a99ce56793aa669c06817bb86021dcdb.ppt
- Количество слайдов: 88
Web Services, Business Process and Enterprise Simulation with MDA Enterprise Collaboration Architecture A tutorial on applying Model Driven Architecture to web services using the OMG Enterprise Collaboration Architecture with UML

Introductions Cory Casanave cory-c@enterprise-component. com www. enterprise-component. com Primary author of “Component Collaboration Architecture” in EDOC
It’s about Collaboration z Collaboration is a key differentiation and key cost center (Healthcare Example) y Customer Collaboration y Claim processing y Disputes y Physician Collaboration y Payer Collaboration y Hospital Collaboration y Broker Collaboration y Government Collaboration y Employee Collaboration y Others. . . Copyright © 2000 -2003, Data Access Technologies, Inc. The system integrates multiple collaborations
Integrating Enterprises, People & Systems - Worldwide z Business Requirements y. Virtual Enterprises y. Enterprise Integration (EAI) y. Supply-chain automation (B 2 B) y. Customer Integration (B 2 B) y. Web deployment (B 2 C) y. Internet Marketplace (B 2 C) z Collaboration and Integration Copyright © 2000 -2003, Data Access Technologies, Inc.
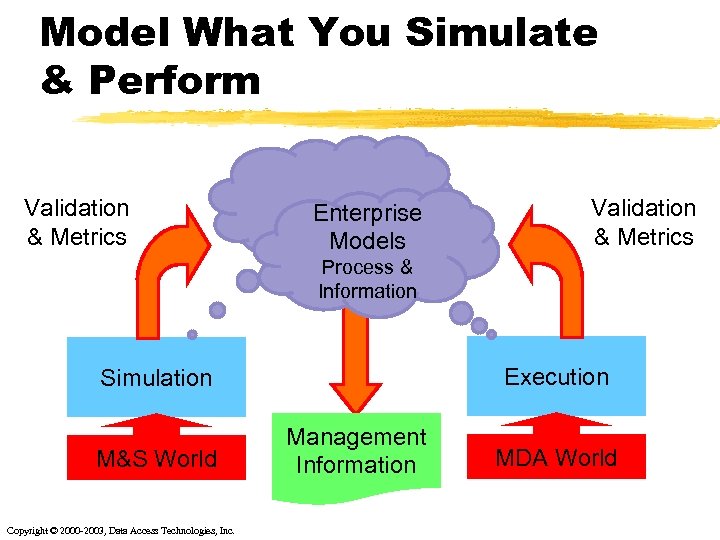
Model What You Simulate & Perform Validation & Metrics Enterprise Models Validation & Metrics Process & Information Execution Simulation M&S World Copyright © 2000 -2003, Data Access Technologies, Inc. Management Information MDA World
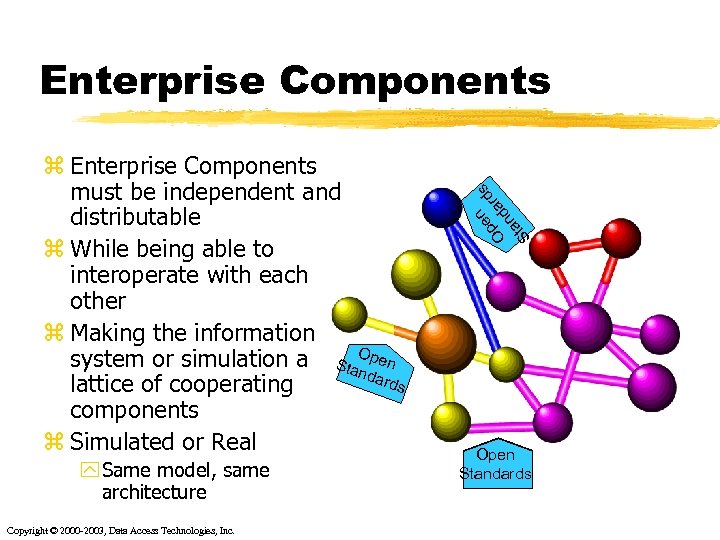
z Enterprise Components must be independent and distributable z While being able to interoperate with each other z Making the information system or simulation a Sta. Open nda rds lattice of cooperating components z Simulated or Real y Same model, same architecture Copyright © 2000 -2003, Data Access Technologies, Inc. n s pe ard O d n ta S Enterprise Components Open Standards
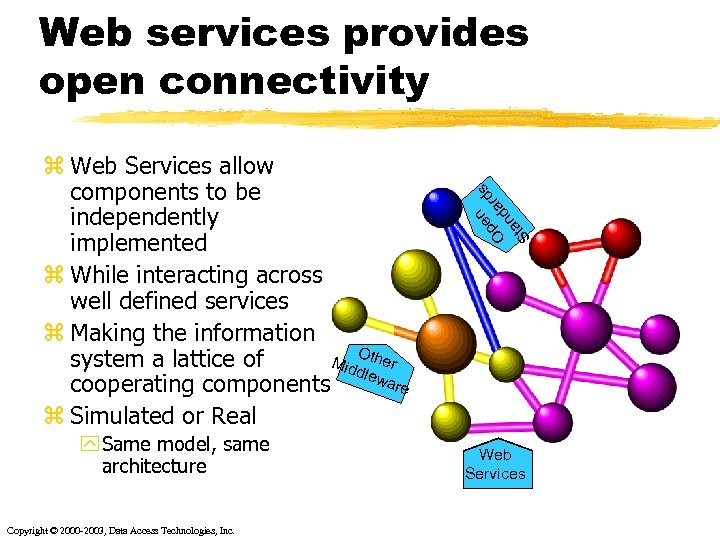
z Web Services allow components to be independently implemented z While interacting across well defined services z Making the information O system a lattice of Mid ther dlew are cooperating components z Simulated or Real y Same model, same architecture Copyright © 2000 -2003, Data Access Technologies, Inc. n s pe ard O d n ta S Web services provides open connectivity Web Services
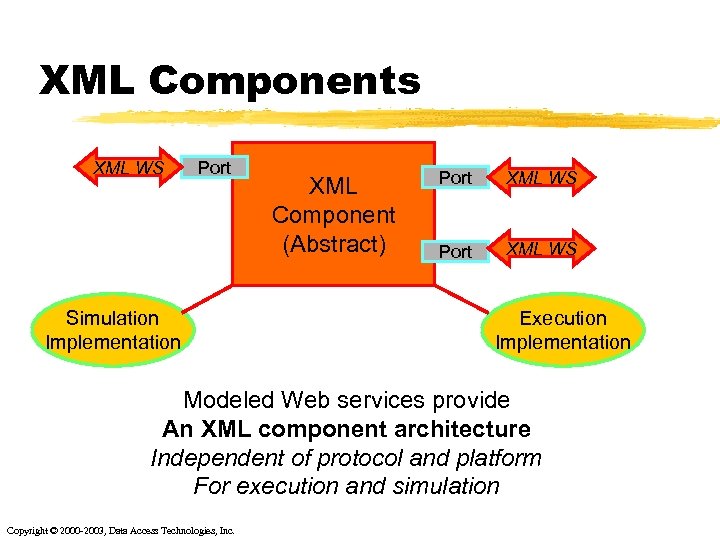
XML Components XML WS Port Simulation Implementation XML Component (Abstract) Port XML WS Execution Implementation Modeled Web services provide An XML component architecture Independent of protocol and platform For execution and simulation Copyright © 2000 -2003, Data Access Technologies, Inc.
Core Requirements z Web Services y. Providing flexible connectivity between components implemented in a variety of technologies for both simulation and execution y. Web services provides for the connecting points between components z Common Models y. Models of process, structure, roles, interactions, components and information representing the collaborative fabric of the enterprise driving both execution and simulation Copyright © 2000 -2003, Data Access Technologies, Inc.
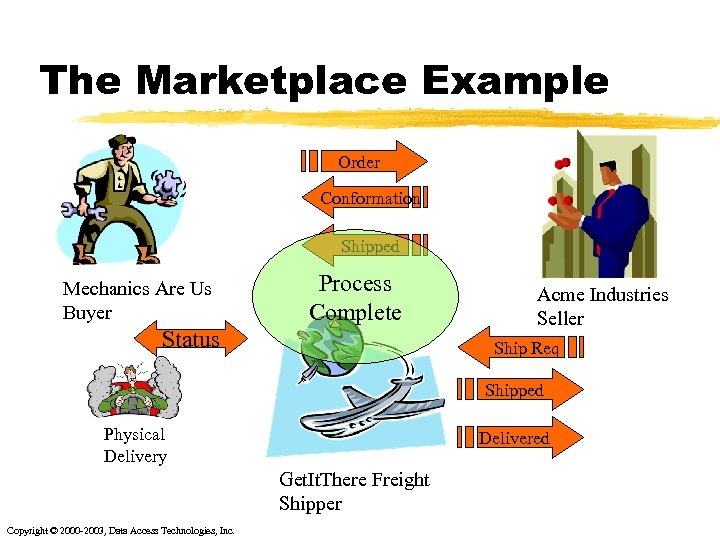
The Marketplace Example Order Conformation Shipped Mechanics Are Us Buyer Process Complete Status Acme Industries Seller Ship Req Shipped Physical Delivery Delivered Get. It. There Freight Shipper Copyright © 2000 -2003, Data Access Technologies, Inc.
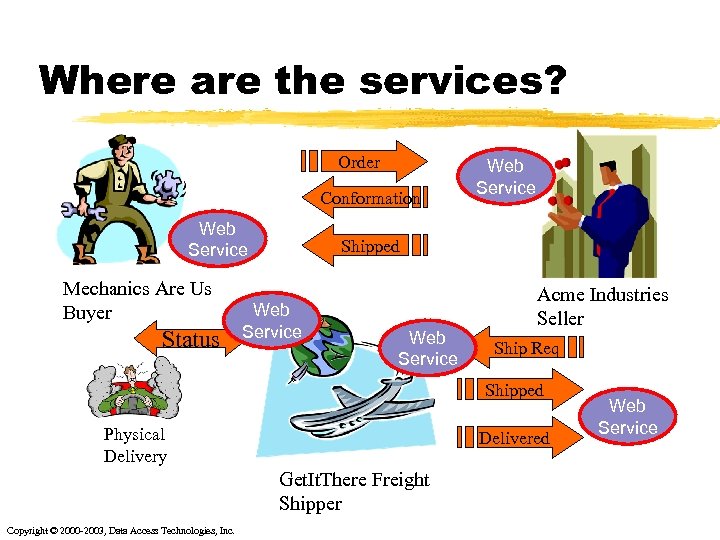
Where are the services? Order Conformation Web Service Mechanics Are Us Buyer Status Web Service Shipped Web Service Acme Industries Seller Ship Req Shipped Physical Delivery Delivered Get. It. There Freight Shipper Copyright © 2000 -2003, Data Access Technologies, Inc. Web Service
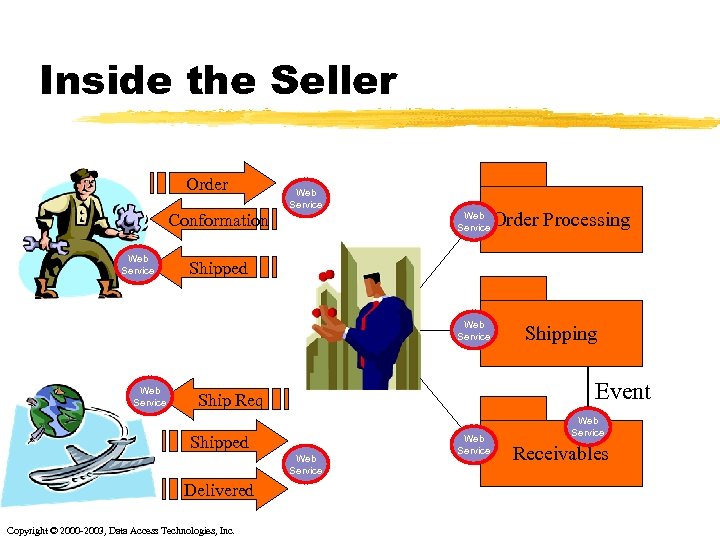
Inside the Seller Order Web Service Order Processing Web Service Conformation Shipping Shipped Event Ship Req Shipped Web Service Delivered Copyright © 2000 -2003, Data Access Technologies, Inc. Web Service Receivables
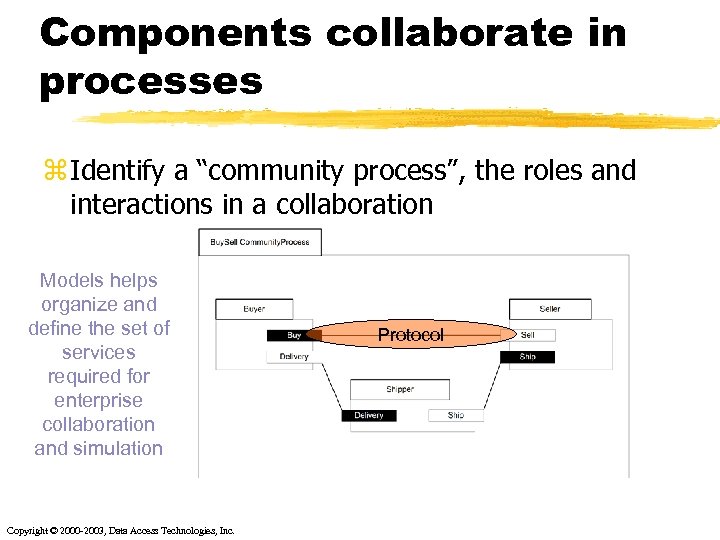
Components collaborate in processes z Identify a “community process”, the roles and interactions in a collaboration Models helps organize and define the set of services required for enterprise collaboration and simulation Copyright © 2000 -2003, Data Access Technologies, Inc. Protocol
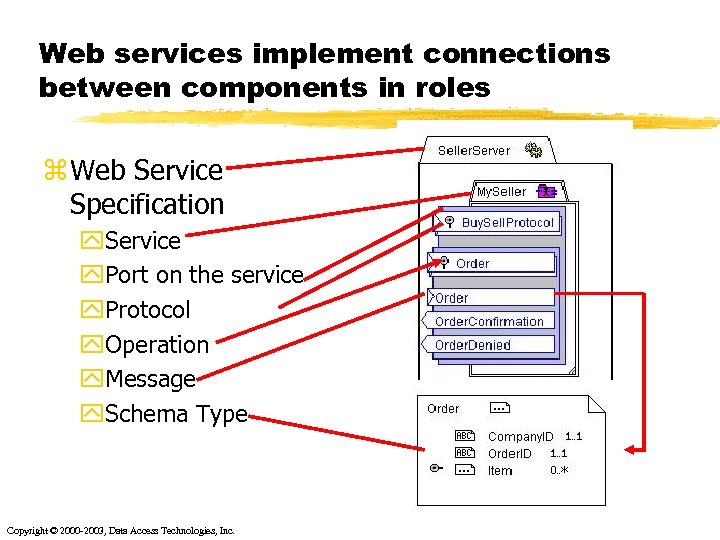
Web services implement connections between components in roles z Web Service Specification y. Service y. Port on the service y. Protocol y. Operation y. Message y. Schema Type Copyright © 2000 -2003, Data Access Technologies, Inc.

The new center z The strategic core of you systems must be the enterprise its self z Only technology independent business focused models will survive the transience of technology and lock-in z These models can become part of your source code, driving enterprise applications and simulations z Enabler: Model Driven Architecture (MDA) with EDOC-Enterprise Collaboration Architecture Copyright © 2000 -2003, Data Access Technologies, Inc.
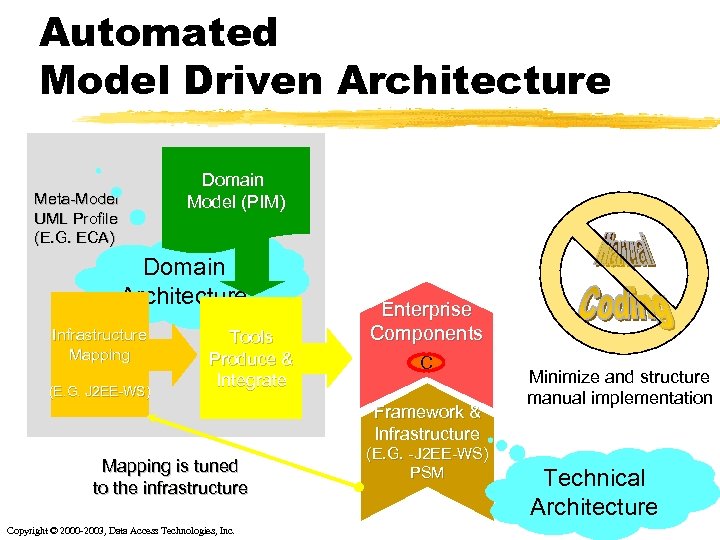
Automated Model Driven Architecture Domain Model (PIM) Meta-Model UML Profile (E. G. ECA) Domain Architecture Infrastructure Mapping (E. G. J 2 EE-WS) Tools Produce & Integrate Enterprise Components C Framework & Infrastructure Mapping is tuned to the infrastructure Copyright © 2000 -2003, Data Access Technologies, Inc. (E. G. -J 2 EE-WS) PSM Minimize and structure manual implementation Technical Architecture
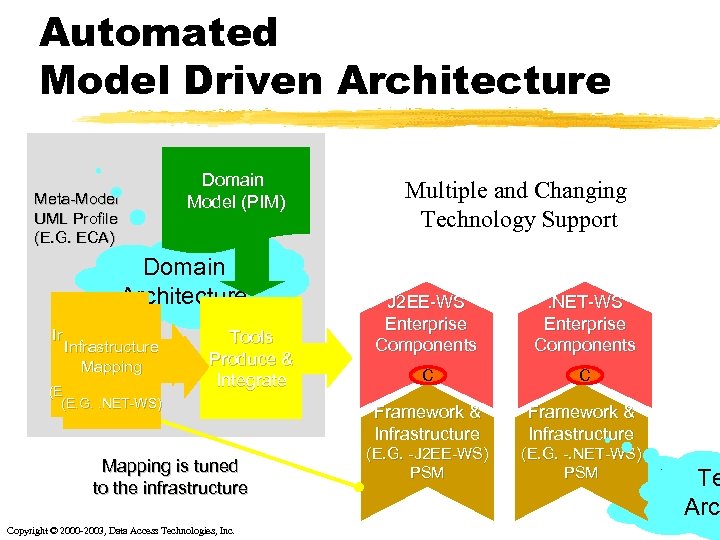
Automated Model Driven Architecture Domain Model (PIM) Meta-Model UML Profile (E. G. ECA) Domain Architecture Infrastructure Mapping (E. G. J 2 EE-WS) (E. G. . NET-WS) Tools Produce & Integrate Mapping is tuned to the infrastructure Copyright © 2000 -2003, Data Access Technologies, Inc. Multiple and Changing Technology Support J 2 EE-WS Enterprise Components C . NET-WS Enterprise Components C C Framework & Infrastructure (E. G. -J 2 EE-WS) PSM (E. G. -. NET-WS) PSM Techn Te Archite Arc
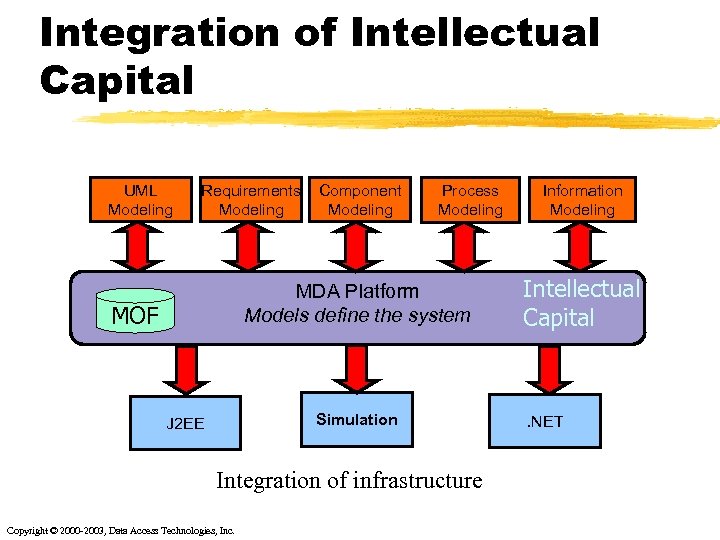
Integration of Intellectual Capital UML Modeling Requirements Modeling Component Modeling Process Modeling MDA Platform Models define the system MOF Simulation J 2 EE Integration of infrastructure Copyright © 2000 -2003, Data Access Technologies, Inc. Information Modeling Intellectual Capital . NET
The Enterprise Collaboration Architecture z ECA is a “profile of UML”, a way to use UML for a specific purpose - it is an OMG standard y That purpose is modeling enterprise systems and components. z You can also think of this as a “modeling framework” for enterprise computing z ECA is part of the “Model Driven Architecture” (MDA) initiative of the OMG y Using precise modeling techniques as part of the development lifecycle to speed development and provide technology independence z ECA has been adopted by the OMG as part of the EDOC RFP. z ECA defines an architecture and meta model Copyright © 2000 -2003, Data Access Technologies, Inc.
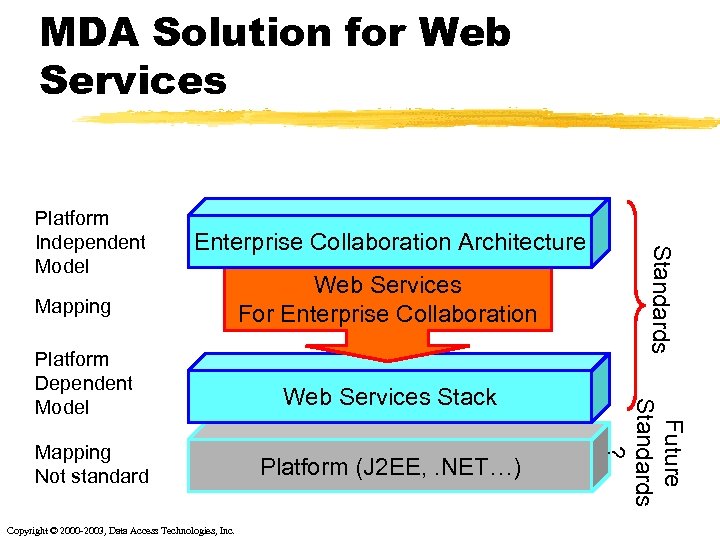
MDA Solution for Web Services Enterprise Collaboration Architecture Mapping Not standard Copyright © 2000 -2003, Data Access Technologies, Inc. Web Services Stack Platform (J 2 EE, . NET…) Future Standards ? Platform Dependent Model Web Services For Enterprise Collaboration Standards Platform Independent Model
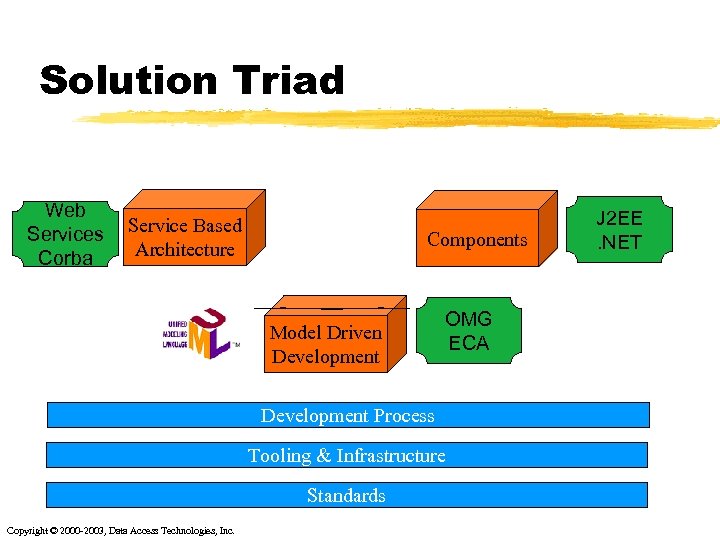
Solution Triad Web Services Corba Service Based Architecture Components Model Driven Development OMG ECA Development Process Tooling & Infrastructure Standards Copyright © 2000 -2003, Data Access Technologies, Inc. J 2 EE. NET
Loose Coupling z Loose coupling is the ability for independent parts of systems to be built and evolve independently z Tightly coupled systems y. Prevent change (the next legacy system) y. Cause lock-in y. Become unmanageable y. Prevent reuse z Quality architecture is essential for loose coupling Copyright © 2000 -2003, Data Access Technologies, Inc.

Architecture Goals z Create a system from loosely coupled “enterprise components” that can evolve independently z Provide well defined interfaces and interaction points between these enterprise components z Make each enterprise component a reusable asset that can serve many business processes z Build the information system as a community of interacting enterprise components z Utilize open standards such as Web Services, EJB and Corba to integrate the enterprise components Copyright © 2000 -2003, Data Access Technologies, Inc.
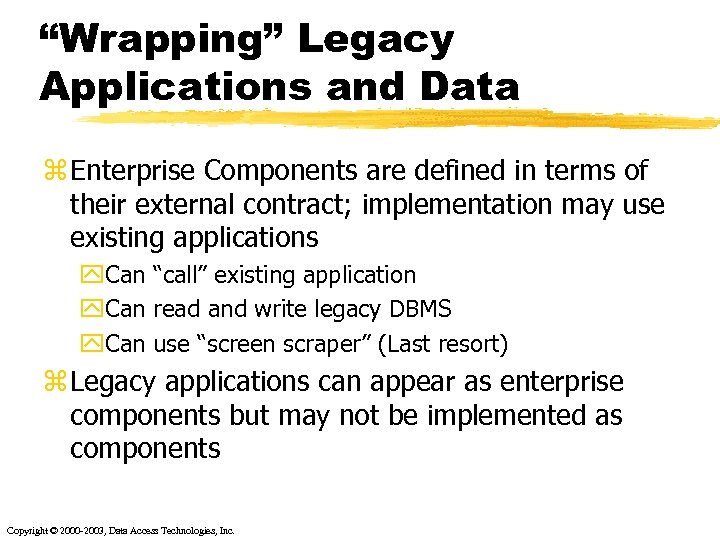
“Wrapping” Legacy Applications and Data z Enterprise Components are defined in terms of their external contract; implementation may use existing applications y. Can “call” existing application y. Can read and write legacy DBMS y. Can use “screen scraper” (Last resort) z Legacy applications can appear as enterprise components but may not be implemented as components Copyright © 2000 -2003, Data Access Technologies, Inc.
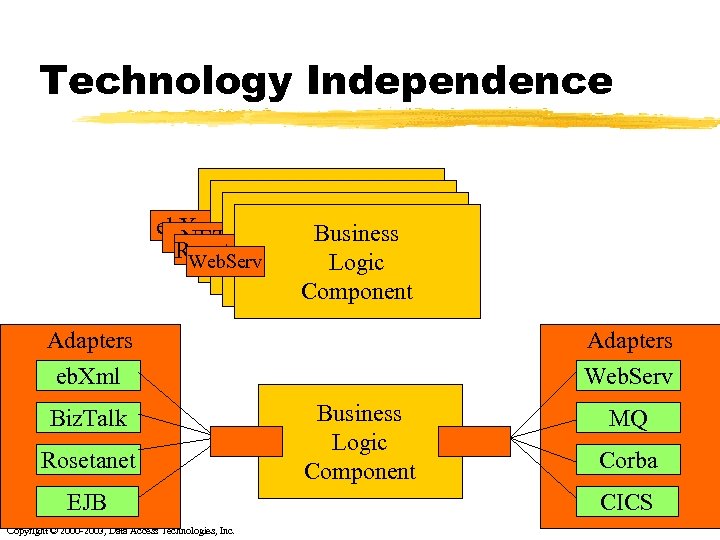
Technology Independence What the infrastructure Business vendors would Business Logic eb. Xml Business Logic. NET have you do Roseta. Net Logic Web. Serv Component Logic Component Adapters eb. Xml Biz. Talk Rosetanet EJB Copyright © 2000 -2003, Data Access Technologies, Inc. Adapters Web. Serv Business Logic Component MQ Corba CICS
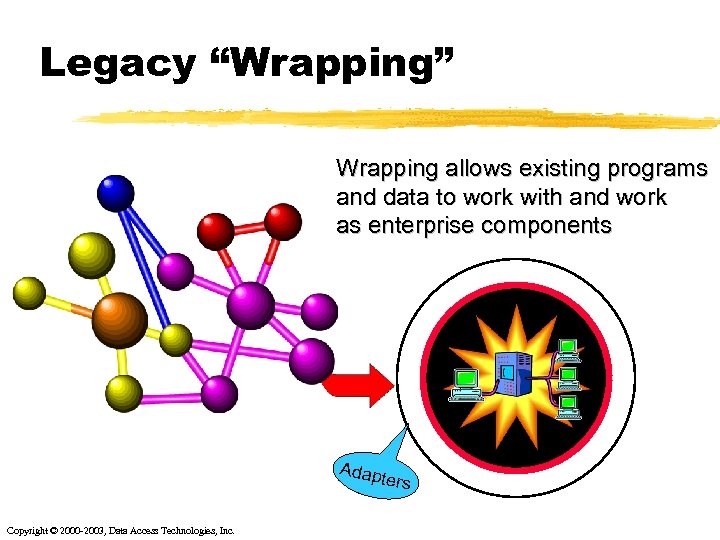
Legacy “Wrapping” Wrapping allows existing programs and data to work with and work as enterprise components Adap ters Copyright © 2000 -2003, Data Access Technologies, Inc.
Collaborations and Roles Conceptual Foundation Portions copied with permission of Trygve Reenskaug - Taskon OORAM (http: //www. ifi. uio. no/~trygver)
History OORAM Object Oriented Role Analysis UML Collaborations Influence Copyright © 2000 -2003, Data Access Technologies, Inc. Enterprise Collaboration Architecture
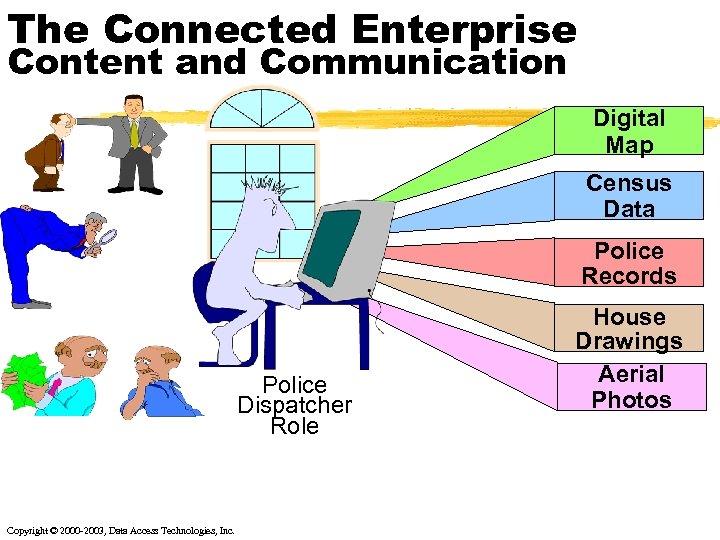
The Connected Enterprise Content and Communication Digital Map Census Data Police Records Police Dispatcher Role Copyright © 2000 -2003, Data Access Technologies, Inc. House Drawings Aerial Photos
Multiple roles in a collaboration Copyright © 2000 -2003, Data Access Technologies, Inc.
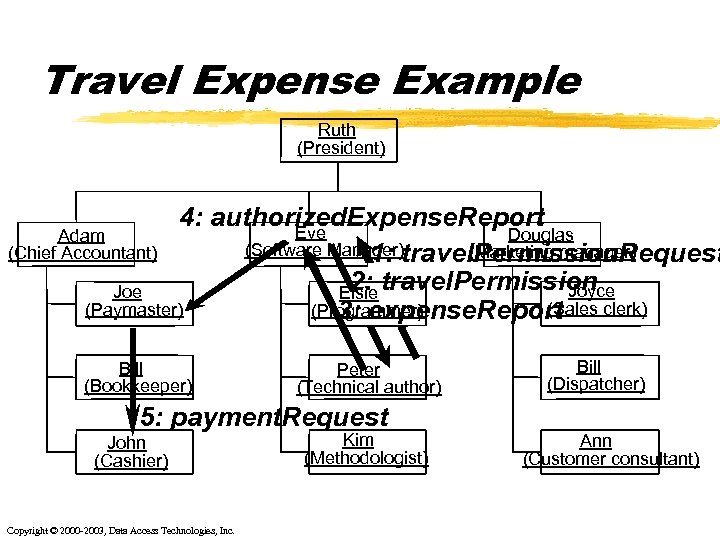
Travel Expense Example Ruth (President) 4: authorized. Expense. Report Eve Douglas Adam (Software Manager)travel. Permission. Request (Marketing manager) (Chief Accountant) 1: 2: travel. Permission Joyce Joe Elsie (Sales (Paymaster) (Programmer) 3: expense. Report clerk) Bill (Bookkeeper) Peter (Technical author) 5: payment. Request John (Cashier) Copyright © 2000 -2003, Data Access Technologies, Inc. Kim (Methodologist) Bill (Dispatcher) Ann (Customer consultant)
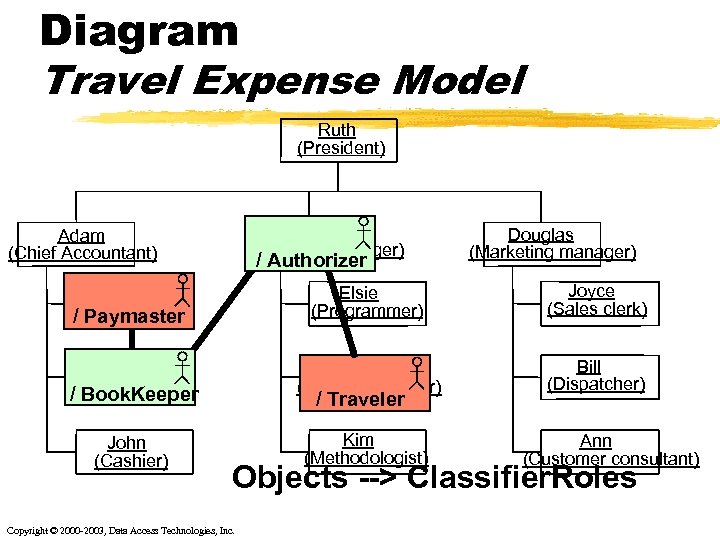
Diagram Travel Expense Model Ruth (President) Eve (Software Manager) Adam (Chief Accountant) / Authorizer Douglas (Marketing manager) Joe (Paymaster) / Paymaster Elsie (Programmer) Joyce (Sales clerk) Bill (Bookkeeper) / Book. Keeper Peter (Technical author) Bill (Dispatcher) John (Cashier) Kim (Methodologist) / Traveler Ann (Customer consultant) Objects --> Classifier. Roles Copyright © 2000 -2003, Data Access Technologies, Inc.
Collaboration Diagram Copyright © 2000 -2003, Data Access Technologies, Inc.
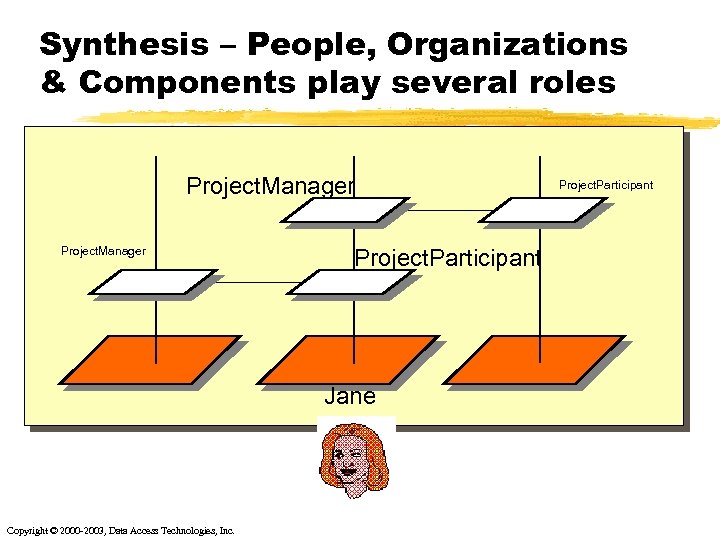
Synthesis – People, Organizations & Components play several roles Project. Manager Project. Participant Jane Copyright © 2000 -2003, Data Access Technologies, Inc. Project. Participant
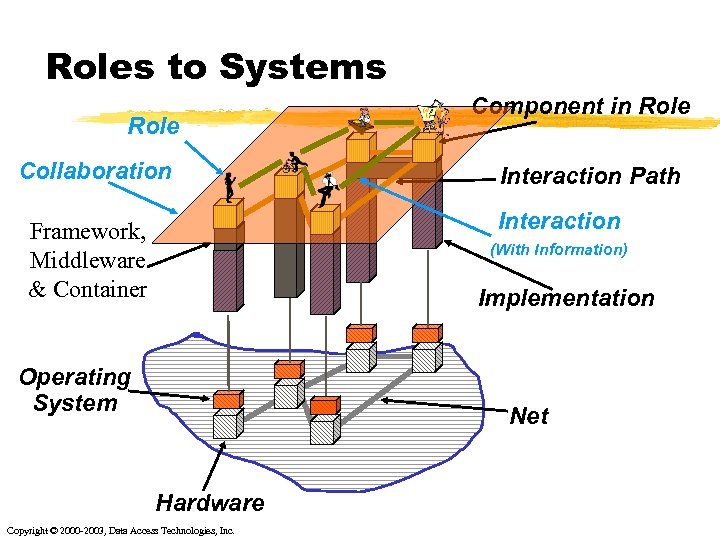
Roles to Systems Role Collaboration Component in Role Interaction Path Interaction Framework, Middleware & Container (With Information) Implementation Operating System Net Hardware Copyright © 2000 -2003, Data Access Technologies, Inc.
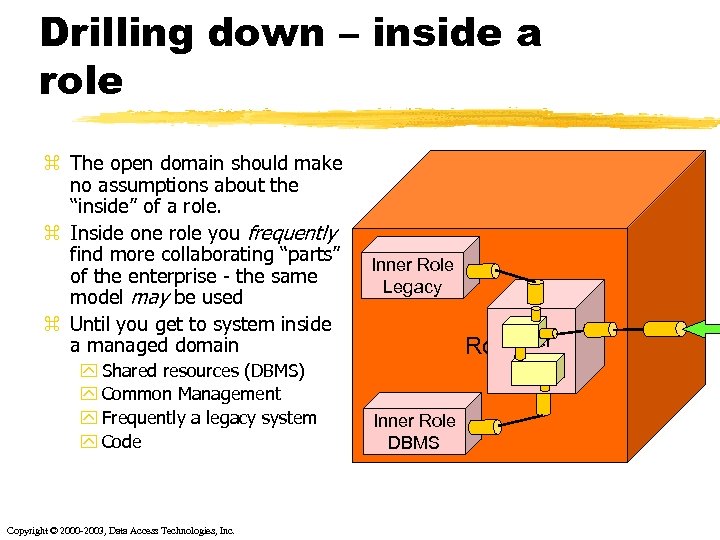
Drilling down – inside a role z The open domain should make no assumptions about the “inside” of a role. z Inside one role you frequently find more collaborating “parts” of the enterprise - the same model may be used z Until you get to system inside a managed domain y Shared resources (DBMS) y Common Management y Frequently a legacy system y Code Copyright © 2000 -2003, Data Access Technologies, Inc. Inner Role Legacy Role. Inner Role DBMS

Standards for Global Internet Computing XML EDOC. NET BPML XLANG WSDL SOAP XML-Schema

Web Service Standards z. XML Schema & DTD y. Description and packaging of data z. WSDL y. Specification a services, operations and flows available via a service z. Soap y. Basic messaging and packaging y. Extensions for Soap-RPC with WSDL Copyright © 2000 -2003, Data Access Technologies, Inc.

EDOC Component Collaboration Architecture The model of collaborative work
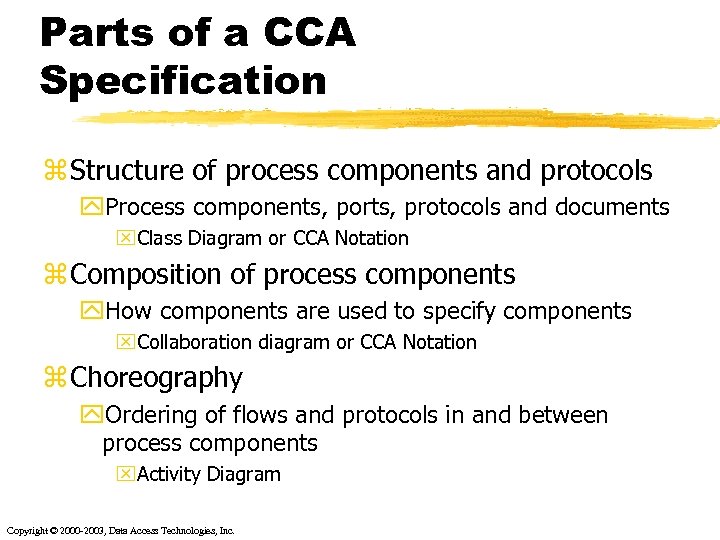
Parts of a CCA Specification z Structure of process components and protocols y. Process components, ports, protocols and documents x. Class Diagram or CCA Notation z Composition of process components y. How components are used to specify components x. Collaboration diagram or CCA Notation z Choreography y. Ordering of flows and protocols in and between process components x. Activity Diagram Copyright © 2000 -2003, Data Access Technologies, Inc.

ECA Methodology A simple methodology for creating collaborative business processes

Basic Steps z Identify roles and organize roles into collaborations z Define collaboration documents z Create basic business transactions z Organize into protocols and events z Use protocols to define ports on roles z Drill-down into role detail z Implement roles z Configure implementations for deployment with technology specifics z Deploy Copyright © 2000 -2003, Data Access Technologies, Inc.
Identifying roles and collaborations Copyright © 2000 -2003, Data Access Technologies, Inc.
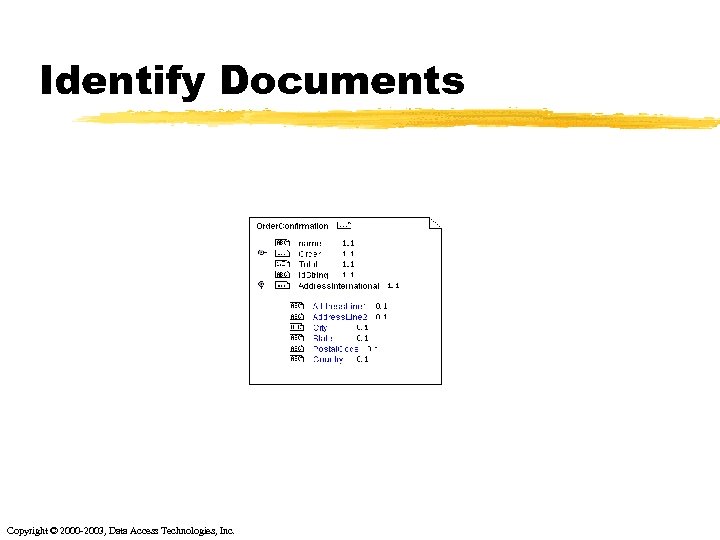
Identify Documents Copyright © 2000 -2003, Data Access Technologies, Inc.
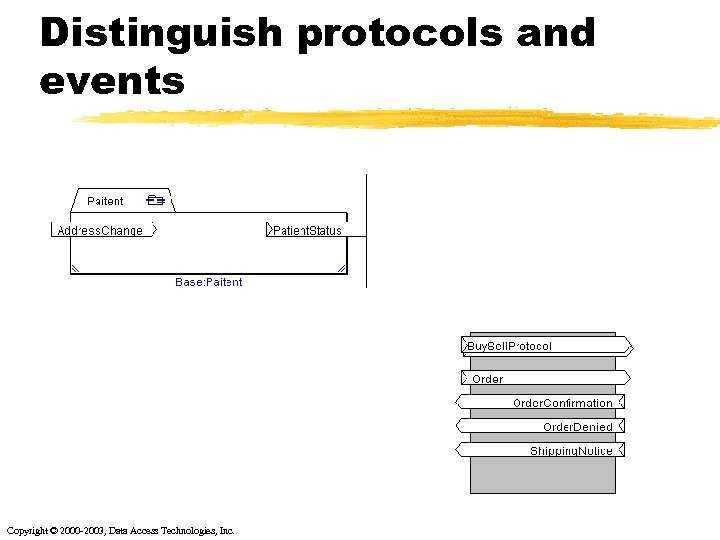
Distinguish protocols and events Copyright © 2000 -2003, Data Access Technologies, Inc.
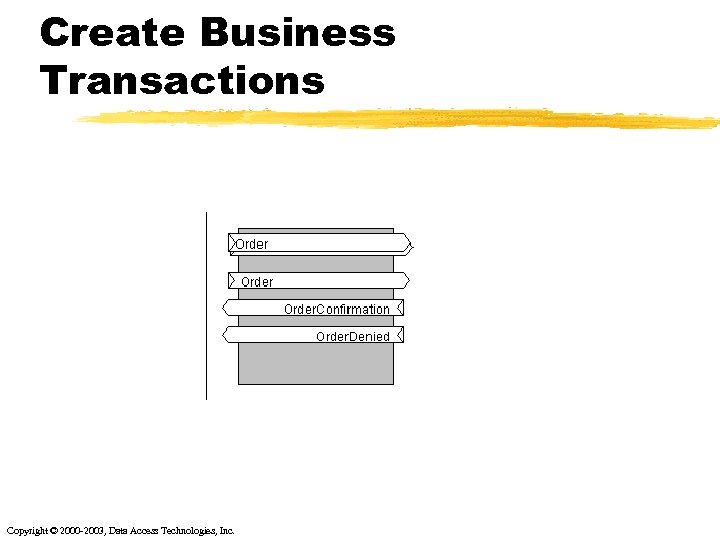
Create Business Transactions Copyright © 2000 -2003, Data Access Technologies, Inc.
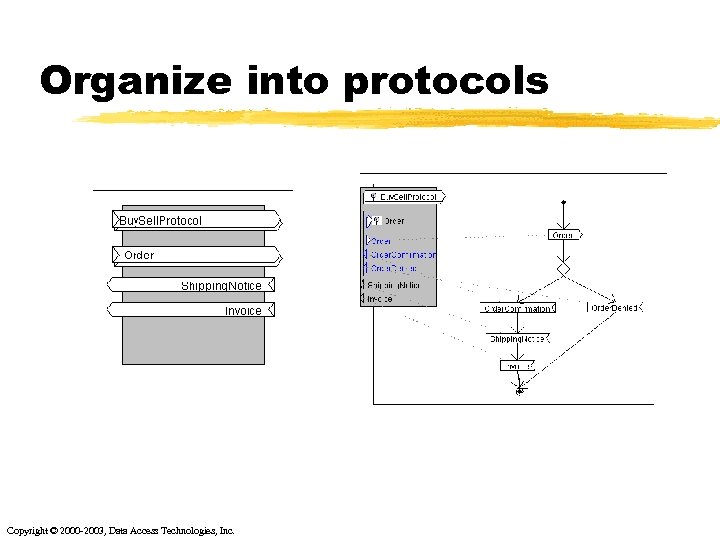
Organize into protocols Copyright © 2000 -2003, Data Access Technologies, Inc.
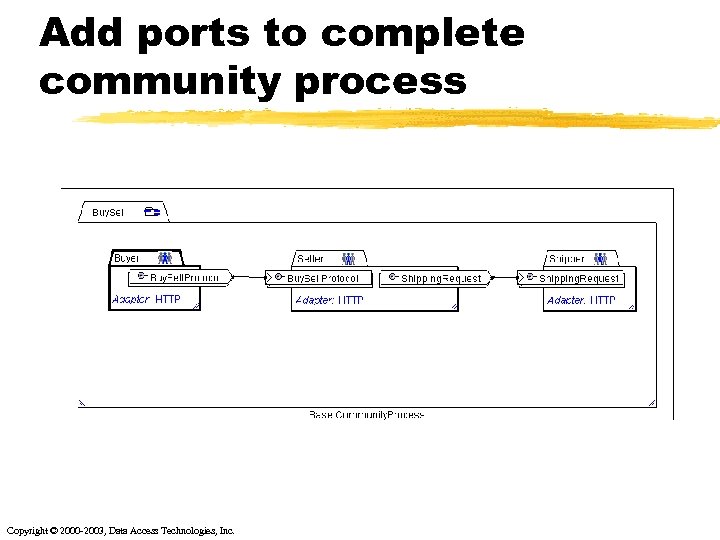
Add ports to complete community process Copyright © 2000 -2003, Data Access Technologies, Inc.
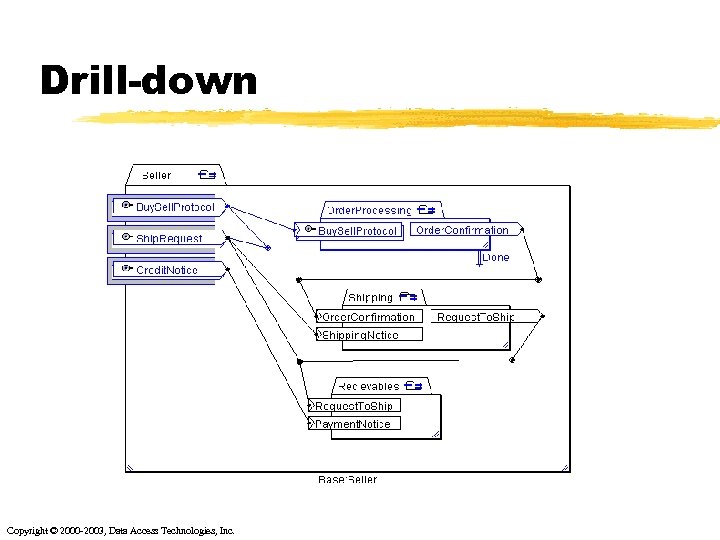
Drill-down Copyright © 2000 -2003, Data Access Technologies, Inc.
Add implementation z. As component compositions z. In a programming language z. By using an external service z. Wrap legacy z. As a simulation Copyright © 2000 -2003, Data Access Technologies, Inc.
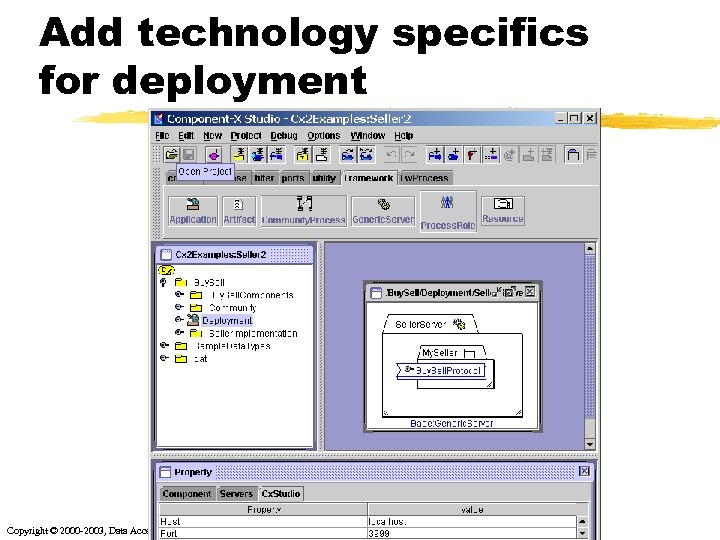
Add technology specifics for deployment Copyright © 2000 -2003, Data Access Technologies, Inc.

WSEC Web Services for Enterprise Collaboration In standards process
Main Parts z Distributed Component Profile y. How to define & structure distributed components z Aspects y. How to augment a model for a technology z Aspects defined for WSDL/Schema y. The augmentations required for Web Services z Mapping y. Transformations between ECA and WSDL/Schema Copyright © 2000 -2003, Data Access Technologies, Inc.
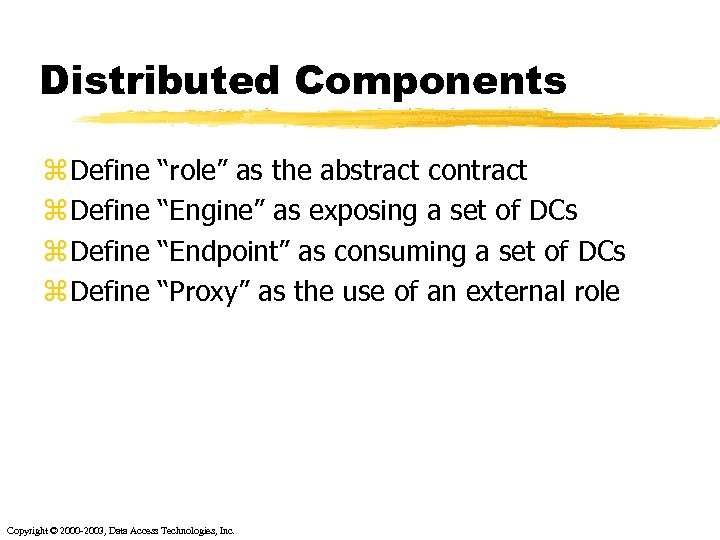
Distributed Components z Define “role” as the abstract contract “Engine” as exposing a set of DCs “Endpoint” as consuming a set of DCs “Proxy” as the use of an external role Copyright © 2000 -2003, Data Access Technologies, Inc.
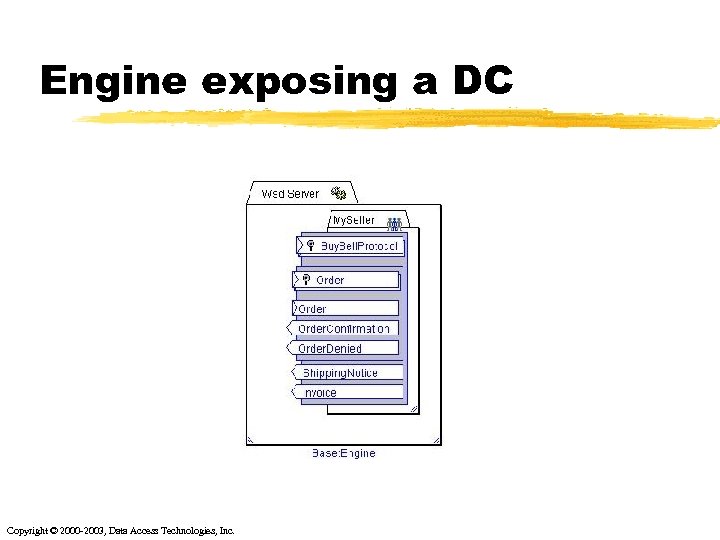
Engine exposing a DC Copyright © 2000 -2003, Data Access Technologies, Inc.
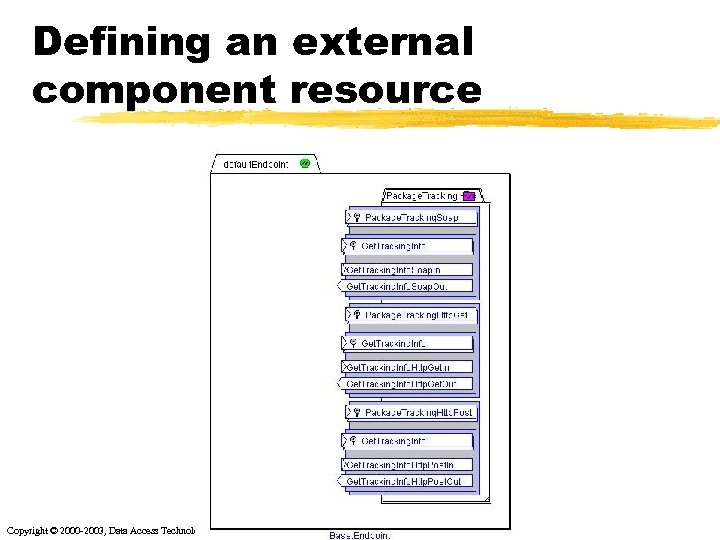
Defining an external component resource Copyright © 2000 -2003, Data Access Technologies, Inc.
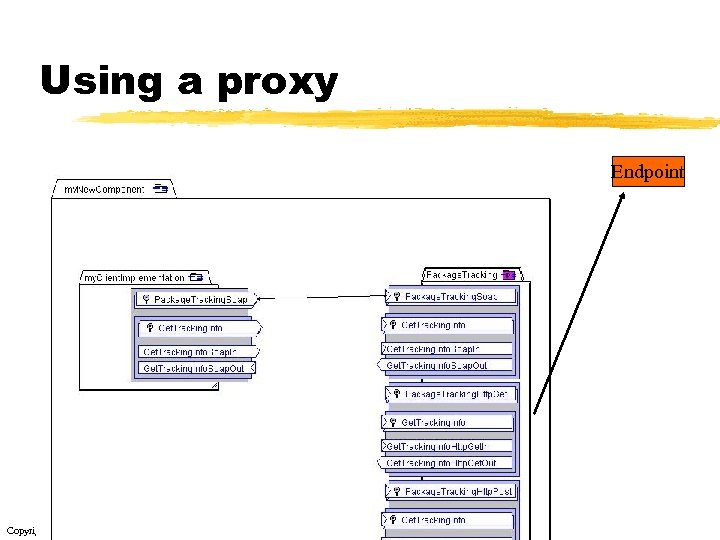
Using a proxy Endpoint Copyright © 2000 -2003, Data Access Technologies, Inc.
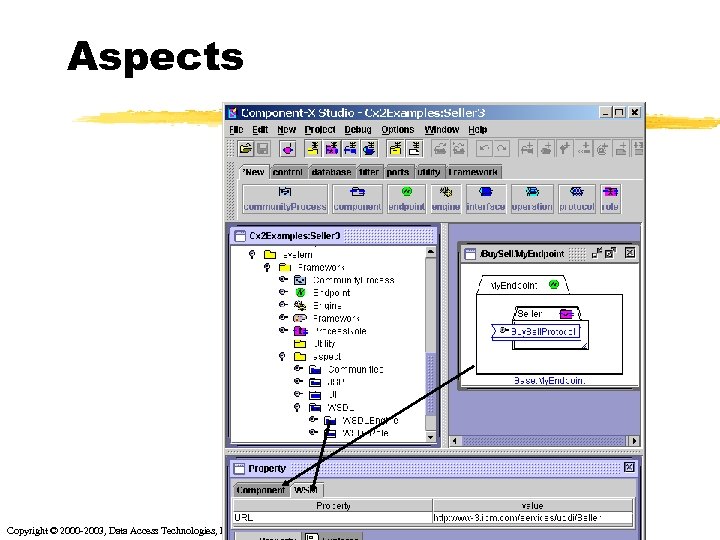
Aspects Copyright © 2000 -2003, Data Access Technologies, Inc.
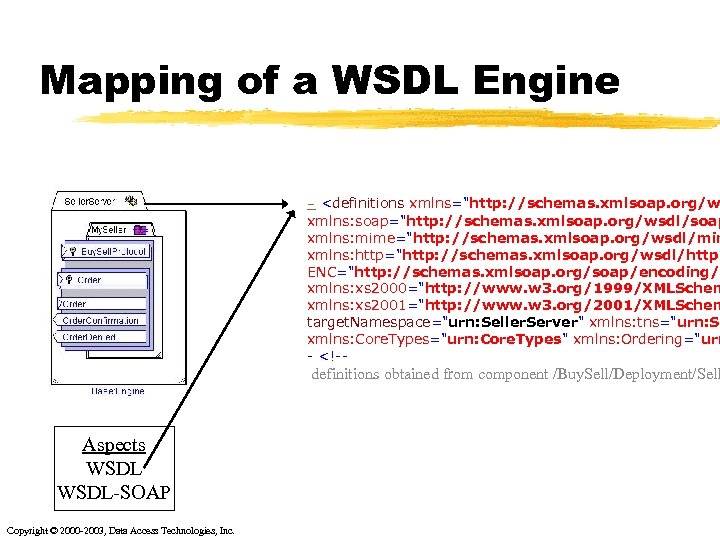
Mapping of a WSDL Engine - <definitions xmlns="http: //schemas. xmlsoap. org/w xmlns: soap="http: //schemas. xmlsoap. org/wsdl/soap xmlns: mime="http: //schemas. xmlsoap. org/wsdl/mim xmlns: http="http: //schemas. xmlsoap. org/wsdl/http/ ENC="http: //schemas. xmlsoap. org/soap/encoding/" xmlns: xs 2000="http: //www. w 3. org/1999/XMLSchem xmlns: xs 2001="http: //www. w 3. org/2001/XMLSchem target. Namespace="urn: Seller. Server" xmlns: tns="urn: Se xmlns: Core. Types="urn: Core. Types" xmlns: Ordering="urn - <!-- definitions obtained from component /Buy. Sell/Deployment/Sell Aspects WSDL-SOAP Copyright © 2000 -2003, Data Access Technologies, Inc.
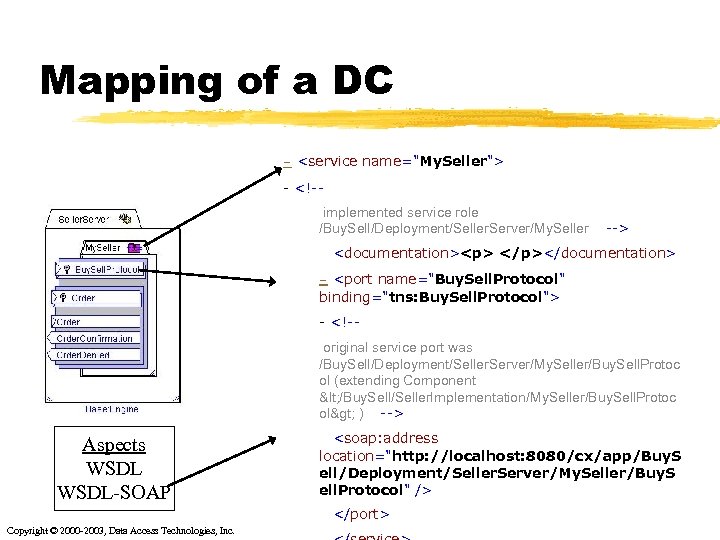
Mapping of a DC - <service name="My. Seller"> - <!-implemented service role /Buy. Sell/Deployment/Seller. Server/My. Seller --> <documentation><p> </p></documentation> - <port name="Buy. Sell. Protocol" binding="tns: Buy. Sell. Protocol"> - <!-original service port was /Buy. Sell/Deployment/Seller. Server/My. Seller/Buy. Sell. Protoc ol (extending Component < /Buy. Sell/Seller. Implementation/My. Seller/Buy. Sell. Protoc ol> ) --> Aspects WSDL-SOAP <soap: address location="http: //localhost: 8080/cx/app/Buy. S ell/Deployment/Seller. Server/My. Seller/Buy. S ell. Protocol" /> </port> Copyright © 2000 -2003, Data Access Technologies, Inc.
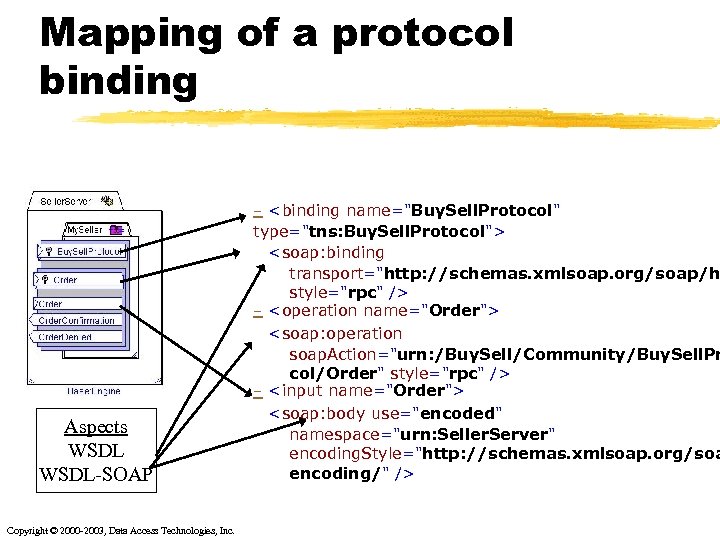
Mapping of a protocol binding Aspects WSDL-SOAP Copyright © 2000 -2003, Data Access Technologies, Inc. - <binding name="Buy. Sell. Protocol" type="tns: Buy. Sell. Protocol"> <soap: binding transport="http: //schemas. xmlsoap. org/soap/h style="rpc" /> - <operation name="Order"> <soap: operation soap. Action="urn: /Buy. Sell/Community/Buy. Sell. Pr col/Order" style="rpc" /> - <input name="Order"> <soap: body use="encoded" namespace="urn: Seller. Server" encoding. Style="http: //schemas. xmlsoap. org/soa encoding/" />
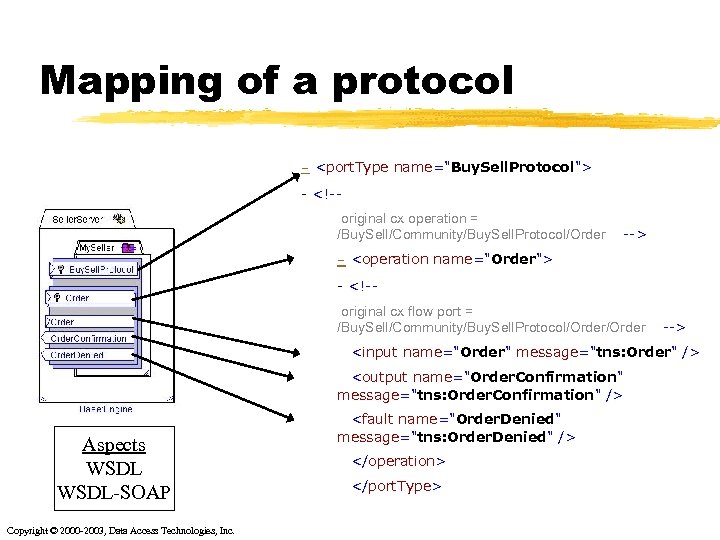
Mapping of a protocol - <port. Type name="Buy. Sell. Protocol"> - <!-original cx operation = /Buy. Sell/Community/Buy. Sell. Protocol/Order --> - <operation name="Order"> - <!-original cx flow port = /Buy. Sell/Community/Buy. Sell. Protocol/Order --> <input name="Order" message="tns: Order" /> <output name="Order. Confirmation" message="tns: Order. Confirmation" /> Aspects WSDL-SOAP Copyright © 2000 -2003, Data Access Technologies, Inc. <fault name="Order. Denied" message="tns: Order. Denied" /> </operation> </port. Type>
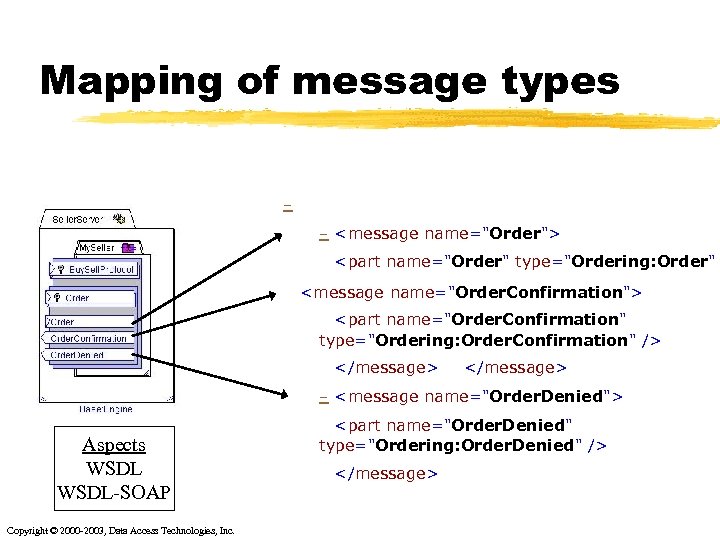
Mapping of message types - <message name="Order"> <part name="Order" type="Ordering: Order" <message name="Order. Confirmation"> <part name="Order. Confirmation" type="Ordering: Order. Confirmation" /> </message> - <message name="Order. Denied"> Aspects WSDL-SOAP Copyright © 2000 -2003, Data Access Technologies, Inc. <part name="Order. Denied" type="Ordering: Order. Denied" /> </message>
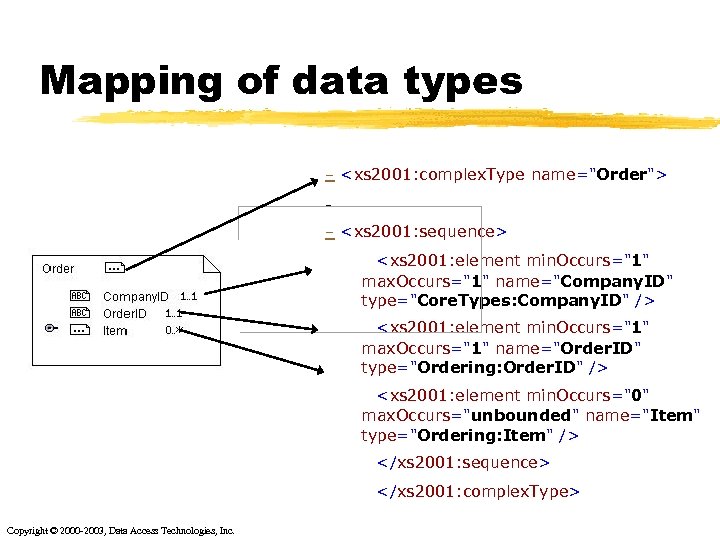
Mapping of data types - <xs 2001: complex. Type name="Order"> - - <xs 2001: sequence> <xs 2001: element min. Occurs="1" max. Occurs="1" name="Company. ID" type="Core. Types: Company. ID" /> <xs 2001: element min. Occurs="1" max. Occurs="1" name="Order. ID" type="Ordering: Order. ID" /> <xs 2001: element min. Occurs="0" max. Occurs="unbounded" name="Item" type="Ordering: Item" /> </xs 2001: sequence> </xs 2001: complex. Type> Copyright © 2000 -2003, Data Access Technologies, Inc.
Ways to map z Generate code and other artifacts y Usually required to adapt to legacy y Emulates the manual process z Assemble and configure existing generic and specific components y Both efficient and dynamic z Interpret or otherwise “animate” the high-level model y High level & dynamic but may have performance issues z Simulate y Evaluate technical and business impact through simulation Copyright © 2000 -2003, Data Access Technologies, Inc.
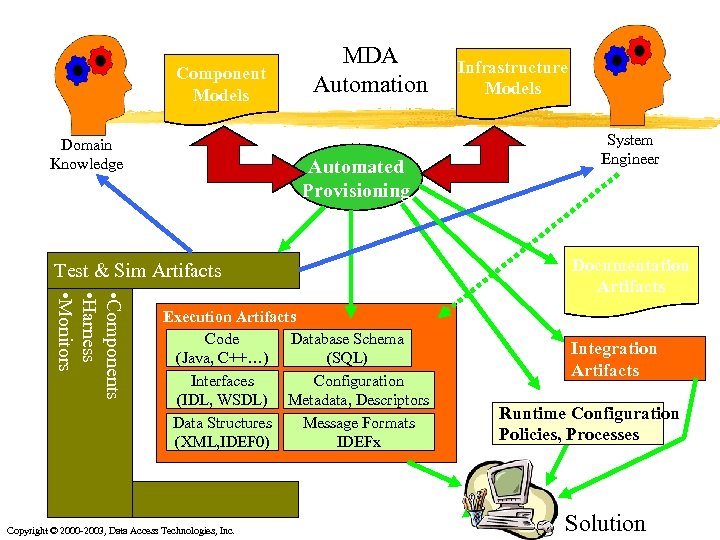
Component Models Domain Knowledge MDA Automation Automated Provisioning Test & Sim Artifacts • Components • Harness • Monitors Execution Artifacts Code Database Schema (Java, C++…) (SQL) Interfaces Configuration (IDL, WSDL) Metadata, Descriptors Data Structures Message Formats (XML, IDEF 0) IDEFx Copyright © 2000 -2003, Data Access Technologies, Inc. Infrastructure Models System Engineer Documentation Artifacts Integration Artifacts Runtime Configuration Policies, Processes Solution
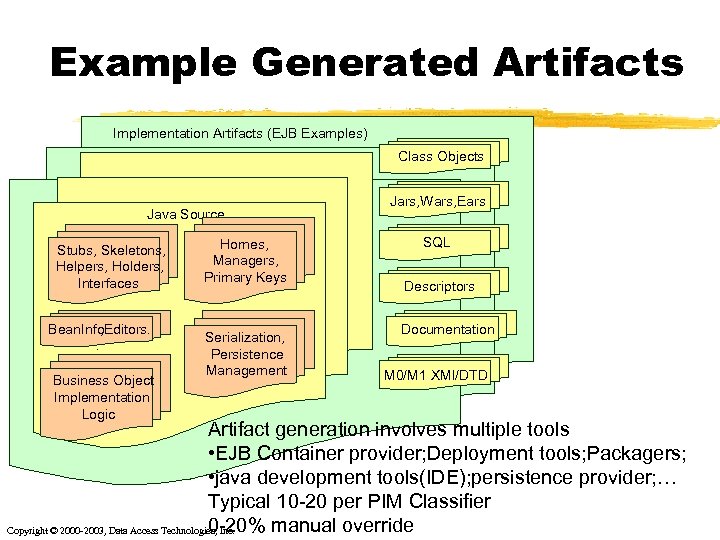
Example Generated Artifacts Implementation Artifacts (EJB Examples) Class Objects Java Source Stubs, Skeletons, Helpers, Holders, Interfaces Bean. Info , Editors. . Business Object Implementation Logic Homes, Managers, Primary Keys Serialization, Persistence Management Jars, Wars, Ears SQL Descriptors Documentation M 0/M 1 XMI/DTD Artifact generation involves multiple tools • EJB Container provider; Deployment tools; Packagers; • java development tools(IDE); persistence provider; … Typical 10 -20 per PIM Classifier 0 -20% manual override Copyright © 2000 -2003, Data Access Technologies, Inc.
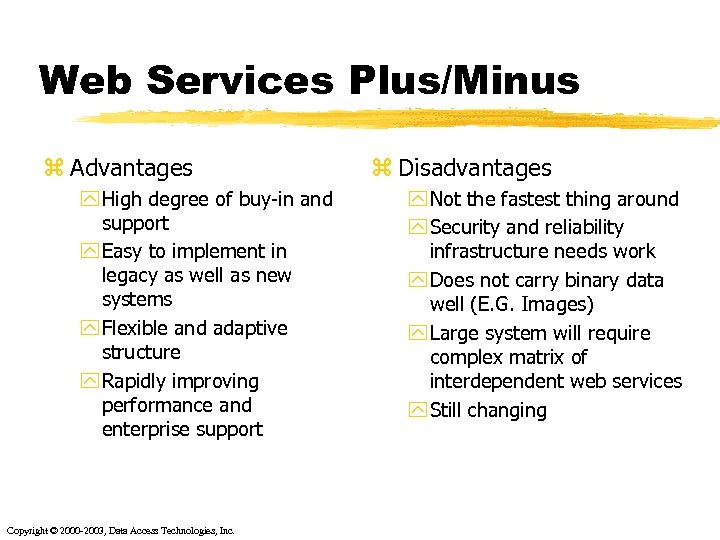
Web Services Plus/Minus z Advantages y High degree of buy-in and support y Easy to implement in legacy as well as new systems y Flexible and adaptive structure y Rapidly improving performance and enterprise support Copyright © 2000 -2003, Data Access Technologies, Inc. z Disadvantages y Not the fastest thing around y Security and reliability infrastructure needs work y Does not carry binary data well (E. G. Images) y Large system will require complex matrix of interdependent web services y Still changing
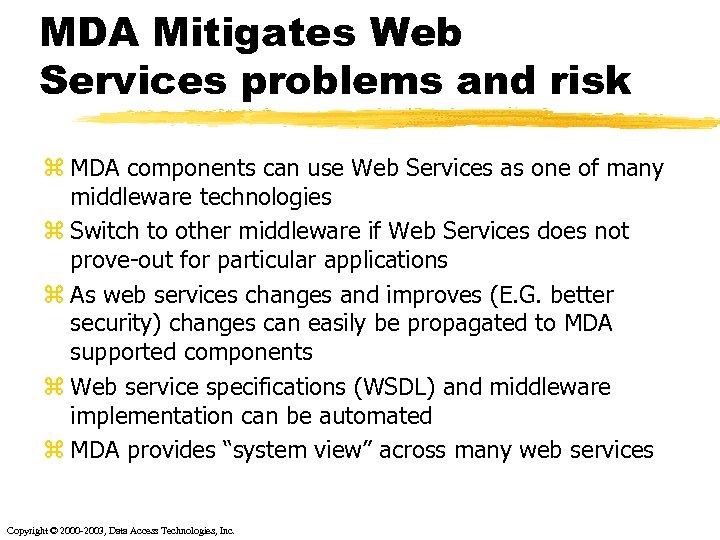
MDA Mitigates Web Services problems and risk z MDA components can use Web Services as one of many middleware technologies z Switch to other middleware if Web Services does not prove-out for particular applications z As web services changes and improves (E. G. better security) changes can easily be propagated to MDA supported components z Web service specifications (WSDL) and middleware implementation can be automated z MDA provides “system view” across many web services Copyright © 2000 -2003, Data Access Technologies, Inc.

GSA Enterprise Model Example Thanks to George Thomas Enterprise Architect General Services Administration
![[4] GSA PIM Copyright © 2000 -2003, Data Access Technologies, Inc. [4] GSA PIM Copyright © 2000 -2003, Data Access Technologies, Inc.](https://present5.com/presentation/a99ce56793aa669c06817bb86021dcdb/image-71.jpg)
[4] GSA PIM Copyright © 2000 -2003, Data Access Technologies, Inc.
![[4] GSA PIM Copyright © 2000 -2003, Data Access Technologies, Inc. [4] GSA PIM Copyright © 2000 -2003, Data Access Technologies, Inc.](https://present5.com/presentation/a99ce56793aa669c06817bb86021dcdb/image-72.jpg)
[4] GSA PIM Copyright © 2000 -2003, Data Access Technologies, Inc.
![[4] FEA Inheritance Copyright © 2000 -2003, Data Access Technologies, Inc. [4] FEA Inheritance Copyright © 2000 -2003, Data Access Technologies, Inc.](https://present5.com/presentation/a99ce56793aa669c06817bb86021dcdb/image-73.jpg)
[4] FEA Inheritance Copyright © 2000 -2003, Data Access Technologies, Inc.
![[4] FEA base. Role Copyright © 2000 -2003, Data Access Technologies, Inc. [4] FEA base. Role Copyright © 2000 -2003, Data Access Technologies, Inc.](https://present5.com/presentation/a99ce56793aa669c06817bb86021dcdb/image-74.jpg)
[4] FEA base. Role Copyright © 2000 -2003, Data Access Technologies, Inc.
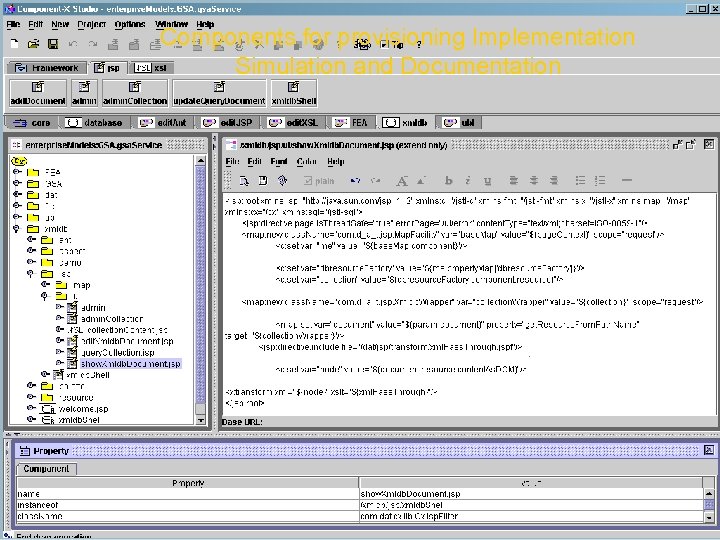
Components provisioning Implementation Frameworksforas OO Design Simulation and Documentation Patterns Copyright © 2000 -2003, Data Access Technologies, Inc.
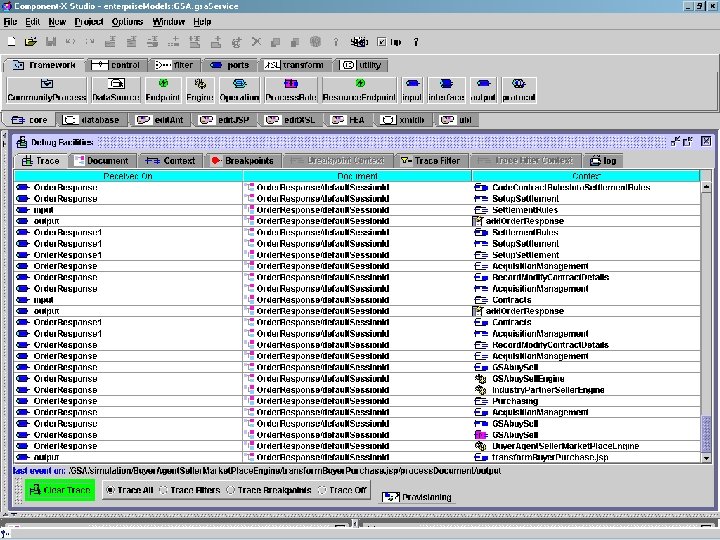
GSA Process Model Trace z. Next few slides are screen shots from Live Simulation of a notional ‘to-be’ GSA EA model in Component-X, which traces through each and every component in the business collaborations that have been modeled Copyright © 2000 -2003, Data Access Technologies, Inc.
Model-driven UI for submitting a UBL Order Copyright © 2000 -2003, Data Access Technologies, Inc.
trace population Copyright © 2000 -2003, Data Access Technologies, Inc.
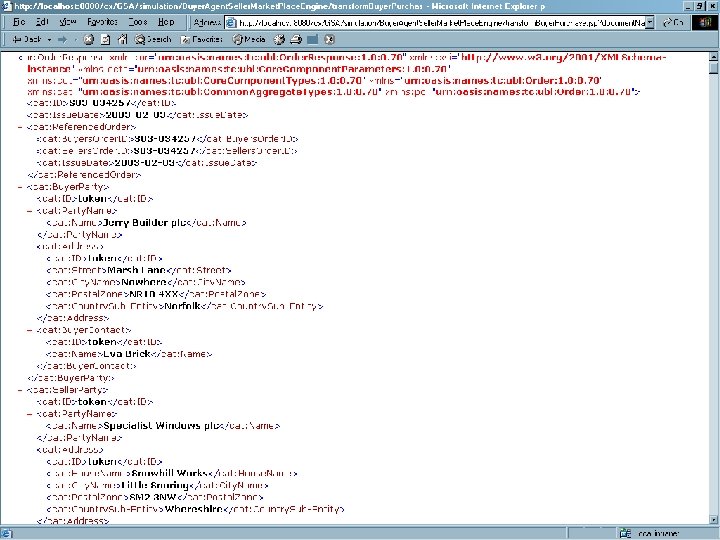
The UBL Order. Response Copyright © 2000 -2003, Data Access Technologies, Inc.
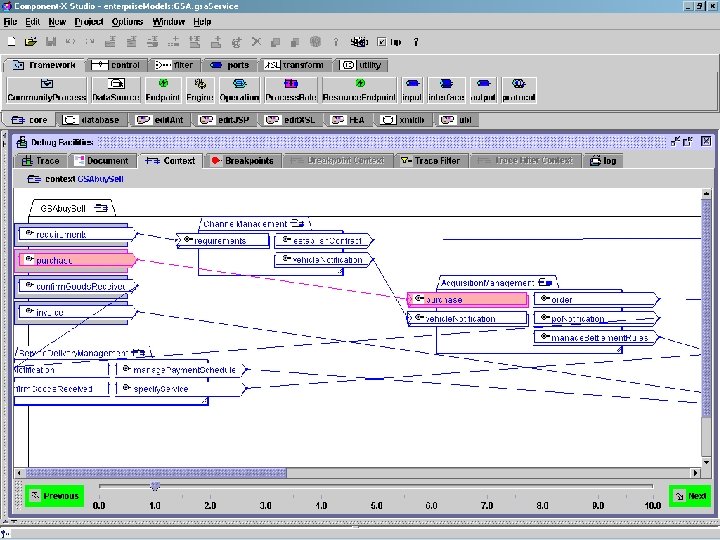
GSABuy. Sell component context Copyright © 2000 -2003, Data Access Technologies, Inc.
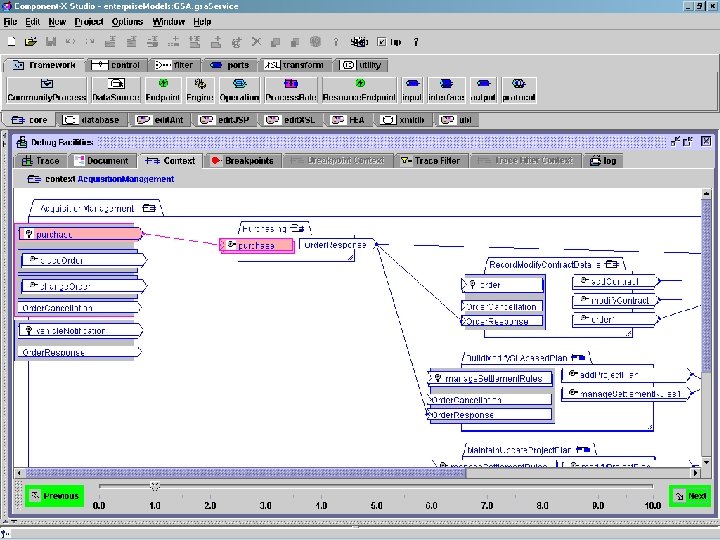
view of ‘recursive decomposition’ Copyright © 2000 -2003, Data Access Technologies, Inc.
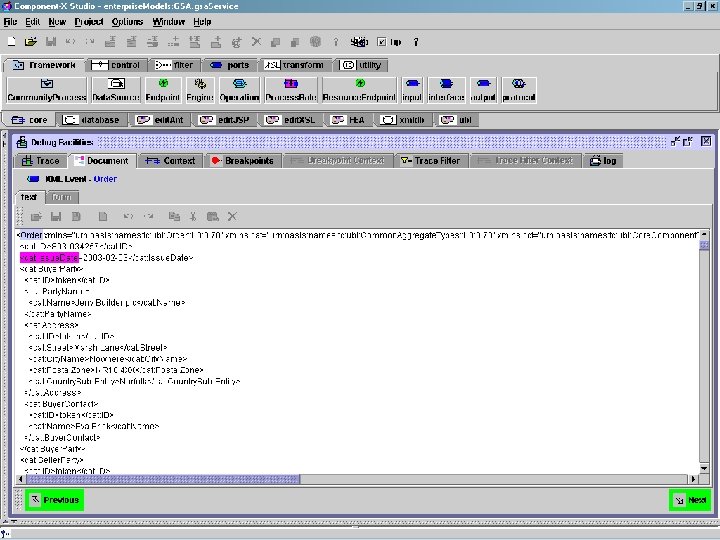
in-context UBL Order data Copyright © 2000 -2003, Data Access Technologies, Inc.
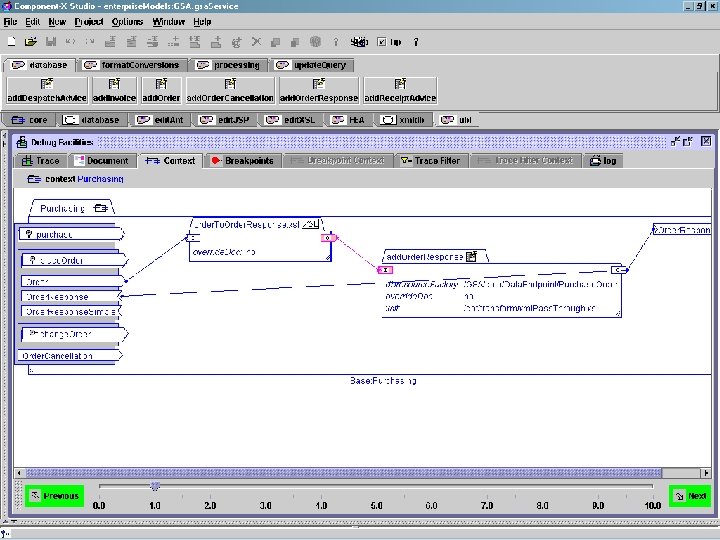
Purchasing component context Copyright © 2000 -2003, Data Access Technologies, Inc.
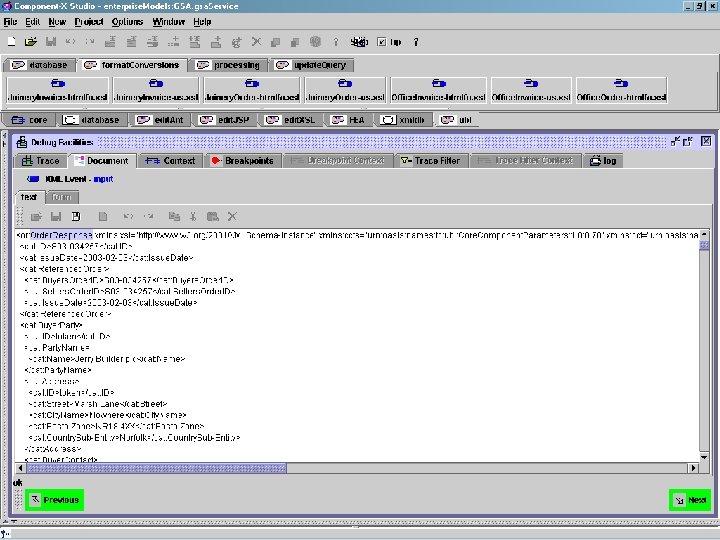
in-context UBL Order. Response data Copyright © 2000 -2003, Data Access Technologies, Inc.
FOP generated performance_trace. pdf Copyright © 2000 -2003, Data Access Technologies, Inc.
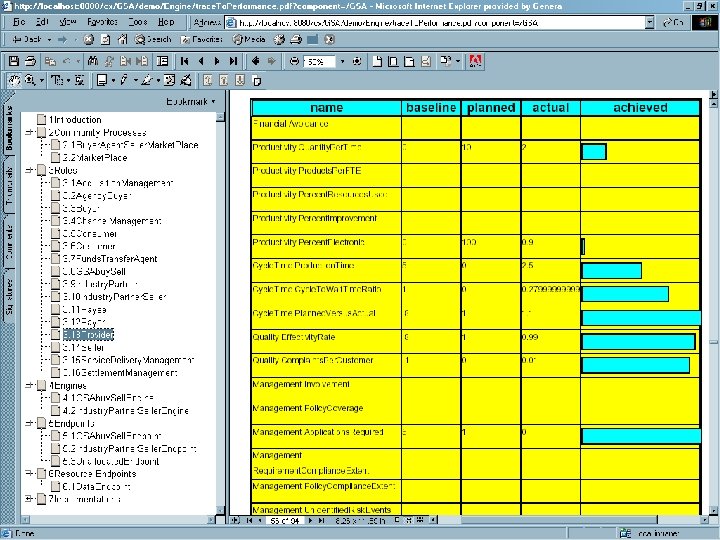
B-P-A-A as ABM input Copyright © 2000 -2003, Data Access Technologies, Inc.
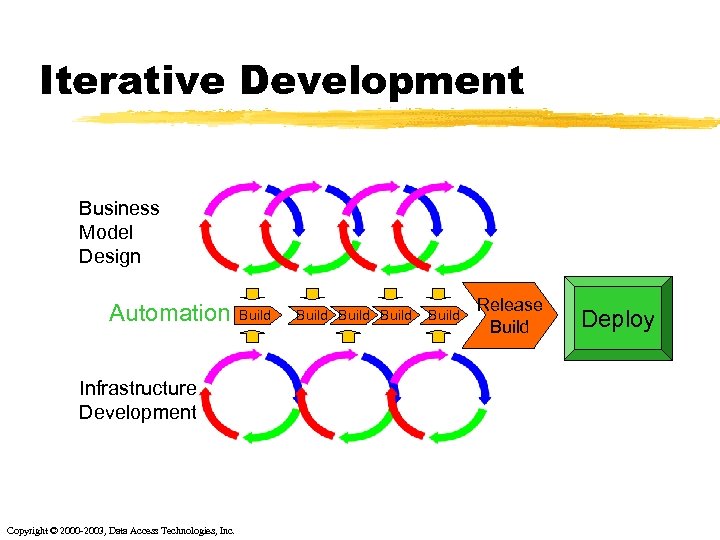
Iterative Development Business Model Design Automation Infrastructure Development Copyright © 2000 -2003, Data Access Technologies, Inc. Build Build Release Build Deploy
Net effect z Using these open standards and automated techniques we can; y. Achieve the strategic advantage of an open and flexible enterprise y. Produce and/or integrate these systems FASTER and CHEAPER than could be done with legacy techniques y. Provide a lasting asset that will outlive the technology of the day z Integration of modeling, simulation and executable systems Copyright © 2000 -2003, Data Access Technologies, Inc.
a99ce56793aa669c06817bb86021dcdb.ppt