73fdc9573ec9696cc2cb70bc4aef0bec.ppt
- Количество слайдов: 26
 What is Static Analysis • Static analysis is the process of examining source code prior to compilation (and execution) • Static analysis can diagnose for: – Quality aspects such as maintainability, reliability, understandability and complexity – Testing issues – Coding standard compliance issues – Best programming practices and unsafe programming constructs and coding defects
What is Static Analysis • Static analysis is the process of examining source code prior to compilation (and execution) • Static analysis can diagnose for: – Quality aspects such as maintainability, reliability, understandability and complexity – Testing issues – Coding standard compliance issues – Best programming practices and unsafe programming constructs and coding defects
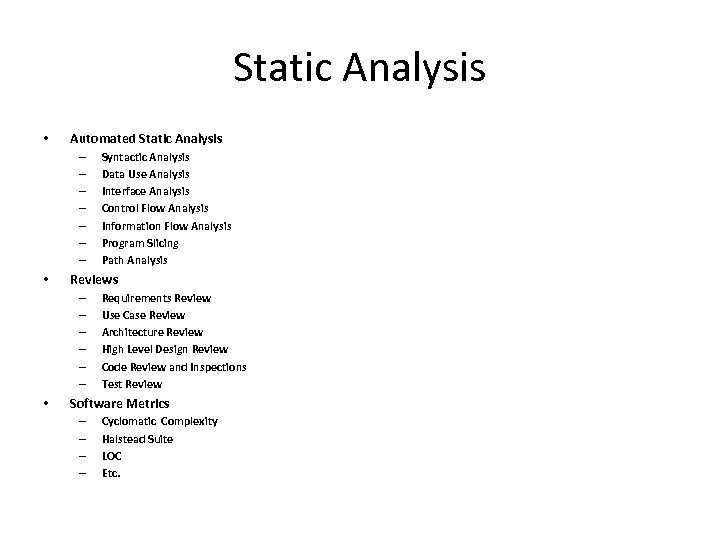 Static Analysis • Automated Static Analysis – – – – • Reviews – – – • Syntactic Analysis Data Use Analysis Interface Analysis Control Flow Analysis Information Flow Analysis Program Slicing Path Analysis Requirements Review Use Case Review Architecture Review High Level Design Review Code Review and Inspections Test Review Software Metrics – – Cyclomatic Complexity Halstead Suite LOC Etc.
Static Analysis • Automated Static Analysis – – – – • Reviews – – – • Syntactic Analysis Data Use Analysis Interface Analysis Control Flow Analysis Information Flow Analysis Program Slicing Path Analysis Requirements Review Use Case Review Architecture Review High Level Design Review Code Review and Inspections Test Review Software Metrics – – Cyclomatic Complexity Halstead Suite LOC Etc.
 Automated Static Analysis Analyzes your program without executing it • Doesn’t depend on having good test cases or even any test cases • Generally, doesn’t know what your software is supposed to do • Looks for violations of reasonable programming – Shouldn’t throw NPE – Shouldn’t allow SQL injection • Not a replacement for testing • Very good at finding problems on untested paths • But many defects can’t be found with static analysis
Automated Static Analysis Analyzes your program without executing it • Doesn’t depend on having good test cases or even any test cases • Generally, doesn’t know what your software is supposed to do • Looks for violations of reasonable programming – Shouldn’t throw NPE – Shouldn’t allow SQL injection • Not a replacement for testing • Very good at finding problems on untested paths • But many defects can’t be found with static analysis
 Can you Find the Bug? if (listeners == null) listeners. remove(listener); JDK 1. 6. 0, b 105, sun. awt. x 11. XMSelection lines 243 -244
Can you Find the Bug? if (listeners == null) listeners. remove(listener); JDK 1. 6. 0, b 105, sun. awt. x 11. XMSelection lines 243 -244
 Can you Find the Bug? 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 import java. io. Input. Stream. Reader; import java. io. Buffered. Reader; import java. io. IOException; public class Coding. Horror { public static void main(String args[]) { Input. Stream. Reader isr = new Input. Stream. Reader(System. in); Buffered. Reader br = new Buffered. Reader(isr); String input = null; try { input = br. read. Line(); // e. g. , peel } catch (IOException ioex) { System. err. println(ioex. get. Message()); } input. replace(‘e’, ‘o’); if (input == “pool”) { System. out. println(“User entered peel. ”); } else { System. out. println(“User entered something else. ”); } } }
Can you Find the Bug? 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 import java. io. Input. Stream. Reader; import java. io. Buffered. Reader; import java. io. IOException; public class Coding. Horror { public static void main(String args[]) { Input. Stream. Reader isr = new Input. Stream. Reader(System. in); Buffered. Reader br = new Buffered. Reader(isr); String input = null; try { input = br. read. Line(); // e. g. , peel } catch (IOException ioex) { System. err. println(ioex. get. Message()); } input. replace(‘e’, ‘o’); if (input == “pool”) { System. out. println(“User entered peel. ”); } else { System. out. println(“User entered something else. ”); } } }
 What is the Bug here? /** Construct a Web. Spider */ public Web. Spider() { Web. Spider w = new Web. Spider(); }
What is the Bug here? /** Construct a Web. Spider */ public Web. Spider() { Web. Spider w = new Web. Spider(); }
 What is the Bug here? public String found. Type() { return this. found. Type(); }
What is the Bug here? public String found. Type() { return this. found. Type(); }
 Why do Bugs Occur? Nobody is perfect • Common types of errors: • Misunderstood language features, API methods • Typos (using wrong boolean operator, forgetting parentheses or brackets, etc. ) • Misunderstood class or method invariants • Everyone makes syntax errors, but the compiler catches them • What about bugs one step removed from a syntax error?
Why do Bugs Occur? Nobody is perfect • Common types of errors: • Misunderstood language features, API methods • Typos (using wrong boolean operator, forgetting parentheses or brackets, etc. ) • Misunderstood class or method invariants • Everyone makes syntax errors, but the compiler catches them • What about bugs one step removed from a syntax error?
 What is Static Testing • Static testing is using static analysis as part of the test trajectory • Static and Dynamic testing are supplementary – static analysis does not replace dynamic testing but can significantly reduce dynamic testing effort • Static testing achieves 100% statement coverage • Including explicit static analysis in test coverage: – Improves overall test quality and test planning – Results in shorter dynamic testing time – Allows stronger focus testing on complex and crucial modules
What is Static Testing • Static testing is using static analysis as part of the test trajectory • Static and Dynamic testing are supplementary – static analysis does not replace dynamic testing but can significantly reduce dynamic testing effort • Static testing achieves 100% statement coverage • Including explicit static analysis in test coverage: – Improves overall test quality and test planning – Results in shorter dynamic testing time – Allows stronger focus testing on complex and crucial modules
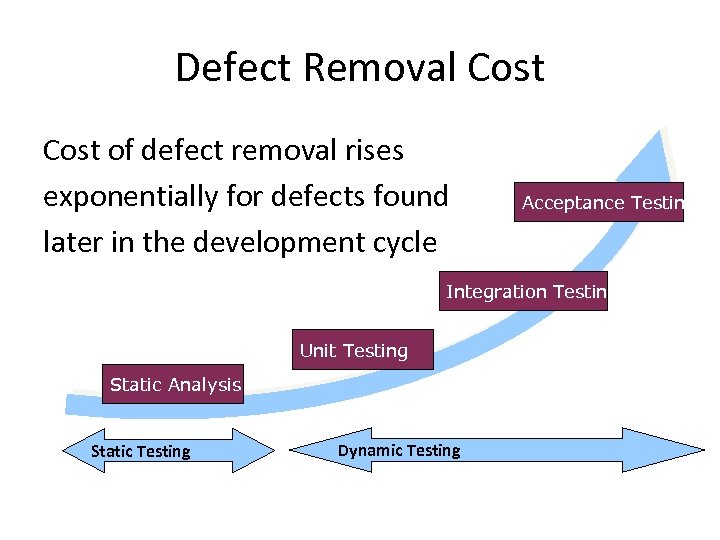 Defect Removal Cost of defect removal rises exponentially for defects found later in the development cycle Acceptance Testing Integration Testing Unit Testing Static Analysis Static Testing Dynamic Testing
Defect Removal Cost of defect removal rises exponentially for defects found later in the development cycle Acceptance Testing Integration Testing Unit Testing Static Analysis Static Testing Dynamic Testing
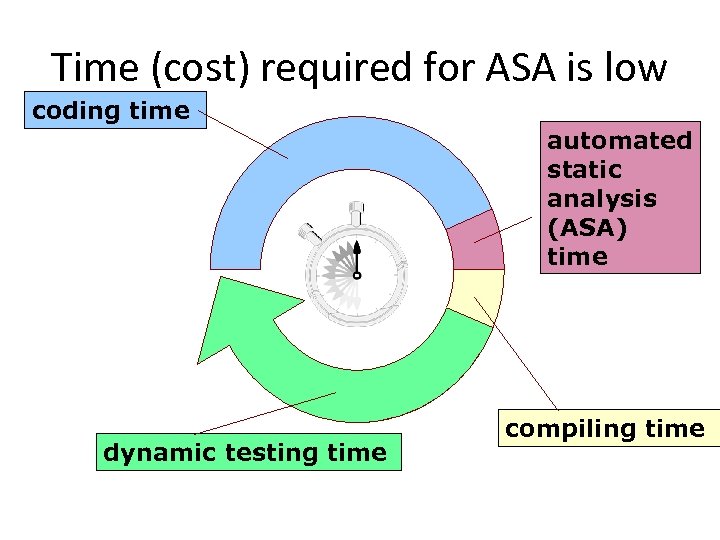 Time (cost) required for ASA is low coding time automated static analysis (ASA) time dynamic testing time compiling time
Time (cost) required for ASA is low coding time automated static analysis (ASA) time dynamic testing time compiling time
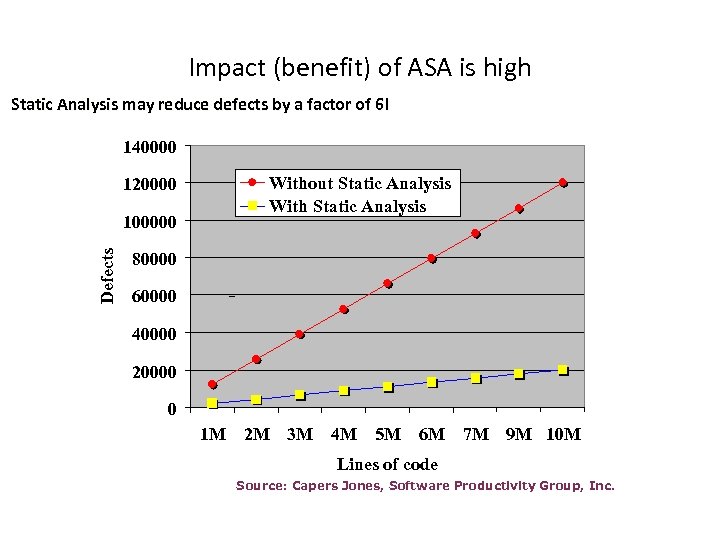 Impact (benefit) of ASA is high Static Analysis may reduce defects by a factor of 6! 140000 Without Static Analysis With Static Analysis 120000 Defects 100000 80000 60000 40000 20000 0 1 M 2 M 3 M 4 M 5 M 6 M 7 M 9 M 10 M Lines of code Source: Capers Jones, Software Productivity Group, Inc.
Impact (benefit) of ASA is high Static Analysis may reduce defects by a factor of 6! 140000 Without Static Analysis With Static Analysis 120000 Defects 100000 80000 60000 40000 20000 0 1 M 2 M 3 M 4 M 5 M 6 M 7 M 9 M 10 M Lines of code Source: Capers Jones, Software Productivity Group, Inc.
 Software Manager Findings on Static Analysis • We proved the tight relationship between static analysis and the reduction of support efforts on released software products. Dr. Thomas Liedtke and Dr. Christian Ebert Alcatel AG in Stuttgart, Germany On the Benefits of Reinforcing Code Inspection Activities, Euro. Star 1995
Software Manager Findings on Static Analysis • We proved the tight relationship between static analysis and the reduction of support efforts on released software products. Dr. Thomas Liedtke and Dr. Christian Ebert Alcatel AG in Stuttgart, Germany On the Benefits of Reinforcing Code Inspection Activities, Euro. Star 1995
 Analyst Findings on Static Analysis • 60% of the software faults that were found in released software products could have been detected by means of static analysis Bloor Research Ltd. , UK CAST Tools report of 1996
Analyst Findings on Static Analysis • 60% of the software faults that were found in released software products could have been detected by means of static analysis Bloor Research Ltd. , UK CAST Tools report of 1996
 Researcher Findings on Static Analysis • On average, 40% of the faults that could be found through static analysis will eventually become a defect in the field. Professor Dr. Les Hatton, University of Kent
Researcher Findings on Static Analysis • On average, 40% of the faults that could be found through static analysis will eventually become a defect in the field. Professor Dr. Les Hatton, University of Kent
 Stages of Automated Static Analysis • • Syntactic Analysis Data Use Analysis Control Flow Analysis Interface Analysis Program Slicing Information Flow Analysis Path Analysis
Stages of Automated Static Analysis • • Syntactic Analysis Data Use Analysis Control Flow Analysis Interface Analysis Program Slicing Information Flow Analysis Path Analysis
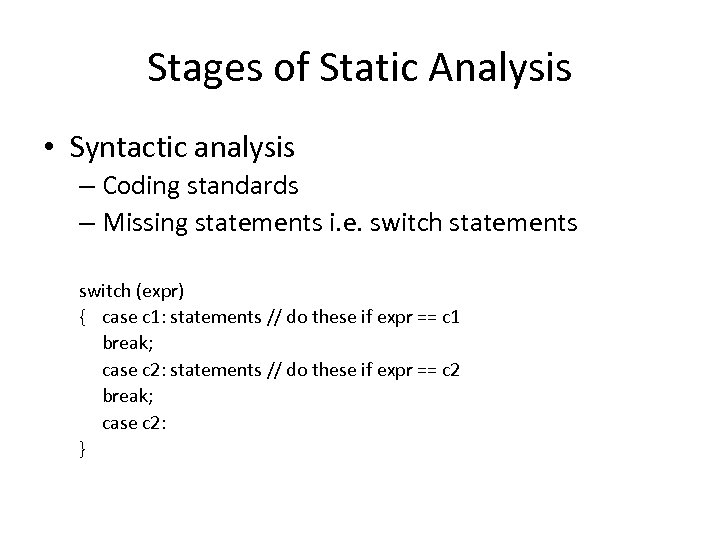 Stages of Static Analysis • Syntactic analysis – Coding standards – Missing statements i. e. switch statements switch (expr) { case c 1: statements // do these if expr == c 1 break; case c 2: statements // do these if expr == c 2 break; case c 2: }
Stages of Static Analysis • Syntactic analysis – Coding standards – Missing statements i. e. switch statements switch (expr) { case c 1: statements // do these if expr == c 1 break; case c 2: statements // do these if expr == c 2 break; case c 2: }
 What is the Error in this Code? class Test. Resource. Leak { public Core. Response process(Entit entity) throws Resource. Exception { Core. Response coreresponse = new Core. Response(); Database. Connection dbcon = new Database. Connection(); Connection con 1 = null; Connection con 2 = null; //getting the Data Base Connection try { con 1 = dbcon. get. Connection(); con 2 = dbcon. get. Connection(); . . . } catch(Exception e) { con 1. close(); throw new Resource. Exception(e. get. Message(), e) ; } con 1. close(); return coreresponse; } }
What is the Error in this Code? class Test. Resource. Leak { public Core. Response process(Entit entity) throws Resource. Exception { Core. Response coreresponse = new Core. Response(); Database. Connection dbcon = new Database. Connection(); Connection con 1 = null; Connection con 2 = null; //getting the Data Base Connection try { con 1 = dbcon. get. Connection(); con 2 = dbcon. get. Connection(); . . . } catch(Exception e) { con 1. close(); throw new Resource. Exception(e. get. Message(), e) ; } con 1. close(); return coreresponse; } }
 Data Use Analysis • Aim is to identify data flows that do not conform to sound programming practices, e. g. variables are not read before they are written; inactive code. • A purely symbolic form of analysis, i. e. no specific data values are considered. • Based upon a number of relationships between variables and expressions. • Process involves annotating a program flow graph with each data object definition (D), usage (U) and elimination (E). • Analysis involves flow graph traversal, e. g. DD paths suggest redundancy, DE paths are most likely to be bugs.
Data Use Analysis • Aim is to identify data flows that do not conform to sound programming practices, e. g. variables are not read before they are written; inactive code. • A purely symbolic form of analysis, i. e. no specific data values are considered. • Based upon a number of relationships between variables and expressions. • Process involves annotating a program flow graph with each data object definition (D), usage (U) and elimination (E). • Analysis involves flow graph traversal, e. g. DD paths suggest redundancy, DE paths are most likely to be bugs.
 Control Flow Analysis • Aim is to detect poorly structured code, e. g. multiple exits from a loop, dead code etc • Process again typically involves translating the program into a flow graph. • By a process of repeated reduction inaccessible code and certain classes of nontermination can be identified
Control Flow Analysis • Aim is to detect poorly structured code, e. g. multiple exits from a loop, dead code etc • Process again typically involves translating the program into a flow graph. • By a process of repeated reduction inaccessible code and certain classes of nontermination can be identified
 Program Slicing • Program slicing involves focusing on a particular subset of variables within a given program. • The parts of the program that are relevant to the subset of variables denotes a program slice. • Some applications: – Program testing & re-testing: provides focus with respect to test case design and the selection of regression tests. – Program comprehension: slicing provides a useful aid to understanding code where no documentation exists.
Program Slicing • Program slicing involves focusing on a particular subset of variables within a given program. • The parts of the program that are relevant to the subset of variables denotes a program slice. • Some applications: – Program testing & re-testing: provides focus with respect to test case design and the selection of regression tests. – Program comprehension: slicing provides a useful aid to understanding code where no documentation exists.
 Types of program Slicing • Backward: – For a given statement S, a backward slice through a program contains all statements that effect whether control reaches S and also all statements that effect the value of variables that occur in S. • Forward: – For a given statement S, a forward slice through a program contains all statements that are affected by S. • Static: – A static program slice is calculated symbolically, i. e. takes no account of concrete data values. • Dynamic: – A dynamic program slice is calculated based upon particular data values. Note that forward and backward slices can be calculated either statically or dynamically.
Types of program Slicing • Backward: – For a given statement S, a backward slice through a program contains all statements that effect whether control reaches S and also all statements that effect the value of variables that occur in S. • Forward: – For a given statement S, a forward slice through a program contains all statements that are affected by S. • Static: – A static program slice is calculated symbolically, i. e. takes no account of concrete data values. • Dynamic: – A dynamic program slice is calculated based upon particular data values. Note that forward and backward slices can be calculated either statically or dynamically.
 Program Slicing Example Program read(X); read(Y); Q : = 0; R : = X; while R >= Y do begin R : = R - Y; Q : = Q + 1 end; print(Q); print(R); A Program Slice read(X); read(Y); R : = X; while R >= Y do begin R : = R - Y; end; print(R); Program Slice for the variable ‘R’
Program Slicing Example Program read(X); read(Y); Q : = 0; R : = X; while R >= Y do begin R : = R - Y; Q : = Q + 1 end; print(Q); print(R); A Program Slice read(X); read(Y); R : = X; while R >= Y do begin R : = R - Y; end; print(R); Program Slice for the variable ‘R’
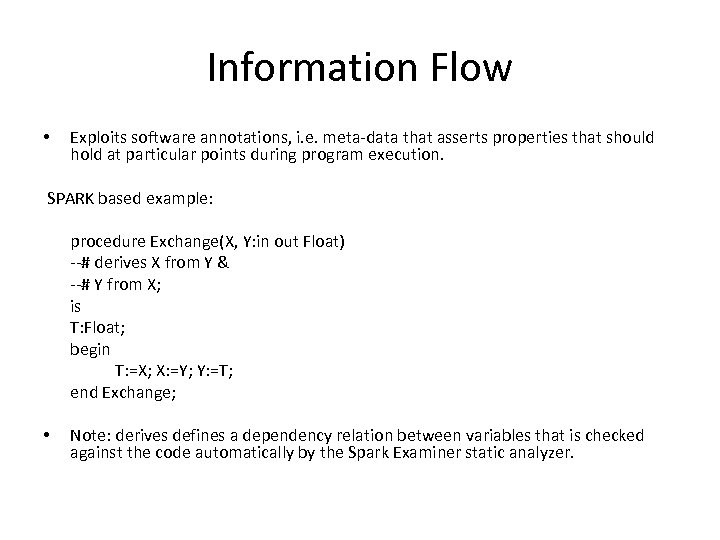 Information Flow • Exploits software annotations, i. e. meta-data that asserts properties that should hold at particular points during program execution. SPARK based example: procedure Exchange(X, Y: in out Float) --# derives X from Y & --# Y from X; is T: Float; begin T: =X; X: =Y; Y: =T; end Exchange; • Note: derives defines a dependency relation between variables that is checked against the code automatically by the Spark Examiner static analyzer.
Information Flow • Exploits software annotations, i. e. meta-data that asserts properties that should hold at particular points during program execution. SPARK based example: procedure Exchange(X, Y: in out Float) --# derives X from Y & --# Y from X; is T: Float; begin T: =X; X: =Y; Y: =T; end Exchange; • Note: derives defines a dependency relation between variables that is checked against the code automatically by the Spark Examiner static analyzer.
 Use of Static Analysis in Secure Coding • Security Vulnerabilities: – Cross-site Scripting (XSS) – SQL Injection – Command Injection – Buffer Overflows – Memory Leaks – Integer Overflows
Use of Static Analysis in Secure Coding • Security Vulnerabilities: – Cross-site Scripting (XSS) – SQL Injection – Command Injection – Buffer Overflows – Memory Leaks – Integer Overflows
 Find. Bugs JDK 1. 6. 0 -b 105 • 379 correctness warnings • we judge that at least 213 of these are serious issues that should be fixed Google's Java codebase • over a 6 month period, using various versions of Find. Bugs • 1, 127 warnings • 807 filed as bugs • 518 fixed in code
Find. Bugs JDK 1. 6. 0 -b 105 • 379 correctness warnings • we judge that at least 213 of these are serious issues that should be fixed Google's Java codebase • over a 6 month period, using various versions of Find. Bugs • 1, 127 warnings • 807 filed as bugs • 518 fixed in code


