284e102375dbb2ecc86b89bf9bd9f12d.ppt
- Количество слайдов: 37
 Who’s watching your network DNS Security Extensions Presentation to 19 th NANOG meeting Albuquerque, NM Edward Lewis lewis@tislabs. com NAI Labs June 11 -13, 2000
Who’s watching your network DNS Security Extensions Presentation to 19 th NANOG meeting Albuquerque, NM Edward Lewis lewis@tislabs. com NAI Labs June 11 -13, 2000
 Who’s watching your network Changes are coming to DNS • DNS is undergoing a number of changes – DNSSEC - my topic – Dynamic Update • RFC 2136 (see bibliography for URL) – IPv 6 - new A 6 records and reverse map • http: //www. ietf. org/internet-drafts/draft-ietf-ipngwgdns-lookups-08. txt – Various other improvements • EDNS 0 - ftp: //ftp. isi. edu/in-notes/rfc 2671. txt • Software boosts #2 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network Changes are coming to DNS • DNS is undergoing a number of changes – DNSSEC - my topic – Dynamic Update • RFC 2136 (see bibliography for URL) – IPv 6 - new A 6 records and reverse map • http: //www. ietf. org/internet-drafts/draft-ietf-ipngwgdns-lookups-08. txt – Various other improvements • EDNS 0 - ftp: //ftp. isi. edu/in-notes/rfc 2671. txt • Software boosts #2 11 -13 June 2000 lewis@tislabs. com
 Who’s watching your network DNSSEC Ingredients • DNS Security Extensions – KEY and SIG resource records – NXT resource records • Query-Response Security – TSIG and SIG(0) meta records – TKEY meta record • Serving Security Data – CERT(ificate) resource record • Dynamic Update Security – Update authorization #3 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network DNSSEC Ingredients • DNS Security Extensions – KEY and SIG resource records – NXT resource records • Query-Response Security – TSIG and SIG(0) meta records – TKEY meta record • Serving Security Data – CERT(ificate) resource record • Dynamic Update Security – Update authorization #3 11 -13 June 2000 lewis@tislabs. com
 Who’s watching your network Features • Protection of Internet-scale DNS data transfers – Data is signed using scaleable public keys – Absent data notices (e. g. NXDOMAIN) secured • Protection of local DNS transfers – Entire message secured (header and data) • Public Key Infrastructure – Look up keys instead of trusting “what is heard” or manually entered • Secured dynamic updates to zones – Authorized changes to zone data can be made #4 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network Features • Protection of Internet-scale DNS data transfers – Data is signed using scaleable public keys – Absent data notices (e. g. NXDOMAIN) secured • Protection of local DNS transfers – Entire message secured (header and data) • Public Key Infrastructure – Look up keys instead of trusting “what is heard” or manually entered • Secured dynamic updates to zones – Authorized changes to zone data can be made #4 11 -13 June 2000 lewis@tislabs. com
 Who’s watching your network Specification, Software Status • DNSSEC is defined in RFC 2535 & others – IETF proposed standard (proposed, draft, full) – See bibliography for more docs • Internet Software Consortium’s BIND – Version 8. 2 (March 1999) was the beginning • Not a full implementation of DNSSEC • Current version 8. 2. 2 -P 5 – Third Beta of Version 9 has been released • Partial build of what will be the first full implementation of DNSSEC #5 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network Specification, Software Status • DNSSEC is defined in RFC 2535 & others – IETF proposed standard (proposed, draft, full) – See bibliography for more docs • Internet Software Consortium’s BIND – Version 8. 2 (March 1999) was the beginning • Not a full implementation of DNSSEC • Current version 8. 2. 2 -P 5 – Third Beta of Version 9 has been released • Partial build of what will be the first full implementation of DNSSEC #5 11 -13 June 2000 lewis@tislabs. com
 Who’s watching your network State of the Protocol • Work is progressing to refine protocol – IETF WG on DNS Extensions (DNSEXT) – Much work remains to progress to "Full Standard" – Internet Drafts document the work in progress • Operational experience is very limited – IETF WG on DNS Operations (DNSOP) – Three workshops have been held with BINDv 8 – “How to operate” and “policy” questions abound #6 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network State of the Protocol • Work is progressing to refine protocol – IETF WG on DNS Extensions (DNSEXT) – Much work remains to progress to "Full Standard" – Internet Drafts document the work in progress • Operational experience is very limited – IETF WG on DNS Operations (DNSOP) – Three workshops have been held with BINDv 8 – “How to operate” and “policy” questions abound #6 11 -13 June 2000 lewis@tislabs. com
 Who’s watching your network Deployment Plans • Major push in Europe – Three cc. TLD's plan to have signed zones by first quarter next year, one as soon as 1/1/2001 – CENTR has a DNSSEC WG in action • Root Servers – Looking into adoption, sooner rather than later – Need BIND 9 to be out & stable first • U. S. – Nothing firm, just some "interest" • Deployment experience is needed to evaluate the current protocol definition #7 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network Deployment Plans • Major push in Europe – Three cc. TLD's plan to have signed zones by first quarter next year, one as soon as 1/1/2001 – CENTR has a DNSSEC WG in action • Root Servers – Looking into adoption, sooner rather than later – Need BIND 9 to be out & stable first • U. S. – Nothing firm, just some "interest" • Deployment experience is needed to evaluate the current protocol definition #7 11 -13 June 2000 lewis@tislabs. com
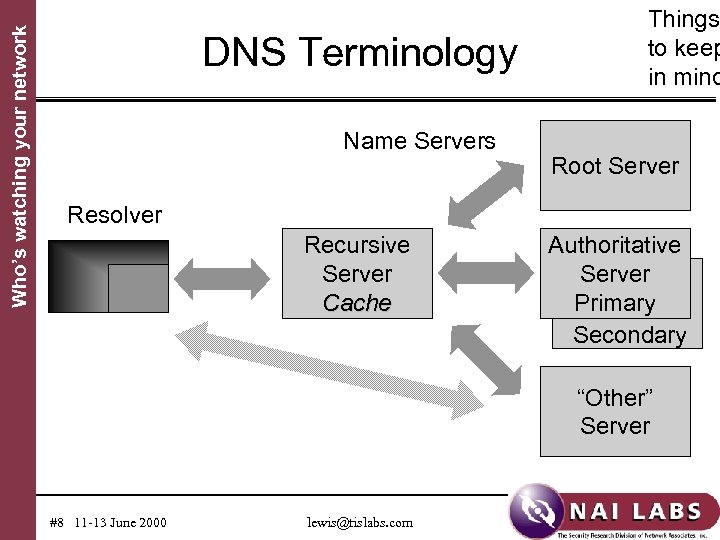 Who’s watching your network DNS Terminology Name Servers Things to keep in mind Root Server Resolver Recursive Server Cache Authoritative Server Primary Secondary “Other” Server #8 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network DNS Terminology Name Servers Things to keep in mind Root Server Resolver Recursive Server Cache Authoritative Server Primary Secondary “Other” Server #8 11 -13 June 2000 lewis@tislabs. com
 Who’s watching your network DNS RRs and RR sets Things to keep in mind •
Who’s watching your network DNS RRs and RR sets Things to keep in mind •
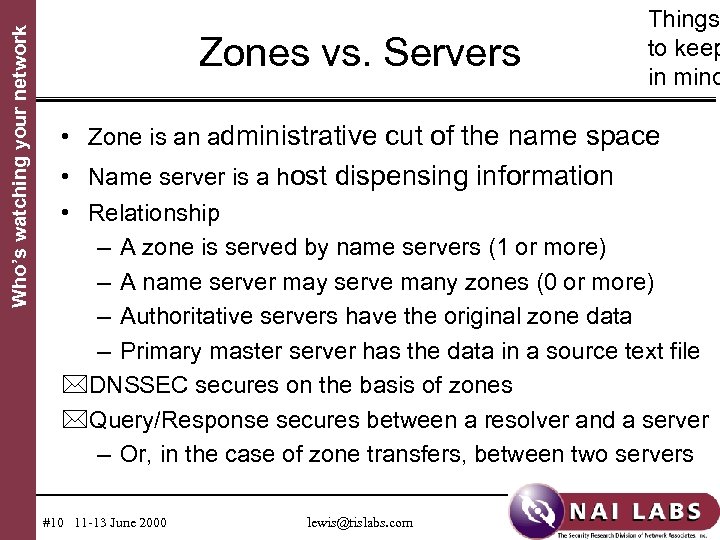 Who’s watching your network Zones vs. Servers Things to keep in mind • Zone is an administrative cut of the name space • Name server is a host dispensing information • Relationship – A zone is served by name servers (1 or more) – A name server may serve many zones (0 or more) – Authoritative servers have the original zone data – Primary master server has the data in a source text file *DNSSEC secures on the basis of zones *Query/Response secures between a resolver and a server – Or, in the case of zone transfers, between two servers #10 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network Zones vs. Servers Things to keep in mind • Zone is an administrative cut of the name space • Name server is a host dispensing information • Relationship – A zone is served by name servers (1 or more) – A name server may serve many zones (0 or more) – Authoritative servers have the original zone data – Primary master server has the data in a source text file *DNSSEC secures on the basis of zones *Query/Response secures between a resolver and a server – Or, in the case of zone transfers, between two servers #10 11 -13 June 2000 lewis@tislabs. com
 Who’s watching your network Cryptography Things to keep in mind • Symmetric keys (aka shared secret) – One key, encrypts and decrypts/signs and verifies – Problem: distributing the secretly, storing the secretly • Asymmetric keys (aka public key) – Pair of keys, one encrypts/signs, other decrypts/verifies – Problem: slower than symmetric • Optimization – Use asymmetric keys to agree upon a symmetric key • Other issues: patents and export control #11 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network Cryptography Things to keep in mind • Symmetric keys (aka shared secret) – One key, encrypts and decrypts/signs and verifies – Problem: distributing the secretly, storing the secretly • Asymmetric keys (aka public key) – Pair of keys, one encrypts/signs, other decrypts/verifies – Problem: slower than symmetric • Optimization – Use asymmetric keys to agree upon a symmetric key • Other issues: patents and export control #11 11 -13 June 2000 lewis@tislabs. com
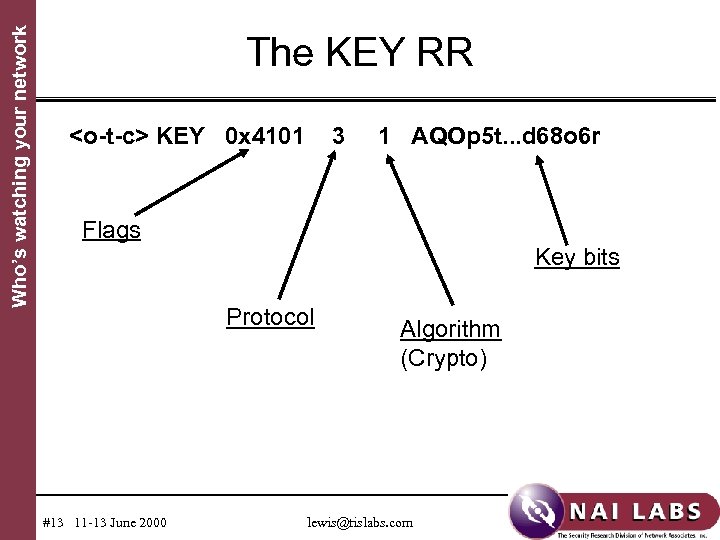
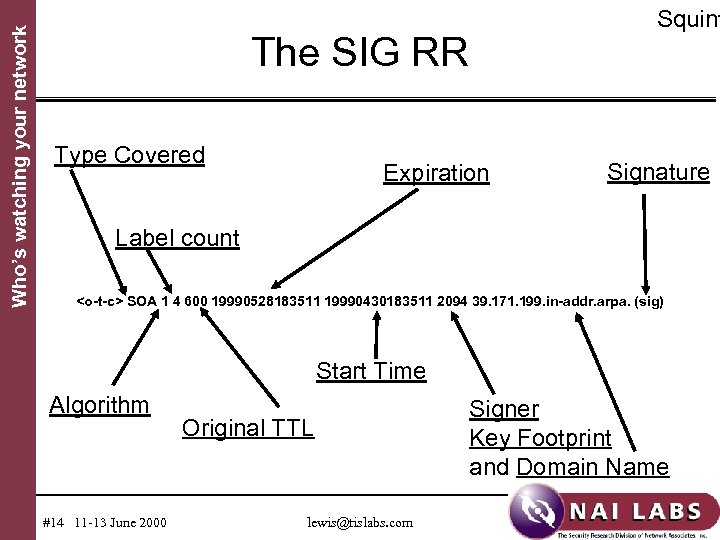
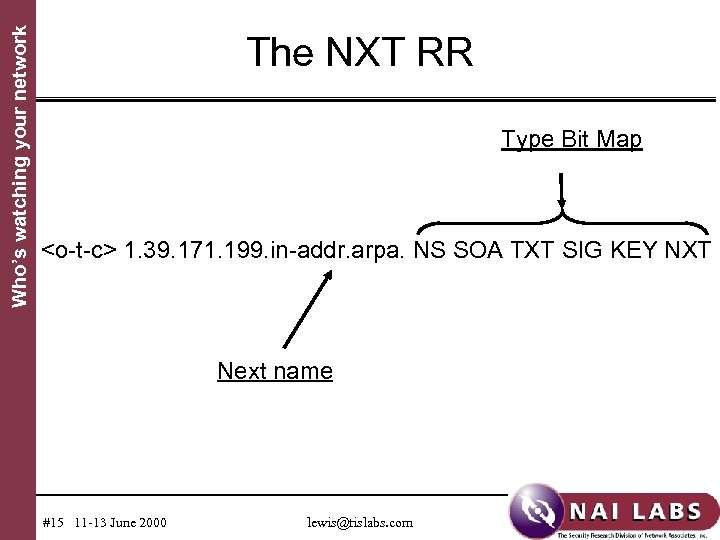
 Who’s watching your network DNS Security Extensions Start of "detail s" • Protecting data transfers in which scalability is critical – I. e. , inter-server queries • Resource records introduced – SIG holds a digital signature (asym. keys) – KEY holds a public key – NXT indicates data present and next name #12 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network DNS Security Extensions Start of "detail s" • Protecting data transfers in which scalability is critical – I. e. , inter-server queries • Resource records introduced – SIG holds a digital signature (asym. keys) – KEY holds a public key – NXT indicates data present and next name #12 11 -13 June 2000 lewis@tislabs. com
 Who’s watching your network The KEY RR
Who’s watching your network The KEY RR
 Who’s watching your network Squint The SIG RR Type Covered Expiration Signature Label count
Who’s watching your network Squint The SIG RR Type Covered Expiration Signature Label count
 Who’s watching your network The NXT RR Type Bit Map
Who’s watching your network The NXT RR Type Bit Map
 Who’s watching your network A quirk of NXT • The NXT record indicates the data sets present at the owner's name • It also indicates the next name in the zone • There is one NXT for most names, but delegation names have two – A delegation name appears both above and below the cut point – One NXT belongs to the "upper" zone – The other to the "lower" zone • NXT's are not generally "loved" #16 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network A quirk of NXT • The NXT record indicates the data sets present at the owner's name • It also indicates the next name in the zone • There is one NXT for most names, but delegation names have two – A delegation name appears both above and below the cut point – One NXT belongs to the "upper" zone – The other to the "lower" zone • NXT's are not generally "loved" #16 11 -13 June 2000 lewis@tislabs. com
 Who’s watching your network A signed zone, page 1 • This example shows the KEY, SIG, and NXT RRs ; Generated by dns_signer dated October 18, 1999 $ORIGIN tise. cairn. net. @ 14400 IN SOA test. netsec. tislabs. com. lewis. tislabs. com. 2000020701 1 D 1 H 1 W 4 H 14400 IN SIG SOA 3 3 14400 20000306184745 20000207184745 48320 tise. cairn. net. ( AIr. F 9 Hb/Bzo. Z 3 xir 1 K 81 x. Lzpr. IEVBFZLEE 6 Sqy 8 Hla. U 5 r 3 ux Vf. Bbc. TA= ) 14400 IN KEY 0 x 4100 3 3 ( ALb/q. ZQ/o. VHyotu. Sb. BWI 1 N+OYw. RLv 5 RMc 7 XXb 0 w. YE/t. Y 02 q. F Uf+9 cz. S 0 B 7 p. U 2 j. Ypp. F 7 Rw. L 8 b/Oc. WG 3 i. Azaztzq 6 S 0 Zo. QIh 8 J M 5 Lummz. Ji. Nl 3 aqx. Dx. UZH 6 pwm. PNui. Mb. Gl++2 t. Uks+MAallp. Uz 4 t. EJPe. BF+Zj 8 bo. Yw. Wh. QDa. V 6 nw. DY 6 k. Irq. Rqhv. Am. OZHqtqz. FT 6 Sd. A 07 us. EZEz. Zk. XXS 6 PIg 6 Jc. N 7 m. Nh. Ua 0 qk. DSNTIkr. HWNCh++G 56 dt. KNxk 4 qn 3 ESreg/S 2 BRGWQ 2/7 X 0 Pj. My. Bk. Defvd. Isw ) 14400 IN SIG KEY 3 3 14400 20000225145656 20000128145656 48320 tise. cairn. net. ( AKM 6 fd. Jmc. V 3 Wec 7 s. YKR 5 kt. X 2 C 3 k. WTLTc. ITD 4 i. BP 2 r. JVSF 1 Kx nsi 3 b. RI= ) . . . continues on next slide. . . #17 11 -13 June 2000 lewis@tislabs. com Squint
Who’s watching your network A signed zone, page 1 • This example shows the KEY, SIG, and NXT RRs ; Generated by dns_signer dated October 18, 1999 $ORIGIN tise. cairn. net. @ 14400 IN SOA test. netsec. tislabs. com. lewis. tislabs. com. 2000020701 1 D 1 H 1 W 4 H 14400 IN SIG SOA 3 3 14400 20000306184745 20000207184745 48320 tise. cairn. net. ( AIr. F 9 Hb/Bzo. Z 3 xir 1 K 81 x. Lzpr. IEVBFZLEE 6 Sqy 8 Hla. U 5 r 3 ux Vf. Bbc. TA= ) 14400 IN KEY 0 x 4100 3 3 ( ALb/q. ZQ/o. VHyotu. Sb. BWI 1 N+OYw. RLv 5 RMc 7 XXb 0 w. YE/t. Y 02 q. F Uf+9 cz. S 0 B 7 p. U 2 j. Ypp. F 7 Rw. L 8 b/Oc. WG 3 i. Azaztzq 6 S 0 Zo. QIh 8 J M 5 Lummz. Ji. Nl 3 aqx. Dx. UZH 6 pwm. PNui. Mb. Gl++2 t. Uks+MAallp. Uz 4 t. EJPe. BF+Zj 8 bo. Yw. Wh. QDa. V 6 nw. DY 6 k. Irq. Rqhv. Am. OZHqtqz. FT 6 Sd. A 07 us. EZEz. Zk. XXS 6 PIg 6 Jc. N 7 m. Nh. Ua 0 qk. DSNTIkr. HWNCh++G 56 dt. KNxk 4 qn 3 ESreg/S 2 BRGWQ 2/7 X 0 Pj. My. Bk. Defvd. Isw ) 14400 IN SIG KEY 3 3 14400 20000225145656 20000128145656 48320 tise. cairn. net. ( AKM 6 fd. Jmc. V 3 Wec 7 s. YKR 5 kt. X 2 C 3 k. WTLTc. ITD 4 i. BP 2 r. JVSF 1 Kx nsi 3 b. RI= ) . . . continues on next slide. . . #17 11 -13 June 2000 lewis@tislabs. com Squint
 Who’s watching your network A signed zone, page 2 @ 14400 IN NS buddy. netsec. tislabs. com. 14400 IN NS active. netsec. tislabs. com. 14400 IN NS test. netsec. tislabs. com. 14400 IN SIG NS 3 3 14400 20000225145656 20000128145656 48320 tise. cairn. net. ( AKqbf 3 k. RV 1 P 63 j. DVS 96 dq 9 d. MB/OXj. Lw 0 FDtd. Uuy. VIq 2 Q 3 Z 23 Ep 5835 k= ) 14400 IN NXT active. tise. cairn. net. NS SOA SIG KEY NXT 14400 IN SIG NXT 3 3 14400 20000225145656 20000128145656 48320 tise. cairn. net. ( AHZa. L 7 Bj. H 0 l 2 VULl. QJb 6 g. XIs. Xj. Rh. ICs. Wv. Map. Vf. P 2 q. Br. GMGYl 3 c 7 y. Ik 8= ) active 14400 IN CNAME active. netsec. tislabs. com. 14400 IN SIG CNAME 3 4 14400 20000225145656 20000128145656 48320 tise. cairn. net. ( ACqtg. IY 8 Tkw. Tw 83 r. Qmt 3 f 0 P 0 x+Tmpc. Ct. Cz 1+Es. Fm. Yybc. SY 0 lh. P 2 Nht 4= ) active 14400 IN NXT amp. tise. cairn. net. CNAME SIG NXT 14400 IN SIG NXT 3 4 14400 20000225145656 20000128145656 48320 tise. cairn. net. ( AC 75 id. Nr. Am 5 O 1 YUS 1 ZBD 9 ec. Dg. EDd. FWl. WN+et. N 74 Aq. Vo. Dlht. YW 8 dm. Weo= ) amp 14400 IN NS test. netsec. tislabs. com. 14400 IN NS active. netsec. tislabs. com. 14400 IN NS buddy. netsec. tislabs. com. amp 14400 IN NXT buddy. tise. cairn. net. NS SIG KEY NXT 14400 IN SIG NXT 3 4 14400 20000225145656 20000128145656 48320 tise. cairn. net. ( ADg 3 LFw 5 Gvc. FHg. C 7 Ua. CZr. K/rn 5 IVOg 8 dd. Tgk. Wz 9 PK 9 Z 1 Kv. To. Qb. NZ 3 NQ= ) . . and there's still more to the zone, not shown #18 11 -13 June 2000 lewis@tislabs. com Squint
Who’s watching your network A signed zone, page 2 @ 14400 IN NS buddy. netsec. tislabs. com. 14400 IN NS active. netsec. tislabs. com. 14400 IN NS test. netsec. tislabs. com. 14400 IN SIG NS 3 3 14400 20000225145656 20000128145656 48320 tise. cairn. net. ( AKqbf 3 k. RV 1 P 63 j. DVS 96 dq 9 d. MB/OXj. Lw 0 FDtd. Uuy. VIq 2 Q 3 Z 23 Ep 5835 k= ) 14400 IN NXT active. tise. cairn. net. NS SOA SIG KEY NXT 14400 IN SIG NXT 3 3 14400 20000225145656 20000128145656 48320 tise. cairn. net. ( AHZa. L 7 Bj. H 0 l 2 VULl. QJb 6 g. XIs. Xj. Rh. ICs. Wv. Map. Vf. P 2 q. Br. GMGYl 3 c 7 y. Ik 8= ) active 14400 IN CNAME active. netsec. tislabs. com. 14400 IN SIG CNAME 3 4 14400 20000225145656 20000128145656 48320 tise. cairn. net. ( ACqtg. IY 8 Tkw. Tw 83 r. Qmt 3 f 0 P 0 x+Tmpc. Ct. Cz 1+Es. Fm. Yybc. SY 0 lh. P 2 Nht 4= ) active 14400 IN NXT amp. tise. cairn. net. CNAME SIG NXT 14400 IN SIG NXT 3 4 14400 20000225145656 20000128145656 48320 tise. cairn. net. ( AC 75 id. Nr. Am 5 O 1 YUS 1 ZBD 9 ec. Dg. EDd. FWl. WN+et. N 74 Aq. Vo. Dlht. YW 8 dm. Weo= ) amp 14400 IN NS test. netsec. tislabs. com. 14400 IN NS active. netsec. tislabs. com. 14400 IN NS buddy. netsec. tislabs. com. amp 14400 IN NXT buddy. tise. cairn. net. NS SIG KEY NXT 14400 IN SIG NXT 3 4 14400 20000225145656 20000128145656 48320 tise. cairn. net. ( ADg 3 LFw 5 Gvc. FHg. C 7 Ua. CZr. K/rn 5 IVOg 8 dd. Tgk. Wz 9 PK 9 Z 1 Kv. To. Qb. NZ 3 NQ= ) . . and there's still more to the zone, not shown #18 11 -13 June 2000 lewis@tislabs. com Squint
 Who’s watching your network DNSSEC Queries Query. Response Security DNSSEC Security #19 11 -13 June 2000 lewis@tislabs. com Squint
Who’s watching your network DNSSEC Queries Query. Response Security DNSSEC Security #19 11 -13 June 2000 lewis@tislabs. com Squint
 Who’s watching your network Going secure • Preparation (not necessarily in order) – – A "secured" zone begins with an "unsecured" zone Zone key pair generated and validated by parent SIG records generated for each set in zone NXT and SIG(NXT) are generated and added • Running – Response to query includes the desired set(s), the SIG (set), and possibly KEY and SIG(KEY)'s that will help the resolver evaluate the answer – There are many variations on this, this is the general theme #20 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network Going secure • Preparation (not necessarily in order) – – A "secured" zone begins with an "unsecured" zone Zone key pair generated and validated by parent SIG records generated for each set in zone NXT and SIG(NXT) are generated and added • Running – Response to query includes the desired set(s), the SIG (set), and possibly KEY and SIG(KEY)'s that will help the resolver evaluate the answer – There are many variations on this, this is the general theme #20 11 -13 June 2000 lewis@tislabs. com
 Who’s watching your network Query/Response Security • Processing power is a greater issue than scalability – This includes lightweight resolver queries to a "preferred" server – Zone transfers (AXFR) – A basis for securing dynamic update • (Meta-) Resource records introduced – TSIG/SIG(0) – TKEY #21 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network Query/Response Security • Processing power is a greater issue than scalability – This includes lightweight resolver queries to a "preferred" server – Zone transfers (AXFR) – A basis for securing dynamic update • (Meta-) Resource records introduced – TSIG/SIG(0) – TKEY #21 11 -13 June 2000 lewis@tislabs. com
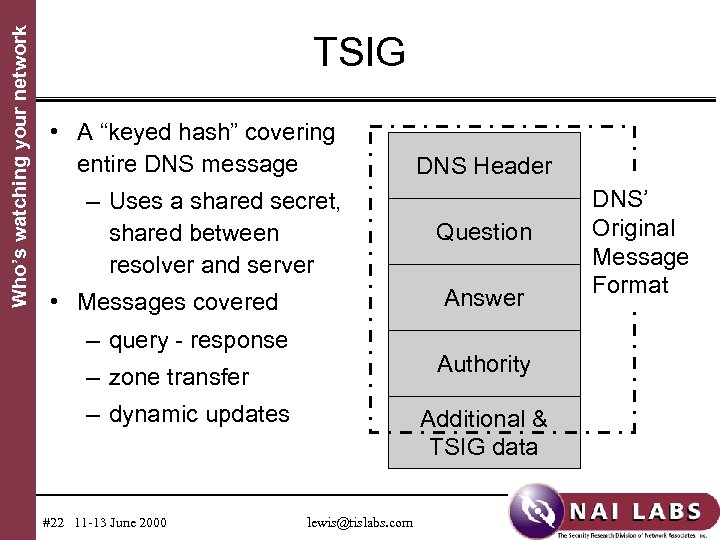 Who’s watching your network TSIG • A “keyed hash” covering entire DNS message – Uses a shared secret, shared between resolver and server Question Answer • Messages covered – query - response Authority – zone transfer – dynamic updates #22 11 -13 June 2000 DNS Header Additional & TSIG data lewis@tislabs. com DNS’ Original Message Format
Who’s watching your network TSIG • A “keyed hash” covering entire DNS message – Uses a shared secret, shared between resolver and server Question Answer • Messages covered – query - response Authority – zone transfer – dynamic updates #22 11 -13 June 2000 DNS Header Additional & TSIG data lewis@tislabs. com DNS’ Original Message Format
 Who’s watching your network TSIG Notes • Storage of shared secret is an issue – No problem for named. conf, it can be protected – Problem for resolv. conf – TKEY is a proposed method for creating TSIGs • Early use of TSIG – Zone transfers – “Special” clients (e. g. , DHCP updaters) • Widespread use later – Once overhead of sharing secrets is reduced #23 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network TSIG Notes • Storage of shared secret is an issue – No problem for named. conf, it can be protected – Problem for resolv. conf – TKEY is a proposed method for creating TSIGs • Early use of TSIG – Zone transfers – “Special” clients (e. g. , DHCP updaters) • Widespread use later – Once overhead of sharing secrets is reduced #23 11 -13 June 2000 lewis@tislabs. com
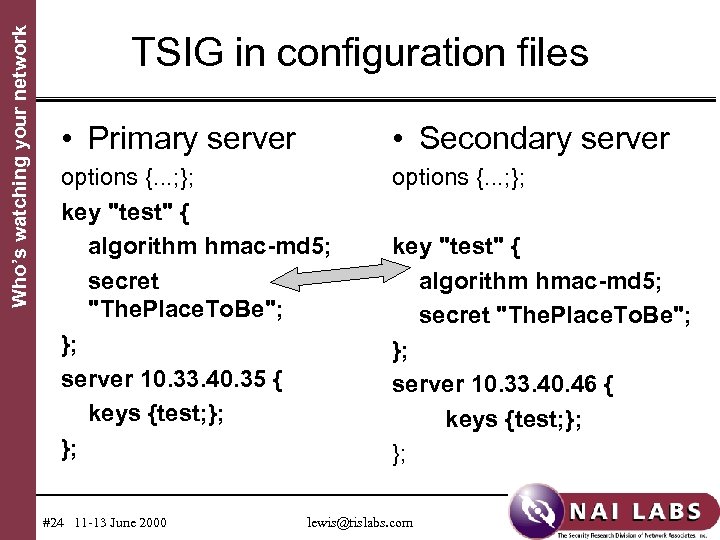 Who’s watching your network TSIG in configuration files • Primary server • Secondary server options {. . . ; }; key "test" { algorithm hmac-md 5; secret "The. Place. To. Be"; }; server 10. 33. 40. 35 { keys {test; }; }; options {. . . ; }; #24 11 -13 June 2000 key "test" { algorithm hmac-md 5; secret "The. Place. To. Be"; }; server 10. 33. 40. 46 { keys {test; }; }; lewis@tislabs. com
Who’s watching your network TSIG in configuration files • Primary server • Secondary server options {. . . ; }; key "test" { algorithm hmac-md 5; secret "The. Place. To. Be"; }; server 10. 33. 40. 35 { keys {test; }; }; options {. . . ; }; #24 11 -13 June 2000 key "test" { algorithm hmac-md 5; secret "The. Place. To. Be"; }; server 10. 33. 40. 46 { keys {test; }; }; lewis@tislabs. com
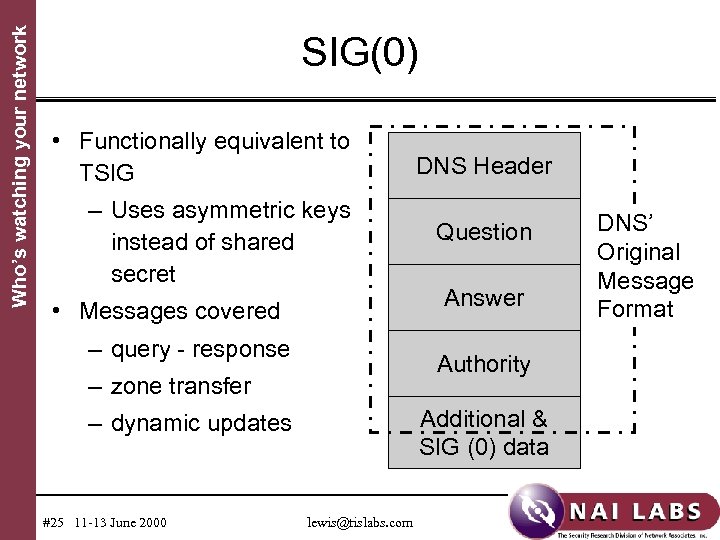 Who’s watching your network SIG(0) • Functionally equivalent to TSIG – Uses asymmetric keys instead of shared secret • Messages covered – query - response Question Answer Authority – zone transfer Additional & SIG (0) data – dynamic updates #25 11 -13 June 2000 DNS Header lewis@tislabs. com DNS’ Original Message Format
Who’s watching your network SIG(0) • Functionally equivalent to TSIG – Uses asymmetric keys instead of shared secret • Messages covered – query - response Question Answer Authority – zone transfer Additional & SIG (0) data – dynamic updates #25 11 -13 June 2000 DNS Header lewis@tislabs. com DNS’ Original Message Format
 Who’s watching your network SIG (0) Notes • Defined in RFC 2535 w/KEY, SIG, and NXT – A current Internet Draft fixes the specification • SIG(0) requires a public key to be in a zone • Suffers performance hit of public key cryptography – Useful where performance hit isn't as bad as overhead managing shared secrets • Requires client to have a private key available to the resolver #26 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network SIG (0) Notes • Defined in RFC 2535 w/KEY, SIG, and NXT – A current Internet Draft fixes the specification • SIG(0) requires a public key to be in a zone • Suffers performance hit of public key cryptography – Useful where performance hit isn't as bad as overhead managing shared secrets • Requires client to have a private key available to the resolver #26 11 -13 June 2000 lewis@tislabs. com
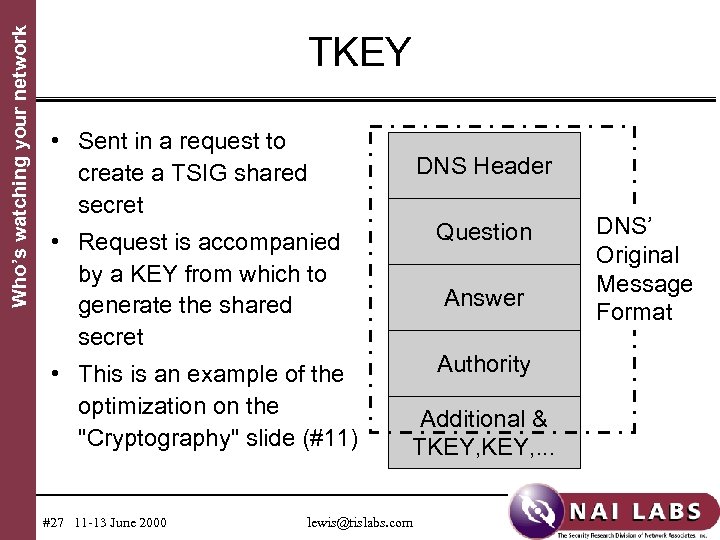 Who’s watching your network TKEY • Sent in a request to create a TSIG shared secret DNS Header • Request is accompanied by a KEY from which to generate the shared secret Question • This is an example of the optimization on the "Cryptography" slide (#11) Authority #27 11 -13 June 2000 Answer Additional & TKEY, . . . lewis@tislabs. com DNS’ Original Message Format
Who’s watching your network TKEY • Sent in a request to create a TSIG shared secret DNS Header • Request is accompanied by a KEY from which to generate the shared secret Question • This is an example of the optimization on the "Cryptography" slide (#11) Authority #27 11 -13 June 2000 Answer Additional & TKEY, . . . lewis@tislabs. com DNS’ Original Message Format
 Who’s watching your network TKEY Notes • TKEY is sent by resolver to set up a TSIG with server – Diffie-Hellman mode – GSSAPI - in Windows 2000 – Server or Client assigned (no implementations) • A TSIG is set up and used in subsequent queries and responses • Unsigned DH TKEY requests can pose a denial of service threat – Allowing "anonymous" TKEY is dangerous because of the CPU load induced #28 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network TKEY Notes • TKEY is sent by resolver to set up a TSIG with server – Diffie-Hellman mode – GSSAPI - in Windows 2000 – Server or Client assigned (no implementations) • A TSIG is set up and used in subsequent queries and responses • Unsigned DH TKEY requests can pose a denial of service threat – Allowing "anonymous" TKEY is dangerous because of the CPU load induced #28 11 -13 June 2000 lewis@tislabs. com
 Who’s watching your network Security Data Server • DNS can provide a public, scaleable, redundant mechanism to pass public security data – Certificates & Public Keys • DNSSEC validation of data has limits – DNSSEC provides that "what you see is what I sent" – DNSSEC does not provide assurance that the contents were entered correctly • Resource record introduced – CERT(ificate) #29 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network Security Data Server • DNS can provide a public, scaleable, redundant mechanism to pass public security data – Certificates & Public Keys • DNSSEC validation of data has limits – DNSSEC provides that "what you see is what I sent" – DNSSEC does not provide assurance that the contents were entered correctly • Resource record introduced – CERT(ificate) #29 11 -13 June 2000 lewis@tislabs. com
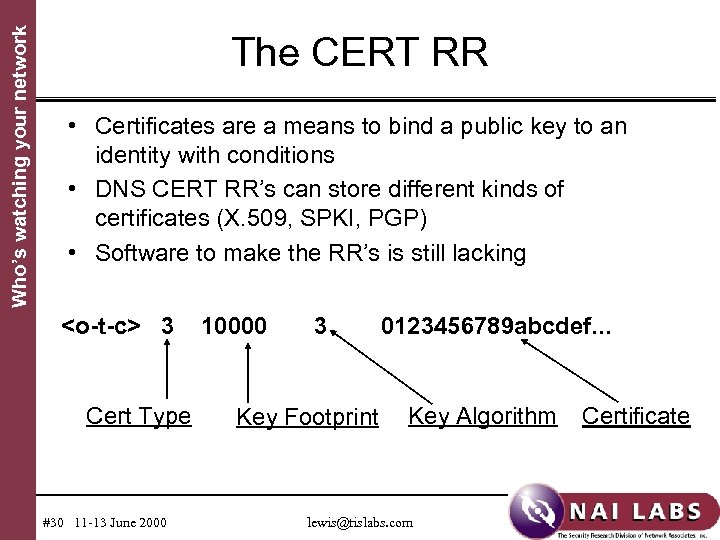 Who’s watching your network The CERT RR • Certificates are a means to bind a public key to an identity with conditions • DNS CERT RR’s can store different kinds of certificates (X. 509, SPKI, PGP) • Software to make the RR’s is still lacking
Who’s watching your network The CERT RR • Certificates are a means to bind a public key to an identity with conditions • DNS CERT RR’s can store different kinds of certificates (X. 509, SPKI, PGP) • Software to make the RR’s is still lacking
 Who’s watching your network Securing Dynamic Update • Still in definition • BINDv 9 will implement "Simple Secure Update" – TSIG or SIG(0) covered messages identify the requestor – The name server holds an authorization matrix indicating whether the requestor is allowed to make the requested change – Granularity of the policy is being defined, some defaults are being identified, rest is up to admin #31 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network Securing Dynamic Update • Still in definition • BINDv 9 will implement "Simple Secure Update" – TSIG or SIG(0) covered messages identify the requestor – The name server holds an authorization matrix indicating whether the requestor is allowed to make the requested change – Granularity of the policy is being defined, some defaults are being identified, rest is up to admin #31 11 -13 June 2000 lewis@tislabs. com
 Who’s watching your network Impact Start of "wrapup" • DNSSEC will increase attention paid to DNS – Data (SIG) "expires" from the authoritative server • No more "load & forget" – Delegations have a recurring relationship – Administrators have to manage keys • NOC procedures needed for this – Need more resources (CPU) to run #32 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network Impact Start of "wrapup" • DNSSEC will increase attention paid to DNS – Data (SIG) "expires" from the authoritative server • No more "load & forget" – Delegations have a recurring relationship – Administrators have to manage keys • NOC procedures needed for this – Need more resources (CPU) to run #32 11 -13 June 2000 lewis@tislabs. com
 Who’s watching your network Validating Delegations • Validation of a zone's keys by its parent is important – Provides "proof" of zone delegation – Relationship between delegations be interactive • Work is progressing on automating this • Will this help keep registry info current? #33 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network Validating Delegations • Validation of a zone's keys by its parent is important – Provides "proof" of zone delegation – Relationship between delegations be interactive • Work is progressing on automating this • Will this help keep registry info current? #33 11 -13 June 2000 lewis@tislabs. com
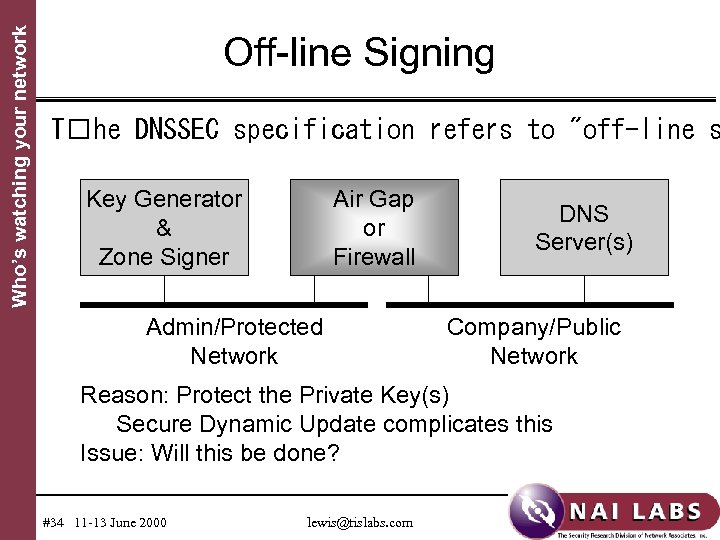 Who’s watching your network Off-line Signing T he DNSSEC specification refers to "off-line s Key Generator & Zone Signer Air Gap or Firewall Admin/Protected Network DNS Server(s) Company/Public Network Reason: Protect the Private Key(s) Secure Dynamic Update complicates this Issue: Will this be done? #34 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network Off-line Signing T he DNSSEC specification refers to "off-line s Key Generator & Zone Signer Air Gap or Firewall Admin/Protected Network DNS Server(s) Company/Public Network Reason: Protect the Private Key(s) Secure Dynamic Update complicates this Issue: Will this be done? #34 11 -13 June 2000 lewis@tislabs. com
 Who’s watching your network Performance Hits • Resource consumption – Increase data held and transferred – Increase in use of TCP – Increase in CPU cycles • Verifying keys (up to the root) will require more queries – Requires a lot of computation, message latency #35 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network Performance Hits • Resource consumption – Increase data held and transferred – Increase in use of TCP – Increase in CPU cycles • Verifying keys (up to the root) will require more queries – Requires a lot of computation, message latency #35 11 -13 June 2000 lewis@tislabs. com
 Who’s watching your network Bibliography - IETF Documents • IETF Standards Documents – RFC 2535 -2539 and 2541 • http: //www. ietf. org/rfc 2535. txt and others • http: //www. ietf. org/rfc 2136. txt -- Dynamic Update • ftp: //ftp. isi. edu/in-notes/rfc 2845. txt -- TSIG – DNSEXT, DNSOP WG pages • http: //www. ietf. org/html. charters/dnsext-charter. html • http: //www. ietf. org/html. charters/dnsop-charter. html – Internet Drafts (relevant to DNS security) • TKEY • http: //www. ietf. org/internet-drafts/draft-ietf-dnsext-tkey-02. txt • SIG(0) • http: //www. ietf. org/internet-drafts/draft-ietf-dnsext-sig-zero-01. txt • Simple Secure Update • http: //www. ietf. org/internet-drafts/draft-ietf-dnsext-simple-secure-update-00. txt • Other documents • • http: //www. ietf. org/internet-drafts/draft-ietf-dnsext-zone-status-01. txt http: //www. ietf. org/internet-drafts/draft-ietf-dnsext-signing-auth-00. txt #36 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network Bibliography - IETF Documents • IETF Standards Documents – RFC 2535 -2539 and 2541 • http: //www. ietf. org/rfc 2535. txt and others • http: //www. ietf. org/rfc 2136. txt -- Dynamic Update • ftp: //ftp. isi. edu/in-notes/rfc 2845. txt -- TSIG – DNSEXT, DNSOP WG pages • http: //www. ietf. org/html. charters/dnsext-charter. html • http: //www. ietf. org/html. charters/dnsop-charter. html – Internet Drafts (relevant to DNS security) • TKEY • http: //www. ietf. org/internet-drafts/draft-ietf-dnsext-tkey-02. txt • SIG(0) • http: //www. ietf. org/internet-drafts/draft-ietf-dnsext-sig-zero-01. txt • Simple Secure Update • http: //www. ietf. org/internet-drafts/draft-ietf-dnsext-simple-secure-update-00. txt • Other documents • • http: //www. ietf. org/internet-drafts/draft-ietf-dnsext-zone-status-01. txt http: //www. ietf. org/internet-drafts/draft-ietf-dnsext-signing-auth-00. txt #36 11 -13 June 2000 lewis@tislabs. com
 Who’s watching your network Bibliography - Other Documents • Technical Presentations – NAI Labs paper • http: //www. nai. com/nai_labs/asp_set/network_security/dns_secure_paper. asp • Some of its references are out of date – NIC-SE Workshop, May, 1999 • http: //www. nic-se. se/dnssec/ – CAIRN Workshop, September, 1999 • http: //www. cairn. net/DNSSEC/ — NLnet Labs • http: //www. nlnetlabs. nl. /dnssec/ • DNS & BIND – Cricket Liu is working on explaining DNSSEC • http: //www. hp. dk/kursus/dns (in Danish) - PDF files are at the bottom of the page, in English – BIND • http: //www. isc. org/products/BIND/ • ftp: //ftp. isc. org/isc/bind 9/ • URLs checked May. 31, 2000 #37 11 -13 June 2000 lewis@tislabs. com
Who’s watching your network Bibliography - Other Documents • Technical Presentations – NAI Labs paper • http: //www. nai. com/nai_labs/asp_set/network_security/dns_secure_paper. asp • Some of its references are out of date – NIC-SE Workshop, May, 1999 • http: //www. nic-se. se/dnssec/ – CAIRN Workshop, September, 1999 • http: //www. cairn. net/DNSSEC/ — NLnet Labs • http: //www. nlnetlabs. nl. /dnssec/ • DNS & BIND – Cricket Liu is working on explaining DNSSEC • http: //www. hp. dk/kursus/dns (in Danish) - PDF files are at the bottom of the page, in English – BIND • http: //www. isc. org/products/BIND/ • ftp: //ftp. isc. org/isc/bind 9/ • URLs checked May. 31, 2000 #37 11 -13 June 2000 lewis@tislabs. com


