5823451815c452b3ba3b368e81f5bcf6.ppt
- Количество слайдов: 21

Web Services Security – Ready for Wireless? Immo Hüneke, Technical Architect Storage Days Europe 2003 Birmingham 13 May 2003 Objec valu. E T Contents Confidential & Proprietary to Object. Value Ltd. © 2003
Agenda ¢ Who is Object. Value ¢ What is meant by Web Services ¢ Approaches to Wireless Security ¢ Web Services (WS-) Security ¢ An example ¢ Discussion ¢ Conclusion and Recommendation Objec valu. E T Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? 13 May 2003 2

Object. Value ¢ Founded 2002 – see www. objectvalue. com ¢ Vehicle for my consulting and contracting activities ¢ Example projects l Technical support for Tandem-based Intelligent Network call routing system (Mobile operator in South Africa) l Requirements study for Engineering Access Modelling and Planning systems (Underground railway operating company) ¢ Expertise in mobile computing, wireless internet and advanced methodology Objec valu. E T Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? 13 May 2003 3
Web Services ¢ Web Services are replacing other integration technologies in many contexts ¢ They promise in the long term to enable the fully automated assembly of distributed application functionality on demand from published service components l This is currently a pipe dream ¢ Nevertheless, many application vendors are urgently overhauling their products to expose their individual functions as Web Services l l l Peoplesoft SAP all Microsoft products released with the. NET branding Objec valu. E T Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? 13 May 2003 4

Web Services (ii) ¢ Web Services, using XML as a lingua franca, have emerged as the next-generation Web-based technology for exchanging information ¢ Web Services are modular, self-describing applications that are accessible over the Internet ¢ Web Services are based on open standards ¢ Web Services enable Web-based applications to interoperate between any platform, object model, and programming language (in theory!) ¢ “Web Services allow any piece of software to communicate with a standardized XML messaging system. ” Hari Mailvaganam Objec valu. E T Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? 13 May 2003 5
Web Services (iii) ¢ Two main schools of thought l Both supported through OASIS/Open ¢ eb. XML (more mature, top-down) l “Business Web Services” (Sun) l Business Process / Business Document model l BPSS, CPP/CPA, eb. MS, SOAP with Attachments, MIME ¢ WSDL/UDDI (more noise, bottom-up) l “Enterprise Web Services” (Sun) l Remote Method Call model l WSDL, UDDI repository, SOAP (“WUS”), plus options: WS-Transaction WS-Security BPEL 4 WS … Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? Objec valu. E T 13 May 2003 6
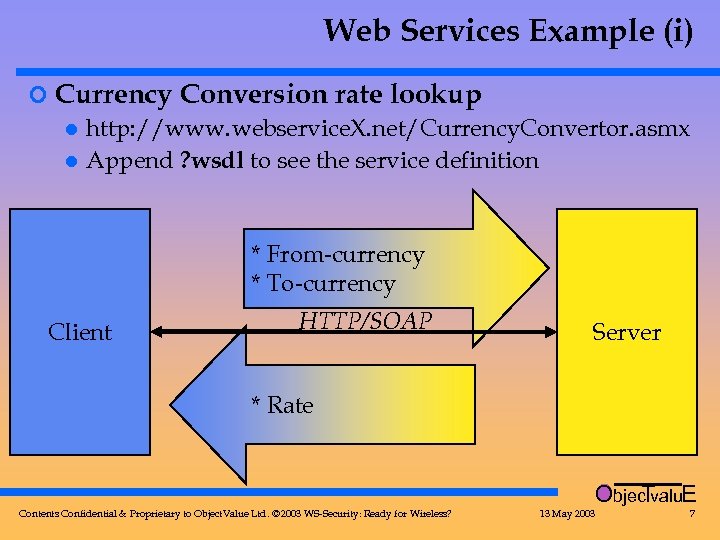
Web Services Example (i) ¢ Currency Conversion rate lookup l http: //www. webservice. X. net/Currency. Convertor. asmx l Append ? wsdl to see the service definition * From-currency * To-currency Client HTTP/SOAP Server * Rate Objec valu. E T Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? 13 May 2003 7
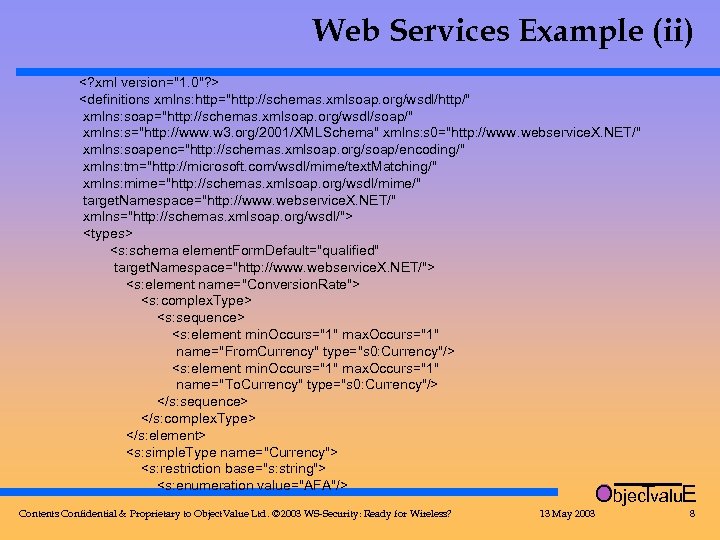
Web Services Example (ii) <? xml version="1. 0"? > <definitions xmlns: http="http: //schemas. xmlsoap. org/wsdl/http/" xmlns: soap="http: //schemas. xmlsoap. org/wsdl/soap/" xmlns: s="http: //www. w 3. org/2001/XMLSchema" xmlns: s 0="http: //www. webservice. X. NET/" xmlns: soapenc="http: //schemas. xmlsoap. org/soap/encoding/" xmlns: tm="http: //microsoft. com/wsdl/mime/text. Matching/" xmlns: mime="http: //schemas. xmlsoap. org/wsdl/mime/" target. Namespace="http: //www. webservice. X. NET/" xmlns="http: //schemas. xmlsoap. org/wsdl/"> <types> <s: schema element. Form. Default="qualified" target. Namespace="http: //www. webservice. X. NET/"> <s: element name="Conversion. Rate"> <s: complex. Type> <s: sequence> <s: element min. Occurs="1" max. Occurs="1" name="From. Currency" type="s 0: Currency"/> <s: element min. Occurs="1" max. Occurs="1" name="To. Currency" type="s 0: Currency"/> </s: sequence> </s: complex. Type> </s: element> <s: simple. Type name="Currency"> <s: restriction base="s: string"> <s: enumeration value="AFA"/> Objec valu. E T Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? 13 May 2003 8
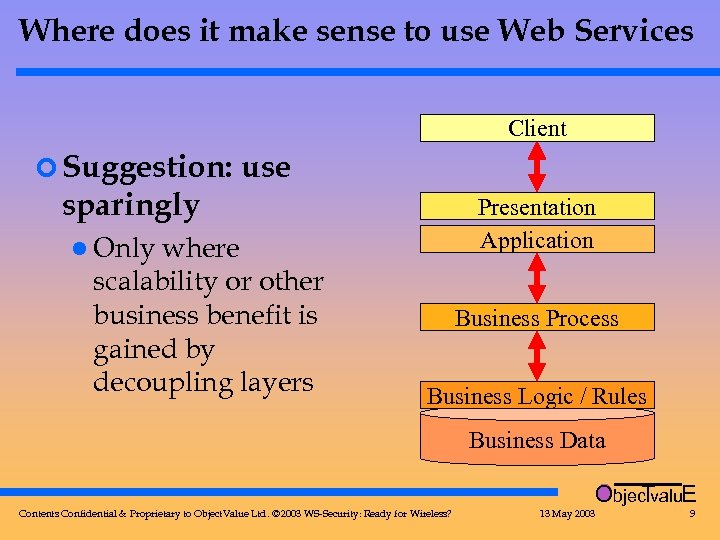
Where does it make sense to use Web Services Client ¢ Suggestion: use sparingly where scalability or other business benefit is gained by decoupling layers Presentation Application l Only Business Process Business Logic / Rules Business Data Objec valu. E T Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? 13 May 2003 9
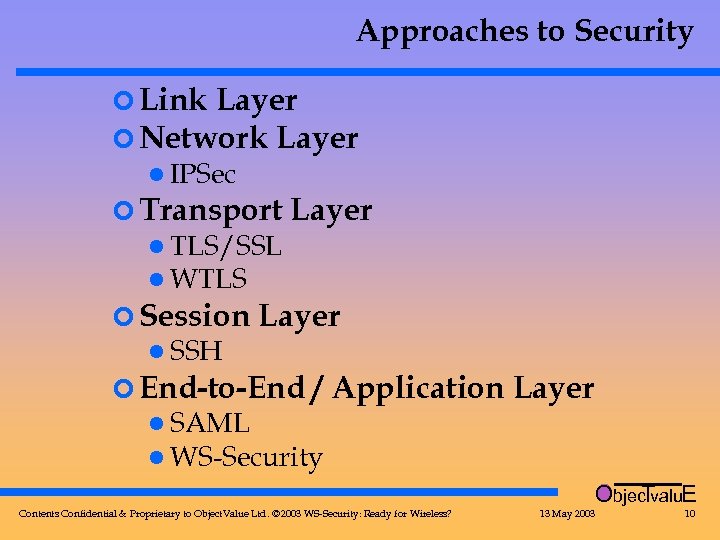
Approaches to Security ¢ Link Layer ¢ Network Layer l IPSec ¢ Transport l TLS/SSL l WTLS ¢ Session l SSH Layer ¢ End-to-End / Application Layer l SAML l WS-Security Objec valu. E T Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? 13 May 2003 10
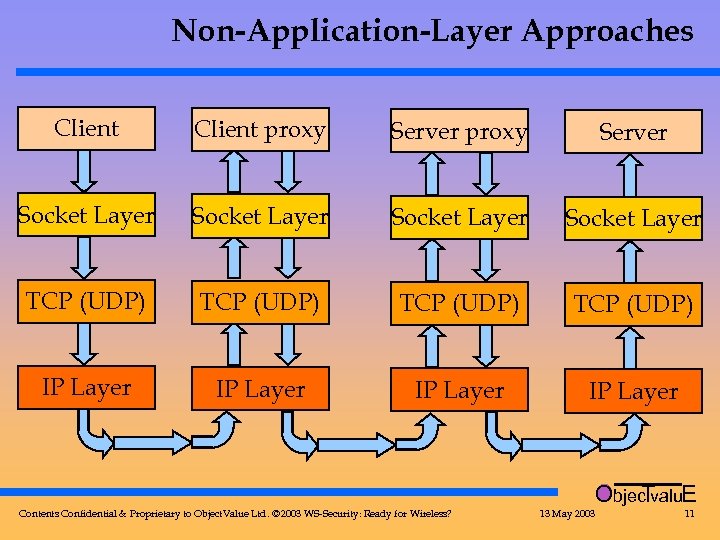
Non-Application-Layer Approaches Client proxy Server Socket Layer TCP (UDP) IP Layer Objec valu. E T Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? 13 May 2003 11
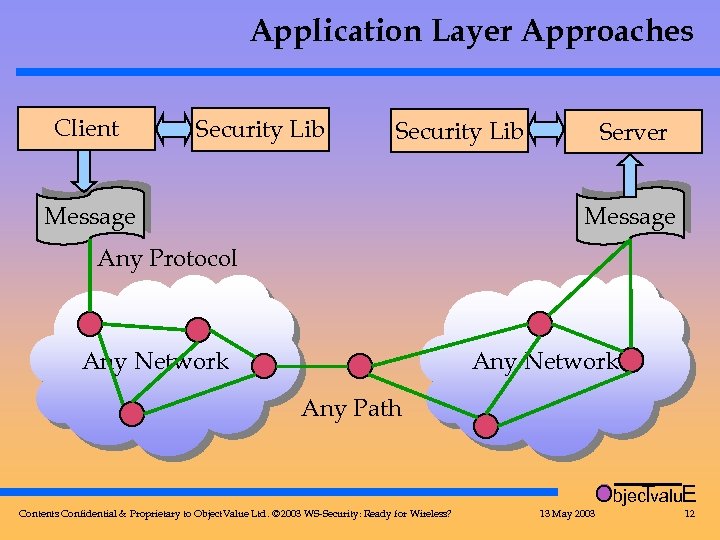
Application Layer Approaches Client Security Lib Message Server Message Any Protocol Any Network Any Path Objec valu. E T Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? 13 May 2003 12

Web Services Security ¢ Services provided l Single-message security tokens and digital (XML) signature l Message integrity XML Signature l Message authentication confidentiality XML Encryption Objec valu. E T Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? 13 May 2003 13
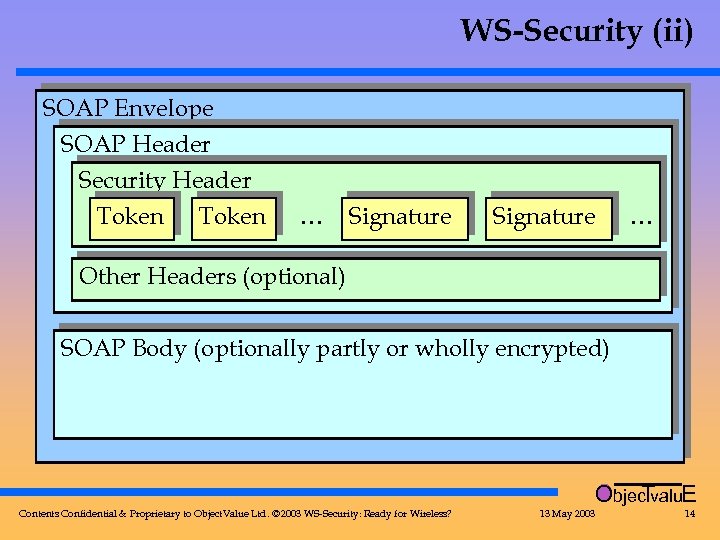
WS-Security (ii) SOAP Envelope SOAP Header Security Header Token … Signature … Other Headers (optional) SOAP Body (optionally partly or wholly encrypted) Objec valu. E T Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? 13 May 2003 14

WS-Security (iii) <? xml version="1. 0" encoding="utf-8"? > <S: Envelope xmlns: S="http: //www. w 3. org/2001/12/soap-envelope" xmlns: ds="http: //www. w 3. org/2000/09/xmldsig#"> <S: Header> <wsse: Security xmlns: wsse="http: //schemas. xmlsoap. org/ws/2002/xx/secext"> <wsse: Username. Token wsu: Id="My. ID">. . . </wsse: Username. Token> <ds: Signature> <ds: Signed. Info>. . . </ds: Signed. Info> <ds: Signature. Value>DJbchm 5 g. K. . . </ds: Signature. Value> <ds: Key. Info>. . . </ds: Key. Info> </ds: Signature> </wsse: Security> </S: Header> <S: Body wsu: Id="Msg. Body">. . . </S: Body> </S: Envelope> Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? 13 May 2003 Objec valu. E T 15

Example ¢ Mobile Sales Rep enters a customer order ¢ Message Authentication is used to verify the identity of the user (and check access permissions – outside scope of WS-Security) ¢ Message Integrity is used to ensure that the order cannot be modified in transit without detection (e. g. to change quantity, price or delivery address) ¢ Message Confidentiality is used to ensure that the customer’s order details are not seen by anyone except the supplier Objec valu. E T Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? 13 May 2003 16
Advantages ¢ End to end message confidentiality, integrity and authentication are assured ¢ Messages can be stored, retrieved and forwarded arbitrary numbers of times ¢ Extensible l Multiple security token formats l Multiple trust domains l Multiple signature formats l Multiple encryption technologies Objec valu. E T Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? 13 May 2003 17

Drawbacks Immaturity of the specification ¢ Many things outside the scope ¢ l l l Trust establishment Security policy exchange and agreement Security context specification Authentication mechanisms Key management Only one security header per message ¢ Processing and bandwidth overheads ¢ XML and SOAP are verbose: WS-Security exacerbates this l Signatures & tokens must be generated / checked every time l Onerous verification, logging and error reporting l ¢ Not ideally suited to inter-enterprise exchanges Objec valu. E T Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? 13 May 2003 18

Conclusion and Recommendation ¢ Yes, it can be done ¢ But the effort doesn’t seem worth it for the current generation of mobile devices ¢ VPN-style solutions lead to quicker and more dependable results ¢ Wait for standards to settle down ¢ Decide your business model l Extension of the enterprise network to the mobile l Direct interaction of mobile device with Web Services offered by multiple providers Objec valu. E T Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? 13 May 2003 19
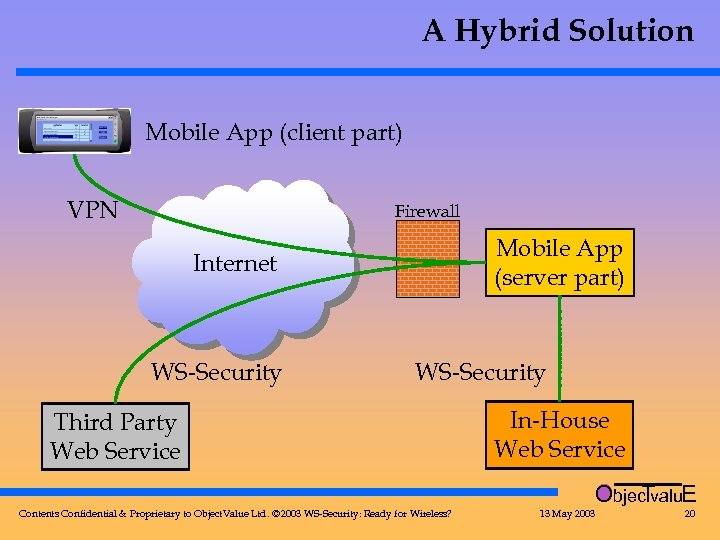
A Hybrid Solution Mobile App (client part) VPN Firewall Mobile App (server part) Internet WS-Security Third Party Web Service In-House Web Service Objec valu. E T Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? 13 May 2003 20

Thank You! a Softw Questions? alu. E T ec v re s stem nt Sy me lop deve on, llingt a c ay, W m o rd W ildfo d Kingd u e 1 G d. , 3 NS, Unit. com Lt e t. Valu y SM 6 8 jectvalue or c b irect Obje Surre. o D www Eng, C BCS 238 Sc M 072 B 1 )794 om neke ü (0 ; +44 tvalue. c mo H 35 Im ec 5 58 839 ke@obj 20 4 (0) o. hune 4 ' + * imm bj O cy & ltan onsu Objec valu. E T Contents Confidential & Proprietary to Object. Value Ltd. © 2003 WS-Security: Ready for Wireless? 13 May 2003 21
5823451815c452b3ba3b368e81f5bcf6.ppt