318b491b00773bbd7db59a02eb34d90e.ppt
- Количество слайдов: 56

Welcome to Our Presentation Bob Danielson Instructor for Mesa Community College

What will be covered Security Terminology Security Threats Security Vulnerabilities and Solutions Discussion of the configuration part of class

Terminology Threat – Anyone or anything that can attack or compromise you Vulnerability – Something that can be taken advantage of by the Threat

Who is a threat? Those around us can be a threat because they have access to our equipment Those that are not near us are also a threat o They can access our equipment through our Internet connection o They can access our equipment through our wireless devices
The Low Down Threats can occur from anywhere and can be anyone You must be ready!!!

What are the Vulnerabilities? Identity Theft Wireless/Wired Vulnerabilities Issues that our Kids Deal With o o § Blogs Sharing Information and Consequences Predators Cyber Bullying Morals of the issue
Identity Theft Phishing This commonly involves sending an e-mail claiming to be a legitimate company They try to obtain personal information You get these all them time!!!
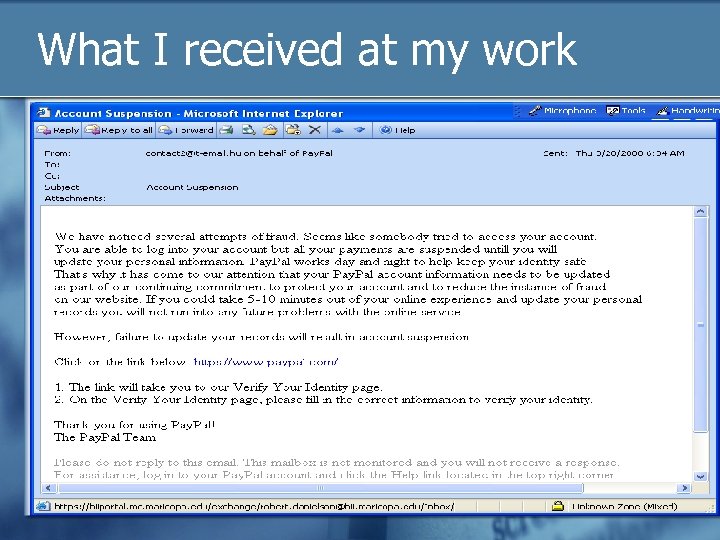
What I received at my work
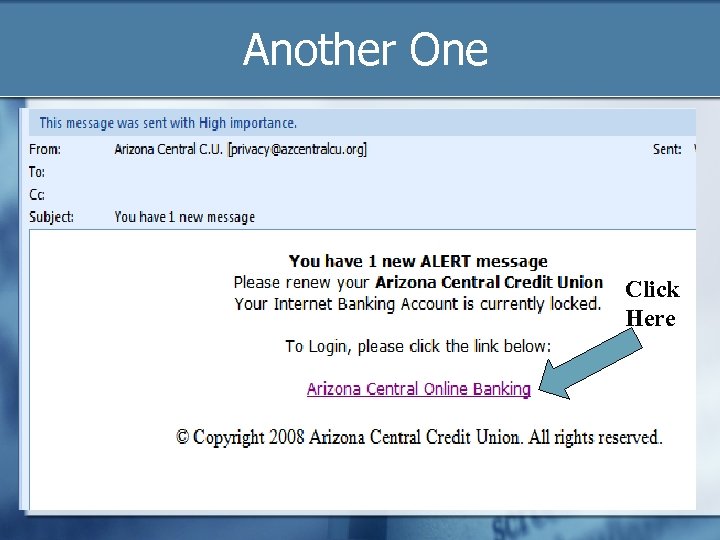
Another One Click Here
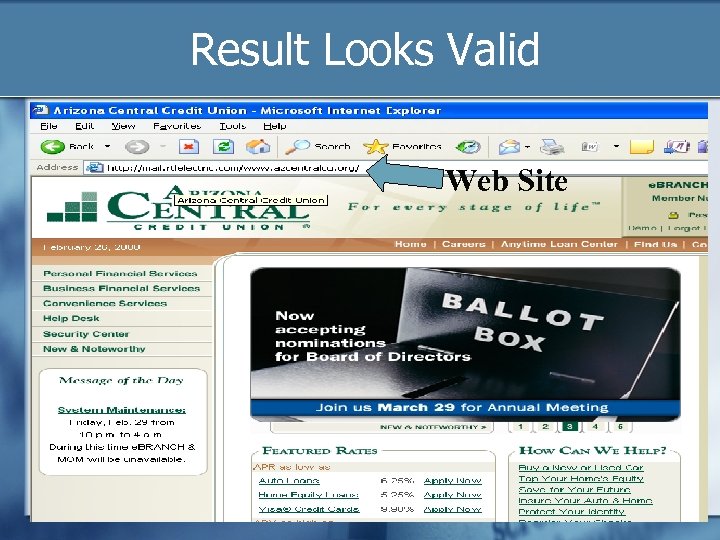
Result Looks Valid Web Site

Web Site was Compromised!!

Be Careful with your personal information § Install anti-phishing tools

How to Compromise a Computer Your computer through the Internet Your computer through wireless

Through the Internet Virus, Worms and Trojan Horse Commonly use e-mail to infect your computer All you have to do is open e-mail § § § Don’t open any e-mail from someone you don’t know Set e-mail to preview message instead Delete e-mail which you don’t know sender Don’t run an Active. X programs on web sites Install Virus Scanner and Firewalls

Through Wireless o o Terminology to know: SSID Encryption WEP, WPA or something else MAC Filtering

Make Wireless Router Secure Disable the SSID Broadcast Enable MAC Filtering Configure Encryption o Use WPA instead of WEP

Summary on Security You need to take the initiative to make your home computer secure If you don’t, who will. Probably your child Let’s look at how that can be bad!!!

Dangers for your child Blogs Their sharing of information Consequences of sharing Predators Cyberbullying

What is a BLOG? My. Space is an example: Express yourself freely. Create a COOL site with videos, personal thoughts and pictures. Listen to music of your choosing. Talk to your friends. Make new friends.
This Includes Music Videos, Interests and Expressive Pictures
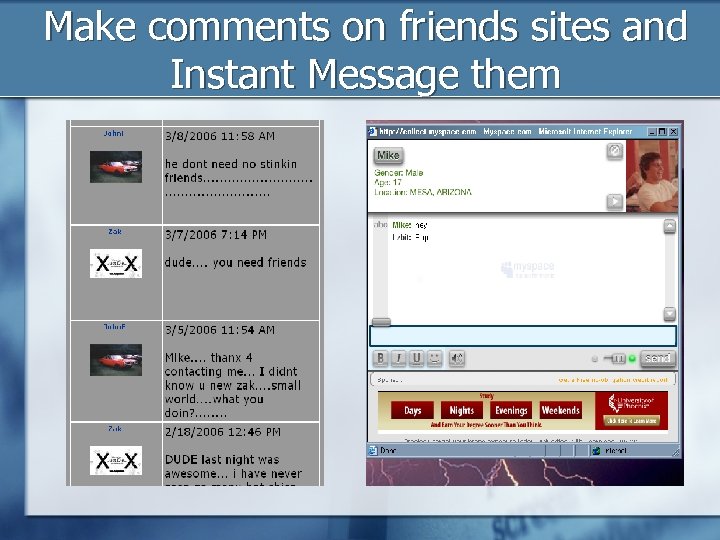
Make comments on friends sites and Instant Message them

However, people are anonymous

The reality of Blogs You might see it as a fun, safe place to be. It is a very personal blog. In fact, this site can be used to harm you, your family and your friends! What you post can enable predators to find you. Posting inappropriate material can cause you to hurt your future career, before it starts. It can cause you to be kidnapped or worse loose your life.

How about chat rooms? GMan: hey! what's up, it's mike. how ya been? Go. Girl: mike who GMan: uh. . hello anyone home MIKE Go. Girl: Mikey M. ? ? ? GMan: yeah i've had your s/n for ever just never messaged you Go. Girl: oh now i feel real loved GMan: ok. . . what are you up to today? Go. Girl: idk maybe theater, the one in the mall GMan: yep, but I first gotta stop by John's house Go. Girl: John S. ?
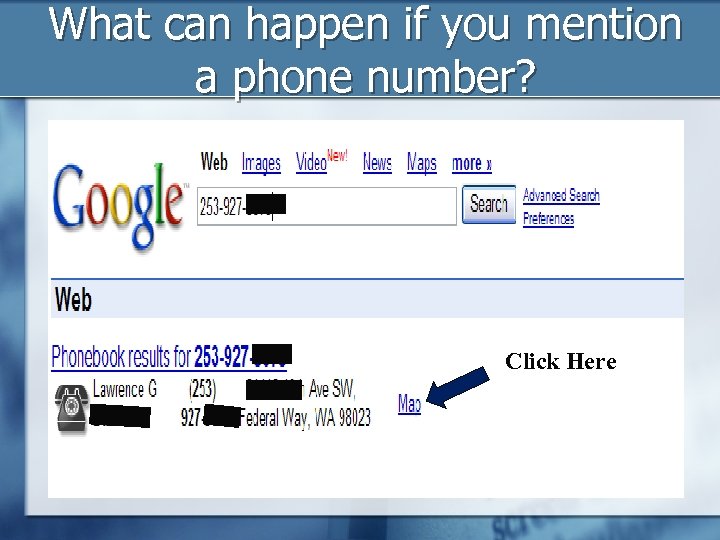
What can happen if you mention a phone number? Click Here
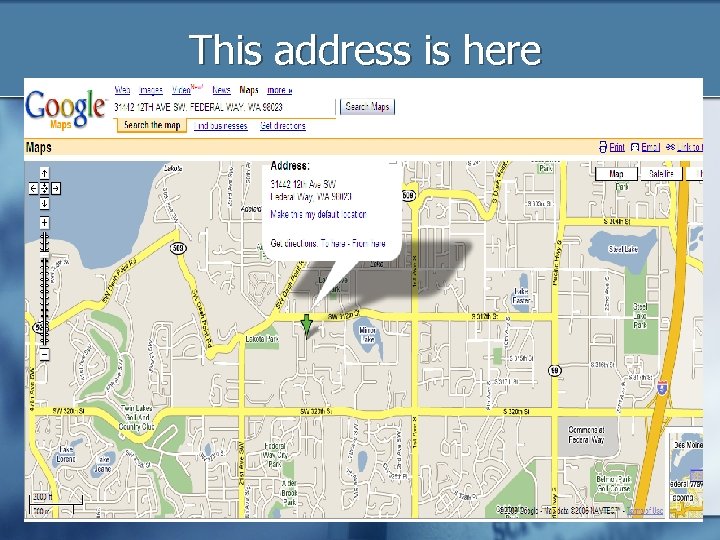
This address is here
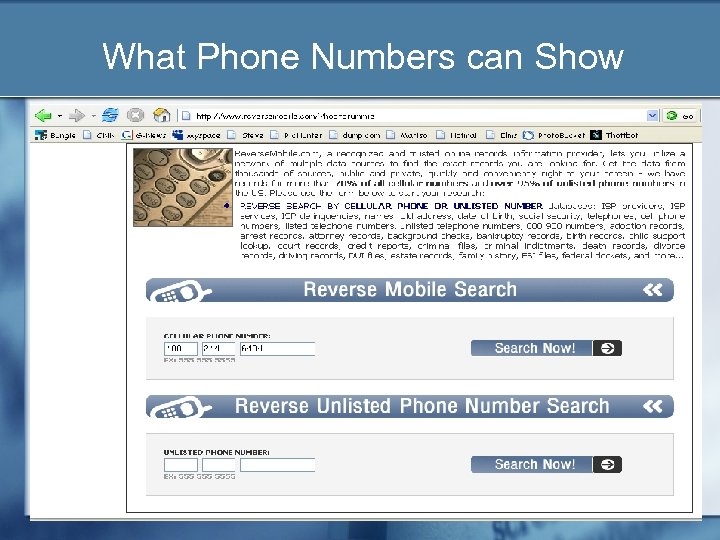
What Phone Numbers can Show

These are the rules Don’t Post: Name Age Phone Other personal information (but what does this include? )
Break Time Let’s take a 15 Minute break o Click on the Leave Room button right now. o When you return, click on the Enter Room button. When we all get back we will continue
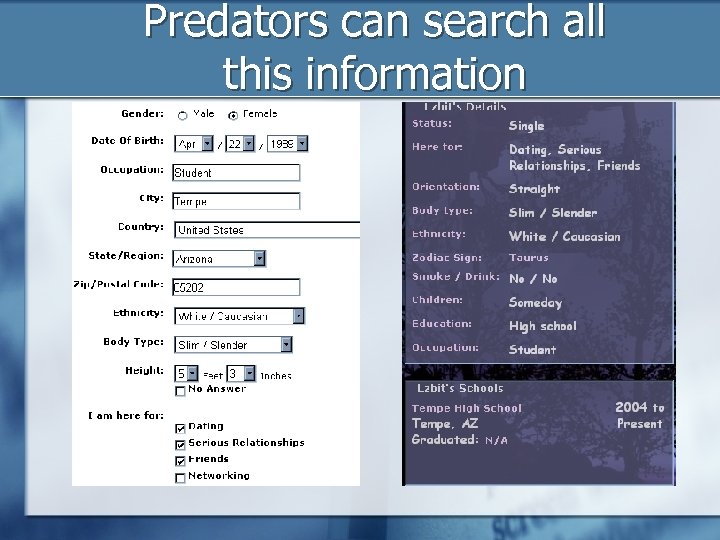
Predators can search all this information
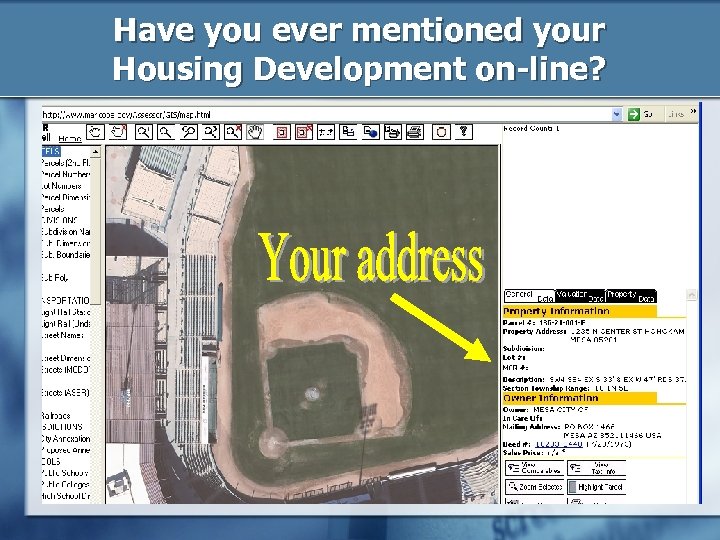
Have you ever mentioned your Housing Development on-line?
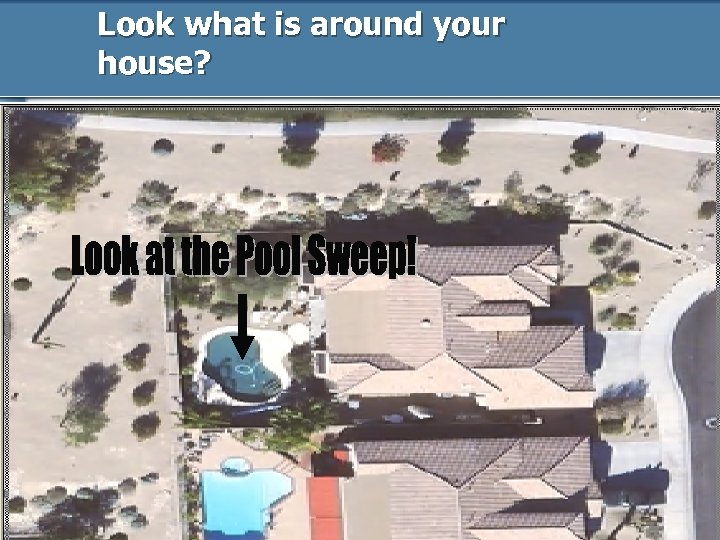
Look what is around your house?
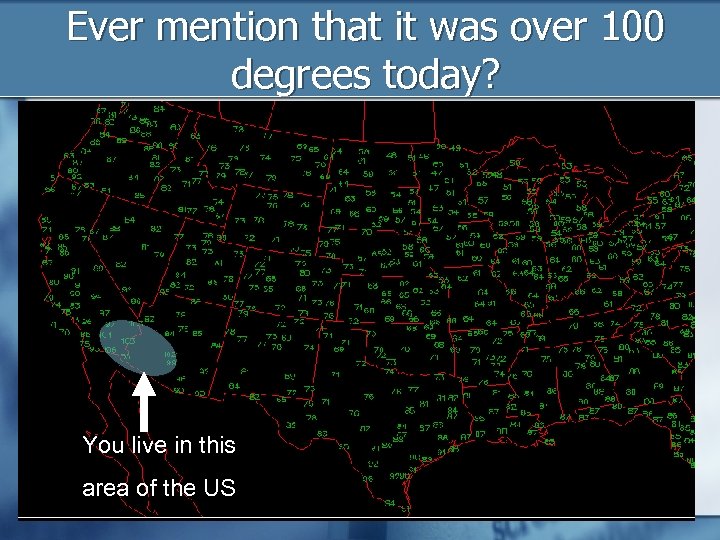
Ever mention that it was over 100 degrees today? You live in this area of the US

Add Statements like “We have a game tonight, Go Toros” What your friends share also point to you!

Consequences of Inappropriate Material Information you place on blog is public and everyone can see it. Zero tolerance policies – a picture of you holding a drink can disqualify you from opportunities. Even if you work for yourself you still have to satisfy your customers.

Real Examples v Texas teacher loses job and license because of Internet photos. v. St. Louis Journalist Loses Job because of Weblog v. List of people fired because of their blogs http: //homepage. mac. com/popemark/iblog/C 2041067432/E 372054822/

High School Musical Star posted inappropriate material She is a role model for your children
Consider this • Alison Chang went on a youth trip • She took pictures and posted them on the web
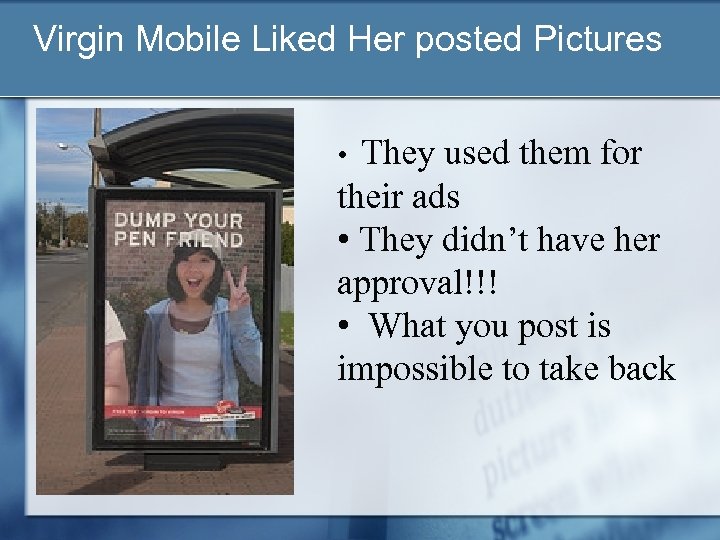
Virgin Mobile Liked Her posted Pictures They used them for their ads • They didn’t have her approval!!! • What you post is impossible to take back •
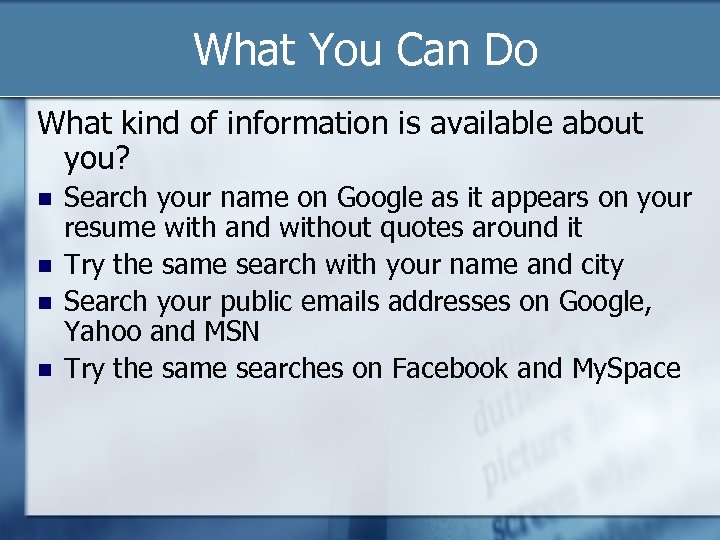
What You Can Do What kind of information is available about you? Search your name on Google as it appears on your resume with and without quotes around it Try the same search with your name and city Search your public emails addresses on Google, Yahoo and MSN Try the same searches on Facebook and My. Space
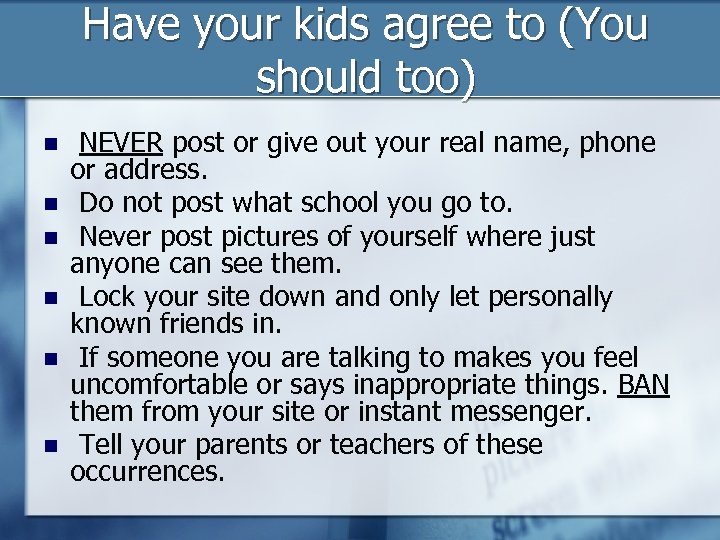
Have your kids agree to (You should too) NEVER post or give out your real name, phone or address. Do not post what school you go to. Never post pictures of yourself where just anyone can see them. Lock your site down and only let personally known friends in. If someone you are talking to makes you feel uncomfortable or says inappropriate things. BAN them from your site or instant messenger. Tell your parents or teachers of these occurrences.
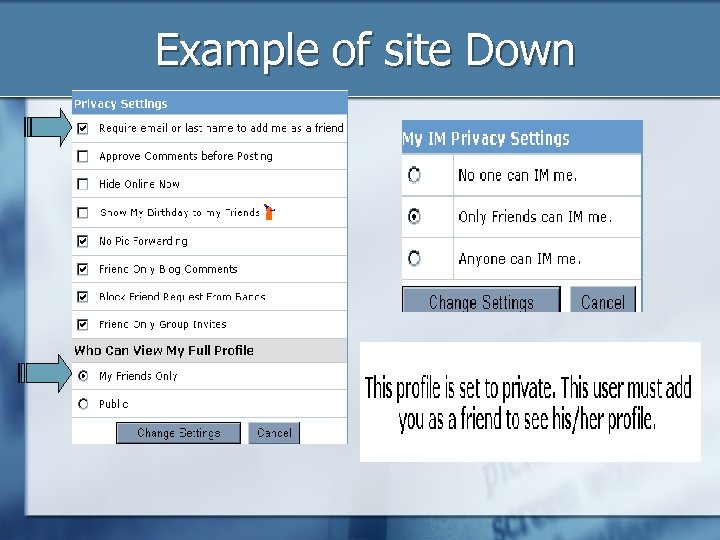
Example of site Down
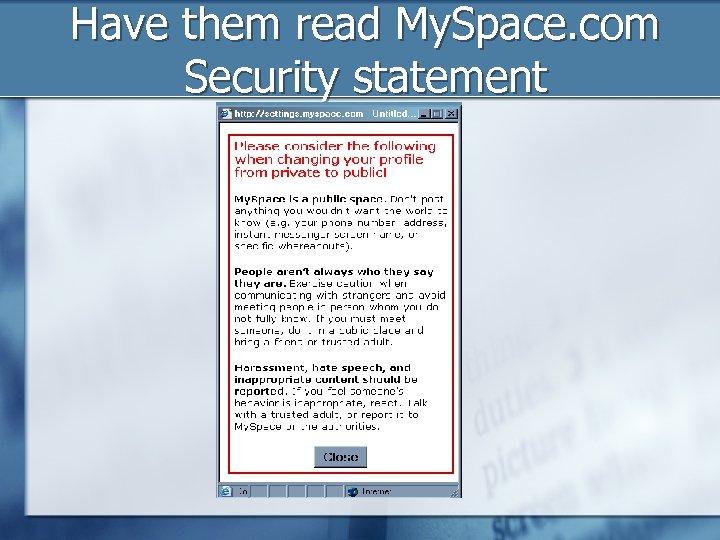
Have them read My. Space. com Security statement

Personal Information Summary No one knows who they actually are talking to Sign a Internet usage contract with your parents www. protectkids. com
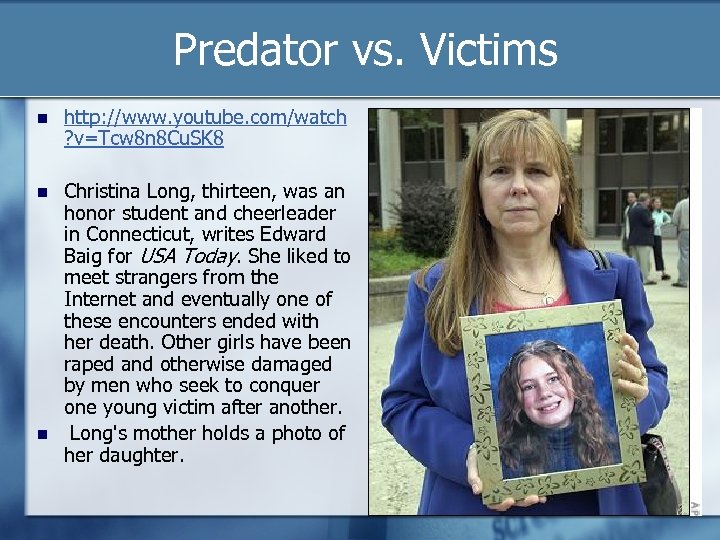
Predator vs. Victims http: //www. youtube. com/watch ? v=Tcw 8 n 8 Cu. SK 8 Christina Long, thirteen, was an honor student and cheerleader in Connecticut, writes Edward Baig for USA Today. She liked to meet strangers from the Internet and eventually one of these encounters ended with her death. Other girls have been raped and otherwise damaged by men who seek to conquer one young victim after another. Long's mother holds a photo of her daughter.

How do Predators operate? Their goal is to meet you face to face They attempt to make you dependent on them and draw you away from family They pretend that their likes and dislikes are the same as yours They will give you gifts Involve you in shameful activities. They can use this as blackmail if you decide that you don’t want a face to face meeting
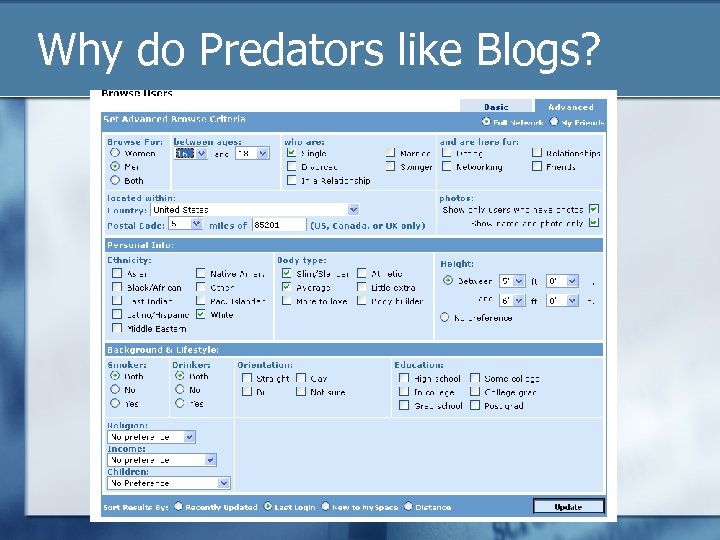
Why do Predators like Blogs?
You need to understand this! http: //msnbc. msn. com/id/9878187/ Internet Predator sting operation WA DC (2004): 18 men in 2 and ½ days WA DC (2005): 19 men in 2 and ½ days CA (2006): 51 men in 3 days

And what were their excuses? This is my first time doing this They told me that they were older I would not have harmed them I was concerned that the youth was home alone so came over to keep them company I was trying to teach them a lesson about talking to strangers on the Internet

Cyber Bullying What is Cyber Bullying? "Cyber bullying" is when teen is tormented, threatened, harassed, humiliated, embarrassed or otherwise targeted by another teen using the Internet, interactive and digital technologies or mobile phones. It has to have a minor on both sides, or at least have been instigated by a minor against another minor. Once adults become involved, it is plain and simple cyber-harassment or cyber stalking. Adult cyberharassment or cyber stalking is NEVER called cyber bullying.

Types of Cyberbullying The kind of threat: The communication uses lewd language The communication insults you directly (“You are stupid!”) The communication threatens you vaguely (“I’m going to get you!”) The communication threatens you with bodily harm. (“I’m going to beat you up!”) There is a general serious threat. (“There is a bomb in the school!” or “Don’t take the school bus today!”) The communication threatens you with serious bodily harm or death (“I am going to break your legs!” or “I am going to kill you!”)

How to Stop it? You as parents must know what your kids are doing Tell them to: o o Inform your School Inform the Police When notifying these people make sure you print out and have copies of the solicited information.
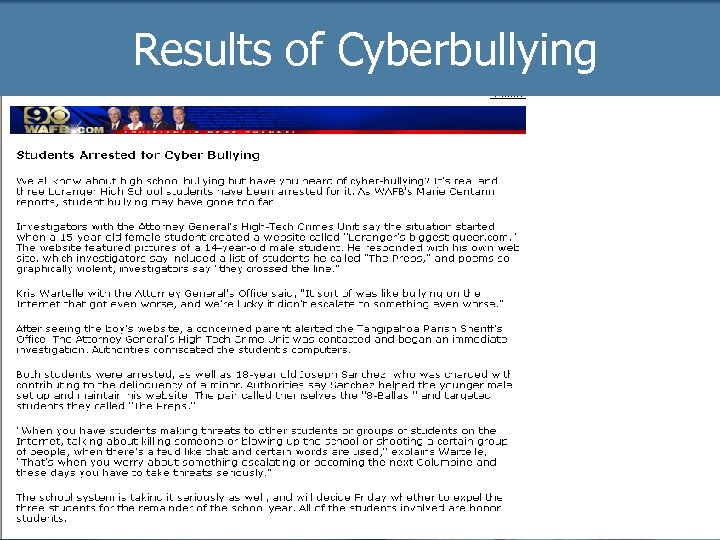
Results of Cyberbullying

Keys to success Be responsible Make adjustments in your life where needed Help your children to understand this Open communication with your kids so that they let you know what is going on Take control of home security

Statements to remember Discussion about 4 th of July “With freedom comes great responsibility. . . We are not set at liberty to pursue selfish ends. “ Even Spiderman said: "With great power comes great responsibility. "

Now you are ready to learn how to do this
318b491b00773bbd7db59a02eb34d90e.ppt