2af0646a9625a94881b3a9444f5b69aa.ppt
- Количество слайдов: 117
 Welcome to Fluke Network’s Wireless Networking Workshop!
Welcome to Fluke Network’s Wireless Networking Workshop!
 Your Fluke Networks Systems Engineer • Name: Carl Hohenstein • Contact #: 978 -250 -7360 • Email: Carl. Hohenstein@flukenetworks. com • Located in Northern Massachusetts 2
Your Fluke Networks Systems Engineer • Name: Carl Hohenstein • Contact #: 978 -250 -7360 • Email: Carl. Hohenstein@flukenetworks. com • Located in Northern Massachusetts 2
 Your Fluke Networks Account Manager • Name: Jon Tettambel (NYC Workshop Area) • Contact #: 201 -370 -7025 • Email: Jon. Tettambel@flukenetworks. com • Located in Basking Ridge, NJ 3
Your Fluke Networks Account Manager • Name: Jon Tettambel (NYC Workshop Area) • Contact #: 201 -370 -7025 • Email: Jon. Tettambel@flukenetworks. com • Located in Basking Ridge, NJ 3
 Your Fluke Networks Account Manager • Name: Chris Stark (Boston Workshop Area) • Contact #: 508 -278 -8089 • Email: Chris. Stark@flukenetworks. com • Located in Uxbridge MA 4
Your Fluke Networks Account Manager • Name: Chris Stark (Boston Workshop Area) • Contact #: 508 -278 -8089 • Email: Chris. Stark@flukenetworks. com • Located in Uxbridge MA 4
 Survey and Prize Drawing • Fill out customer information survey • How did you find out about the workshop? • What were your expectations? • Help us improve our workshops! • Comments? We’ll pick these up at the end for the drawing! 5
Survey and Prize Drawing • Fill out customer information survey • How did you find out about the workshop? • What were your expectations? • Help us improve our workshops! • Comments? We’ll pick these up at the end for the drawing! 5
 Agenda Wireless Growth - Where are YOU headed? Wireless Standards • • 802 Standards, Terminology, Frequencies A look at 802. 11 a, b, g Wireless A, B, C’s • A- Choose a PHY Layer Analyze. Air Wi-Fi Spectrum Analyzer • Detect, identify, and locate RF interference in 802. 11 WLANs • • B- Choose a Topology C- Choose a Security Method Interpert. Air WLAN Site Survey Software • Intelligent WLAN planning, verification, and expansion Ether. Scope Series II Network Assistant • Next generation network troubleshooter for 10, 100 and Gigabit, copper, fiber and wireless LANs. 6
Agenda Wireless Growth - Where are YOU headed? Wireless Standards • • 802 Standards, Terminology, Frequencies A look at 802. 11 a, b, g Wireless A, B, C’s • A- Choose a PHY Layer Analyze. Air Wi-Fi Spectrum Analyzer • Detect, identify, and locate RF interference in 802. 11 WLANs • • B- Choose a Topology C- Choose a Security Method Interpert. Air WLAN Site Survey Software • Intelligent WLAN planning, verification, and expansion Ether. Scope Series II Network Assistant • Next generation network troubleshooter for 10, 100 and Gigabit, copper, fiber and wireless LANs. 6
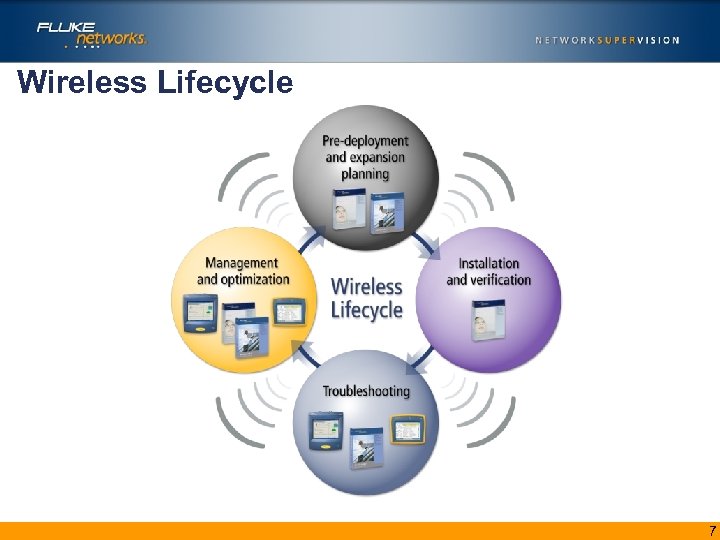 Wireless Lifecycle 7
Wireless Lifecycle 7
 Growing Excellence and Innovation 1993 Fluke Networks was founded as a division of Fluke Corporation, the world’s leading name in industrial test and measurement solutions. 1998 - $109 M Danaher Corporation, a $5 billion company with headquarters in Washington, D. C purchases Fluke Corporation. 2000 - $178 M Fluke Networks becomes a standalone company within the Danaher Corporation. 2005 - $261 M In the last 12 years, Fluke Networks products have won more awards for excellence than any other company in the industry— launching key industry firsts and leading the way in every category we serve. 8
Growing Excellence and Innovation 1993 Fluke Networks was founded as a division of Fluke Corporation, the world’s leading name in industrial test and measurement solutions. 1998 - $109 M Danaher Corporation, a $5 billion company with headquarters in Washington, D. C purchases Fluke Corporation. 2000 - $178 M Fluke Networks becomes a standalone company within the Danaher Corporation. 2005 - $261 M In the last 12 years, Fluke Networks products have won more awards for excellence than any other company in the industry— launching key industry firsts and leading the way in every category we serve. 8
 Fluke Networks Today • Part of a $7 B premiere global enterprise • Continuously profitable company since its inception • Over 500 associates worldwide Everett, WA: Worldwide Headquarters, Infrastructure Design Center Colorado Springs: Enterprise Networks Design Center Sales Offices & Associates: Worldwide 9
Fluke Networks Today • Part of a $7 B premiere global enterprise • Continuously profitable company since its inception • Over 500 associates worldwide Everett, WA: Worldwide Headquarters, Infrastructure Design Center Colorado Springs: Enterprise Networks Design Center Sales Offices & Associates: Worldwide 9
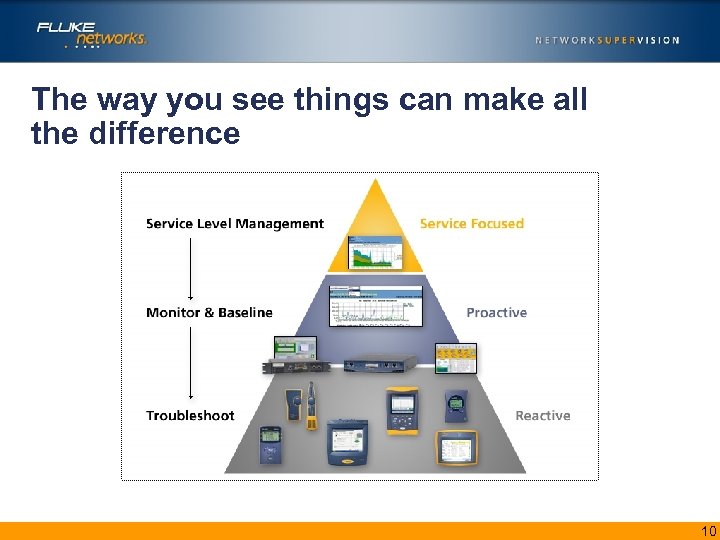 The way you see things can make all the difference 10
The way you see things can make all the difference 10
 Wireless- Growth “Where are YOU headed? ”
Wireless- Growth “Where are YOU headed? ”
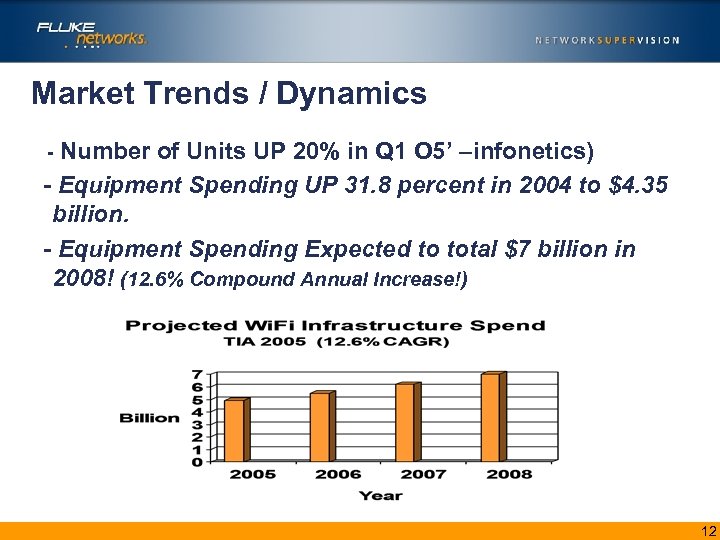 Market Trends / Dynamics - Number of Units UP 20% in Q 1 O 5’ –infonetics) - Equipment Spending UP 31. 8 percent in 2004 to $4. 35 billion. - Equipment Spending Expected to total $7 billion in 2008! (12. 6% Compound Annual Increase!) 12
Market Trends / Dynamics - Number of Units UP 20% in Q 1 O 5’ –infonetics) - Equipment Spending UP 31. 8 percent in 2004 to $4. 35 billion. - Equipment Spending Expected to total $7 billion in 2008! (12. 6% Compound Annual Increase!) 12
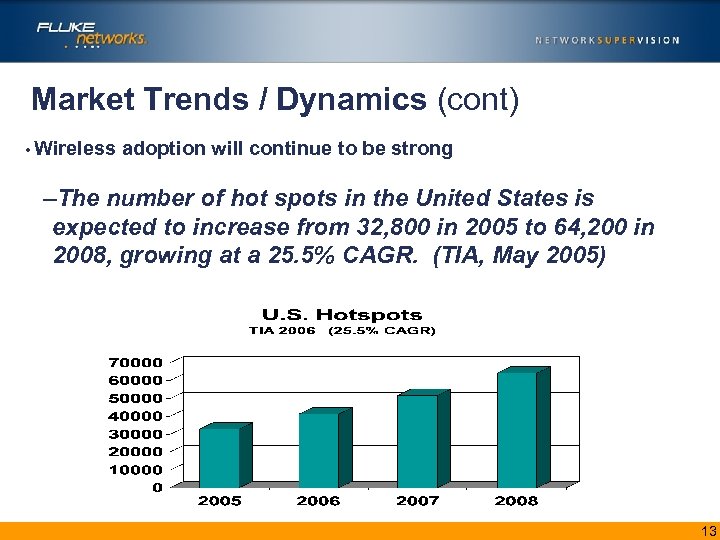 Market Trends / Dynamics (cont) • Wireless adoption will continue to be strong –The number of hot spots in the United States is expected to increase from 32, 800 in 2005 to 64, 200 in 2008, growing at a 25. 5% CAGR. (TIA, May 2005) 13
Market Trends / Dynamics (cont) • Wireless adoption will continue to be strong –The number of hot spots in the United States is expected to increase from 32, 800 in 2005 to 64, 200 in 2008, growing at a 25. 5% CAGR. (TIA, May 2005) 13
 Wireless “The Standards”
Wireless “The Standards”
 Wireless Standards OR (or 802. X) Welcome back to the IEEE 802 Standard for LAN Technologies: • 802. 3/802. 5 defines the MAC/PHY layer for Ethernet and TR LANS • 802. 1 defines Management (e. g. 802. 1 d, 802. 1 Q, 802. 1 X) • 802. 2 defines LLC • 802. 11 defines the MAC/PHY for Wireless! • 802. 11 a/b/g defines PHY Layer standards for wireless transmission • 802. 11 i defines robust WLAN security protocols (TKIP, CCMP) 802. 11 e for Qo. S and Throughput • 15
Wireless Standards OR (or 802. X) Welcome back to the IEEE 802 Standard for LAN Technologies: • 802. 3/802. 5 defines the MAC/PHY layer for Ethernet and TR LANS • 802. 1 defines Management (e. g. 802. 1 d, 802. 1 Q, 802. 1 X) • 802. 2 defines LLC • 802. 11 defines the MAC/PHY for Wireless! • 802. 11 a/b/g defines PHY Layer standards for wireless transmission • 802. 11 i defines robust WLAN security protocols (TKIP, CCMP) 802. 11 e for Qo. S and Throughput • 15
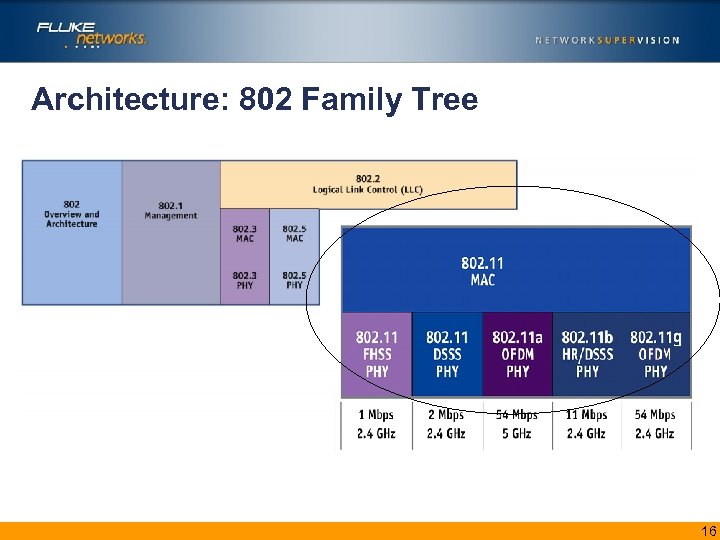 Architecture: 802 Family Tree 16
Architecture: 802 Family Tree 16
 Wireless A-B-Cs A-Pick a PHY Layer B- Pick a Topology C- Choose Security
Wireless A-B-Cs A-Pick a PHY Layer B- Pick a Topology C- Choose Security
 Wireless - PHY Basics Four PHY Layers Defined for WLAN Transmission • FHSS ( Frequency Hopping Spread Spectrum) • DSSS & HRDSS ((High-Rate)) Direct Sequence Spread Spectrum) • OFDM (Orthogonal Frequency Division Multiplexing) • PBCC (Packet Binary Convolution Coding) 18
Wireless - PHY Basics Four PHY Layers Defined for WLAN Transmission • FHSS ( Frequency Hopping Spread Spectrum) • DSSS & HRDSS ((High-Rate)) Direct Sequence Spread Spectrum) • OFDM (Orthogonal Frequency Division Multiplexing) • PBCC (Packet Binary Convolution Coding) 18
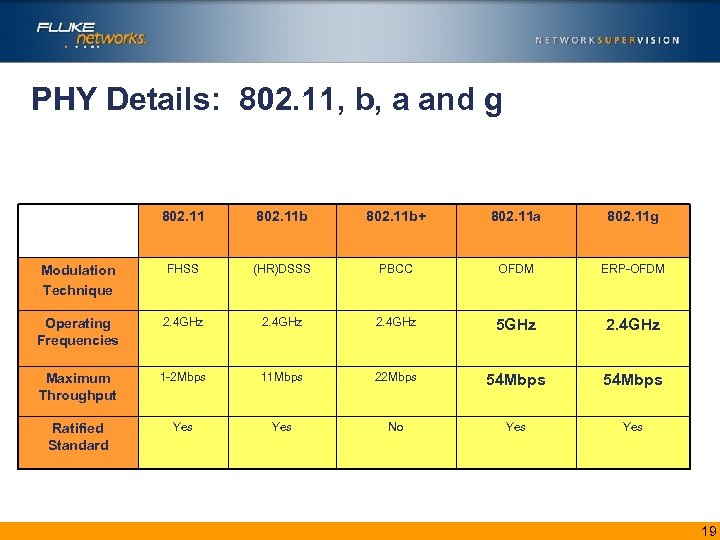 PHY Details: 802. 11, b, a and g 802. 11 b+ 802. 11 a 802. 11 g Modulation Technique FHSS (HR)DSSS PBCC OFDM ERP-OFDM Operating Frequencies 2. 4 GHz 5 GHz 2. 4 GHz Maximum Throughput 1 -2 Mbps 11 Mbps 22 Mbps 54 Mbps Ratified Standard Yes No Yes 19
PHY Details: 802. 11, b, a and g 802. 11 b+ 802. 11 a 802. 11 g Modulation Technique FHSS (HR)DSSS PBCC OFDM ERP-OFDM Operating Frequencies 2. 4 GHz 5 GHz 2. 4 GHz Maximum Throughput 1 -2 Mbps 11 Mbps 22 Mbps 54 Mbps Ratified Standard Yes No Yes 19
 802. 11 b • Uses 2. 4 GHz band – Industrial, Scientific, Medical (ISM) band – Shared with microwave ovens and 2. 4 GHz cordless telephones • 14 channels (11 in U. S. ) – 3 non-overlapping channels • Channels 1, 6, and 11 • Maximum speed is 11 Mbps – 1, 2, 5. 5, and 11 Mbps speeds 20
802. 11 b • Uses 2. 4 GHz band – Industrial, Scientific, Medical (ISM) band – Shared with microwave ovens and 2. 4 GHz cordless telephones • 14 channels (11 in U. S. ) – 3 non-overlapping channels • Channels 1, 6, and 11 • Maximum speed is 11 Mbps – 1, 2, 5. 5, and 11 Mbps speeds 20
 802. 11 g • Uses same 2. 4 GHz band as 802. 11 b – Industrial, Scientific, Medical (ISM) band – Shared with microwave ovens and 2. 4 GHz cordless telephones • 14 channels (11 in U. S. ) – 3 non-overlapping channels • Channels 1, 6, and 11 • Maximum speed is 54 Mbps (raw) – 1, 2, 5. 5, and 11 Mbps speeds (802. 11 b) – 6, 9, 12, 18, 24 Mbps speeds (required) – 36, 48, and 54 Mbps speeds (optional) 21
802. 11 g • Uses same 2. 4 GHz band as 802. 11 b – Industrial, Scientific, Medical (ISM) band – Shared with microwave ovens and 2. 4 GHz cordless telephones • 14 channels (11 in U. S. ) – 3 non-overlapping channels • Channels 1, 6, and 11 • Maximum speed is 54 Mbps (raw) – 1, 2, 5. 5, and 11 Mbps speeds (802. 11 b) – 6, 9, 12, 18, 24 Mbps speeds (required) – 36, 48, and 54 Mbps speeds (optional) 21
 802. 11 a • Uses 5 GHz band – Unlicensed National Information Infrastructure (U-NII) band – 12 channels • NO overlapping channels • Maximum speed is 54 Mbps – 6, 12, and 24 Mbps (mandatory) – 9, 18, 36, and 54 Mbps (optional) 22
802. 11 a • Uses 5 GHz band – Unlicensed National Information Infrastructure (U-NII) band – 12 channels • NO overlapping channels • Maximum speed is 54 Mbps – 6, 12, and 24 Mbps (mandatory) – 9, 18, 36, and 54 Mbps (optional) 22
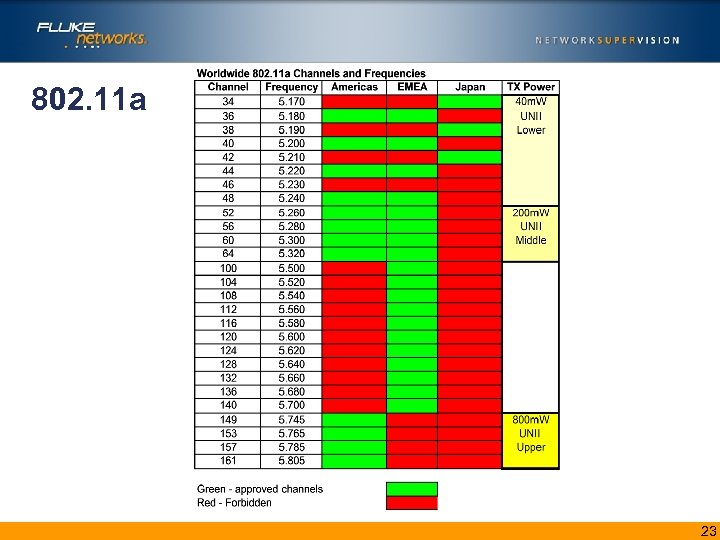 802. 11 a 23
802. 11 a 23
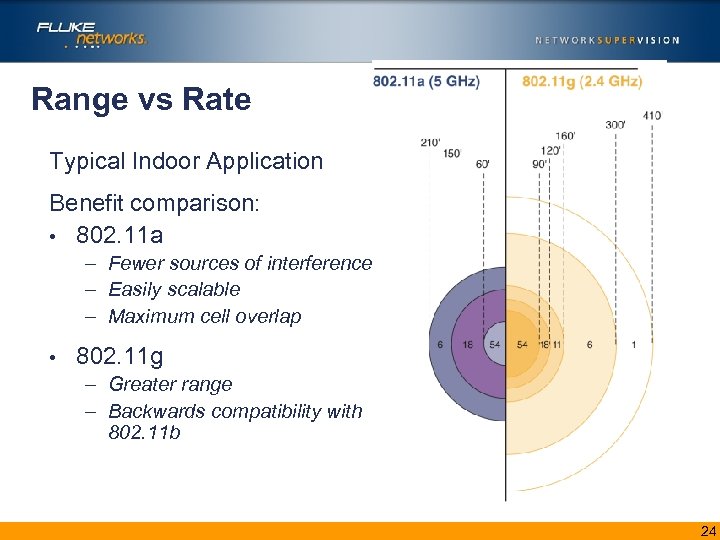 Range vs Rate Typical Indoor Application Benefit comparison: • 802. 11 a – Fewer sources of interference – Easily scalable – Maximum cell overlap • 802. 11 g – Greater range – Backwards compatibility with 802. 11 b 24
Range vs Rate Typical Indoor Application Benefit comparison: • 802. 11 a – Fewer sources of interference – Easily scalable – Maximum cell overlap • 802. 11 g – Greater range – Backwards compatibility with 802. 11 b 24
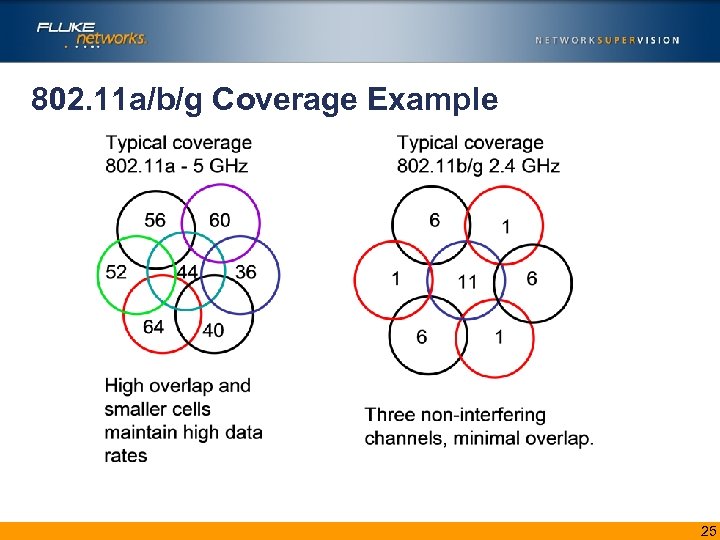 802. 11 a/b/g Coverage Example 25
802. 11 a/b/g Coverage Example 25
 Trends • 802. 11 g is by far the leading WLAN technology in enterprise (new install), followed by 802. 11 b (largest installed base) – Both are 2. 4 GHz. • 802. 11 a is still around, but growth is slow. • 802. 11 n in development for 100 Mb/s – 600 Mb/s speeds 26
Trends • 802. 11 g is by far the leading WLAN technology in enterprise (new install), followed by 802. 11 b (largest installed base) – Both are 2. 4 GHz. • 802. 11 a is still around, but growth is slow. • 802. 11 n in development for 100 Mb/s – 600 Mb/s speeds 26
 Wireless- RF Spectrum Analysis with FLUKE Networks Analyze Air™ Wi-Fi Spectrum Analyzer
Wireless- RF Spectrum Analysis with FLUKE Networks Analyze Air™ Wi-Fi Spectrum Analyzer
 Wireless Challenges? • Wireless network performance depends upon a “clean” RF environment – Unregulated/crowded nature of ISM band makes tracking down interference source difficult – Lack of spectrum use policies means the unexpected is common – RF problems are rarely continuous; makes finding them much harder – You must ALWAYS suspect the physical layer first! • Interference issues cannot be found with typical Wi-Fi card -based software tools! 28
Wireless Challenges? • Wireless network performance depends upon a “clean” RF environment – Unregulated/crowded nature of ISM band makes tracking down interference source difficult – Lack of spectrum use policies means the unexpected is common – RF problems are rarely continuous; makes finding them much harder – You must ALWAYS suspect the physical layer first! • Interference issues cannot be found with typical Wi-Fi card -based software tools! 28
 The solution is Analyze. Air! Analyze. Air™ Wi-Fi Spectrum Analyzer Detect, identify, and locate RF interference in 802. 11 WLANs Solve physical layer problems that prevent wireless connectivity • RF spectrum analysis for troubleshooting and optimizing Wireless LANs • Real-time device detection, identification and location • Takes the cost and complexity out of wireless RF analysis • Decodes the spectrum to tell you what’s using your network • Make your WLAN network perform optimally – Critical for high-demand applications like Vo. WLAN Simple to use for IT professionals, powerful enough for RF experts 29
The solution is Analyze. Air! Analyze. Air™ Wi-Fi Spectrum Analyzer Detect, identify, and locate RF interference in 802. 11 WLANs Solve physical layer problems that prevent wireless connectivity • RF spectrum analysis for troubleshooting and optimizing Wireless LANs • Real-time device detection, identification and location • Takes the cost and complexity out of wireless RF analysis • Decodes the spectrum to tell you what’s using your network • Make your WLAN network perform optimally – Critical for high-demand applications like Vo. WLAN Simple to use for IT professionals, powerful enough for RF experts 29
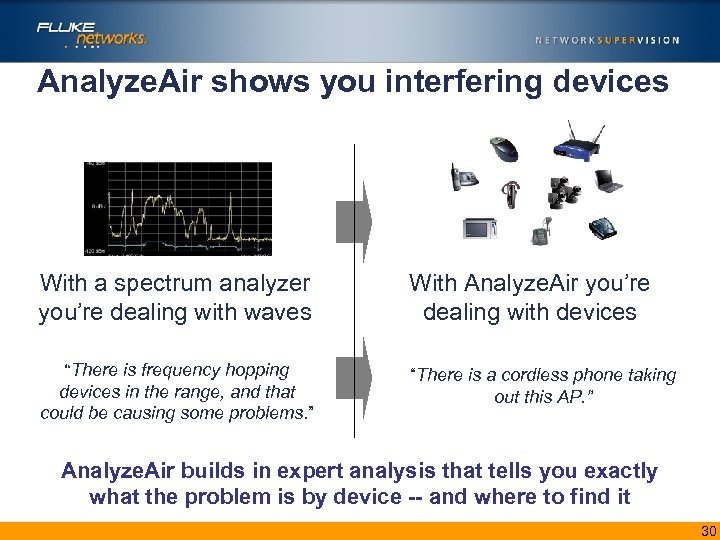 Analyze. Air shows you interfering devices With a spectrum analyzer you’re dealing with waves “There is frequency hopping devices in the range, and that could be causing some problems. ” With Analyze. Air you’re dealing with devices “There is a cordless phone taking out this AP. ” Analyze. Air builds in expert analysis that tells you exactly what the problem is by device -- and where to find it 30
Analyze. Air shows you interfering devices With a spectrum analyzer you’re dealing with waves “There is frequency hopping devices in the range, and that could be causing some problems. ” With Analyze. Air you’re dealing with devices “There is a cordless phone taking out this AP. ” Analyze. Air builds in expert analysis that tells you exactly what the problem is by device -- and where to find it 30
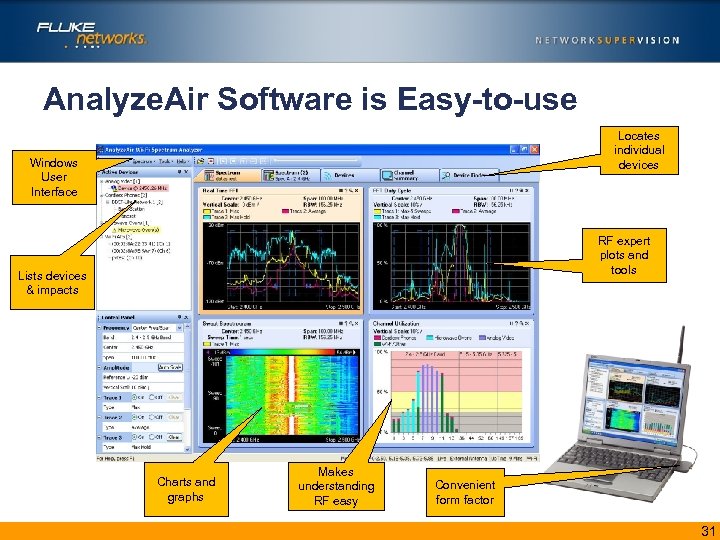 Analyze. Air Software is Easy-to-use Locates individual devices Windows User Interface RF expert plots and tools Lists devices & impacts Charts and graphs Makes understanding RF easy Convenient form factor 31
Analyze. Air Software is Easy-to-use Locates individual devices Windows User Interface RF expert plots and tools Lists devices & impacts Charts and graphs Makes understanding RF easy Convenient form factor 31
 Customer Story -- Stock Trading Floor • US based stock trading floor – Open 4 story high environment • Executives on the 4 th story heats up danish in a microwave – Microwave took over 50% of Wi-Fi channel 11 – Caused major problems on trading floor • IT dept did everything right in Wi-Fi installation – Performed a site survey and brought in a spectrum analyzer • Except they checked on the weekend when no one was using the microwave! • Our solution found the problem in minutes – Fixed the problem by changing the microwave – Problem had existed for months! 32
Customer Story -- Stock Trading Floor • US based stock trading floor – Open 4 story high environment • Executives on the 4 th story heats up danish in a microwave – Microwave took over 50% of Wi-Fi channel 11 – Caused major problems on trading floor • IT dept did everything right in Wi-Fi installation – Performed a site survey and brought in a spectrum analyzer • Except they checked on the weekend when no one was using the microwave! • Our solution found the problem in minutes – Fixed the problem by changing the microwave – Problem had existed for months! 32
 Customer Story -- Hospital’s security dept installed video camera due to high theft rate without telling IT dept • The cameras interfered with channels 6 & 11 • IT hired an RF engineer to do a site survey • – Recommended to only use channel 1 in impacted areas • IT not satisfied with RF engineer’s response – Purchased our solution – In 30 minutes found 4 analog video cameras causing problem – Working with security to find 802. 11 compliant cameras – Problem had existed for months 33
Customer Story -- Hospital’s security dept installed video camera due to high theft rate without telling IT dept • The cameras interfered with channels 6 & 11 • IT hired an RF engineer to do a site survey • – Recommended to only use channel 1 in impacted areas • IT not satisfied with RF engineer’s response – Purchased our solution – In 30 minutes found 4 analog video cameras causing problem – Working with security to find 802. 11 compliant cameras – Problem had existed for months 33
 Analyze. Air Components • Analyze. Air consists of both hardware and software – – • Analyze. Air PC card Software CD Omni antenna Directional antenna Analyze. Air runs on either a: – Opti. View™ Series II Integrated Network Analyzer – Laptop or tablet PC 34
Analyze. Air Components • Analyze. Air consists of both hardware and software – – • Analyze. Air PC card Software CD Omni antenna Directional antenna Analyze. Air runs on either a: – Opti. View™ Series II Integrated Network Analyzer – Laptop or tablet PC 34
 System Requirements • • Opti. View™ Series II Integrated Network Analyzer or Laptop/tablet computer with Pentium® series processor running at 1 GHz or faster Windows® 2000 SP 4 or Windows® XP SP 1 or SP 2 512 MB RAM Display resolution of 800 x 600 or higher (1024 x 768 recommended) 30 MB of available hard disk space Available Card. Bus slot in laptop/tablet PC 802. 11 capability (recommended) CD or DVD drive 35
System Requirements • • Opti. View™ Series II Integrated Network Analyzer or Laptop/tablet computer with Pentium® series processor running at 1 GHz or faster Windows® 2000 SP 4 or Windows® XP SP 1 or SP 2 512 MB RAM Display resolution of 800 x 600 or higher (1024 x 768 recommended) 30 MB of available hard disk space Available Card. Bus slot in laptop/tablet PC 802. 11 capability (recommended) CD or DVD drive 35
 Wireless A-B-C A-Pick a PHY Layer B- Pick a Topology C- Choose Security
Wireless A-B-C A-Pick a PHY Layer B- Pick a Topology C- Choose Security
 Wireless- Choose a Topology • Basic Service Set (BSS) – A group of stations communicating with each other • Independent Basic Service Set (IBSS) – BSS communicating in Ad-Hoc Mode • Infrastructure Basic Service Set (Infrastructure BSS) – BSS communicating in Infrastructure (AP) Mode • Extended Service Set (ESS) – BSS’s connected together through a backbone network 37
Wireless- Choose a Topology • Basic Service Set (BSS) – A group of stations communicating with each other • Independent Basic Service Set (IBSS) – BSS communicating in Ad-Hoc Mode • Infrastructure Basic Service Set (Infrastructure BSS) – BSS communicating in Infrastructure (AP) Mode • Extended Service Set (ESS) – BSS’s connected together through a backbone network 37
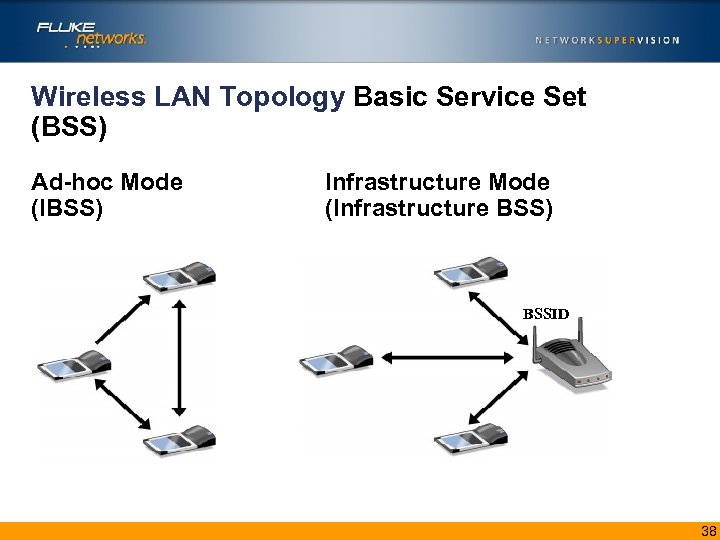 Wireless LAN Topology Basic Service Set (BSS) Ad-hoc Mode (IBSS) Infrastructure Mode (Infrastructure BSS) BSSID 38
Wireless LAN Topology Basic Service Set (BSS) Ad-hoc Mode (IBSS) Infrastructure Mode (Infrastructure BSS) BSSID 38
 Wireless- Choose a Topology • BSSID (Basic Service Set Identifier) – Usually the MAC address of the AP hosting the BSS clients – Used by all BSS Stations in the Frame Header • SSID (Service Set Identifier) – Name given to all AP’s in an ESS – Transmitted in non-encrypted management frames 39
Wireless- Choose a Topology • BSSID (Basic Service Set Identifier) – Usually the MAC address of the AP hosting the BSS clients – Used by all BSS Stations in the Frame Header • SSID (Service Set Identifier) – Name given to all AP’s in an ESS – Transmitted in non-encrypted management frames 39
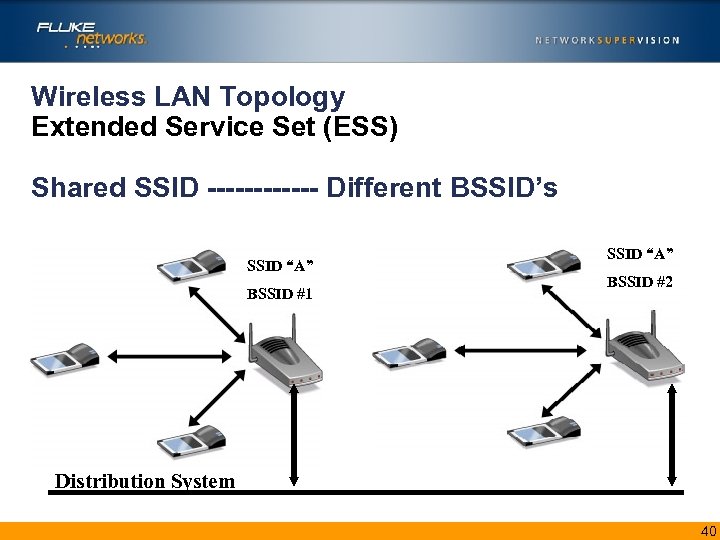 Wireless LAN Topology Extended Service Set (ESS) Shared SSID ------ Different BSSID’s SSID “A” BSSID #1 SSID “A” BSSID #2 Distribution System 40
Wireless LAN Topology Extended Service Set (ESS) Shared SSID ------ Different BSSID’s SSID “A” BSSID #1 SSID “A” BSSID #2 Distribution System 40
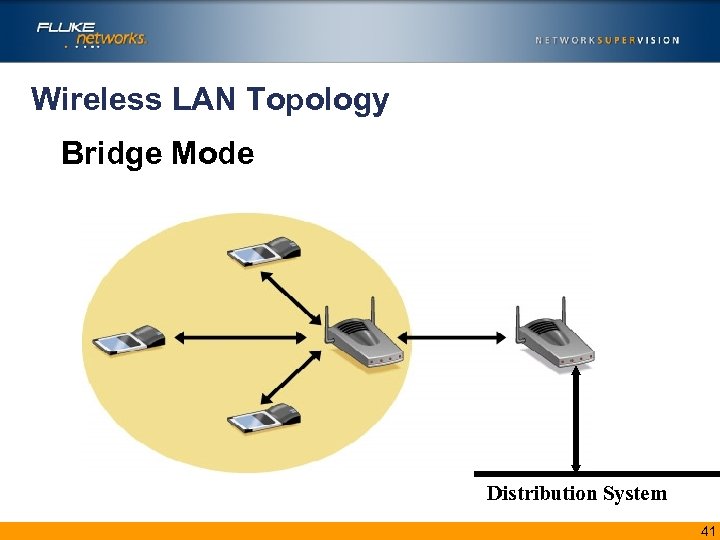 Wireless LAN Topology Bridge Mode Distribution System 41
Wireless LAN Topology Bridge Mode Distribution System 41
 Wireless- Choose a Topology • Beacons – Announce the existence of a network and it’s parameters – Define the basic service area for a BSS • Probe Requests – Used by stations to scan an area for existing 802. 11 networks – Include the SSID and rates supported by the station • Probe Responses – Sent in response to Probe Requests by the AP or assigned Ad-Hoc Station – Contain all information found in the Beacon Frame 42
Wireless- Choose a Topology • Beacons – Announce the existence of a network and it’s parameters – Define the basic service area for a BSS • Probe Requests – Used by stations to scan an area for existing 802. 11 networks – Include the SSID and rates supported by the station • Probe Responses – Sent in response to Probe Requests by the AP or assigned Ad-Hoc Station – Contain all information found in the Beacon Frame 42
 Wireless- Choose a Topology • 802. 11 Authentication (Two-Step) – The process of a station identifying itself before being allowed to transmit frames • Association (Two-Step) – The process of a station “registering” with a chosen AP AFTER 802. 11 authentication. The AP registers the station on the network. Association is the equivalent of “plugging in” to a wired network. 43
Wireless- Choose a Topology • 802. 11 Authentication (Two-Step) – The process of a station identifying itself before being allowed to transmit frames • Association (Two-Step) – The process of a station “registering” with a chosen AP AFTER 802. 11 authentication. The AP registers the station on the network. Association is the equivalent of “plugging in” to a wired network. 43
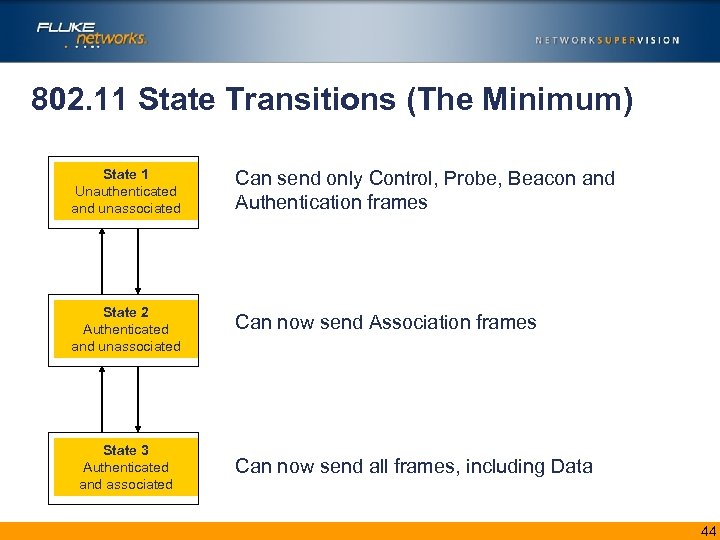 802. 11 State Transitions (The Minimum) State 1 Unauthenticated and unassociated Can send only Control, Probe, Beacon and Authentication frames State 2 Authenticated and unassociated Can now send Association frames State 3 Authenticated and associated Can now send all frames, including Data 44
802. 11 State Transitions (The Minimum) State 1 Unauthenticated and unassociated Can send only Control, Probe, Beacon and Authentication frames State 2 Authenticated and unassociated Can now send Association frames State 3 Authenticated and associated Can now send all frames, including Data 44
 Wireless A-B-C A-Pick a PHY Layer B- Pick a Topology C- Choose Security
Wireless A-B-C A-Pick a PHY Layer B- Pick a Topology C- Choose Security
 WLAN Security Q&A Key Questions: – How can I protect against war drivers? – Are there rogue devices in my network? – How does wireless relate to my other security solutions? Challenges: – The rogue user (Geek, thief, or both? ) – User Policy – Authentication + Encryption Result: – Secured wireless network 46
WLAN Security Q&A Key Questions: – How can I protect against war drivers? – Are there rogue devices in my network? – How does wireless relate to my other security solutions? Challenges: – The rogue user (Geek, thief, or both? ) – User Policy – Authentication + Encryption Result: – Secured wireless network 46
 Let me introduce you to “The War Driver” 47
Let me introduce you to “The War Driver” 47
 “The War Driver” Tools of the trade! 48
“The War Driver” Tools of the trade! 48
 The User Policy Challenge: How do I ensure users aren’t bringing in rogue equipment from home? Fact: You have wireless, whether you know it or not. . . – – – Home APs cost <$50 and are widely available Home equipment may not respond to SNMP queries All home equipment is a security hole out of the box Design Approaches: – – Outlaw private wireless LAN equipment Enforce the policy with periodic walkthroughs (ES Search!) 49
The User Policy Challenge: How do I ensure users aren’t bringing in rogue equipment from home? Fact: You have wireless, whether you know it or not. . . – – – Home APs cost <$50 and are widely available Home equipment may not respond to SNMP queries All home equipment is a security hole out of the box Design Approaches: – – Outlaw private wireless LAN equipment Enforce the policy with periodic walkthroughs (ES Search!) 49
 The Authentication + Encryption Challenges: My authentication methods are top-notch so I’m safe, right? My WLAN data is encrypted so I’m safe, right? 50
The Authentication + Encryption Challenges: My authentication methods are top-notch so I’m safe, right? My WLAN data is encrypted so I’m safe, right? 50
 WLAN Security = Authentication + Encryption Early Security “Solutions” – Don’t Send Beacons? – Don’t Broadcast my SSID? – Filter MAC addresses? – How about a VPN? 51
WLAN Security = Authentication + Encryption Early Security “Solutions” – Don’t Send Beacons? – Don’t Broadcast my SSID? – Filter MAC addresses? – How about a VPN? 51
 WLAN Security = Authentication + Encryption “Trivial” Authentication Methods Include – – OPEN WEP (Wired Equivalency Protocol) WPA-PSK (Wi-Fi Protected Access/Pre-shared Key) Also called 802. 11 i-PSK These methods can be easily Hacked!! 52
WLAN Security = Authentication + Encryption “Trivial” Authentication Methods Include – – OPEN WEP (Wired Equivalency Protocol) WPA-PSK (Wi-Fi Protected Access/Pre-shared Key) Also called 802. 11 i-PSK These methods can be easily Hacked!! 52
 802. 1 X AUTHENTICATION The premise of 802. 1 X is to authenticate the User NOT the machine – Also Called WPA or WPA “Enterprise” – Based on the Extensible Authentication Framework Protocol (EAP) – Uses a RADIUS server to provide authorization, authentication and accounting (AAA) services – Does not specify authentication mechanism 53
802. 1 X AUTHENTICATION The premise of 802. 1 X is to authenticate the User NOT the machine – Also Called WPA or WPA “Enterprise” – Based on the Extensible Authentication Framework Protocol (EAP) – Uses a RADIUS server to provide authorization, authentication and accounting (AAA) services – Does not specify authentication mechanism 53
 802. 1 X- Different EAP Methods • LEAP (Lightweight EAP) • TLS (Transport Layer Security) • TTLS (Tunneled TLS) & PEAP (Protected EAP) – Establish a TLS tunnel w/certificates – Encrypt a legacy or unencrypted authentication Protocol – Examples of “inner” authentication protocols include: • Eap-MD 5 Challenge, • EAP-Generic Token Card, • EAP-MSCHAP-V 2 – Non-Eap include: • • PAP CHAP MS-CHAP LDAP Kerberos 54
802. 1 X- Different EAP Methods • LEAP (Lightweight EAP) • TLS (Transport Layer Security) • TTLS (Tunneled TLS) & PEAP (Protected EAP) – Establish a TLS tunnel w/certificates – Encrypt a legacy or unencrypted authentication Protocol – Examples of “inner” authentication protocols include: • Eap-MD 5 Challenge, • EAP-Generic Token Card, • EAP-MSCHAP-V 2 – Non-Eap include: • • PAP CHAP MS-CHAP LDAP Kerberos 54
 WLAN Security = Authentication + Encryption Methods: • WEP (Wired Equivalency Protocol) • Dynamic WEP (w/802. 1 X) • TKIP (802. 11 i - Temporal Key Integrity Protocol) • CCMP (802. 11 i - Counter Mode with CBC-MAC Protocol) – also known as WPA-2 57
WLAN Security = Authentication + Encryption Methods: • WEP (Wired Equivalency Protocol) • Dynamic WEP (w/802. 1 X) • TKIP (802. 11 i - Temporal Key Integrity Protocol) • CCMP (802. 11 i - Counter Mode with CBC-MAC Protocol) – also known as WPA-2 57
 WEP Overview Request Challenge Static Key Request Granted 58
WEP Overview Request Challenge Static Key Request Granted 58
 The WEP Challenge Can I count on WEP as my security solution? Fact: WEP has 3 Critical Flaws – 40 AND 128 bit keys can be easily hacked – re-keying clients is a management nightmare – susceptible to “man-in-the-middle” attacks Design Approaches: – Several Short-term solutions – A couple of emerging long-term solutions 59
The WEP Challenge Can I count on WEP as my security solution? Fact: WEP has 3 Critical Flaws – 40 AND 128 bit keys can be easily hacked – re-keying clients is a management nightmare – susceptible to “man-in-the-middle” attacks Design Approaches: – Several Short-term solutions – A couple of emerging long-term solutions 59
 WPA (Wi-Fi Protected Access) • Improves WEP by adding key management and addressing flaws in original WEP • Uses 802. 1 X for Authentication • Uses TKIP for Encryption 60
WPA (Wi-Fi Protected Access) • Improves WEP by adding key management and addressing flaws in original WEP • Uses 802. 1 X for Authentication • Uses TKIP for Encryption 60
 Encryption Key Management • TKIP (Temporal Key Integrity Protocol) – Manages/changes WEP keys – Multiple Master Keys – Per-Frame Keying – Sequence Counter – New Message Integrity Check (MIC) – Launch of Counter-measures! (Re-check validation, shut-down communications, Key refresh) 61
Encryption Key Management • TKIP (Temporal Key Integrity Protocol) – Manages/changes WEP keys – Multiple Master Keys – Per-Frame Keying – Sequence Counter – New Message Integrity Check (MIC) – Launch of Counter-measures! (Re-check validation, shut-down communications, Key refresh) 61
 WPA 2 • Improves on WEP by addressing the last “flaw” – Based on 802. 11 i standard – RC 4 encryption mechanism is replaced by AES (Advanced Encryption Standard) which is much more robust. • Requires appropriate chipset in Access Point • FIPS 140 -2 eligible (Government approved – strong encryption) 62
WPA 2 • Improves on WEP by addressing the last “flaw” – Based on 802. 11 i standard – RC 4 encryption mechanism is replaced by AES (Advanced Encryption Standard) which is much more robust. • Requires appropriate chipset in Access Point • FIPS 140 -2 eligible (Government approved – strong encryption) 62
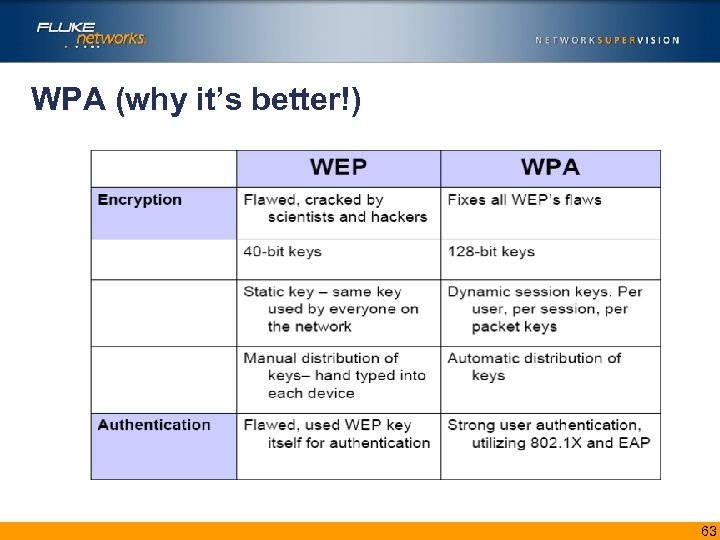 WPA (why it’s better!) 63
WPA (why it’s better!) 63
 So, What can I do? • “War drivers” will access your network if you leave an open door. – Most will look for easier targets if you have ANY security – WEP is enough to discourage only casual users • Remember, WEP is completely ineffective against real hackers!! – Use WPA at the very least, and if possible WPA 2, with 802. 1 x authentication 64
So, What can I do? • “War drivers” will access your network if you leave an open door. – Most will look for easier targets if you have ANY security – WEP is enough to discourage only casual users • Remember, WEP is completely ineffective against real hackers!! – Use WPA at the very least, and if possible WPA 2, with 802. 1 x authentication 64
 Wireless - Site Survey with FLUKE Networks Interpret. Air WLAN Site Survey
Wireless - Site Survey with FLUKE Networks Interpret. Air WLAN Site Survey
 Traditional Site Survey Issues – Time wasted in rework from trial-and-error placement of APs – Are there coverage ‘holes’ or areas of performance problems? – How do you ensure that the network you plan and install today will meet tomorrow’s requirements? 66
Traditional Site Survey Issues – Time wasted in rework from trial-and-error placement of APs – Are there coverage ‘holes’ or areas of performance problems? – How do you ensure that the network you plan and install today will meet tomorrow’s requirements? 66
 The solution is Interpret. Air! Interpret. Air™ WLAN Site Survey Software Intelligent WLAN planning, verification, and expansion Easily plan, simulate, and verify wireless networks using graphic visualization • Easily and graphically survey 802. 11 a/b/g wireless networks • Visualize RF health using a customizable combination of performance parameters • Discover areas of sub-optimal coverage • Tune RF performance • Document WLAN environment Maximize performance, minimize deployment time 67
The solution is Interpret. Air! Interpret. Air™ WLAN Site Survey Software Intelligent WLAN planning, verification, and expansion Easily plan, simulate, and verify wireless networks using graphic visualization • Easily and graphically survey 802. 11 a/b/g wireless networks • Visualize RF health using a customizable combination of performance parameters • Discover areas of sub-optimal coverage • Tune RF performance • Document WLAN environment Maximize performance, minimize deployment time 67
 What is the objective of a site survey? Design for Coverage Design for Performance Vs. • Clear specifications must be agreed upon before any survey work can begin: – Desired data rate – AP coverage/count - % of facility, # of Users – Plan for growth! – Signal strength – Signal to Noise Ratio • Desired applications drive specifications – “Normal” client use (How might it change? ) – Vo. WLAN – Specialized applications (healthcare patient telemetry, etc. ) Other Considerations: • AP Mounting • Cabling 68
What is the objective of a site survey? Design for Coverage Design for Performance Vs. • Clear specifications must be agreed upon before any survey work can begin: – Desired data rate – AP coverage/count - % of facility, # of Users – Plan for growth! – Signal strength – Signal to Noise Ratio • Desired applications drive specifications – “Normal” client use (How might it change? ) – Vo. WLAN – Specialized applications (healthcare patient telemetry, etc. ) Other Considerations: • AP Mounting • Cabling 68
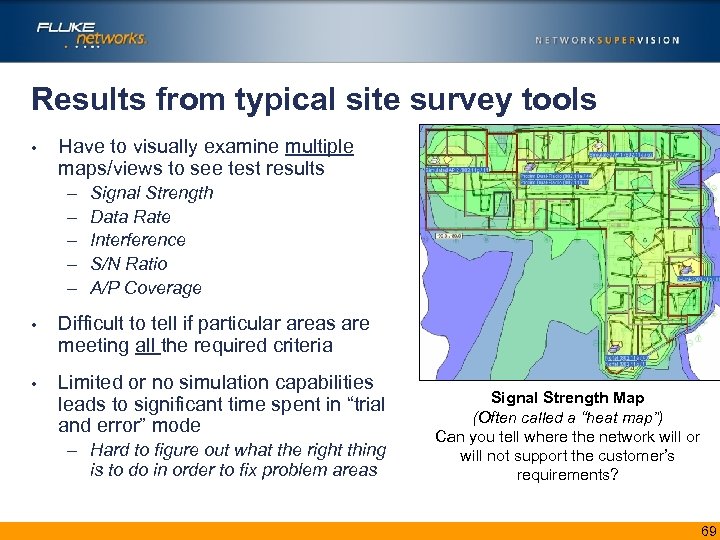 Results from typical site survey tools • Have to visually examine multiple maps/views to see test results – – – Signal Strength Data Rate Interference S/N Ratio A/P Coverage • Difficult to tell if particular areas are meeting all the required criteria • Limited or no simulation capabilities leads to significant time spent in “trial and error” mode – Hard to figure out what the right thing is to do in order to fix problem areas Signal Strength Map (Often called a “heat map”) Can you tell where the network will or will not support the customer’s requirements? 69
Results from typical site survey tools • Have to visually examine multiple maps/views to see test results – – – Signal Strength Data Rate Interference S/N Ratio A/P Coverage • Difficult to tell if particular areas are meeting all the required criteria • Limited or no simulation capabilities leads to significant time spent in “trial and error” mode – Hard to figure out what the right thing is to do in order to fix problem areas Signal Strength Map (Often called a “heat map”) Can you tell where the network will or will not support the customer’s requirements? 69
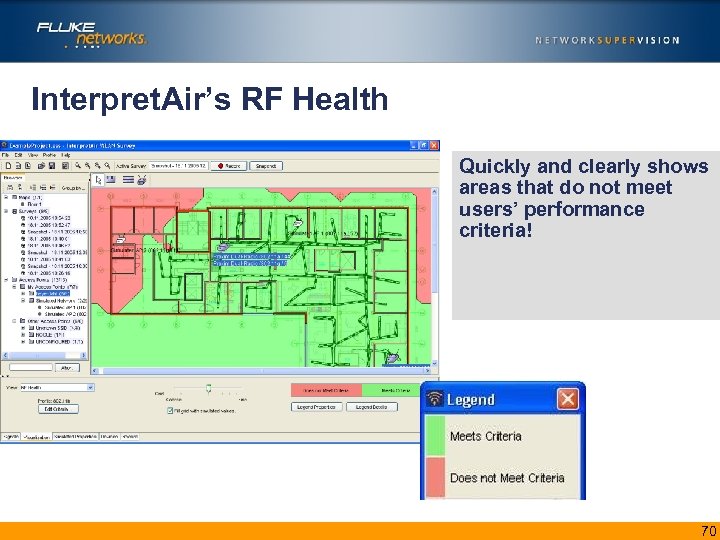 Interpret. Air’s RF Health Quickly and clearly shows areas that do not meet users’ performance criteria! 70
Interpret. Air’s RF Health Quickly and clearly shows areas that do not meet users’ performance criteria! 70
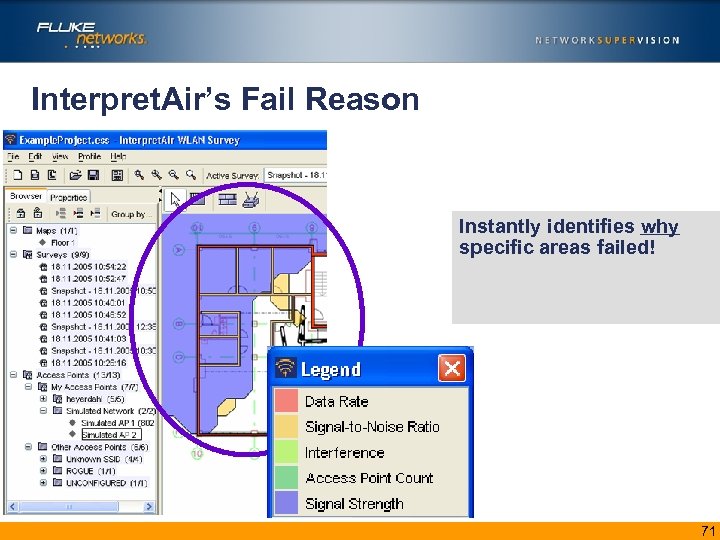 Interpret. Air’s Fail Reason Instantly identifies why specific areas failed! 71
Interpret. Air’s Fail Reason Instantly identifies why specific areas failed! 71
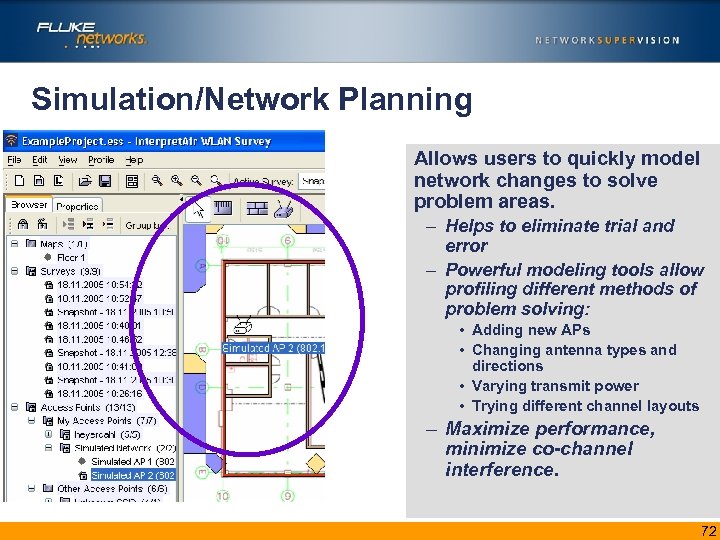 Simulation/Network Planning Allows users to quickly model network changes to solve problem areas. – Helps to eliminate trial and error – Powerful modeling tools allow profiling different methods of problem solving: • Adding new APs • Changing antenna types and directions • Varying transmit power • Trying different channel layouts – Maximize performance, minimize co-channel interference. 72
Simulation/Network Planning Allows users to quickly model network changes to solve problem areas. – Helps to eliminate trial and error – Powerful modeling tools allow profiling different methods of problem solving: • Adding new APs • Changing antenna types and directions • Varying transmit power • Trying different channel layouts – Maximize performance, minimize co-channel interference. 72
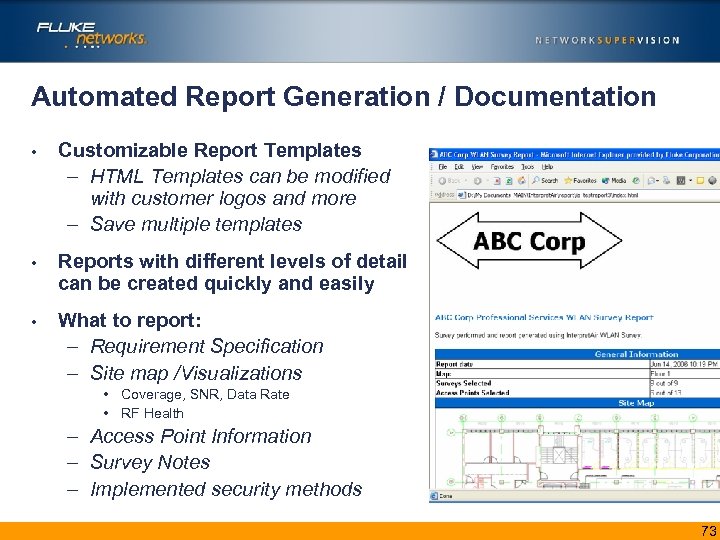 Automated Report Generation / Documentation • Customizable Report Templates – HTML Templates can be modified with customer logos and more – Save multiple templates • Reports with different levels of detail can be created quickly and easily • What to report: – Requirement Specification – Site map /Visualizations • Coverage, SNR, Data Rate • RF Health – Access Point Information – Survey Notes – Implemented security methods 73
Automated Report Generation / Documentation • Customizable Report Templates – HTML Templates can be modified with customer logos and more – Save multiple templates • Reports with different levels of detail can be created quickly and easily • What to report: – Requirement Specification – Site map /Visualizations • Coverage, SNR, Data Rate • RF Health – Access Point Information – Survey Notes – Implemented security methods 73
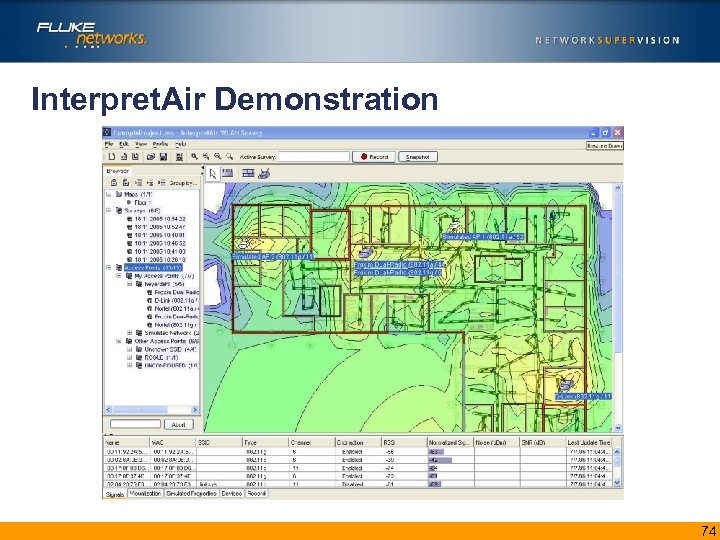 Interpret. Air Demonstration 74
Interpret. Air Demonstration 74
 System Requirements • Opti. View™ Series II Integrated Network Analyzer or Laptop/tablet computer with Pentium® III series processor • Operating System: Windows XP or 2000 Professional • Memory: 512 MB RAM • Disk space: 500 MB hard drive space available • Network Interface: One supported wireless LAN Network Interface Card 75
System Requirements • Opti. View™ Series II Integrated Network Analyzer or Laptop/tablet computer with Pentium® III series processor • Operating System: Windows XP or 2000 Professional • Memory: 512 MB RAM • Disk space: 500 MB hard drive space available • Network Interface: One supported wireless LAN Network Interface Card 75
 Wireless- Troubleshooting with FLUKE Networks Ether. Scope™ Network Assistant ECA 100305
Wireless- Troubleshooting with FLUKE Networks Ether. Scope™ Network Assistant ECA 100305
 Network managers challenged • Network managers are tasked with – Supporting these new users, new networks, new technologies and new applications – All while still delivering the network reliability and security users and business managers demand • It’s a difficult and challenging task – keeping control of a wireless network that by design is constantly changing • This is where Fluke Networks can help – Ether. Scope Series II Wireless Network Assistant 77
Network managers challenged • Network managers are tasked with – Supporting these new users, new networks, new technologies and new applications – All while still delivering the network reliability and security users and business managers demand • It’s a difficult and challenging task – keeping control of a wireless network that by design is constantly changing • This is where Fluke Networks can help – Ether. Scope Series II Wireless Network Assistant 77
 Troubleshooting wireless networks • There a lot of wires in a wireless network – from access point to switch to server to router • The Ether. Scope Network Assistant analyzes both – Gigabit wired networks – 802. 11 a/b/g wireless networks • Identify problems on both sides of the access point – WLAN-only solutions don’t deliver the whole picture that network professionals need for robust troubleshooting • Ether. Scope discovers active networks, mobile clients and access points • Drill down into devices to see configuration details • Troubleshoot WLAN connectivity, authentication and performance issues • All this in small, light-weight rugged package that goes where notebook PCs shouldn’t 78
Troubleshooting wireless networks • There a lot of wires in a wireless network – from access point to switch to server to router • The Ether. Scope Network Assistant analyzes both – Gigabit wired networks – 802. 11 a/b/g wireless networks • Identify problems on both sides of the access point – WLAN-only solutions don’t deliver the whole picture that network professionals need for robust troubleshooting • Ether. Scope discovers active networks, mobile clients and access points • Drill down into devices to see configuration details • Troubleshoot WLAN connectivity, authentication and performance issues • All this in small, light-weight rugged package that goes where notebook PCs shouldn’t 78
 Troubleshooting WLAN security concerns • Ether. Scope Network Assistant helps address wireless security vulnerabilities • Walk the site to detect and identify – Unauthorized rogue devices – Unprotected access points – “Locate” feature pinpoints these devices • Periodically survey the network for changes that could indicate a security breach 79
Troubleshooting WLAN security concerns • Ether. Scope Network Assistant helps address wireless security vulnerabilities • Walk the site to detect and identify – Unauthorized rogue devices – Unprotected access points – “Locate” feature pinpoints these devices • Periodically survey the network for changes that could indicate a security breach 79
 WLAN Maintenance • The Ether. Scope goes where notebook PCs shouldn’t – form factor appropriate for taking with you to the equipment room, closet, warehouse, under the desk • Rugged and portable – Easy to use – Include the necessary utilities for network and device management • Web browser • Telnet • Terminal emulator 80
WLAN Maintenance • The Ether. Scope goes where notebook PCs shouldn’t – form factor appropriate for taking with you to the equipment room, closet, warehouse, under the desk • Rugged and portable – Easy to use – Include the necessary utilities for network and device management • Web browser • Telnet • Terminal emulator 80
 Gigabit LAN troubleshooting • Gb. E is moving to the desktop – Ether. Scope tests 10, 100 and 1000 Mbps Ethernet • Switches are deployed deeper into the network – Ether. Scope’s switch diagnostics provide visibility into switched networks for quicker, more complete problem resolution • More equipment types are being networked (PCs, printers, copiers, terminals, security systems, vending) – Ether. Scope discovers networks, VLANs, and 1000+ devices automatically and provides detail device information – Reporting capability for documentation of the LAN • Cabling is still a source of problems – Ether. Scope tests UTP/STP and fiber optic cabling and includes toning to help locate cables 81
Gigabit LAN troubleshooting • Gb. E is moving to the desktop – Ether. Scope tests 10, 100 and 1000 Mbps Ethernet • Switches are deployed deeper into the network – Ether. Scope’s switch diagnostics provide visibility into switched networks for quicker, more complete problem resolution • More equipment types are being networked (PCs, printers, copiers, terminals, security systems, vending) – Ether. Scope discovers networks, VLANs, and 1000+ devices automatically and provides detail device information – Reporting capability for documentation of the LAN • Cabling is still a source of problems – Ether. Scope tests UTP/STP and fiber optic cabling and includes toning to help locate cables 81
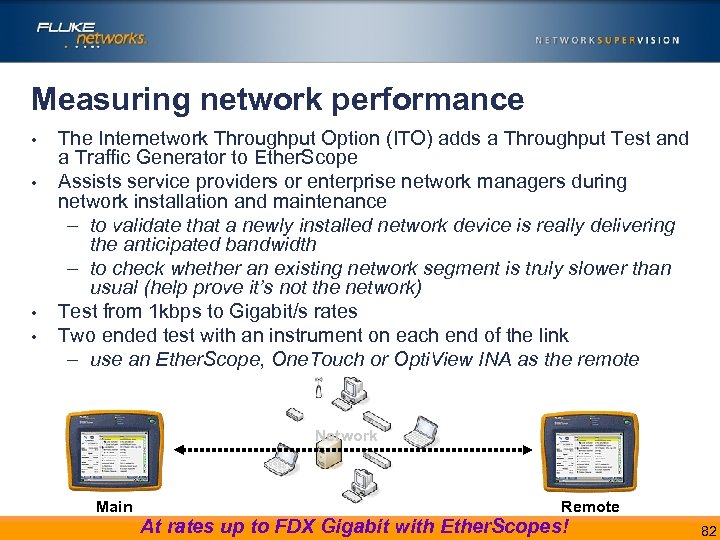 Measuring network performance • • The Internetwork Throughput Option (ITO) adds a Throughput Test and a Traffic Generator to Ether. Scope Assists service providers or enterprise network managers during network installation and maintenance – to validate that a newly installed network device is really delivering the anticipated bandwidth – to check whether an existing network segment is truly slower than usual (help prove it’s not the network) Test from 1 kbps to Gigabit/s rates Two ended test with an instrument on each end of the link – use an Ether. Scope, One. Touch or Opti. View INA as the remote Network Main Remote At rates up to FDX Gigabit with Ether. Scopes! 82
Measuring network performance • • The Internetwork Throughput Option (ITO) adds a Throughput Test and a Traffic Generator to Ether. Scope Assists service providers or enterprise network managers during network installation and maintenance – to validate that a newly installed network device is really delivering the anticipated bandwidth – to check whether an existing network segment is truly slower than usual (help prove it’s not the network) Test from 1 kbps to Gigabit/s rates Two ended test with an instrument on each end of the link – use an Ether. Scope, One. Touch or Opti. View INA as the remote Network Main Remote At rates up to FDX Gigabit with Ether. Scopes! 82
 What problems does the new Ether. Scope solve?
What problems does the new Ether. Scope solve?
 What are the problems with wireless networks • Don’t know what network types are active – feature: Network Discovery • • • Don’t know who is using the WLAN Need to verify device configurations Can’t connect or login Not getting the expected performance (“too slow”) Security concerns (e. g. rogue clients) WLAN isn’t documented 84
What are the problems with wireless networks • Don’t know what network types are active – feature: Network Discovery • • • Don’t know who is using the WLAN Need to verify device configurations Can’t connect or login Not getting the expected performance (“too slow”) Security concerns (e. g. rogue clients) WLAN isn’t documented 84
 Discovering the types of wireless networks • Click “Network Discovery” • Four network types are discovered – an infrastructure network is comprised of systems and mobile clients connected through an Access Point (AP) which is connected to wired Ethernet network. Most common type. – an adhoc network is comprised of mobile clients transmitting directly to any other; No AP needed – a bridge network is comprised of two APs or dedicated 802. 11 bridges that communicate to provide link between two physically separate networks – a IP subnet is comprised of WLAN devices for which IP addresses have been discovered including Ether. Scopes 85
Discovering the types of wireless networks • Click “Network Discovery” • Four network types are discovered – an infrastructure network is comprised of systems and mobile clients connected through an Access Point (AP) which is connected to wired Ethernet network. Most common type. – an adhoc network is comprised of mobile clients transmitting directly to any other; No AP needed – a bridge network is comprised of two APs or dedicated 802. 11 bridges that communicate to provide link between two physically separate networks – a IP subnet is comprised of WLAN devices for which IP addresses have been discovered including Ether. Scopes 85
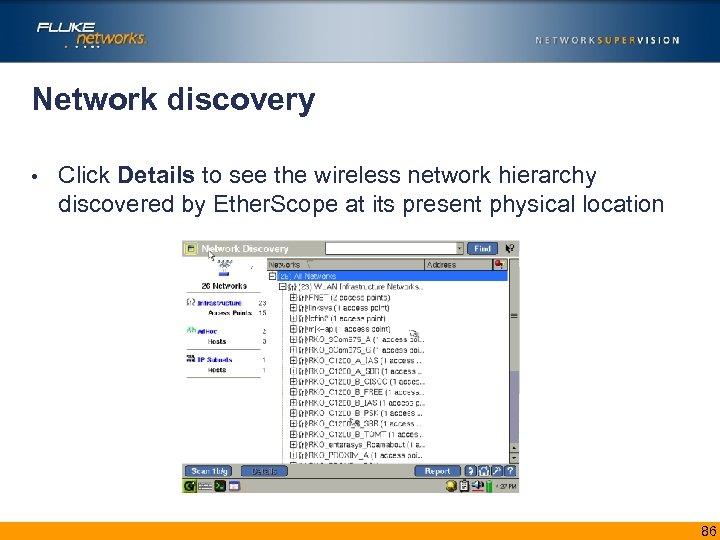 Network discovery • Click Details to see the wireless network hierarchy discovered by Ether. Scope at its present physical location insert screen shot of Network Discovery details 86
Network discovery • Click Details to see the wireless network hierarchy discovered by Ether. Scope at its present physical location insert screen shot of Network Discovery details 86
 What are the problems with wireless networks • Don’t know what network types are active – feature: Network Discovery • Don’t know who is using the WLAN – feature: Device Discovery • • • Need to verify device configurations Can’t connect or login Not getting the expected performance (“too slow”) Security concerns (e. g. rogue clients) WLAN isn’t documented 87
What are the problems with wireless networks • Don’t know what network types are active – feature: Network Discovery • Don’t know who is using the WLAN – feature: Device Discovery • • • Need to verify device configurations Can’t connect or login Not getting the expected performance (“too slow”) Security concerns (e. g. rogue clients) WLAN isn’t documented 87
 Discovering who is using the network • Click “Device Discovery” then “Details” – see the number of devices on the network by type – an access point is the “connecting” point used to coordinate wireless traffic and provide connectivity to the LAN. – a bridge node is a device that provide a wireless connection between wired networks. This feature can be built into Access Points. – a mobile client is an end point or node on the wireless network. These are typically general purpose computers but might also include other dedicated wireless devices. – an adhoc client is a node that comprises a peer-to-peer network that requires no access point. – a host is a special category that only includes This Ether. Scope. 88
Discovering who is using the network • Click “Device Discovery” then “Details” – see the number of devices on the network by type – an access point is the “connecting” point used to coordinate wireless traffic and provide connectivity to the LAN. – a bridge node is a device that provide a wireless connection between wired networks. This feature can be built into Access Points. – a mobile client is an end point or node on the wireless network. These are typically general purpose computers but might also include other dedicated wireless devices. – an adhoc client is a node that comprises a peer-to-peer network that requires no access point. – a host is a special category that only includes This Ether. Scope. 88
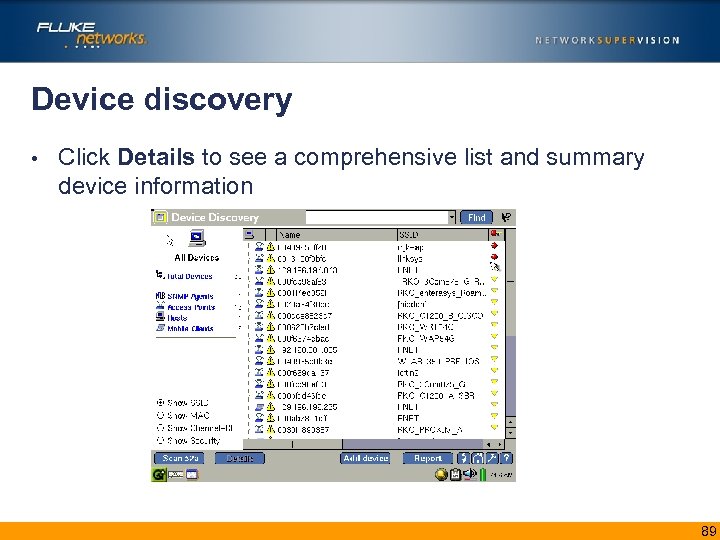 Device discovery • Click Details to see a comprehensive list and summary device information insert screen shot of Device Discovery details 89
Device discovery • Click Details to see a comprehensive list and summary device information insert screen shot of Device Discovery details 89
 What are the problems with wireless networks • Don’t know what network types are active – feature: Network Discovery • Don’t know who is using the WLAN – feature: Device Discovery • Need to verify device configurations – feature: Device Discovery Details Not getting the expected performance (“too slow”) • Security concerns (e. g. rogue clients) • Can’t connect or login • WLAN isn’t documented • 90
What are the problems with wireless networks • Don’t know what network types are active – feature: Network Discovery • Don’t know who is using the WLAN – feature: Device Discovery • Need to verify device configurations – feature: Device Discovery Details Not getting the expected performance (“too slow”) • Security concerns (e. g. rogue clients) • Can’t connect or login • WLAN isn’t documented • 90
 Configuration information presented • SSID is Service Set ID. Typically, the wireless network comprised of an AP and wireless stations is given an SSID name. This uniquely identifies a WLAN and is used when configuring security options. • MAC is a medium access control address. 802. 11 devices have unique MAC addresses that are used to identify devices. • Channel is a common frequency used to direct communication between an 802. 11 radio card an access point. • Signal is the transmission of 802. 11 frames by radiating RF energy at a given strength. The stronger the signal the better the coverage and connection. • Noise is unwanted, interfering RF energy that disrupt normal system operations. Noise level impacts connectivity and performance. • Security represents the level of 802. 11 packet encryption and network authentication for which a device is configured. 91
Configuration information presented • SSID is Service Set ID. Typically, the wireless network comprised of an AP and wireless stations is given an SSID name. This uniquely identifies a WLAN and is used when configuring security options. • MAC is a medium access control address. 802. 11 devices have unique MAC addresses that are used to identify devices. • Channel is a common frequency used to direct communication between an 802. 11 radio card an access point. • Signal is the transmission of 802. 11 frames by radiating RF energy at a given strength. The stronger the signal the better the coverage and connection. • Noise is unwanted, interfering RF energy that disrupt normal system operations. Noise level impacts connectivity and performance. • Security represents the level of 802. 11 packet encryption and network authentication for which a device is configured. 91
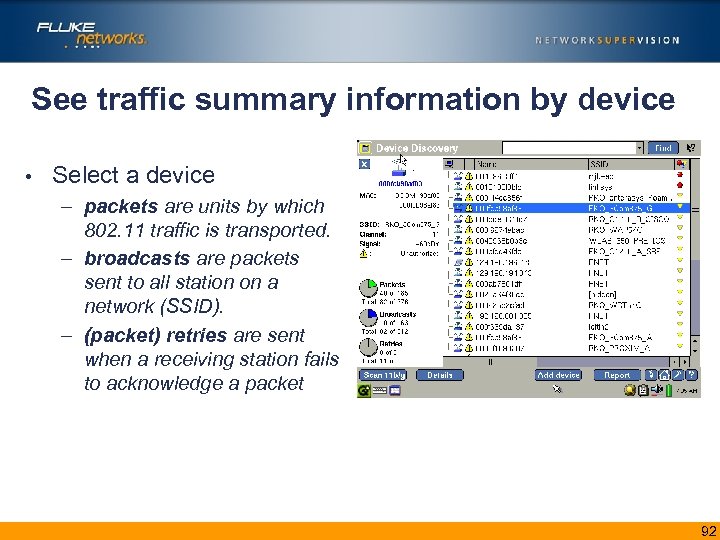 See traffic summary information by device • Select a device – packets are units by which 802. 11 traffic is transported. – broadcasts are packets sent to all station on a network (SSID). – (packet) retries are sent when a receiving station fails to acknowledge a packet 92
See traffic summary information by device • Select a device – packets are units by which 802. 11 traffic is transported. – broadcasts are packets sent to all station on a network (SSID). – (packet) retries are sent when a receiving station fails to acknowledge a packet 92
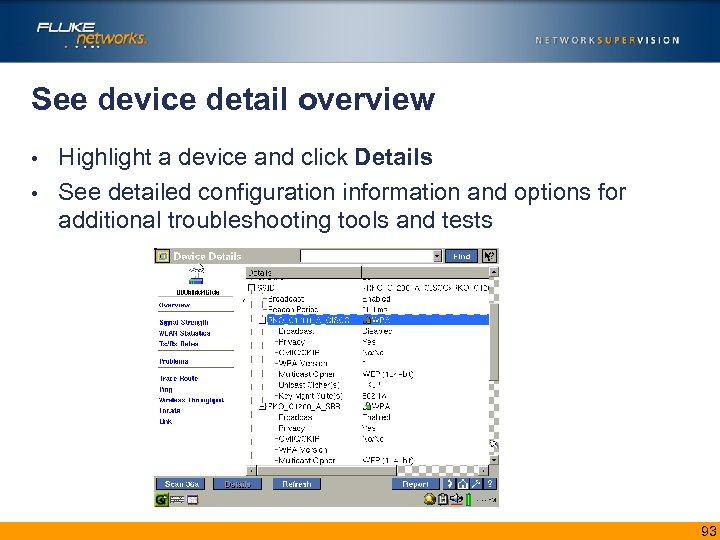 See device detail overview Highlight a device and click Details • See detailed configuration information and options for additional troubleshooting tools and tests • 93
See device detail overview Highlight a device and click Details • See detailed configuration information and options for additional troubleshooting tools and tests • 93
 What are the problems with wireless networks • • Don’t know what network types are active – feature: Network Discovery Don’t know who is using the WLAN – feature: Device Discovery Need to verify device configurations – feature: Device Discovery Details Not getting the expected performance (“too slow”) – feature: Channel statistics Security concerns (e. g. rogue clients) Can’t connect or login WLAN isn’t documented 94
What are the problems with wireless networks • • Don’t know what network types are active – feature: Network Discovery Don’t know who is using the WLAN – feature: Device Discovery Need to verify device configurations – feature: Device Discovery Details Not getting the expected performance (“too slow”) – feature: Channel statistics Security concerns (e. g. rogue clients) Can’t connect or login WLAN isn’t documented 94
 Troubleshooting wireless LAN performance and connectivity issues • A common measure of wireless network performance is speed, typically expressed in Mbps • Speed is impacted by the transmission technology and local RF conditions 95
Troubleshooting wireless LAN performance and connectivity issues • A common measure of wireless network performance is speed, typically expressed in Mbps • Speed is impacted by the transmission technology and local RF conditions 95
 Analyze performance and connectivity issues by examining channel statistics • A channel is defined as the common frequency that is used to direct communication between an 802. 11 radio card an access point. – 802. 11 b/g • 14 channels; 11 in US • Channels 1, 6, and 11 non-overlapping • Uses 22 MHz wide channels – 802. 11 a • 12 channels • Uses 20 MHz wide channels • NO overlapping channels 96
Analyze performance and connectivity issues by examining channel statistics • A channel is defined as the common frequency that is used to direct communication between an 802. 11 radio card an access point. – 802. 11 b/g • 14 channels; 11 in US • Channels 1, 6, and 11 non-overlapping • Uses 22 MHz wide channels – 802. 11 a • 12 channels • Uses 20 MHz wide channels • NO overlapping channels 96
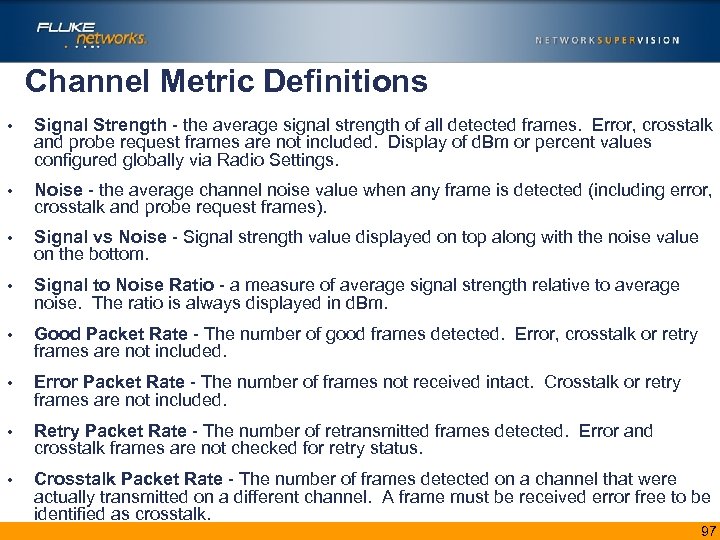 Channel Metric Definitions • Signal Strength - the average signal strength of all detected frames. Error, crosstalk and probe request frames are not included. Display of d. Bm or percent values configured globally via Radio Settings. • Noise - the average channel noise value when any frame is detected (including error, crosstalk and probe request frames). • Signal vs Noise - Signal strength value displayed on top along with the noise value on the bottom. • Signal to Noise Ratio - a measure of average signal strength relative to average noise. The ratio is always displayed in d. Bm. • Good Packet Rate - The number of good frames detected. Error, crosstalk or retry frames are not included. • Error Packet Rate - The number of frames not received intact. Crosstalk or retry frames are not included. • Retry Packet Rate - The number of retransmitted frames detected. Error and crosstalk frames are not checked for retry status. • Crosstalk Packet Rate - The number of frames detected on a channel that were actually transmitted on a different channel. A frame must be received error free to be identified as crosstalk. 97
Channel Metric Definitions • Signal Strength - the average signal strength of all detected frames. Error, crosstalk and probe request frames are not included. Display of d. Bm or percent values configured globally via Radio Settings. • Noise - the average channel noise value when any frame is detected (including error, crosstalk and probe request frames). • Signal vs Noise - Signal strength value displayed on top along with the noise value on the bottom. • Signal to Noise Ratio - a measure of average signal strength relative to average noise. The ratio is always displayed in d. Bm. • Good Packet Rate - The number of good frames detected. Error, crosstalk or retry frames are not included. • Error Packet Rate - The number of frames not received intact. Crosstalk or retry frames are not included. • Retry Packet Rate - The number of retransmitted frames detected. Error and crosstalk frames are not checked for retry status. • Crosstalk Packet Rate - The number of frames detected on a channel that were actually transmitted on a different channel. A frame must be received error free to be identified as crosstalk. 97
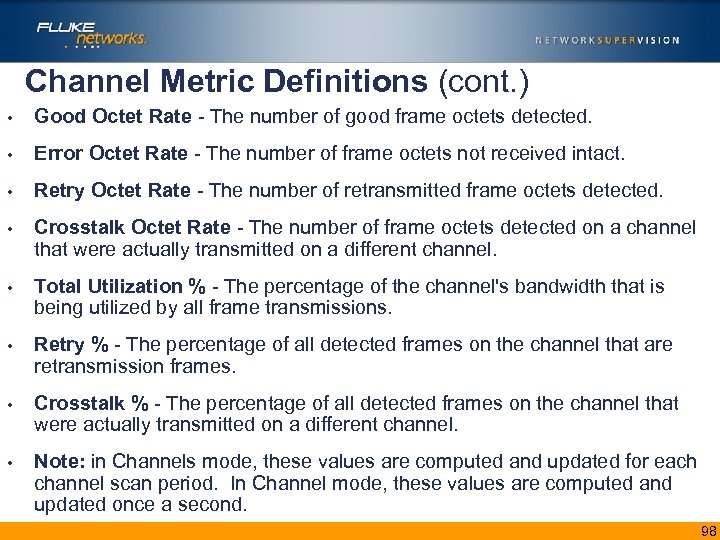 Channel Metric Definitions (cont. ) • Good Octet Rate - The number of good frame octets detected. • Error Octet Rate - The number of frame octets not received intact. • Retry Octet Rate - The number of retransmitted frame octets detected. • Crosstalk Octet Rate - The number of frame octets detected on a channel that were actually transmitted on a different channel. • Total Utilization % - The percentage of the channel's bandwidth that is being utilized by all frame transmissions. • Retry % - The percentage of all detected frames on the channel that are retransmission frames. • Crosstalk % - The percentage of all detected frames on the channel that were actually transmitted on a different channel. • Note: in Channels mode, these values are computed and updated for each channel scan period. In Channel mode, these values are computed and updated once a second. 98
Channel Metric Definitions (cont. ) • Good Octet Rate - The number of good frame octets detected. • Error Octet Rate - The number of frame octets not received intact. • Retry Octet Rate - The number of retransmitted frame octets detected. • Crosstalk Octet Rate - The number of frame octets detected on a channel that were actually transmitted on a different channel. • Total Utilization % - The percentage of the channel's bandwidth that is being utilized by all frame transmissions. • Retry % - The percentage of all detected frames on the channel that are retransmission frames. • Crosstalk % - The percentage of all detected frames on the channel that were actually transmitted on a different channel. • Note: in Channels mode, these values are computed and updated for each channel scan period. In Channel mode, these values are computed and updated once a second. 98
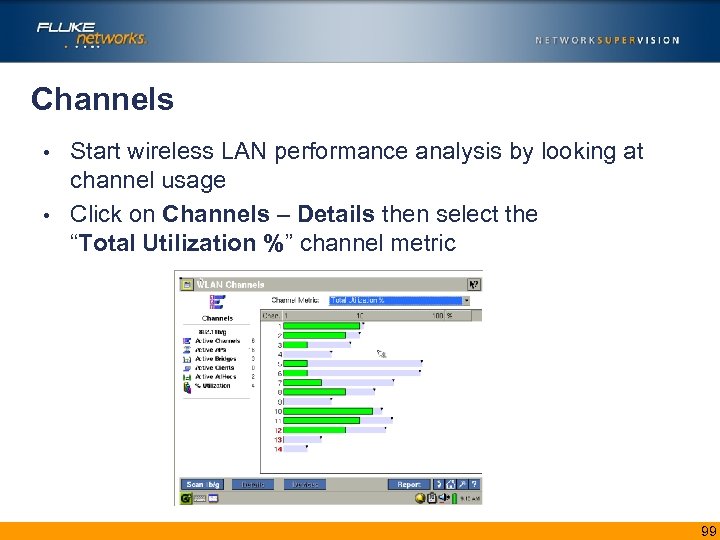 Channels Start wireless LAN performance analysis by looking at channel usage • Click on Channels – Details then select the “Total Utilization %” channel metric • 99
Channels Start wireless LAN performance analysis by looking at channel usage • Click on Channels – Details then select the “Total Utilization %” channel metric • 99
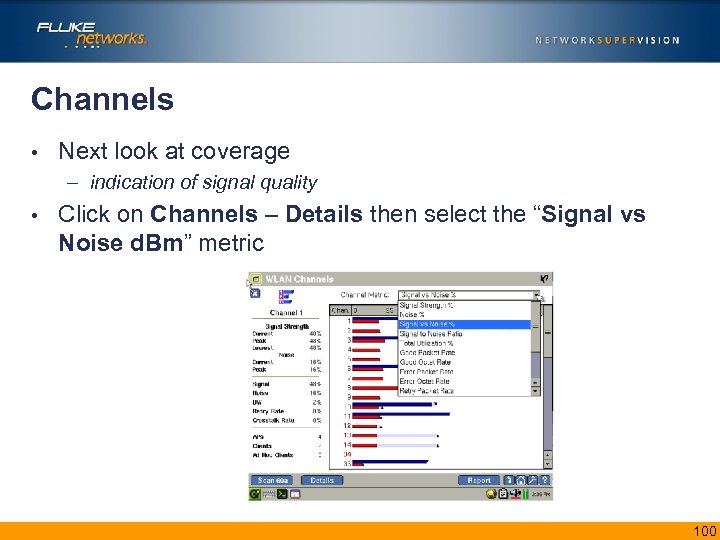 Channels • Next look at coverage – indication of signal quality • Click on Channels – Details then select the “Signal vs Noise d. Bm” metric 100
Channels • Next look at coverage – indication of signal quality • Click on Channels – Details then select the “Signal vs Noise d. Bm” metric 100
 Noise • Non 802. 11 energy (non-compliant signal strength) • Get noise readings from radio card • Indicates noise floor level • Used to evaluate channel quality – Signal-to-Noise ratio • Noise level impacts connectivity and performance • Shows distribution of noise across channels • • Channel Quality represented by signal-to-noise ratio (rule of thumb? ) 101
Noise • Non 802. 11 energy (non-compliant signal strength) • Get noise readings from radio card • Indicates noise floor level • Used to evaluate channel quality – Signal-to-Noise ratio • Noise level impacts connectivity and performance • Shows distribution of noise across channels • • Channel Quality represented by signal-to-noise ratio (rule of thumb? ) 101
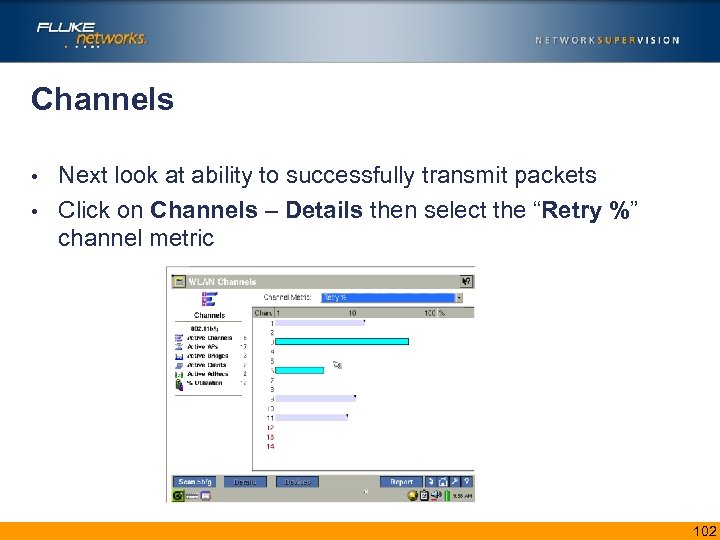 Channels Next look at ability to successfully transmit packets • Click on Channels – Details then select the “Retry %” channel metric • 102
Channels Next look at ability to successfully transmit packets • Click on Channels – Details then select the “Retry %” channel metric • 102
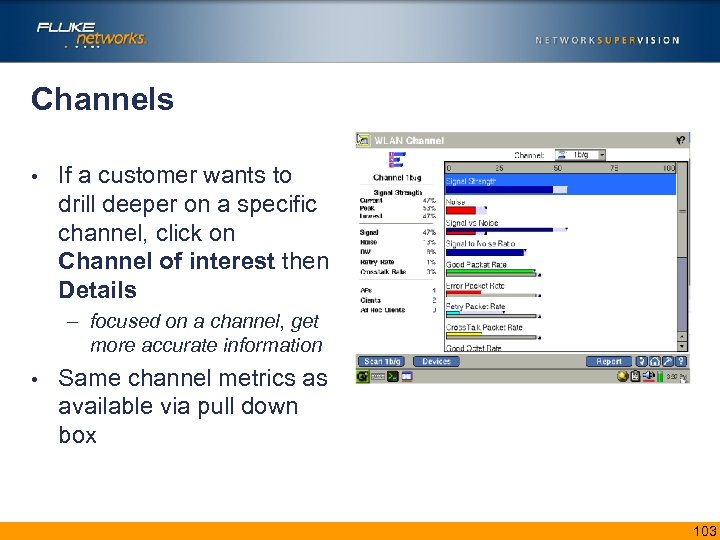 Channels • If a customer wants to drill deeper on a specific channel, click on Channel of interest then Details – focused on a channel, get more accurate information • Same channel metrics as available via pull down box 103
Channels • If a customer wants to drill deeper on a specific channel, click on Channel of interest then Details – focused on a channel, get more accurate information • Same channel metrics as available via pull down box 103
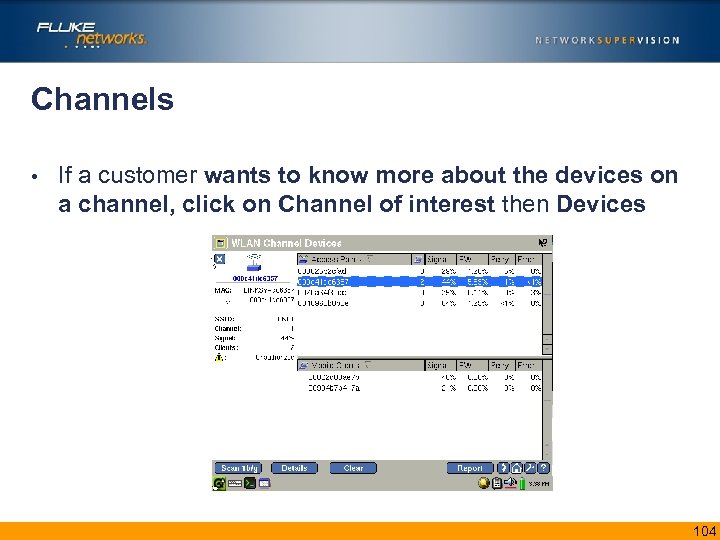 Channels • If a customer wants to know more about the devices on a channel, click on Channel of interest then Devices 104
Channels • If a customer wants to know more about the devices on a channel, click on Channel of interest then Devices 104
 Analyze wireless network health by examining channel utilization • A channel utilization measures the % of bandwidth consumed by packets transmitted by wireless devices (Access Points, mobile clients, etc. ) on a single frequency 105
Analyze wireless network health by examining channel utilization • A channel utilization measures the % of bandwidth consumed by packets transmitted by wireless devices (Access Points, mobile clients, etc. ) on a single frequency 105
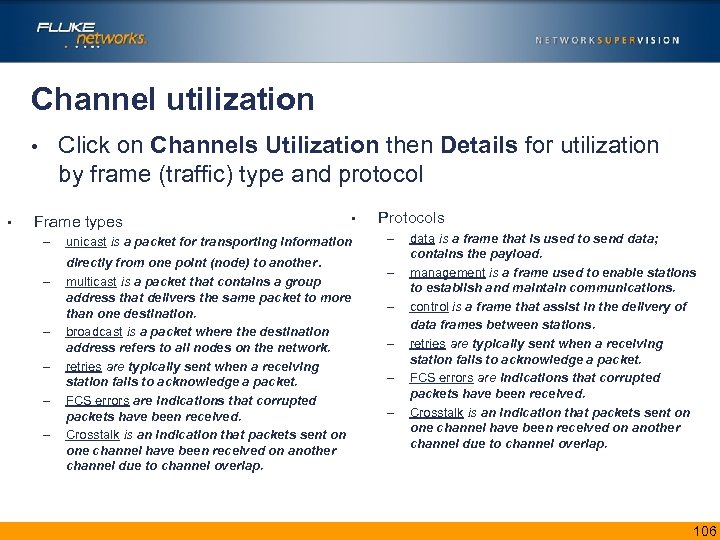 Channel utilization Click on Channels Utilization then Details for utilization by frame (traffic) type and protocol • • Frame types – • unicast is a packet for transporting information directly from one point (node) to another. – – – multicast is a packet that contains a group address that delivers the same packet to more than one destination. broadcast is a packet where the destination address refers to all nodes on the network. retries are typically sent when a receiving station fails to acknowledge a packet. FCS errors are indications that corrupted packets have been received. Crosstalk is an indication that packets sent on one channel have been received on another channel due to channel overlap. Protocols – – – data is a frame that is used to send data; contains the payload. management is a frame used to enable stations to establish and maintain communications. control is a frame that assist in the delivery of data frames between stations. retries are typically sent when a receiving station fails to acknowledge a packet. FCS errors are indications that corrupted packets have been received. Crosstalk is an indication that packets sent on one channel have been received on another channel due to channel overlap. 106
Channel utilization Click on Channels Utilization then Details for utilization by frame (traffic) type and protocol • • Frame types – • unicast is a packet for transporting information directly from one point (node) to another. – – – multicast is a packet that contains a group address that delivers the same packet to more than one destination. broadcast is a packet where the destination address refers to all nodes on the network. retries are typically sent when a receiving station fails to acknowledge a packet. FCS errors are indications that corrupted packets have been received. Crosstalk is an indication that packets sent on one channel have been received on another channel due to channel overlap. Protocols – – – data is a frame that is used to send data; contains the payload. management is a frame used to enable stations to establish and maintain communications. control is a frame that assist in the delivery of data frames between stations. retries are typically sent when a receiving station fails to acknowledge a packet. FCS errors are indications that corrupted packets have been received. Crosstalk is an indication that packets sent on one channel have been received on another channel due to channel overlap. 106
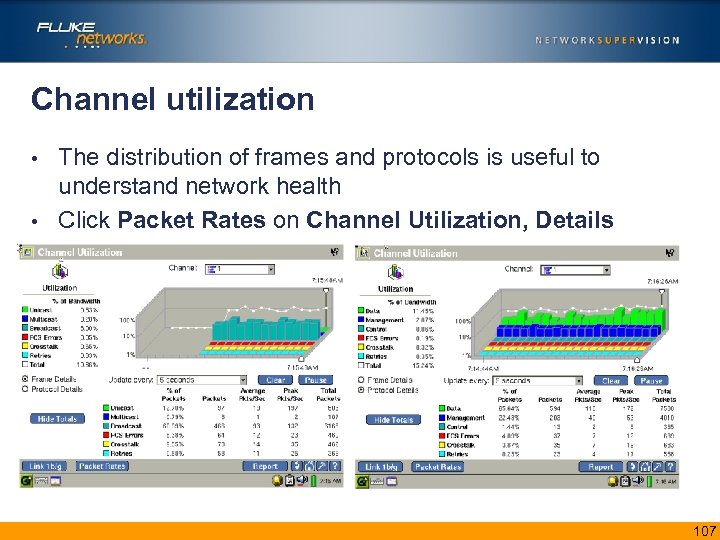 Channel utilization The distribution of frames and protocols is useful to understand network health • Click Packet Rates on Channel Utilization, Details • 107
Channel utilization The distribution of frames and protocols is useful to understand network health • Click Packet Rates on Channel Utilization, Details • 107
 What are the problems with wireless networks • • Don’t know what network types are active – feature: Network Discovery Don’t know who is using the WLAN – feature: Device Discovery Need to verify device configurations – feature: Device Discovery Details Not getting the expected performance (“too slow”) – feature: Channel statistics Security concerns (e. g. rogue clients) – feature: Security Scan Can’t connect or login WLAN isn’t documented 108
What are the problems with wireless networks • • Don’t know what network types are active – feature: Network Discovery Don’t know who is using the WLAN – feature: Device Discovery Need to verify device configurations – feature: Device Discovery Details Not getting the expected performance (“too slow”) – feature: Channel statistics Security concerns (e. g. rogue clients) – feature: Security Scan Can’t connect or login WLAN isn’t documented 108
 Identifying security vulnerabilities • Security threats are identified two ways – unprotected devices are not using encryption to manage connections • unprotected devices can be a path into your network – unauthorized devices are not approved by the IT manager to be on the network • Ether. Scope assumes all devices are unauthorized until made otherwise 109
Identifying security vulnerabilities • Security threats are identified two ways – unprotected devices are not using encryption to manage connections • unprotected devices can be a path into your network – unauthorized devices are not approved by the IT manager to be on the network • Ether. Scope assumes all devices are unauthorized until made otherwise 109
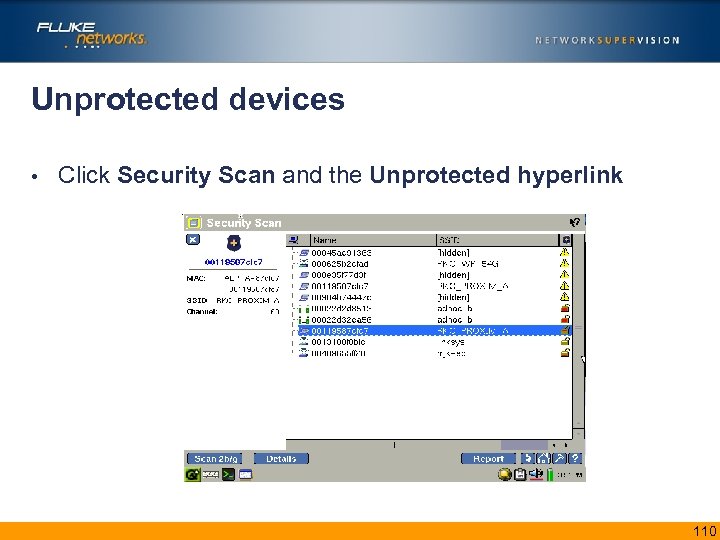 Unprotected devices • Click Security Scan and the Unprotected hyperlink 110
Unprotected devices • Click Security Scan and the Unprotected hyperlink 110
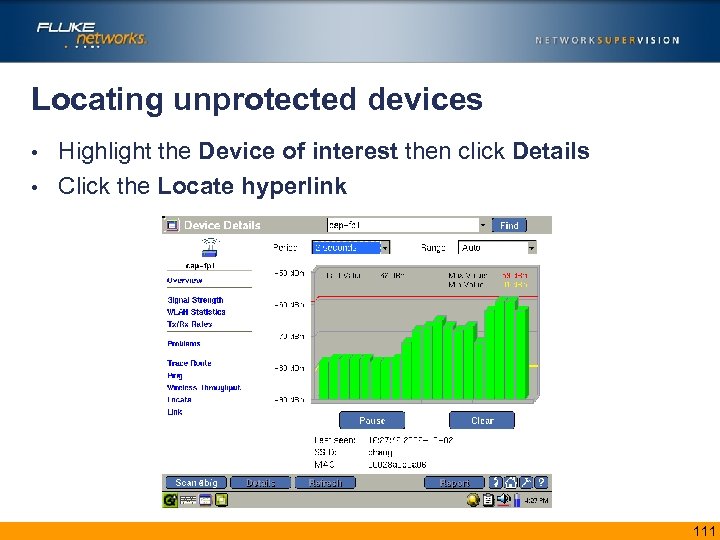 Locating unprotected devices Highlight the Device of interest then click Details • Click the Locate hyperlink • 111
Locating unprotected devices Highlight the Device of interest then click Details • Click the Locate hyperlink • 111
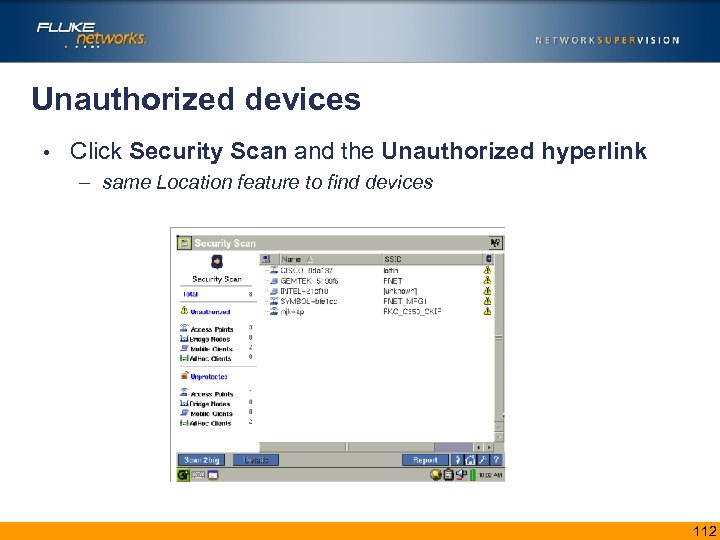 Unauthorized devices • Click Security Scan and the Unauthorized hyperlink – same Location feature to find devices insert screen shot of security scan unauthorized devices 112
Unauthorized devices • Click Security Scan and the Unauthorized hyperlink – same Location feature to find devices insert screen shot of security scan unauthorized devices 112
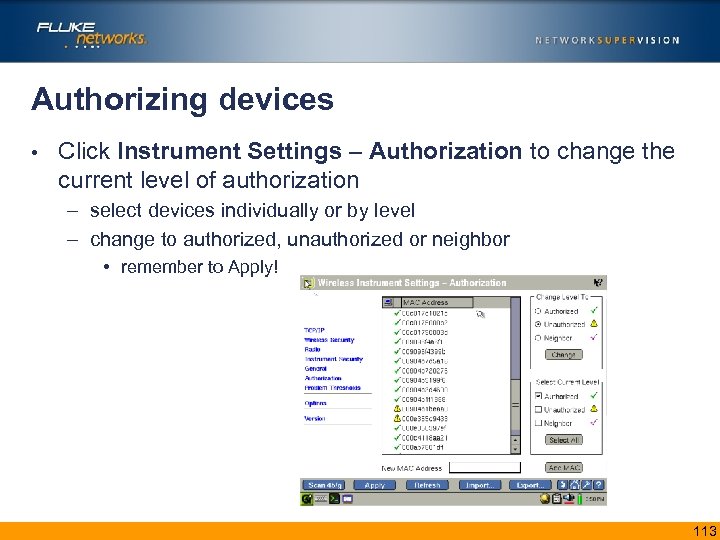 Authorizing devices • Click Instrument Settings – Authorization to change the current level of authorization – select devices individually or by level – change to authorized, unauthorized or neighbor • remember to Apply! 113
Authorizing devices • Click Instrument Settings – Authorization to change the current level of authorization – select devices individually or by level – change to authorized, unauthorized or neighbor • remember to Apply! 113
 What are the problems with wireless networks • • Don’t know what network types are active – feature: Network Discovery Don’t know who is using the WLAN – feature: Device Discovery Need to verify device configurations – feature: Device Discovery Details Not getting the expected performance (“too slow”) – feature: Channel statistics Security concerns (e. g. rogue clients) – feature: Security Scan Can’t connect or login – feature: Login Diagnosis WLAN isn’t documented 114
What are the problems with wireless networks • • Don’t know what network types are active – feature: Network Discovery Don’t know who is using the WLAN – feature: Device Discovery Need to verify device configurations – feature: Device Discovery Details Not getting the expected performance (“too slow”) – feature: Channel statistics Security concerns (e. g. rogue clients) – feature: Security Scan Can’t connect or login – feature: Login Diagnosis WLAN isn’t documented 114
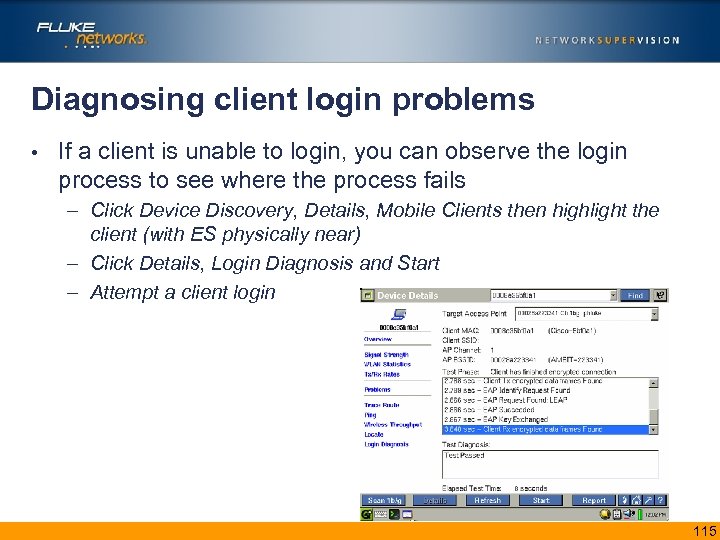 Diagnosing client login problems • If a client is unable to login, you can observe the login process to see where the process fails – Click Device Discovery, Details, Mobile Clients then highlight the client (with ES physically near) – Click Details, Login Diagnosis and Start – Attempt a client login Insert screen shot and emphasize key points 115
Diagnosing client login problems • If a client is unable to login, you can observe the login process to see where the process fails – Click Device Discovery, Details, Mobile Clients then highlight the client (with ES physically near) – Click Details, Login Diagnosis and Start – Attempt a client login Insert screen shot and emphasize key points 115
 What are the problems with wireless networks • • Don’t know what network types are active – feature: Network Discovery Don’t know who is using the WLAN – feature: Device Discovery Need to verify device configurations – feature: Device Discovery Details Not getting the expected performance (“too slow”) – feature: Channel statistics Security concerns (e. g. rogue clients) – feature: Security Scan Can’t connect or login – feature: Login Diagnosis WLAN isn’t documented – feature: Reports 116
What are the problems with wireless networks • • Don’t know what network types are active – feature: Network Discovery Don’t know who is using the WLAN – feature: Device Discovery Need to verify device configurations – feature: Device Discovery Details Not getting the expected performance (“too slow”) – feature: Channel statistics Security concerns (e. g. rogue clients) – feature: Security Scan Can’t connect or login – feature: Login Diagnosis WLAN isn’t documented – feature: Reports 116
 Documenting the wireless LAN • Save Reports to document WLAN attributes • New Applications make more easier report viewing and management – Report Viewer and File Manager 117
Documenting the wireless LAN • Save Reports to document WLAN attributes • New Applications make more easier report viewing and management – Report Viewer and File Manager 117
 Ether. Scope, Interpret. Air and Analyze. Air allow you to management the entire wireless lifecycle • Ether. Scope Series II Network Assistant – Helping first responders solve network problems fast – Integrated troubleshooting capabilities for 802. 11 a/b/g networks – Wireless analysis assists with today’s hot issues: security, performance and connectivity problems • Interpret. Air Wireless Site Survey Software – Easily and graphically survey 802. 11 a/b/g wireless networks – Visualize RF health using a customizable combination of performance parameters – Document the WLAN environment • Analyze. Air Wi-Fi Spectrum Analyzer – RF spectrum analysis for troubleshooting and optimizing Wireless LANs – Real-time device detection, identification, and location – Takes the cost and complexity out of wireless RF analysis 118
Ether. Scope, Interpret. Air and Analyze. Air allow you to management the entire wireless lifecycle • Ether. Scope Series II Network Assistant – Helping first responders solve network problems fast – Integrated troubleshooting capabilities for 802. 11 a/b/g networks – Wireless analysis assists with today’s hot issues: security, performance and connectivity problems • Interpret. Air Wireless Site Survey Software – Easily and graphically survey 802. 11 a/b/g wireless networks – Visualize RF health using a customizable combination of performance parameters – Document the WLAN environment • Analyze. Air Wi-Fi Spectrum Analyzer – RF spectrum analysis for troubleshooting and optimizing Wireless LANs – Real-time device detection, identification, and location – Takes the cost and complexity out of wireless RF analysis 118
 Thanks for coming to Fluke Network’s Wireless Networking Workshop! ANY OTHER QUESTIONS?
Thanks for coming to Fluke Network’s Wireless Networking Workshop! ANY OTHER QUESTIONS?


