b8a0455ea43c861f91a8c7aade428fc6.ppt
- Количество слайдов: 83

Windows 2000: Concepts & Deployment Larry Lieberman NT Support Engineer Premier Enterprise Support Microsoft Corporation

Agenda v v Active Directory Microsoft DNS Distributed Security System Management

Active Directory v v v Architecture Components Planning AD Design
AD Architecture v v v X. 500 derived data model Directory stored schema Windows 2000 Trusted Computing Base security model Delegated Administration Model DNS integration

AD Components (1/10) v v v Objects Organizational Units (OUs) Domains Sites Trees & Forests Global Catalog
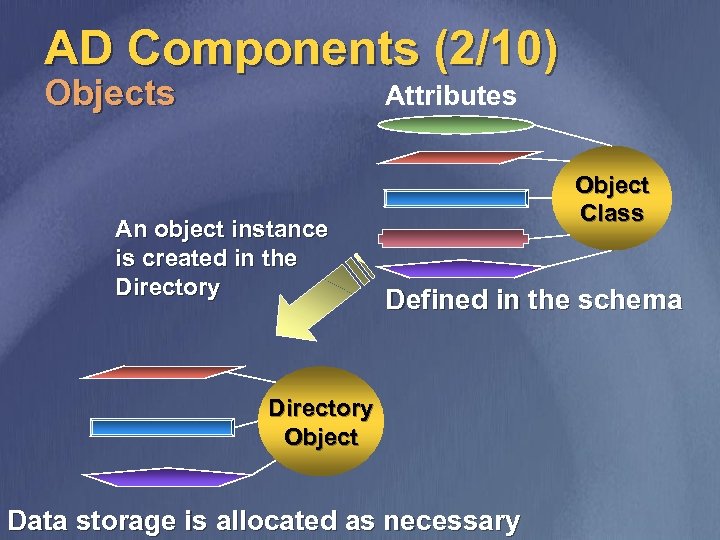
AD Components (2/10) Objects Attributes An object instance is created in the Directory Object Class Defined in the schema Directory Object Data storage is allocated as necessary
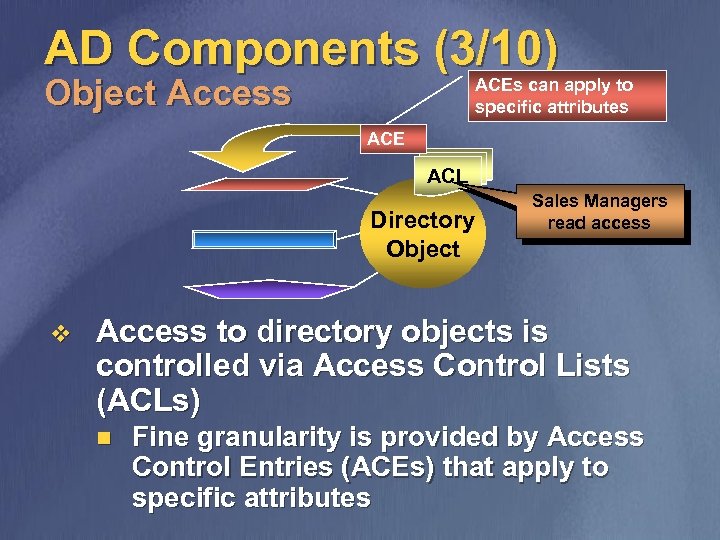
AD Components (3/10) Object Access ACEs can apply to specific attributes ACE ACL Directory Object v Sales Managers read access Access to directory objects is controlled via Access Control Lists (ACLs) n Fine granularity is provided by Access Control Entries (ACEs) that apply to specific attributes
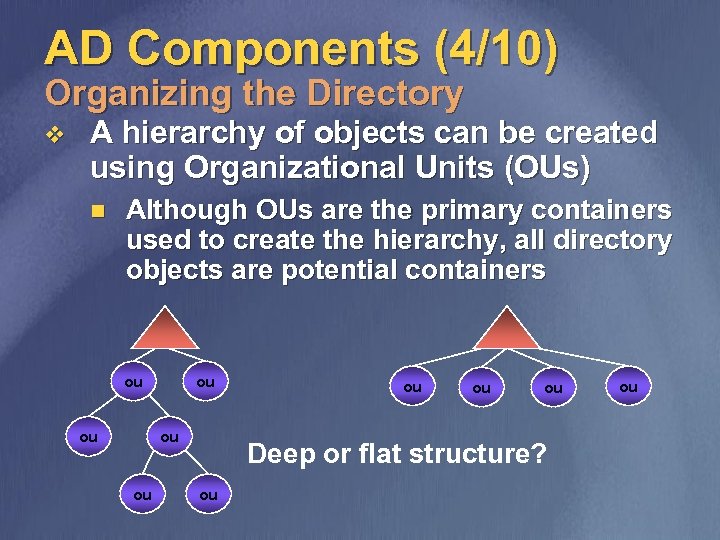
AD Components (4/10) Organizing the Directory v A hierarchy of objects can be created using Organizational Units (OUs) n Although OUs are the primary containers used to create the hierarchy, all directory objects are potential containers ou ou Deep or flat structure? ou ou
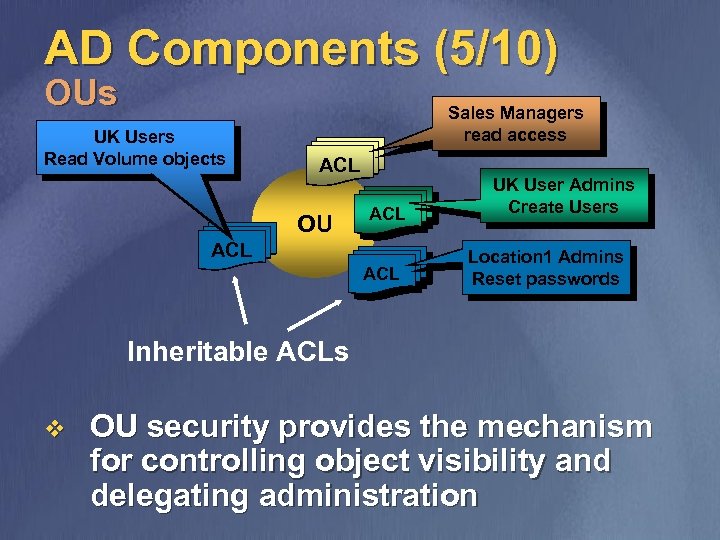
AD Components (5/10) OUs UK Users Read Volume objects Sales Managers read access ACL OU ACL ACL UK User Admins Create Users Location 1 Admins Reset passwords Inheritable ACLs v OU security provides the mechanism for controlling object visibility and delegating administration
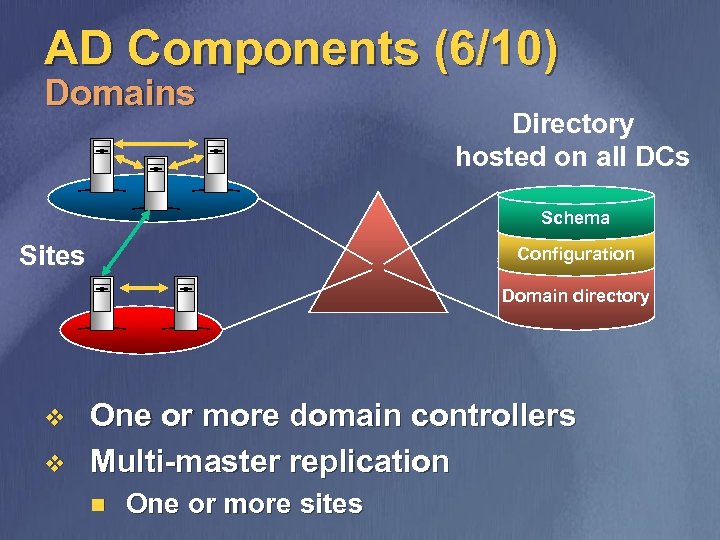
AD Components (6/10) Domains Directory hosted on all DCs Schema Sites Configuration Domain directory v v One or more domain controllers Multi-master replication n One or more sites
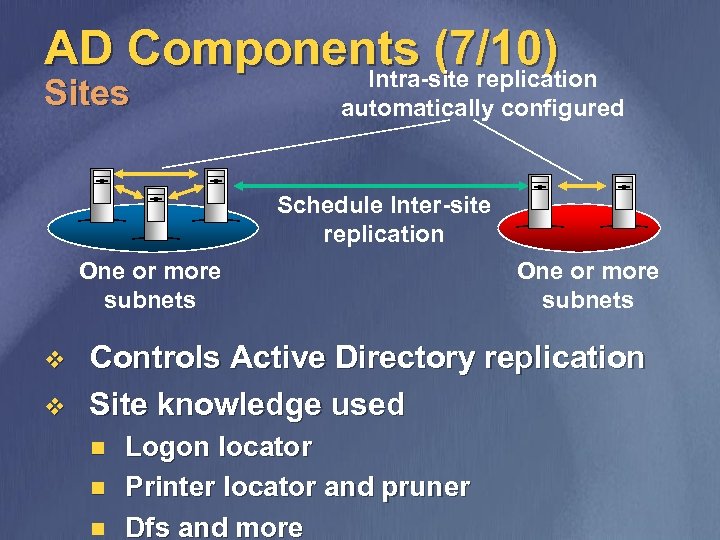
AD Components (7/10) Intra-site replication Sites automatically configured Schedule Inter-site replication One or more subnets v v One or more subnets Controls Active Directory replication Site knowledge used n n n Logon locator Printer locator and pruner Dfs and more
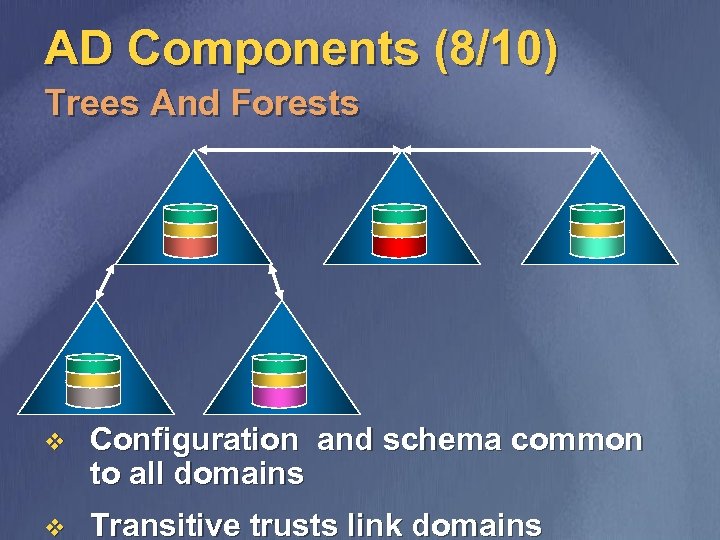
AD Components (8/10) Trees And Forests v Configuration and schema common to all domains v Transitive trusts link domains
AD Components (9/10) Boundaries v v Replication Administration Security Policy Group Policy
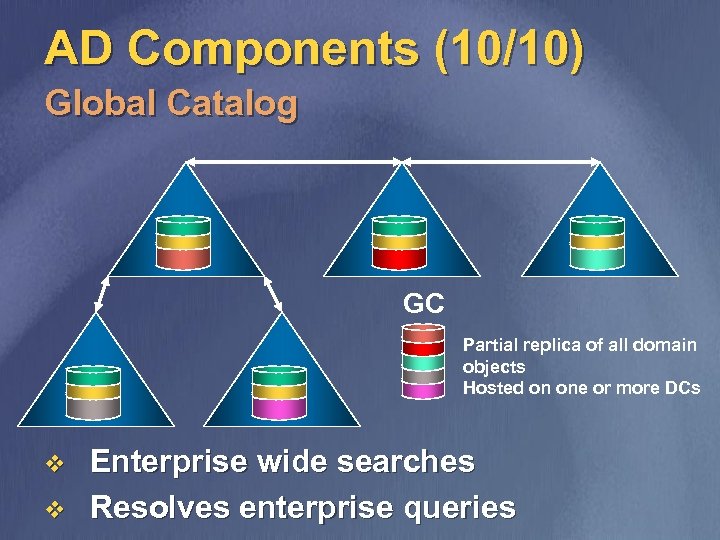
AD Components (10/10) Global Catalog GC Partial replica of all domain objects Hosted on one or more DCs v v Enterprise wide searches Resolves enterprise queries

Planning AD Design (1/6) Considerations v v v v Defining a logical hierarchy of resources Administrative architectures Allocation of physical resources and budget Current infrastructure and upgrade strategies Data availability requirements Network bandwidth Politics

Planning AD Design (2/6) One Or More Forests v v All domains in a forest share a common schema and global catalog Create multiple forests if: n n n Separate schemas are required One or more domains are required to be isolated from the spanning tree of transitive trusts Total administrative autonomy is required

Planning AD Design (3/6) Domain Structure v Where possible use a single domain n n v Use OUs to delegate administration Use sites to tune replication Use multiple domains when there is a requirement for n n n Scalability across WANs Autonomous administrative entities Different security account policies n password, lockout and Kerberos ticket

Planning AD Design (4/6) Multiple Domains(1/3) v Containment of network traffic n n v Directory replication Policies (FRS) In-place upgrades from Windows NT domains n n n Autonomous divisions with separate names No technical reasons, only politics Names are not important

Planning AD Design (5/6) Multiple Domains(2/3) v Each domain has an incremental overhead n n v Increased administration Increased hardware n Separate DCs are required for each domain Try to avoid creating divisional or departmental domains for purely political reasons n Change is inevitable, they are easy to create and hard to retire

Planning AD Design (6/6) Multiple Domains(3/3) v Separate the production forest from development and testing n v Prevents unwanted schema changes propagating through the enterprise Create a separate forest to restrict access for business partners

Microsoft DNS v v v Windows 2000 DNS Requirements MS DNS Features DNS Design

DNS Requirements v v A DNS server that is authoritative for a Windows 2000 domain MUST support SRV records (RFC 2052) It also should support dynamic updates (RFC 2136) n The NETLOGON service on the domain controller automatically registers all of the domain services and the site that it supports

MS DNS Features (1/12) v v v Active Directory integration Dynamic Update Aging Administrative tools Caching resolver

MS DNS Features (2/12) Active Directory Integration v AD-integrated DNS zone is multi-master
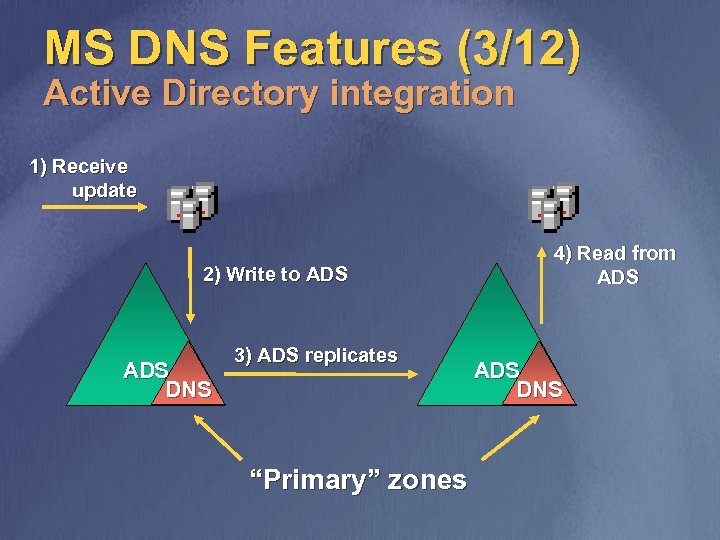
MS DNS Features (3/12) Active Directory integration 1) Receive update 2) Write to ADS DNS 3) ADS replicates “Primary” zones 4) Read from ADS DNS

MS DNS Features (4/12) Active Directory integration v AD-integrated DNS zone is multi-master n n High availability of write, as well as read Doesn’t require separate from AD replication

MS DNS Features (5/12) Active Directory integration v v ADS replication is loosely consistent Name-level collision n v Two hosts create same name simultaneously (first writer wins) Attribute-level collision n Two hosts modify A RRset for microsoft. com simultaneously (lastwriter wins)

MS DNS Features (6/12) Dynamic Update v v Based on RFC 2136 Client discovers primary server for the zone where the record should be added/deleted Client sends a dynamic update package to the primary server Primary server processes the update
MS DNS Features (7/12) Dynamic Update v Windows 2000 computer registers n n A RR with: n Hostname. Primary. Dns. Suffix (default) n and Hostname. Adapter. Specific. Dns. Suffix (if configured) PTR RR if adapter is not DHCP configured or DHCP server doesn’t support DNS RR registration

MS DNS Features (8/12) Dynamic Update v Windows 2000 DHCP server registers (based on draft-ietf-dhcp-dns-*. txt) n n n v PTR records on behalf of upgraded clients (default) A and PTR records on behalf of downlevel clients (default) A and PTR records on behalf of upgraded clients (if configured) Windows 2000 DHCP server removes records that it registered upon lease expiration

MS DNS Features (9/12) Secure Dynamic Update v v Based on draft-skwan-gss-tsig-04. txt Available only on AD-integrated zones Per -zone and -name granularity ACL on each zone and name

MS DNS Features (10/12) Aging/Scavenging v v Enables deletion of the stale records in AD-integrated zones Requires periodic refreshes of the records

MS DNS Features (12/12) Caching Resolver v Windows 2000 service n n v Caches RRs according to TTL Negative caching Tracks transient/Pn. P adapters Reorders servers according to responsiveness Fewer round-trips, fewer timeouts, faster response time

DNS Design (1/11) To support DC locator v v DNS server authoritative for the DC records MUST support SRV RRs Support for Dynamic Updates is recommended

DNS Design (2/11) v Delegate a DNS zone for each AD domain to the DNS servers running on the DCs in that AD domain

DNS Design (3/11) corp. example. com Zones: Primary AD-int “corp. example. com”
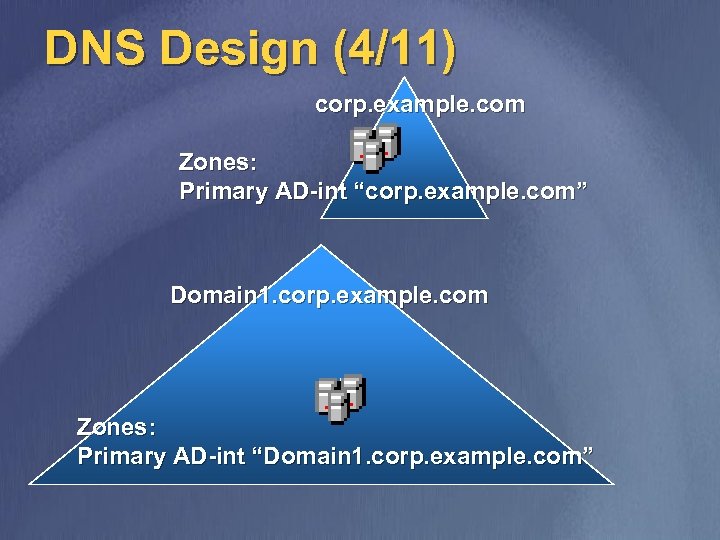
DNS Design (4/11) corp. example. com Zones: Primary AD-int “corp. example. com” Domain 1. corp. example. com Zones: Primary AD-int “Domain 1. corp. example. com”

DNS Design (5/11) v v Delegate a DNS zone for each AD domain to the DNS servers running on a DC in that AD domain Install a DNS server on at least two DCs in each AD domain and one DC in each site
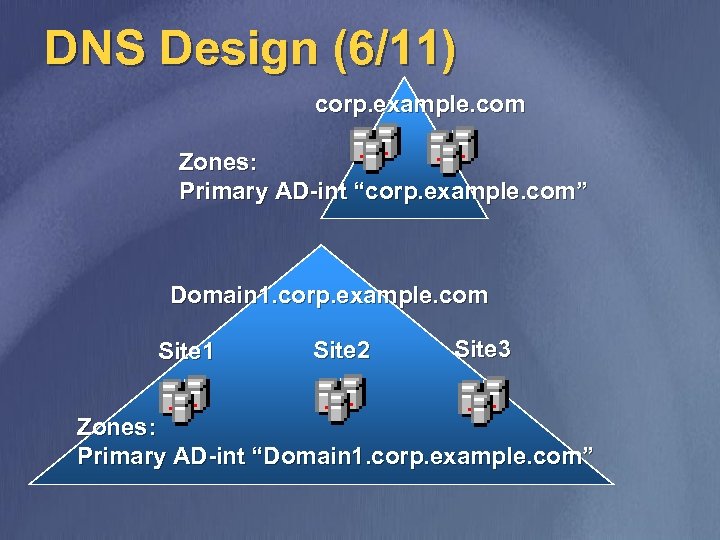
DNS Design (6/11) corp. example. com Zones: Primary AD-int “corp. example. com” Domain 1. corp. example. com Site 1 Site 2 Site 3 Zones: Primary AD-int “Domain 1. corp. example. com”

DNS Design (7/11) v v v Delegate a DNS zone for each AD domain to the DNS servers running on a DC in that AD domain Install a DNS server on at least two DCs in each AD domain and one DC in each site If different sites in the forest are connected over slow link, delegate the zone “_msdcs. <Forest. Name>” and make at least one DNS server in every site secondary for this zone
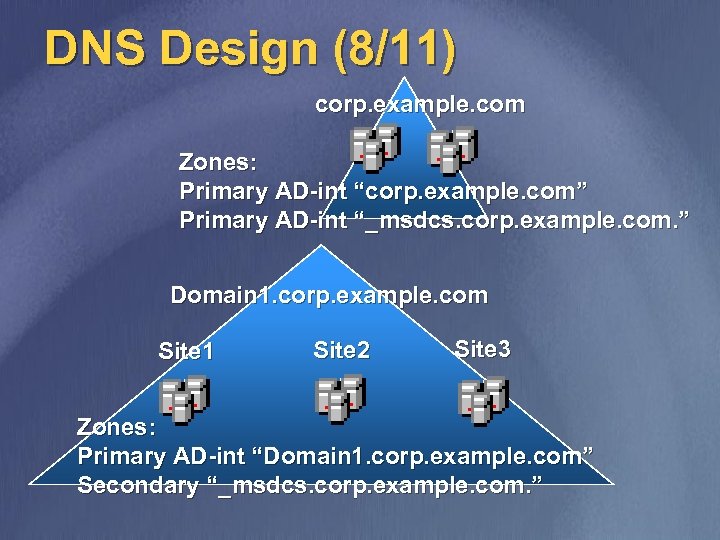
DNS Design (8/11) corp. example. com Zones: Primary AD-int “corp. example. com” Primary AD-int “_msdcs. corp. example. com. ” Domain 1. corp. example. com Site 1 Site 2 Site 3 Zones: Primary AD-int “Domain 1. corp. example. com” Secondary “_msdcs. corp. example. com. ”
DNS Design (9/11) v v Install a DNS server on at least two DCs in each AD domain and one DC in each site Delegate a DNS zone for each AD domain to the DNS servers running on a DC in that AD domain If different domains of the forest are connected over slow links, delegate the zone _msdcs. <Forest. Name> and make at least one DNS server in every site secondary for this zone Each client should be configured to query at least two DNS servers one of which is in the same site
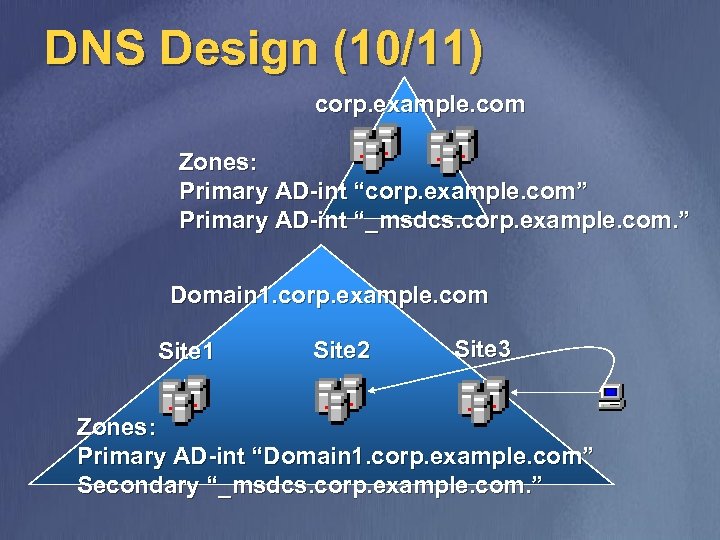
DNS Design (10/11) corp. example. com Zones: Primary AD-int “corp. example. com” Primary AD-int “_msdcs. corp. example. com. ” Domain 1. corp. example. com Site 1 Site 2 Site 3 Zones: Primary AD-int “Domain 1. corp. example. com” Secondary “_msdcs. corp. example. com. ”
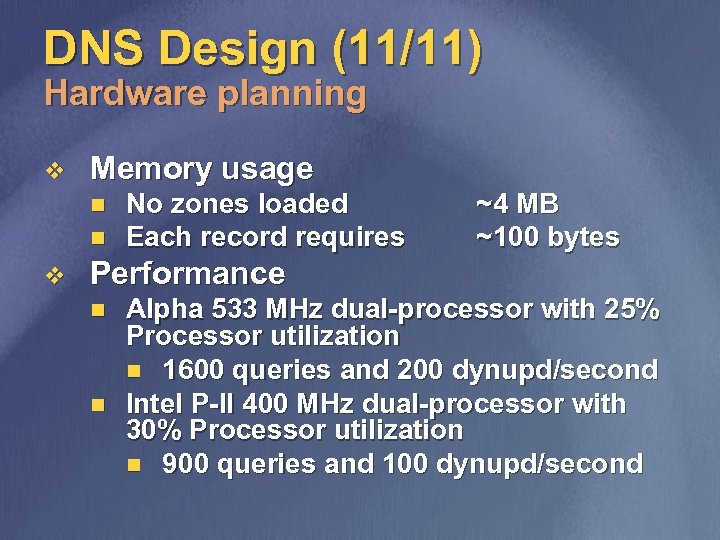
DNS Design (11/11) Hardware planning v Memory usage n n v No zones loaded Each record requires ~4 MB ~100 bytes Performance n n Alpha 533 MHz dual-processor with 25% Processor utilization n 1600 queries and 200 dynupd/second Intel P-II 400 MHz dual-processor with 30% Processor utilization n 900 queries and 100 dynupd/second

Security Topics v v v v Kerberos Integration with Windows NT Security Provider Architecture Public Key Security Components Smart card logon and authentication Encrypting File System Security Policies and Domain Trust Secure Windows NT Configuration

Security Goals v v v Single enterprise logon Integrated security services with Windows NT Directory Service Delegated administration and scalability for large domains Strong network authentication protocols Standard protocols for interoperability of authentication

Authentication/ Authorization v Authenticate using domain credentials n v Authorization based on group membership n v User account defined in Active Directory Centralize management of access rights Distributed security tied to the Windows NT Security Model n n Network services use impersonation Object-based access control lists
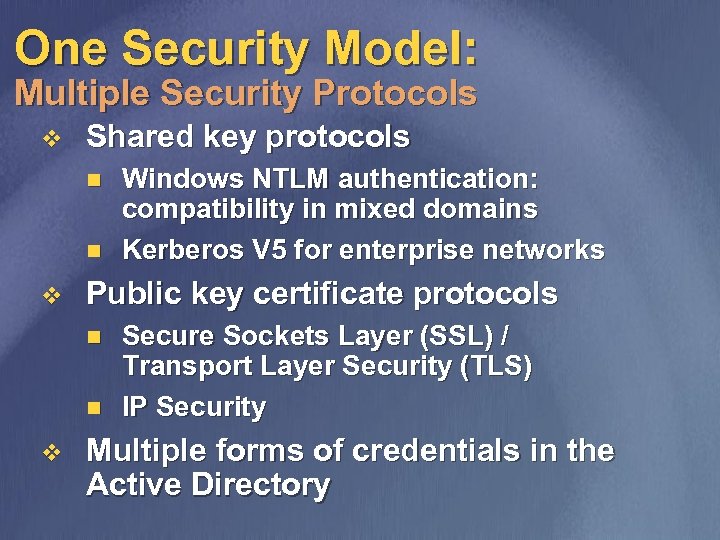
One Security Model: Multiple Security Protocols v Shared key protocols n n v Public key certificate protocols n n v Windows NTLM authentication: compatibility in mixed domains Kerberos V 5 for enterprise networks Secure Sockets Layer (SSL) / Transport Layer Security (TLS) IP Security Multiple forms of credentials in the Active Directory
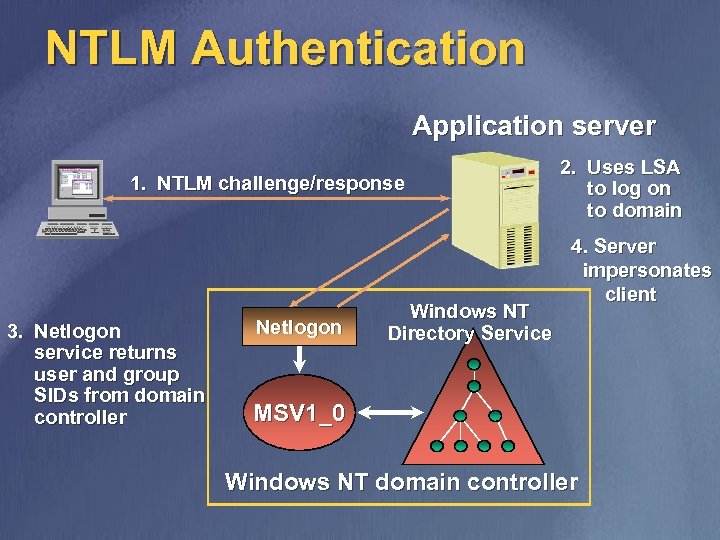
NTLM Authentication Application server 1. NTLM challenge/response 3. Netlogon service returns user and group SIDs from domain controller Netlogon Windows NT Directory Service 2. Uses LSA to log on to domain 4. Server impersonates client MSV 1_0 Windows NT domain controller
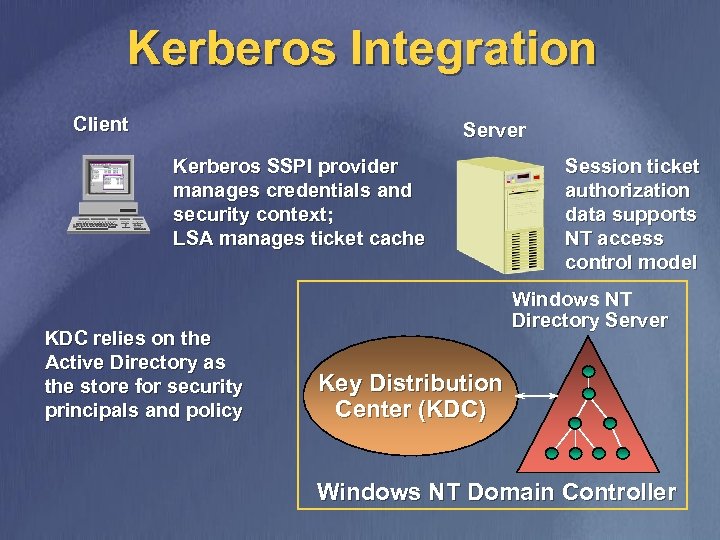
Kerberos Integration Client Server Kerberos SSPI provider manages credentials and security context; LSA manages ticket cache KDC relies on the Active Directory as the store for security principals and policy Session ticket authorization data supports NT access control model Windows NT Directory Server Key Distribution Center (KDC) Windows NT Domain Controller

Kerberos Protocol Advantages v Faster connection authentication n n v v Mutual authentication of both client, server Delegation of authentication n v Impersonation in three-tier client/server architectures Transitive trust between domains n v Server scalability for high-volume connections Reuse session tickets from cache Simplify inter-domain trust management Mature IETF standard for interoperability n Testing with MIT Kerberos V 5 Release

Kerberos Unix Interoperability v Based on Kerberos V 5 Protocol n n v Windows NT DS hosts the KDC n n n v RFC 1510 and RFC 1964 token format Testing with MIT Kerb V 5 Release UNIX clients to Unix Servers UNIX clients to NT Servers NT clients to UNIX Servers Simple cross-realm authentication n UNIX realm to NT domain
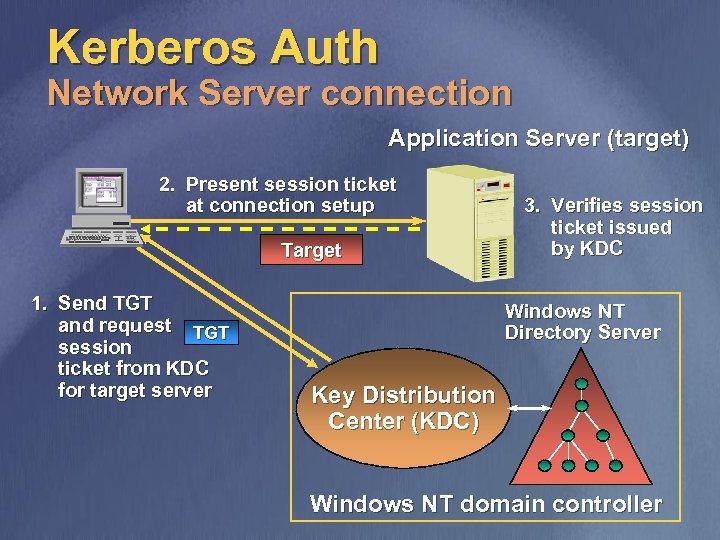
Kerberos Auth Network Server connection Application Server (target) 2. Present session ticket at connection setup Target 1. Send TGT and request TGT session ticket from KDC for target server 3. Verifies session ticket issued by KDC Windows NT Directory Server Key Distribution Center (KDC) Windows NT domain controller
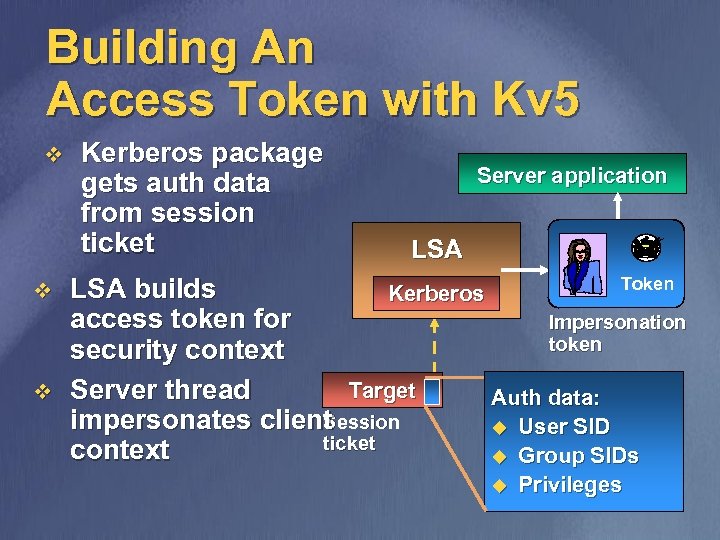
Building An Access Token with Kv 5 v v v Kerberos package gets auth data from session ticket Server application LSA Token LSA builds Kerberos access token for Impersonation token security context Target Server thread Auth data: Session impersonates client u User SID ticket context u Group SIDs u Privileges
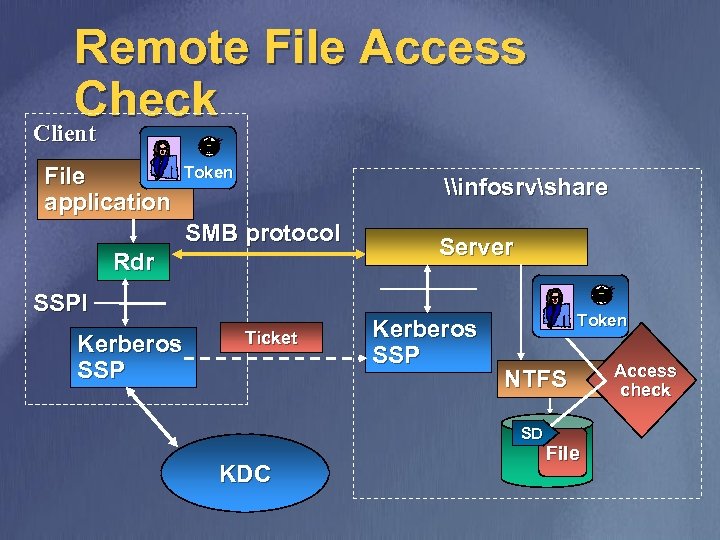
Remote File Access Check Client File application Token \infosrvshare SMB protocol Rdr SSPI Kerberos SSP Ticket Server Kerberos SSP Token NTFS SD KDC File Access check
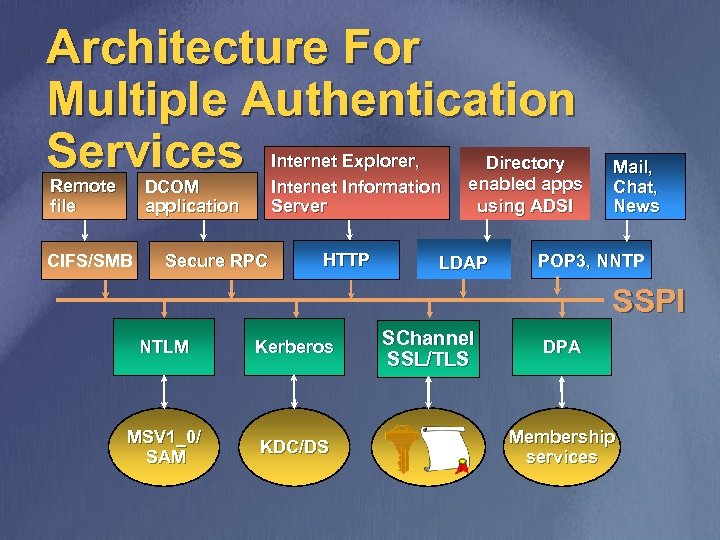
Architecture For Multiple Authentication Services Remote file Internet Explorer, Internet Information Server DCOM application CIFS/SMB Secure RPC HTTP Directory enabled apps using ADSI LDAP Mail, Chat, News POP 3, NNTP SSPI NTLM Kerberos MSV 1_0/ SAM KDC/DS SChannel SSL/TLS DPA Membership services

Windows NT 4. 0 - 5. 0 Interoperability v Windows NT 4. 0 clients and servers n v Windows NT 5. 0 clients n n n v Use NTLM authentication Locate NT 5. 0 Active Directory and KDC Support smart card logon Use Kerberos or NTLM protocol Windows NT 5. 0 Servers n Accept both NTLM or Kerberos protocol
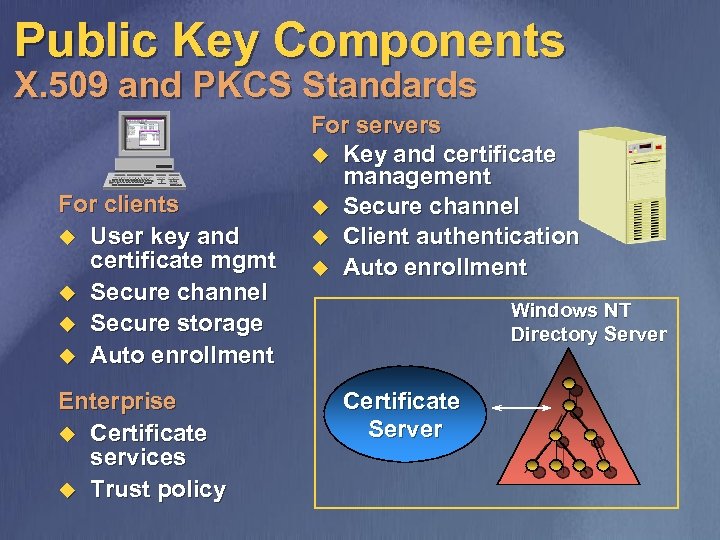
Public Key Components X. 509 and PKCS Standards For clients u User key and certificate mgmt u Secure channel u Secure storage u Auto enrollment Enterprise u Certificate services u Trust policy For servers u Key and certificate management u Secure channel u Client authentication u Auto enrollment Windows NT Directory Server Certificate Server
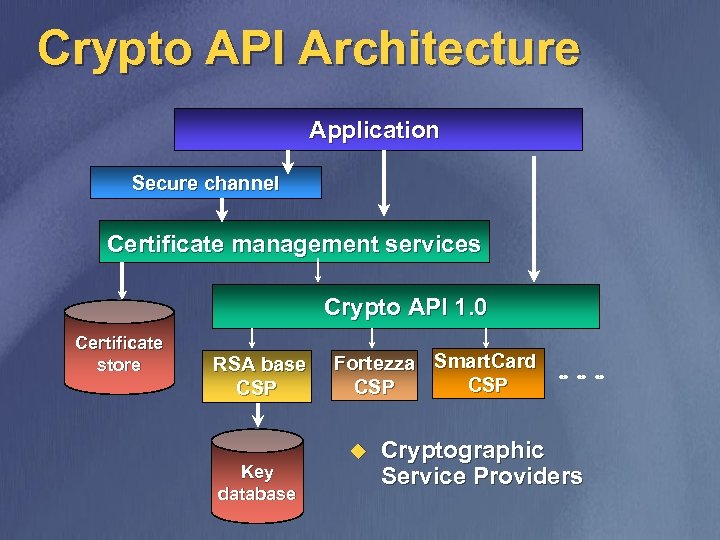
Crypto API Architecture Application Secure channel Certificate management services Crypto API 1. 0 Certificate store RSA base CSP Key database Fortezza Smart. Card CSP u Cryptographic Service Providers

SSL Client Authentication Integrated Security Administration v Strong authentication using X. 509 certificates n v Security account management n v v Single user ID for multiple protocols Use existing infrastructure: ccount admin and access control Accept third-party X. 509 certificates from trusted Certificate Authorities Inter-business authentication
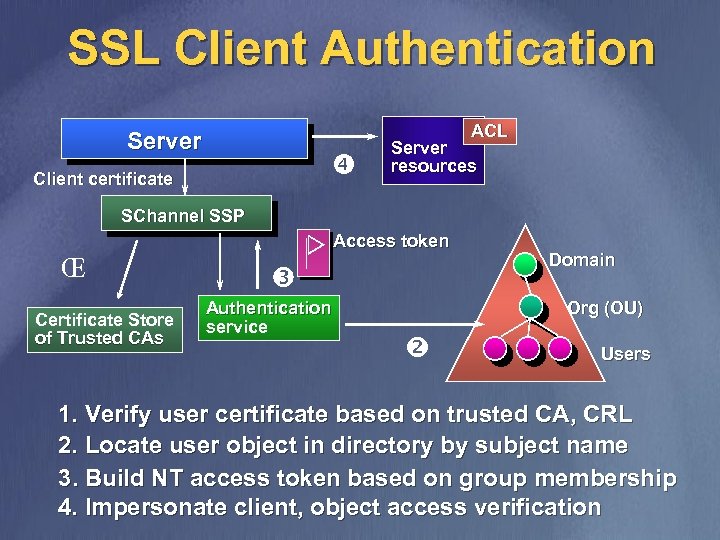
SSL Client Authentication ACL Server Client certificate Server resources SChannel SSP Access token ΠCertificate Store of Trusted CAs Authentication service Domain Org (OU) Users 1. Verify user certificate based on trusted CA, CRL 2. Locate user object in directory by subject name 3. Build NT access token based on group membership 4. Impersonate client, object access verification
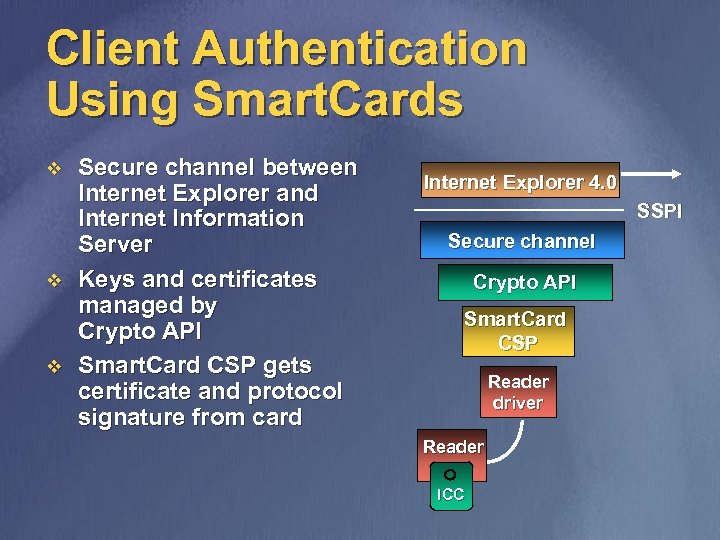
Client Authentication Using Smart. Cards v v v Secure channel between Internet Explorer and Internet Information Server Keys and certificates managed by Crypto API Smart. Card CSP gets certificate and protocol signature from card Internet Explorer 4. 0 SSPI Secure channel Crypto API Smart. Card CSP Reader driver Reader ICC
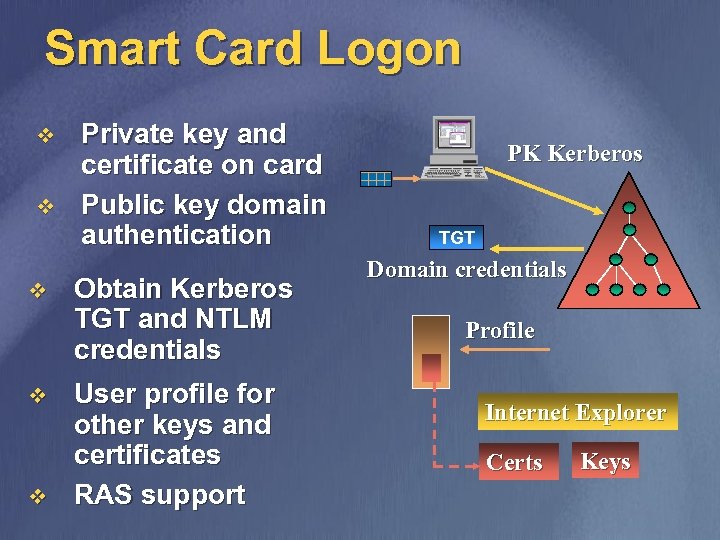
Smart Card Logon v v v Private key and certificate on card Public key domain authentication Obtain Kerberos TGT and NTLM credentials User profile for other keys and certificates RAS support PK Kerberos TGT Domain credentials Profile Internet Explorer Certs Keys

Management Of Trust v Trust policy decisions n n v Trust determination made locally n v What CAs are trusted? What are they trusted for? Ø Client Authentication, Ø Server Authentication, Ø Authenticode Certificate path verification Configure trust policy centrally n Define trust policy in Policy Editor Ø Signed by an authorized user

Encrypting File System v Privacy of data that goes beyond access control n n v Integrated with core operating system components n n n v Protect confidential data on laptops Configurable approach to data recovery Windows NT File System - NTFS Crypto API key management LSA security policy Transparent and very high performance
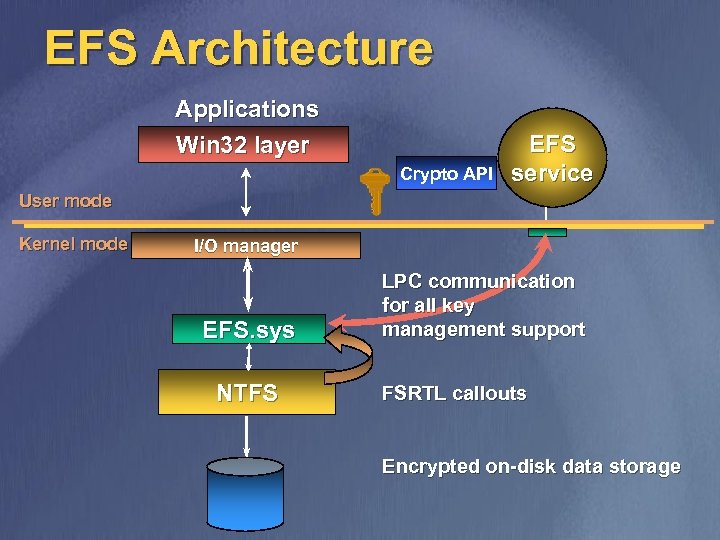
EFS Architecture Applications Win 32 layer Crypto API EFS service User mode Kernel mode I/O manager EFS. sys NTFS LPC communication for all key management support FSRTL callouts Encrypted on-disk data storage
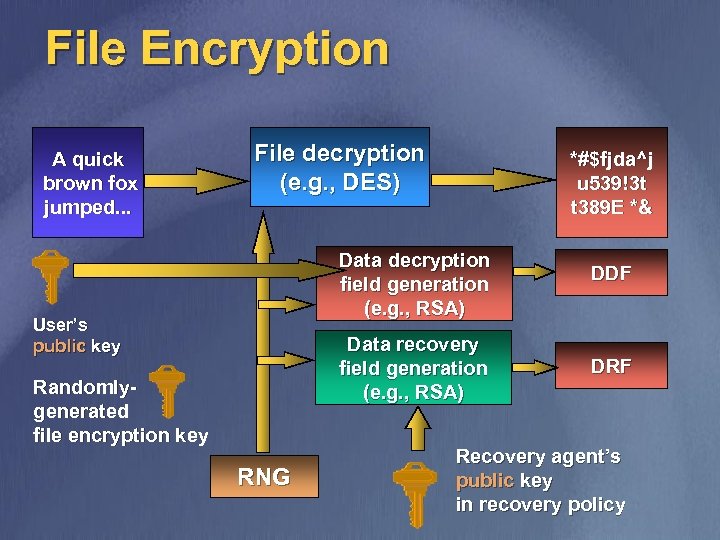
File Encryption A quick brown fox jumped. . . File decryption (e. g. , DES) *#$fjda^j u 539!3 t t 389 E *& Data decryption field generation (e. g. , RSA) User’s public key Data recovery field generation (e. g. , RSA) Randomlygenerated file encryption key RNG DDF DRF Recovery agent’s public key in recovery policy
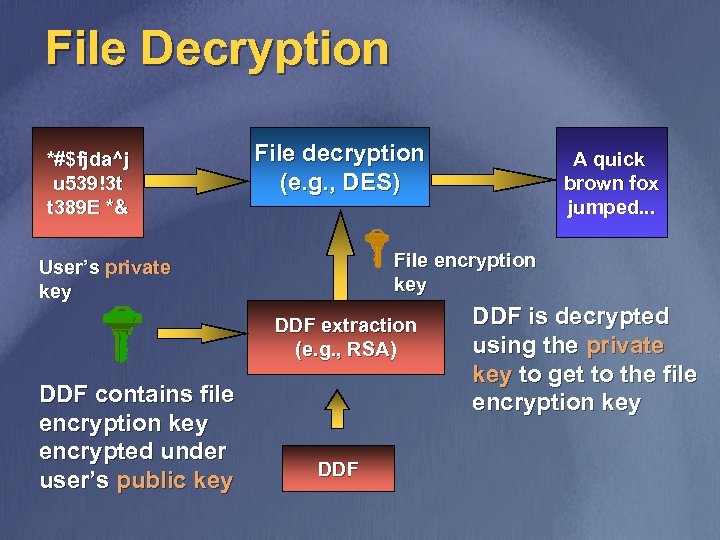
File Decryption *#$fjda^j u 539!3 t t 389 E *& File decryption (e. g. , DES) File encryption key User’s private key DDF extraction (e. g. , RSA) DDF contains file encryption key encrypted under user’s public key A quick brown fox jumped. . . DDF is decrypted using the private key to get to the file encryption key

Active Directory Security Features v Organization Units (OU) to organize the directory name space n v Directory object security n n v Users, groups, computers in separate containers Per property access control Per property auditing Delegation of administration n Who can create, manage users, groups, computer accounts, other objects
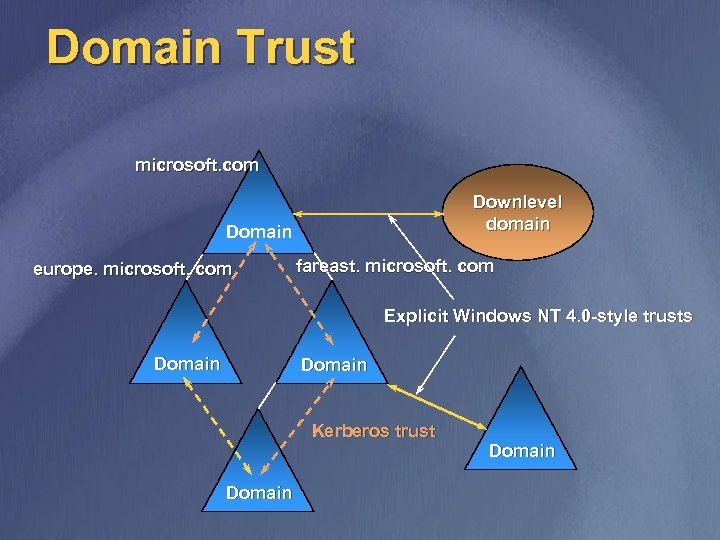
Domain Trust microsoft. com Downlevel domain Domain europe. microsoft. com fareast. microsoft. com Explicit Windows NT 4. 0 -style trusts Domain Kerberos trust Domain

Managing Security v Security Configuration Editor (SCE) n v Group Policy Editor n v Defines security configuration templates Defines hierarchy of user or computer policy templates for OUs up to the Domain Security configuration is part of Group Policy n n Group Policy for a computer includes the security configuration Security configuration applied at startup

A Security Configuration v Covers various security areas n n n Account Policies -- password, lockout, kerberos Local Policies -- auditing, user rights, . . . Restricted Groups -- Administrators, Power Users, … Registry & File System -- security descriptors Services -- startup mode and security descriptors

Summary (1/2) v Kerberos for domain authentication for the Enterprise n v Public key security components n n n v Mutual authentication, transitive trust Certificate Services to issue organization certificates Personal key and certificate management Public key credentials for servers Directory-based SSL/TLS client authentication using X. 509 certificates

Summary v v v v Crypto API enhancements Smart card logon and dialup access Message encryption using SSPI SMB data encryption using IPsec Encrypting File System DS Security Administration and Policy Security Configuration Editor Cross-platform authentication interoperability

Group Policy Objects

Group Policy Definition v “The ability for the administrator to state a wish about the state of their users’ environment once, and then rely on the system to enforce that wish!”

Group Policy Review v Policies Are Not Profiles n n v A profile is a collection of user environment settings that the user may change Group Policy is a collection of user environment settings, specified by the administrator Group Policy is more than simple “lockdown” n Group Policy enhances the “Follow Me!” experience by enabling organizations to: n Set registry settings securely and without fear of tattooing (Administrative Templates) n Specify security oriented settings (Security Settings) n Install software (Software Installation) n Re-direct “My Documents, ” “Desktop, ” etc. to the network (Folder redirection) n Implement tiered scripts (Scripts)
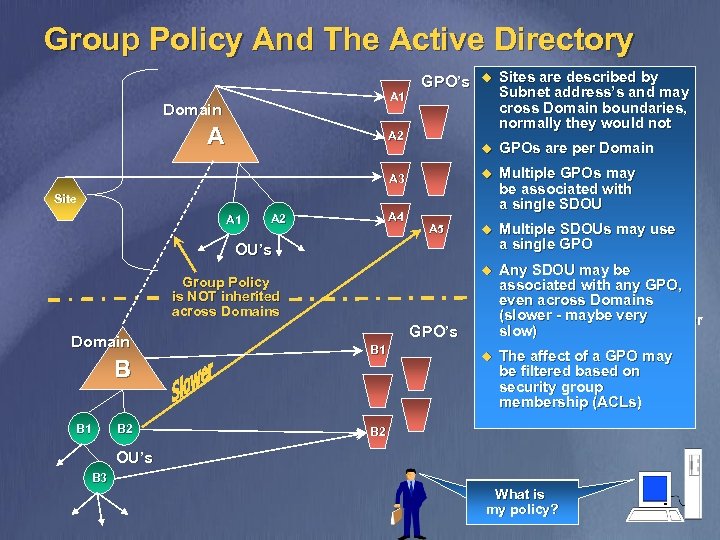
Group Policy And The Active Directory A 1 Domain A GPO’s A 2 u Sites are described by Subnet address’s and may cross Domain boundaries, normally they would not u GPOs are per Domain u u A 3 A 4 A 2 be associated with a single SDOU A 5 OU’s B B 2 B 1 a single SDOU Multiple SDOUs may use u a single GPO Multiple SDOUs may use u GPO’s B 1 a single GPO Any SDOU may be associated with any GPO, u Any SDOU may be even across Domains associated with any GPO, (slower - maybe very even across Domains (slower slow) - maybe very slow) u Group Policy is NOT inherited across Domain Multiple GPOs may u be associated with Multiple GPOs may Site A 1 GPOs are per Domain u The affect of a GPO may u be filtered based on The affect of a GPO may be filtered based on security group membership (ACLs) B 2 OU’s B 3 What is my policy?

Group Policy Linked To OUs v v v The OU structure is your administrative structure Group Policy configuration must be tuned to fit your OUs structure Design for the most stable and maintainable solution

Filtering v Security Groups may be used to filter the effect of Group Policy n v v Any Group Policy may have it’s scope modified by setting ACL permissions Read and Apply Group Policy (AGP) ACEs are required for Group Policy to be applied Only filter if necessary n Keep simple if possible
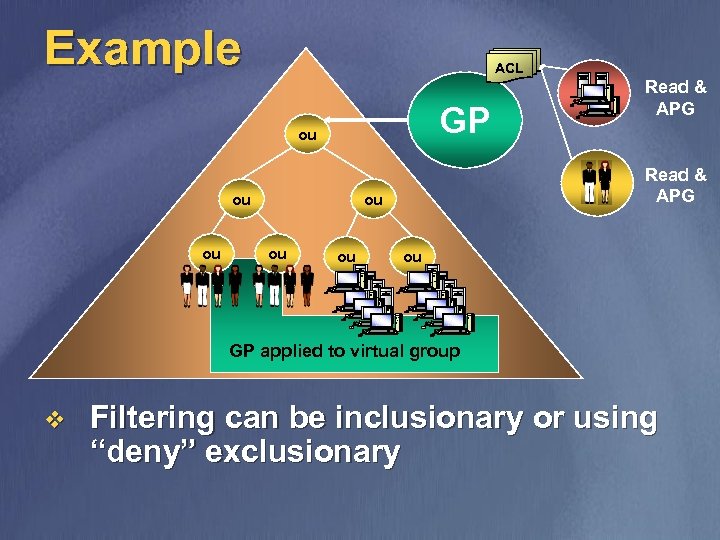
Example ACL GP ou ou ou Read & APG ou GP applied to virtual group v Filtering can be inclusionary or using “deny” exclusionary

Conclusion v v Active Directory DNS Security Features Group Policy

b8a0455ea43c861f91a8c7aade428fc6.ppt