved critical patches for multiple machines at an administrator appointed time (replaced with WSUS) WSUS n Same as SUS but includes support for other patches such as Office and critical drivers
Updates o Manual n o Windows Updates n o Automatic process fine for small deployments SUS n o Requires user intervention – labor intensive Updates approved critical patches for multiple machines at an administrator appointed time (replaced with WSUS) WSUS n Same as SUS but includes support for other patches such as Office and critical drivers
 PKI o Some uses n o o EFS, Authentication, Smart Card, IPSec, Servers Auto enrollment Command line tools (Certreq. exe, Certutil. exe) Key recovery (DRA or KRA) Delta CRL
PKI o Some uses n o o EFS, Authentication, Smart Card, IPSec, Servers Auto enrollment Command line tools (Certreq. exe, Certutil. exe) Key recovery (DRA or KRA) Delta CRL
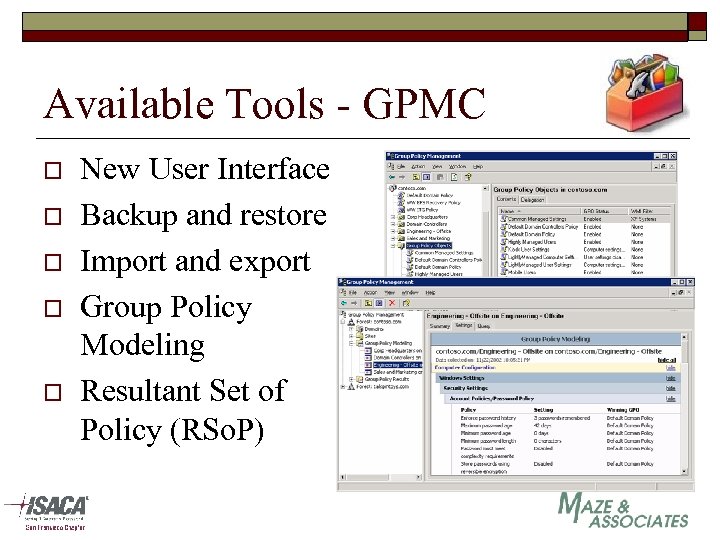 Available Tools - GPMC o o o New User Interface Backup and restore Import and export Group Policy Modeling Resultant Set of Policy (RSo. P)
Available Tools - GPMC o o o New User Interface Backup and restore Import and export Group Policy Modeling Resultant Set of Policy (RSo. P)
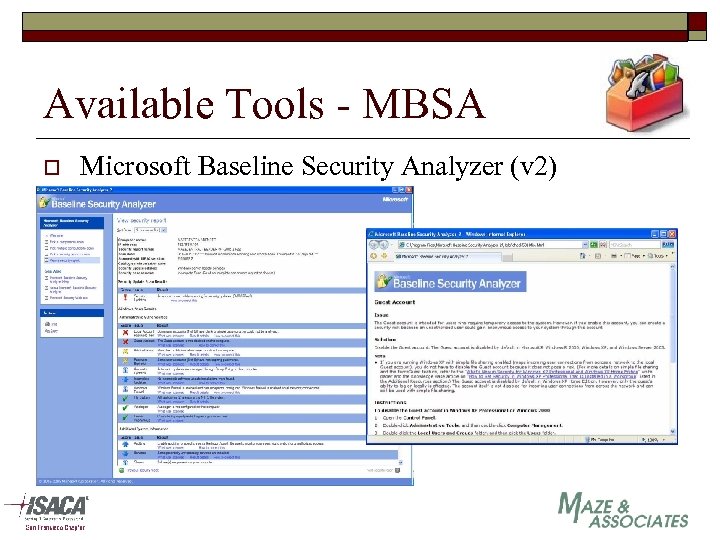 Available Tools - MBSA o Microsoft Baseline Security Analyzer (v 2)
Available Tools - MBSA o Microsoft Baseline Security Analyzer (v 2)
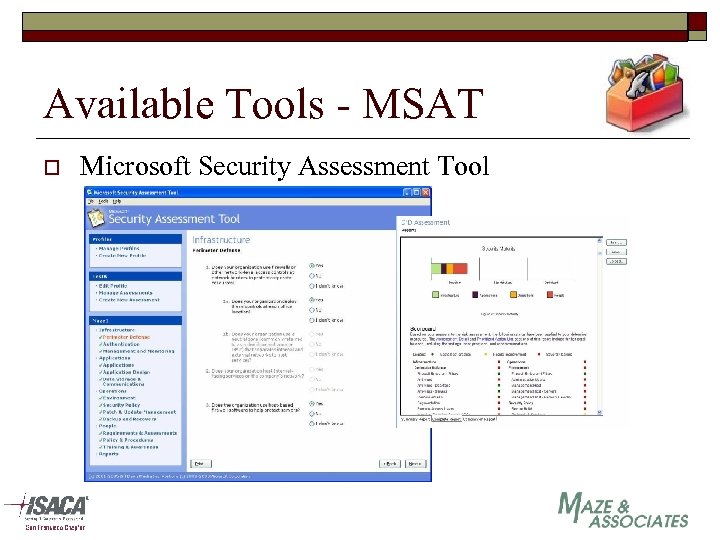 Available Tools - MSAT o Microsoft Security Assessment Tool
Available Tools - MSAT o Microsoft Security Assessment Tool
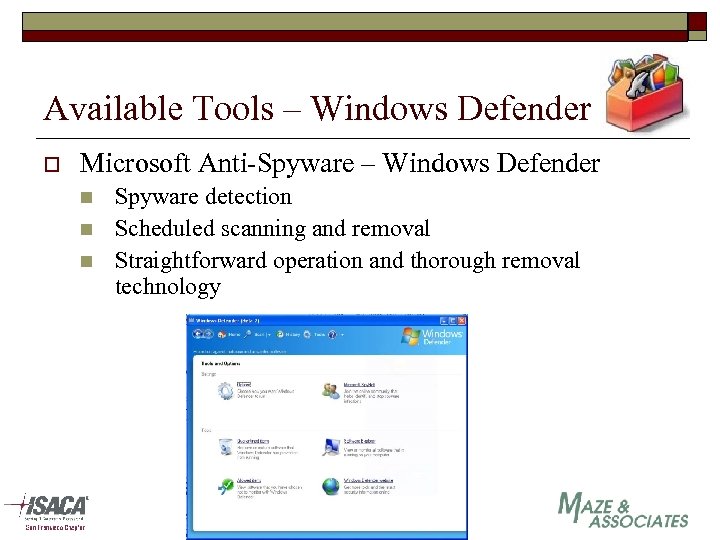 Available Tools – Windows Defender o Microsoft Anti-Spyware – Windows Defender n n n Spyware detection Scheduled scanning and removal Straightforward operation and thorough removal technology
Available Tools – Windows Defender o Microsoft Anti-Spyware – Windows Defender n n n Spyware detection Scheduled scanning and removal Straightforward operation and thorough removal technology
 Available Tools o Security Resource Kit n o Various tools to enumerate access control lists, list drivers, list services, dump event logs, parse logs, determine authentication method, and much more Security Guide n n Templates Various test scripts
Available Tools o Security Resource Kit n o Various tools to enumerate access control lists, list drivers, list services, dump event logs, parse logs, determine authentication method, and much more Security Guide n n Templates Various test scripts
 3 rd Party Tools o o Winternals http: //www. winternals. com/ Sysinternals http: //www. systernals. com/ CERT http: //www. cert. org/ SANS http: //www. sans. org/
3 rd Party Tools o o Winternals http: //www. winternals. com/ Sysinternals http: //www. systernals. com/ CERT http: //www. cert. org/ SANS http: //www. sans. org/
 Resources o Windows Server 2003 Security Guide n o o http: //go. microsoft. com/fwlink/? Link. Id=14846 Window. Security. com Sec. Wish@microsoft. com (Feedback email) Microsoft Windows Security Resource Kit (2 nd Ed. ) ISBN 0 -7356 -2174 -8 Service Pack 1 Overview n http: //www. microsoft. com/technet/prodtechnol/windowss erver 2003/servicepack/overview. mspx
Resources o Windows Server 2003 Security Guide n o o http: //go. microsoft. com/fwlink/? Link. Id=14846 Window. Security. com Sec. Wish@microsoft. com (Feedback email) Microsoft Windows Security Resource Kit (2 nd Ed. ) ISBN 0 -7356 -2174 -8 Service Pack 1 Overview n http: //www. microsoft. com/technet/prodtechnol/windowss erver 2003/servicepack/overview. mspx
 Resources o o o o Microsoft Security Assessment Tool (MSAT) https: //www. securityguidance. com/ Microsoft Security http: //www. microsoft. com/security/default. mspx Microsoft Baseline Security Analyzer (MBSA) http: //www. microsoft. com/technet/security/tools/mb sahome. mspx Microsoft Anti-Spyware (beta) Defender http: //www. microsoft. com/athome/security/spyware/ software/default. mspx
Resources o o o o Microsoft Security Assessment Tool (MSAT) https: //www. securityguidance. com/ Microsoft Security http: //www. microsoft. com/security/default. mspx Microsoft Baseline Security Analyzer (MBSA) http: //www. microsoft. com/technet/security/tools/mb sahome. mspx Microsoft Anti-Spyware (beta) Defender http: //www. microsoft. com/athome/security/spyware/ software/default. mspx
 Resources o o o Root. Kit Revealer http: //www. sysinternals. com/Utilities/Rootkit. Reveal er. html Strider Ghost. Buster Project (Rootkit detector) http: //research. microsoft. com/rootkit/ Threats and Countermeasures: Security Settings in Windows Server 2003 and Windows XP http: //go. microsoft. com/fwlink/? Link. Id=15160
Resources o o o Root. Kit Revealer http: //www. sysinternals. com/Utilities/Rootkit. Reveal er. html Strider Ghost. Buster Project (Rootkit detector) http: //research. microsoft. com/rootkit/ Threats and Countermeasures: Security Settings in Windows Server 2003 and Windows XP http: //go. microsoft. com/fwlink/? Link. Id=15160
 Contact Info o Donald E. Hester n Donald. H@Maze. Associates. com n https: //www. linkedin. com/in/donaldehester
Contact Info o Donald E. Hester n Donald. H@Maze. Associates. com n https: //www. linkedin. com/in/donaldehester


