c986059dd7e957b8ac3a42ed302117d0.ppt
- Количество слайдов: 51

Web Site Advertising and Retailing z Discuss the advantages of net advertising z Discuss the multifaceted approaches of advertising z Discuss net advertising dos and don’ts z Discuss the use of log files, Double. Click and tags as methods for gathering advertising statistics z Discuss the use of web banners z Discuss the use of the web for retailing z Discuss changes in internet-based retailing approaches z Discuss affiliation programs

Security Objectives z Discuss the roles encryption and certificates play z Contrast symmetric and asymmetric encryption z Discuss key activities in certification management z Define: Cryptography, digital ID, key, digital signature, hash coding, hash algorithm, message digest, private key, public key, CERT z Discuss protecting intranets with firewalls and corporate servers against being attacked through the Internet z Discuss the role Secure Socket Layer, Secure HTTP, and Secure Electronic Transaction protocols play in protecting e-commerce

The Net as an Advertising Resource z. It’s fast y. Print ads: 4 -6 weeks to create, 2 -6 weeks to publication y. Web ads: matter of days y. Changes can be made quickly z. Inexpensive y. Direct mail: $. 50 -$. 75/piece vs. email: $. 10/piece (no limit on length) z. Allows pictures and testimonials z. Multifaceted

Nature of Communication: Two Methods z Personal contact model (one-to-one) y. Also called prospecting y. Firm’s employees individually search for, qualify, and contact potential customers z Mass media model (many-to-one) y. Firm delivers message and broadcasts it through billboards, newspaper, television, etc. y. Addressable media is sometimes distinguished from mass media y. Addressable media is directed to known addresses, and includes direct mail, telephone calls, and e-mail

Multifaceted Advertising Approaches z. Usenet new groups z. Free email services (17. 8% WSJ 3/21/99): Free. Mark Communications, Juno Online Services z. Games: Bay. Bank, www. riddler. com z. Interactive screen savers(freeloader) z. Framing: http: //totalnews. com (formerly) z. Advertorial z. Ad Robot (push technology) z“persistence: ” ICQ

Web Terms Used in Advertising z CPM is a dollar amount for each thousand people in the estimated audience z A visit occurs when a visitor requests a page from a web y. Further page loads counted as part of the visit for a time period chosen by the site administrator z Trial visit -First time a visitor loads a web site; A subsequent visit is a repeat visit z Page view y. Each time a visitor loads a page- if the page has an ad, this is called an ad view

Web Terms Used in Advertising z Impression -- each time a banner ad loads y. If a visitor clicks the ad to open it, it is called a click or click-through y. Advertisers use market segmentation x. Divides the pool of potential customers into common demographic characteristics, such as age, gender, income level, etc. called segments x. Targets specific messages to these groups x. Micromarketing- targeting very small market segments

What about Web Banners? z. Unique to Net z. Usually limited text with hot link z. Different sizes sell for different prices z. Site may rotate banner (e. g. , Yahoo and C -Net) z. Lots of competition z. Hard to assess impact
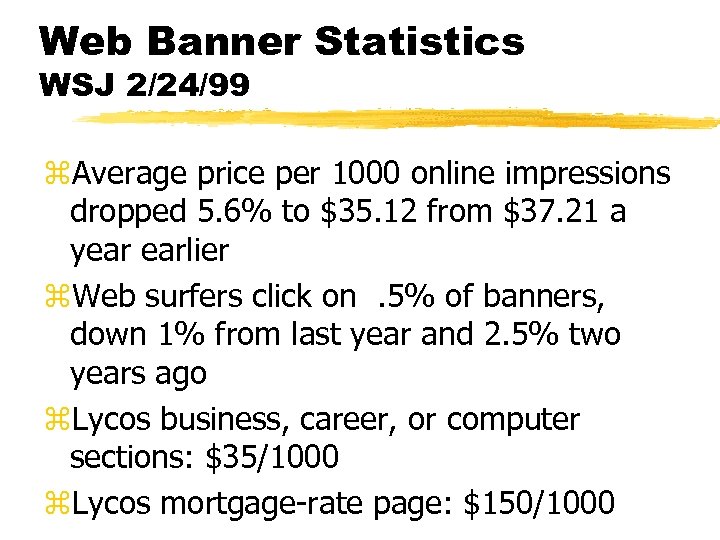
Web Banner Statistics WSJ 2/24/99 z. Average price per 1000 online impressions dropped 5. 6% to $35. 12 from $37. 21 a year earlier z. Web surfers click on. 5% of banners, down 1% from last year and 2. 5% two years ago z. Lycos business, career, or computer sections: $35/1000 z. Lycos mortgage-rate page: $150/1000

Running Time cyberatlas 8/28/2000 z. Over 7, 000 new banner ads appear each week, but they only run an average of less than three weeks (based on year study of top 500 websites) z. Staying power depends on industry yautomotive banners: 7. 8 weeks (avg) yhardware/electronics banners: 4. 1 weeks (avg) z. Most ad campaigns garner less than 44, 000 impressions

Choosing the Best Place to Advertise z. Popular sites (C&S): y. AOL y. Yahoo y. Microsoft’s Network y. Lycos Inc z. Post in all categories that fit and on industry-appropriate forums z. Give robots your URL zwww. submit-it. com z. Put URL at bottom of your e-mail

Definition of Branding z. Elements of branding y. Differentiation y. Relevance x. Degree the product offers utility to the customer y. Perceived value

Creating and Maintaining Brands on the Web z. What is the role of brand names? z. Top 100 e-commerce sites spent an average of $8 million to create and build their online brands in 1998 z. In 1999, dot-coms spent $3. 1 billion in traditional advertising including TV, radio and print (WSJ 4/3/2000) z. Dot-com advertising spending 2% of total $87. 5 of US advertising spending (WSJ 4/3/2000)

Emotional vs. Rational Branding z. Emotional appeals work well in mass media because ad targets are passive y. Do not work well on Web, however, because Web is active medium z. Rational branding y. Gives people valuable service in exchange for viewing ads y. Examples include free e-mail and secure shopping services y. Navigators can play a role here

Advertising Considerations z. Mix traditional with net advertising yplace e-mail address and URL on advertising, catalogs, letterhead, business cards (resumes) ypick a memorable URL y. Play media off one another- Victoria’s Secret z. Use promotions: y. First on-line purchase y. Coupons z. Identify target markets

Advertising Do’s z. View the competition yget ideas for your site ycheck out other’s HTML z. Spend time as a user z. Stay abreast of trends z. Include complementary links (“Welcome to my site, please leave!”) z. Check your links periodically z. Post press releases to mailing lists z. Relationship Marketing

Relationship Marketing (1: 1 Marketing) z. Market via more personal touch y. Get personal testimonials of people in the trenches who have used product y. Personalized web pages y. Contribute to discussion groups y. Company exec may answer e-mail z. Focus on maintaining and enhancing relationships ycosts 5 times as much to acquire new customer than to retain current one

Net agents z“intelligent agents”, “software agents” z. Software, often applying artificial intelligence, to support buyers ylocating information or products yreceiving personalized information on the basis of a predetermined profile yreturn comparative information based on user z. Can make decisions or initiate requests

Getting Statistics about Advertising Impact z. Double. Click, Match. Logic, Real. Media, Inc. ybuy ad space on Web and keep their own tally of ads on a page ysome customers ban these advertisers from using any data from their web site x. P&G, GM and Match. Logic x. IBM bars websites where it advertises (>800 web sites) from collect its ad-campaign data z. HTTPD logs z. Tags z. Cookies

Double. Click, Inc z. Sells advertising space on network of 1400 websites z. Information to better customize ads z. Predicts what you will buy on Web based on what you have purchased online and offline z. Pay $1 billion to buy Abacus Direct ymay need to revise privacy statement z. Plan requires help of online retailer

Getting Statistics about Advertising Impact z Use HTTPD log files z Log counts every access yincludes access to each image ymay be hard to determine unique independent entries z Logs contain domain names, not user names, of visitors z Logs also include time, date and accessed URL z Get logs from ISP z Logs themselves may be large
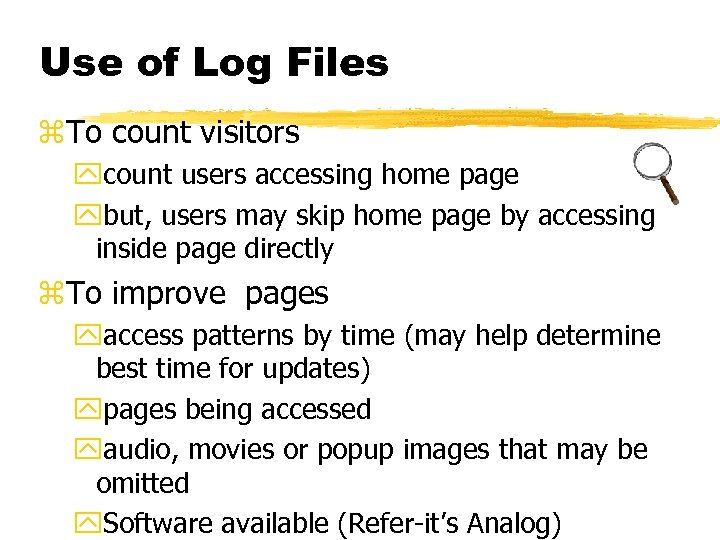
Use of Log Files z. To count visitors ycount users accessing home page ybut, users may skip home page by accessing inside page directly z. To improve pages yaccess patterns by time (may help determine best time for updates) ypages being accessed yaudio, movies or popup images that may be omitted y. Software available (Refer-it’s Analog)

New Standard to Count Visits: Tags z. Fast Steering Committee z. Programmer adds simple software codes to Web ad yno one owns codes ycan be freely inserted z. Advertisers don’t trust numbers y. Cache ads aren’t counted
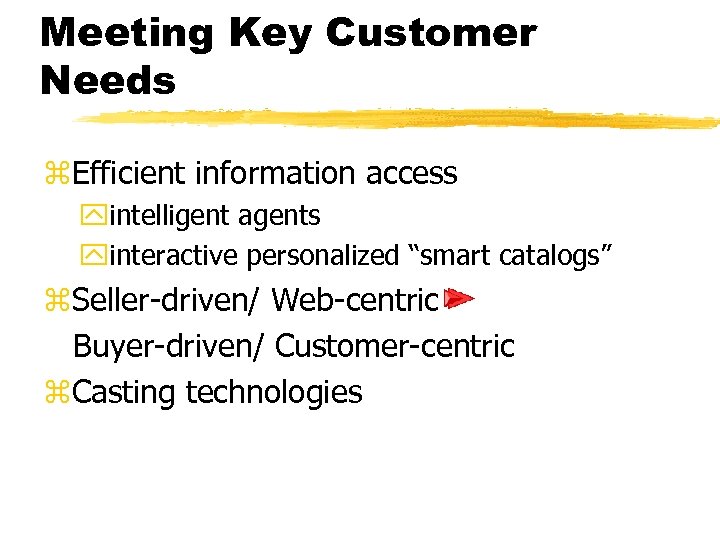
Meeting Key Customer Needs z. Efficient information access yintelligent agents yinteractive personalized “smart catalogs” z. Seller-driven/ Web-centric Buyer-driven/ Customer-centric z. Casting technologies
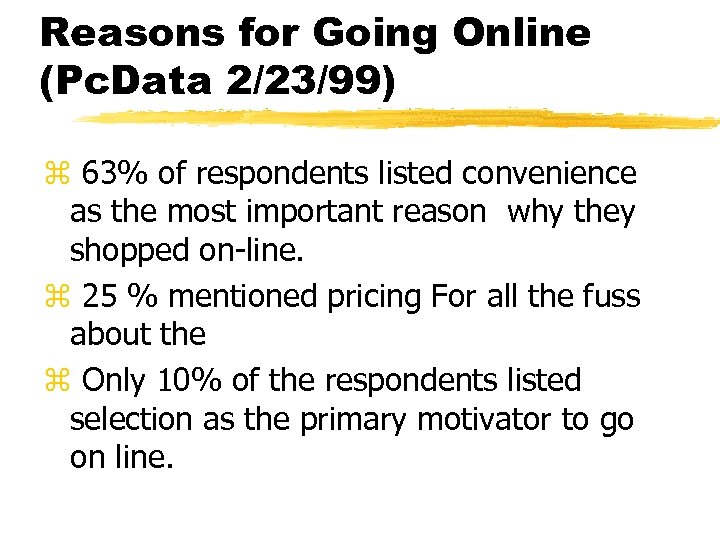
Reasons for Going Online (Pc. Data 2/23/99) z 63% of respondents listed convenience as the most important reason why they shopped on-line. z 25 % mentioned pricing For all the fuss about the z Only 10% of the respondents listed selection as the primary motivator to go on line.

Internet Retailing -tailing) (WSJ 4/5/2000) (e y. Last year doubled to $15 billion y. Expected to rise 53% to 23 billion in 2000 y. Costs rising faster than sales xadvertising xwarehouses xonline assistance (Land’s End, e. Toys) y. Building a high quality e-tailing website costs $30 million y. Building a brand costs$100 million

Internet Retail Establishments z. Brochure ytells company’s story in text and pictures z. Company mailbox yautomated mail response to e-mail requests z. Specialty store ystorefronts with product catalogs y http: //www. virtualvin. com/; http: //www. fridgedoor. com/ z. Cybermall z. Subscription

Storefronts and Cityscapes z. There are “no bad parts of town” z. Don’t pay premium for name alone. z. Reasonably priced storefronts offer some advantages. z. Belong to multiple communities yput host page in one location yplace links to your pages in other malls z. Push products (insurance)may do better face-to-face

Cybermalls z. Retail complex that houses dozens of specialty stores yhttp: //malls. com/awesome x$25 mo/ 5 pages - $850 mo/maintained y. CUC Net. Market: www. netmarket. com y. ZD Net’s Computershopper: www. zdnet. com/computershopper z. Malls with traffic and big business tenants (i. e. , IBM) cost more

Subscription/Fee-Based Marketing z Marketing-subscription mixed model y. Revenue derived from fee and it also accepts some level of advertising y. Used by newspapers and magazines y. Successful web models include New York Times, the Wall Street Journal, ESPN, Reuters, and Northern Light z Fee for transaction Model y. Online travel agents and car-buying services can remove an intermediary from a value chain

Affiliation Programs z Description of AMAZON. COM’s affiliate program (started in 1996): We pay 15% on individually linked books and 5% on all other items. You build a custom bookstore, music store, and video store on your site or simply put up a link to Amazon. com and get paid on all sales. We do the customer service, shipping and tracking of sales. With our program there are no hidden sales quotas or performance tiers. Put up a link and start earning today. z www. referit. com

Security on the Internet z. CERT z. Encryption z. Digital Signatures/Certificate Authorities z. Protocols z. Firewalls

Computer Emergency Response Team (CERT) z. Housed at Carnegie Mellon University z. Responds to security events and incidents within the U. S. government and private sector z. Posts CERT alerts to inform Internet users about recent security events z. Posts CERT DNS attack advisory about domain name service attacks
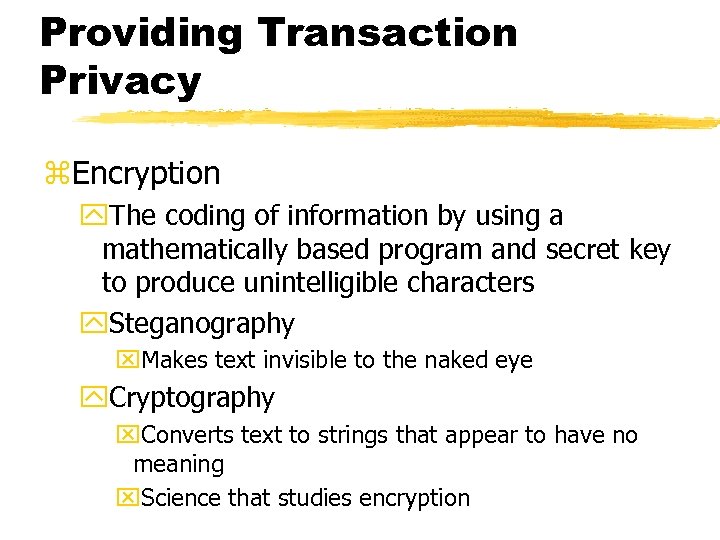
Providing Transaction Privacy z. Encryption y. The coding of information by using a mathematically based program and secret key to produce unintelligible characters y. Steganography x. Makes text invisible to the naked eye y. Cryptography x. Converts text to strings that appear to have no meaning x. Science that studies encryption

Encryption z. Mutation of information in any form plain text cipher text plain text z. Based on algorithm and key y. Key - very large string of zeros and ones: the larger the better! y. Algorithm - mathematical function y 40 -bit keys are considered minimal, 128 -bit keys provide much more secure encryption
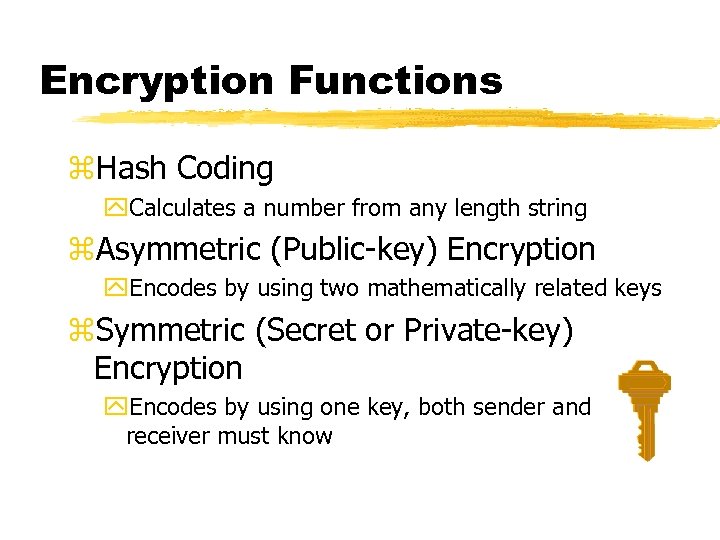
Encryption Functions z. Hash Coding y. Calculates a number from any length string z. Asymmetric (Public-key) Encryption y. Encodes by using two mathematically related keys z. Symmetric (Secret or Private-key) Encryption y. Encodes by using one key, both sender and receiver must know

Cryptography z. Private (Secret) key cryptography Symmetric yshared key (both parties agree) ydoes not scale ynonrepudiation is impossible y. Date Encryption Standard (DES); Triple DES z. Public key cryptography - Asymmetric ypublic and private keys ydigital signatures ysuited for multiple users
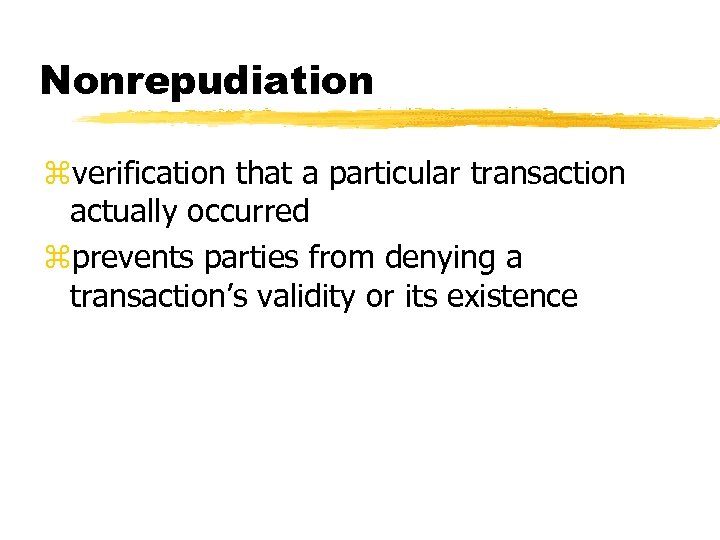
Nonrepudiation zverification that a particular transaction actually occurred zprevents parties from denying a transaction’s validity or its existence

Digital Signature z. Mathematical algorithms for encrypting z. A puts private key and document together z. A generates unique number called digital signature (fingerprint or message digest) z. Fingerprint attached to original message and further encrypted with private key z. Message sent to B z. B decrypts using A’s public key z. Checks for modification with calculations to get matching fingerprint

Certificate Authority (CA) z. Alternative to secure transmission z. Uses trusted third party to authenticate public key z. Certificate is digitally signed by CA to verify identity and credentials z. Identification requirements vary by CA z. Every digital certificate is unique z. Digital certificate is sent along with digital message z. Have expiration date

Certification Management z. Digital certificates yissue yregister ygenerate ymanage yrevoke z. To insure yusers authorized transaction ytransaction hasn’t been tampered ydigital receipt and time stamping

Hierarchy for CA Root central facility/Policy approval Certification Authorities/Cybernotaries Local Registration Authorities Encryption Entities Digital Signature Entities User Certificates/Digital Signatures End Entities
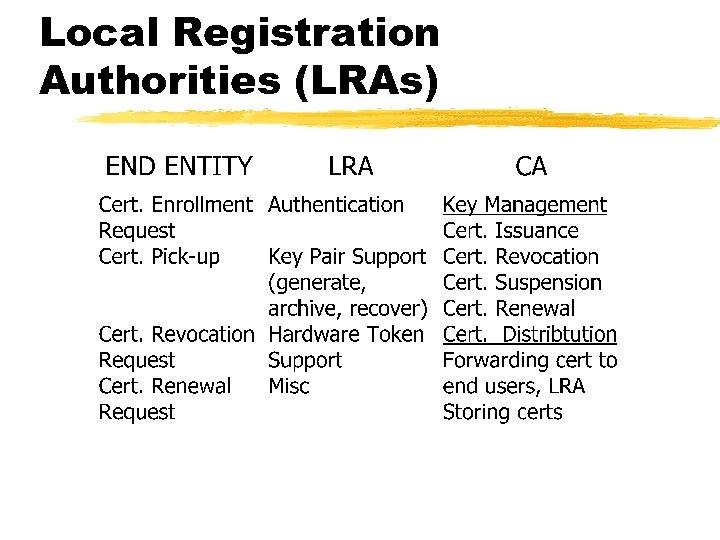
Local Registration Authorities (LRAs)

CA Tutorial zhttp: //www. kpmgca. com/download. htm

Veri. Sign OEM z. CA software: cross-platform, shrinkwrapped product z. PKI and digital certificate solutions z. Supports LRA y. Query manager (SQL) y. Transaction Manager (integrity of certificates) y. Signing server y. Middleware Framework

Secure Sockets Layer (SSL) Protocol z. Secures many types of connections between two computers on Internet z. Developed by Netscape z. Had backing of Apple. Soft, DEC, Master. Card International z. Provides a security handshake in which the client and server computers exchange the level of security to be used, certificates, among other things

Secure Sockets Layer (SSL) Protocol z. Provides either 40 -bit or 128 -bit encryption z. Secures data packets at network layer z. Secures connections between two computers; checks certificates z. Session keys are used to create the cipher text from plain text during the session z. Can secure communications in addition to HTTP (i. e. , FTP) z. Uses public and private key encryption
Secure HTTP (S-HTTP) Protocol z. Extension to HTTP that provides numerous security features y. Client and server authentication y. Spontaneous encryption y. Request/response nonrepudiation z. Provides symmetric and public-key encryption, and message digests (summaries of messages as integers) z. Open protocol designed to secure web transactions using special packet headers

Secure Electronic Transaction z Backed by Master. Card, Visa, IBM, Netscape and Microsoft z Secures credit card transactions z Uses digital certificate yconsumer’s name yfew digits of consumer’s credit card yname of bank that issued card z Merchant uses public key cryptography to verify consumer’s identity z Provides confidentiality of payment info z Provides merchant authentication

Firewalls z. Control damage to your data and computer systems z. Protect against spoofing z. Implement access controls based on contents of the packets of data transmitted between two parties or devices on a network z. Single point of control for security on network

Firewalls z. Should be stripped of any unnecessary software z. Categories of firewalls include y. Packet filters x. Examine all packets flowing through the firewall y. Gateway servers x. Filter traffic based on the requested application y. Proxy servers x. Communicate on behalf of the private network x. Serve as a huge cache for Web pages
c986059dd7e957b8ac3a42ed302117d0.ppt