8c8b777fbf961007c19af114cecc2fcb.ppt
- Количество слайдов: 52
 What is Forensic Computing COMP 4027 Forensic Computing: Tools and Techniques Helen Ashman
What is Forensic Computing COMP 4027 Forensic Computing: Tools and Techniques Helen Ashman
 What is Forensics? • Forensic Science – The application of science to those criminal and civil laws that are enforced by police agencies in a criminal justice system (Saferstein, 2004) • Think like Sherlock Holmes!!
What is Forensics? • Forensic Science – The application of science to those criminal and civil laws that are enforced by police agencies in a criminal justice system (Saferstein, 2004) • Think like Sherlock Holmes!!
 History & Development of Forensic Science • Francis Galton (1822 -1911) – First definitive study of fingerprints • Sir Arthur Conan Doyle (1887) – Sherlock Holmes mysteries • Leone Lattes (1887 -1954) – Discovered blood groupings (A, B, AB, & O) • Calvin Goddard (1891 -1955) – Firearms and bullet comparison • Albert Osborn (1858 -1946) – Developed principles of document examination • Hans Gross (1847 -1915) – First treatise on using scientific disciplines in criminal investigations.
History & Development of Forensic Science • Francis Galton (1822 -1911) – First definitive study of fingerprints • Sir Arthur Conan Doyle (1887) – Sherlock Holmes mysteries • Leone Lattes (1887 -1954) – Discovered blood groupings (A, B, AB, & O) • Calvin Goddard (1891 -1955) – Firearms and bullet comparison • Albert Osborn (1858 -1946) – Developed principles of document examination • Hans Gross (1847 -1915) – First treatise on using scientific disciplines in criminal investigations.
 History & Development of Forensic Science • Edmond Locard (1877 -1966) Principle of Exchange “. . when a person commits a crime something is always left at the scene of the crime that was not present when the person arrived. ” The purpose of an investigation is to locate identify and preserve evidence-data on which a judgment or conclusion can be based. • FBI (1932) National Lab to provide forensic services to all law enforcement agencies in the country
History & Development of Forensic Science • Edmond Locard (1877 -1966) Principle of Exchange “. . when a person commits a crime something is always left at the scene of the crime that was not present when the person arrived. ” The purpose of an investigation is to locate identify and preserve evidence-data on which a judgment or conclusion can be based. • FBI (1932) National Lab to provide forensic services to all law enforcement agencies in the country
 Boundaries We can identify what and when something happened, but not necessarily who perpetrated the crime.
Boundaries We can identify what and when something happened, but not necessarily who perpetrated the crime.
 Terminology • Forensic Computing – Computer Forensics – Network Forensics • • Electronic Evidence Electronic Forensics Digital Forensic Science • These terms are used interchangeably • We use Digital Forensics broadly to included investigation of all devices and the other terms in a more specific sense • Sometimes ‘Forensics’ replaced by Criminalistics
Terminology • Forensic Computing – Computer Forensics – Network Forensics • • Electronic Evidence Electronic Forensics Digital Forensic Science • These terms are used interchangeably • We use Digital Forensics broadly to included investigation of all devices and the other terms in a more specific sense • Sometimes ‘Forensics’ replaced by Criminalistics
 What is Digital Forensics? • Kruse and Heiser. – Computer Forensics • “Preservation, identification, extraction, documentation, and interpretation of computer data” • John Daniele (Technical Security & Intelligence Inc. ) – “Computer Forensics is the collection of techniques, processes and procedures used to preserve, extract, analyze and present electronic evidence within criminal or civil court. ”
What is Digital Forensics? • Kruse and Heiser. – Computer Forensics • “Preservation, identification, extraction, documentation, and interpretation of computer data” • John Daniele (Technical Security & Intelligence Inc. ) – “Computer Forensics is the collection of techniques, processes and procedures used to preserve, extract, analyze and present electronic evidence within criminal or civil court. ”
 What is Digital Forensics? • Steve Hailey (Cyber. Security Institute) – “The preservation, identification, extraction, interpretation, and documentation of computer evidence, to include the rules of evidence, legal processes, integrity of evidence, factual reporting of the information found, and providing expert opinion in a court of law or other legal proceeding as to what was found. ”
What is Digital Forensics? • Steve Hailey (Cyber. Security Institute) – “The preservation, identification, extraction, interpretation, and documentation of computer evidence, to include the rules of evidence, legal processes, integrity of evidence, factual reporting of the information found, and providing expert opinion in a court of law or other legal proceeding as to what was found. ”
 What is Digital Forensics? • Australian definition • Computer forensics is the application of computer science to the process of collecting digital evidence from electronic storage media in such a way as to preserve the state of the original item. This must be done according to the established rules of gathering evidence that will be presented to a court of law. • Mc. Kemmish (1999) states that the process of computer forensics can be broken down into the four key areas of identification, preservation, analysis and presentation.
What is Digital Forensics? • Australian definition • Computer forensics is the application of computer science to the process of collecting digital evidence from electronic storage media in such a way as to preserve the state of the original item. This must be done according to the established rules of gathering evidence that will be presented to a court of law. • Mc. Kemmish (1999) states that the process of computer forensics can be broken down into the four key areas of identification, preservation, analysis and presentation.
 Mc. Kemmish definition (1) 1. Identification: • Identification consists of locating the electronic devices that may contain evidence. In order to locate the information the examiner must have some idea of what they are looking for and how it is stored. By correctly identifying relevant devices at the outset of an investigation the time taken to complete the forensic process can be greatly reduced.
Mc. Kemmish definition (1) 1. Identification: • Identification consists of locating the electronic devices that may contain evidence. In order to locate the information the examiner must have some idea of what they are looking for and how it is stored. By correctly identifying relevant devices at the outset of an investigation the time taken to complete the forensic process can be greatly reduced.
 Mc. Kemmish definition (2) 2. • Preservation: Preservation of evidence is vital for a successful case to be made in a court of law. There must be a guarantee that all precautions have been made to ensure evidence has not been tampered with or accidentally eliminated. Digital evidence is more susceptible to accidental change than physical evidence, so special purpose tools are required to be used. These tools must be tested and validated to lessen the chance of contamination of the digital crime scene.
Mc. Kemmish definition (2) 2. • Preservation: Preservation of evidence is vital for a successful case to be made in a court of law. There must be a guarantee that all precautions have been made to ensure evidence has not been tampered with or accidentally eliminated. Digital evidence is more susceptible to accidental change than physical evidence, so special purpose tools are required to be used. These tools must be tested and validated to lessen the chance of contamination of the digital crime scene.
 Mc. Kemmish definition (3) 3. Analysis: • Analysis of the evidence is necessary to bring it into a state that is meaningful to humans. 4. Presentation: • This is the final stage of the computer forensics process where the evidence is presented to a court of law. This stage demands that procedures for the forensic process and policies regarding the evidence have been properly followed and documented as required.
Mc. Kemmish definition (3) 3. Analysis: • Analysis of the evidence is necessary to bring it into a state that is meaningful to humans. 4. Presentation: • This is the final stage of the computer forensics process where the evidence is presented to a court of law. This stage demands that procedures for the forensic process and policies regarding the evidence have been properly followed and documented as required.
 The Field • • Results derived from sound evidentiary practices The Expertise test – Court decision Methodology test – Repeatable & Verifiable Technology Test – Keeping up to date
The Field • • Results derived from sound evidentiary practices The Expertise test – Court decision Methodology test – Repeatable & Verifiable Technology Test – Keeping up to date
 RULE 1 Minimal Handling of the Original The application of computer forensic processes during the examination of original data shall be kept to an absolute minimum
RULE 1 Minimal Handling of the Original The application of computer forensic processes during the examination of original data shall be kept to an absolute minimum
 RULE 2 Account for any change Where changes occur during a forensic examination, the nature, extent and reason for such change should be properly accounted for.
RULE 2 Account for any change Where changes occur during a forensic examination, the nature, extent and reason for such change should be properly accounted for.
 RULE 3 Comply with the rules of evidence The application or development of forensic tools and techniques should be undertaken with regard to the relevant rules of evidence.
RULE 3 Comply with the rules of evidence The application or development of forensic tools and techniques should be undertaken with regard to the relevant rules of evidence.
 RULE 4 Don’t Exceed your Knowledge The forensic computer specialist should not undertake an examination that is beyond their current level of knowledge and skill.
RULE 4 Don’t Exceed your Knowledge The forensic computer specialist should not undertake an examination that is beyond their current level of knowledge and skill.
 Where will it take us? • • Identifying What, When, and How Preservation of variety of media Data Recovery New methods / New technologies
Where will it take us? • • Identifying What, When, and How Preservation of variety of media Data Recovery New methods / New technologies
 Range of Skills
Range of Skills
 Range of Skills
Range of Skills
 Digital Forensic Science “The use of scientifically derived and proven methods toward the preservation, collection, validation, identification, analysis, interpretation, documentation and presentation of digital evidence derived from digital sources for the purpose of facilitating or furthering the reconstruction of events found to be criminal, or helping to anticipate unauthorized actions shown to be disruptive to planned operations. ” Source: (2001). Digital Forensic Research Workshop (DFRWS)
Digital Forensic Science “The use of scientifically derived and proven methods toward the preservation, collection, validation, identification, analysis, interpretation, documentation and presentation of digital evidence derived from digital sources for the purpose of facilitating or furthering the reconstruction of events found to be criminal, or helping to anticipate unauthorized actions shown to be disruptive to planned operations. ” Source: (2001). Digital Forensic Research Workshop (DFRWS)
 A taxonomy of Forensic Computing – What do we need to know? • The taxonomy proposed by Broucek and Turner (2001) suggests that FC includes • Computer Science: Operating Systems and Application Software, Systems Programming and Programming Languages, Computer Security, Computer Law (national and international), Criminal, Civil and Soft Law • Information Systems: Systems Management and Policies, User Education and Training • Social Science: Socio-political issues (privacy, encryption, surveillance), Activism, Hacktivism, Cyberterrorism and Cyber-warfare, Socio-psychological impacts of computing
A taxonomy of Forensic Computing – What do we need to know? • The taxonomy proposed by Broucek and Turner (2001) suggests that FC includes • Computer Science: Operating Systems and Application Software, Systems Programming and Programming Languages, Computer Security, Computer Law (national and international), Criminal, Civil and Soft Law • Information Systems: Systems Management and Policies, User Education and Training • Social Science: Socio-political issues (privacy, encryption, surveillance), Activism, Hacktivism, Cyberterrorism and Cyber-warfare, Socio-psychological impacts of computing
 Other Forensic Science Services • Forensic Pathology – Sudden unnatural or violent deaths • Forensic Anthropology – Identification of human skeletal remains • Forensic Entomology – Insects • Forensic Psychiatry • Forensic Psychology • Forensic Odontology – Dental • Forensic Engineering
Other Forensic Science Services • Forensic Pathology – Sudden unnatural or violent deaths • Forensic Anthropology – Identification of human skeletal remains • Forensic Entomology – Insects • Forensic Psychiatry • Forensic Psychology • Forensic Odontology – Dental • Forensic Engineering
 Digital Forensic Communities • There at least 3 distinct communities within Digital Forensics – Law Enforcement – Military – Business & Industry • Possibly a 4 th – Academia
Digital Forensic Communities • There at least 3 distinct communities within Digital Forensics – Law Enforcement – Military – Business & Industry • Possibly a 4 th – Academia
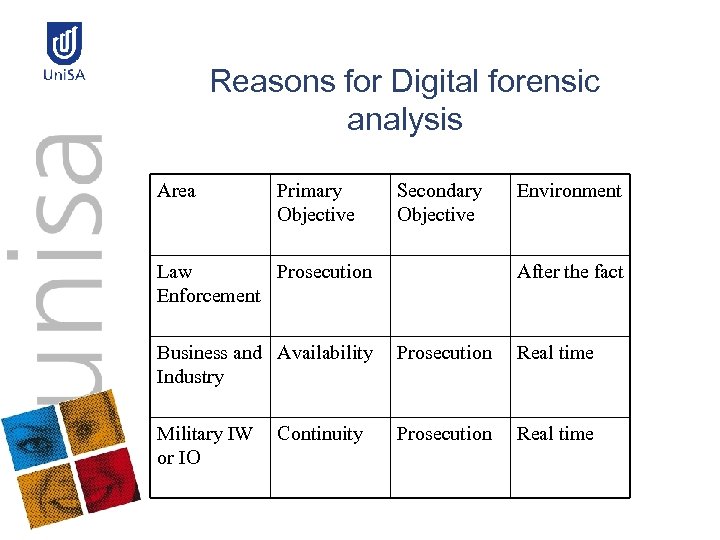 Reasons for Digital forensic analysis Area Primary Objective Secondary Objective Law Prosecution Enforcement Environment After the fact Business and Availability Industry Prosecution Real time Military IW or IO Prosecution Real time Continuity
Reasons for Digital forensic analysis Area Primary Objective Secondary Objective Law Prosecution Enforcement Environment After the fact Business and Availability Industry Prosecution Real time Military IW or IO Prosecution Real time Continuity
 Cybercrime • Popularly presented as – Hackers cracking web sites – Criminals looking for • Bank account numbers • Credit card numbers • Trade secrets – For financial gain – Top secret military information
Cybercrime • Popularly presented as – Hackers cracking web sites – Criminals looking for • Bank account numbers • Credit card numbers • Trade secrets – For financial gain – Top secret military information
 Cybercrime • The more mundane reality – The adoption of technology has been taken up by criminals too • Accounting information • Client information • etc – Criminals include • • Drug distributors Prostitution rings Illegal gambling and many others
Cybercrime • The more mundane reality – The adoption of technology has been taken up by criminals too • Accounting information • Client information • etc – Criminals include • • Drug distributors Prostitution rings Illegal gambling and many others
 Cybercrime • Computers can be used – As a repository for information – As a tool for committing a crime – As a tool for organising crime • Networked PC (LAN or modem) – Information could be stored remotely – Criminal activity can be committed anywhere in the world (Stoll, 1991) • Difficult to investigate • Attractive to those who want to be remote from the crime scene
Cybercrime • Computers can be used – As a repository for information – As a tool for committing a crime – As a tool for organising crime • Networked PC (LAN or modem) – Information could be stored remotely – Criminal activity can be committed anywhere in the world (Stoll, 1991) • Difficult to investigate • Attractive to those who want to be remote from the crime scene
 Case Studies • Enron – The Andersen partner in charge of the Enron account allegedly ordered 1000 s of e-mail messages deleted from staff computers – Computer forensics specialists were called in to retrieve e-mail messages from: • • • Servers Backup tapes Hard drives Disk caches E-mail archives (Lotus Notes was used) File slack – 1 in 10 people throw nothing away – The receivers can also be targeted
Case Studies • Enron – The Andersen partner in charge of the Enron account allegedly ordered 1000 s of e-mail messages deleted from staff computers – Computer forensics specialists were called in to retrieve e-mail messages from: • • • Servers Backup tapes Hard drives Disk caches E-mail archives (Lotus Notes was used) File slack – 1 in 10 people throw nothing away – The receivers can also be targeted
 Case Studies • A client suspected possible Internet misuse. • Covert examination of more than 60 machines uncovered a trail of misuse • One employee was successfully convicted on child pornography charges • A number of disciplinary cases for downloading pornographic images were also made
Case Studies • A client suspected possible Internet misuse. • Covert examination of more than 60 machines uncovered a trail of misuse • One employee was successfully convicted on child pornography charges • A number of disciplinary cases for downloading pornographic images were also made
 Case Studies • Examination of an employee’s computer revealed they had been downloading client information in order to start a rival business • Savings in the region of US $ 10 million as a result of two days’ investigation
Case Studies • Examination of an employee’s computer revealed they had been downloading client information in order to start a rival business • Savings in the region of US $ 10 million as a result of two days’ investigation
 Case Studies • An insurance company contested a claim for £ 100, 000 for loss of all data from a company’s central computer • The computer was allegedly flattened by a large industrial magnet • Extensive damage was made to the casing and mother board • Hard disk when examined was undamaged and all data was recovered
Case Studies • An insurance company contested a claim for £ 100, 000 for loss of all data from a company’s central computer • The computer was allegedly flattened by a large industrial magnet • Extensive damage was made to the casing and mother board • Hard disk when examined was undamaged and all data was recovered
 Case Studies • A large corporation had paid a considerable sum for a state of the art computer running on a mirrored RAID array • They could not get the system to work and the supplier refused to help • Investigation revealed that no operating system files were present on the hard disk and what had been delivered would never work
Case Studies • A large corporation had paid a considerable sum for a state of the art computer running on a mirrored RAID array • They could not get the system to work and the supplier refused to help • Investigation revealed that no operating system files were present on the hard disk and what had been delivered would never work
 Computer Forensics What kind of questions can computer evidence help to answer? • • • Where were you at 4 pm on the 6 th July 1999? Did anyone tamper with this file? Who could it have been? Is this software on the suspect’s computer stolen? Has this suspect been downloading files with illegal content, e. g. pornography? Have you been attempting to hack into the website of the National Security Agency? Did you intentionally introduce a computer virus into this network? Have you been wasting time playing games at work? Did you threaten this colleague using email messages? Are you involved in this well-known drug money laundering gang?
Computer Forensics What kind of questions can computer evidence help to answer? • • • Where were you at 4 pm on the 6 th July 1999? Did anyone tamper with this file? Who could it have been? Is this software on the suspect’s computer stolen? Has this suspect been downloading files with illegal content, e. g. pornography? Have you been attempting to hack into the website of the National Security Agency? Did you intentionally introduce a computer virus into this network? Have you been wasting time playing games at work? Did you threaten this colleague using email messages? Are you involved in this well-known drug money laundering gang?
 Computer Forensics Besides criminal cases, where is computer forensic analysis used? • insurance investigations • “whistle-blowers” • commercial transactions • disputed contracts • Lawsuits • Customs • Tax Office • any disputed event. . .
Computer Forensics Besides criminal cases, where is computer forensic analysis used? • insurance investigations • “whistle-blowers” • commercial transactions • disputed contracts • Lawsuits • Customs • Tax Office • any disputed event. . .
 Computer Evidence So where do you get “computer evidence”? • • • local diskettes, hard disk temporary storage, system files paper snoop it off the network sniff it off the victim’s computer daily audit and activity logs housekeeping files Windows cache files deleted files file slack - wasted space on the disk “shadow files” and many more. . .
Computer Evidence So where do you get “computer evidence”? • • • local diskettes, hard disk temporary storage, system files paper snoop it off the network sniff it off the victim’s computer daily audit and activity logs housekeeping files Windows cache files deleted files file slack - wasted space on the disk “shadow files” and many more. . .
 Search and Seizure How police carry out “search and seizure” of computer evidence • Isolate the device from any network (pull the plug) • Connect a streaming device • Create a secure tamper-proof copy of the entire drive, e. g. a CD • All evidence will be produced from the copy, not from the suspect’s disks
Search and Seizure How police carry out “search and seizure” of computer evidence • Isolate the device from any network (pull the plug) • Connect a streaming device • Create a secure tamper-proof copy of the entire drive, e. g. a CD • All evidence will be produced from the copy, not from the suspect’s disks
 Evidence • We need to know: – Where the evidence is – What the evidence means – How to put it together
Evidence • We need to know: – Where the evidence is – What the evidence means – How to put it together
 Aim in collecting evidence • Collect and analyse evidence to form one or more chronological sequences of events that fit the evidence – There may be more than one! • Can’t always be conclusive as system/network evidence is circumstantial in nature • It is a feedback loop – Analysis leads to more evidence which feeds analysis…
Aim in collecting evidence • Collect and analyse evidence to form one or more chronological sequences of events that fit the evidence – There may be more than one! • Can’t always be conclusive as system/network evidence is circumstantial in nature • It is a feedback loop – Analysis leads to more evidence which feeds analysis…
 Sources of Evidence • Three basic sources: – Users – Systems (including backups) – Networks/communications • Basically we rely on logs and remnants recovered from a compromised system
Sources of Evidence • Three basic sources: – Users – Systems (including backups) – Networks/communications • Basically we rely on logs and remnants recovered from a compromised system
 Sources of Evidence • Users – First hand observations • Systems – Log files! – Intruder remnants (processes, files etc) • Networks/communications – – Network Logs Firewall logs Modem banks/telephone logs Network transaction auditing
Sources of Evidence • Users – First hand observations • Systems – Log files! – Intruder remnants (processes, files etc) • Networks/communications – – Network Logs Firewall logs Modem banks/telephone logs Network transaction auditing
 Chain Of Custody • Who has had access to the evidence? • What procedures did they follow in working with the evidence? • How can we show that our analysis is based on copies that are identical to the original evidence? • Answer: documentation, checksums, timestamps
Chain Of Custody • Who has had access to the evidence? • What procedures did they follow in working with the evidence? • How can we show that our analysis is based on copies that are identical to the original evidence? • Answer: documentation, checksums, timestamps
 Evidence Preservation • Make a copy – Generate checksums of original, copy – Verify accuracy of copy through checksum • Document – Who collected it from where, how, when, maybe why • Give a copy (or the original) to the custodian – Custodian gives copies to others – Document chain of custody – Fewer custodians is better – fewer to testify that way
Evidence Preservation • Make a copy – Generate checksums of original, copy – Verify accuracy of copy through checksum • Document – Who collected it from where, how, when, maybe why • Give a copy (or the original) to the custodian – Custodian gives copies to others – Document chain of custody – Fewer custodians is better – fewer to testify that way
 Collect Volatile Evidence • “Volatile evidence” is evidence that will disappear soon, such as information about active network connections, or the current contents of volatile memory. • Contrast this with the contents of a disk or tape.
Collect Volatile Evidence • “Volatile evidence” is evidence that will disappear soon, such as information about active network connections, or the current contents of volatile memory. • Contrast this with the contents of a disk or tape.
 Collect Volatile Evidence • From Farmer & Venema – http: //www. porcupine. org – – – Registers, peripheral memory, caches. . . Memory (virtual, physical) Network state Running processes Disks, floppies, tapes CD/ROM, printouts.
Collect Volatile Evidence • From Farmer & Venema – http: //www. porcupine. org – – – Registers, peripheral memory, caches. . . Memory (virtual, physical) Network state Running processes Disks, floppies, tapes CD/ROM, printouts.
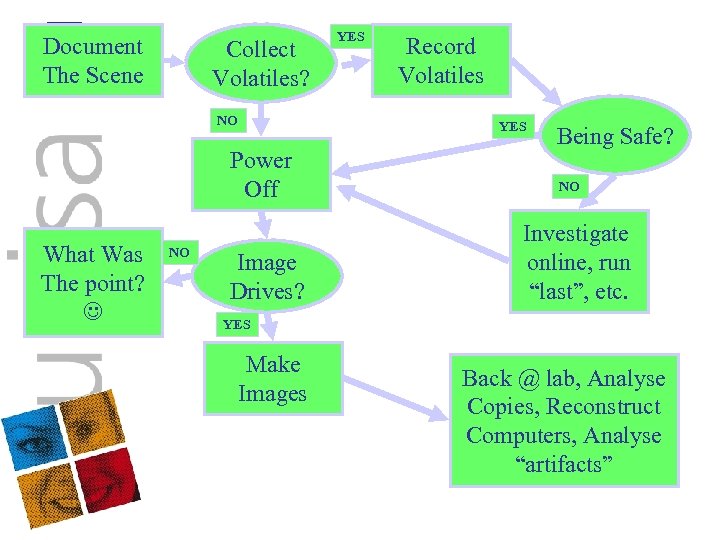 Document The Scene Collect Volatiles? NO NO Record Volatiles YES Power Off What Was The point? YES Image Drives? Being Safe? NO Investigate online, run “last”, etc. YES Make Images Back @ lab, Analyse Copies, Reconstruct Computers, Analyse “artifacts”
Document The Scene Collect Volatiles? NO NO Record Volatiles YES Power Off What Was The point? YES Image Drives? Being Safe? NO Investigate online, run “last”, etc. YES Make Images Back @ lab, Analyse Copies, Reconstruct Computers, Analyse “artifacts”
 Challenges Eric Holder, Deputy Attorney General of the United States Subcommittee on Crime of the House Committee on the Judiciary and the Subcommittee on Criminal Oversight of the Senate Committee on the Judiciary: • Technical challenges that hinder law enforcement’s ability to find and prosecute criminals operating online; • Legal challenges resulting from laws and legal tools needed to investigate cybercrime lagging behind technological, structural, social changes; • and resource challenges to ensure we have satisfied critical investigative and prosecutorial needs at all levels of government.
Challenges Eric Holder, Deputy Attorney General of the United States Subcommittee on Crime of the House Committee on the Judiciary and the Subcommittee on Criminal Oversight of the Senate Committee on the Judiciary: • Technical challenges that hinder law enforcement’s ability to find and prosecute criminals operating online; • Legal challenges resulting from laws and legal tools needed to investigate cybercrime lagging behind technological, structural, social changes; • and resource challenges to ensure we have satisfied critical investigative and prosecutorial needs at all levels of government.
 Challenges NIJ 2001 Study • There is near-term window of opportunity for law enforcement to gain a foothold in containing electronic crimes. • Most State and local law enforcement agencies report that they lack adequate training, equipment and staff to meet their present and future needs to combat electronic crime. • Greater awareness of electronic crime should be promoted for all stakeholders, including prosecutors, judges, academia, industry, and the general public.
Challenges NIJ 2001 Study • There is near-term window of opportunity for law enforcement to gain a foothold in containing electronic crimes. • Most State and local law enforcement agencies report that they lack adequate training, equipment and staff to meet their present and future needs to combat electronic crime. • Greater awareness of electronic crime should be promoted for all stakeholders, including prosecutors, judges, academia, industry, and the general public.
 General Challenges • Computer forensics is in its infancy • Different from other forensic sciences as the media that is examined and the tools/techniques for the examiner are products of a market-driven private sector. • No real basic theoretical background upon which to conduct empirical hypothesis testing • No true professional designations • Proper training lacking **** • At least 3 different “communities” with different demands • Still more of an art than a true science
General Challenges • Computer forensics is in its infancy • Different from other forensic sciences as the media that is examined and the tools/techniques for the examiner are products of a market-driven private sector. • No real basic theoretical background upon which to conduct empirical hypothesis testing • No true professional designations • Proper training lacking **** • At least 3 different “communities” with different demands • Still more of an art than a true science
 Specific Challenges • • No International Definitions of Computer Crime No International agreements on extraditions Multitude of OS platforms and file systems Incredibly large storage capacity needed – Terabytes of data
Specific Challenges • • No International Definitions of Computer Crime No International agreements on extraditions Multitude of OS platforms and file systems Incredibly large storage capacity needed – Terabytes of data
 Specific Challenges • Small footprint storage devices – Compact flash – Memory sticks – Thumb drives • • • Networked environments RAID systems Grid computing Embedded processors ? ?
Specific Challenges • Small footprint storage devices – Compact flash – Memory sticks – Thumb drives • • • Networked environments RAID systems Grid computing Embedded processors ? ?
 Specific Challenges • Where is the “crime scene? ” • What constitutes evidence? ? • What are we looking for? ?
Specific Challenges • Where is the “crime scene? ” • What constitutes evidence? ? • What are we looking for? ?


