346cc5f875ef58339dee2136705f6e09.ppt
- Количество слайдов: 32

Windows NT Single Sign On ® Back. Office® Applications (Part I) Peter Brundrett Program Manager Windows NT Security Microsoft Corporation

Agenda u u Windows NT single sign on Kerberos v 5 authentication and SSPI Three-tier security delegation Windows NT authorization

Single Sign On Issues u User issue: l u Administrator issue: l l u Too many places to define user accounts Hard to determine user access Security issue: l l u Too many passwords to remember Clear text passwords Hard to disable an account IT Manager issue: l Heterogeneous computer systems

Single Sign On Goals u User l l u Administrator l l l u Logon once to the Enterprise Use few passwords, ideally one! Create user account once Assign access based on roles Manage accounts across systems Security administrator l Define and verify security policies
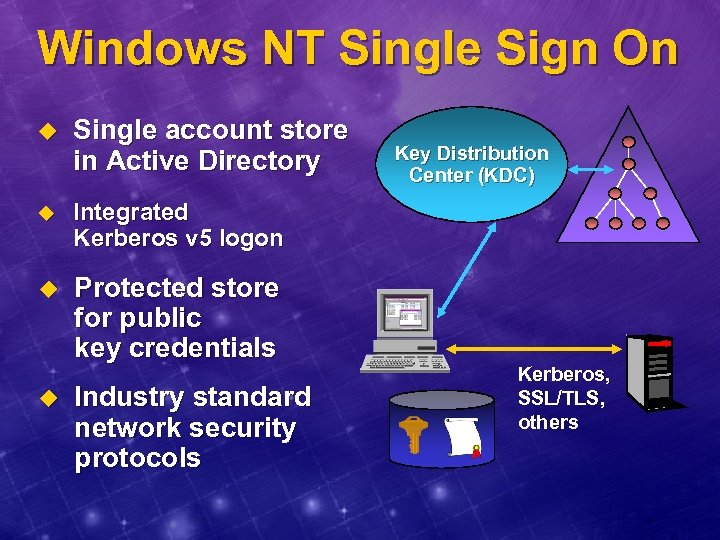
Windows NT Single Sign On u Single account store in Active Directory u Integrated Kerberos v 5 logon u Protected store for public key credentials u Industry standard network security protocols Key Distribution Center (KDC) Kerberos, SSL/TLS, others
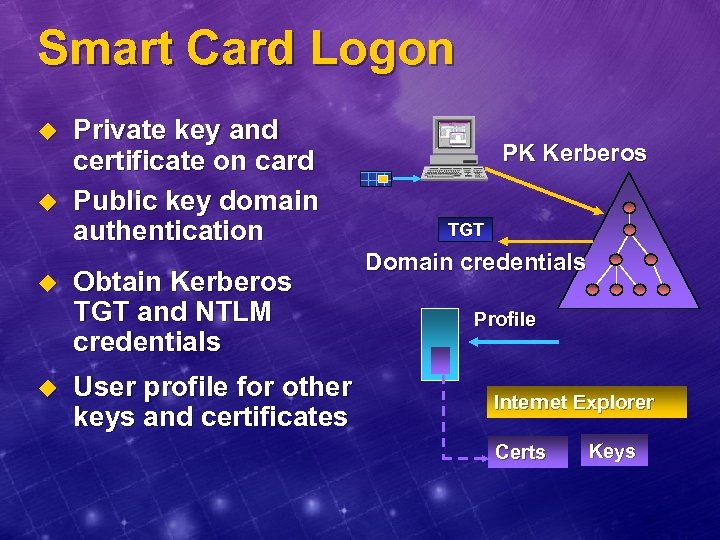
Smart Card Logon u u Private key and certificate on card Public key domain authentication Obtain Kerberos TGT and NTLM credentials User profile for other keys and certificates PK Kerberos TGT Domain credentials Profile Internet Explorer Certs Keys

Windows NT Single Sign On u u u Standards-based Distributed System Infrastructure Well documented APIs for developers Platform services used in applications Integrated logon to strategic platforms Integrated Windows NT authorization
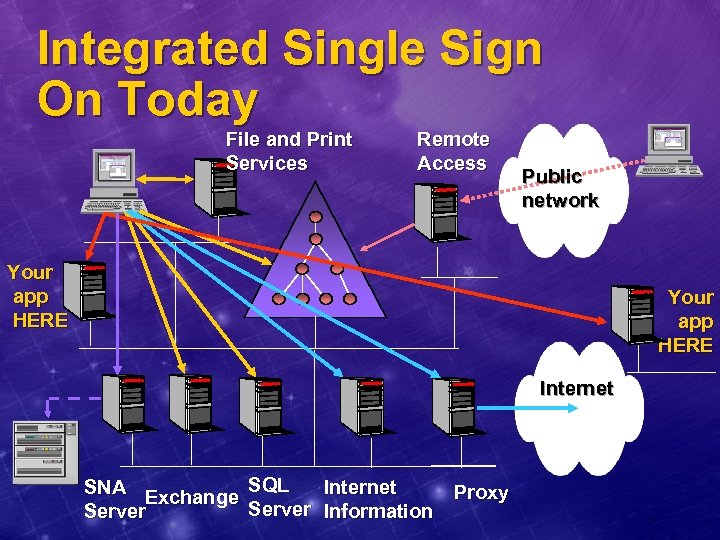
Integrated Single Sign On Today File and Print Services Remote Access Public network Your app HERE Internet SNA Exchange Server SQL Internet Proxy Server Information

Back. Office Logo Program u u u Security requirements for client/ server applications Core baseline requirements Windows NT authentication l l u NTLM for Windows NT 4. 0 Kerberos v 5 for Windows NT 5. 0 Benefits l l Easier administration, stronger security Intranet ready!

Secure Applications u Connection authentication l l u Secure communication l u Message privacy and integrity Impersonation and delegation l u Establish credentials Mutual authentication of client and server Assuming client’s identity Authorization and auditing l Using security descriptors
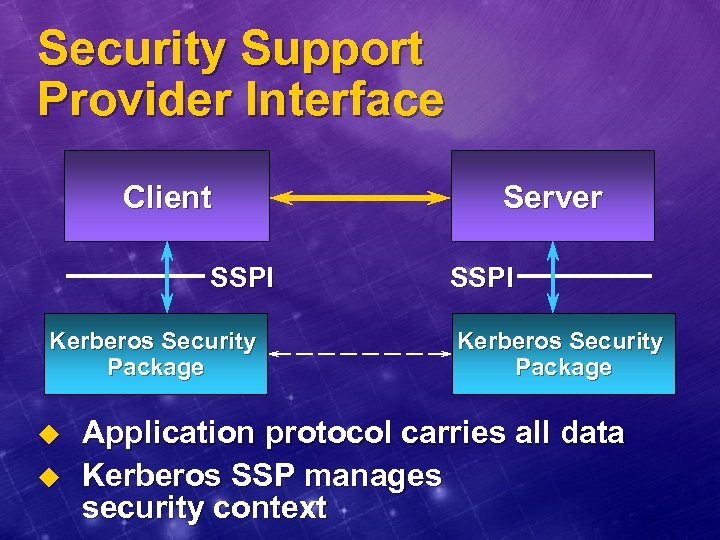
Security Support Provider Interface Client SSPI Kerberos Security Package u u Server SSPI Kerberos Security Package Application protocol carries all data Kerberos SSP manages security context

Connection Authentication u Client side l l l u Acquire credentials l Default or alternate Initialize security context Initiate connection Server side l l Acquire credentials l Default or alternate Accept client’s security context

Example: SSPI u Security package name l l u Authentication l l u “Kerberos” or “Negotiate” Negotiate package will choose Kerberos Initialize. Security. Context Accept. Security. Context Impersonation

Impersonation u Security contexts l u Access Token associated with processes and threads l Primary Token l Client Token Impersonation l l Accessing system resources on client’s behalf Access check and auditing on private resources
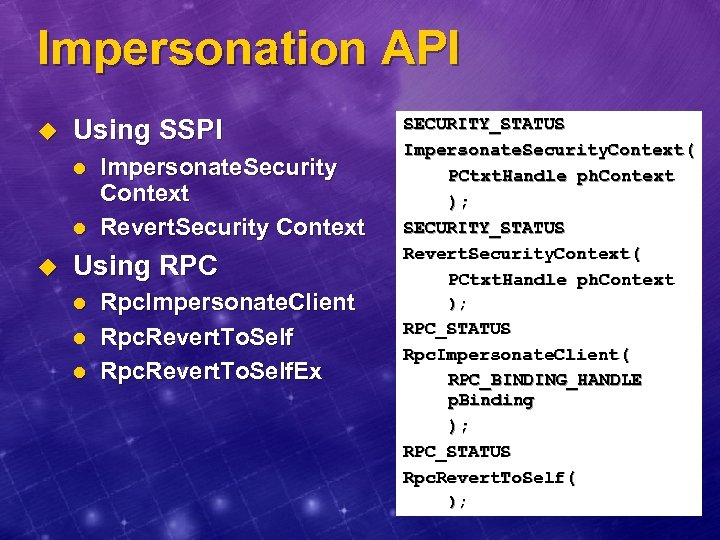
Impersonation API u Using SSPI l l u Impersonate. Security Context Revert. Security Context Using RPC l l l Rpc. Impersonate. Client Rpc. Revert. To. Self. Ex SECURITY_STATUS Impersonate. Security. Context( PCtxt. Handle ph. Context ); SECURITY_STATUS Revert. Security. Context( PCtxt. Handle ph. Context ); RPC_STATUS Rpc. Impersonate. Client( RPC_BINDING_HANDLE p. Binding ); RPC_STATUS Rpc. Revert. To. Self( );
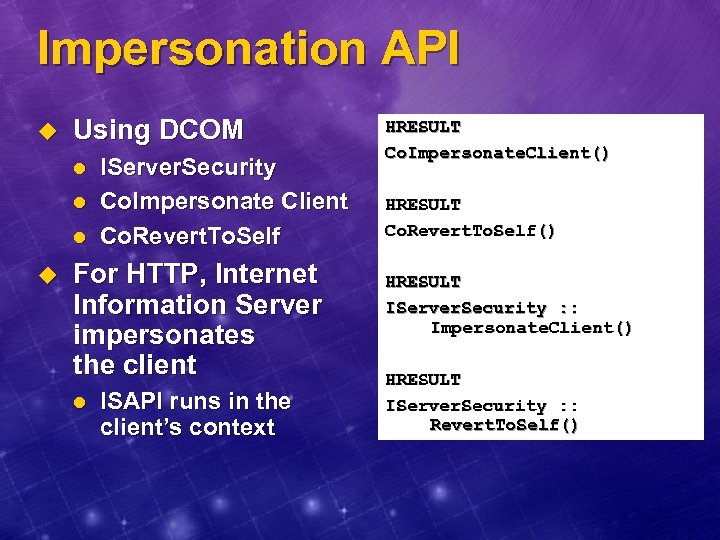
Impersonation API u Using DCOM l l l u IServer. Security Co. Impersonate Client Co. Revert. To. Self For HTTP, Internet Information Server impersonates the client l ISAPI runs in the client’s context HRESULT Co. Impersonate. Client() HRESULT Co. Revert. To. Self() HRESULT IServer. Security : : Impersonate. Client() HRESULT IServer. Security : : Revert. To. Self()
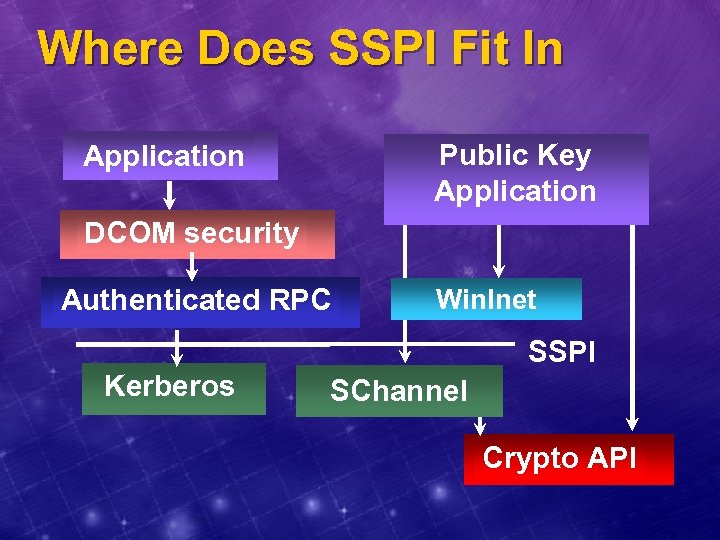
Where Does SSPI Fit In Public Key Application DCOM security Authenticated RPC Win. Inet SSPI Kerberos SChannel Crypto API

Kerberos Authentication u u u Kerberos service uses Active Directory Implemented by SSPI security provider Mutual authentication Supports 3 -tier delegation Windows NT access control Standards-based interoperability
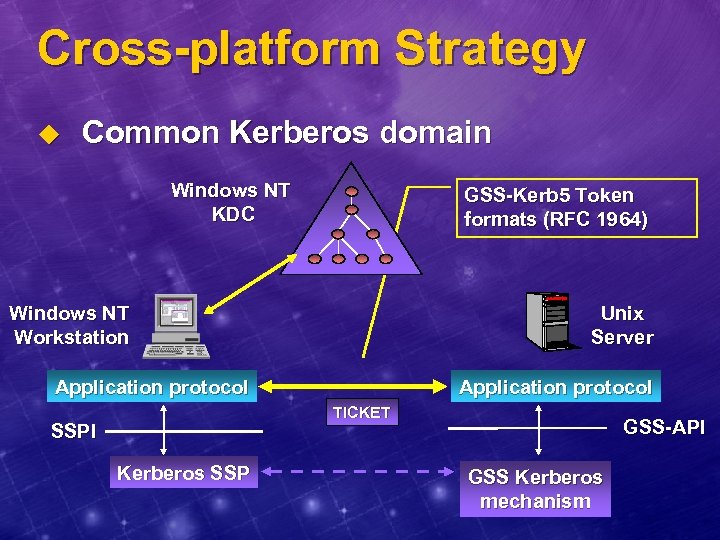
Cross-platform Strategy u Common Kerberos domain Windows NT KDC GSS-Kerb 5 Token formats (RFC 1964) Windows NT Workstation Unix Server Application protocol TICKET SSPI Kerberos SSP GSS-API GSS Kerberos mechanism

Three-Tier Security Delegation u u End-to-end user authentication Application requires data from several sources Flexibility to separate Web server from back-end data servers Single user account l u Simplify user management Access control through groups
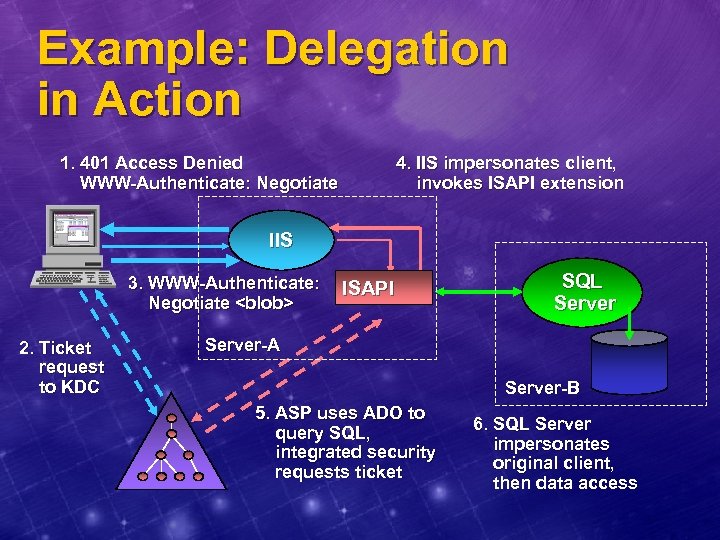
Example: Delegation in Action 1. 401 Access Denied WWW-Authenticate: Negotiate 4. IIS impersonates client, invokes ISAPI extension IIS 3. WWW-Authenticate: Negotiate <blob> 2. Ticket request to KDC ISAPI SQL Server-A Server-B 5. ASP uses ADO to query SQL, integrated security requests ticket 6. SQL Server impersonates original client, then data access
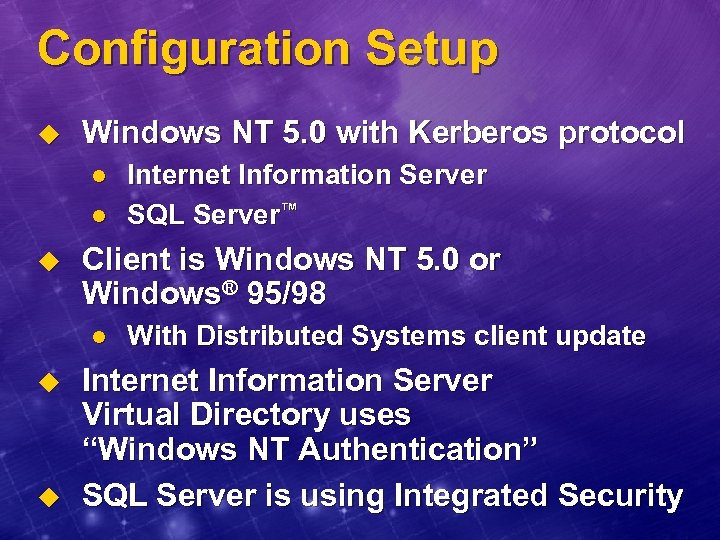
Configuration Setup u Windows NT 5. 0 with Kerberos protocol l l u Client is Windows NT 5. 0 or Windows® 95/98 l u u Internet Information Server SQL Server™ With Distributed Systems client update Internet Information Server Virtual Directory uses “Windows NT Authentication” SQL Server is using Integrated Security

Trusted For Delegation u Delegation means… l l l u u Server can do anything on behalf of client Trusted not to run unauthorized services Enabled on per-server basis Enable on the computer object in Active Directory Do not assume delegation is always enabled!

Windows NT Authorization u u What is the client allowed to do? Single sign on is not sufficient l l u Centralize authorization through roles Windows NT group membership Integrate authentication with server security model l Windows NT object security model
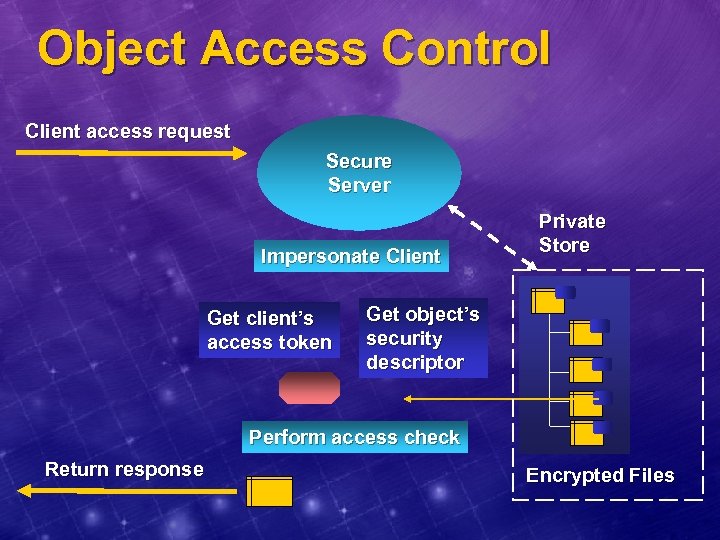
Object Access Control Client access request Secure Server Impersonate Client Get client’s access token Private Store Get object’s security descriptor Perform access check Return response Encrypted Files
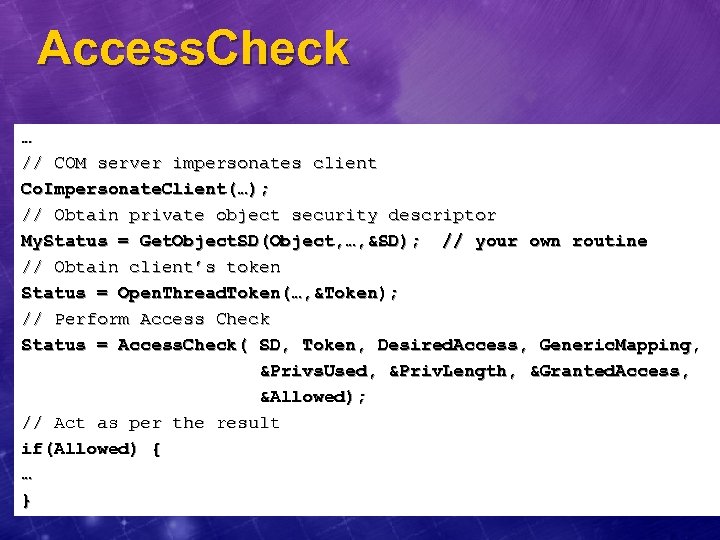
Access. Check … // COM server impersonates client Co. Impersonate. Client(…); // Obtain private object security descriptor My. Status = Get. Object. SD(Object, …, &SD); // your own routine // Obtain client’s token Status = Open. Thread. Token(…, &Token); // Perform Access Check Status = Access. Check( SD, Token, Desired. Access, Generic. Mapping, &Privs. Used, &Priv. Length, &Granted. Access, &Allowed); // Act as per the result if(Allowed) { … }
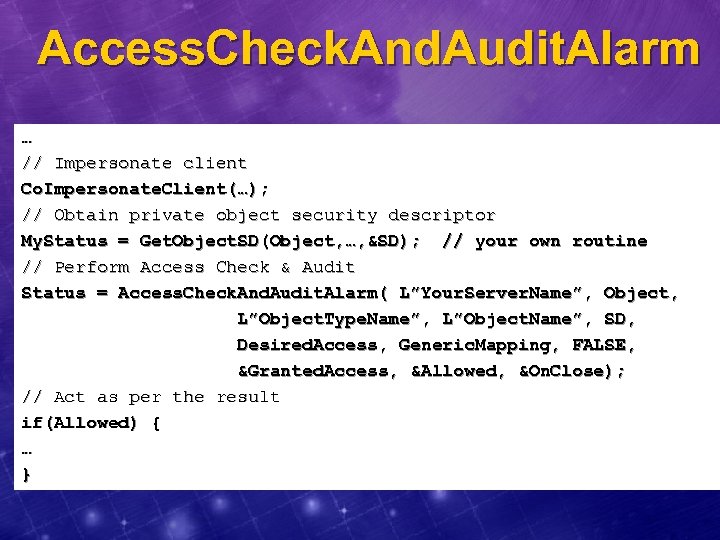
Access. Check. And. Audit. Alarm … // Impersonate client Co. Impersonate. Client(…); // Obtain private object security descriptor My. Status = Get. Object. SD(Object, …, &SD); // your own routine // Perform Access Check & Audit Status = Access. Check. And. Audit. Alarm( L”Your. Server. Name”, Object, L”Object. Type. Name”, L”Object. Name”, SD, Desired. Access, Generic. Mapping, FALSE, &Granted. Access, &Allowed, &On. Close); // Act as per the result if(Allowed) { … }

User Account Management u One unified enterprise account image l l u Synchronize with other account stores l l u All account properties, extensible schema LDAP access, remote management Directory synchronization - LDAP, LDIF Password change notification Authorization based on group membership for central access control l Roles defined by group membership

Single Sign On Summary u Comprehensive solution today l l u Cross-platform with industry standards l l u Windows NT and Back. Office services Platform security services for applications Kerberos v 5 and GSS token formats X. 509 v 3 certificates with SSL/TLS Familiar Windows NT security model extended to n-tier applications

Call To Action u Stop prompting for passwords! l l l u u u Use Windows NT distributed security Use SSPI or DCOM/RPC security Use Windows NT access control Leverage industry standard protocols for cross-platform security Depend on Active Directory for single user account store Check out the Security Showcase!

More Information u SSPI l l l u Kerberos v 5 l l u Distributed Security Services whitepaper http: //www. microsoft. com/ntserver Back. Office logo program l u SSPI Whitepaper on MSDN Platform SDK: doc and samples mssdksampleswin 32winntsecuritysockauth http: //www. microsoft. com/backoffice/designed MSPress® l “Running Microsoft Internet Information Server”

346cc5f875ef58339dee2136705f6e09.ppt