2e74eed773034edf2acd51899a0da374.ppt
- Количество слайдов: 18
![Why Security? A Commitment for [the Agency’s] Executives [CIO’s name] EC Presentation [date] Why Security? A Commitment for [the Agency’s] Executives [CIO’s name] EC Presentation [date]](https://present5.com/presentation/2e74eed773034edf2acd51899a0da374/image-1.jpg) Why Security? A Commitment for [the Agency’s] Executives [CIO’s name] EC Presentation [date]
Why Security? A Commitment for [the Agency’s] Executives [CIO’s name] EC Presentation [date]
![[the Agency] Today v [the Agency’s] mission and vision v The way we do [the Agency] Today v [the Agency’s] mission and vision v The way we do](https://present5.com/presentation/2e74eed773034edf2acd51899a0da374/image-2.jpg) [the Agency] Today v [the Agency’s] mission and vision v The way we do business is changing v Increased reliance on systems and technology v Increased threats to information and systems 2
[the Agency] Today v [the Agency’s] mission and vision v The way we do business is changing v Increased reliance on systems and technology v Increased threats to information and systems 2
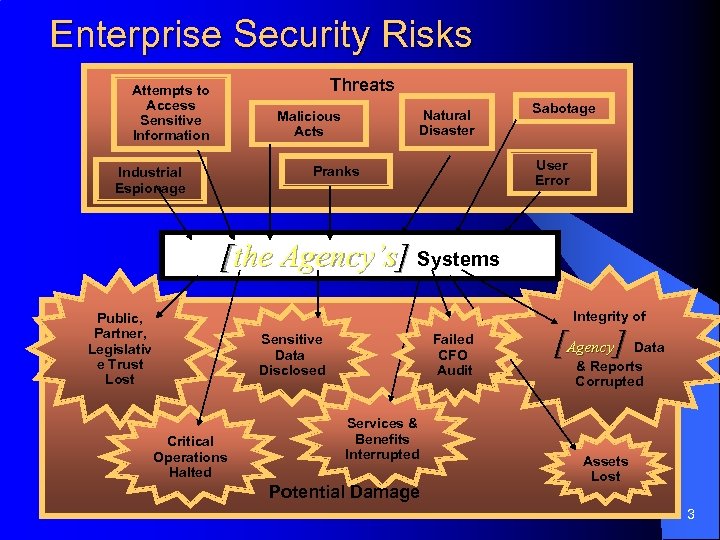 Enterprise Security Risks Threats Attempts to Access Sensitive Information Natural Disaster Malicious Acts User Error Pranks Industrial Espionage Sabotage [the Agency’s] Systems Integrity of Public, Partner, Legislativ e Trust Lost Sensitive Data Disclosed Critical Operations Halted Failed CFO Audit Services & Benefits Interrupted Potential Damage [Agency] Data & Reports Corrupted Assets Lost 3
Enterprise Security Risks Threats Attempts to Access Sensitive Information Natural Disaster Malicious Acts User Error Pranks Industrial Espionage Sabotage [the Agency’s] Systems Integrity of Public, Partner, Legislativ e Trust Lost Sensitive Data Disclosed Critical Operations Halted Failed CFO Audit Services & Benefits Interrupted Potential Damage [Agency] Data & Reports Corrupted Assets Lost 3
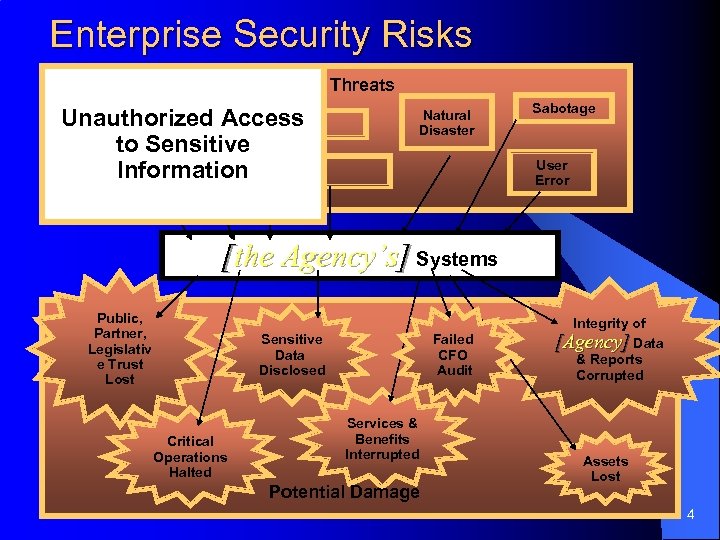 Enterprise Security Risks Threats Unauthorized Access to Sensitive Information Natural Disaster Sabotage User Error [the Agency’s] Systems Public, Partner, Legislativ e Trust Lost Sensitive Data Disclosed Critical Operations Halted Failed CFO Audit Services & Benefits Interrupted Potential Damage Integrity of [Agency] Data & Reports Corrupted Assets Lost 4
Enterprise Security Risks Threats Unauthorized Access to Sensitive Information Natural Disaster Sabotage User Error [the Agency’s] Systems Public, Partner, Legislativ e Trust Lost Sensitive Data Disclosed Critical Operations Halted Failed CFO Audit Services & Benefits Interrupted Potential Damage Integrity of [Agency] Data & Reports Corrupted Assets Lost 4
![Enterprise Security Risks Threats Natural Disaster Industrial Espionage Sabotage User Error [the Agency’s] Systems Enterprise Security Risks Threats Natural Disaster Industrial Espionage Sabotage User Error [the Agency’s] Systems](https://present5.com/presentation/2e74eed773034edf2acd51899a0da374/image-5.jpg) Enterprise Security Risks Threats Natural Disaster Industrial Espionage Sabotage User Error [the Agency’s] Systems Public, Partner, Legislativ e Trust Lost Sensitive Data Disclosed Critical Operations Halted Failed CFO Audit Services & Benefits Interrupted Potential Damage Integrity of [Agency] Data & Reports Corrupted Assets Lost 5
Enterprise Security Risks Threats Natural Disaster Industrial Espionage Sabotage User Error [the Agency’s] Systems Public, Partner, Legislativ e Trust Lost Sensitive Data Disclosed Critical Operations Halted Failed CFO Audit Services & Benefits Interrupted Potential Damage Integrity of [Agency] Data & Reports Corrupted Assets Lost 5
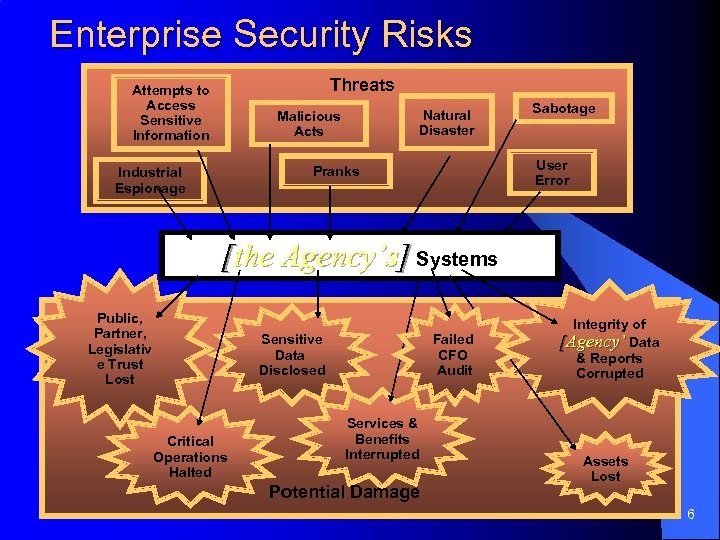 Enterprise Security Risks Threats Attempts to Access Sensitive Information Natural Disaster Malicious Acts User Error Pranks Industrial Espionage Sabotage [the Agency’s] Systems Public, Partner, Legislativ e Trust Lost Sensitive Data Disclosed Critical Operations Halted Failed CFO Audit Services & Benefits Interrupted Potential Damage Integrity of [Agency’ Data & Reports Corrupted Assets Lost 6
Enterprise Security Risks Threats Attempts to Access Sensitive Information Natural Disaster Malicious Acts User Error Pranks Industrial Espionage Sabotage [the Agency’s] Systems Public, Partner, Legislativ e Trust Lost Sensitive Data Disclosed Critical Operations Halted Failed CFO Audit Services & Benefits Interrupted Potential Damage Integrity of [Agency’ Data & Reports Corrupted Assets Lost 6
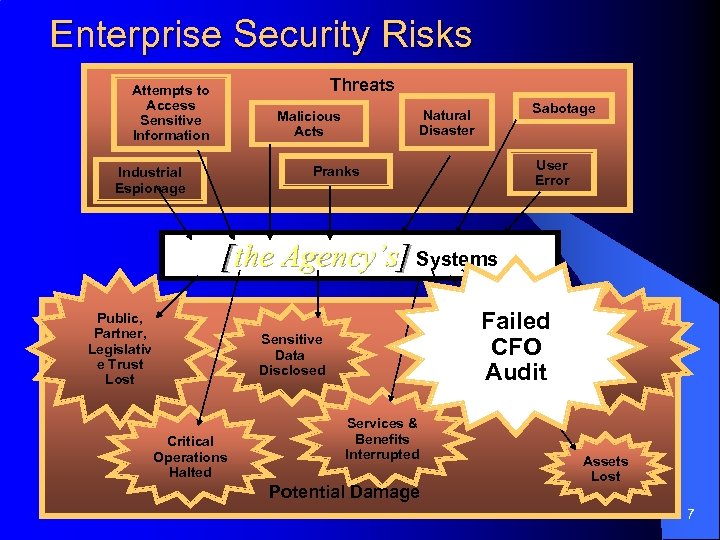 Enterprise Security Risks Threats Attempts to Access Sensitive Information Sabotage Natural Disaster Malicious Acts User Error Pranks Industrial Espionage [the Agency’s] Systems Public, Partner, Legislativ e Trust Lost Failed CFO Audit Sensitive Data Disclosed Critical Operations Halted Services & Benefits Interrupted Potential Damage Assets Lost 7
Enterprise Security Risks Threats Attempts to Access Sensitive Information Sabotage Natural Disaster Malicious Acts User Error Pranks Industrial Espionage [the Agency’s] Systems Public, Partner, Legislativ e Trust Lost Failed CFO Audit Sensitive Data Disclosed Critical Operations Halted Services & Benefits Interrupted Potential Damage Assets Lost 7
![Why is Security Important to [the Agency’s] ? v Protect privacy information v Protect Why is Security Important to [the Agency’s] ? v Protect privacy information v Protect](https://present5.com/presentation/2e74eed773034edf2acd51899a0da374/image-8.jpg) Why is Security Important to [the Agency’s] ? v Protect privacy information v Protect processes and corporate assets v Provide continuity of services v Provide accessibility of information It is a prudent business practice to reduce risks to [the Agency’s] 8
Why is Security Important to [the Agency’s] ? v Protect privacy information v Protect processes and corporate assets v Provide continuity of services v Provide accessibility of information It is a prudent business practice to reduce risks to [the Agency’s] 8
 Why is Security Important to US? Each One Of Us Is Accountable! 9
Why is Security Important to US? Each One Of Us Is Accountable! 9
 Laws and Regulations v Computer Security Act of 1987 v Privacy Act of 1974 v Freedom of Information Act v Presidential Decision Directive (PDD) 63 v OMB A-130, Appendix III, Revised v Health Insurance Portability and Accountability Act v FISMA of 2002 10
Laws and Regulations v Computer Security Act of 1987 v Privacy Act of 1974 v Freedom of Information Act v Presidential Decision Directive (PDD) 63 v OMB A-130, Appendix III, Revised v Health Insurance Portability and Accountability Act v FISMA of 2002 10
 Audit’s Point of Weaknesses v General Accounting Office v Internal Revenue Service v Office of the Inspector General v Chief Financial Officer v Office of Information Services 11
Audit’s Point of Weaknesses v General Accounting Office v Internal Revenue Service v Office of the Inspector General v Chief Financial Officer v Office of Information Services 11
![[the Agency’s] Enterprise Security Program Policy, Training, Engineering, and Management Oversight for all [the [the Agency’s] Enterprise Security Program Policy, Training, Engineering, and Management Oversight for all [the](https://present5.com/presentation/2e74eed773034edf2acd51899a0da374/image-12.jpg) [the Agency’s] Enterprise Security Program Policy, Training, Engineering, and Management Oversight for all [the Agency’s] employees, contractors, and agents
[the Agency’s] Enterprise Security Program Policy, Training, Engineering, and Management Oversight for all [the Agency’s] employees, contractors, and agents
 Security Program Elements v Personnel and Physical Security v Security Awareness, Training, & Education v Remote Access Security v Audit Systems v Business Contingency Planning v Risk Management v Workstation Security v Integrating Security into the v LAN Security SDLC v Security Determinations and Requirements v Security Plans & Certification v Systems Access Security v Acquisitions & Contracts v Security Incidents v E-Mail & Facsimile Security v Internet / Intranet Security v Virus Prevention, Detection, & Reporting v Medicare Contractor Oversight 13
Security Program Elements v Personnel and Physical Security v Security Awareness, Training, & Education v Remote Access Security v Audit Systems v Business Contingency Planning v Risk Management v Workstation Security v Integrating Security into the v LAN Security SDLC v Security Determinations and Requirements v Security Plans & Certification v Systems Access Security v Acquisitions & Contracts v Security Incidents v E-Mail & Facsimile Security v Internet / Intranet Security v Virus Prevention, Detection, & Reporting v Medicare Contractor Oversight 13
 Current Enterprise Security Initiatives v GPRA Goal of Zero Material Weaknesses for the Year 2000 and Beyond v [the Agency’s] Enterprise Security Handbook v Information Technology Architecture w IT Council Security Committee v HIPAA Compliance 14
Current Enterprise Security Initiatives v GPRA Goal of Zero Material Weaknesses for the Year 2000 and Beyond v [the Agency’s] Enterprise Security Handbook v Information Technology Architecture w IT Council Security Committee v HIPAA Compliance 14
 Immediate Next Steps v Designation of Information Systems Security Officers v Re-certification of User Access Privileges v Corrective Action Plans to Audit Findings v [the Agency’s] Contractor Oversight v Security Awareness and Training 15
Immediate Next Steps v Designation of Information Systems Security Officers v Re-certification of User Access Privileges v Corrective Action Plans to Audit Findings v [the Agency’s] Contractor Oversight v Security Awareness and Training 15
![Summary v Recognize that security risks in [the Agency’s] environment impact [the Agency’s] Mission. Summary v Recognize that security risks in [the Agency’s] environment impact [the Agency’s] Mission.](https://present5.com/presentation/2e74eed773034edf2acd51899a0da374/image-16.jpg) Summary v Recognize that security risks in [the Agency’s] environment impact [the Agency’s] Mission. v Security is a management responsibility. v Security is everybody’s business. 16
Summary v Recognize that security risks in [the Agency’s] environment impact [the Agency’s] Mission. v Security is a management responsibility. v Security is everybody’s business. 16
![We ask you to: v Encourage and support [the Agency’s] security initiative activities! v We ask you to: v Encourage and support [the Agency’s] security initiative activities! v](https://present5.com/presentation/2e74eed773034edf2acd51899a0da374/image-17.jpg) We ask you to: v Encourage and support [the Agency’s] security initiative activities! v Lead by example! v Be proactive! 17
We ask you to: v Encourage and support [the Agency’s] security initiative activities! v Lead by example! v Be proactive! 17
 Thank You
Thank You


