822ed6c0c97ebb58c49e604a52daa6b9.ppt
- Количество слайдов: 28
Week 6 Monday, February 27 • IT Infrastructure • Reliability and Security of IT Services • Security R. Ching, Ph. D. • MIS Area • California State University, Sacramento 1

IT Infrastructure, Another View… R. Ching, Ph. D. • MIS Area • California State University, Sacramento 2
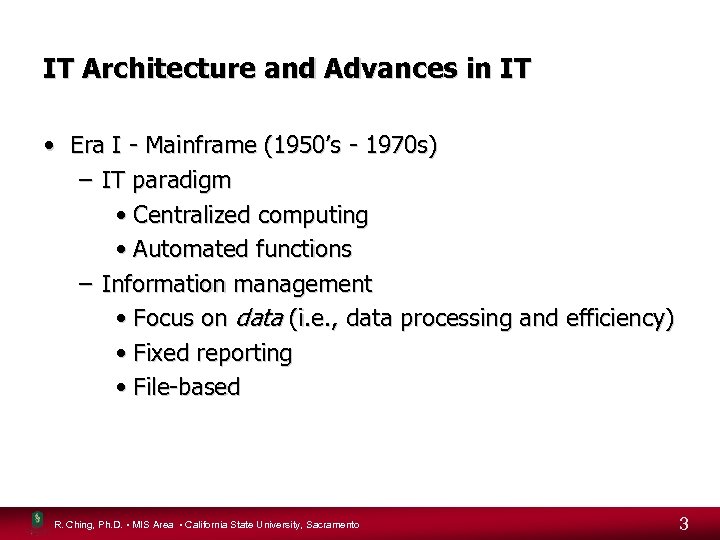
IT Architecture and Advances in IT • Era I - Mainframe (1950’s - 1970 s) – IT paradigm • Centralized computing • Automated functions – Information management • Focus on data (i. e. , data processing and efficiency) • Fixed reporting • File-based R. Ching, Ph. D. • MIS Area • California State University, Sacramento 3
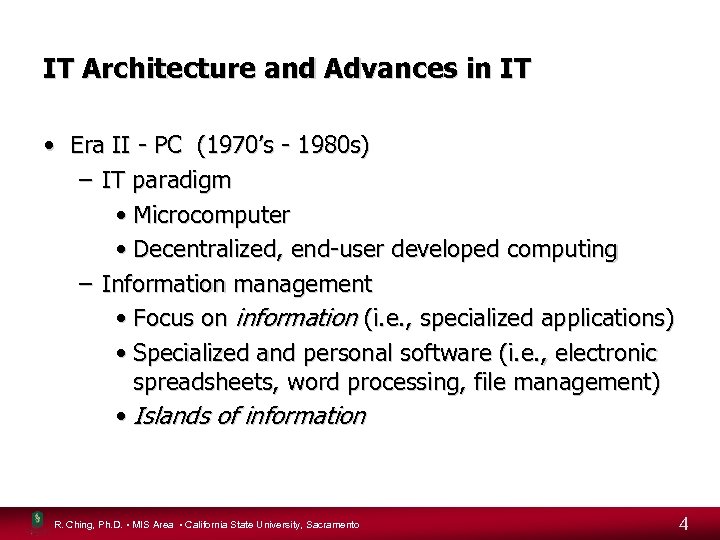
IT Architecture and Advances in IT • Era II - PC (1970’s - 1980 s) – IT paradigm • Microcomputer • Decentralized, end-user developed computing – Information management • Focus on information (i. e. , specialized applications) • Specialized and personal software (i. e. , electronic spreadsheets, word processing, file management) • Islands of information R. Ching, Ph. D. • MIS Area • California State University, Sacramento 4
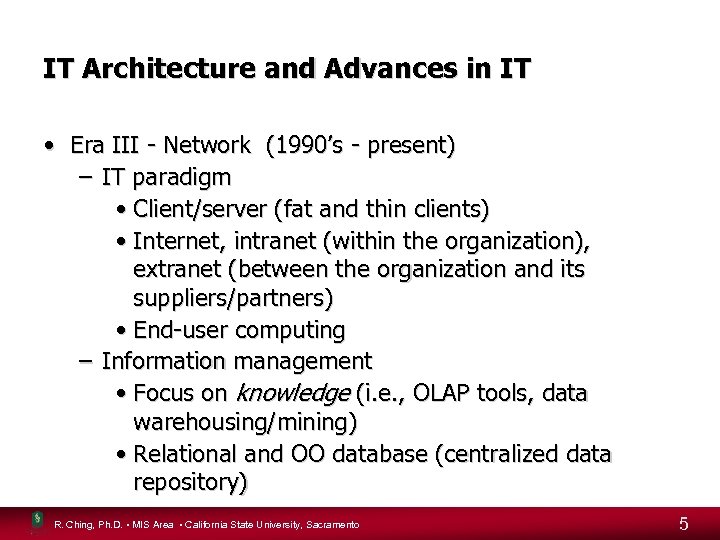
IT Architecture and Advances in IT • Era III - Network (1990’s - present) – IT paradigm • Client/server (fat and thin clients) • Internet, intranet (within the organization), extranet (between the organization and its suppliers/partners) • End-user computing – Information management • Focus on knowledge (i. e. , OLAP tools, data warehousing/mining) • Relational and OO database (centralized data repository) R. Ching, Ph. D. • MIS Area • California State University, Sacramento 5
Infrastructure Delivering the right information to the right people at the right time • Delivering IT resources to support users throughout the organization • Four layer infrastructure (Weill and Broadbent) – IT components – Human IT infrastructure – Shared IT services – services that users can draw upon and share to conduct business – Shared and standard IT applications – stable applications that change less frequently R. Ching, Ph. D. • MIS Area • California State University, Sacramento 6
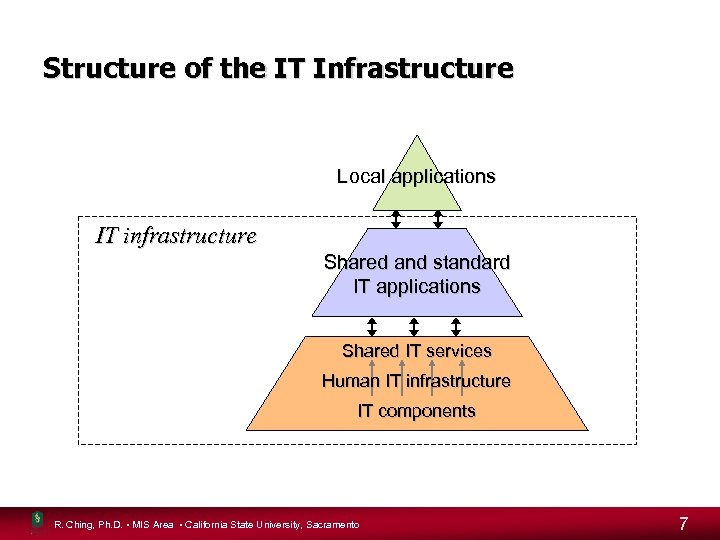
Structure of the IT Infrastructure Local applications IT infrastructure Shared and standard IT applications Shared IT services Human IT infrastructure IT components R. Ching, Ph. D. • MIS Area • California State University, Sacramento 7
Three Views of IT Infrastructure • Economies of scale (utility) – providing IT/IS as a service to the business to facilitate operations – Emphasis on reducing costs • Support for business programs (dependent) – IT tied to business plan and value-added initiatives • Flexibility to meet changes in the marketplace (enabling) – IT planning tied to business strategic plan – Co-alignment between business strategy and IT strategy – Strategic IT and strategic IT planning R. Ching, Ph. D. • MIS Area • California State University, Sacramento 8
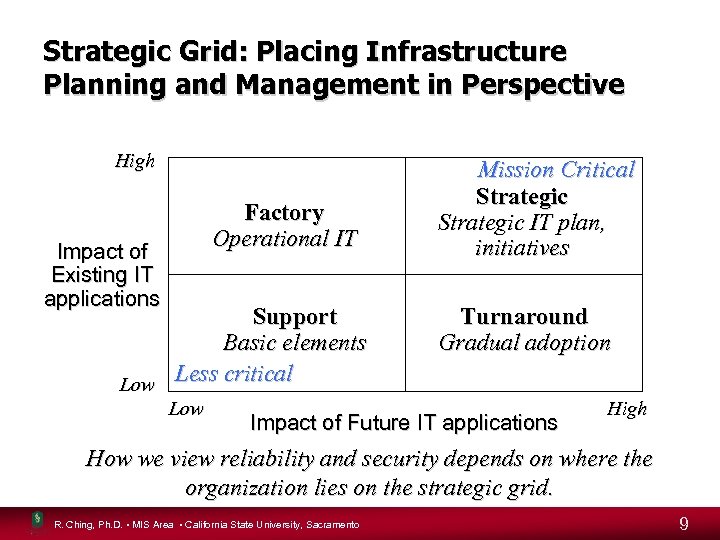
Strategic Grid: Placing Infrastructure Planning and Management in Perspective High Factory Operational IT Impact of Existing IT applications Support Basic elements Low Less critical Low Mission Critical Strategic IT plan, initiatives Turnaround Gradual adoption Impact of Future IT applications High How we view reliability and security depends on where the organization lies on the strategic grid. R. Ching, Ph. D. • MIS Area • California State University, Sacramento 9

Reliability and Availability of the Infrastructure R. Ching, Ph. D. • MIS Area • California State University, Sacramento 10

Infrastructure Reliability • Ensuring continuous operations in support of the organization – 27 x 7 operation (if important) – Redundancy of components – Cost of maintaining continuous operations vs. cost of failure – Threats and countermeasures R. Ching, Ph. D. • MIS Area • California State University, Sacramento 11
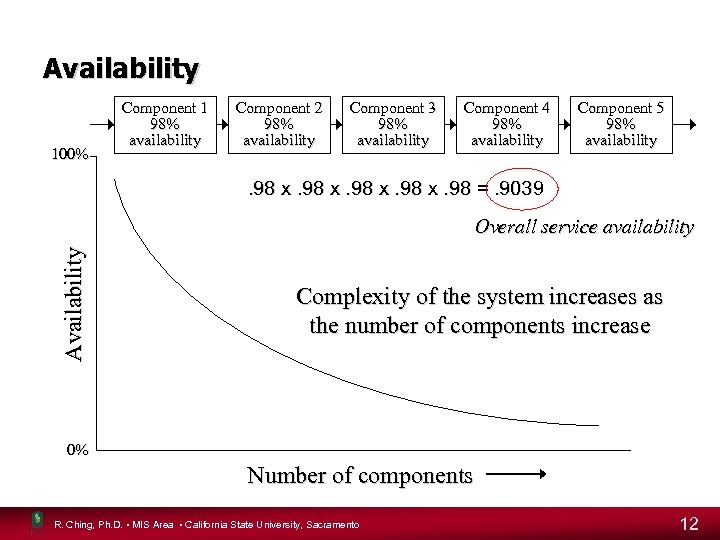
Availability 100% Component 1 98% availability Component 2 98% availability Component 3 98% availability Component 4 98% availability Component 5 98% availability . 98 x. 98 =. 9039 Availability Overall service availability Complexity of the system increases as the number of components increase 0% Number of components R. Ching, Ph. D. • MIS Area • California State University, Sacramento 12
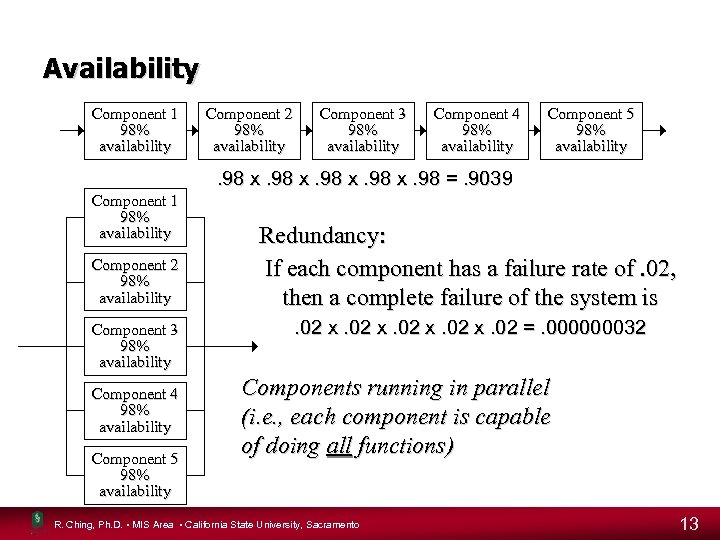
Availability Component 1 98% availability Component 2 98% availability Component 3 98% availability Component 4 98% availability Component 5 98% availability . 98 x. 98 =. 9039 Component 1 98% availability Component 2 98% availability Component 3 98% availability Component 4 98% availability Component 5 98% availability Redundancy: If each component has a failure rate of. 02, then a complete failure of the system is. 02 x. 02 =. 000000032 Components running in parallel (i. e. , each component is capable of doing all functions) R. Ching, Ph. D. • MIS Area • California State University, Sacramento 13

Making a High-Availability Facility • • • Uninterruptible electric power delivery Physical security Climate control and fire suppression Network connectivity N+1 and N+N redundancy of mission critical components R. Ching, Ph. D. • MIS Area • California State University, Sacramento 14

Malicious Threats and Defensive Measures • Types of threats: – External attacks – denial of service (Do. S) – Intrusion – access via the IT infrastructure – Viruses and worms • Defensive measures – Security policies – defines security by recognizing IT as a resource – Firewalls – Authentication – Encryption – Patching and change management – Intrusion detection and network monitoring R. Ching, Ph. D. • MIS Area • California State University, Sacramento 15

Risk Management • Risk of failure or a breach of security • Must be classified (i. e. , critical, not critical, etc. ) • Addressed in proportion to their likelihood and potential consequences • Management action to mitigate risks – Costs vs. potential benefits – Expected loss (probability of a threat occurring x cost) R. Ching, Ph. D. • MIS Area • California State University, Sacramento 16
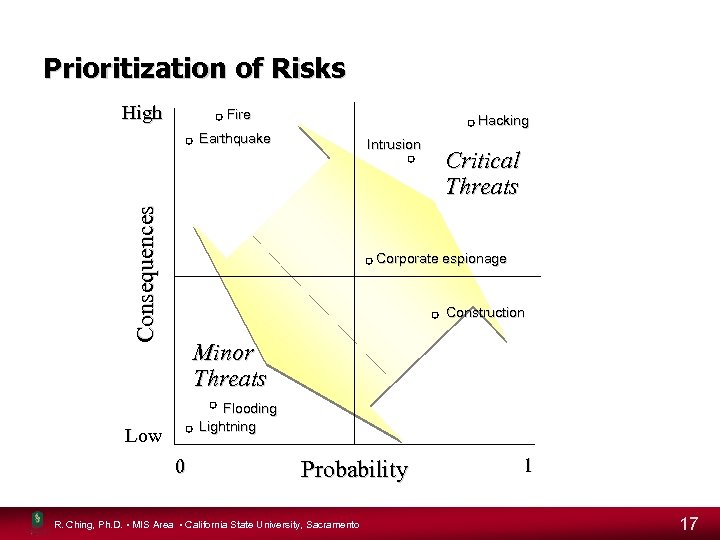
Prioritization of Risks High Fire Hacking Consequences Earthquake Intrusion Critical Threats Corporate espionage Construction Minor Threats Flooding Lightning Low 0 Probability R. Ching, Ph. D. • MIS Area • California State University, Sacramento 1 17

Managing Threats and Risks • • • Sound infrastructure design Disciplined execution of operating procedures Careful documentation Established crisis management procedures Rehearsing incident response – Security audit • Recovery procedures R. Ching, Ph. D. • MIS Area • California State University, Sacramento 18

Another View of Security and Threats… R. Ching, Ph. D. • MIS Area • California State University, Sacramento 19
Threats • Any situation or event, whether intentional or unintentional, that will adversely affect a system and consequently the organization. – Tangible losses (hardware, software, data) – Intangible losses (credibility, confidentiality) Countermeasures and Contingency Plans R. Ching, Ph. D. • MIS Area • California State University, Sacramento 20

Threats and Countermeasures • Initiate countermeasures to overcome threats – Consider the types of threat and their impact on the organization • Cost-effectiveness • Frequency • Severity R. Ching, Ph. D. • MIS Area • California State University, Sacramento 21
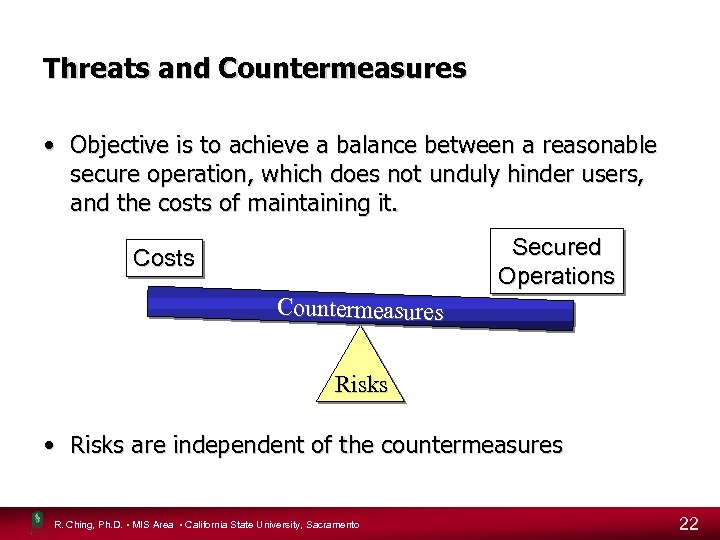
Threats and Countermeasures • Objective is to achieve a balance between a reasonable secure operation, which does not unduly hinder users, and the costs of maintaining it. Secured Operations Costs Countermeasures Risks • Risks are independent of the countermeasures R. Ching, Ph. D. • MIS Area • California State University, Sacramento 22
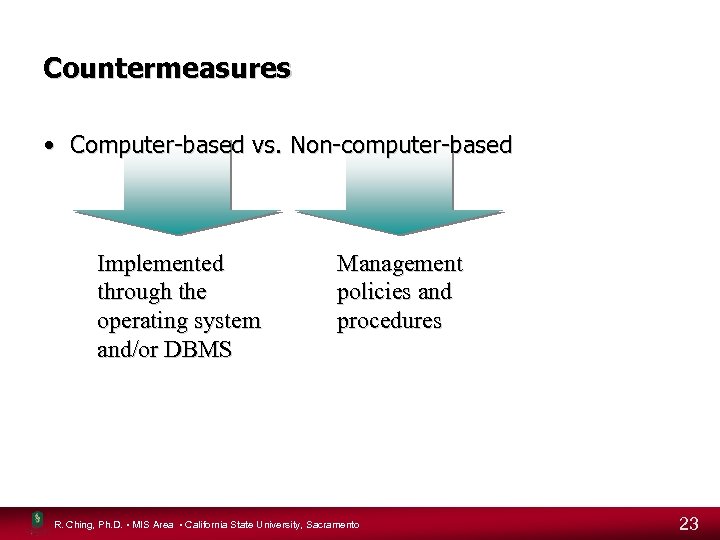
Countermeasures • Computer-based vs. Non-computer-based Implemented through the operating system and/or DBMS Management policies and procedures R. Ching, Ph. D. • MIS Area • California State University, Sacramento 23

Computer-Based Controls • • • Authorization Backup (and recovery) Journaling Integrity controls Encryption Associated procedures R. Ching, Ph. D. • MIS Area • California State University, Sacramento 24
Noncomputer-Based Controls • • • Security policy and contingency plans Personnel controls Securing positioning of equipment Secure data and software Escrow agreements Maintenance agreements Physical access controls Building controls Emergency arrangements R. Ching, Ph. D. • MIS Area • California State University, Sacramento Managementoriented 25
Non-Computer-Based Controls: Countermeasures • Security policy and contingency plan – Security - covers the operations of the database – Contingency plan - addresses plans for catastrophic events • Procedures to follow • Line of command • Personal controls – Assessing and monitoring employees – Training – Responsibilities - sharing and splitting – Job controls R. Ching, Ph. D. • MIS Area • California State University, Sacramento 26
Non-Computer-Based Controls: Countermeasures • Securing: – Hardware – Data and software • Physical access controls – Internal and external • Emergency arrangements – Cold, warm and hot sites R. Ching, Ph. D. • MIS Area • California State University, Sacramento 27

Non-Computer-Based Controls: Countermeasures • Risk analysis – Identify assets – Identify threats and risks – Establish their costs relative to losses – Determine countermeasure • Establish effectiveness of the countermeasure • Establish cost of implementing the countermeasure – Examine cost/benefit of countermeasure – Make recommendation R. Ching, Ph. D. • MIS Area • California State University, Sacramento 28
822ed6c0c97ebb58c49e604a52daa6b9.ppt