a1b9f0cca0750eb6ba8622228fc14be2.ppt
- Количество слайдов: 75
 Week 1: Introduction & Symmetric Cryptographic 1
Week 1: Introduction & Symmetric Cryptographic 1
 Technology and applications play a big role on community services and security aspects 2
Technology and applications play a big role on community services and security aspects 2
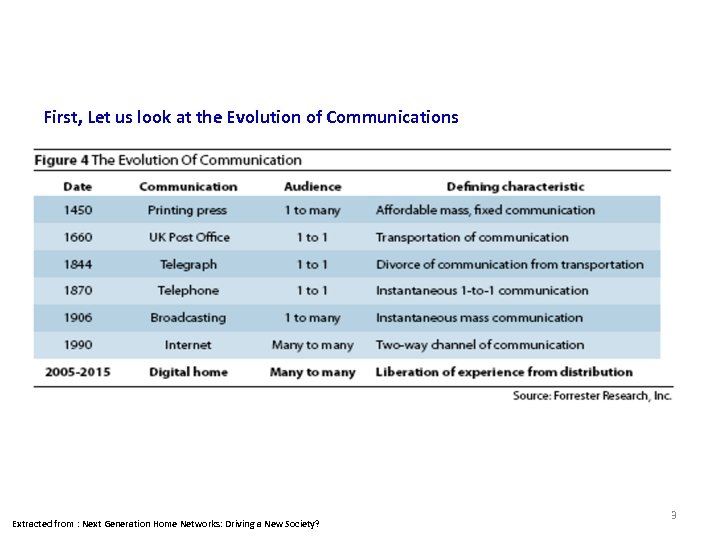 Consumer Market First, Let us look at the Evolution of Communications Extracted from : Next Generation Home Networks: Driving a New Society? 3
Consumer Market First, Let us look at the Evolution of Communications Extracted from : Next Generation Home Networks: Driving a New Society? 3
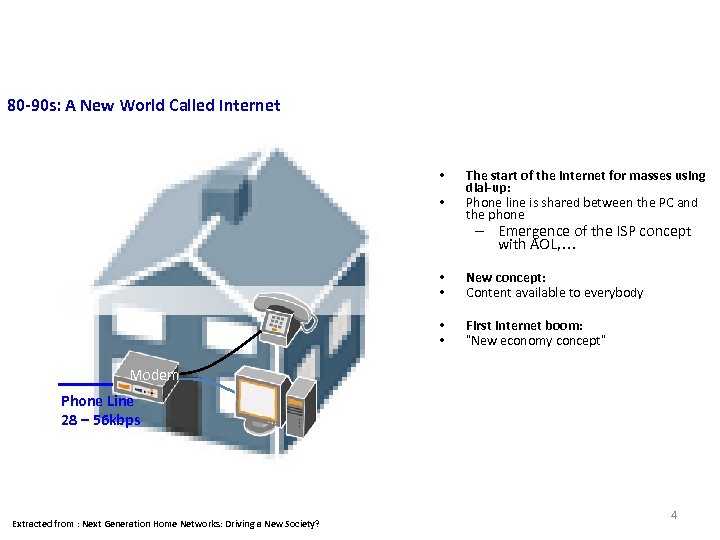 Consumer Market 80 -90 s: A New World Called Internet • • The start of the Internet for masses using dial-up: Phone line is shared between the PC and the phone – Emergence of the ISP concept with AOL, … • • New concept: Content available to everybody • • First Internet boom: “New economy concept” Modem Phone Line 28 – 56 kbps Extracted from : Next Generation Home Networks: Driving a New Society? 4
Consumer Market 80 -90 s: A New World Called Internet • • The start of the Internet for masses using dial-up: Phone line is shared between the PC and the phone – Emergence of the ISP concept with AOL, … • • New concept: Content available to everybody • • First Internet boom: “New economy concept” Modem Phone Line 28 – 56 kbps Extracted from : Next Generation Home Networks: Driving a New Society? 4
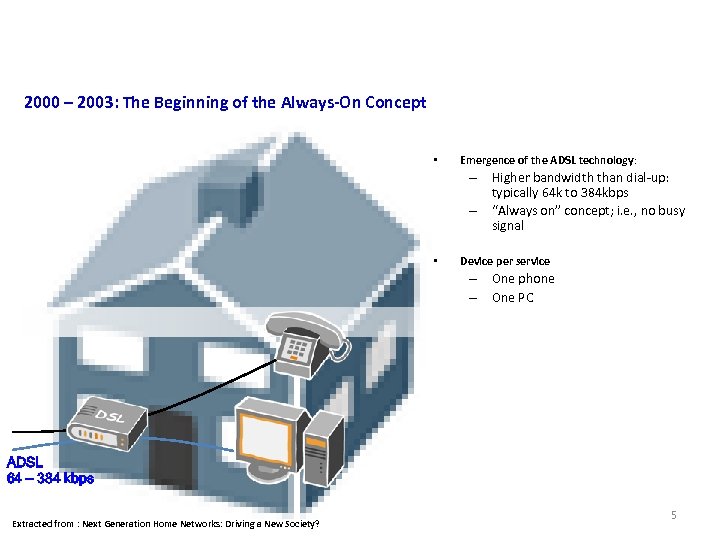 Consumer Market 2000 – 2003: The Beginning of the Always-On Concept • Emergence of the ADSL technology: – Higher bandwidth than dial-up: typically 64 k to 384 kbps – “Always on” concept; i. e. , no busy signal • Device per service – One phone – One PC ADSL 64 – 384 kbps Extracted from : Next Generation Home Networks: Driving a New Society? 5
Consumer Market 2000 – 2003: The Beginning of the Always-On Concept • Emergence of the ADSL technology: – Higher bandwidth than dial-up: typically 64 k to 384 kbps – “Always on” concept; i. e. , no busy signal • Device per service – One phone – One PC ADSL 64 – 384 kbps Extracted from : Next Generation Home Networks: Driving a New Society? 5
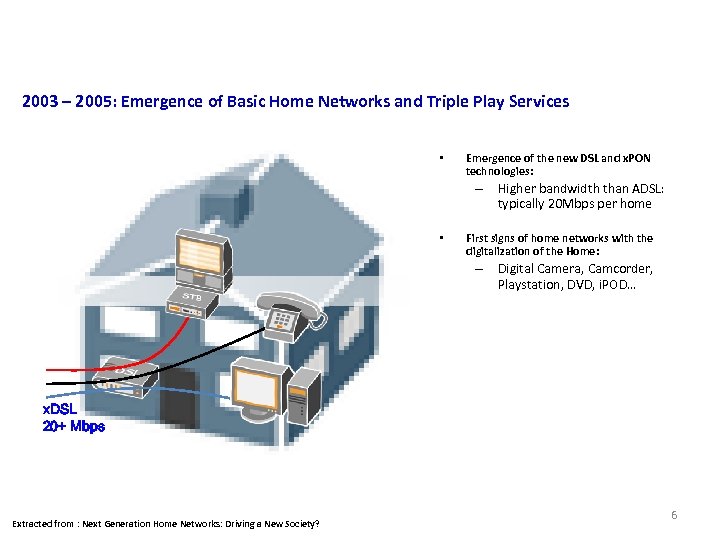 Consumer Market 2003 – 2005: Emergence of Basic Home Networks and Triple Play Services • Emergence of the new DSL and x. PON technologies: – Higher bandwidth than ADSL: typically 20 Mbps per home • First signs of home networks with the digitalization of the Home: – Digital Camera, Camcorder, Playstation, DVD, i. POD… x. DSL 20+ Mbps Extracted from : Next Generation Home Networks: Driving a New Society? 6
Consumer Market 2003 – 2005: Emergence of Basic Home Networks and Triple Play Services • Emergence of the new DSL and x. PON technologies: – Higher bandwidth than ADSL: typically 20 Mbps per home • First signs of home networks with the digitalization of the Home: – Digital Camera, Camcorder, Playstation, DVD, i. POD… x. DSL 20+ Mbps Extracted from : Next Generation Home Networks: Driving a New Society? 6
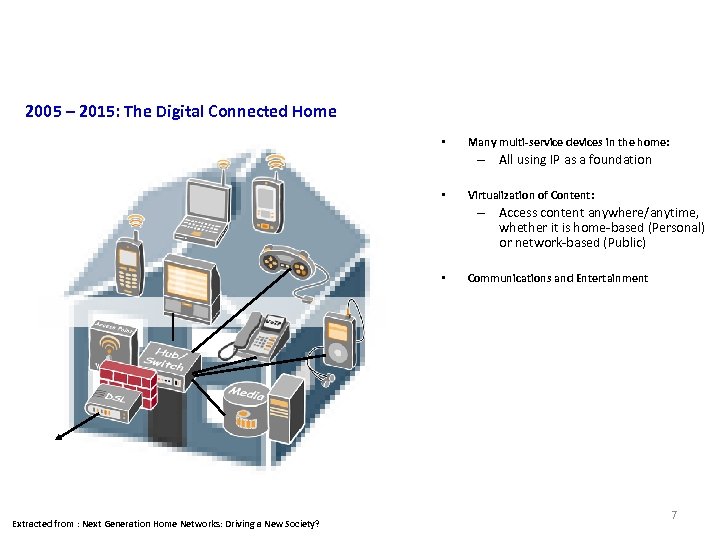 Consumer Market 2005 – 2015: The Digital Connected Home • Many multi-service devices in the home: – All using IP as a foundation • Virtualization of Content: – Access content anywhere/anytime, whether it is home-based (Personal) or network-based (Public) • Extracted from : Next Generation Home Networks: Driving a New Society? Communications and Entertainment 7
Consumer Market 2005 – 2015: The Digital Connected Home • Many multi-service devices in the home: – All using IP as a foundation • Virtualization of Content: – Access content anywhere/anytime, whether it is home-based (Personal) or network-based (Public) • Extracted from : Next Generation Home Networks: Driving a New Society? Communications and Entertainment 7
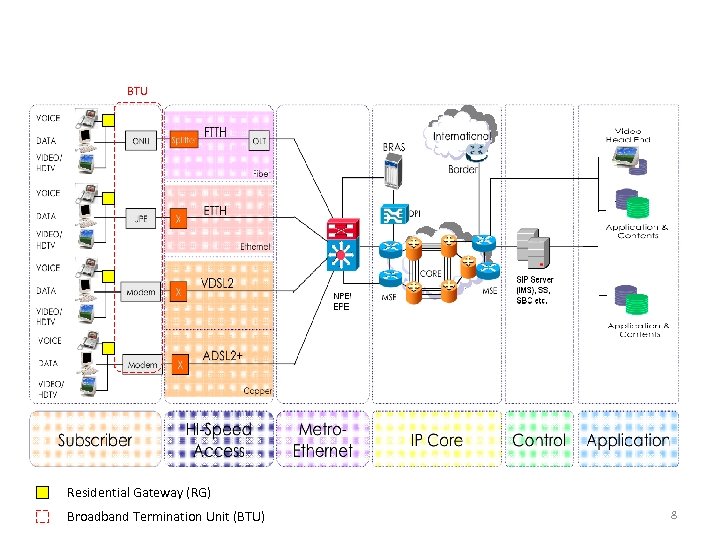 Example of Network Infrastructure BTU Residential Gateway (RG) Broadband Termination Unit (BTU) 8
Example of Network Infrastructure BTU Residential Gateway (RG) Broadband Termination Unit (BTU) 8
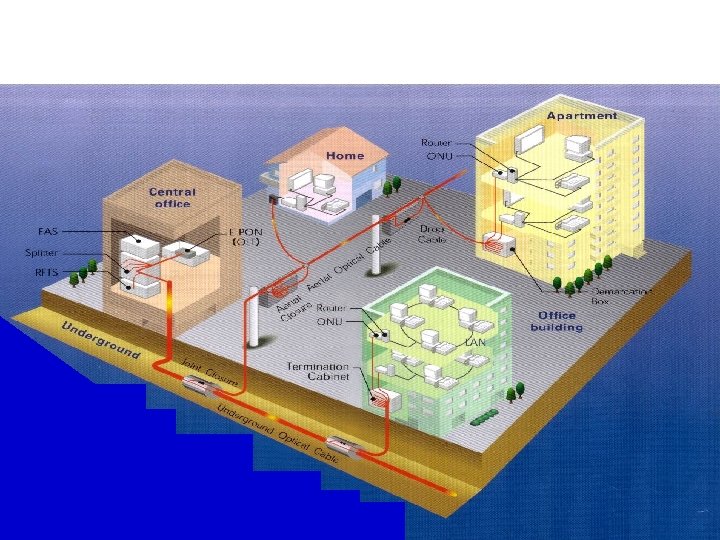 Example of Network Infrastructure 9
Example of Network Infrastructure 9
 Applications over Network 10
Applications over Network 10
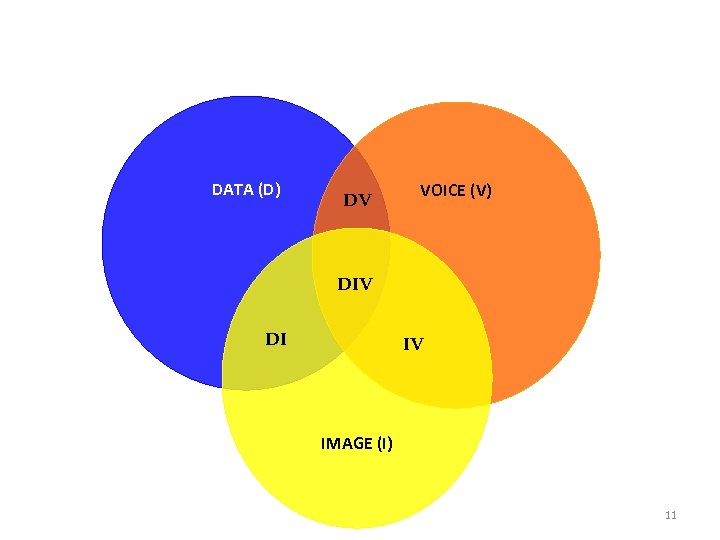 Services DATA (D) DV VOICE (V) DIV DI IV IMAGE (I) 11
Services DATA (D) DV VOICE (V) DIV DI IV IMAGE (I) 11
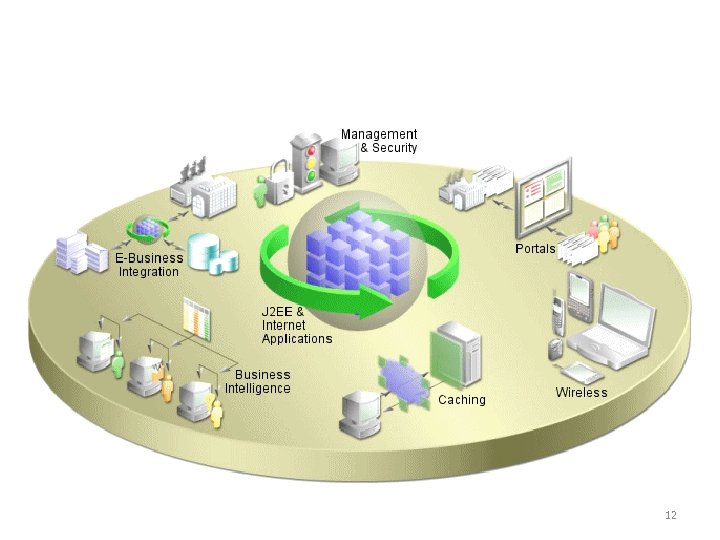 Services 12
Services 12
 What are we facing? 13
What are we facing? 13
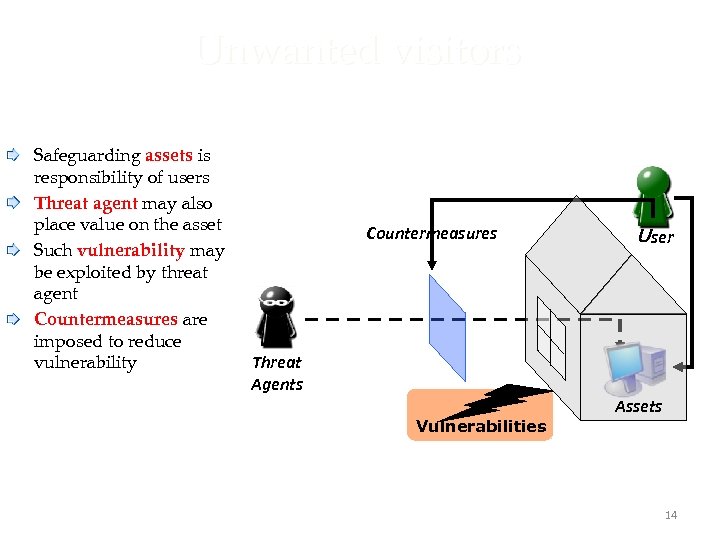 Unwanted visitors Safeguarding assets is responsibility of users Threat agent may also place value on the asset Such vulnerability may be exploited by threat agent Countermeasures are imposed to reduce vulnerability Countermeasures Threat Agents Vulnerabilities 14 User Assets 14
Unwanted visitors Safeguarding assets is responsibility of users Threat agent may also place value on the asset Such vulnerability may be exploited by threat agent Countermeasures are imposed to reduce vulnerability Countermeasures Threat Agents Vulnerabilities 14 User Assets 14
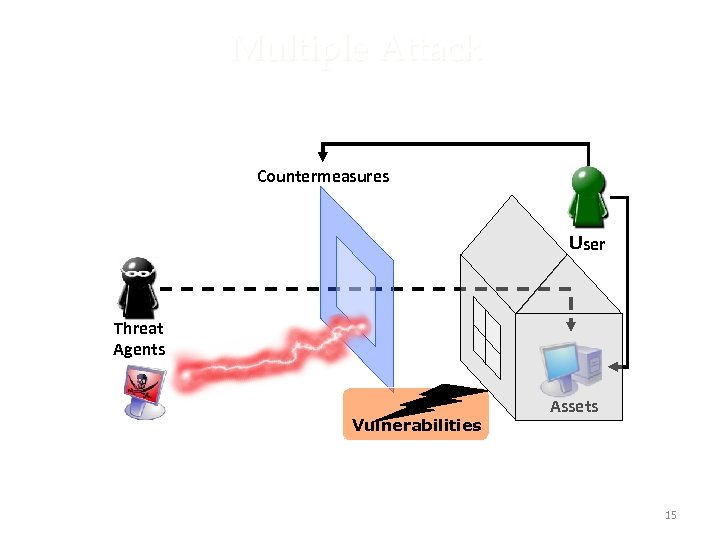 Multiple Attack Countermeasures User Threat Agents Vulnerabilities 15 Assets 15
Multiple Attack Countermeasures User Threat Agents Vulnerabilities 15 Assets 15
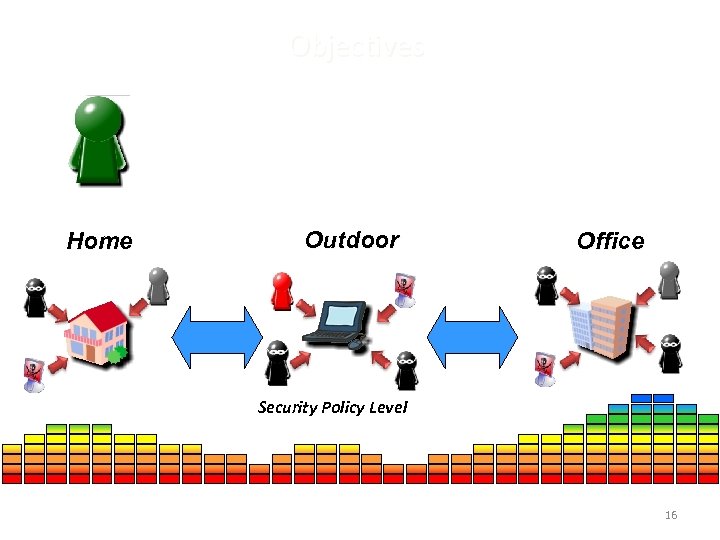 Objectives Home Outdoor Office Security Policy Level 16 16
Objectives Home Outdoor Office Security Policy Level 16 16
 Security mechanism is embedded on technology. Security use in daily basis. 17
Security mechanism is embedded on technology. Security use in daily basis. 17
 Security use in daily basis 1 - biometric 18
Security use in daily basis 1 - biometric 18
 Security use in daily basis 2 - Business 19
Security use in daily basis 2 - Business 19
 Security use in daily basis 3 – Voice Communication 20
Security use in daily basis 3 – Voice Communication 20
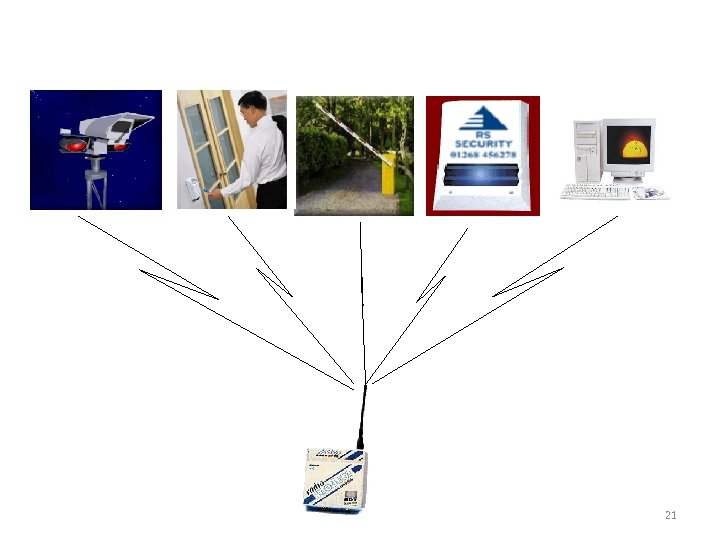 Security use in daily basis 4 – Integration Operation 21
Security use in daily basis 4 – Integration Operation 21
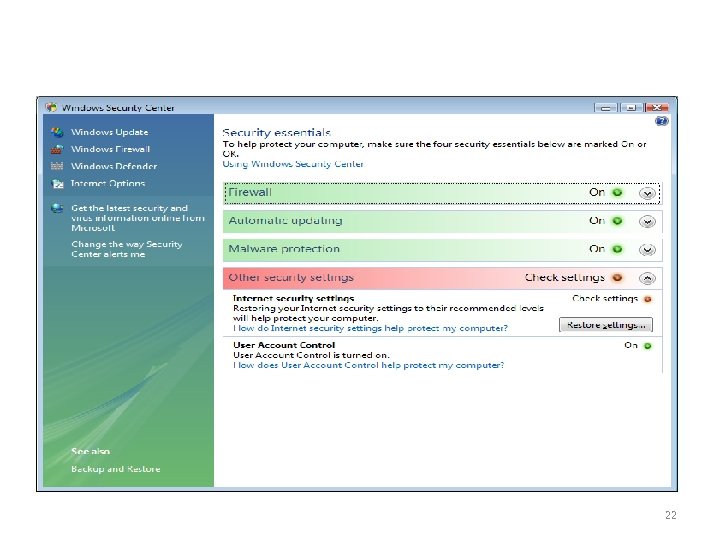 Security use in daily basis 5 – Operating System 22
Security use in daily basis 5 – Operating System 22
 Security use in daily basis 6 – WEB 23
Security use in daily basis 6 – WEB 23
 Let me share with you on OSI layers and Internet layers 24
Let me share with you on OSI layers and Internet layers 24
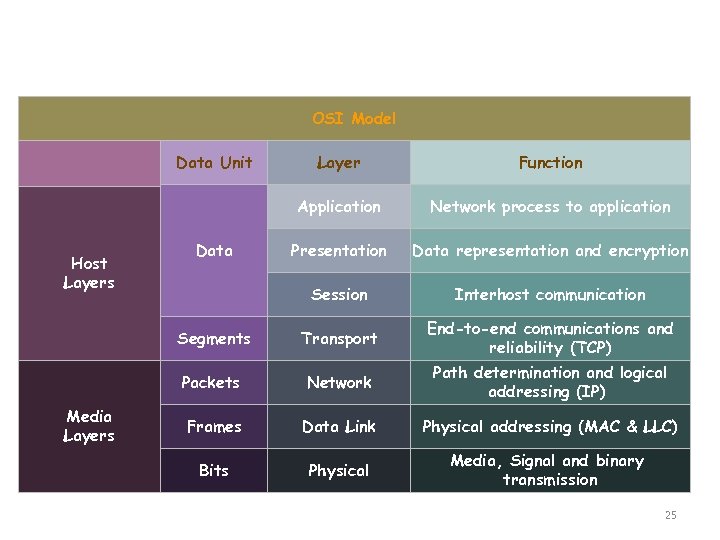 Seventh layers OSI Model Application OSI Model Network process to application Presentation Data Unit Layer Function Application Network process to application Presentation Host Layers Session Presentation Data representation and encryption Session Interhost communication Segments Transport End-to-end communications and reliability (TCP) Network Packets Network Path determination and logical addressing (IP) Media Data Link Layers Frames Data Link Physical addressing (MAC & LLC) Bits Physical Media, Signal and binary transmission 25
Seventh layers OSI Model Application OSI Model Network process to application Presentation Data Unit Layer Function Application Network process to application Presentation Host Layers Session Presentation Data representation and encryption Session Interhost communication Segments Transport End-to-end communications and reliability (TCP) Network Packets Network Path determination and logical addressing (IP) Media Data Link Layers Frames Data Link Physical addressing (MAC & LLC) Bits Physical Media, Signal and binary transmission 25
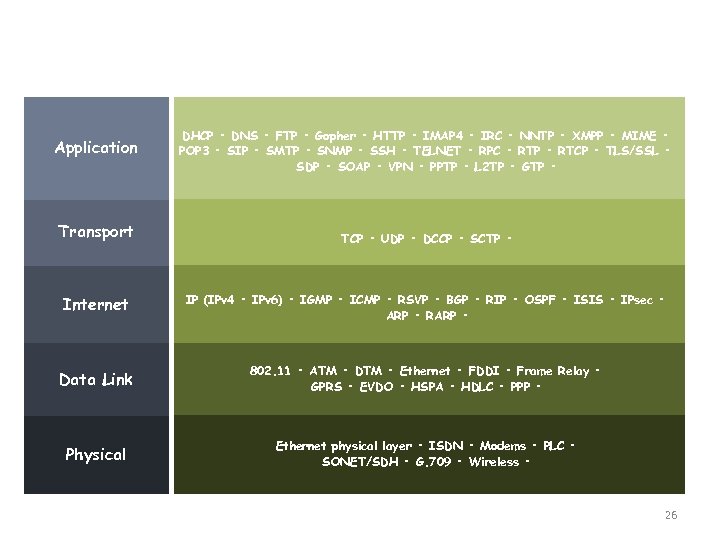 Five Layers TCP/IP Model Application Transport Application DHCP • DNS • FTP • Gopher • HTTP • IMAP 4 • IRC • NNTP • XMPP • MIME • POP 3 • SIP • SMTP • SNMP • SSH • TELNET • RPC • RTP • RTCP • TLS/SSL • SDP • SOAP • VPN • PPTP • L 2 TP • GTP • Presentation TCP • UDP • DCCP • SCTP • Internet IP (IPv 4 • IPv 6) • IGMP • ICMP • RSVP • BGP • RIP • OSPF • ISIS • IPsec • ARP • RARP • Data Link 802. 11 • ATM • DTM • Ethernet • FDDI • Frame Relay • GPRS • EVDO • HSPA • HDLC • PPP • Physical Ethernet physical layer • ISDN • Modems • PLC • SONET/SDH • G. 709 • Wireless • 26
Five Layers TCP/IP Model Application Transport Application DHCP • DNS • FTP • Gopher • HTTP • IMAP 4 • IRC • NNTP • XMPP • MIME • POP 3 • SIP • SMTP • SNMP • SSH • TELNET • RPC • RTP • RTCP • TLS/SSL • SDP • SOAP • VPN • PPTP • L 2 TP • GTP • Presentation TCP • UDP • DCCP • SCTP • Internet IP (IPv 4 • IPv 6) • IGMP • ICMP • RSVP • BGP • RIP • OSPF • ISIS • IPsec • ARP • RARP • Data Link 802. 11 • ATM • DTM • Ethernet • FDDI • Frame Relay • GPRS • EVDO • HSPA • HDLC • PPP • Physical Ethernet physical layer • ISDN • Modems • PLC • SONET/SDH • G. 709 • Wireless • 26
 Hexadecimal dump of the Packet • Hexadecimal Dump of the Packet • • 0: 00 e 0 f 726 3 fe 9 0800 2086 354 b 0800 4500 16: 0028 08 b 9 4000 ff 06 999 a 8 b 85 d 96 e 8 b 85 32: e 902 9005 0017 7214 f 115 9431 1028 5010 48: 2238 1 c 80 0000 . . ÷&? . . 5 K. . E. . (. . @. . . . n. . . . r. . 1. (P. "8. . 27
Hexadecimal dump of the Packet • Hexadecimal Dump of the Packet • • 0: 00 e 0 f 726 3 fe 9 0800 2086 354 b 0800 4500 16: 0028 08 b 9 4000 ff 06 999 a 8 b 85 d 96 e 8 b 85 32: e 902 9005 0017 7214 f 115 9431 1028 5010 48: 2238 1 c 80 0000 . . ÷&? . . 5 K. . E. . (. . @. . . . n. . . . r. . 1. (P. "8. . 27
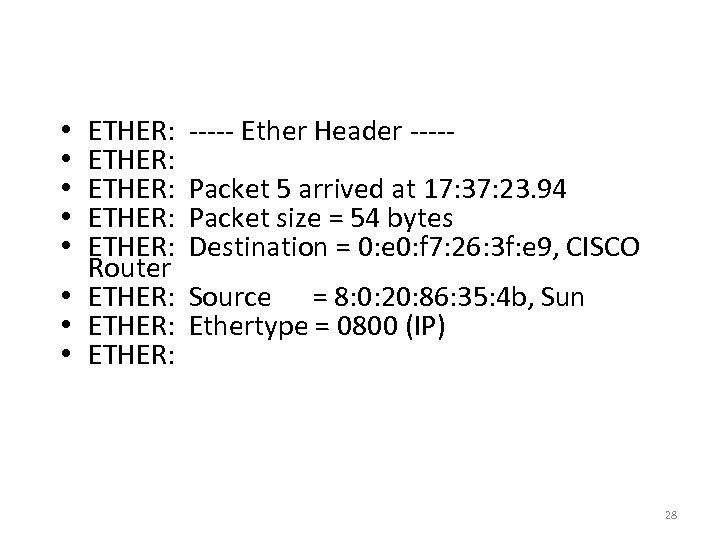 Packet Decode ETHER: ETHER: Router • ETHER: • • • ----- Ether Header ----Packet 5 arrived at 17: 37: 23. 94 Packet size = 54 bytes Destination = 0: e 0: f 7: 26: 3 f: e 9, CISCO Source = 8: 0: 20: 86: 35: 4 b, Sun Ethertype = 0800 (IP) 28
Packet Decode ETHER: ETHER: Router • ETHER: • • • ----- Ether Header ----Packet 5 arrived at 17: 37: 23. 94 Packet size = 54 bytes Destination = 0: e 0: f 7: 26: 3 f: e 9, CISCO Source = 8: 0: 20: 86: 35: 4 b, Sun Ethertype = 0800 (IP) 28
 Packet Decode IP: IP: IP: IP: IP: ----- IP Header ----Version = 4 Header length = 20 bytes Type of service = 0 x 00 (normal) Total length = 40 bytes Identification = 2233 Flags = 0 x 4. 1. . . = do not fragment. . 0. . . = last fragment Fragment offset = 0 bytes Time to live = 255 seconds/hops Protocol = 6 (TCP) Header checksum = 999 a Source address = 139. 133. 217. 110, client Destination address = 139. 133. 2, server. abdn. ac. uk No options 29
Packet Decode IP: IP: IP: IP: IP: ----- IP Header ----Version = 4 Header length = 20 bytes Type of service = 0 x 00 (normal) Total length = 40 bytes Identification = 2233 Flags = 0 x 4. 1. . . = do not fragment. . 0. . . = last fragment Fragment offset = 0 bytes Time to live = 255 seconds/hops Protocol = 6 (TCP) Header checksum = 999 a Source address = 139. 133. 217. 110, client Destination address = 139. 133. 2, server. abdn. ac. uk No options 29
 Packet Decode TCP: TCP: TCP: TCP: TCP: ----- TCP Header ----Source port = 36869 Destination port = 23 (TELNET) Sequence number = 1913975061 Acknowledgement number = 2486243368 Data offset = 20 bytes Flags = 0 x 10. . = No urgent pointer. . . 1. . = Acknowledgement. . 0. . . = No push. . . 0. . = No reset. . . 0. = No Syn. . . . 0 = No Fin Window = 8760 Checksum = 0 x 1 c 80 Urgent pointer = 0 No options 30
Packet Decode TCP: TCP: TCP: TCP: TCP: ----- TCP Header ----Source port = 36869 Destination port = 23 (TELNET) Sequence number = 1913975061 Acknowledgement number = 2486243368 Data offset = 20 bytes Flags = 0 x 10. . = No urgent pointer. . . 1. . = Acknowledgement. . 0. . . = No push. . . 0. . = No reset. . . 0. = No Syn. . . . 0 = No Fin Window = 8760 Checksum = 0 x 1 c 80 Urgent pointer = 0 No options 30
 Five Layers TCP/IP Model TCP/IP Fundamentals Connection-oriented and connectionless services The TCP/IP layers Differences between OSI and TCP/IP models 31
Five Layers TCP/IP Model TCP/IP Fundamentals Connection-oriented and connectionless services The TCP/IP layers Differences between OSI and TCP/IP models 31
 Connection-Oriented Services • Connection-oriented service modeled after the telephone system – To talk to someone, pick up a phone, dial the number, talk and disconnect • Similarly, in a network, the service user will – Establish a connection – Use the connection – Release the connection – The sender, receiver and the network may conduct a negotiation about data transfer speed, maximum message size, etc 32
Connection-Oriented Services • Connection-oriented service modeled after the telephone system – To talk to someone, pick up a phone, dial the number, talk and disconnect • Similarly, in a network, the service user will – Establish a connection – Use the connection – Release the connection – The sender, receiver and the network may conduct a negotiation about data transfer speed, maximum message size, etc 32
 Connection-Oriented Services • Connection-oriented service is used when reliability is important – E. g. , for file transfer, we want that all bits arrive correctly and in the order they were sent 33
Connection-Oriented Services • Connection-oriented service is used when reliability is important – E. g. , for file transfer, we want that all bits arrive correctly and in the order they were sent 33
 Connectionless Services • Connectionless service modeled after the postal system – Each message (letter) carries the full destination address – Each message is routed through the system independent of all others – If two messages are sent to the same destination, normally the first one to be sent should arrive first. But it is possible that the second message arrives first 34
Connectionless Services • Connectionless service modeled after the postal system – Each message (letter) carries the full destination address – Each message is routed through the system independent of all others – If two messages are sent to the same destination, normally the first one to be sent should arrive first. But it is possible that the second message arrives first 34
 TCP/IP Protocol Suite • • • TCP / IP – Transmission Control Protocol / Internet Protocol Developed prior to the OSI model Layers of TCP/IP do not match exactly with those in the OSI model Used in the Internet Ability to connect multiple networks in a seamless way was one of the major design goals which led to development of TCP / IP 35
TCP/IP Protocol Suite • • • TCP / IP – Transmission Control Protocol / Internet Protocol Developed prior to the OSI model Layers of TCP/IP do not match exactly with those in the OSI model Used in the Internet Ability to connect multiple networks in a seamless way was one of the major design goals which led to development of TCP / IP 35
 TCP/IP Protocol Suite • TCP / IP – refers to a collection of data communication protocols • This name TCP/IP is misleading because TCP and IP are only two of the many protocols that compose the suite • TCP / IP has its origins in the work done by the US Department of Defense. 36
TCP/IP Protocol Suite • TCP / IP – refers to a collection of data communication protocols • This name TCP/IP is misleading because TCP and IP are only two of the many protocols that compose the suite • TCP / IP has its origins in the work done by the US Department of Defense. 36
 TCP / IP Suite • The TCP / IP suite does not define any specific protocols at the data link and physical layers 37
TCP / IP Suite • The TCP / IP suite does not define any specific protocols at the data link and physical layers 37
 Application Layer • The Application layer is equivalent to the combined OSI Session, Presentation, and Application layers • All the functions handled by these 3 layers in the OSI model are handled by the Application layer in TCP / IP model 38
Application Layer • The Application layer is equivalent to the combined OSI Session, Presentation, and Application layers • All the functions handled by these 3 layers in the OSI model are handled by the Application layer in TCP / IP model 38
 Application Layer This layer contains all the higher-level protocols FTP – File Transfer Protocol – basic file transfer between hosts (computers) SMTP – Simple Mail Transfer Protocol (for email) HTTP – Hyper Text Transfer Protocol (for web browsing) Data unit created at this layer is called a message 39
Application Layer This layer contains all the higher-level protocols FTP – File Transfer Protocol – basic file transfer between hosts (computers) SMTP – Simple Mail Transfer Protocol (for email) HTTP – Hyper Text Transfer Protocol (for web browsing) Data unit created at this layer is called a message 39
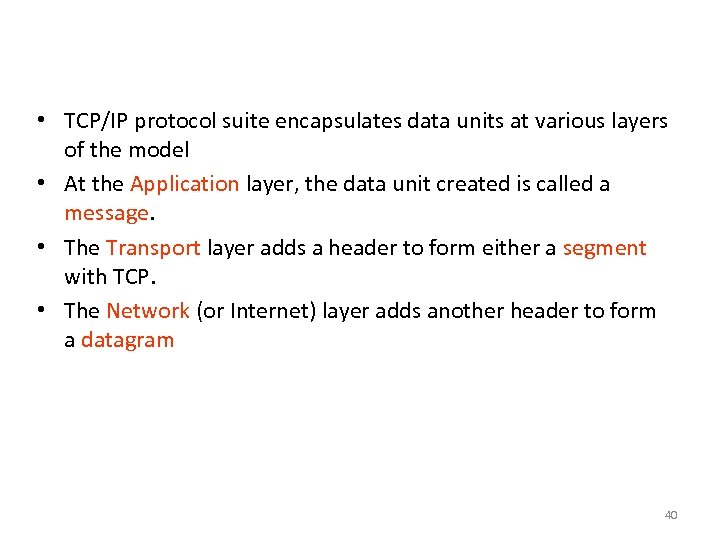 Encapsulation of Data • TCP/IP protocol suite encapsulates data units at various layers of the model • At the Application layer, the data unit created is called a message. • The Transport layer adds a header to form either a segment with TCP. • The Network (or Internet) layer adds another header to form a datagram 40
Encapsulation of Data • TCP/IP protocol suite encapsulates data units at various layers of the model • At the Application layer, the data unit created is called a message. • The Transport layer adds a header to form either a segment with TCP. • The Network (or Internet) layer adds another header to form a datagram 40
 Encapsulation of Data • Datagram – A self-contained message unit which contains sufficient information to allow it to be routed from the source to the destination • The protocol used at the data link layer encapsulates the datagram into a frame and this is transmitted across the transmission medium. 41
Encapsulation of Data • Datagram – A self-contained message unit which contains sufficient information to allow it to be routed from the source to the destination • The protocol used at the data link layer encapsulates the datagram into a frame and this is transmitted across the transmission medium. 41
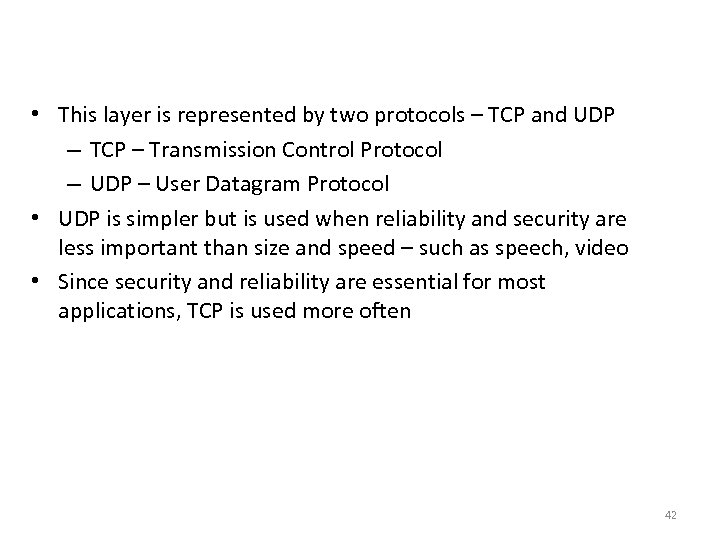 Transport Layer - UDP • This layer is represented by two protocols – TCP and UDP – TCP – Transmission Control Protocol – UDP – User Datagram Protocol • UDP is simpler but is used when reliability and security are less important than size and speed – such as speech, video • Since security and reliability are essential for most applications, TCP is used more often 42
Transport Layer - UDP • This layer is represented by two protocols – TCP and UDP – TCP – Transmission Control Protocol – UDP – User Datagram Protocol • UDP is simpler but is used when reliability and security are less important than size and speed – such as speech, video • Since security and reliability are essential for most applications, TCP is used more often 42
 Transport Layer - TCP • TCP is a reliable connection-oriented protocol • Allows error-free transmission • Incoming byte stream is fragmented into a number of shorter messages and these are passed on to the next layer • At the receiving end the TCP reassembles the messages into an output stream • TCP also handles flow control – to control data transfer rate 43
Transport Layer - TCP • TCP is a reliable connection-oriented protocol • Allows error-free transmission • Incoming byte stream is fragmented into a number of shorter messages and these are passed on to the next layer • At the receiving end the TCP reassembles the messages into an output stream • TCP also handles flow control – to control data transfer rate 43
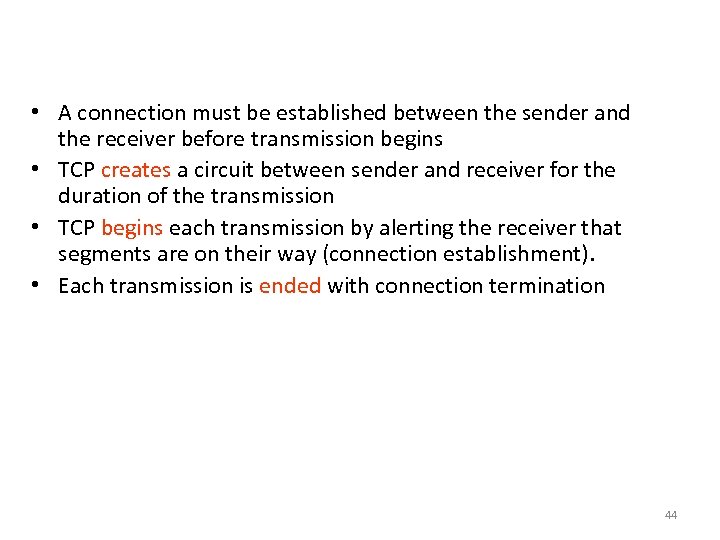 Transport Layer - TCP • A connection must be established between the sender and the receiver before transmission begins • TCP creates a circuit between sender and receiver for the duration of the transmission • TCP begins each transmission by alerting the receiver that segments are on their way (connection establishment). • Each transmission is ended with connection termination 44
Transport Layer - TCP • A connection must be established between the sender and the receiver before transmission begins • TCP creates a circuit between sender and receiver for the duration of the transmission • TCP begins each transmission by alerting the receiver that segments are on their way (connection establishment). • Each transmission is ended with connection termination 44
 Transport Layer - TCP • Each segment created by TCP includes – A sequencing number for re-ordering after receipt. – An acknowledgement ID number – Source address – Destination address – Checksum – for error detection – Data – And other fields 45
Transport Layer - TCP • Each segment created by TCP includes – A sequencing number for re-ordering after receipt. – An acknowledgement ID number – Source address – Destination address – Checksum – for error detection – Data – And other fields 45
 Internetwork or Network Layer Also referred to as Network Layer or Internetwork Layer Internetwork Protocol (IP) is an unreliable and connectionless protocol It offers a best–effort delivery service No error checking IP does its best to get a transmission through to its destination but with no guarantees Noise can cause bit errors during transmission Datagrams maybe discarded due to timeout errors Example of best-effort delivery service is: post-office 46
Internetwork or Network Layer Also referred to as Network Layer or Internetwork Layer Internetwork Protocol (IP) is an unreliable and connectionless protocol It offers a best–effort delivery service No error checking IP does its best to get a transmission through to its destination but with no guarantees Noise can cause bit errors during transmission Datagrams maybe discarded due to timeout errors Example of best-effort delivery service is: post-office 46
 Internetwork or Network Layer IP transports data in packets called datagrams Each datagram is transported separately Datagrams can be of variable lengths (up to 64 KB) Datagrams may travel along different routes and may arrive out of sequence IP does not keep track of the routes IP does not have the facility to reorder datagrams once they arrive A datagram contains a header and data The header contains a number of fields including source and destination address 47
Internetwork or Network Layer IP transports data in packets called datagrams Each datagram is transported separately Datagrams can be of variable lengths (up to 64 KB) Datagrams may travel along different routes and may arrive out of sequence IP does not keep track of the routes IP does not have the facility to reorder datagrams once they arrive A datagram contains a header and data The header contains a number of fields including source and destination address 47
 Comparison of OSI and TCP/IP Models • The OSI model makes a clear distinction between services, interfaces and protocols – Each layer performs some service for the layer above it – A layer’s interface tells the processes above it how to access it. It specifies what the parameters are and what results to expect (somewhat like a function declaration) – The protocols used in a layer are used to get the job done. 48
Comparison of OSI and TCP/IP Models • The OSI model makes a clear distinction between services, interfaces and protocols – Each layer performs some service for the layer above it – A layer’s interface tells the processes above it how to access it. It specifies what the parameters are and what results to expect (somewhat like a function declaration) – The protocols used in a layer are used to get the job done. 48
 Comparison of OSI and TCP/IP Models • The OSI model has 7 layers while the TCP/ IP model has 5 layers • Both have network, transport, and application layers, but the other layers are different • OSI model supports both connectionless and connectionoriented communication • TCP/IP supports only connectionless communication 49
Comparison of OSI and TCP/IP Models • The OSI model has 7 layers while the TCP/ IP model has 5 layers • Both have network, transport, and application layers, but the other layers are different • OSI model supports both connectionless and connectionoriented communication • TCP/IP supports only connectionless communication 49
 Before I explain to you on security layer Let review back the slides that presenting on “security use in daily basis” 50
Before I explain to you on security layer Let review back the slides that presenting on “security use in daily basis” 50
 What is behind of these applications? What is a mechanism that make it secure? 51
What is behind of these applications? What is a mechanism that make it secure? 51
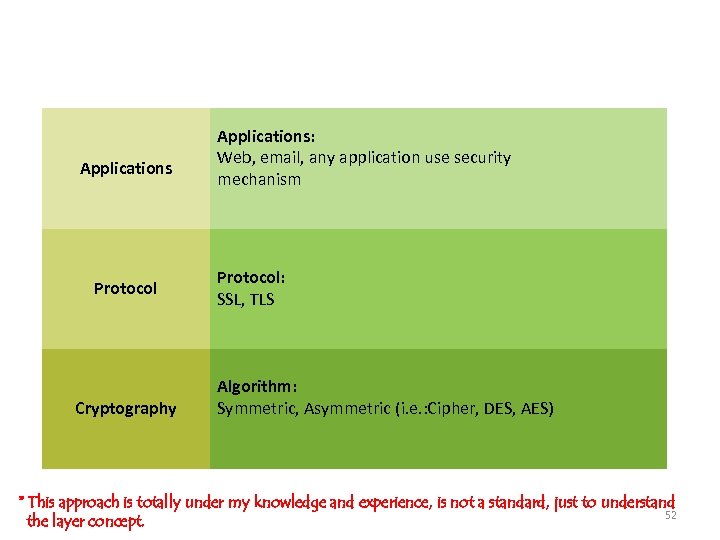 Security Flows Applications Protocol Cryptography Applications: Web, email, any application use security mechanism Protocol: SSL, TLS Algorithm: Symmetric, Asymmetric (i. e. : Cipher, DES, AES) * This approach is totally under my knowledge and experience, is not a standard, just to understand 52 the layer concept.
Security Flows Applications Protocol Cryptography Applications: Web, email, any application use security mechanism Protocol: SSL, TLS Algorithm: Symmetric, Asymmetric (i. e. : Cipher, DES, AES) * This approach is totally under my knowledge and experience, is not a standard, just to understand 52 the layer concept.
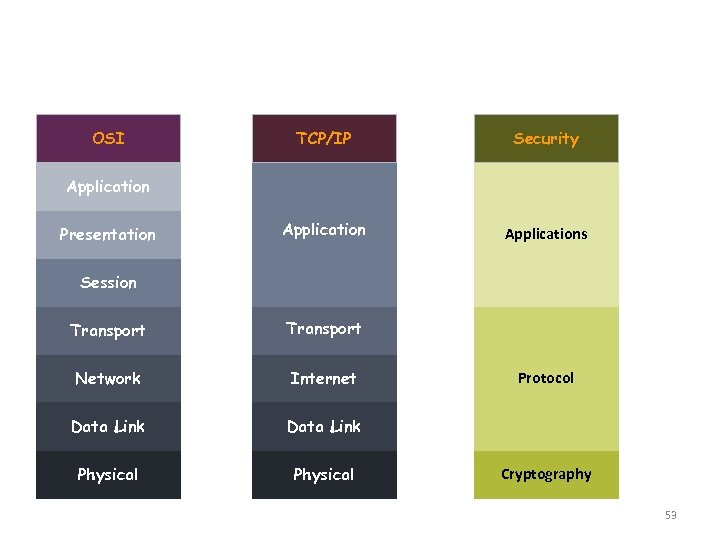 Security versus OSI & TCP/IP Model OSI TCP/IP Application Presentation Security Applications Session Transport Network Internet Data Link Physical Protocol Cryptography 53
Security versus OSI & TCP/IP Model OSI TCP/IP Application Presentation Security Applications Session Transport Network Internet Data Link Physical Protocol Cryptography 53
 Concept Why we want security? Let review back the slides that presenting on “security use in daily basis” 54
Concept Why we want security? Let review back the slides that presenting on “security use in daily basis” 54
 Intruder 55
Intruder 55
 Hacking - 1 56
Hacking - 1 56
 Hacking - 2 DATA CENTER 57
Hacking - 2 DATA CENTER 57
 Objectives Home Outdoor Office Security Policy Level 58 58
Objectives Home Outdoor Office Security Policy Level 58 58
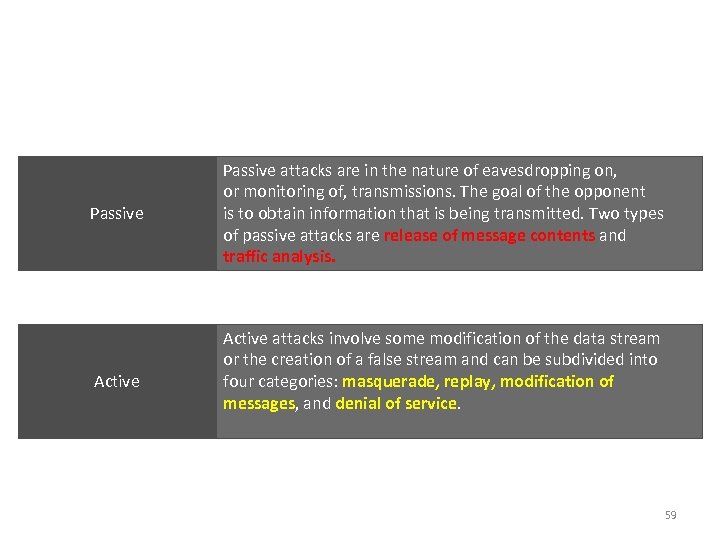 Type of Attacks Passive Active Passive attacks are in the nature of eavesdropping on, or monitoring of, transmissions. The goal of the opponent is to obtain information that is being transmitted. Two types of passive attacks are release of message contents and traffic analysis. Active attacks involve some modification of the data stream or the creation of a false stream and can be subdivided into four categories: masquerade, replay, modification of messages, and denial of service. 59
Type of Attacks Passive Active Passive attacks are in the nature of eavesdropping on, or monitoring of, transmissions. The goal of the opponent is to obtain information that is being transmitted. Two types of passive attacks are release of message contents and traffic analysis. Active attacks involve some modification of the data stream or the creation of a false stream and can be subdivided into four categories: masquerade, replay, modification of messages, and denial of service. 59
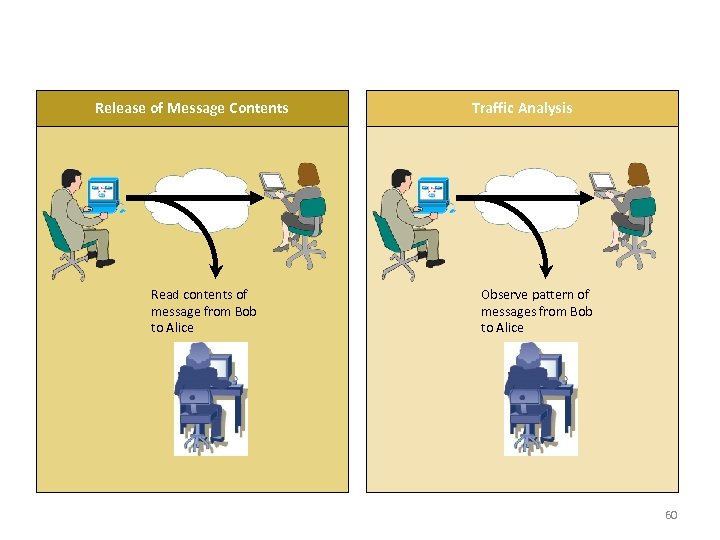 Passive Attack Release of Message Contents Read contents of message from Bob to Alice Traffic Analysis Observe pattern of messages from Bob to Alice 60
Passive Attack Release of Message Contents Read contents of message from Bob to Alice Traffic Analysis Observe pattern of messages from Bob to Alice 60
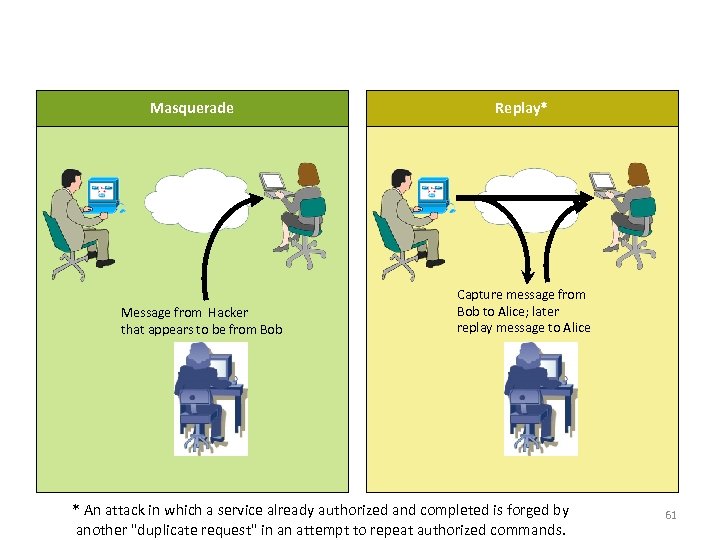 Active Attack - 1 Masquerade Message from Hacker that appears to be from Bob Replay* Capture message from Bob to Alice; later replay message to Alice * An attack in which a service already authorized and completed is forged by another "duplicate request" in an attempt to repeat authorized commands. 61
Active Attack - 1 Masquerade Message from Hacker that appears to be from Bob Replay* Capture message from Bob to Alice; later replay message to Alice * An attack in which a service already authorized and completed is forged by another "duplicate request" in an attempt to repeat authorized commands. 61
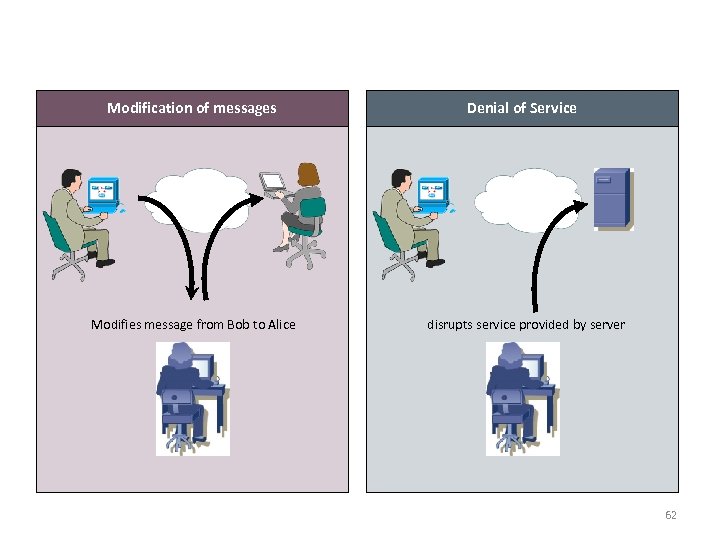 Active Attack - 2 Modification of messages Modifies message from Bob to Alice Denial of Service disrupts service provided by server 62
Active Attack - 2 Modification of messages Modifies message from Bob to Alice Denial of Service disrupts service provided by server 62
 Could you explain to me why we need security? 63
Could you explain to me why we need security? 63
 Why We Need Security Privacy The protection of data from unauthorized disclosure. Integrity The assurance that data received are exactly as sent by an authorized entity (i. e. , contain no modification, insertion, deletion. Authentication The assurance that the communicating entity is the one that it claims to be. Nonrepudation Provides protection against denial by one of the entities involved in a communication of having participated in all or part of the communication. 64
Why We Need Security Privacy The protection of data from unauthorized disclosure. Integrity The assurance that data received are exactly as sent by an authorized entity (i. e. , contain no modification, insertion, deletion. Authentication The assurance that the communicating entity is the one that it claims to be. Nonrepudation Provides protection against denial by one of the entities involved in a communication of having participated in all or part of the communication. 64
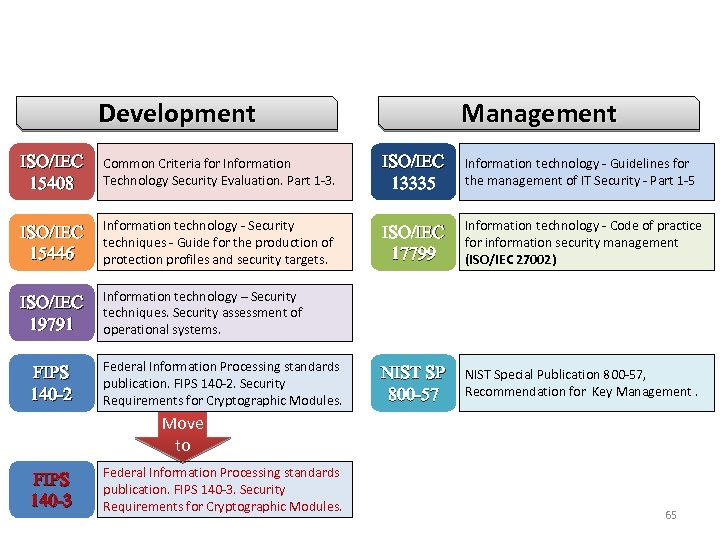 International Standards Development Management ISO/IEC 15408 Common Criteria for Information Technology Security Evaluation. Part 1 -3. ISO/IEC 13335 Information technology - Guidelines for the management of IT Security - Part 1 -5 ISO/IEC 15446 Information technology - Security techniques - Guide for the production of protection profiles and security targets. ISO/IEC 17799 Information technology - Code of practice for information security management (ISO/IEC 27002) ISO/IEC 19791 Information technology – Security techniques. Security assessment of operational systems. NIST SP 800 -57 NIST Special Publication 800 -57, Recommendation for Key Management. FIPS 140 -2 Federal Information Processing standards publication. FIPS 140 -2. Security Requirements for Cryptographic Modules. Move to FIPS 140 -3 Federal Information Processing standards publication. FIPS 140 -3. Security Requirements for Cryptographic Modules. 65
International Standards Development Management ISO/IEC 15408 Common Criteria for Information Technology Security Evaluation. Part 1 -3. ISO/IEC 13335 Information technology - Guidelines for the management of IT Security - Part 1 -5 ISO/IEC 15446 Information technology - Security techniques - Guide for the production of protection profiles and security targets. ISO/IEC 17799 Information technology - Code of practice for information security management (ISO/IEC 27002) ISO/IEC 19791 Information technology – Security techniques. Security assessment of operational systems. NIST SP 800 -57 NIST Special Publication 800 -57, Recommendation for Key Management. FIPS 140 -2 Federal Information Processing standards publication. FIPS 140 -2. Security Requirements for Cryptographic Modules. Move to FIPS 140 -3 Federal Information Processing standards publication. FIPS 140 -3. Security Requirements for Cryptographic Modules. 65
 International Standards We are focus on X. 800 security services 66
International Standards We are focus on X. 800 security services 66
 X. 800 Services • X. 800 defines a security service as a service provided by a protocol layer of communicating open systems, which ensures adequate security of the systems or of data transfers. • A clearer definition is found in RFC 2828, which provides the following definition: – a processing or communication service that is provided by a system to give a specific kind of protection to system resources; – security services implement security policies and are implemented by security mechanisms. 67
X. 800 Services • X. 800 defines a security service as a service provided by a protocol layer of communicating open systems, which ensures adequate security of the systems or of data transfers. • A clearer definition is found in RFC 2828, which provides the following definition: – a processing or communication service that is provided by a system to give a specific kind of protection to system resources; – security services implement security policies and are implemented by security mechanisms. 67
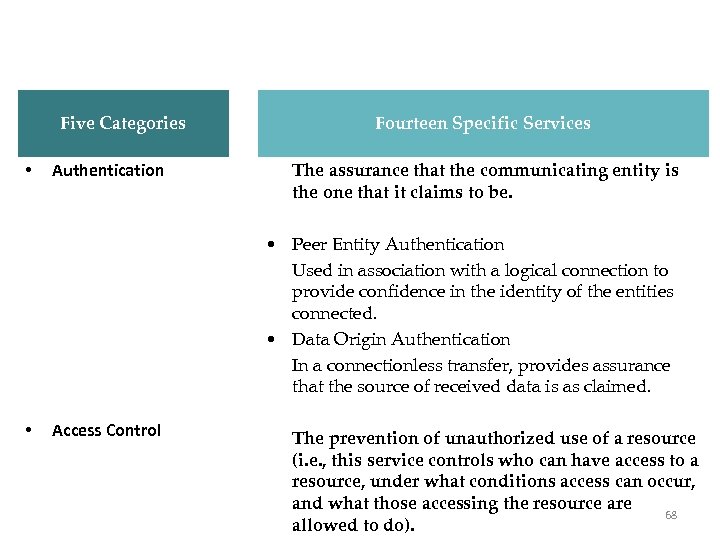 X. 800 Services Five Categories • Authentication Fourteen Specific Services The assurance that the communicating entity is the one that it claims to be. • Peer Entity Authentication Used in association with a logical connection to provide confidence in the identity of the entities connected. • Data Origin Authentication In a connectionless transfer, provides assurance that the source of received data is as claimed. • Access Control The prevention of unauthorized use of a resource (i. e. , this service controls who can have access to a resource, under what conditions access can occur, and what those accessing the resource are 68 allowed to do).
X. 800 Services Five Categories • Authentication Fourteen Specific Services The assurance that the communicating entity is the one that it claims to be. • Peer Entity Authentication Used in association with a logical connection to provide confidence in the identity of the entities connected. • Data Origin Authentication In a connectionless transfer, provides assurance that the source of received data is as claimed. • Access Control The prevention of unauthorized use of a resource (i. e. , this service controls who can have access to a resource, under what conditions access can occur, and what those accessing the resource are 68 allowed to do).
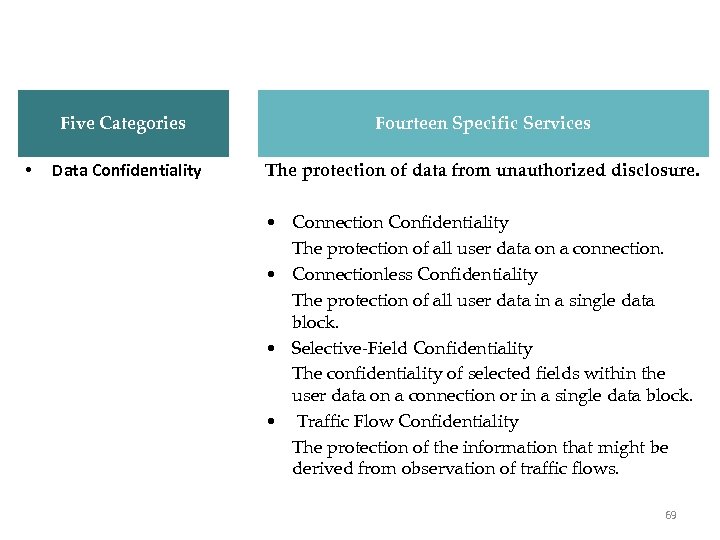 X. 800 Services Five Categories • Fourteen Specific Services Data Confidentiality The protection of data from unauthorized disclosure. • Connection Confidentiality The protection of all user data on a connection. • Connectionless Confidentiality The protection of all user data in a single data block. • Selective-Field Confidentiality The confidentiality of selected fields within the user data on a connection or in a single data block. • Traffic Flow Confidentiality The protection of the information that might be derived from observation of traffic flows. 69
X. 800 Services Five Categories • Fourteen Specific Services Data Confidentiality The protection of data from unauthorized disclosure. • Connection Confidentiality The protection of all user data on a connection. • Connectionless Confidentiality The protection of all user data in a single data block. • Selective-Field Confidentiality The confidentiality of selected fields within the user data on a connection or in a single data block. • Traffic Flow Confidentiality The protection of the information that might be derived from observation of traffic flows. 69
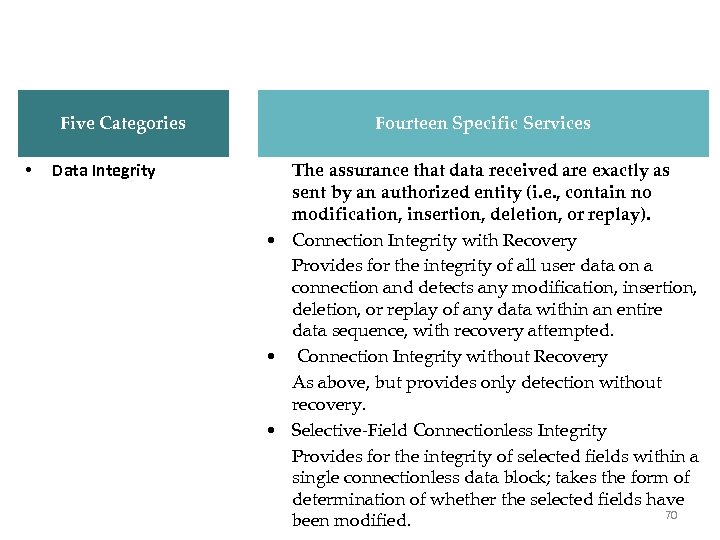 X. 800 Services Five Categories • Data Integrity Fourteen Specific Services The assurance that data received are exactly as sent by an authorized entity (i. e. , contain no modification, insertion, deletion, or replay). • Connection Integrity with Recovery Provides for the integrity of all user data on a connection and detects any modification, insertion, deletion, or replay of any data within an entire data sequence, with recovery attempted. • Connection Integrity without Recovery As above, but provides only detection without recovery. • Selective-Field Connectionless Integrity Provides for the integrity of selected fields within a single connectionless data block; takes the form of determination of whether the selected fields have 70 been modified.
X. 800 Services Five Categories • Data Integrity Fourteen Specific Services The assurance that data received are exactly as sent by an authorized entity (i. e. , contain no modification, insertion, deletion, or replay). • Connection Integrity with Recovery Provides for the integrity of all user data on a connection and detects any modification, insertion, deletion, or replay of any data within an entire data sequence, with recovery attempted. • Connection Integrity without Recovery As above, but provides only detection without recovery. • Selective-Field Connectionless Integrity Provides for the integrity of selected fields within a single connectionless data block; takes the form of determination of whether the selected fields have 70 been modified.
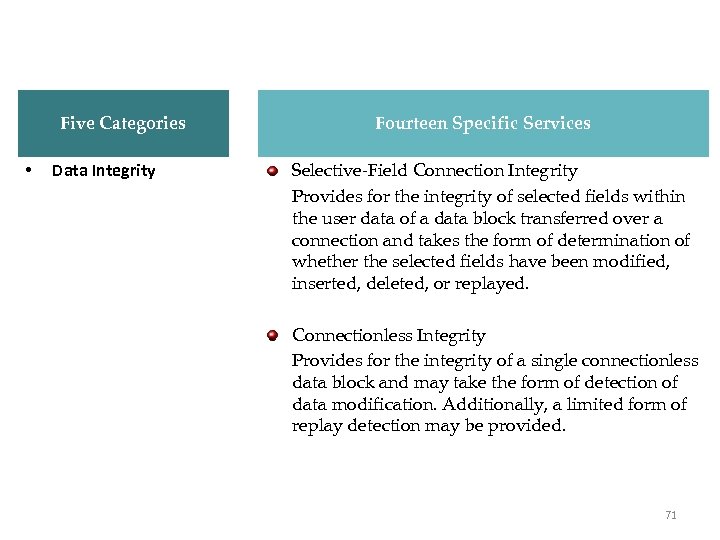 X. 800 Services Five Categories • Data Integrity Fourteen Specific Services Selective-Field Connection Integrity Provides for the integrity of selected fields within the user data of a data block transferred over a connection and takes the form of determination of whether the selected fields have been modified, inserted, deleted, or replayed. Connectionless Integrity Provides for the integrity of a single connectionless data block and may take the form of detection of data modification. Additionally, a limited form of replay detection may be provided. 71
X. 800 Services Five Categories • Data Integrity Fourteen Specific Services Selective-Field Connection Integrity Provides for the integrity of selected fields within the user data of a data block transferred over a connection and takes the form of determination of whether the selected fields have been modified, inserted, deleted, or replayed. Connectionless Integrity Provides for the integrity of a single connectionless data block and may take the form of detection of data modification. Additionally, a limited form of replay detection may be provided. 71
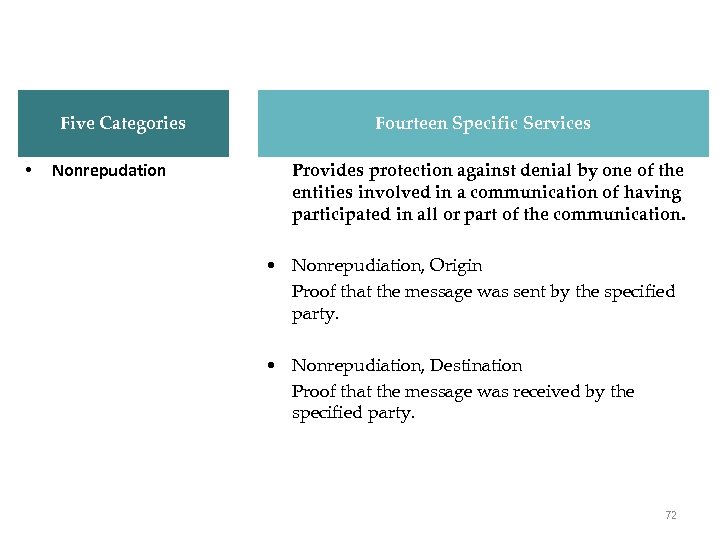 X. 800 Services Five Categories • Nonrepudation Fourteen Specific Services Provides protection against denial by one of the entities involved in a communication of having participated in all or part of the communication. • Nonrepudiation, Origin Proof that the message was sent by the specified party. • Nonrepudiation, Destination Proof that the message was received by the specified party. 72
X. 800 Services Five Categories • Nonrepudation Fourteen Specific Services Provides protection against denial by one of the entities involved in a communication of having participated in all or part of the communication. • Nonrepudiation, Origin Proof that the message was sent by the specified party. • Nonrepudiation, Destination Proof that the message was received by the specified party. 72
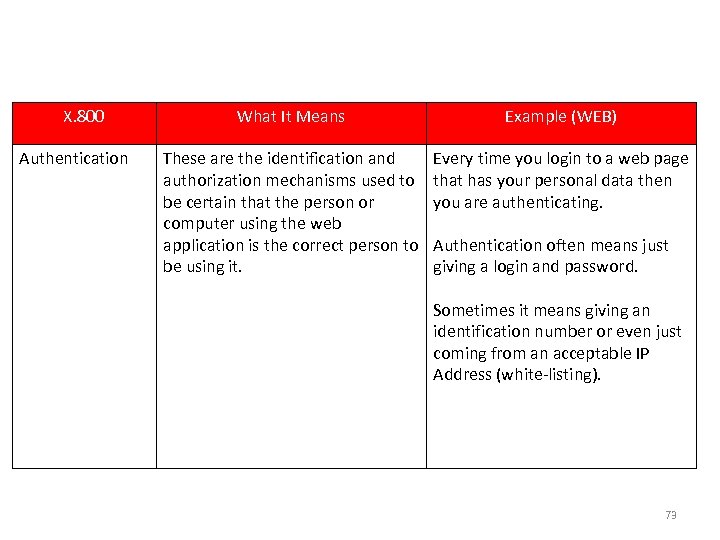 Example : Goal & Setting X. 800 Authentication What It Means Example (WEB) These are the identification and authorization mechanisms used to be certain that the person or computer using the web application is the correct person to be using it. Every time you login to a web page that has your personal data then you are authenticating. Authentication often means just giving a login and password. Sometimes it means giving an identification number or even just coming from an acceptable IP Address (white-listing). 73
Example : Goal & Setting X. 800 Authentication What It Means Example (WEB) These are the identification and authorization mechanisms used to be certain that the person or computer using the web application is the correct person to be using it. Every time you login to a web page that has your personal data then you are authenticating. Authentication often means just giving a login and password. Sometimes it means giving an identification number or even just coming from an acceptable IP Address (white-listing). 73
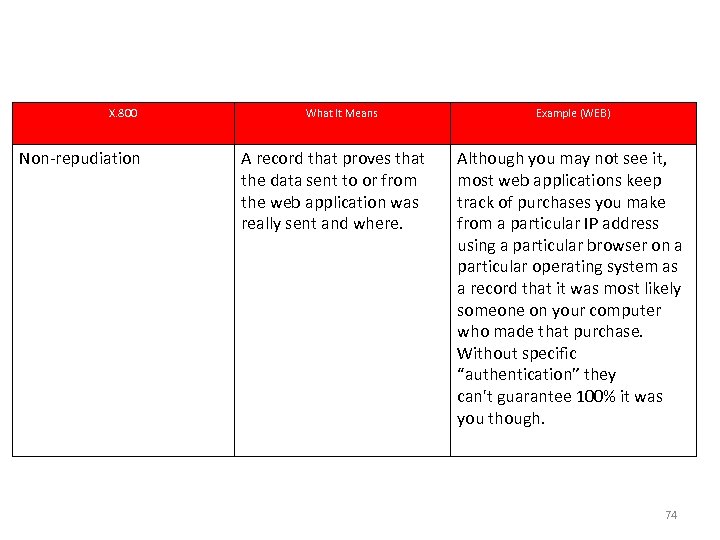 Example : Goal & Setting X. 800 Non-repudiation What It Means A record that proves that the data sent to or from the web application was really sent and where. Example (WEB) Although you may not see it, most web applications keep track of purchases you make from a particular IP address using a particular browser on a particular operating system as a record that it was most likely someone on your computer who made that purchase. Without specific “authentication” they can't guarantee 100% it was you though. 74
Example : Goal & Setting X. 800 Non-repudiation What It Means A record that proves that the data sent to or from the web application was really sent and where. Example (WEB) Although you may not see it, most web applications keep track of purchases you make from a particular IP address using a particular browser on a particular operating system as a record that it was most likely someone on your computer who made that purchase. Without specific “authentication” they can't guarantee 100% it was you though. 74
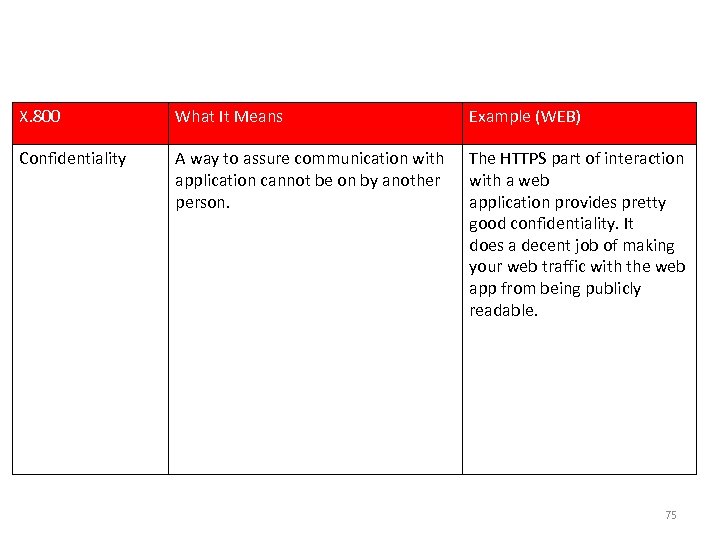 Example : Goal & Setting X. 800 What It Means Example (WEB) Confidentiality A way to assure communication with application cannot be on by another person. The HTTPS part of interaction with a web application provides pretty good confidentiality. It does a decent job of making your web traffic with the web app from being publicly readable. 75
Example : Goal & Setting X. 800 What It Means Example (WEB) Confidentiality A way to assure communication with application cannot be on by another person. The HTTPS part of interaction with a web application provides pretty good confidentiality. It does a decent job of making your web traffic with the web app from being publicly readable. 75


