373f3d92abb554f97270319cc011247e.ppt
- Количество слайдов: 49
 What’s new in Trend Micro Filip Demianiuk Sales Engineer Eastern Europe 13. 11. 06
What’s new in Trend Micro Filip Demianiuk Sales Engineer Eastern Europe 13. 11. 06
 Agenda • Trend Micro – Cisco alliance • Enterprise Protection Strategy • Innovation – – – NVW Enforcer IWSA IMSA IGSA TMMS • Q&A Copyright 2006 - Trend Micro Inc.
Agenda • Trend Micro – Cisco alliance • Enterprise Protection Strategy • Innovation – – – NVW Enforcer IWSA IMSA IGSA TMMS • Q&A Copyright 2006 - Trend Micro Inc.
 Trend Micro - Cisco Alliance
Trend Micro - Cisco Alliance
 Strategic importance of Cisco Alliance Copyright 2006 - Trend Micro Inc.
Strategic importance of Cisco Alliance Copyright 2006 - Trend Micro Inc.
 Strategic importance of Cisco Alliance “ One of Trend Micro’s Key differentiators against Symantec and Mc. Afee is the strength of it’s alliance with Cisco” Analyst event with Eva Chen • Cisco key priority for Trend Micro Executive Board • Opportunity for Trend to leverage the Cisco Brand • Competitive UTM Copyright 2006 - Trend Micro Inc.
Strategic importance of Cisco Alliance “ One of Trend Micro’s Key differentiators against Symantec and Mc. Afee is the strength of it’s alliance with Cisco” Analyst event with Eva Chen • Cisco key priority for Trend Micro Executive Board • Opportunity for Trend to leverage the Cisco Brand • Competitive UTM Copyright 2006 - Trend Micro Inc.
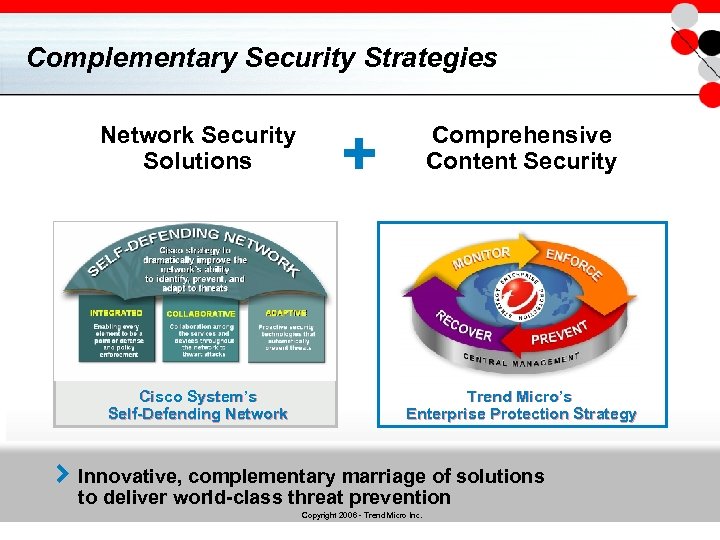 Complementary Security Strategies Network Security Solutions Cisco System’s Self-Defending Network + Comprehensive Content Security Trend Micro’s Enterprise Protection Strategy Innovative, complementary marriage of solutions to deliver world-class threat prevention Copyright 2006 - Trend Micro Inc.
Complementary Security Strategies Network Security Solutions Cisco System’s Self-Defending Network + Comprehensive Content Security Trend Micro’s Enterprise Protection Strategy Innovative, complementary marriage of solutions to deliver world-class threat prevention Copyright 2006 - Trend Micro Inc.
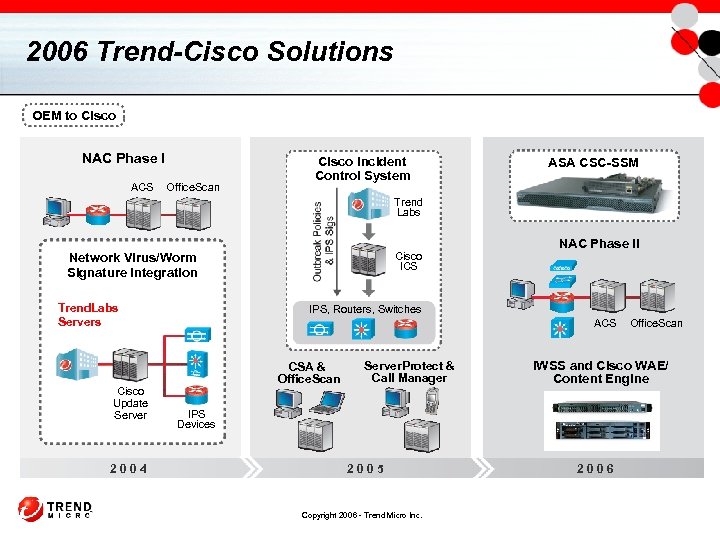 2006 Trend-Cisco Solutions OEM to Cisco NAC Phase I ACS Office. Scan Cisco Incident Control System ASA CSC-SSM Trend Labs Cisco ICS Network Virus/Worm Signature Integration Trend. Labs Servers Cisco Update Server 2004 NAC Phase II IPS, Routers, Switches ACS CSA & Office. Scan Server. Protect & Call Manager IWSS and Cisco WAE/ Content Engine IPS Devices 2005 Copyright 2006 - Trend Micro Inc. Office. Scan 2006
2006 Trend-Cisco Solutions OEM to Cisco NAC Phase I ACS Office. Scan Cisco Incident Control System ASA CSC-SSM Trend Labs Cisco ICS Network Virus/Worm Signature Integration Trend. Labs Servers Cisco Update Server 2004 NAC Phase II IPS, Routers, Switches ACS CSA & Office. Scan Server. Protect & Call Manager IWSS and Cisco WAE/ Content Engine IPS Devices 2005 Copyright 2006 - Trend Micro Inc. Office. Scan 2006
 Enterprise Protection Strategy
Enterprise Protection Strategy
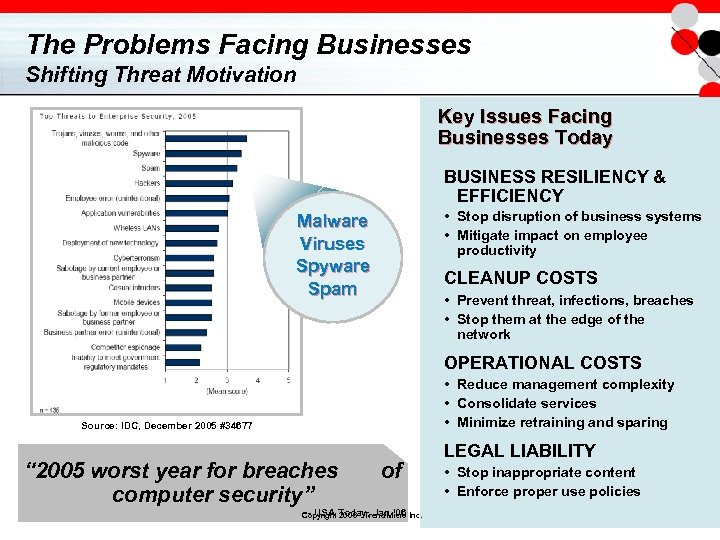 The Problems Facing Businesses Shifting Threat Motivation Key Issues Facing Businesses Today BUSINESS RESILIENCY & EFFICIENCY • Stop disruption of business systems • Mitigate impact on employee productivity Malware Viruses Spyware Spam CLEANUP COSTS • Prevent threat, infections, breaches • Stop them at the edge of the network OPERATIONAL COSTS • Reduce management complexity • Consolidate services • Minimize retraining and sparing Source: IDC, December 2005 #34677 “ 2005 worst year for breaches computer security” of -- USA 2006 - Trend Micro Copyright Today, Jan ‘ 06 Inc. LEGAL LIABILITY • Stop inappropriate content • Enforce proper use policies
The Problems Facing Businesses Shifting Threat Motivation Key Issues Facing Businesses Today BUSINESS RESILIENCY & EFFICIENCY • Stop disruption of business systems • Mitigate impact on employee productivity Malware Viruses Spyware Spam CLEANUP COSTS • Prevent threat, infections, breaches • Stop them at the edge of the network OPERATIONAL COSTS • Reduce management complexity • Consolidate services • Minimize retraining and sparing Source: IDC, December 2005 #34677 “ 2005 worst year for breaches computer security” of -- USA 2006 - Trend Micro Copyright Today, Jan ‘ 06 Inc. LEGAL LIABILITY • Stop inappropriate content • Enforce proper use policies
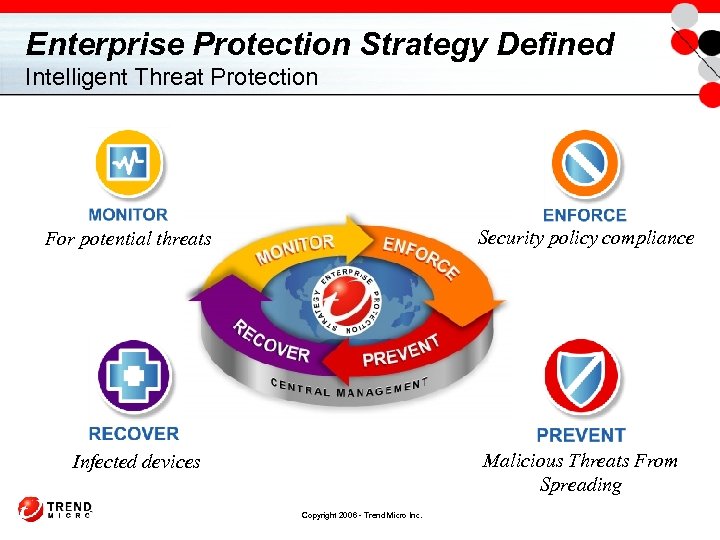 Enterprise Protection Strategy Defined Intelligent Threat Protection Security policy compliance For potential threats Malicious Threats From Spreading Infected devices Copyright 2006 - Trend Micro Inc.
Enterprise Protection Strategy Defined Intelligent Threat Protection Security policy compliance For potential threats Malicious Threats From Spreading Infected devices Copyright 2006 - Trend Micro Inc.
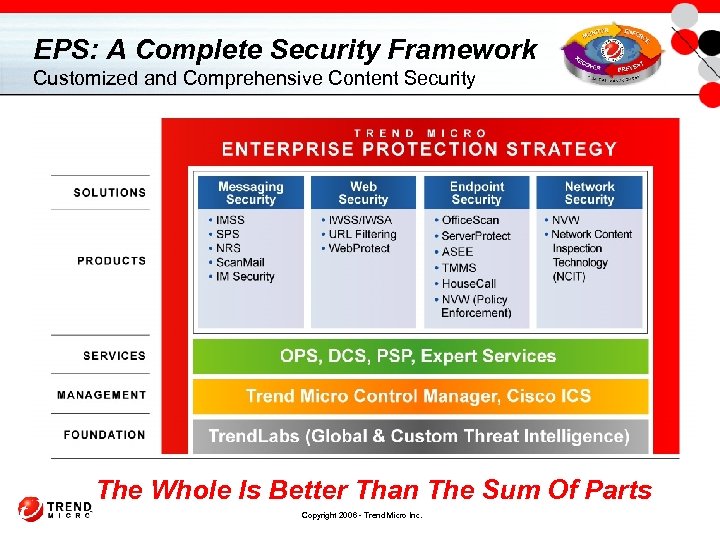 EPS: A Complete Security Framework Customized and Comprehensive Content Security The Whole Is Better Than The Sum Of Parts Copyright 2006 - Trend Micro Inc.
EPS: A Complete Security Framework Customized and Comprehensive Content Security The Whole Is Better Than The Sum Of Parts Copyright 2006 - Trend Micro Inc.
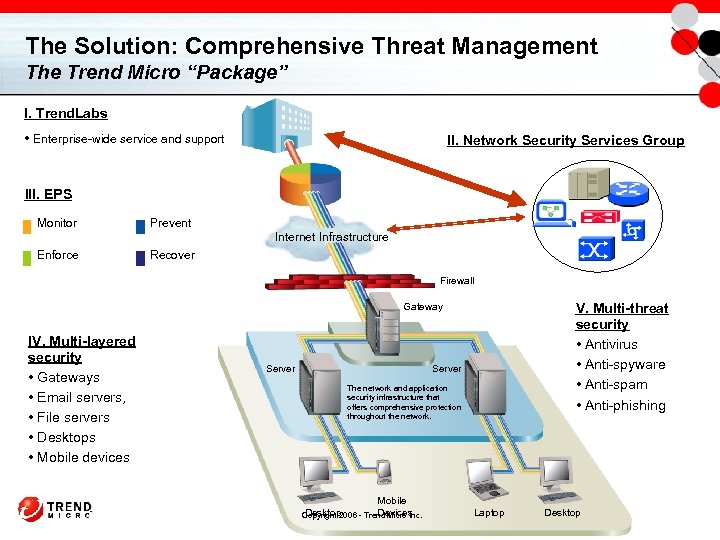 The Solution: Comprehensive Threat Management The Trend Micro “Package” I. Trend. Labs • Enterprise-wide service and support II. Network Security Services Group III. EPS Monitor Prevent Internet Infrastructure Enforce Recover Firewall V. Multi-threat security • Antivirus • Anti-spyware • Anti-spam • Anti-phishing Gateway IV. Multi-layered security • Gateways • Email servers, • File servers • Desktops • Mobile devices Server The network and application security infrastructure that offers comprehensive protection throughout the network. Mobile Desktop Devices Copyright 2006 - Trend Micro Inc. Laptop Desktop
The Solution: Comprehensive Threat Management The Trend Micro “Package” I. Trend. Labs • Enterprise-wide service and support II. Network Security Services Group III. EPS Monitor Prevent Internet Infrastructure Enforce Recover Firewall V. Multi-threat security • Antivirus • Anti-spyware • Anti-spam • Anti-phishing Gateway IV. Multi-layered security • Gateways • Email servers, • File servers • Desktops • Mobile devices Server The network and application security infrastructure that offers comprehensive protection throughout the network. Mobile Desktop Devices Copyright 2006 - Trend Micro Inc. Laptop Desktop
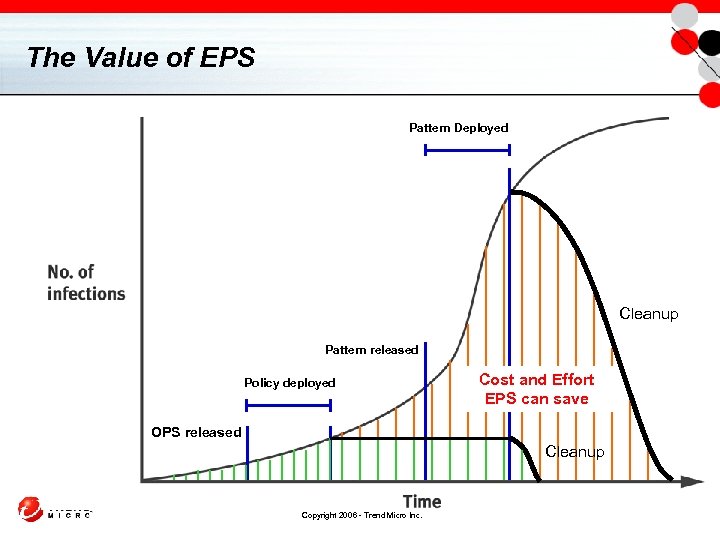 The Value of EPS Pattern Deployed Cleanup Pattern released Policy deployed Cost and Effort EPS can save OPS released Cleanup Copyright 2006 - Trend Micro Inc.
The Value of EPS Pattern Deployed Cleanup Pattern released Policy deployed Cost and Effort EPS can save OPS released Cleanup Copyright 2006 - Trend Micro Inc.
 Innovation
Innovation
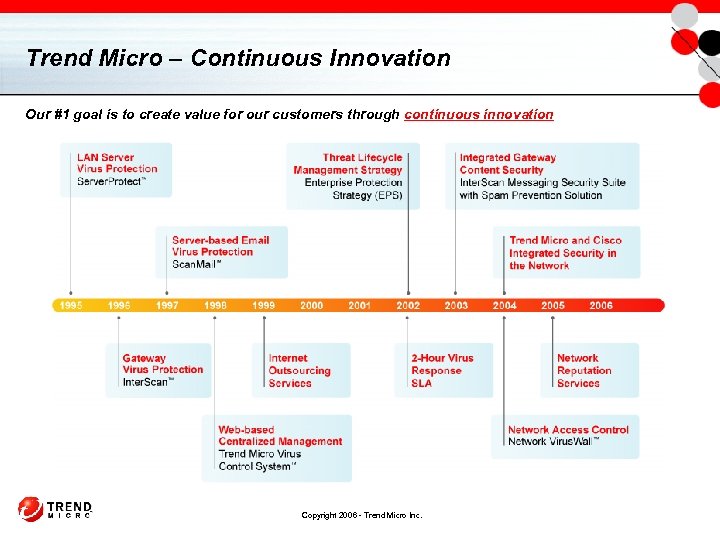 Trend Micro – Continuous Innovation Our #1 goal is to create value for our customers through continuous innovation Copyright 2006 - Trend Micro Inc.
Trend Micro – Continuous Innovation Our #1 goal is to create value for our customers through continuous innovation Copyright 2006 - Trend Micro Inc.
 Innovation NVW Enforcer
Innovation NVW Enforcer
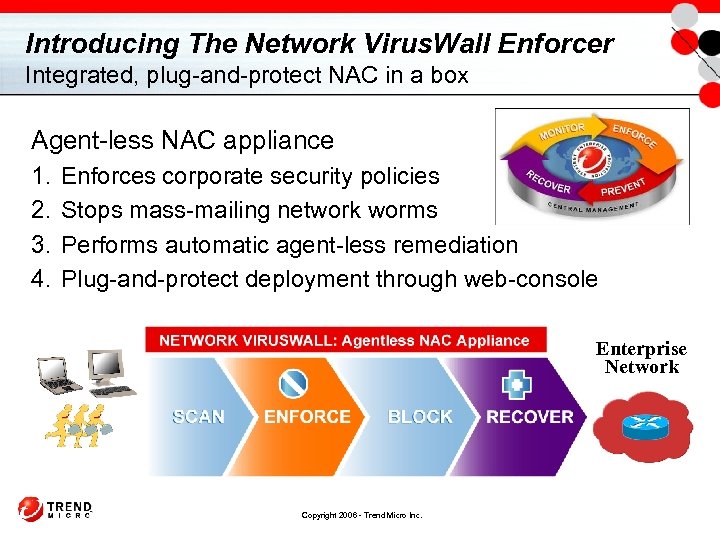 Introducing The Network Virus. Wall Enforcer Integrated, plug-and-protect NAC in a box Agent-less NAC appliance 1. 2. 3. 4. Enforces corporate security policies Stops mass-mailing network worms Performs automatic agent-less remediation Plug-and-protect deployment through web-console Enterprise Network Copyright 2006 - Trend Micro Inc.
Introducing The Network Virus. Wall Enforcer Integrated, plug-and-protect NAC in a box Agent-less NAC appliance 1. 2. 3. 4. Enforces corporate security policies Stops mass-mailing network worms Performs automatic agent-less remediation Plug-and-protect deployment through web-console Enterprise Network Copyright 2006 - Trend Micro Inc.
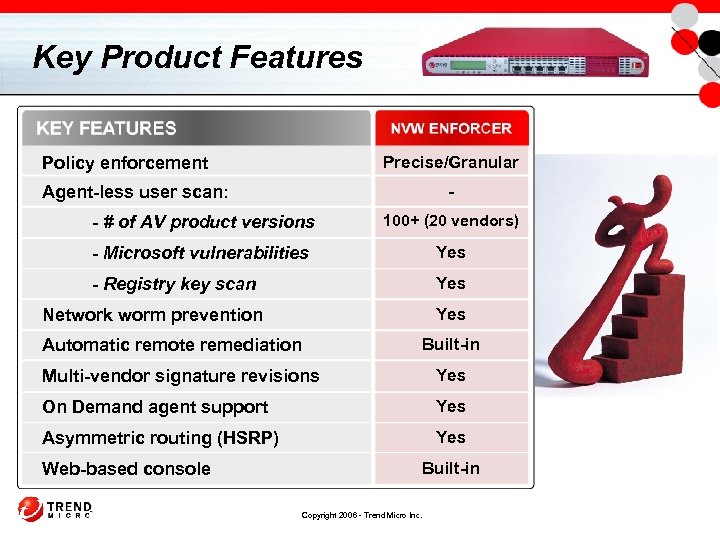 Key Product Features Precise/Granular Policy enforcement - Agent-less user scan: - # of AV product versions 100+ (20 vendors) - Microsoft vulnerabilities Yes - Registry key scan Yes Network worm prevention Built-in Automatic remote remediation Multi-vendor signature revisions Yes On Demand agent support Yes Asymmetric routing (HSRP) Yes Built-in Web-based console Copyright 2006 - Trend Micro Inc.
Key Product Features Precise/Granular Policy enforcement - Agent-less user scan: - # of AV product versions 100+ (20 vendors) - Microsoft vulnerabilities Yes - Registry key scan Yes Network worm prevention Built-in Automatic remote remediation Multi-vendor signature revisions Yes On Demand agent support Yes Asymmetric routing (HSRP) Yes Built-in Web-based console Copyright 2006 - Trend Micro Inc.
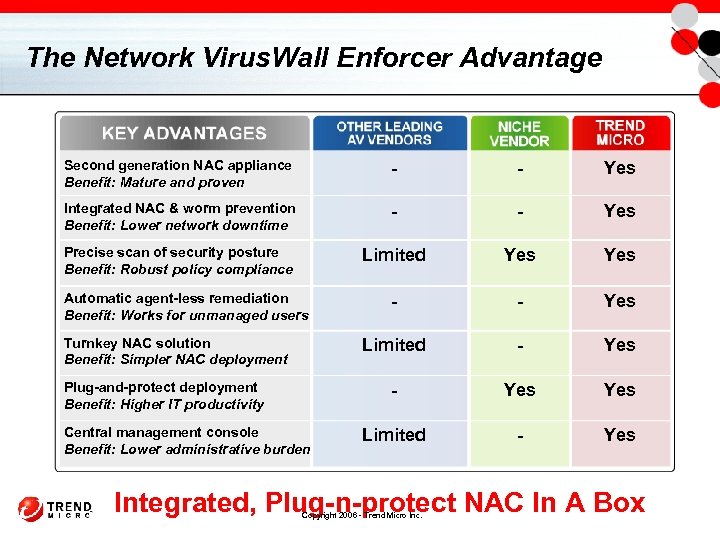 The Network Virus. Wall Enforcer Advantage Second generation NAC appliance Benefit: Mature and proven - - Yes Integrated NAC & worm prevention Benefit: Lower network downtime - - Yes Precise scan of security posture Benefit: Robust policy compliance Limited Yes - - Yes Limited - Yes Automatic agent-less remediation Benefit: Works for unmanaged users Turnkey NAC solution Benefit: Simpler NAC deployment Plug-and-protect deployment Benefit: Higher IT productivity Central management console Benefit: Lower administrative burden Integrated, Plug-n-protect NAC In A Box Copyright 2006 - Trend Micro Inc.
The Network Virus. Wall Enforcer Advantage Second generation NAC appliance Benefit: Mature and proven - - Yes Integrated NAC & worm prevention Benefit: Lower network downtime - - Yes Precise scan of security posture Benefit: Robust policy compliance Limited Yes - - Yes Limited - Yes Automatic agent-less remediation Benefit: Works for unmanaged users Turnkey NAC solution Benefit: Simpler NAC deployment Plug-and-protect deployment Benefit: Higher IT productivity Central management console Benefit: Lower administrative burden Integrated, Plug-n-protect NAC In A Box Copyright 2006 - Trend Micro Inc.
 Innovation IWSA
Innovation IWSA
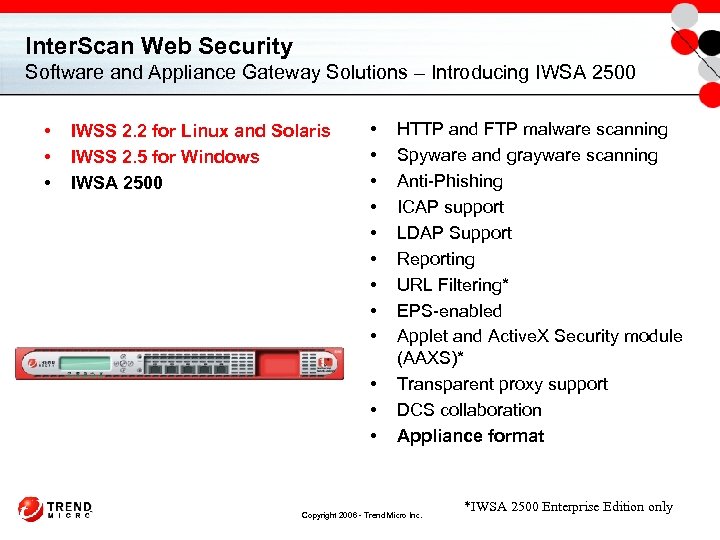 Inter. Scan Web Security Software and Appliance Gateway Solutions – Introducing IWSA 2500 • • • IWSS 2. 2 for Linux and Solaris IWSS 2. 5 for Windows IWSA 2500 • • • HTTP and FTP malware scanning Spyware and grayware scanning Anti-Phishing ICAP support LDAP Support Reporting URL Filtering* EPS-enabled Applet and Active. X Security module (AAXS)* Transparent proxy support DCS collaboration Appliance format Copyright 2006 - Trend Micro Inc. *IWSA 2500 Enterprise Edition only
Inter. Scan Web Security Software and Appliance Gateway Solutions – Introducing IWSA 2500 • • • IWSS 2. 2 for Linux and Solaris IWSS 2. 5 for Windows IWSA 2500 • • • HTTP and FTP malware scanning Spyware and grayware scanning Anti-Phishing ICAP support LDAP Support Reporting URL Filtering* EPS-enabled Applet and Active. X Security module (AAXS)* Transparent proxy support DCS collaboration Appliance format Copyright 2006 - Trend Micro Inc. *IWSA 2500 Enterprise Edition only
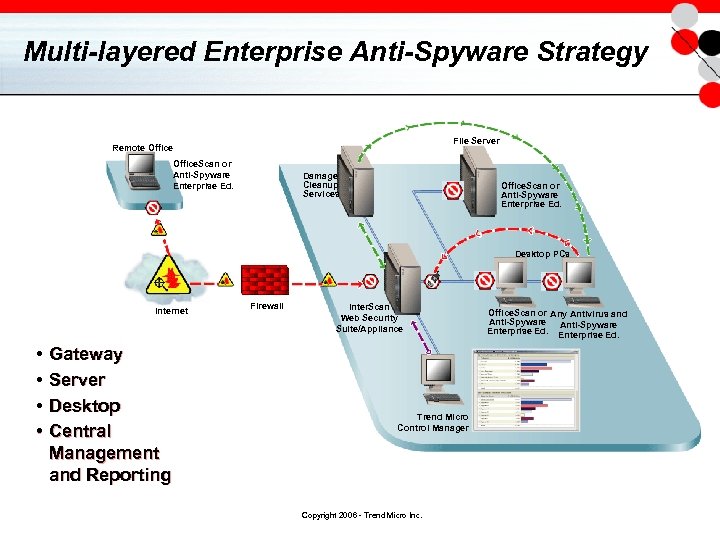 Multi-layered Enterprise Anti-Spyware Strategy File Server Remote Office. Scan or Anti-Spyware Enterprise Ed. Damage Cleanup Services Office. Scan or Anti-Spyware Enterprise Ed. Desktop PCs Internet • • Gateway Server Desktop Central Management and Reporting Firewall Inter. Scan Web Security Suite/Appliance Trend Micro Control Manager Copyright 2006 - Trend Micro Inc. Office. Scan or Any Antivirus and Anti-Spyware Enterprise Ed.
Multi-layered Enterprise Anti-Spyware Strategy File Server Remote Office. Scan or Anti-Spyware Enterprise Ed. Damage Cleanup Services Office. Scan or Anti-Spyware Enterprise Ed. Desktop PCs Internet • • Gateway Server Desktop Central Management and Reporting Firewall Inter. Scan Web Security Suite/Appliance Trend Micro Control Manager Copyright 2006 - Trend Micro Inc. Office. Scan or Any Antivirus and Anti-Spyware Enterprise Ed.
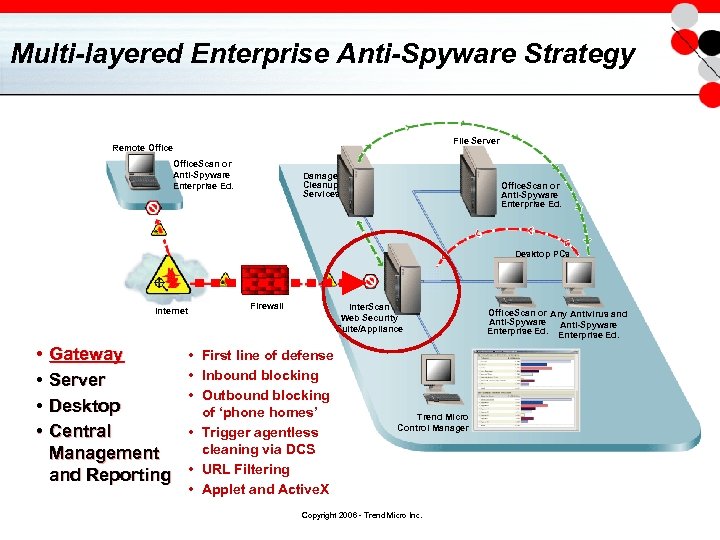 Multi-layered Enterprise Anti-Spyware Strategy File Server Remote Office. Scan or Anti-Spyware Enterprise Ed. Damage Cleanup Services Office. Scan or Anti-Spyware Enterprise Ed. Desktop PCs Internet • • Gateway Server Desktop Central Management and Reporting Firewall Inter. Scan Web Security Suite/Appliance • First line of defense • Inbound blocking • Outbound blocking of ‘phone homes’ • Trigger agentless cleaning via DCS • URL Filtering • Applet and Active. X Trend Micro Control Manager Copyright 2006 - Trend Micro Inc. Office. Scan or Any Antivirus and Anti-Spyware Enterprise Ed.
Multi-layered Enterprise Anti-Spyware Strategy File Server Remote Office. Scan or Anti-Spyware Enterprise Ed. Damage Cleanup Services Office. Scan or Anti-Spyware Enterprise Ed. Desktop PCs Internet • • Gateway Server Desktop Central Management and Reporting Firewall Inter. Scan Web Security Suite/Appliance • First line of defense • Inbound blocking • Outbound blocking of ‘phone homes’ • Trigger agentless cleaning via DCS • URL Filtering • Applet and Active. X Trend Micro Control Manager Copyright 2006 - Trend Micro Inc. Office. Scan or Any Antivirus and Anti-Spyware Enterprise Ed.
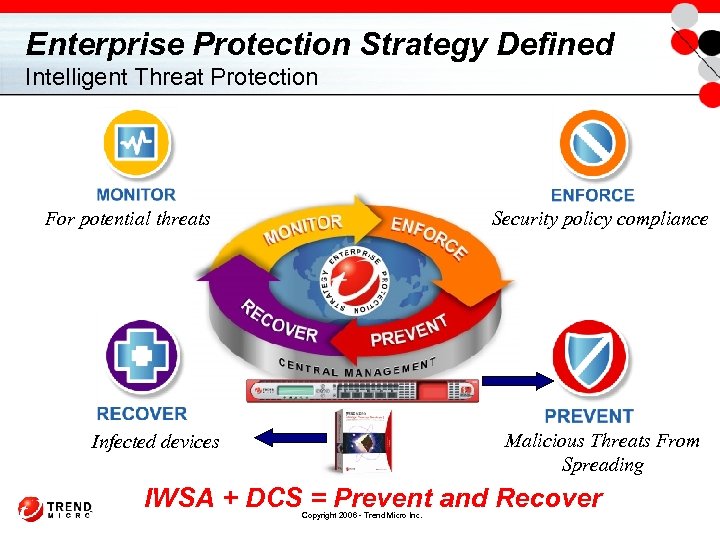 Enterprise Protection Strategy Defined Intelligent Threat Protection Security policy compliance For potential threats Malicious Threats From Spreading Infected devices IWSA + DCS = Prevent and Recover Copyright 2006 - Trend Micro Inc.
Enterprise Protection Strategy Defined Intelligent Threat Protection Security policy compliance For potential threats Malicious Threats From Spreading Infected devices IWSA + DCS = Prevent and Recover Copyright 2006 - Trend Micro Inc.
 Innovation IMSA
Innovation IMSA
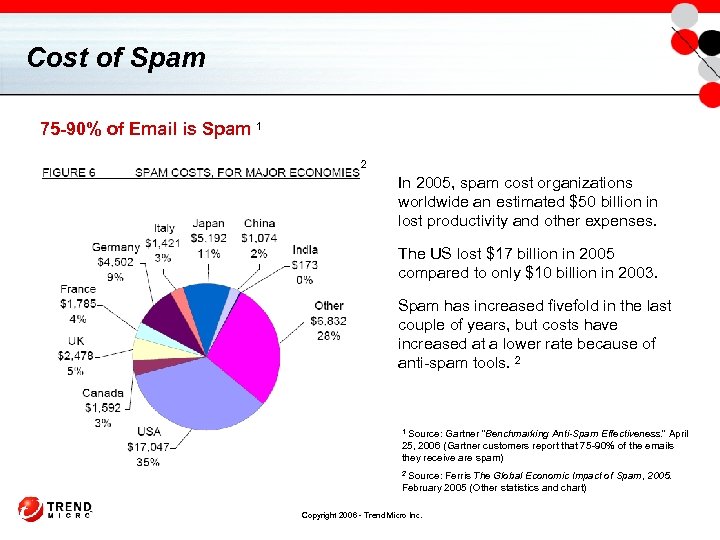 Cost of Spam 75 -90% of Email is Spam 1 2 In 2005, spam cost organizations worldwide an estimated $50 billion in lost productivity and other expenses. The US lost $17 billion in 2005 compared to only $10 billion in 2003. Spam has increased fivefold in the last couple of years, but costs have increased at a lower rate because of anti-spam tools. 2 Source: Gartner “Benchmarking Anti-Spam Effectiveness. ” April 25, 2006 (Gartner customers report that 75 -90% of the emails they receive are spam) 1 Source: Ferris The Global Economic Impact of Spam, 2005. February 2005 (Other statistics and chart) 2 Copyright 2006 - Trend Micro Inc.
Cost of Spam 75 -90% of Email is Spam 1 2 In 2005, spam cost organizations worldwide an estimated $50 billion in lost productivity and other expenses. The US lost $17 billion in 2005 compared to only $10 billion in 2003. Spam has increased fivefold in the last couple of years, but costs have increased at a lower rate because of anti-spam tools. 2 Source: Gartner “Benchmarking Anti-Spam Effectiveness. ” April 25, 2006 (Gartner customers report that 75 -90% of the emails they receive are spam) 1 Source: Ferris The Global Economic Impact of Spam, 2005. February 2005 (Other statistics and chart) 2 Copyright 2006 - Trend Micro Inc.
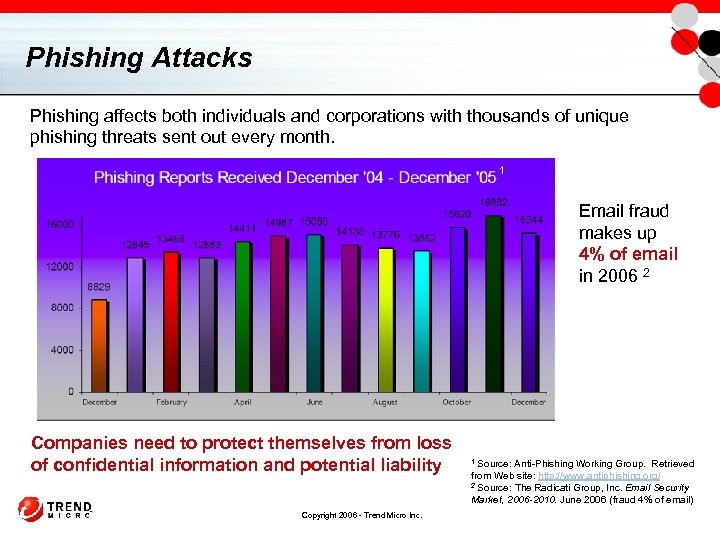 Phishing Attacks Phishing affects both individuals and corporations with thousands of unique phishing threats sent out every month. 1 Email fraud makes up 4% of email in 2006 2 Companies need to protect themselves from loss of confidential information and potential liability Copyright 2006 - Trend Micro Inc. Source: Anti-Phishing Working Group. Retrieved from Web site: http: //www. antiphishing. org/ 2 Source: The Radicati Group, Inc. Email Security Market, 2006 -2010. June 2006 (fraud 4% of email) 1
Phishing Attacks Phishing affects both individuals and corporations with thousands of unique phishing threats sent out every month. 1 Email fraud makes up 4% of email in 2006 2 Companies need to protect themselves from loss of confidential information and potential liability Copyright 2006 - Trend Micro Inc. Source: Anti-Phishing Working Group. Retrieved from Web site: http: //www. antiphishing. org/ 2 Source: The Radicati Group, Inc. Email Security Market, 2006 -2010. June 2006 (fraud 4% of email) 1
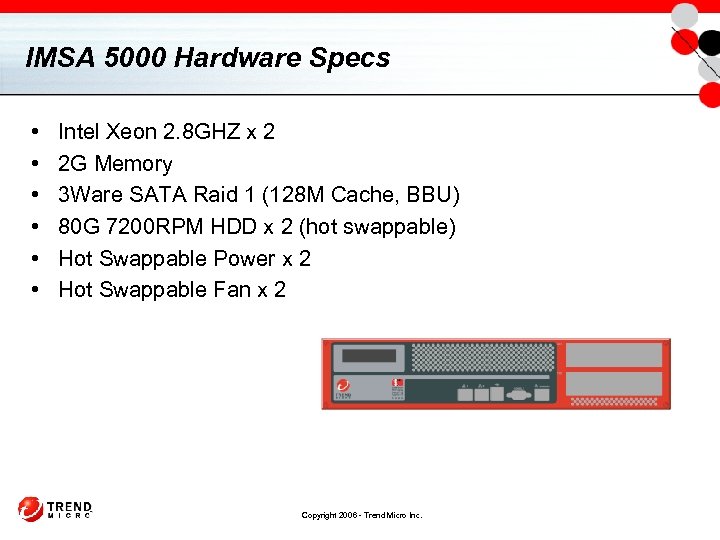 IMSA 5000 Hardware Specs • • • Intel Xeon 2. 8 GHZ x 2 2 G Memory 3 Ware SATA Raid 1 (128 M Cache, BBU) 80 G 7200 RPM HDD x 2 (hot swappable) Hot Swappable Power x 2 Hot Swappable Fan x 2 Copyright 2006 - Trend Micro Inc.
IMSA 5000 Hardware Specs • • • Intel Xeon 2. 8 GHZ x 2 2 G Memory 3 Ware SATA Raid 1 (128 M Cache, BBU) 80 G 7200 RPM HDD x 2 (hot swappable) Hot Swappable Power x 2 Hot Swappable Fan x 2 Copyright 2006 - Trend Micro Inc.
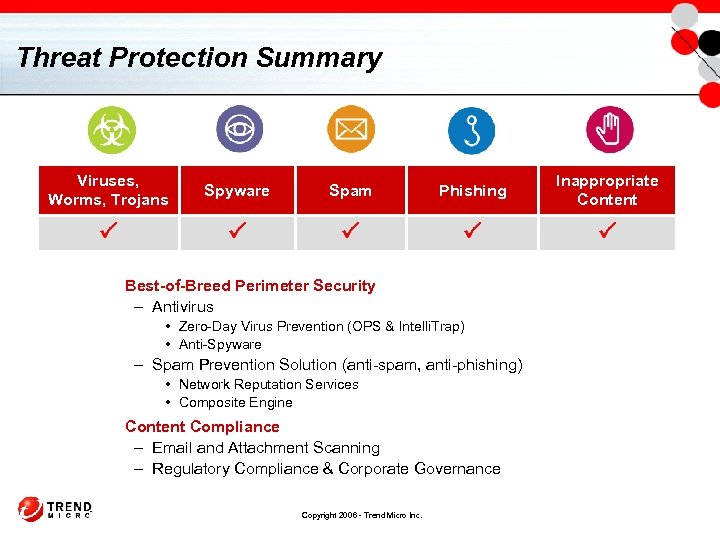 Threat Protection Summary Viruses, Worms, Trojans Spyware Spam Phishing Inappropriate Content Best-of-Breed Perimeter Security – Antivirus • Zero-Day Virus Prevention (OPS & Intelli. Trap) • Anti-Spyware – Spam Prevention Solution (anti-spam, anti-phishing) • Network Reputation Services • Composite Engine Content Compliance – Email and Attachment Scanning – Regulatory Compliance & Corporate Governance Copyright 2006 - Trend Micro Inc.
Threat Protection Summary Viruses, Worms, Trojans Spyware Spam Phishing Inappropriate Content Best-of-Breed Perimeter Security – Antivirus • Zero-Day Virus Prevention (OPS & Intelli. Trap) • Anti-Spyware – Spam Prevention Solution (anti-spam, anti-phishing) • Network Reputation Services • Composite Engine Content Compliance – Email and Attachment Scanning – Regulatory Compliance & Corporate Governance Copyright 2006 - Trend Micro Inc.
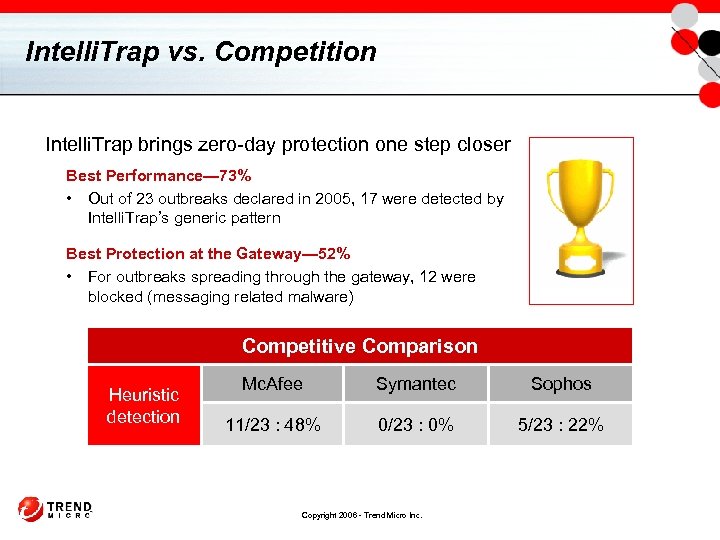 Intelli. Trap vs. Competition Intelli. Trap brings zero-day protection one step closer Best Performance— 73% • Out of 23 outbreaks declared in 2005, 17 were detected by Intelli. Trap’s generic pattern Best Protection at the Gateway— 52% • For outbreaks spreading through the gateway, 12 were blocked (messaging related malware) Competitive Comparison Heuristic detection Mc. Afee Symantec Sophos 11/23 : 48% 0/23 : 0% 5/23 : 22% Copyright 2006 - Trend Micro Inc.
Intelli. Trap vs. Competition Intelli. Trap brings zero-day protection one step closer Best Performance— 73% • Out of 23 outbreaks declared in 2005, 17 were detected by Intelli. Trap’s generic pattern Best Protection at the Gateway— 52% • For outbreaks spreading through the gateway, 12 were blocked (messaging related malware) Competitive Comparison Heuristic detection Mc. Afee Symantec Sophos 11/23 : 48% 0/23 : 0% 5/23 : 22% Copyright 2006 - Trend Micro Inc.
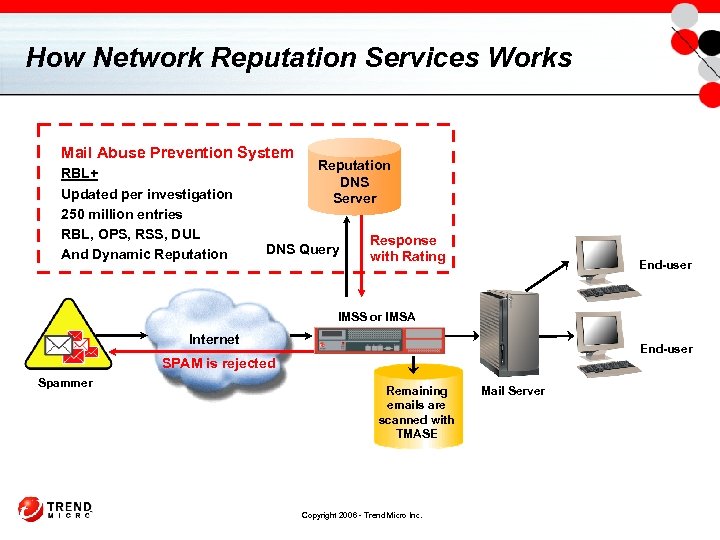 How Network Reputation Services Works Mail Abuse Prevention System RBL+ Updated per investigation 250 million entries RBL, OPS, RSS, DUL And Dynamic Reputation DNS Server DNS Query Response with Rating End-user IMSS or IMSA Internet End-user SPAM is rejected Spammer Remaining emails are scanned with TMASE Copyright 2006 - Trend Micro Inc. Mail Server
How Network Reputation Services Works Mail Abuse Prevention System RBL+ Updated per investigation 250 million entries RBL, OPS, RSS, DUL And Dynamic Reputation DNS Server DNS Query Response with Rating End-user IMSS or IMSA Internet End-user SPAM is rejected Spammer Remaining emails are scanned with TMASE Copyright 2006 - Trend Micro Inc. Mail Server
 Innovation TMMS
Innovation TMMS
 Trend Micro Mobile Security 3. 0 Combined AV & Firewall for Mobiles • Targeted General Availability: December 2006 (standalone) Key Competitive Differentiators – AV & Firewall – Basic IDS – Improved UI Key Features (Details) – Addition of firewall – Avoid synchronized flood attacks via firewall – Simplified registration process • Supported Operating Systems / Versions – Windows Mobile 5. 0, followed by Symbian/S 60 3 rd Edition Copyright 2006 - Trend Micro Inc.
Trend Micro Mobile Security 3. 0 Combined AV & Firewall for Mobiles • Targeted General Availability: December 2006 (standalone) Key Competitive Differentiators – AV & Firewall – Basic IDS – Improved UI Key Features (Details) – Addition of firewall – Avoid synchronized flood attacks via firewall – Simplified registration process • Supported Operating Systems / Versions – Windows Mobile 5. 0, followed by Symbian/S 60 3 rd Edition Copyright 2006 - Trend Micro Inc.
 Innovation IGSA
Innovation IGSA
 What is a Mid-Market customer? • Limited security expertise – A few generalists -often < 5 • • Networks can be complex Don’t have time to become experts But still like to feel in control Need to be seen to have taken appropriate security measures • More price sensitive than Enterprise • IT owns budget and makes purchase decision Copyright 2006 - Trend Micro Inc. ?
What is a Mid-Market customer? • Limited security expertise – A few generalists -often < 5 • • Networks can be complex Don’t have time to become experts But still like to feel in control Need to be seen to have taken appropriate security measures • More price sensitive than Enterprise • IT owns budget and makes purchase decision Copyright 2006 - Trend Micro Inc. ?
 What products do they want? THEY DON’T! They want SOLUTIONS which: • • • Solve recognizable business problems Employ best of breed technology Are simple to buy, deploy and manage Are flexible and scaleable Help IT staff to feel in control Copyright 2006 - Trend Micro Inc.
What products do they want? THEY DON’T! They want SOLUTIONS which: • • • Solve recognizable business problems Employ best of breed technology Are simple to buy, deploy and manage Are flexible and scaleable Help IT staff to feel in control Copyright 2006 - Trend Micro Inc.
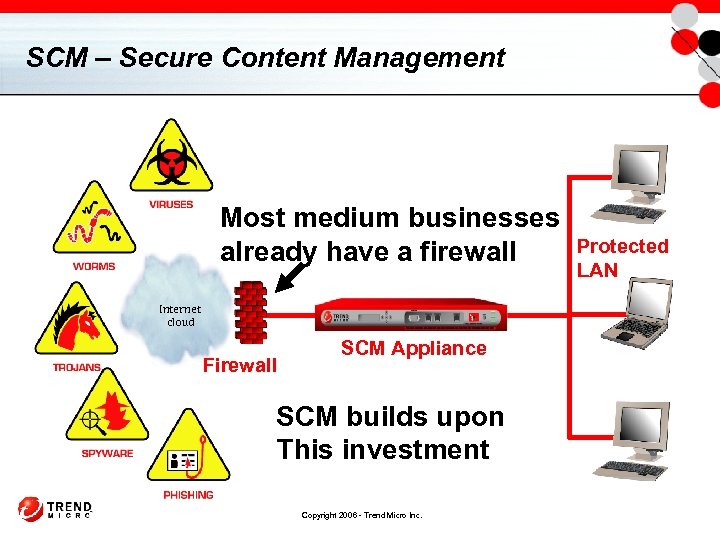 SCM – Secure Content Management Most medium businesses already have a firewall Internet cloud Firewall SCM Appliance SCM builds upon This investment Copyright 2006 - Trend Micro Inc. Protected LAN
SCM – Secure Content Management Most medium businesses already have a firewall Internet cloud Firewall SCM Appliance SCM builds upon This investment Copyright 2006 - Trend Micro Inc. Protected LAN
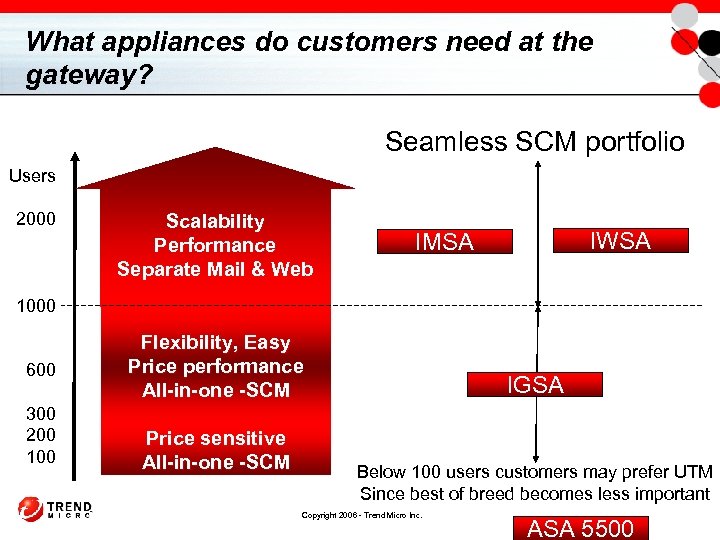 What appliances do customers need at the gateway? Seamless SCM portfolio Users 2000 Scalability Performance Separate Mail & Web IWSA IMSA 1000 600 300 200 100 Flexibility, Easy Price performance All-in-one -SCM Price sensitive All-in-one -SCM IGSA Below 100 users customers may prefer UTM Since best of breed becomes less important Copyright 2006 - Trend Micro Inc. ASA 5500
What appliances do customers need at the gateway? Seamless SCM portfolio Users 2000 Scalability Performance Separate Mail & Web IWSA IMSA 1000 600 300 200 100 Flexibility, Easy Price performance All-in-one -SCM Price sensitive All-in-one -SCM IGSA Below 100 users customers may prefer UTM Since best of breed becomes less important Copyright 2006 - Trend Micro Inc. ASA 5500
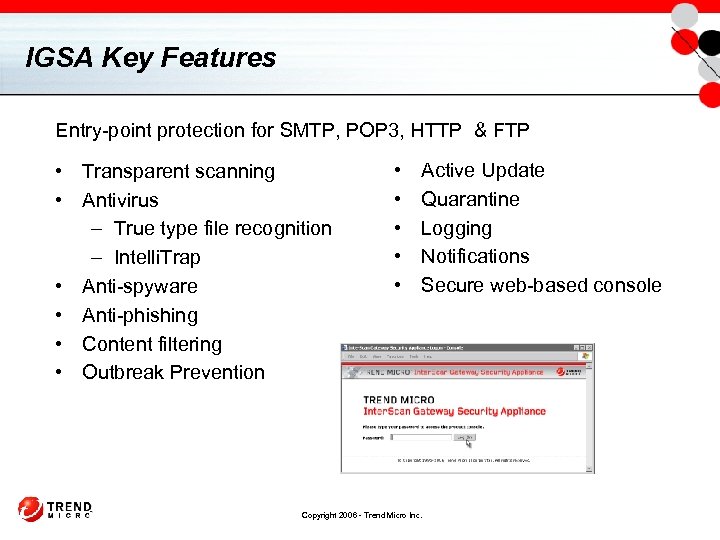 IGSA Key Features Entry-point protection for SMTP, POP 3, HTTP & FTP • Transparent scanning • Antivirus – True type file recognition – Intelli. Trap • Anti-spyware • Anti-phishing • Content filtering • Outbreak Prevention • • • Active Update Quarantine Logging Notifications Secure web-based console Copyright 2006 - Trend Micro Inc.
IGSA Key Features Entry-point protection for SMTP, POP 3, HTTP & FTP • Transparent scanning • Antivirus – True type file recognition – Intelli. Trap • Anti-spyware • Anti-phishing • Content filtering • Outbreak Prevention • • • Active Update Quarantine Logging Notifications Secure web-based console Copyright 2006 - Trend Micro Inc.
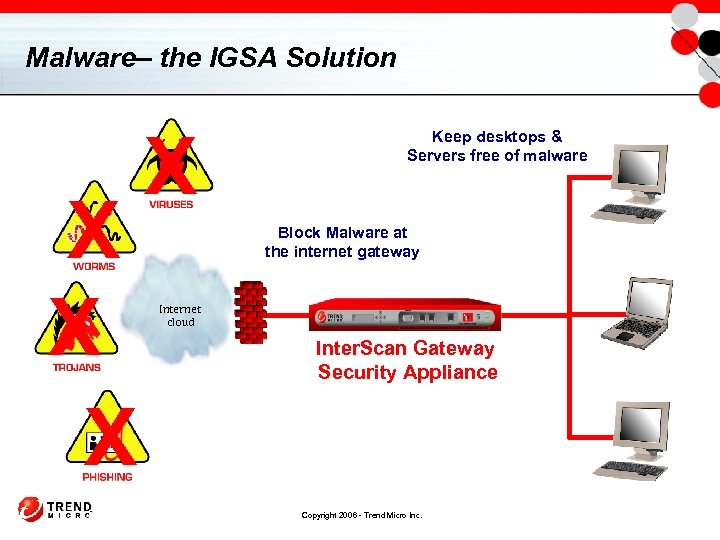 Malware– the IGSA Solution X X Keep desktops & Servers free of malware Block Malware at the internet gateway Internet cloud Inter. Scan Gateway Security Appliance Copyright 2006 - Trend Micro Inc.
Malware– the IGSA Solution X X Keep desktops & Servers free of malware Block Malware at the internet gateway Internet cloud Inter. Scan Gateway Security Appliance Copyright 2006 - Trend Micro Inc.
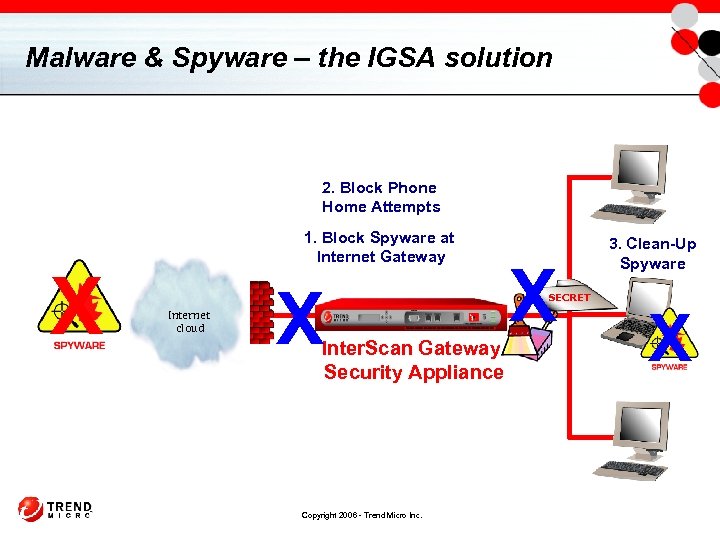 Malware & Spyware – the IGSA solution 2. Block Phone Home Attempts X 1. Block Spyware at Internet Gateway Internet cloud X Inter. Scan Gateway Security Appliance Copyright 2006 - Trend Micro Inc. X SECRET 3. Clean-Up Spyware X
Malware & Spyware – the IGSA solution 2. Block Phone Home Attempts X 1. Block Spyware at Internet Gateway Internet cloud X Inter. Scan Gateway Security Appliance Copyright 2006 - Trend Micro Inc. X SECRET 3. Clean-Up Spyware X
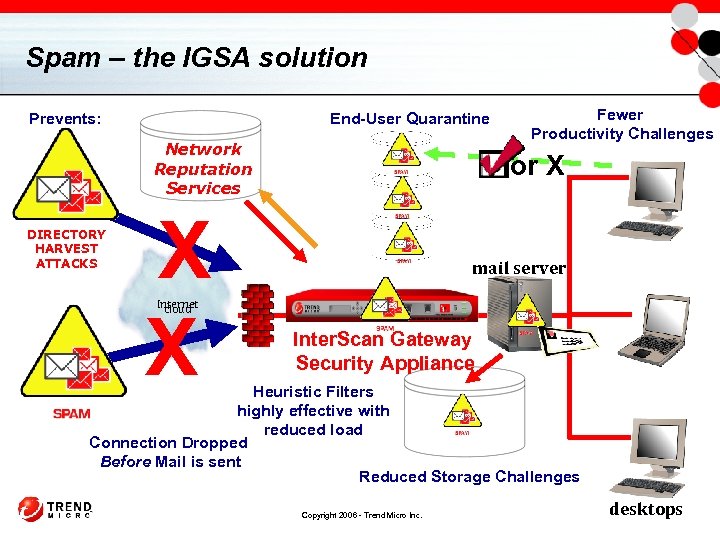 Spam – the IGSA solution End-User Quarantine Prevents: Network Reputation Services DIRECTORY HARVEST ATTACKS X X Fewer Productivity Challenges or X mail server Internet cloud Inter. Scan Gateway Security Appliance Heuristic Filters highly effective with reduced load Connection Dropped Before Mail is sent Reduced Storage Challenges Copyright 2006 - Trend Micro Inc. desktops
Spam – the IGSA solution End-User Quarantine Prevents: Network Reputation Services DIRECTORY HARVEST ATTACKS X X Fewer Productivity Challenges or X mail server Internet cloud Inter. Scan Gateway Security Appliance Heuristic Filters highly effective with reduced load Connection Dropped Before Mail is sent Reduced Storage Challenges Copyright 2006 - Trend Micro Inc. desktops
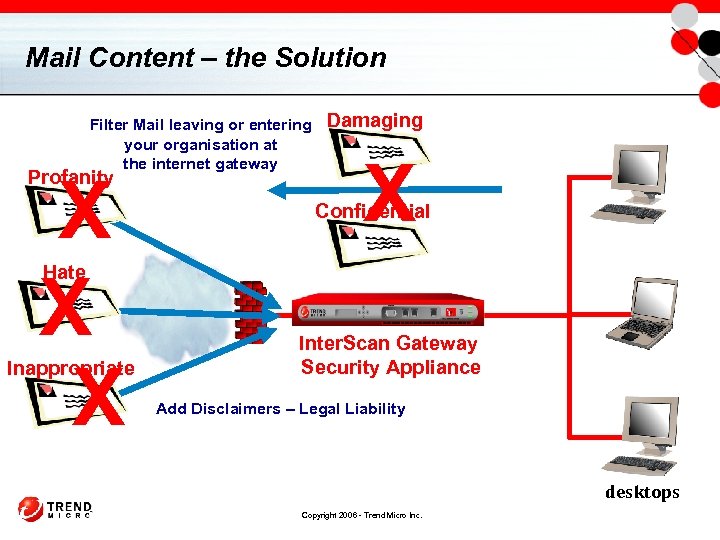 Mail Content – the Solution Filter Mail leaving or entering your organisation at the internet gateway X X X Profanity Damaging X Confidential Hate Inappropriate Inter. Scan Gateway Security Appliance Add Disclaimers – Legal Liability desktops Copyright 2006 - Trend Micro Inc.
Mail Content – the Solution Filter Mail leaving or entering your organisation at the internet gateway X X X Profanity Damaging X Confidential Hate Inappropriate Inter. Scan Gateway Security Appliance Add Disclaimers – Legal Liability desktops Copyright 2006 - Trend Micro Inc.
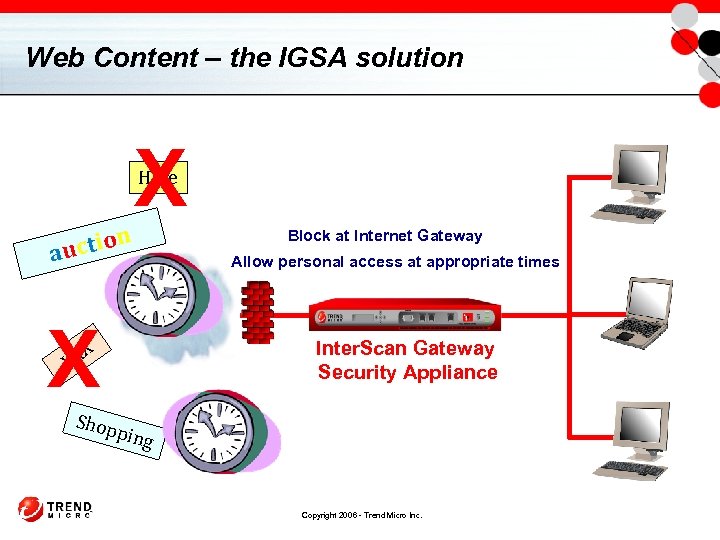 Web Content – the IGSA solution X Hate n uc t i o a X Block at Internet Gateway Allow personal access at appropriate times Inter. Scan Gateway Security Appliance X XX Shop ping Copyright 2006 - Trend Micro Inc.
Web Content – the IGSA solution X Hate n uc t i o a X Block at Internet Gateway Allow personal access at appropriate times Inter. Scan Gateway Security Appliance X XX Shop ping Copyright 2006 - Trend Micro Inc.
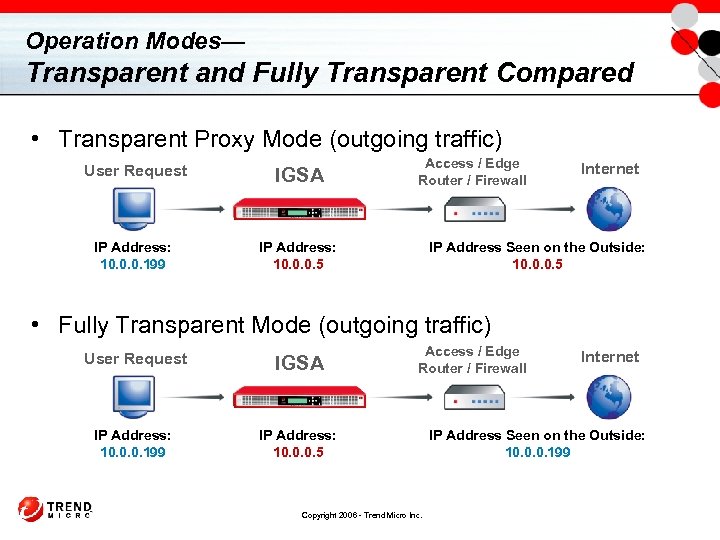 Operation Modes— Transparent and Fully Transparent Compared • Transparent Proxy Mode (outgoing traffic) User Request IGSA IP Address: 10. 0. 0. 199 Access / Edge Router / Firewall IP Address: 10. 0. 0. 5 Internet IP Address Seen on the Outside: 10. 0. 0. 5 • Fully Transparent Mode (outgoing traffic) User Request IGSA IP Address: 10. 0. 0. 199 Access / Edge Router / Firewall IP Address: 10. 0. 0. 5 Copyright 2006 - Trend Micro Inc. Internet IP Address Seen on the Outside: 10. 0. 0. 199
Operation Modes— Transparent and Fully Transparent Compared • Transparent Proxy Mode (outgoing traffic) User Request IGSA IP Address: 10. 0. 0. 199 Access / Edge Router / Firewall IP Address: 10. 0. 0. 5 Internet IP Address Seen on the Outside: 10. 0. 0. 5 • Fully Transparent Mode (outgoing traffic) User Request IGSA IP Address: 10. 0. 0. 199 Access / Edge Router / Firewall IP Address: 10. 0. 0. 5 Copyright 2006 - Trend Micro Inc. Internet IP Address Seen on the Outside: 10. 0. 0. 199
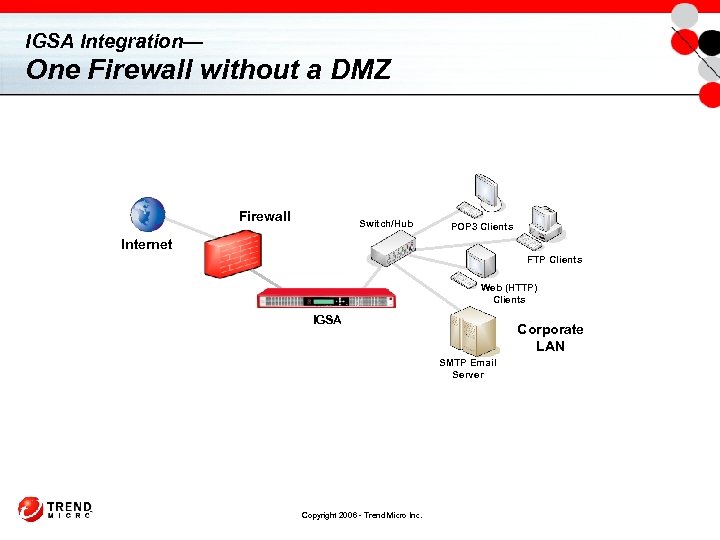 IGSA Integration— One Firewall without a DMZ Firewall Switch/Hub POP 3 Clients Internet FTP Clients Web (HTTP) Clients IGSA Corporate LAN SMTP Email Server Copyright 2006 - Trend Micro Inc.
IGSA Integration— One Firewall without a DMZ Firewall Switch/Hub POP 3 Clients Internet FTP Clients Web (HTTP) Clients IGSA Corporate LAN SMTP Email Server Copyright 2006 - Trend Micro Inc.
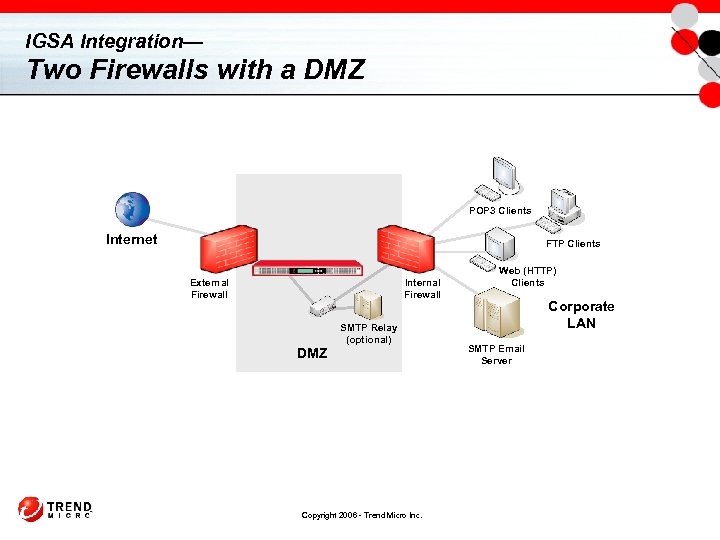 IGSA Integration— Two Firewalls with a DMZ POP 3 Clients Internet FTP Clients External Firewall Internal Firewall DMZ SMTP Relay (optional) Copyright 2006 - Trend Micro Inc. Web (HTTP) Clients Corporate LAN SMTP Email Server
IGSA Integration— Two Firewalls with a DMZ POP 3 Clients Internet FTP Clients External Firewall Internal Firewall DMZ SMTP Relay (optional) Copyright 2006 - Trend Micro Inc. Web (HTTP) Clients Corporate LAN SMTP Email Server
 IGSA Global pricing model Pricing and licensing: – IGSA Hardware replacement – IGSA 100 users * – IGSA 200 users * – IGSA 300 users * – IGSA 600 users * – IGSA 800 users * – IGSA 1000 users * * Includes hardware and software license with all functionality enabled so NRS, URL etc. become differentiators rather than optional add-ons. Hardware Warranty is included in 1 st year price. Copyright 2006 - Trend Micro Inc.
IGSA Global pricing model Pricing and licensing: – IGSA Hardware replacement – IGSA 100 users * – IGSA 200 users * – IGSA 300 users * – IGSA 600 users * – IGSA 800 users * – IGSA 1000 users * * Includes hardware and software license with all functionality enabled so NRS, URL etc. become differentiators rather than optional add-ons. Hardware Warranty is included in 1 st year price. Copyright 2006 - Trend Micro Inc.
 Q&A and Thank You!
Q&A and Thank You!


