 What is EKMI? Enterprise Key Management Infrastructure Take the tour
What is EKMI? Enterprise Key Management Infrastructure Take the tour
 Enterprise Key Management Infrastructure or EKMI is a collection of technology, policies, and procedures for managing all cryptographic keys in the enterprise.
Enterprise Key Management Infrastructure or EKMI is a collection of technology, policies, and procedures for managing all cryptographic keys in the enterprise.
 EKMI is: A Single place to manage all keys A Standard Protocol Platform and Application Independent Always available, even during network failure Scalable to millions of clients. . . and of course, extremely secure
EKMI is: A Single place to manage all keys A Standard Protocol Platform and Application Independent Always available, even during network failure Scalable to millions of clients. . . and of course, extremely secure
 EKMI is comprised of: Public Key Infrastructure, or PKI This is used for digital certificate management, strong-autentication, secure storage, and transpo of symmetric encryption keys Symetric Key Management System, or SKMS SKS Server - for symmetric key management SKCL - for client interactions with SKS Server PKI + SKMS= EKMI
EKMI is comprised of: Public Key Infrastructure, or PKI This is used for digital certificate management, strong-autentication, secure storage, and transpo of symmetric encryption keys Symetric Key Management System, or SKMS SKS Server - for symmetric key management SKCL - for client interactions with SKS Server PKI + SKMS= EKMI
 Lets See How This All Works Together. . .
Lets See How This All Works Together. . .
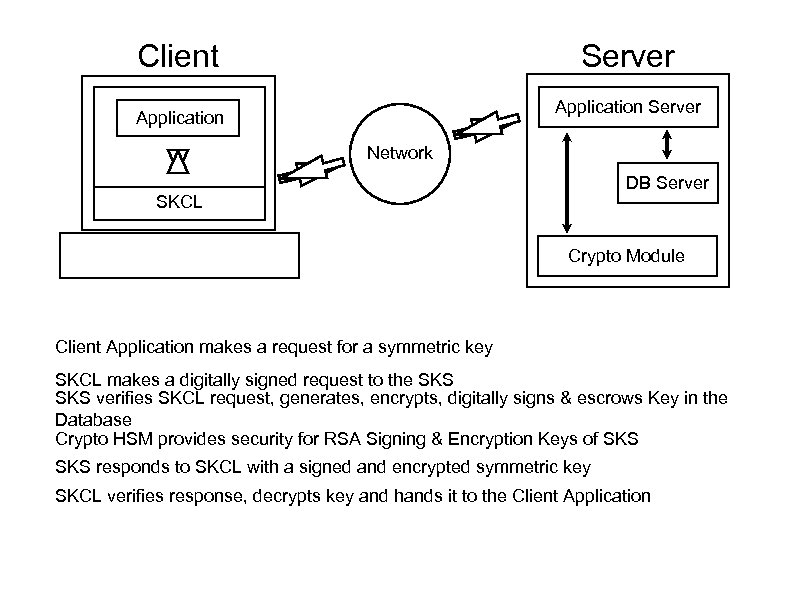 Client Server Application Network DB Server SKCL Crypto Module Client Application makes a request for a symmetric key SKCL makes a digitally signed request to the SKS verifies SKCL request, generates, encrypts, digitally signs & escrows Key in the Database Crypto HSM provides security for RSA Signing & Encryption Keys of SKS responds to SKCL with a signed and encrypted symmetric key SKCL verifies response, decrypts key and hands it to the Client Application
Client Server Application Network DB Server SKCL Crypto Module Client Application makes a request for a symmetric key SKCL makes a digitally signed request to the SKS verifies SKCL request, generates, encrypts, digitally signs & escrows Key in the Database Crypto HSM provides security for RSA Signing & Encryption Keys of SKS responds to SKCL with a signed and encrypted symmetric key SKCL verifies response, decrypts key and hands it to the Client Application
 Since the Keys are generated and “Leased” at the application level, data remains encrypted and secure, not only at rest on the server, but also through transit. What does this mean in practical application. . .
Since the Keys are generated and “Leased” at the application level, data remains encrypted and secure, not only at rest on the server, but also through transit. What does this mean in practical application. . .
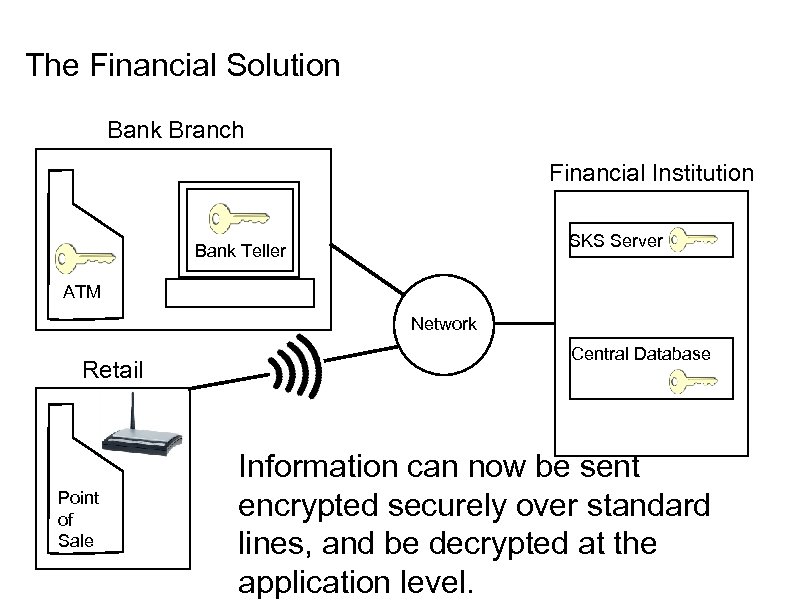 The Financial Solution Bank Branch Financial Institution SKS Server Bank Teller ATM Network Retail Point of Sale Central Database Information can now be sent encrypted securely over standard lines, and be decrypted at the application level.
The Financial Solution Bank Branch Financial Institution SKS Server Bank Teller ATM Network Retail Point of Sale Central Database Information can now be sent encrypted securely over standard lines, and be decrypted at the application level.
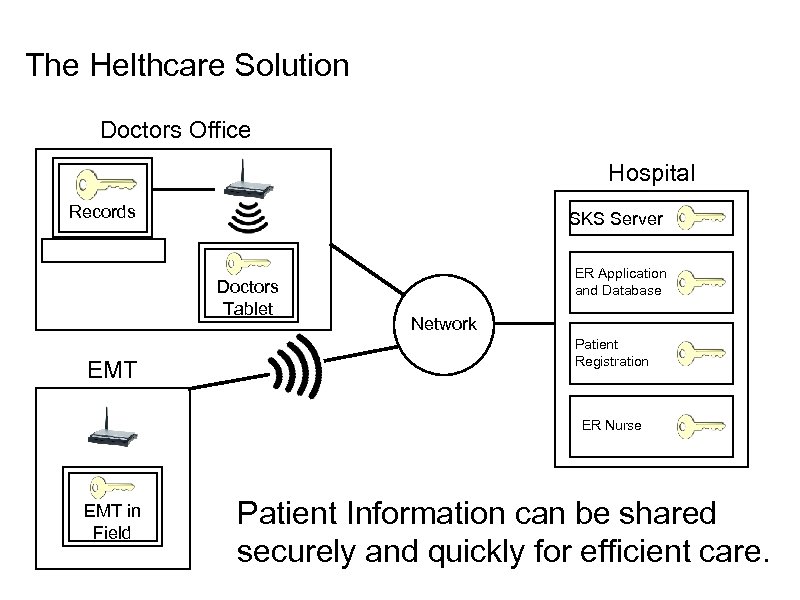 The Helthcare Solution Doctors Office Hospital Records SKS Server Doctors Tablet EMT ER Application and Database Network Patient Registration ER Nurse EMT in Field Patient Information can be shared securely and quickly for efficient care.
The Helthcare Solution Doctors Office Hospital Records SKS Server Doctors Tablet EMT ER Application and Database Network Patient Registration ER Nurse EMT in Field Patient Information can be shared securely and quickly for efficient care.
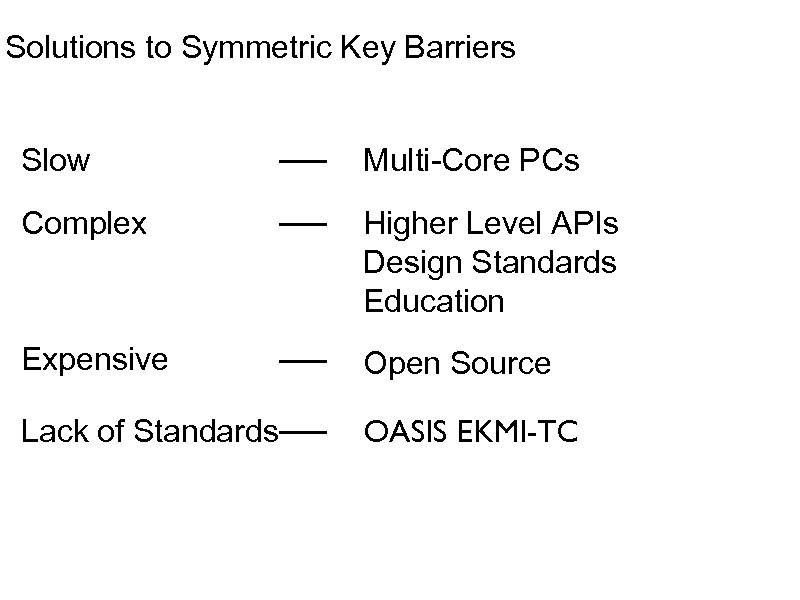 Solutions to Symmetric Key Barriers Slow Multi-Core PCs Complex Higher Level APIs Design Standards Education Expensive Open Source Lack of Standards OASIS EKMI-TC
Solutions to Symmetric Key Barriers Slow Multi-Core PCs Complex Higher Level APIs Design Standards Education Expensive Open Source Lack of Standards OASIS EKMI-TC
 Securing the Core should have been Plan A from the beginning. But its not too late!
Securing the Core should have been Plan A from the beginning. But its not too late!
 OASIS EKMI-TC is driving new key-management standards that cuts across platforms, applications and industries. Get involved!
OASIS EKMI-TC is driving new key-management standards that cuts across platforms, applications and industries. Get involved!