5aa8acabe9aabb292d1299f3e30cea43.ppt
- Количество слайдов: 43
 What is network security? Confidentiality: only sender, intended receiver should “understand” message contents m sender encrypts message m receiver decrypts message Authentication: sender, receiver want to confirm identity of each other Message integrity: sender, receiver want to ensure message not altered (in transit, or afterwards) without detection Access and availability: services must be accessible and available to users 8: Network Security 8 -1
What is network security? Confidentiality: only sender, intended receiver should “understand” message contents m sender encrypts message m receiver decrypts message Authentication: sender, receiver want to confirm identity of each other Message integrity: sender, receiver want to ensure message not altered (in transit, or afterwards) without detection Access and availability: services must be accessible and available to users 8: Network Security 8 -1
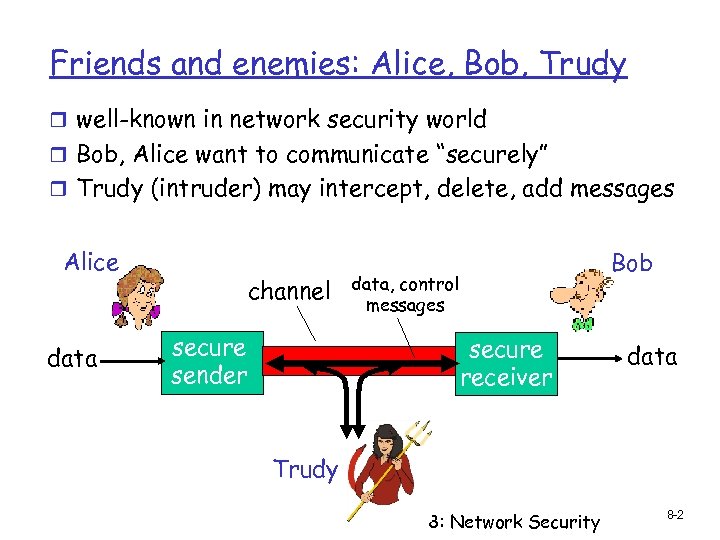 Friends and enemies: Alice, Bob, Trudy r well-known in network security world r Bob, Alice want to communicate “securely” r Trudy (intruder) may intercept, delete, add messages Alice data channel secure sender Bob data, control messages secure receiver data Trudy 8: Network Security 8 -2
Friends and enemies: Alice, Bob, Trudy r well-known in network security world r Bob, Alice want to communicate “securely” r Trudy (intruder) may intercept, delete, add messages Alice data channel secure sender Bob data, control messages secure receiver data Trudy 8: Network Security 8 -2
 Who might Bob, Alice be? r … well, real-life Bobs and Alices! r Web browser/server for electronic transactions (e. g. , on-line purchases) r on-line banking client/server r DNS servers r routers exchanging routing table updates r other examples? 8: Network Security 8 -3
Who might Bob, Alice be? r … well, real-life Bobs and Alices! r Web browser/server for electronic transactions (e. g. , on-line purchases) r on-line banking client/server r DNS servers r routers exchanging routing table updates r other examples? 8: Network Security 8 -3
 There are bad guys (and girls) out there! Q: What can a “bad guy” do? A: a lot! m eavesdrop: intercept messages m actively insert messages into connection m impersonation: can fake (spoof) source address in packet (or any field in packet) m hijacking: “take over” ongoing connection by removing sender or receiver, inserting himself in place m denial of service: prevent service from being used by others (e. g. , by overloading resources) more on this later …… 8: Network Security 8 -4
There are bad guys (and girls) out there! Q: What can a “bad guy” do? A: a lot! m eavesdrop: intercept messages m actively insert messages into connection m impersonation: can fake (spoof) source address in packet (or any field in packet) m hijacking: “take over” ongoing connection by removing sender or receiver, inserting himself in place m denial of service: prevent service from being used by others (e. g. , by overloading resources) more on this later …… 8: Network Security 8 -4
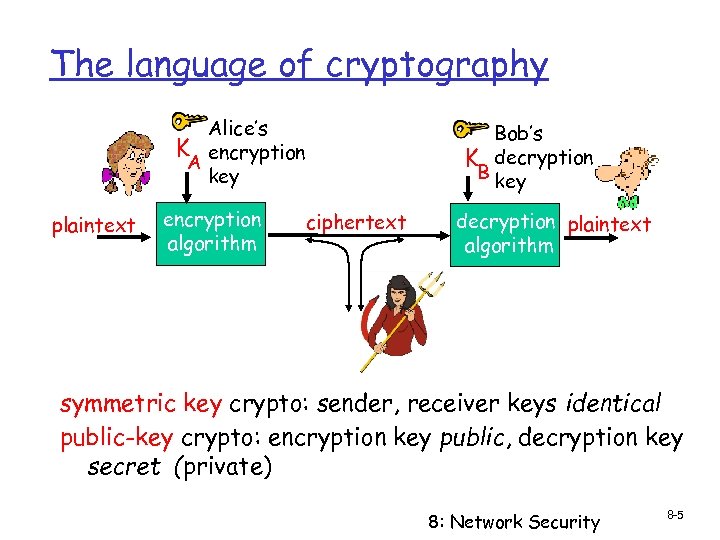 The language of cryptography Alice’s K encryption A key plaintext encryption algorithm Bob’s K decryption B key ciphertext decryption plaintext algorithm symmetric key crypto: sender, receiver keys identical public-key crypto: encryption key public, decryption key secret (private) 8: Network Security 8 -5
The language of cryptography Alice’s K encryption A key plaintext encryption algorithm Bob’s K decryption B key ciphertext decryption plaintext algorithm symmetric key crypto: sender, receiver keys identical public-key crypto: encryption key public, decryption key secret (private) 8: Network Security 8 -5
 Symmetric key cryptography substitution cipher: substituting one thing for another m monoalphabetic cipher: substitute one letter for another plaintext: abcdefghijklmnopqrstuvwxyz ciphertext: mnbvcxzasdfghjklpoiuytrewq E. g. : Plaintext: bob. i love you. alice ciphertext: nkn. s gktc wky. mgsbc Q: How hard to break this simple cipher? : q brute force (how hard? ) q other? 8: Network Security 8 -6
Symmetric key cryptography substitution cipher: substituting one thing for another m monoalphabetic cipher: substitute one letter for another plaintext: abcdefghijklmnopqrstuvwxyz ciphertext: mnbvcxzasdfghjklpoiuytrewq E. g. : Plaintext: bob. i love you. alice ciphertext: nkn. s gktc wky. mgsbc Q: How hard to break this simple cipher? : q brute force (how hard? ) q other? 8: Network Security 8 -6
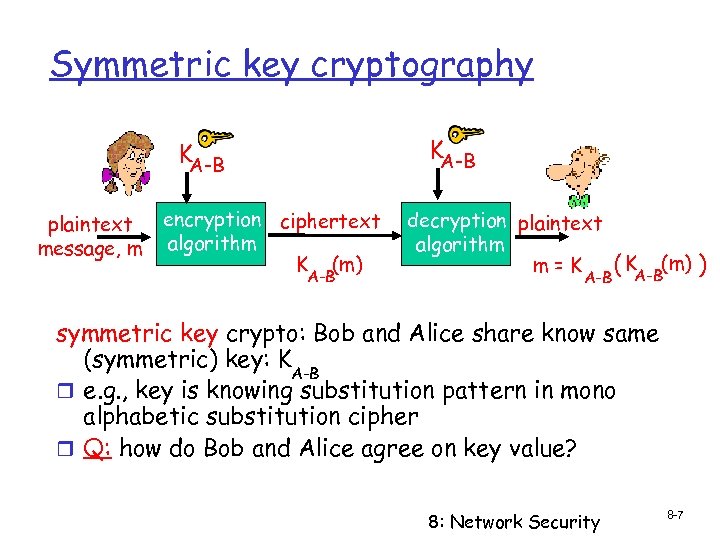 Symmetric key cryptography KA-B plaintext message, m encryption ciphertext algorithm K (m) A-B decryption plaintext algorithm m=K A-B ( KA-B(m) ) symmetric key crypto: Bob and Alice share know same (symmetric) key: K A-B r e. g. , key is knowing substitution pattern in mono alphabetic substitution cipher r Q: how do Bob and Alice agree on key value? 8: Network Security 8 -7
Symmetric key cryptography KA-B plaintext message, m encryption ciphertext algorithm K (m) A-B decryption plaintext algorithm m=K A-B ( KA-B(m) ) symmetric key crypto: Bob and Alice share know same (symmetric) key: K A-B r e. g. , key is knowing substitution pattern in mono alphabetic substitution cipher r Q: how do Bob and Alice agree on key value? 8: Network Security 8 -7
![Symmetric key crypto: DES: Data Encryption Standard r US encryption standard [NIST 1993] r Symmetric key crypto: DES: Data Encryption Standard r US encryption standard [NIST 1993] r](https://present5.com/presentation/5aa8acabe9aabb292d1299f3e30cea43/image-8.jpg) Symmetric key crypto: DES: Data Encryption Standard r US encryption standard [NIST 1993] r 56 -bit symmetric key, 64 -bit plaintext input r How secure is DES? m DES Challenge: 56 -bit-key-encrypted phrase (“Strong cryptography makes the world a safer place”) decrypted (brute force) in 4 months r making DES more secure: m use three keys sequentially (3 -DES) on each datum m use cipher-block chaining 8: Network Security 8 -8
Symmetric key crypto: DES: Data Encryption Standard r US encryption standard [NIST 1993] r 56 -bit symmetric key, 64 -bit plaintext input r How secure is DES? m DES Challenge: 56 -bit-key-encrypted phrase (“Strong cryptography makes the world a safer place”) decrypted (brute force) in 4 months r making DES more secure: m use three keys sequentially (3 -DES) on each datum m use cipher-block chaining 8: Network Security 8 -8
 AES: Advanced Encryption Standard r new (Nov. 2001) symmetric-key NIST standard, replacing DES r processes data in 128 bit blocks r 128, 192, or 256 bit keys r brute force decryption (try each key) taking 1 sec on DES, takes 149 trillion years for AES r block ciphers: DES, 3 DES, Blowfish, AES 8: Network Security 8 -9
AES: Advanced Encryption Standard r new (Nov. 2001) symmetric-key NIST standard, replacing DES r processes data in 128 bit blocks r 128, 192, or 256 bit keys r brute force decryption (try each key) taking 1 sec on DES, takes 149 trillion years for AES r block ciphers: DES, 3 DES, Blowfish, AES 8: Network Security 8 -9
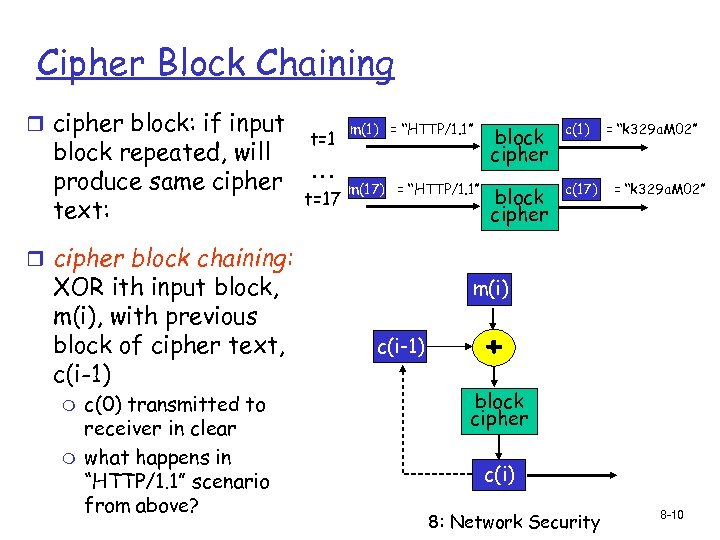 Cipher Block Chaining r cipher block: if input block repeated, will produce same cipher text: t=1 … t=17 m(1) = “HTTP/1. 1” block cipher c(1) m(17) = “HTTP/1. 1” block cipher c(17) = “k 329 a. M 02” r cipher block chaining: XOR ith input block, m(i), with previous block of cipher text, c(i-1) m m c(0) transmitted to receiver in clear what happens in “HTTP/1. 1” scenario from above? m(i) c(i-1) + block cipher c(i) 8: Network Security 8 -10
Cipher Block Chaining r cipher block: if input block repeated, will produce same cipher text: t=1 … t=17 m(1) = “HTTP/1. 1” block cipher c(1) m(17) = “HTTP/1. 1” block cipher c(17) = “k 329 a. M 02” r cipher block chaining: XOR ith input block, m(i), with previous block of cipher text, c(i-1) m m c(0) transmitted to receiver in clear what happens in “HTTP/1. 1” scenario from above? m(i) c(i-1) + block cipher c(i) 8: Network Security 8 -10
 Public key cryptography symmetric key crypto r requires sender, receiver know shared secret key r Q: how to agree on key in first place (particularly if never “met”)? public key cryptography r radically different approach [Diffie. Hellman 76, RSA 78] r sender, receiver do not share secret key r public encryption key known to all r private decryption key known only to receiver 8: Network Security 8 -11
Public key cryptography symmetric key crypto r requires sender, receiver know shared secret key r Q: how to agree on key in first place (particularly if never “met”)? public key cryptography r radically different approach [Diffie. Hellman 76, RSA 78] r sender, receiver do not share secret key r public encryption key known to all r private decryption key known only to receiver 8: Network Security 8 -11
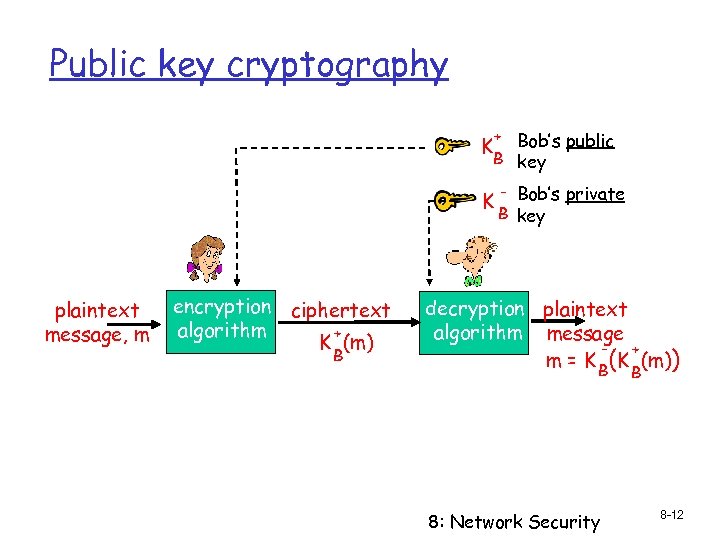 Public key cryptography + Bob’s public B key K K plaintext message, m encryption ciphertext algorithm + K (m) B - Bob’s private B key decryption plaintext algorithm message + m = K B(K (m)) B 8: Network Security 8 -12
Public key cryptography + Bob’s public B key K K plaintext message, m encryption ciphertext algorithm + K (m) B - Bob’s private B key decryption plaintext algorithm message + m = K B(K (m)) B 8: Network Security 8 -12
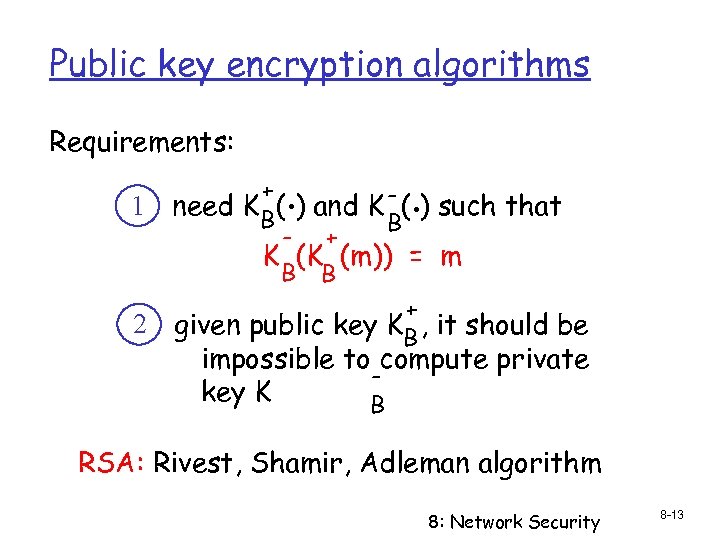 Public key encryption algorithms Requirements: 1 2 . . + need K B( ) and K - ( ) such that B - + K (K (m)) = m B B + given public key KB , it should be impossible to compute private key K B RSA: Rivest, Shamir, Adleman algorithm 8: Network Security 8 -13
Public key encryption algorithms Requirements: 1 2 . . + need K B( ) and K - ( ) such that B - + K (K (m)) = m B B + given public key KB , it should be impossible to compute private key K B RSA: Rivest, Shamir, Adleman algorithm 8: Network Security 8 -13
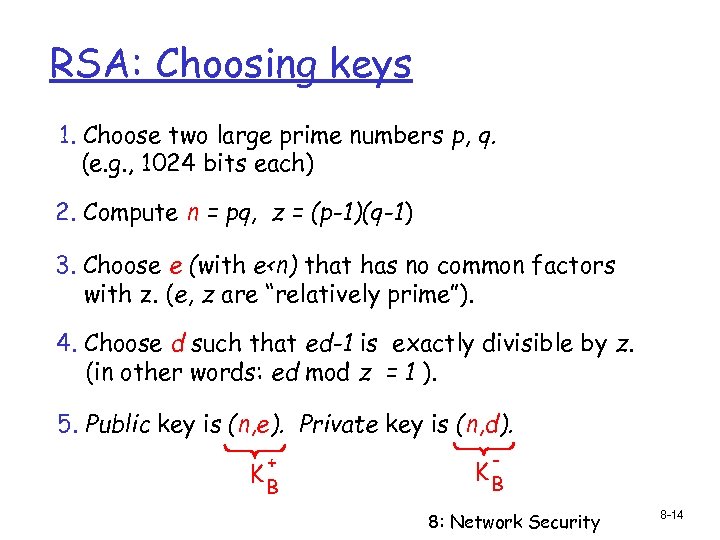 RSA: Choosing keys 1. Choose two large prime numbers p, q. (e. g. , 1024 bits each) 2. Compute n = pq, z = (p-1)(q-1) 3. Choose e (with e
RSA: Choosing keys 1. Choose two large prime numbers p, q. (e. g. , 1024 bits each) 2. Compute n = pq, z = (p-1)(q-1) 3. Choose e (with e
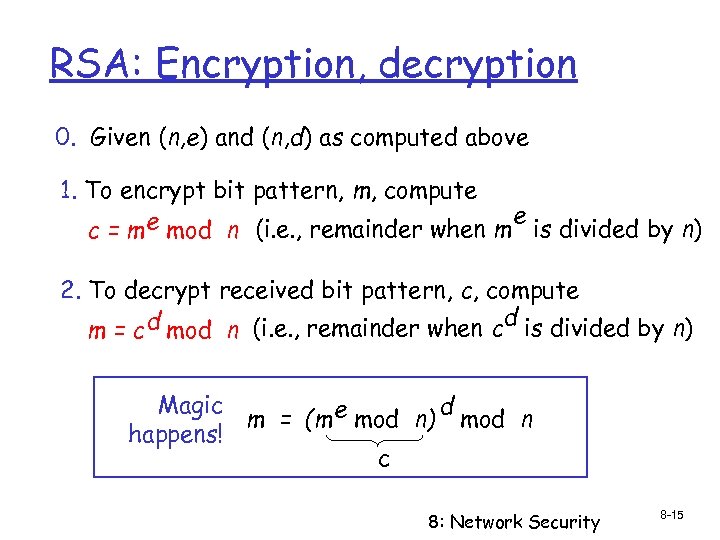 RSA: Encryption, decryption 0. Given (n, e) and (n, d) as computed above 1. To encrypt bit pattern, m, compute e mod n (i. e. , remainder when m e is divided by n) c=m 2. To decrypt received bit pattern, c, compute d m = c d mod n (i. e. , remainder when c is divided by n) Magic d m = (m e mod n) mod n happens! c 8: Network Security 8 -15
RSA: Encryption, decryption 0. Given (n, e) and (n, d) as computed above 1. To encrypt bit pattern, m, compute e mod n (i. e. , remainder when m e is divided by n) c=m 2. To decrypt received bit pattern, c, compute d m = c d mod n (i. e. , remainder when c is divided by n) Magic d m = (m e mod n) mod n happens! c 8: Network Security 8 -15
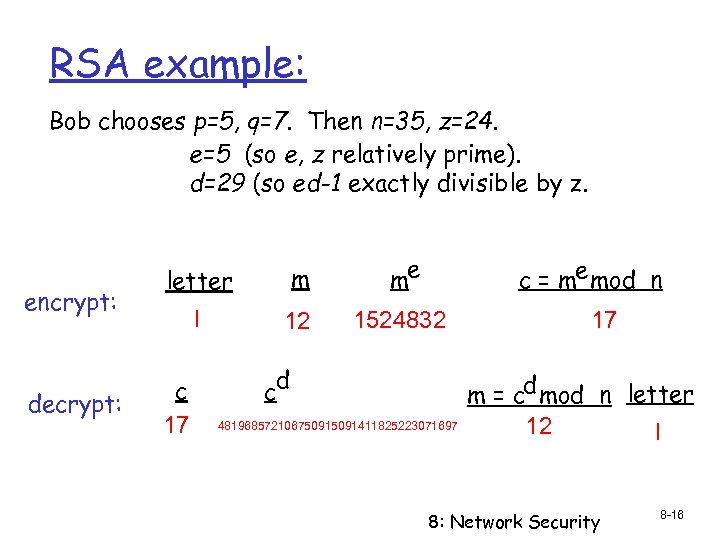 RSA example: Bob chooses p=5, q=7. Then n=35, z=24. e=5 (so e, z relatively prime). d=29 (so ed-1 exactly divisible by z. encrypt: decrypt: letter m me l 12 1524832 c 17 c = me mod n d c 48196857210675091411825223071697 17 m = cd mod n letter 12 l 8: Network Security 8 -16
RSA example: Bob chooses p=5, q=7. Then n=35, z=24. e=5 (so e, z relatively prime). d=29 (so ed-1 exactly divisible by z. encrypt: decrypt: letter m me l 12 1524832 c 17 c = me mod n d c 48196857210675091411825223071697 17 m = cd mod n letter 12 l 8: Network Security 8 -16
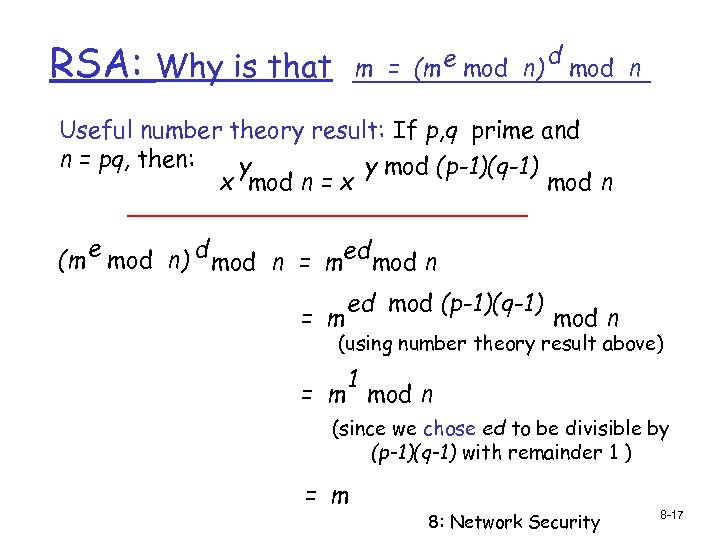 RSA: m = (m e mod n) Why is that d mod n Useful number theory result: If p, q prime and n = pq, then: y y mod (p-1)(q-1) x mod n = x mod n e (m mod n) d mod n = med mod n = m ed mod (p-1)(q-1) mod n (using number theory result above) 1 = m mod n (since we chose ed to be divisible by (p-1)(q-1) with remainder 1 ) = m 8: Network Security 8 -17
RSA: m = (m e mod n) Why is that d mod n Useful number theory result: If p, q prime and n = pq, then: y y mod (p-1)(q-1) x mod n = x mod n e (m mod n) d mod n = med mod n = m ed mod (p-1)(q-1) mod n (using number theory result above) 1 = m mod n (since we chose ed to be divisible by (p-1)(q-1) with remainder 1 ) = m 8: Network Security 8 -17
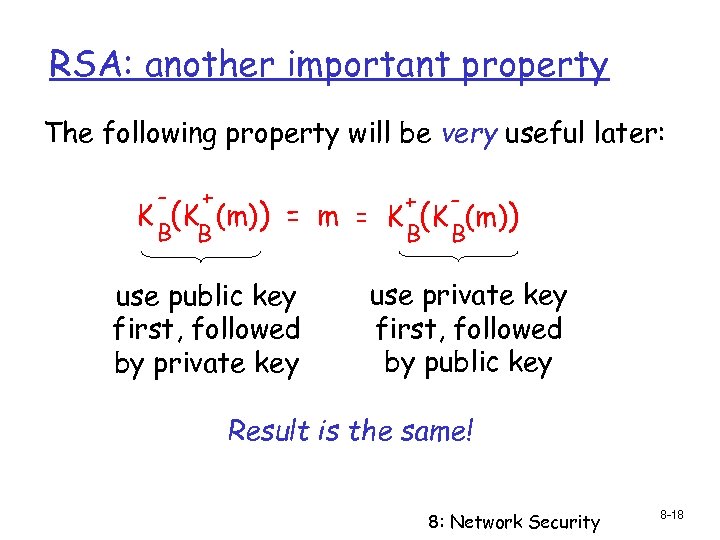 RSA: another important property The following property will be very useful later: - + B B K (K (m)) + = m = K (K (m)) B B use public key first, followed by private key use private key first, followed by public key Result is the same! 8: Network Security 8 -18
RSA: another important property The following property will be very useful later: - + B B K (K (m)) + = m = K (K (m)) B B use public key first, followed by private key use private key first, followed by public key Result is the same! 8: Network Security 8 -18
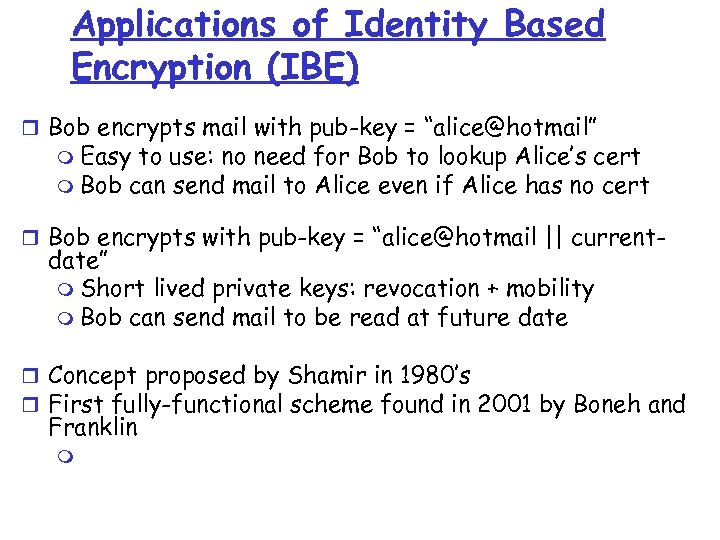 Applications of Identity Based Encryption (IBE) r Bob encrypts mail with pub-key = “alice@hotmail” m Easy to use: no need for Bob to lookup Alice’s cert m Bob can send mail to Alice even if Alice has no cert r Bob encrypts with pub-key = “alice@hotmail || current- date” m Short lived private keys: revocation + mobility m Bob can send mail to be read at future date r Concept proposed by Shamir in 1980’s r First fully-functional scheme found in 2001 by Boneh and Franklin m
Applications of Identity Based Encryption (IBE) r Bob encrypts mail with pub-key = “alice@hotmail” m Easy to use: no need for Bob to lookup Alice’s cert m Bob can send mail to Alice even if Alice has no cert r Bob encrypts with pub-key = “alice@hotmail || current- date” m Short lived private keys: revocation + mobility m Bob can send mail to be read at future date r Concept proposed by Shamir in 1980’s r First fully-functional scheme found in 2001 by Boneh and Franklin m
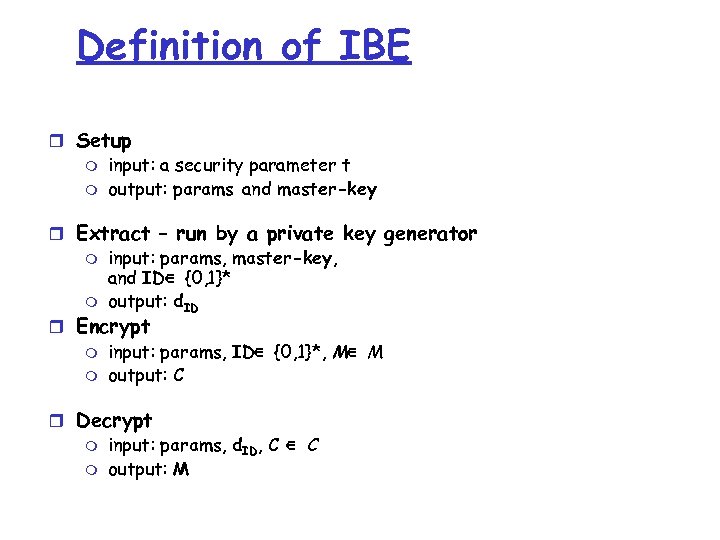 Definition of IBE r Setup m input: a security parameter t m output: params and master-key r Extract – run by a private key generator m input: params, master-key, and ID∈ {0, 1}* m output: d. ID r Encrypt m input: params, ID∈ {0, 1}*, M∈ M m output: C r Decrypt m input: params, d. ID, C ∈ C m output: M
Definition of IBE r Setup m input: a security parameter t m output: params and master-key r Extract – run by a private key generator m input: params, master-key, and ID∈ {0, 1}* m output: d. ID r Encrypt m input: params, ID∈ {0, 1}*, M∈ M m output: C r Decrypt m input: params, d. ID, C ∈ C m output: M
 Security properties of Crypto schemes r Formalization of the notion that no algorithm breaks a crypto system m m defined via a game between an Adversary and a Challenger no polynomially bound Adversary wins the game with nonnegligible advantage r Semantic security against a chosen ciphertext attack m No polynomially bound adversary wins the following game with non-negligible advantage
Security properties of Crypto schemes r Formalization of the notion that no algorithm breaks a crypto system m m defined via a game between an Adversary and a Challenger no polynomially bound Adversary wins the game with nonnegligible advantage r Semantic security against a chosen ciphertext attack m No polynomially bound adversary wins the following game with non-negligible advantage
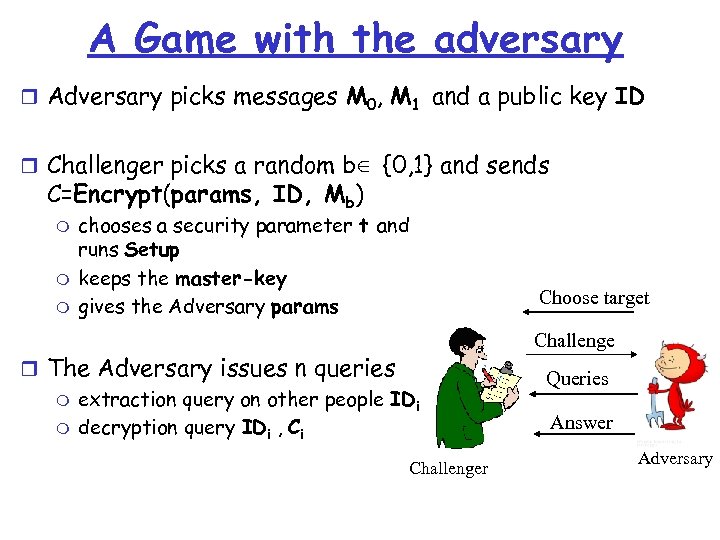 A Game with the adversary r Adversary picks messages M 0, M 1 and a public key ID r Challenger picks a random b∈ {0, 1} and sends C=Encrypt(params, ID, Mb) m m m chooses a security parameter t and runs Setup keeps the master-key gives the Adversary params r The Adversary issues n queries m extraction query on other people IDi m decryption query IDi , Ci Challenger Choose target Challenge Queries Answer Adversary
A Game with the adversary r Adversary picks messages M 0, M 1 and a public key ID r Challenger picks a random b∈ {0, 1} and sends C=Encrypt(params, ID, Mb) m m m chooses a security parameter t and runs Setup keeps the master-key gives the Adversary params r The Adversary issues n queries m extraction query on other people IDi m decryption query IDi , Ci Challenger Choose target Challenge Queries Answer Adversary
 The Game cont’d r The Adversary outputs b’ r The Adversary wins if b=b’ | Prob (the attacker wins) – ½ | should be negligible This game can be made adaptive to model a stronger adversary
The Game cont’d r The Adversary outputs b’ r The Adversary wins if b=b’ | Prob (the attacker wins) – ½ | should be negligible This game can be made adaptive to model a stronger adversary
 Message Integrity Bob receives msg from Alice, wants to ensure: r message originally came from Alice r message not changed since sent by Alice Cryptographic Hash: r takes input m, produces fixed length value, H(m) m e. g. , as in Internet checksum r computationally infeasible to find two different messages, x, y such that H(x) = H(y) m m equivalently: given m = H(x), (x unknown), can not determine x. note: Internet checksum fails this requirement! 8: Network Security 8 -24
Message Integrity Bob receives msg from Alice, wants to ensure: r message originally came from Alice r message not changed since sent by Alice Cryptographic Hash: r takes input m, produces fixed length value, H(m) m e. g. , as in Internet checksum r computationally infeasible to find two different messages, x, y such that H(x) = H(y) m m equivalently: given m = H(x), (x unknown), can not determine x. note: Internet checksum fails this requirement! 8: Network Security 8 -24
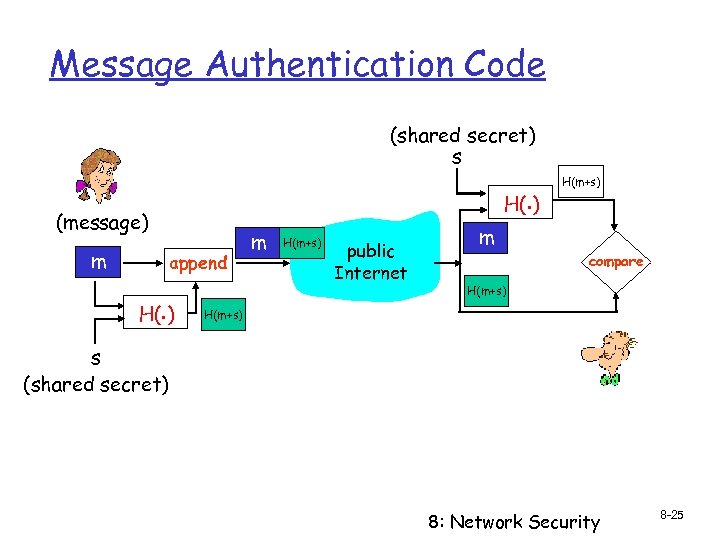 Message Authentication Code (shared secret) s H(. ) (message) m append H(. ) m H(m+s) public Internet H(m+s) m compare H(m+s) s (shared secret) 8: Network Security 8 -25
Message Authentication Code (shared secret) s H(. ) (message) m append H(. ) m H(m+s) public Internet H(m+s) m compare H(m+s) s (shared secret) 8: Network Security 8 -25
 MACs in practice r MD 5 hash function widely used (RFC 1321) m computes 128 -bit MAC in 4 -step process. m arbitrary 128 -bit string x, appears difficult to construct msg m whose MD 5 hash is equal to x r SHA-1 is also used m US standard [NIST, FIPS PUB 180 -1] m 160 -bit MAC 8: Network Security 8 -26
MACs in practice r MD 5 hash function widely used (RFC 1321) m computes 128 -bit MAC in 4 -step process. m arbitrary 128 -bit string x, appears difficult to construct msg m whose MD 5 hash is equal to x r SHA-1 is also used m US standard [NIST, FIPS PUB 180 -1] m 160 -bit MAC 8: Network Security 8 -26
 Digital Signatures cryptographic technique analogous to handwritten signatures. r sender (Bob) digitally signs document, establishing he is document owner/creator. r verifiable, nonforgeable: recipient (Alice) can prove to someone that Bob, and no one else (including Alice), must have signed document 8: Network Security 8 -27
Digital Signatures cryptographic technique analogous to handwritten signatures. r sender (Bob) digitally signs document, establishing he is document owner/creator. r verifiable, nonforgeable: recipient (Alice) can prove to someone that Bob, and no one else (including Alice), must have signed document 8: Network Security 8 -27
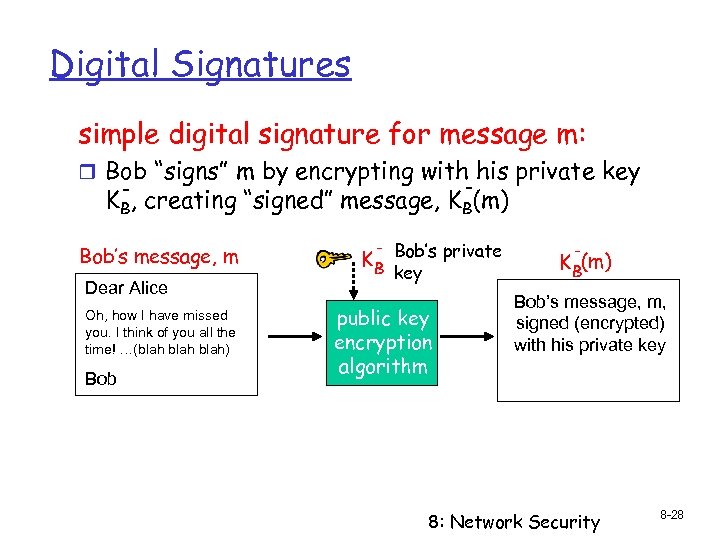 Digital Signatures simple digital signature for message m: r Bob “signs” m by encrypting with his private key - KB, creating “signed” message, KB(m) Bob’s message, m Dear Alice Oh, how I have missed you. I think of you all the time! …(blah) Bob K B Bob’s private key public key encryption algorithm K B(m) Bob’s message, m, signed (encrypted) with his private key 8: Network Security 8 -28
Digital Signatures simple digital signature for message m: r Bob “signs” m by encrypting with his private key - KB, creating “signed” message, KB(m) Bob’s message, m Dear Alice Oh, how I have missed you. I think of you all the time! …(blah) Bob K B Bob’s private key public key encryption algorithm K B(m) Bob’s message, m, signed (encrypted) with his private key 8: Network Security 8 -28
 Digital Signatures (more) - r suppose Alice receives msg m, digital signature K B(m) r Alice verifies m signed by Bob by applying Bob’s + - public key KB to KB(m) then checks KB(KB(m) ) = m. + - r if KB(KB(m) ) = m, whoever signed m must have used Bob’s private key. Alice thus verifies that: ü Bob signed m. ü No one else signed m. ü Bob signed m and not m’. non-repudiation: ü Alice can take m, and signature KB(m) to court and prove that Bob signed m. 8: Network Security 8 -29
Digital Signatures (more) - r suppose Alice receives msg m, digital signature K B(m) r Alice verifies m signed by Bob by applying Bob’s + - public key KB to KB(m) then checks KB(KB(m) ) = m. + - r if KB(KB(m) ) = m, whoever signed m must have used Bob’s private key. Alice thus verifies that: ü Bob signed m. ü No one else signed m. ü Bob signed m and not m’. non-repudiation: ü Alice can take m, and signature KB(m) to court and prove that Bob signed m. 8: Network Security 8 -29
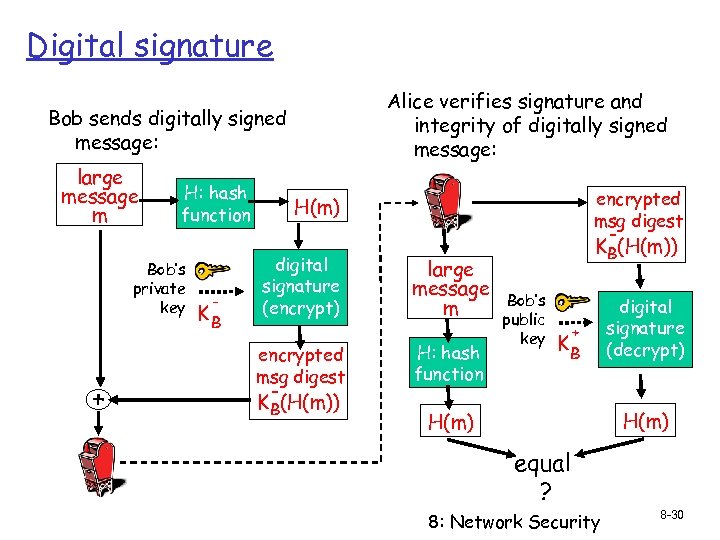 Digital signature Alice verifies signature and integrity of digitally signed message: Bob sends digitally signed message: large message m H: hash function Bob’s private key + - KB encrypted msg digest H(m) digital signature (encrypt) encrypted msg digest KB(H(m)) large message m H: hash function KB(H(m)) Bob’s public key + KB digital signature (decrypt) H(m) equal ? 8: Network Security 8 -30
Digital signature Alice verifies signature and integrity of digitally signed message: Bob sends digitally signed message: large message m H: hash function Bob’s private key + - KB encrypted msg digest H(m) digital signature (encrypt) encrypted msg digest KB(H(m)) large message m H: hash function KB(H(m)) Bob’s public key + KB digital signature (decrypt) H(m) equal ? 8: Network Security 8 -30
 Public Key Certification public key problem: r When Alice obtains Bob’s public key (from web site, e-mail, diskette), how does she know it is Bob’s public key, not Trudy’s? solution: r trusted certification authority (CA) 8: Network Security 8 -31
Public Key Certification public key problem: r When Alice obtains Bob’s public key (from web site, e-mail, diskette), how does she know it is Bob’s public key, not Trudy’s? solution: r trusted certification authority (CA) 8: Network Security 8 -31
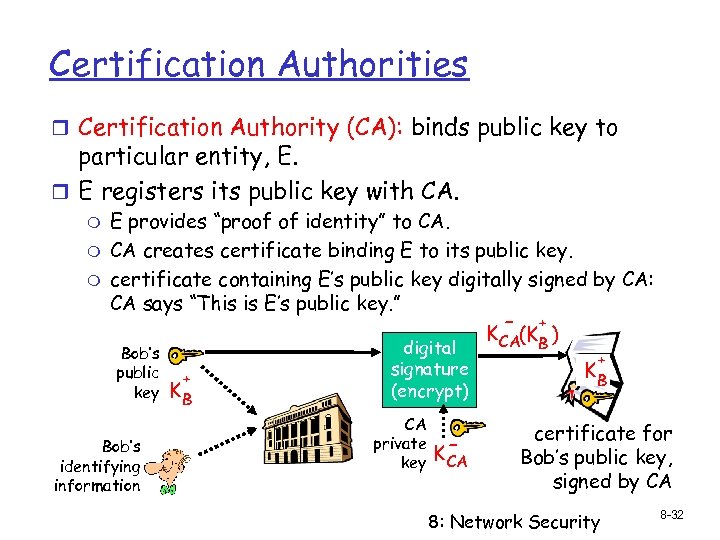 Certification Authorities r Certification Authority (CA): binds public key to particular entity, E. r E registers its public key with CA. m m m E provides “proof of identity” to CA. CA creates certificate binding E to its public key. certificate containing E’s public key digitally signed by CA: CA says “This is E’s public key. ” - + K CA(KB ) Bob’s public key Bob’s identifying information + KB digital signature (encrypt) CA private key K- CA + KB certificate for Bob’s public key, signed by CA 8: Network Security 8 -32
Certification Authorities r Certification Authority (CA): binds public key to particular entity, E. r E registers its public key with CA. m m m E provides “proof of identity” to CA. CA creates certificate binding E to its public key. certificate containing E’s public key digitally signed by CA: CA says “This is E’s public key. ” - + K CA(KB ) Bob’s public key Bob’s identifying information + KB digital signature (encrypt) CA private key K- CA + KB certificate for Bob’s public key, signed by CA 8: Network Security 8 -32
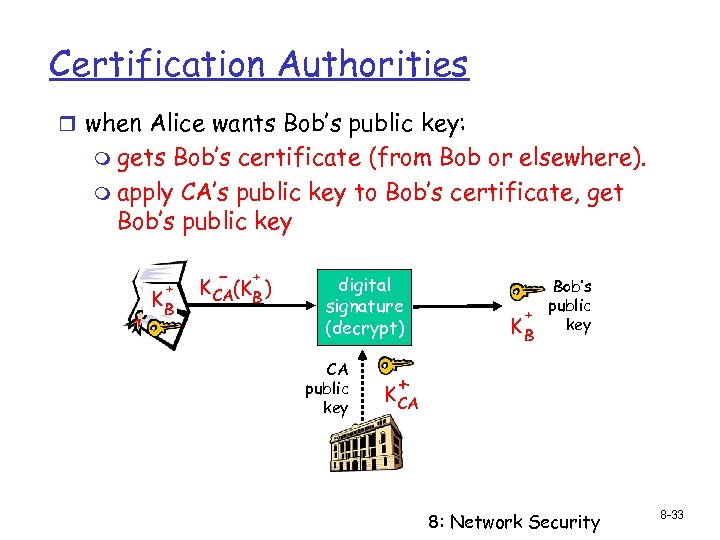 Certification Authorities r when Alice wants Bob’s public key: m gets Bob’s certificate (from Bob or elsewhere). m apply CA’s public key to Bob’s certificate, get Bob’s public key + KB - + K CA(KB ) digital signature (decrypt) CA public key Bob’s public + key KB + K CA 8: Network Security 8 -33
Certification Authorities r when Alice wants Bob’s public key: m gets Bob’s certificate (from Bob or elsewhere). m apply CA’s public key to Bob’s certificate, get Bob’s public key + KB - + K CA(KB ) digital signature (decrypt) CA public key Bob’s public + key KB + K CA 8: Network Security 8 -33
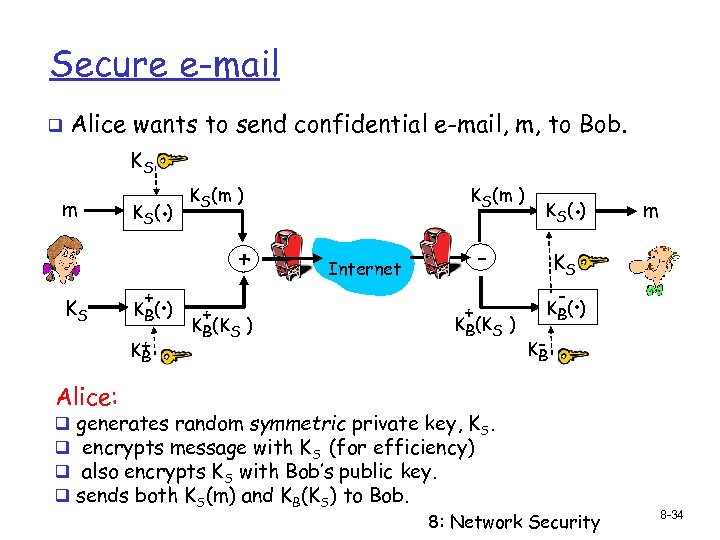 Secure e-mail q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + . K B( ) K+ B KS(m ) + + KB(KS ) . K S( ) - Internet + KB(KS ) m KS - . K B( ) KB Alice: q q generates random symmetric private key, KS. encrypts message with KS (for efficiency) also encrypts KS with Bob’s public key. sends both KS(m) and KB(KS) to Bob. 8: Network Security 8 -34
Secure e-mail q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + . K B( ) K+ B KS(m ) + + KB(KS ) . K S( ) - Internet + KB(KS ) m KS - . K B( ) KB Alice: q q generates random symmetric private key, KS. encrypts message with KS (for efficiency) also encrypts KS with Bob’s public key. sends both KS(m) and KB(KS) to Bob. 8: Network Security 8 -34
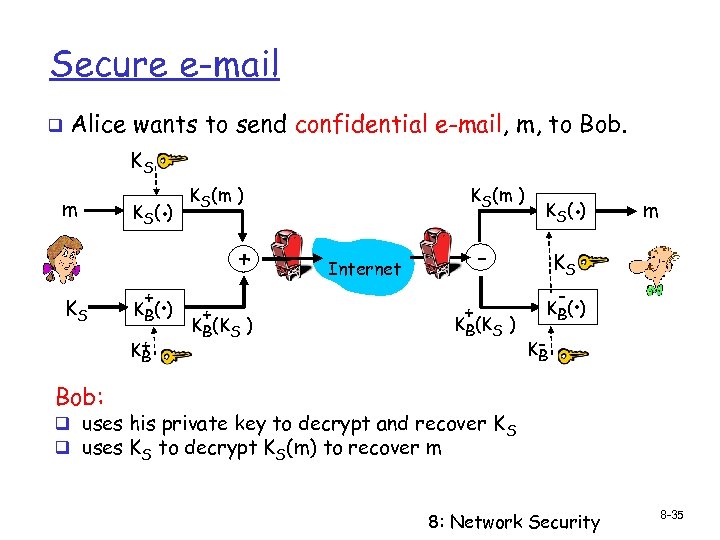 Secure e-mail q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + . K B( ) K+ B KS(m ) + + KB(KS ) . K S( ) - Internet + KB(KS ) m KS - . K B( ) KB Bob: q uses his private key to decrypt and recover K S q uses KS to decrypt KS(m) to recover m 8: Network Security 8 -35
Secure e-mail q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + . K B( ) K+ B KS(m ) + + KB(KS ) . K S( ) - Internet + KB(KS ) m KS - . K B( ) KB Bob: q uses his private key to decrypt and recover K S q uses KS to decrypt KS(m) to recover m 8: Network Security 8 -35
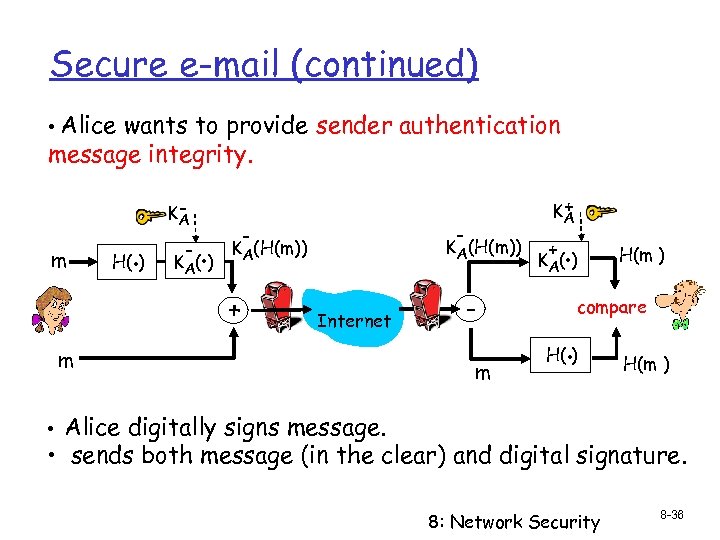 Secure e-mail (continued) • Alice wants to provide sender authentication message integrity. m H(. ) KA - . K A( ) - - KA(H(m)) + + KA Internet m m + . K A( ) H(m ) compare . H( ) H(m ) • Alice digitally signs message. • sends both message (in the clear) and digital signature. 8: Network Security 8 -36
Secure e-mail (continued) • Alice wants to provide sender authentication message integrity. m H(. ) KA - . K A( ) - - KA(H(m)) + + KA Internet m m + . K A( ) H(m ) compare . H( ) H(m ) • Alice digitally signs message. • sends both message (in the clear) and digital signature. 8: Network Security 8 -36
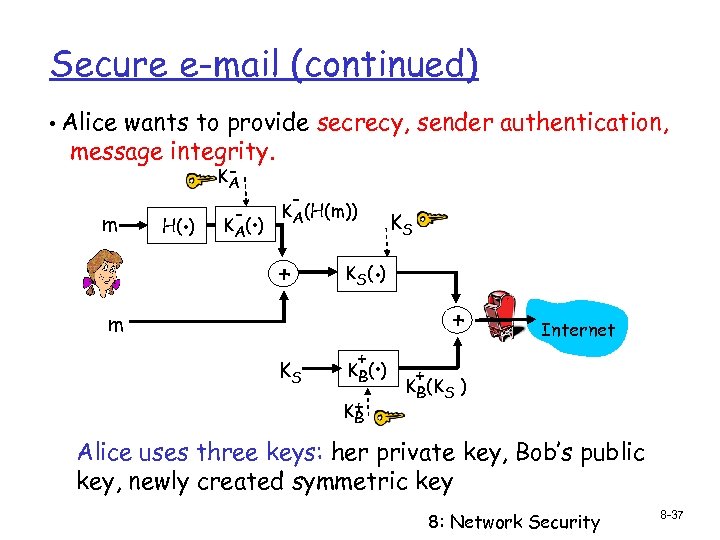 Secure e-mail (continued) • Alice wants to provide secrecy, sender authentication, message integrity. m . H( ) KA - . K A( ) - KA(H(m)) + . K S( ) m KS KS + . K B( ) K+ B + Internet + KB(KS ) Alice uses three keys: her private key, Bob’s public key, newly created symmetric key 8: Network Security 8 -37
Secure e-mail (continued) • Alice wants to provide secrecy, sender authentication, message integrity. m . H( ) KA - . K A( ) - KA(H(m)) + . K S( ) m KS KS + . K B( ) K+ B + Internet + KB(KS ) Alice uses three keys: her private key, Bob’s public key, newly created symmetric key 8: Network Security 8 -37
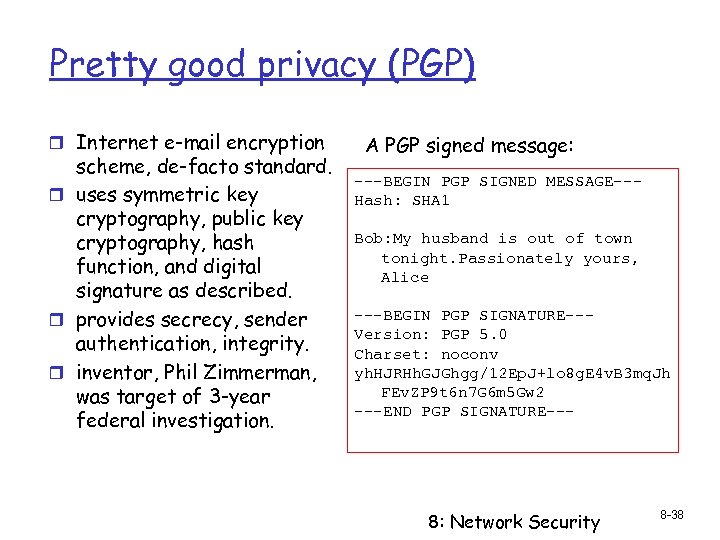 Pretty good privacy (PGP) r Internet e-mail encryption scheme, de-facto standard. r uses symmetric key cryptography, public key cryptography, hash function, and digital signature as described. r provides secrecy, sender authentication, integrity. r inventor, Phil Zimmerman, was target of 3 -year federal investigation. A PGP signed message: ---BEGIN PGP SIGNED MESSAGE--Hash: SHA 1 Bob: My husband is out of town tonight. Passionately yours, Alice ---BEGIN PGP SIGNATURE--Version: PGP 5. 0 Charset: noconv yh. HJRHh. GJGhgg/12 Ep. J+lo 8 g. E 4 v. B 3 mq. Jh FEv. ZP 9 t 6 n 7 G 6 m 5 Gw 2 ---END PGP SIGNATURE--- 8: Network Security 8 -38
Pretty good privacy (PGP) r Internet e-mail encryption scheme, de-facto standard. r uses symmetric key cryptography, public key cryptography, hash function, and digital signature as described. r provides secrecy, sender authentication, integrity. r inventor, Phil Zimmerman, was target of 3 -year federal investigation. A PGP signed message: ---BEGIN PGP SIGNED MESSAGE--Hash: SHA 1 Bob: My husband is out of town tonight. Passionately yours, Alice ---BEGIN PGP SIGNATURE--Version: PGP 5. 0 Charset: noconv yh. HJRHh. GJGhgg/12 Ep. J+lo 8 g. E 4 v. B 3 mq. Jh FEv. ZP 9 t 6 n 7 G 6 m 5 Gw 2 ---END PGP SIGNATURE--- 8: Network Security 8 -38
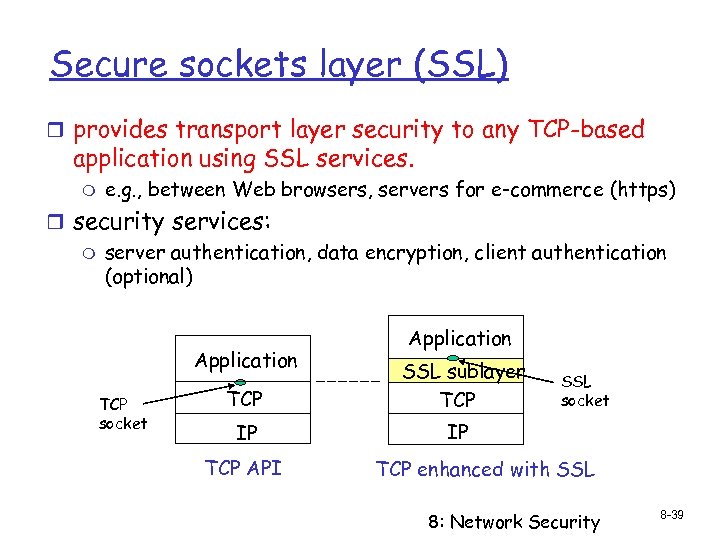 Secure sockets layer (SSL) r provides transport layer security to any TCP-based application using SSL services. m e. g. , between Web browsers, servers for e-commerce (https) r security services: m server authentication, data encryption, client authentication (optional) Application TCP socket Application TCP SSL sublayer TCP IP IP TCP API SSL socket TCP enhanced with SSL 8: Network Security 8 -39
Secure sockets layer (SSL) r provides transport layer security to any TCP-based application using SSL services. m e. g. , between Web browsers, servers for e-commerce (https) r security services: m server authentication, data encryption, client authentication (optional) Application TCP socket Application TCP SSL sublayer TCP IP IP TCP API SSL socket TCP enhanced with SSL 8: Network Security 8 -39
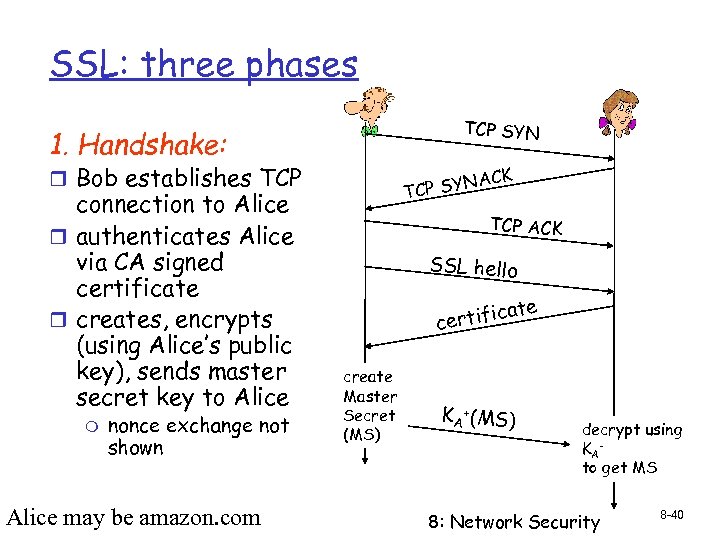 SSL: three phases TCP SYN 1. Handshake: r Bob establishes TCP connection to Alice r authenticates Alice via CA signed certificate r creates, encrypts (using Alice’s public key), sends master secret key to Alice m nonce exchange not shown Alice may be amazon. com ACK P SYN TC TCP ACK SSL hello te ca certifi create Master Secret (MS) KA +(MS) decrypt using KA to get MS 8: Network Security 8 -40
SSL: three phases TCP SYN 1. Handshake: r Bob establishes TCP connection to Alice r authenticates Alice via CA signed certificate r creates, encrypts (using Alice’s public key), sends master secret key to Alice m nonce exchange not shown Alice may be amazon. com ACK P SYN TC TCP ACK SSL hello te ca certifi create Master Secret (MS) KA +(MS) decrypt using KA to get MS 8: Network Security 8 -40
 SSL: three phases 2. Key Derivation: r Alice, Bob use shared secret (MS) to generate 4 keys: m m EB: Bob->Alice data encryption key EA: Alice->Bob data encryption key MB: Bob->Alice MAC key MA: Alice->Bob MAC key r encryption and MAC algorithms negotiable between Bob, Alice 8: Network Security 8 -41
SSL: three phases 2. Key Derivation: r Alice, Bob use shared secret (MS) to generate 4 keys: m m EB: Bob->Alice data encryption key EA: Alice->Bob data encryption key MB: Bob->Alice MAC key MA: Alice->Bob MAC key r encryption and MAC algorithms negotiable between Bob, Alice 8: Network Security 8 -41
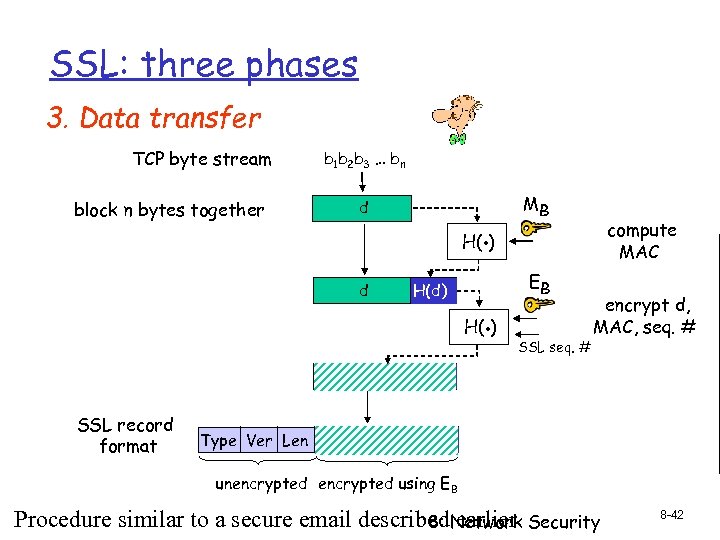 SSL: three phases 3. Data transfer TCP byte stream block n bytes together b 1 b 2 b 3 … bn d . MB compute MAC H( ) d H(d) . H( ) d SSL record format Type Ver Len SSL seq. # encrypt d, MAC, seq. # H(d) d EB H(d) unencrypted using EB Procedure similar to a secure email described. Network Security 8: earlier 8 -42
SSL: three phases 3. Data transfer TCP byte stream block n bytes together b 1 b 2 b 3 … bn d . MB compute MAC H( ) d H(d) . H( ) d SSL record format Type Ver Len SSL seq. # encrypt d, MAC, seq. # H(d) d EB H(d) unencrypted using EB Procedure similar to a secure email described. Network Security 8: earlier 8 -42
 Slides credits r J. F Kurose and K. W. Ross 2: Application Layer 43
Slides credits r J. F Kurose and K. W. Ross 2: Application Layer 43


