Lec_1_Security_class.pptx
- Количество слайдов: 40
 Week 1 Information Security and Data protection Altayeva Aigerim aigerim. muit@gmail. com
Week 1 Information Security and Data protection Altayeva Aigerim aigerim. muit@gmail. com
 Introduction The basic elements of cryptography Avoid mathematical rigor as much as possible Attempt to provide enough of the details: not only understand the “what” but can also appreciate the “why. ”
Introduction The basic elements of cryptography Avoid mathematical rigor as much as possible Attempt to provide enough of the details: not only understand the “what” but can also appreciate the “why. ”
 Content 1. How to Speak Crypto 2. The OSI Security Architecture Security attack Security mechanism Security service 3. Security Attacks Passive Attacks Active Attacks 4. Security Services 5. Simple Substitution Cipher(Caesar Cipher)
Content 1. How to Speak Crypto 2. The OSI Security Architecture Security attack Security mechanism Security service 3. Security Attacks Passive Attacks Active Attacks 4. Security Services 5. Simple Substitution Cipher(Caesar Cipher)
 1. How to Speak Crypto The basic terminology of crypto includes the following. Cryptology is the art and science of making and breaking “secret codes. ” Cryptography is the making of “secret codes. ” Cryptanalysis is the breaking of “secret codes. ” Crypto is a synonym for any or all of the above (and more). The precise meaning should be clear from context.
1. How to Speak Crypto The basic terminology of crypto includes the following. Cryptology is the art and science of making and breaking “secret codes. ” Cryptography is the making of “secret codes. ” Cryptanalysis is the breaking of “secret codes. ” Crypto is a synonym for any or all of the above (and more). The precise meaning should be clear from context.
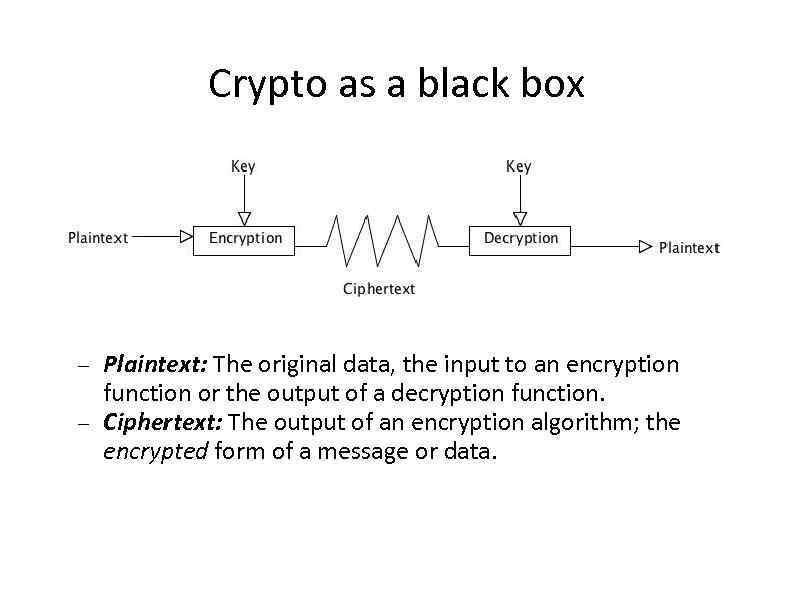 Crypto as a black box Plaintext: The original data, the input to an encryption function or the output of a decryption function. Ciphertext: The output of an encryption algorithm; the encrypted form of a message or data.
Crypto as a black box Plaintext: The original data, the input to an encryption function or the output of a decryption function. Ciphertext: The output of an encryption algorithm; the encrypted form of a message or data.
 Definitions • Computer Security - generic name for the collection of tools designed to protect data and to thwart hackers • Network Security - measures to protect data during their transmission • Internet Security - measures to protect data during their transmission over a collection of interconnected networks
Definitions • Computer Security - generic name for the collection of tools designed to protect data and to thwart hackers • Network Security - measures to protect data during their transmission • Internet Security - measures to protect data during their transmission over a collection of interconnected networks
 Aim of Course • our focus is on General Security which consists of all above definitions
Aim of Course • our focus is on General Security which consists of all above definitions
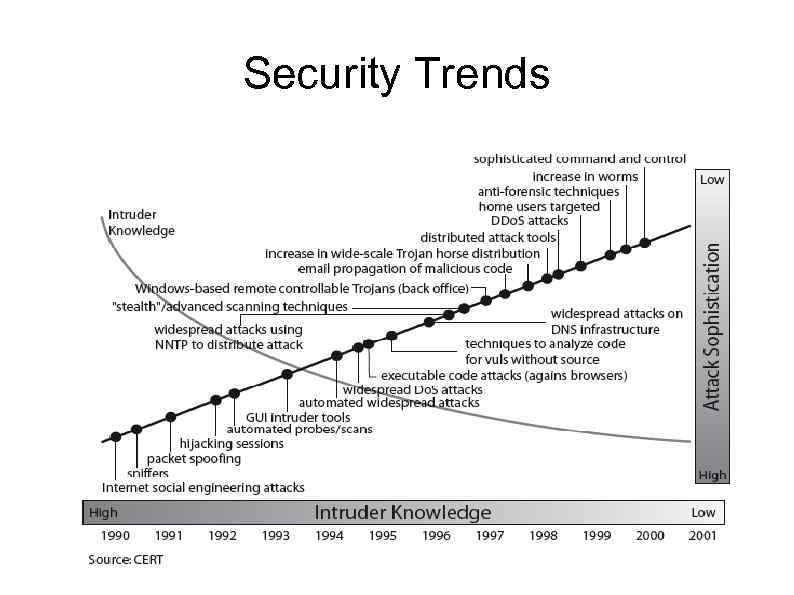 Security Trends
Security Trends
 Cipher: An algorithm for encryption and decryption. A cipher replaces a piece of information (an element in plaintext) with another object, with the intent to conceal meaning. Encryption: The conversion of plaintext or data into unintelligible form by means of a reversible translation, based on a translation table or algorithm. Also called enciphering. Decryption: The translation of encrypted text or data into original text or data. Also called deciphering.
Cipher: An algorithm for encryption and decryption. A cipher replaces a piece of information (an element in plaintext) with another object, with the intent to conceal meaning. Encryption: The conversion of plaintext or data into unintelligible form by means of a reversible translation, based on a translation table or algorithm. Also called enciphering. Decryption: The translation of encrypted text or data into original text or data. Also called deciphering.
 2. OSI Security Architecture • ITU-T X. 800 “Security Architecture for OSI” • defines a systematic way of defining and providing security requirements
2. OSI Security Architecture • ITU-T X. 800 “Security Architecture for OSI” • defines a systematic way of defining and providing security requirements
 The OSI Security Architecture Security attack: Any action that compromises the security of information owned by an organization. Security mechanism: A process (or a device incorporating such a process) that is designed to detect, prevent, or recover from a security attack. Security service: A processing or communication service that enhances the security of the data processing systems and the information transfers of an organization. The services are intended to counter security attacks, and they make use of one or more security mechanisms to provide the service.
The OSI Security Architecture Security attack: Any action that compromises the security of information owned by an organization. Security mechanism: A process (or a device incorporating such a process) that is designed to detect, prevent, or recover from a security attack. Security service: A processing or communication service that enhances the security of the data processing systems and the information transfers of an organization. The services are intended to counter security attacks, and they make use of one or more security mechanisms to provide the service.
 Definitions taken from RFC 2828, Internet Security Glossary. Threat: A potential for violation of security, which exists when there is a circumstance, capability, action, or event that could breach security and cause harm. That is, a threat is a possible danger that might exploit a vulnerability. Attack: An assault on system security that derives from an intelligent threat; that is, an intelligent act that is a deliberate attempt (especially in the sense of a method or technique) to evade security services and violate the security policy of a system.
Definitions taken from RFC 2828, Internet Security Glossary. Threat: A potential for violation of security, which exists when there is a circumstance, capability, action, or event that could breach security and cause harm. That is, a threat is a possible danger that might exploit a vulnerability. Attack: An assault on system security that derives from an intelligent threat; that is, an intelligent act that is a deliberate attempt (especially in the sense of a method or technique) to evade security services and violate the security policy of a system.
 3. Security Attacks A passive attack attempts to learn or make use of information from the system but does not affect system resources. An active attack attempts to alter system resources or affect their operation.
3. Security Attacks A passive attack attempts to learn or make use of information from the system but does not affect system resources. An active attack attempts to alter system resources or affect their operation.
 Passive Attack Passive attacks are eavesdropping on, or monitoring of, transmissions. The goal of the opponent is to obtain information that is being transmitted. Two types of passive attacks are : release of message contents traffic analysis.
Passive Attack Passive attacks are eavesdropping on, or monitoring of, transmissions. The goal of the opponent is to obtain information that is being transmitted. Two types of passive attacks are : release of message contents traffic analysis.
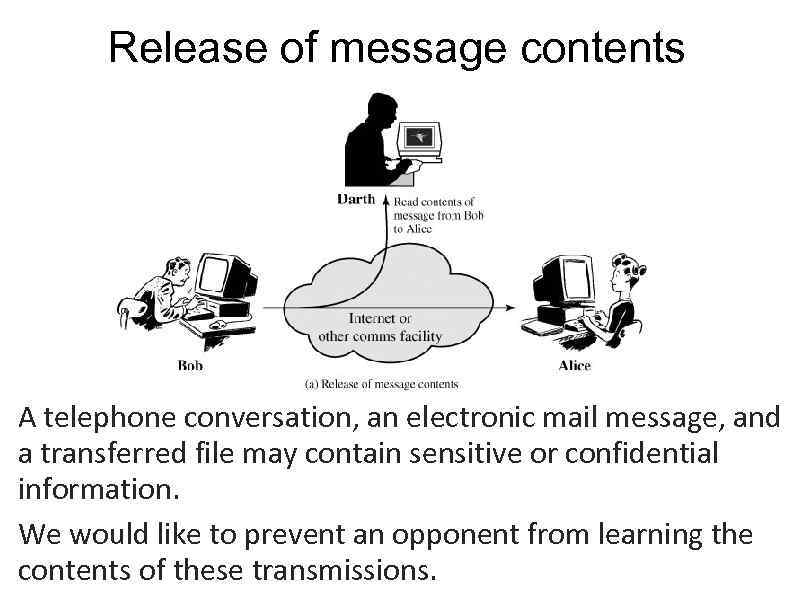 Release of message contents A telephone conversation, an electronic mail message, and a transferred file may contain sensitive or confidential information. We would like to prevent an opponent from learning the contents of these transmissions.
Release of message contents A telephone conversation, an electronic mail message, and a transferred file may contain sensitive or confidential information. We would like to prevent an opponent from learning the contents of these transmissions.
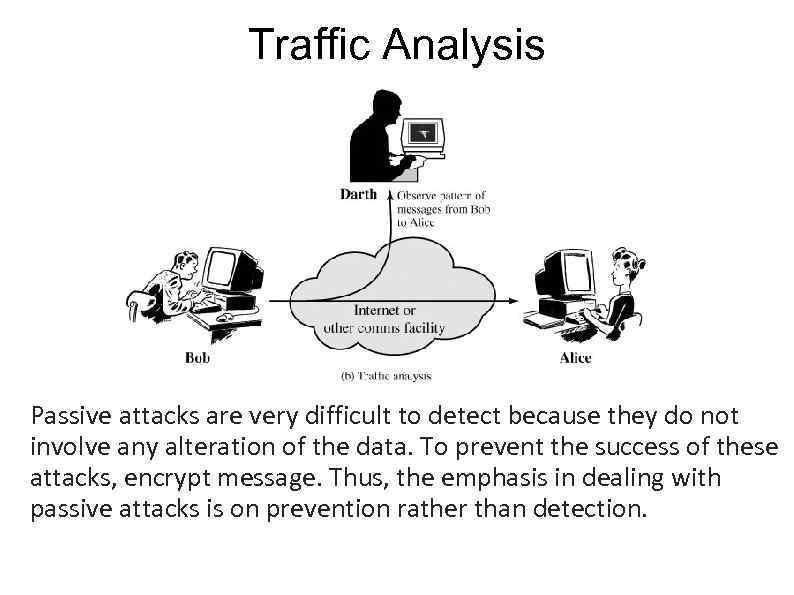 Traffic Analysis Passive attacks are very difficult to detect because they do not involve any alteration of the data. To prevent the success of these attacks, encrypt message. Thus, the emphasis in dealing with passive attacks is on prevention rather than detection.
Traffic Analysis Passive attacks are very difficult to detect because they do not involve any alteration of the data. To prevent the success of these attacks, encrypt message. Thus, the emphasis in dealing with passive attacks is on prevention rather than detection.
 Active Attacks Involve some modification of the data stream or the creation of a false stream and can be subdivided into four categories: Masquerade Replay Modification of messages Denial of service
Active Attacks Involve some modification of the data stream or the creation of a false stream and can be subdivided into four categories: Masquerade Replay Modification of messages Denial of service
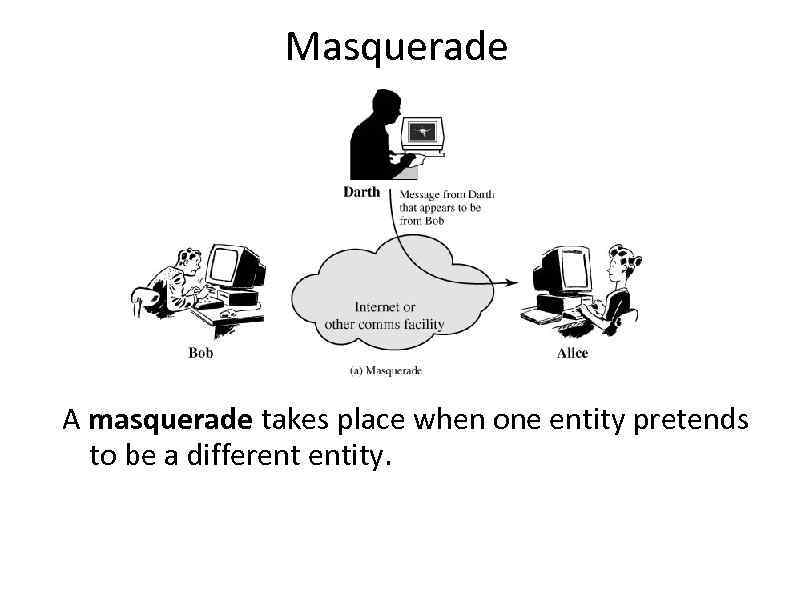 Masquerade A masquerade takes place when one entity pretends to be a different entity.
Masquerade A masquerade takes place when one entity pretends to be a different entity.
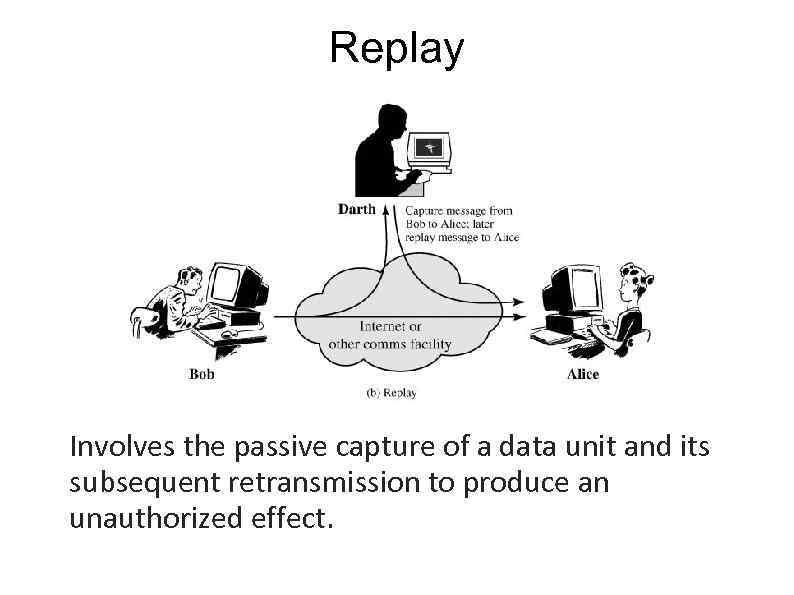 Replay Involves the passive capture of a data unit and its subsequent retransmission to produce an unauthorized effect.
Replay Involves the passive capture of a data unit and its subsequent retransmission to produce an unauthorized effect.
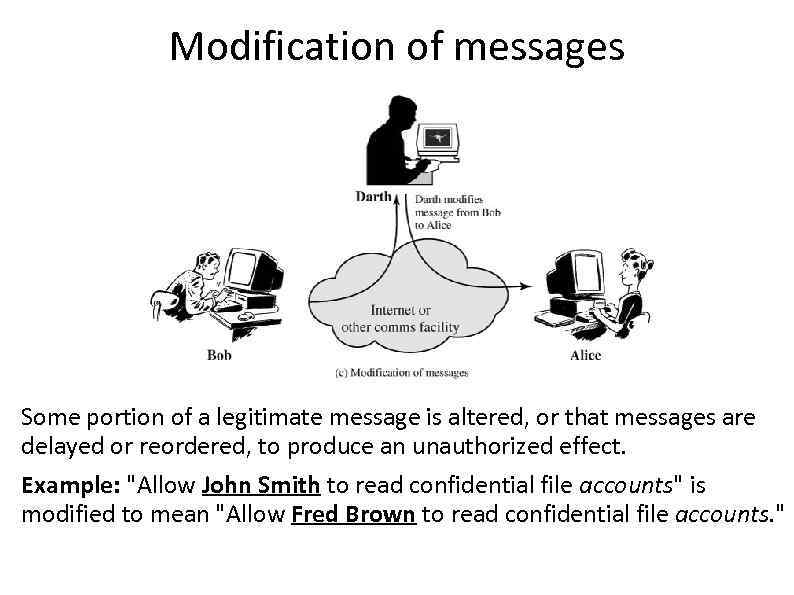 Modification of messages Some portion of a legitimate message is altered, or that messages are delayed or reordered, to produce an unauthorized effect. Example: "Allow John Smith to read confidential file accounts" is modified to mean "Allow Fred Brown to read confidential file accounts. "
Modification of messages Some portion of a legitimate message is altered, or that messages are delayed or reordered, to produce an unauthorized effect. Example: "Allow John Smith to read confidential file accounts" is modified to mean "Allow Fred Brown to read confidential file accounts. "
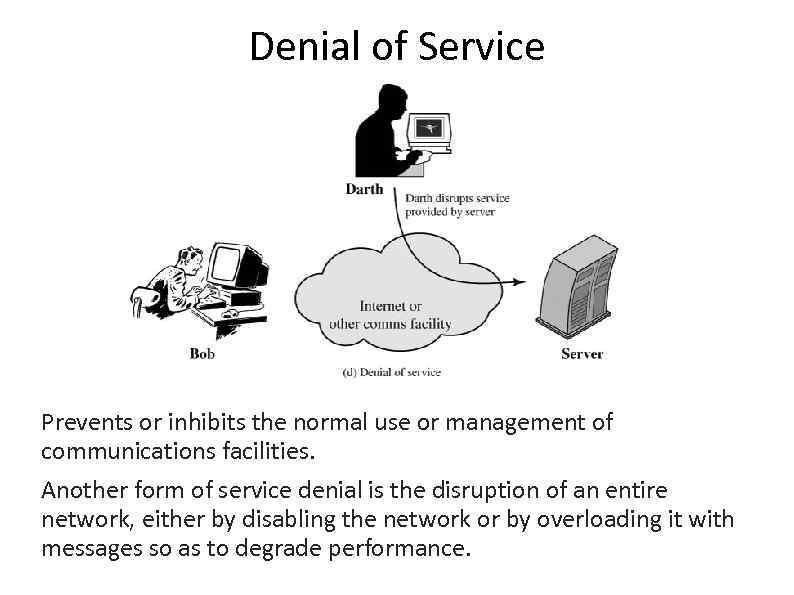 Denial of Service Prevents or inhibits the normal use or management of communications facilities. Another form of service denial is the disruption of an entire network, either by disabling the network or by overloading it with messages so as to degrade performance.
Denial of Service Prevents or inhibits the normal use or management of communications facilities. Another form of service denial is the disruption of an entire network, either by disabling the network or by overloading it with messages so as to degrade performance.
 4. Security Service – enhance security of data processing systems and information transfers of an organization – intended to counter security attacks – using one or more security mechanisms – often replicates functions normally associated with physical documents • which, for example, have signatures, dates; need protection from disclosure, tampering, or destruction; be notarized or witnessed; be recorded or licensed
4. Security Service – enhance security of data processing systems and information transfers of an organization – intended to counter security attacks – using one or more security mechanisms – often replicates functions normally associated with physical documents • which, for example, have signatures, dates; need protection from disclosure, tampering, or destruction; be notarized or witnessed; be recorded or licensed
 Security Service 1. Privacy or confidentiality: keeping information secret from all but those who are authorised to see it. 2. Data integrity: ensuring information has not been altered by unauthorised or unknown means. 3. Entity authentication or identification: identifying and acknowledging the identity of entity (a person, a computer terminal, a credit card, etc. ). 4. Message authentication: corroborating the source of information; also known as data origin authentication.
Security Service 1. Privacy or confidentiality: keeping information secret from all but those who are authorised to see it. 2. Data integrity: ensuring information has not been altered by unauthorised or unknown means. 3. Entity authentication or identification: identifying and acknowledging the identity of entity (a person, a computer terminal, a credit card, etc. ). 4. Message authentication: corroborating the source of information; also known as data origin authentication.
 5. Signature: a means to bind information to an entity. 6. Authorisation: conveyance, to another entity, of official sanction to do or be something. 7. Validation: a means to provide timeliness of authorisation to use or manipulate information or resources. 8. Access control: restricting access to resources to privileged entities. 9. Certification: endorsement of information by a trusted entity. 10. Timestamping: recording the time of creation or existence of information.
5. Signature: a means to bind information to an entity. 6. Authorisation: conveyance, to another entity, of official sanction to do or be something. 7. Validation: a means to provide timeliness of authorisation to use or manipulate information or resources. 8. Access control: restricting access to resources to privileged entities. 9. Certification: endorsement of information by a trusted entity. 10. Timestamping: recording the time of creation or existence of information.
 11. Witnessing: verifying the creation or existence of information by an entity other than the creator. 12. Receipt: acknowledgement that information has been received. 13. Confirmation: acknowledgement that services have been provided. 14. Ownership: a means to provide an entity with the legal right to use or transfer a resource to others. 15. Anonymity: concealing the identity of an entity involved in some process. 16. Non-repudiation: preventing the denial of previous commitments or actions. 17. Revocation: retraction of certification or authorisation.
11. Witnessing: verifying the creation or existence of information by an entity other than the creator. 12. Receipt: acknowledgement that information has been received. 13. Confirmation: acknowledgement that services have been provided. 14. Ownership: a means to provide an entity with the legal right to use or transfer a resource to others. 15. Anonymity: concealing the identity of an entity involved in some process. 16. Non-repudiation: preventing the denial of previous commitments or actions. 17. Revocation: retraction of certification or authorisation.
 Security Services • X. 800: “a service provided by a protocol layer of communicating open systems, which ensures adequate security of the systems or of data transfers” • RFC 2828: “a processing or communication service provided by a system to give a specific kind of protection to system resources”
Security Services • X. 800: “a service provided by a protocol layer of communicating open systems, which ensures adequate security of the systems or of data transfers” • RFC 2828: “a processing or communication service provided by a system to give a specific kind of protection to system resources”
 Security Mechanism • feature designed to detect, prevent, or recover from a security attack • no single mechanism that will support all services required • however one particular element underlies many of the security mechanisms in use: – cryptographic techniques • hence our focus on this topic
Security Mechanism • feature designed to detect, prevent, or recover from a security attack • no single mechanism that will support all services required • however one particular element underlies many of the security mechanisms in use: – cryptographic techniques • hence our focus on this topic
 Security Mechanisms (X. 800) • specific security mechanisms: – encipherment, digital signatures, access controls, data integrity, authentication exchange, traffic padding, routing control, notarization • pervasive security mechanisms: – trusted functionality, security labels, event detection, security audit trails, security recovery
Security Mechanisms (X. 800) • specific security mechanisms: – encipherment, digital signatures, access controls, data integrity, authentication exchange, traffic padding, routing control, notarization • pervasive security mechanisms: – trusted functionality, security labels, event detection, security audit trails, security recovery
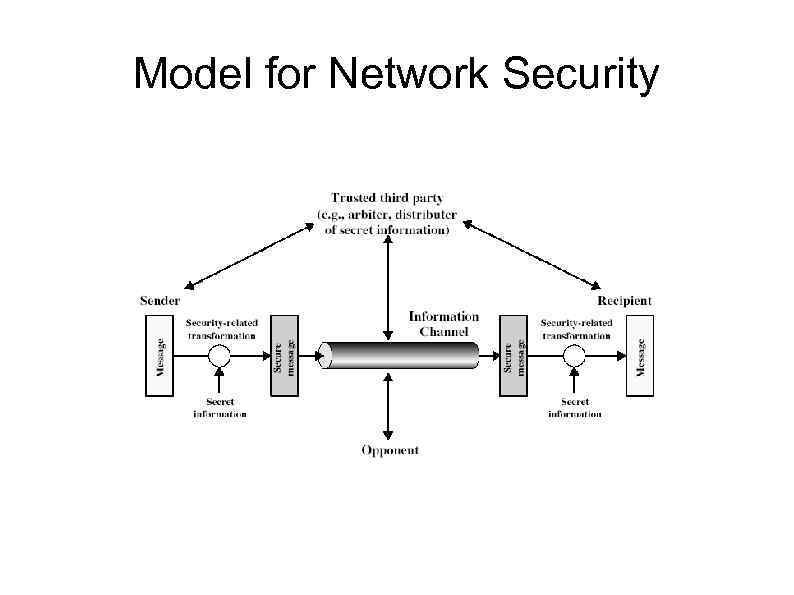 Model for Network Security
Model for Network Security
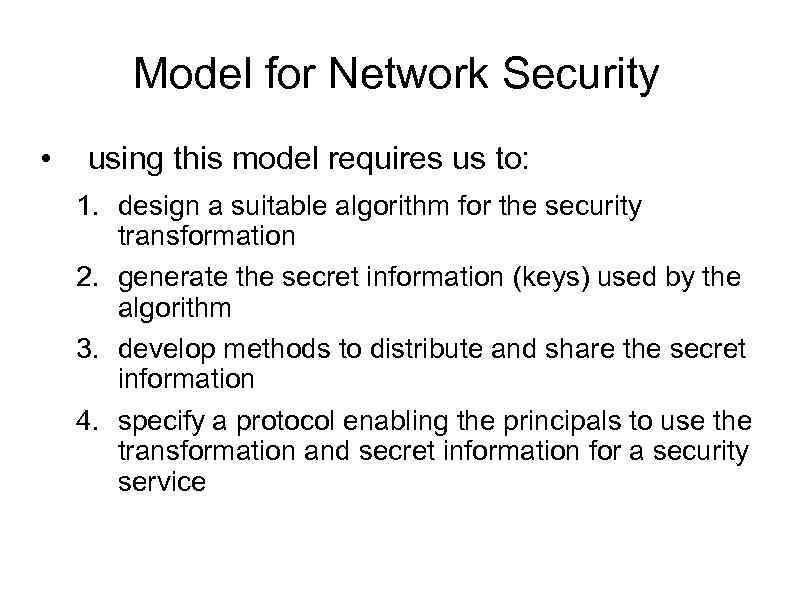 Model for Network Security • using this model requires us to: 1. design a suitable algorithm for the security transformation 2. generate the secret information (keys) used by the algorithm 3. develop methods to distribute and share the secret information 4. specify a protocol enabling the principals to use the transformation and secret information for a security service
Model for Network Security • using this model requires us to: 1. design a suitable algorithm for the security transformation 2. generate the secret information (keys) used by the algorithm 3. develop methods to distribute and share the secret information 4. specify a protocol enabling the principals to use the transformation and secret information for a security service
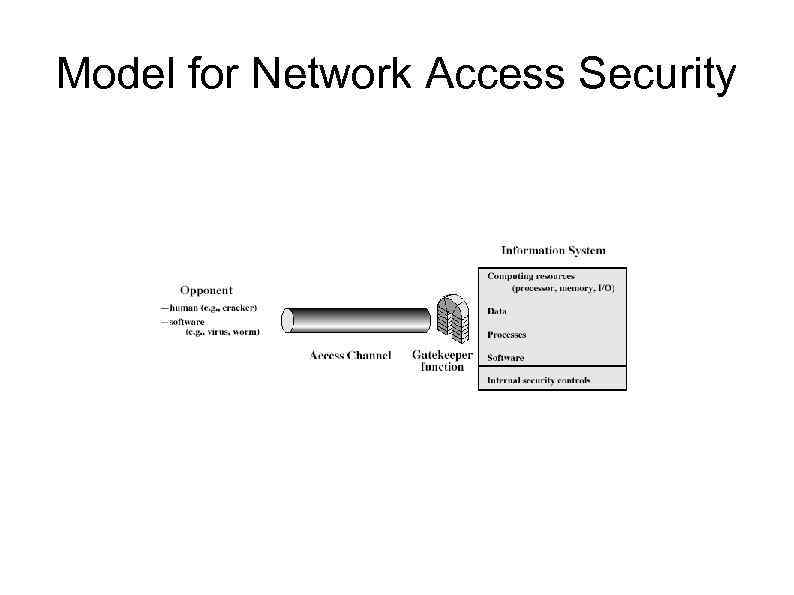 Model for Network Access Security
Model for Network Access Security
 Model for Network Access Security • using this model requires us to: 1. select appropriate gatekeeper functions to identify users 2. implement security controls to ensure only authorised users access designated information or resources • trusted computer systems may be useful to help implement this model
Model for Network Access Security • using this model requires us to: 1. select appropriate gatekeeper functions to identify users 2. implement security controls to ensure only authorised users access designated information or resources • trusted computer systems may be useful to help implement this model
 5. CLASSIC CRYPTO The simple substitution: one of the oldest cipher systems (dating back at least 2, 000 years) one that is ideal for illustrating basic attacks the message is encrypted by substituting the letter of the alphabet n places ahead of the current letter.
5. CLASSIC CRYPTO The simple substitution: one of the oldest cipher systems (dating back at least 2, 000 years) one that is ideal for illustrating basic attacks the message is encrypted by substituting the letter of the alphabet n places ahead of the current letter.
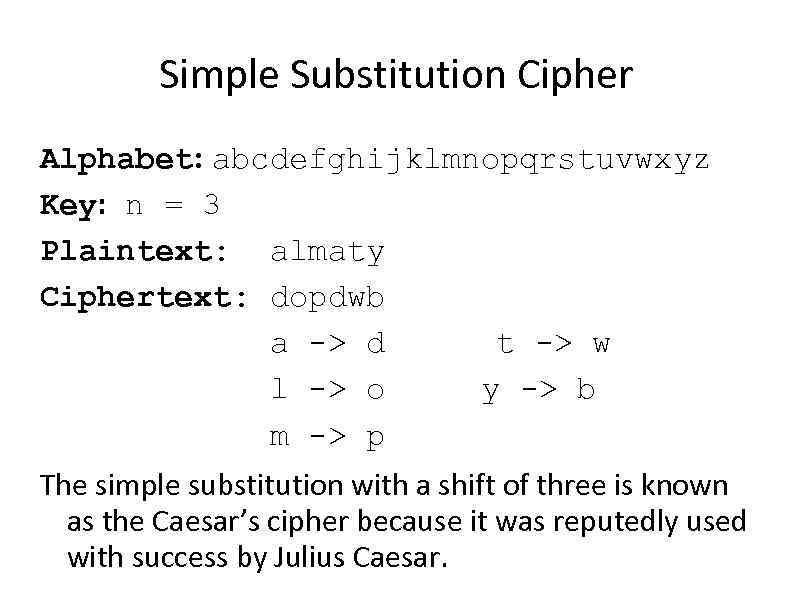 Simple Substitution Cipher Alphabet: abcdefghijklmnopqrstuvwxyz Key: n = 3 Plaintext: almaty Ciphertext: dopdwb a -> d t -> w l -> o y -> b m -> p The simple substitution with a shift of three is known as the Caesar’s cipher because it was reputedly used with success by Julius Caesar.
Simple Substitution Cipher Alphabet: abcdefghijklmnopqrstuvwxyz Key: n = 3 Plaintext: almaty Ciphertext: dopdwb a -> d t -> w l -> o y -> b m -> p The simple substitution with a shift of three is known as the Caesar’s cipher because it was reputedly used with success by Julius Caesar.
 Weaknesses of Caesar cipher If we limit the simple substitution to shifts, then the possible keys are N ∈ {0, 1, 2, . . . , 25}. If the message really was encrypted via a shift by n, Trudy can expect to find the true plaintext —and thereby recover the key — after 13 tries, on average.
Weaknesses of Caesar cipher If we limit the simple substitution to shifts, then the possible keys are N ∈ {0, 1, 2, . . . , 25}. If the message really was encrypted via a shift by n, Trudy can expect to find the true plaintext —and thereby recover the key — after 13 tries, on average.
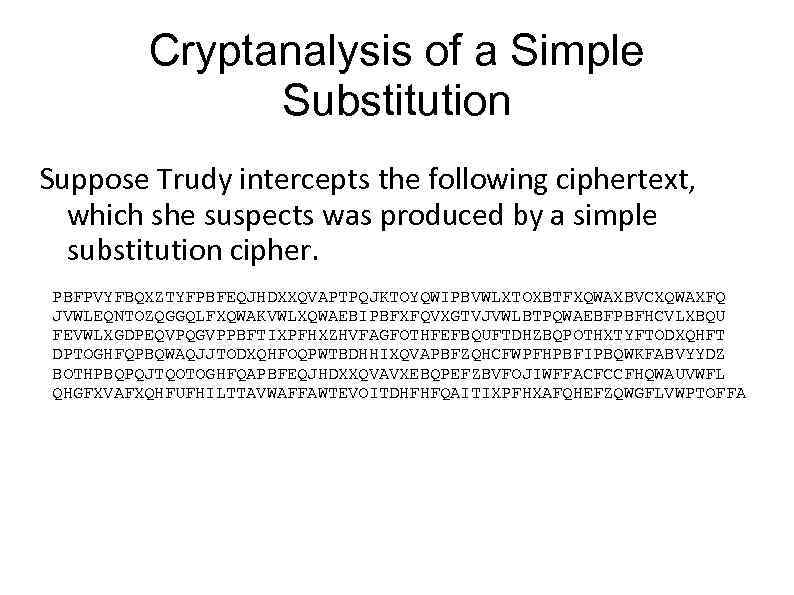 Cryptanalysis of a Simple Substitution Suppose Trudy intercepts the following ciphertext, which she suspects was produced by a simple substitution cipher. PBFPVYFBQXZTYFPBFEQJHDXXQVAPTPQJKTOYQWIPBVWLXTOXBTFXQWAXBVCXQWAXFQ JVWLEQNTOZQGGQLFXQWAKVWLXQWAEBIPBFXFQVXGTVJVWLBTPQWAEBFPBFHCVLXBQU FEVWLXGDPEQVPQGVPPBFTIXPFHXZHVFAGFOTHFEFBQUFTDHZBQPOTHXTYFTODXQHFT DPTOGHFQPBQWAQJJTODXQHFOQPWTBDHHIXQVAPBFZQHCFWPFHPBFIPBQWKFABVYYDZ BOTHPBQPQJTQOTOGHFQAPBFEQJHDXXQVAVXEBQPEFZBVFOJIWFFACFCCFHQWAUVWFL QHGFXVAFXQHFUFHILTTAVWAFFAWTEVOITDHFHFQAITIXPFHXAFQHEFZQWGFLVWPTOFFA
Cryptanalysis of a Simple Substitution Suppose Trudy intercepts the following ciphertext, which she suspects was produced by a simple substitution cipher. PBFPVYFBQXZTYFPBFEQJHDXXQVAPTPQJKTOYQWIPBVWLXTOXBTFXQWAXBVCXQWAXFQ JVWLEQNTOZQGGQLFXQWAKVWLXQWAEBIPBFXFQVXGTVJVWLBTPQWAEBFPBFHCVLXBQU FEVWLXGDPEQVPQGVPPBFTIXPFHXZHVFAGFOTHFEFBQUFTDHZBQPOTHXTYFTODXQHFT DPTOGHFQPBQWAQJJTODXQHFOQPWTBDHHIXQVAPBFZQHCFWPFHPBFIPBQWKFABVYYDZ BOTHPBQPQJTQOTOGHFQAPBFEQJHDXXQVAVXEBQPEFZBVFOJIWFFACFCCFHQWAUVWFL QHGFXVAFXQHFUFHILTTAVWAFFAWTEVOITDHFHFQAITIXPFHXAFQHEFZQWGFLVWPTOFFA
 Assuming the underlying message is English, Trudy can make use of the English letter frequency counts in Figure 2. 2 together with the frequency counts for the ciphertext, which appear in Figure 2. 3. Figure 2. 2
Assuming the underlying message is English, Trudy can make use of the English letter frequency counts in Figure 2. 2 together with the frequency counts for the ciphertext, which appear in Figure 2. 3. Figure 2. 2
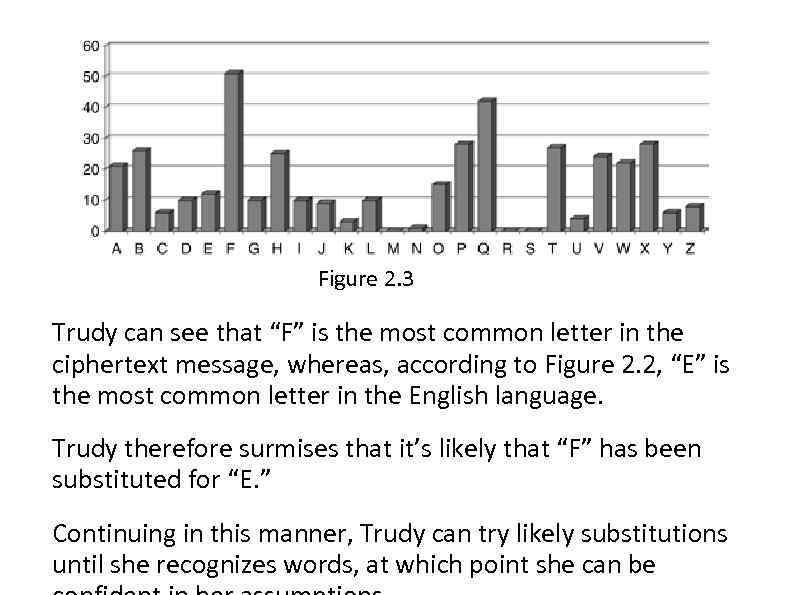 Figure 2. 3 Trudy can see that “F” is the most common letter in the ciphertext message, whereas, according to Figure 2. 2, “E” is the most common letter in the English language. Trudy therefore surmises that it’s likely that “F” has been substituted for “E. ” Continuing in this manner, Trudy can try likely substitutions until she recognizes words, at which point she can be
Figure 2. 3 Trudy can see that “F” is the most common letter in the ciphertext message, whereas, according to Figure 2. 2, “E” is the most common letter in the English language. Trudy therefore surmises that it’s likely that “F” has been substituted for “E. ” Continuing in this manner, Trudy can try likely substitutions until she recognizes words, at which point she can be
 References 1. Information Security Principles and Practice, Mark Stamp Chapter 2, Crypto Basics 2. Cryptography and Network Security Principles and Practices, Fourth Edition, William Stallings Chapter 1. Introduction Chapter 2. Classical Encryption Techniques 2. 1. Symmetric Cipher Model 2. 2. Substitution Techniques
References 1. Information Security Principles and Practice, Mark Stamp Chapter 2, Crypto Basics 2. Cryptography and Network Security Principles and Practices, Fourth Edition, William Stallings Chapter 1. Introduction Chapter 2. Classical Encryption Techniques 2. 1. Symmetric Cipher Model 2. 2. Substitution Techniques
 Thanks for you attention
Thanks for you attention


