8b6d0767b1f116824b2ee4972c0e9447.ppt
- Количество слайдов: 46

Windows 7安全机制 李德虎

Windows 7安全机制 • UAC(User Account Control) • ASLR(Address Space Layout Randomization) • DEP(Data Execute Protection)

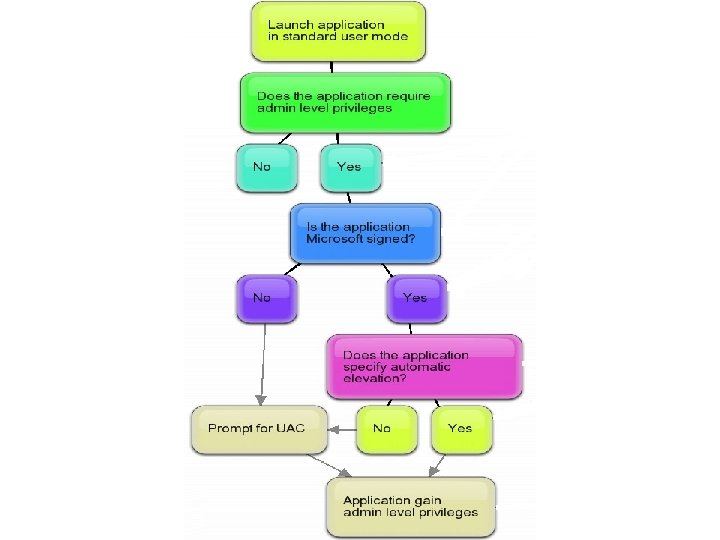
UAC • User Account Control • Goal: to control different accounts üProtect system settings from users üPrivacy between users on shared computers üProtect system security from malware
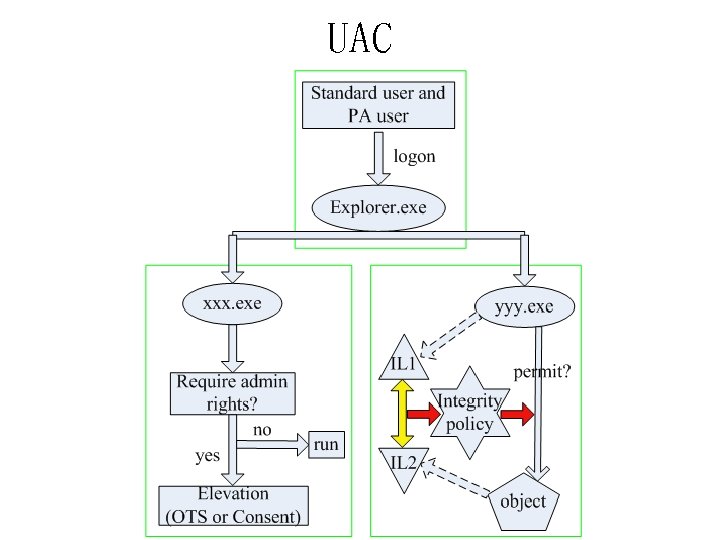
UAC • Idea – Standard user & administrator, by default standard user rights • Techniques – The Protected Administrator (PA) account – UAC elevation prompts – Windows Integrity Mechanism – File system and registry virtualization
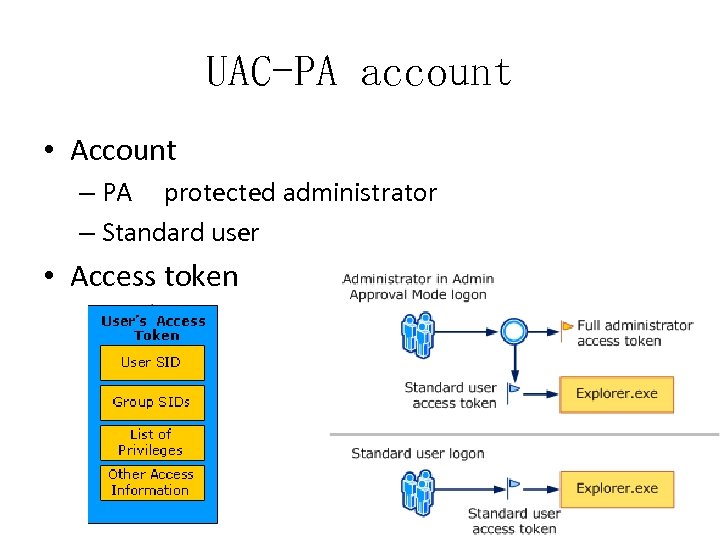
UAC-PA account • Account – PA protected administrator – Standard user • Access token

UAC-PA account • First process – Explorer. exe standard user token • Other processes – Inherit token from explorer. exe or its child processes – So, by default, standard user rights
UAC • Idea – Standard user & administrator, by default standard user rights • Techniques – The Protected Administrator (PA) account – UAC elevation prompts – Windows Integrity Mechanism – File system and registry virtualization
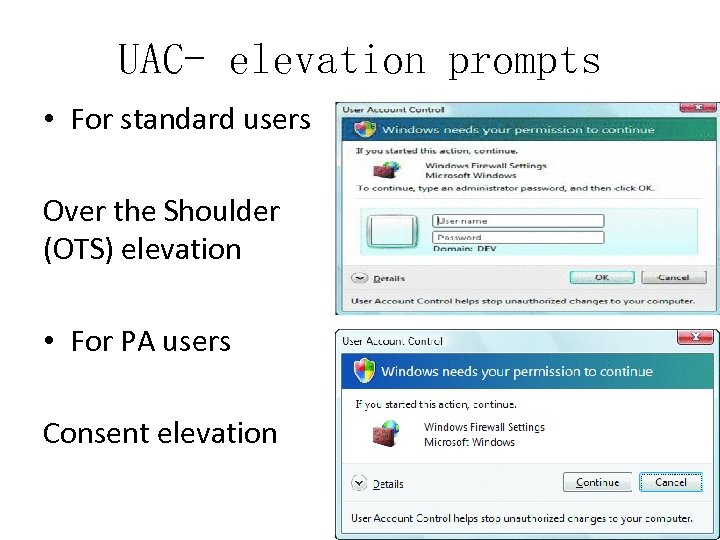
UAC- elevation prompts • For standard users Over the Shoulder (OTS) elevation • For PA users Consent elevation

UAC- elevation prompts • Need Administrator rights? – Most common : Application’s manifest file • Sysinternals : Sigcheck • as. Invoker, highest. Available, require. Administrator – heuristics, etc.
UAC • Idea – Standard user & administrator, by default standard user rights • Techniques – The Protected Administrator (PA) account – UAC elevation prompts – Windows Integrity Mechanism – File system and registry virtualization

UAC-Windows Integrity Mechanism • Windows Integrity Mechanism ØIntegrity level, integrity policy – all processes and objects have integrity levels – an object’s integrity policy can restrict the accesses for a process – Process’s IL>= Object’s IL
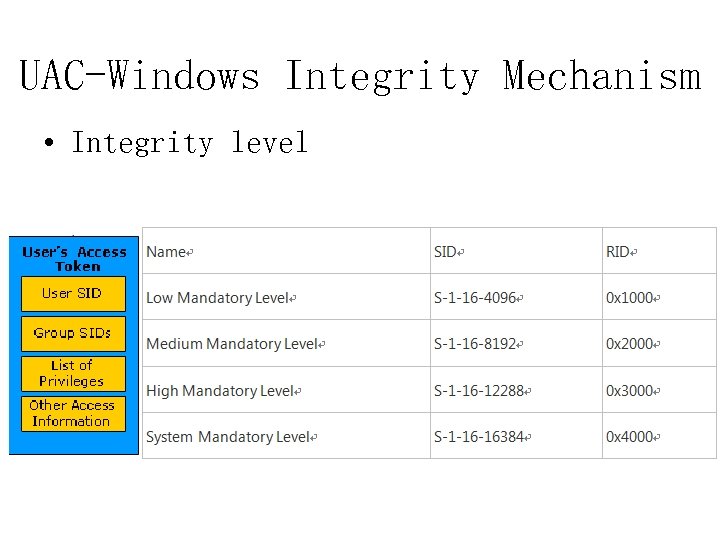
UAC-Windows Integrity Mechanism • Integrity level

UAC-Windows Integrity Mechanism • Integrity level – How is IL assigned? • processes usually inherit the IL of their parents • a process can also launch a process at a different IL – Sysinternals: Process Explorer or Access. Chk

UAC-Windows Integrity Mechanism • Integrity policy – default policy for most objects: No-Write-Up
UAC
UAC • Idea – Standard user & administrator, by default standard user rights • Techniques – The Protected Administrator (PA) account – UAC elevation prompts – Windows Integrity Mechanism – File system and registry virtualization
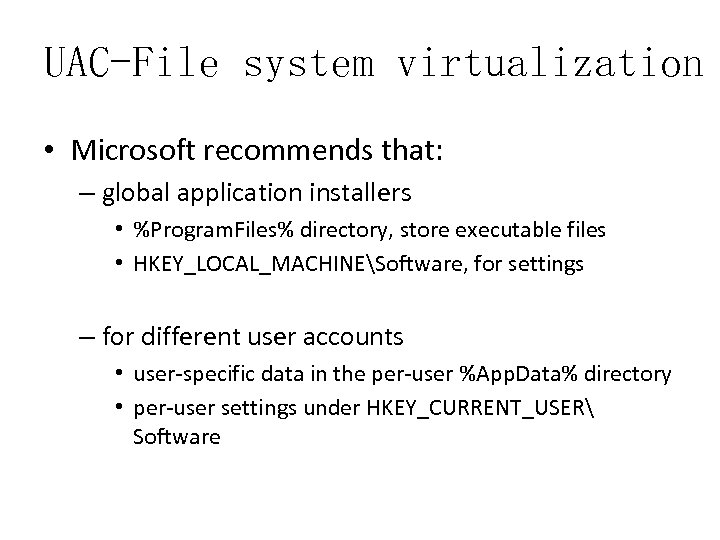
UAC-File system virtualization • Microsoft recommends that: – global application installers • %Program. Files% directory, store executable files • HKEY_LOCAL_MACHINESoftware, for settings – for different user accounts • user-specific data in the per-user %App. Data% directory • per-user settings under HKEY_CURRENT_USER Software

UAC-File system virtualization • Before Windows Vista: – Most Windows systems are single-user – Most users have been administrators • Apps that incorrectly save user data and settings to these locations work anyway, but in Vista it’s different.

UAC-File system virtualization • Legacy in Vista: – 32 -bit – not running with administrative rights – does not have a manifest file indicating that it was written for Windows Vista • Any operations not originating from a process classified as legacy are not virtualized.
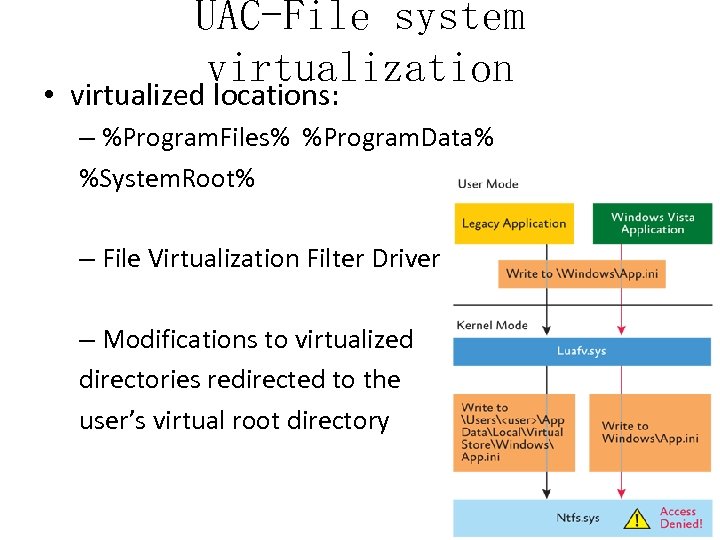
UAC-File system virtualization • virtualized locations: – %Program. Files% %Program. Data% %System. Root% – File Virtualization Filter Driver – Modifications to virtualized directories redirected to the user’s virtual root directory
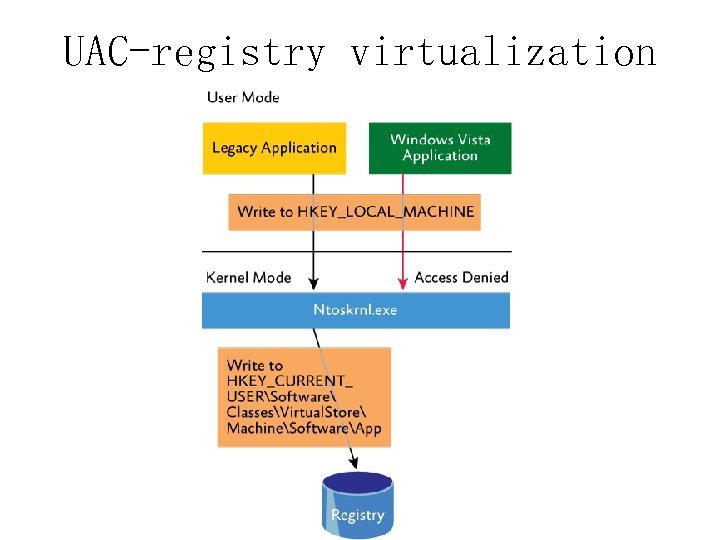
UAC-registry virtualization

UAC-Auto elevation • Goal – smoother user’s experience by reducing prompts • How? – "auto elevates" Windows executables – digitally signed by the Windows publisher, which is the certificate used to sign all code included with Windows(not shipped in Windows isn't included) – located in “secure” directories: e. g. WindowsSystem 32
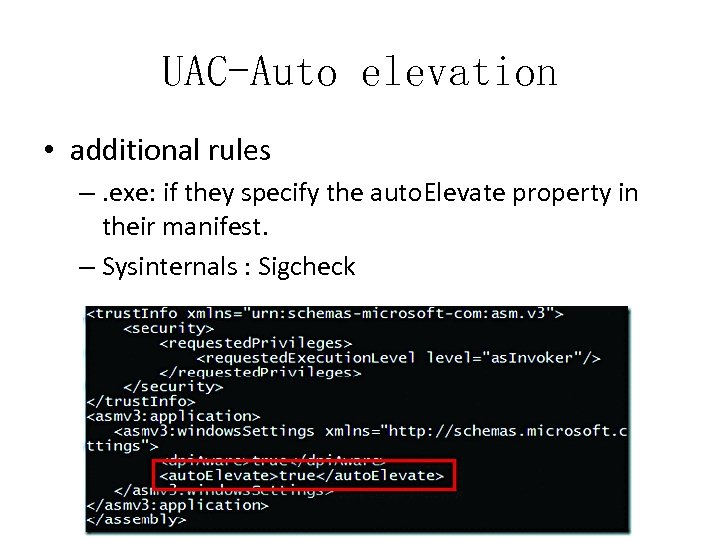
UAC-Auto elevation • additional rules –. exe: if they specify the auto. Elevate property in their manifest. – Sysinternals : Sigcheck

UAC-Auto elevation • additional rules – Microsoft Management Console, Mmc. exe –. MSC file lists the snap-ins MMC is to load ØMmc. exe gpedit. msc – Mmc. exe is a Windows executable –. MSC file(signed by Windows in a secure location) – listed on an internal list of auto-elevate. MSCs
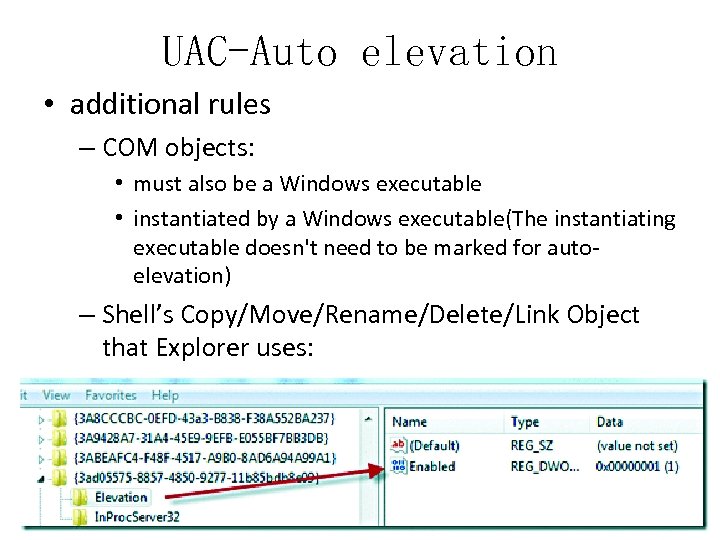
UAC-Auto elevation • additional rules – COM objects: • must also be a Windows executable • instantiated by a Windows executable(The instantiating executable doesn't need to be marked for autoelevation) – Shell’s Copy/Move/Rename/Delete/Link Object that Explorer uses:

UAC • Goal – security boundary between admin and non-admin code • But – Usability prevents the goal from being achieved • Questions – Provide a auto-elevate list? – Third-party software running in a PA account to take advantage of auto-elevation?

Windows 7安全机制 • UAC(User Account Control) • ASLR(Address Space Layout Randomization) • DEP(Data Execute Protection)

ASLR(vista) • Randomizes the addresses where objects are mapped – Images(both executables and DLLs) – heaps, stacks – the PEB and TEBs
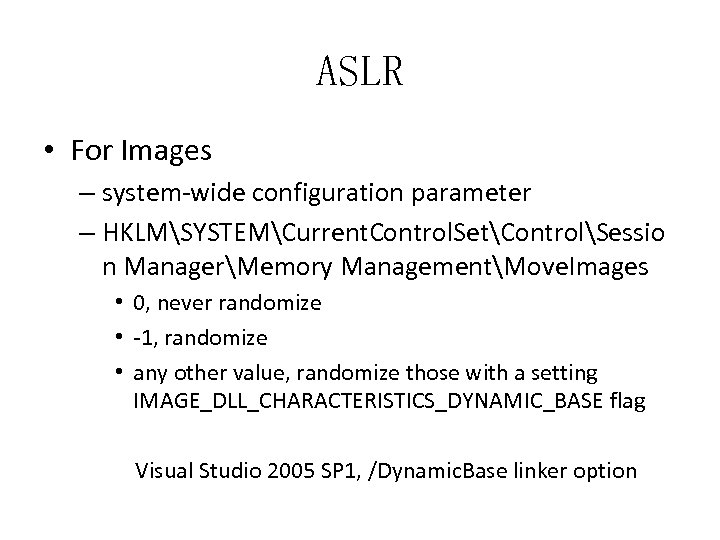
ASLR • For Images – system-wide configuration parameter – HKLMSYSTEMCurrent. Control. SetControlSessio n ManagerMemory ManagementMove. Images • 0, never randomize • -1, randomize • any other value, randomize those with a setting IMAGE_DLL_CHARACTERISTICS_DYNAMIC_BASE flag Visual Studio 2005 SP 1, /Dynamic. Base linker option

ASLR • Exe

ASLR • DLL – a DLL must be loaded at the same address in each process, to be shared – a global bitmap called _Mi. Image. Bit. Map – (0 x 78000000 -0 x 50000000)/64 KB=0 x 2800 bits – an 8 -bit random value initialized with the RDTSC instruction once per boot
ASLR • DLL – first DLL loaded on the system (NTDLL. DLL) • 256 possible locations – subsequent DLLs depends on • the address of NTDLL. DLL • the order in which the DLLs are loaded • To increase the randomness: Smp. Randomize. Dll. List

ASLR • Heap – In the past, Nt. Allocate. Virtual. Memory, a linear address space search, predictable – Vista, Rtl. Heap. Create, randomness

ASLR • Stack twofold randomization – the base of the stack, chosen randomly • a random 5 -bit value x time stamp counter – an offset, where the stack starts, chosen randomly • 9 -bit random value*4 B time stamp counter

Windows 7安全机制 • UAC(User Account Control) • ASLR(Address Space Layout Randomization) • DEP(Data Execute Protection)
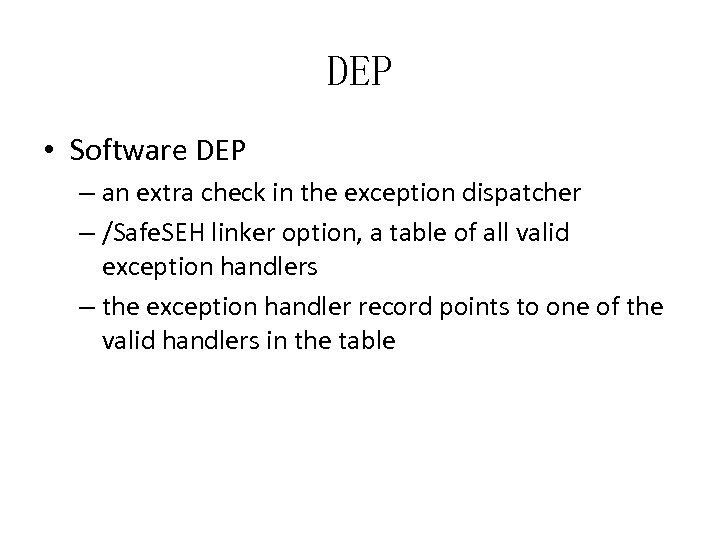
DEP • Software DEP – an extra check in the exception dispatcher – /Safe. SEH linker option, a table of all valid exception handlers – the exception handler record points to one of the valid handlers in the table
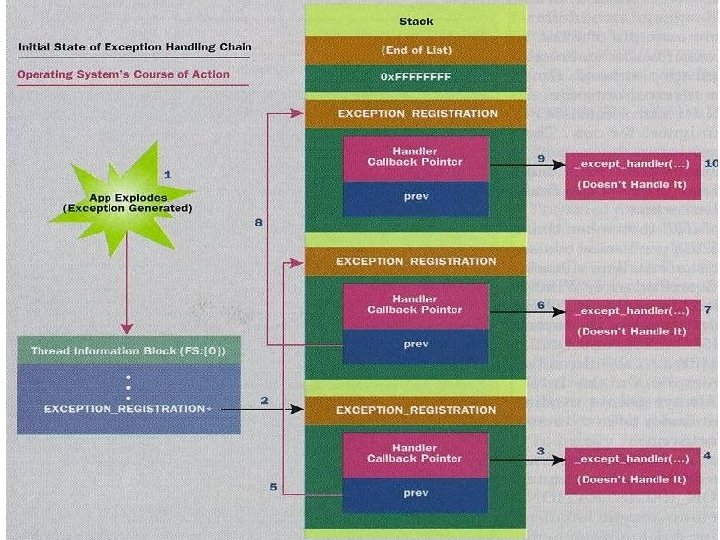

DEP • Hardware support for NX – Windows, page-level protection – X 86, a single bit, R? W? no bit to control execution – CPU after 2004, NX bit (No e. Xecute)

DEP • DEP policies(Vista, server 2008, win 7) – Opt. In – Opt. Out – Always. On – Always. Off
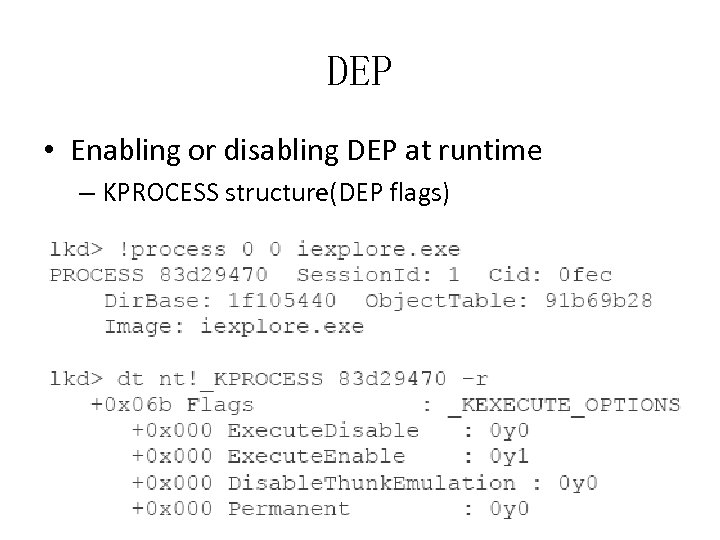
DEP • Enabling or disabling DEP at runtime – KPROCESS structure(DEP flags)

DEP • Enabling or disabling DEP at runtime – Nt. Query. Information. Process Nt. Set. Information. Process – XP SP 3, Vista SP 1, new API • Set. Process. DEPPolicy • Get. System. DEPPolicy

ASLR&DEP • Bypass DEP – Code reuse: ret 2 libc(Ntdll!Zw. Set. Information. Process) • Bypass ASLR – Search in PEB List. Entry, trivially
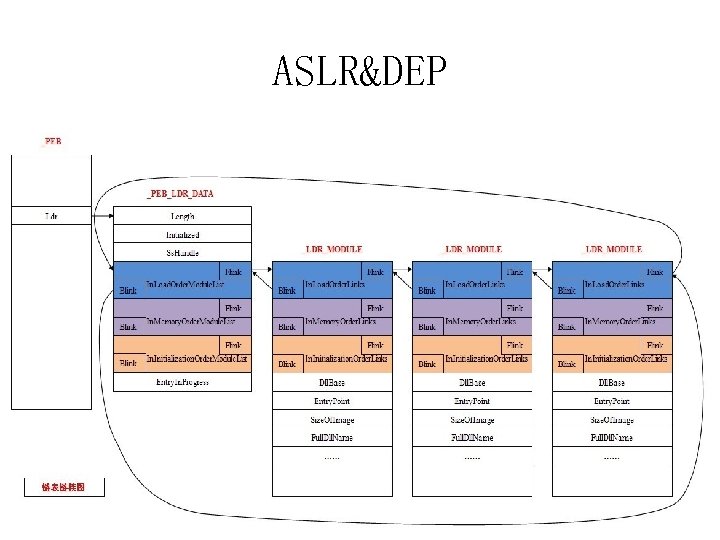
ASLR&DEP
ASLR&DEP • When combined together, quite difficult – DEP: a call to a DEP function in a non ASLR module – ASLR: at least all the system libraries are protected • But not impossible – Some application modules not protected
sites • http: //www. pretentiousname. com/misc/win 7 _uac_whitelist 2. html(Win 7 Elevate 32 v 2. exe) • Video: http: //leo. lss. com. au/W 7 E_VID_INT. htm • Blogs: – http: //technet. microsoft. com/enus/magazine/2009. 07. uac. aspx – http: //technet. microsoft. com/enus/magazine/2007. 06. uac. aspx
8b6d0767b1f116824b2ee4972c0e9447.ppt