846c2da0cbbdf2a4cf03a7143ea9959e.ppt
- Количество слайдов: 22

Web Tap: Intelligent Intrusion Detection Kevin Borders EECS 598 -2 Presentation

Overview • • Target Environment Threat Model Web Tap Design Results Future Work Conclusion Questions Demo EECS 598 -2 Presentation

Target Environment • High-security corporate or government network – Very concerned about information leaks and intruders – Mail server and (optionally) proxy server on network perimeter – Strict firewall settings • Only allow outgoing http traffic on port 80 from workstations • Or use proxy server and block all traffic EECS 598 -2 Presentation

Threat Model • A highly-skilled hacker compromises a vulnerable workstation – E-mail a link to a web page that exploits the browser – E-mail with a trojan in attachment – Hard to prevent due to multitude of browser vulnerabilities EECS 598 -2 Presentation

Threat Model (Part Two) • Hacker needs to communicate with the compromised machine – Traditional Trojans do not work (Back Orifice, etc. ) • Incoming TCP requests blocked – Only two paths available: E-mail and Web (http) – E-mail is risky • Logged • Rapid two-way communication from remote shell can be easily detected – Web is a better way of communicating with machine • Hard to detect • Significantly more bandwidth is available (Without being detected) EECS 598 -2 Presentation

Threat Model (Part Three) • Attacker places a custom Trojan Horse program on the machine – Trojan calls back to the hacker’s machine on port 80 (http) at predetermined times – Two-way communication follows in the form of web transactions – If proxy server is used, transactions must appear to be legitimate • Later on: Demo of callback Trojan through a proxy EECS 598 -2 Presentation
Web Tap Design • Web Tap is a Network-Based Anomaly Detection IDS • Why Network-Based? – Host-Based intrusion detection systems are easily disabled • Why Anomaly Detection? – Highly-skilled hackers use tools with unknown signatures EECS 598 -2 Presentation

Web Tap Design: Implementation • Web Tap implemented as proxy server extension – Records web requests from all users – Extracts important statistics – Builds profile of each user – Raises an alert when it detects non-human web browsing behavior • Note: Web Tap also detects spyware and adware in addition to Trojan Horse programs EECS 598 -2 Presentation
Web Tap Design: Statistics • Web Tap calculates statistics to characterize human web browsing patterns – Delay between requests for the same site – Size of requests (mean, variance, maximum) – Bandwidth usage (upload) per site per five minutes and per day for each user – Total bandwidth usage (upload) per user per five minutes and per day EECS 598 -2 Presentation

Experimental Setup • Statistics were collected from a proxy server with over 30 users (currently have 8 days of data available) – The population group consists of college students, faculty, friends and family members – Home computers with browser configured to use remote proxy server EECS 598 -2 Presentation

Results: Delay Times • Aggregate delay times between accesses to a specific site by a specific user follow a distribution • Jumps can be seen at certain times (30 seconds, 4 minutes, 5 minutes, etc. ) – “Spyware” and other programs use proxy and call back regularly • Trojans (and other programs) which call back regularly can be detected by examining distribution of delay times EECS 598 -2 Presentation
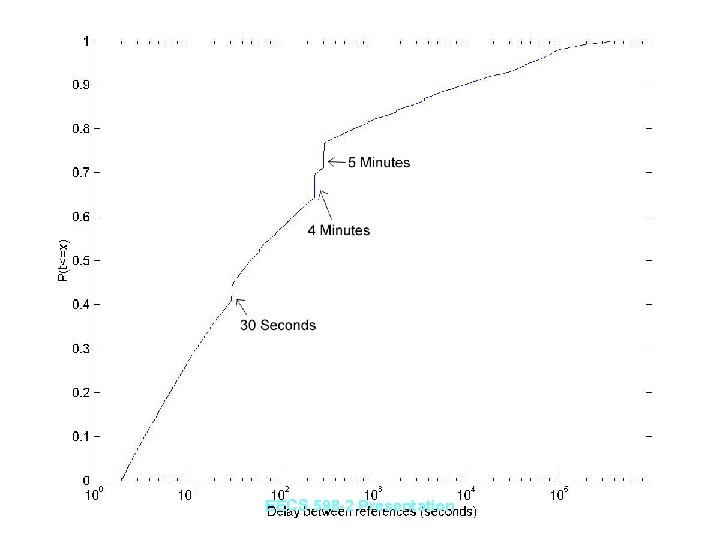
EECS 598 -2 Presentation

Results: Request Size • Outbound HTTP request size alone does not follow a predictable pattern like delay time – Whether a site is being accessed by a program or a person cannot be determined • File uploads of over 3 -4 KB can be detected – Only ten hosts with a request over 4 KB (four over 10 KB) • Useful for detecting data leaks and enforcing “no upload” policy EECS 598 -2 Presentation
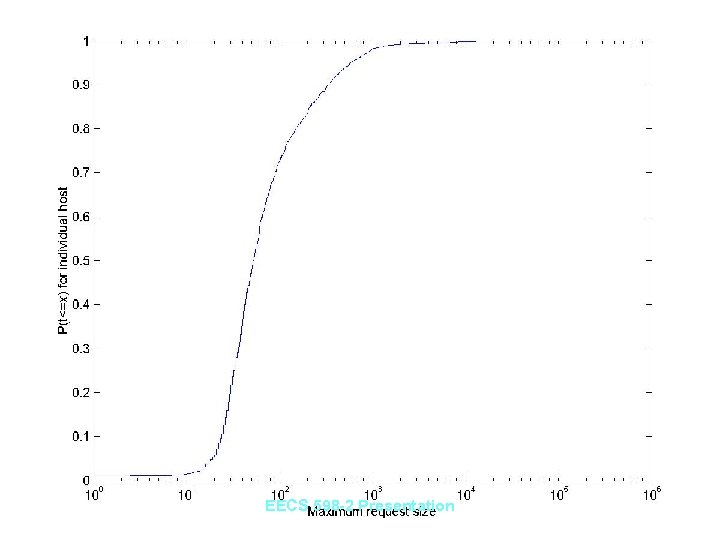
EECS 598 -2 Presentation
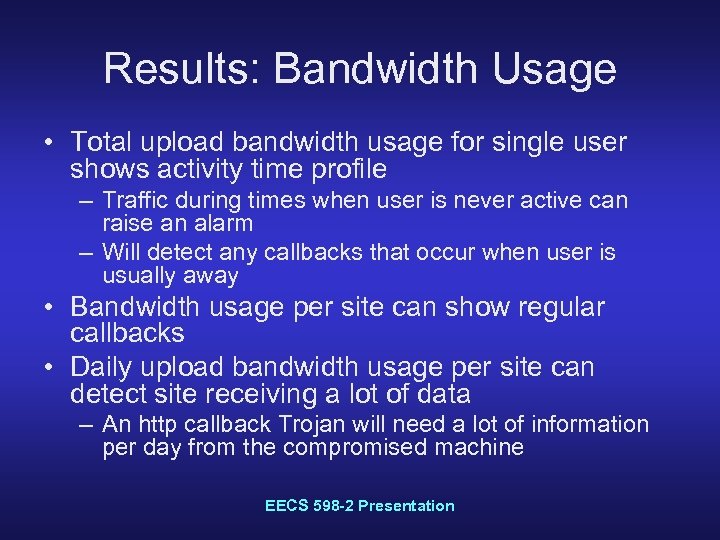
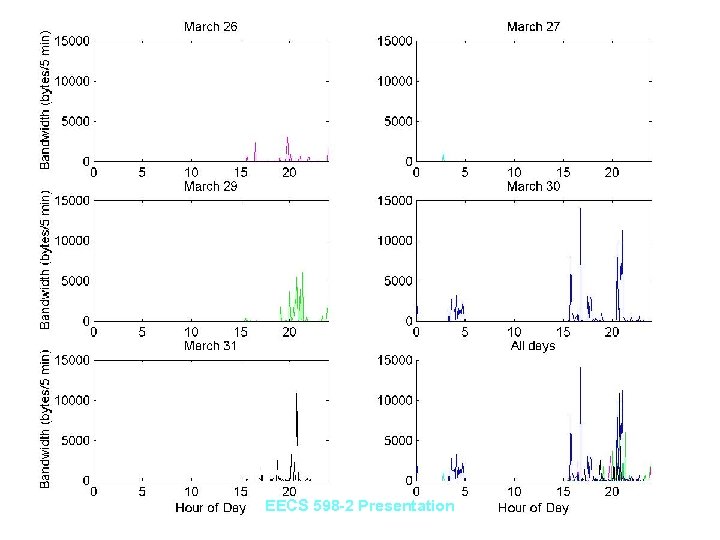
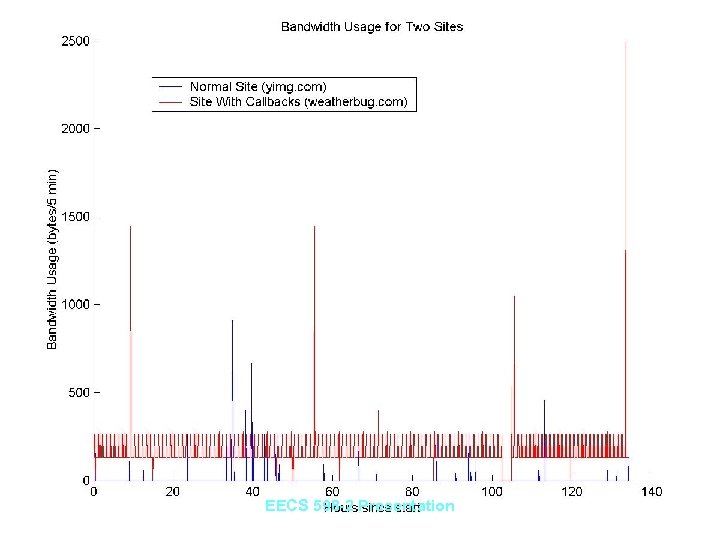
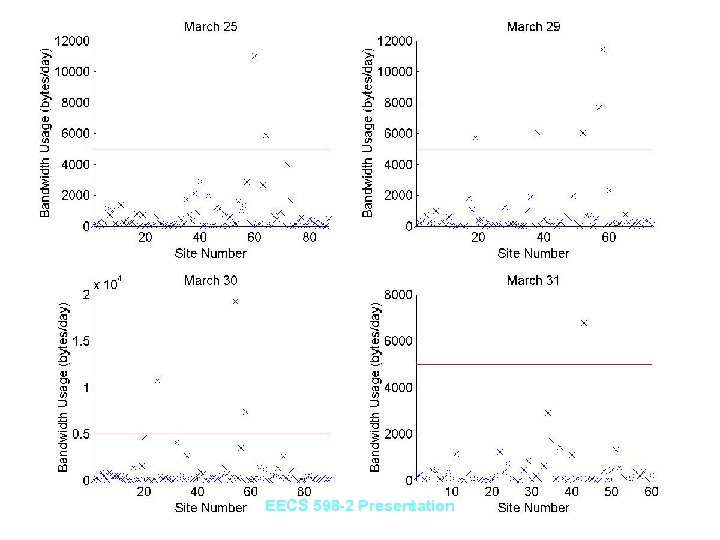
Results: Bandwidth Usage • Total upload bandwidth usage for single user shows activity time profile – Traffic during times when user is never active can raise an alarm – Will detect any callbacks that occur when user is usually away • Bandwidth usage per site can show regular callbacks • Daily upload bandwidth usage per site can detect site receiving a lot of data – An http callback Trojan will need a lot of information per day from the compromised machine EECS 598 -2 Presentation
EECS 598 -2 Presentation
EECS 598 -2 Presentation
EECS 598 -2 Presentation

Future Work • Develop an algorithm to detect entropy in strings – Greatly reduce the number of outbound bytes measured per request • English words contain much less information than random bytes – Would help isolate intense, chaotic (encrypted or compressed) bandwidth usage associated with Trojans • Apply concepts from Web Tap to other protocols – Thorough intrusion detection – Useful in more open networks EECS 598 -2 Presentation

Conclusion • In a high security network, outbound http is the only good way to exfiltrate information • Data exfiltration is done by a Trojan computer program using callbacks • Web Tap is a Network-Based Anomaly Detection system – Human web browsing follows specific patterns which are hard to mimic – Web Tap takes advantage of patterns to hunt down Trojan and “ad/spyware” programs EECS 598 -2 Presentation

Questions? EECS 598 -2 Presentation

It’s Demo Time! EECS 598 -2 Presentation
846c2da0cbbdf2a4cf03a7143ea9959e.ppt