5ae639fc92ccab2ba7df037655f6c582.ppt
- Количество слайдов: 46

Web Service and Security Lilly Wang 1

Agenda n Brief introduction to web service Web service security n Wireless web service n 2

Software Evolution n Main frame based n Two-Tier Client Server n Web-based N-tier Client Server n Web centric highly distributed system 3

Web Service Basics 4

What is web service? n n Self contained Self described (WSDL) Interoperable standard interfaces Dynamically discovered (UDDI) 5

Web Service Characteristics n Openly accessible over Internet n Use XML messages for communication n Loosely-coupled architecture n Involve one or more intermediaries n Heterogeneous in implementation technologies 6
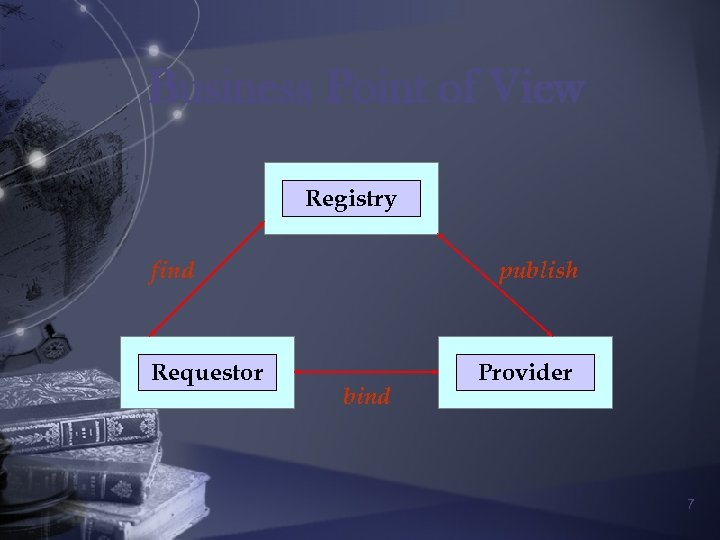
Business Point of View Registry find Requestor publish bind Provider 7
Developer’s Point of View n How to achieve interoperability n How to transport data n How to achieve high performance Web service can be any piece of software that makes itself available over the Internet using standardized web service messaging system and interface 8
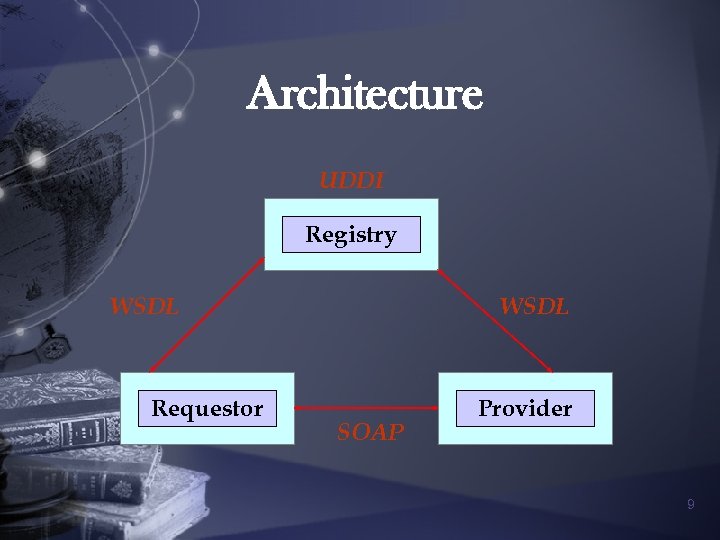
Architecture UDDI Registry WSDL Requestor WSDL SOAP Provider 9

SOAP n Simple Object Access Protocol n Original used for RPC n High-level protocol that defines only the message structure and a few simple rules for message processing n Data packed inside SOAP message for transporting over the network n http: //www. w 3. org/TR/2000/NOTE-SOAP-20000508/ 10

WSDL n Web Service Description Language n Service description component n A specification for describing a service provided or searching n http: //www. w 3. org/TR/2001/NOTE-wsdl- 20010315 11

UDDI n Universal Description Discovery Integration n A technical spec for business registry n Data stored in standardized XML format n APIs for searching n UDDI Business Registry is a fully operational implementation of the UDDI spec n http: //www. oreillynet. com/lpt/a//webservices/2002/02 /12/webservicefaqs. html 12

Types of Web services n Remote Procedure Call (RPC) type Call parameters and return values are serialized in SOAP messages. Data types are supported by XML schema. n Document messaging (DOC) type Operate in asynchronous mode. Similar to mailing lists robots. Good for mobile. 13

Web Service Security 14

Security Basics n n n Authentication Access Control Authorization Data Integrity Non-repudiation 15

Basic Security Mechanism n n n Symmetric/Asymmetric Key Encryption Message Digest Message Authentication Codes (MAC) Digital Signature Digital Certificate 16

Web Service Security Technologies n X. 509 Certificate (RFC 2585) n SSL/TLS (RFC 2246) n Kerberos Tickets (RFC 1510) n XML Signature (http: //www. xml. com/pub/a/2001/08/08/xmldsig. html) n XML Encryption (http: //www. aleksey. com/xmlsec/) n XML-based security token (SAML format ) (http: //www. aleksey. com/xmlsc/) 17

Web Service Security Challenges n SOAP messages can be sent using different transport applications or protocols n There could be legitimate intermediaries that might need to access a part or whole of SOAP messages 18
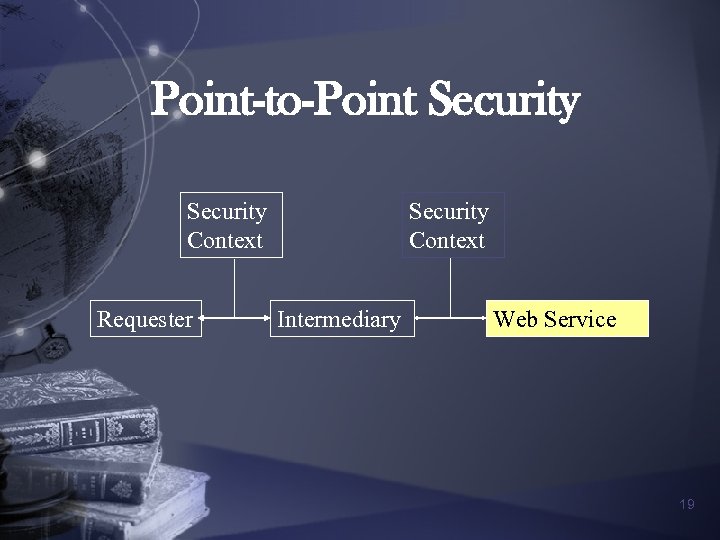
Point-to-Point Security Context Requester Security Context Intermediary Web Service 19
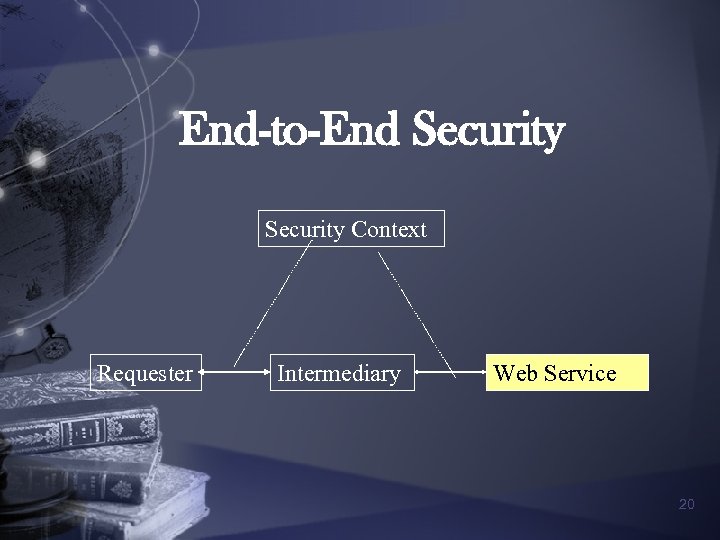
End-to-End Security Context Requester Intermediary Web Service 20

Proposed Security Specification Initial Specifications n n WS-Security WS-Policy WS-Trust WS-Privacy Follow-on Specifications n WS-Secure. Conversation n WS-Federation n WS-Authorization 21

WS-Security n is the foundation for all of the other specs n provides end-to-end message-level security for SOAP messages n defines a SOAP Header element to carry security-related data n Security. Token defined under <Security> tag, containing <Usename. Token> and <Binary. Security. Token> 22

WS-Security n Message integrity is provided by XML Signature and security tokens n Message confidentiality is provided by XML Encryption with security tokens 23
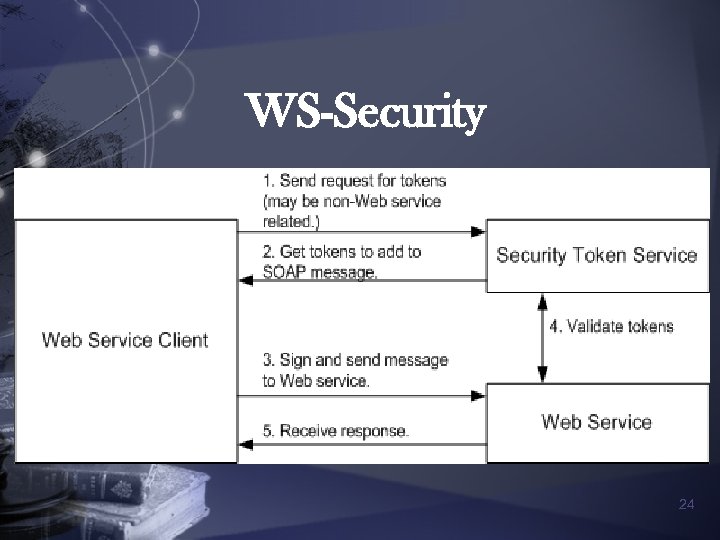
WS-Security 24

WS-Policy Specify how senders and receivers agree on the security requirements and capabilities n <Security. Token> - what type, which issuer n <Integrity> - options for digital signature n <Confidentiality> - options for encryption algorithm n <Visibility> - Which portion of the message must be unencrypted 25

WS-Trust The model for establishing both direct and brokered trust relationship n Defines a way to use SOAP to talk to a KDC, CA or any other security token service center n Use <Request. Security. Token> and <Request. Security. Token. Response> elements 26

n WS-Privacy – defines the privacy policies, such as ACL and delegation n WS-Secure. Conversation – defines XML types and interactions that allows a the establishment of a security context and the creation of keys that are specific to that context 27

n WS-Federation – defines how to construct federated trust among different securitytoken service centers n WS-Authorization – describes how access policies for a web service are specified and managed 28
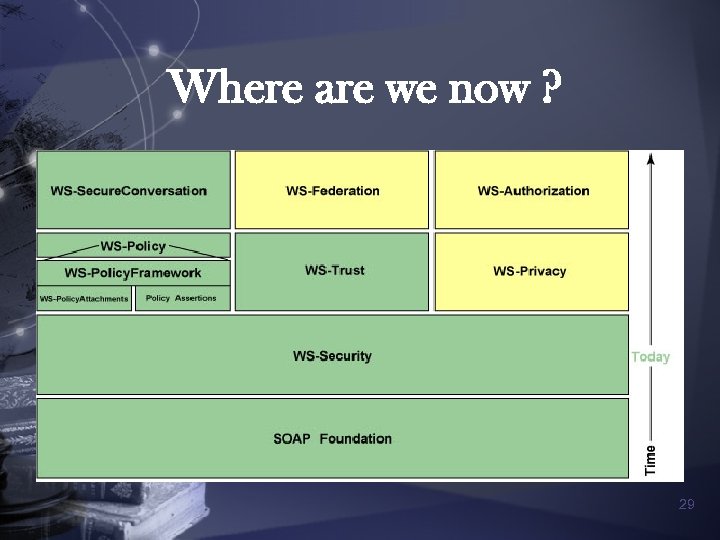
Where are we now ? 29

Wireless Web Service 30

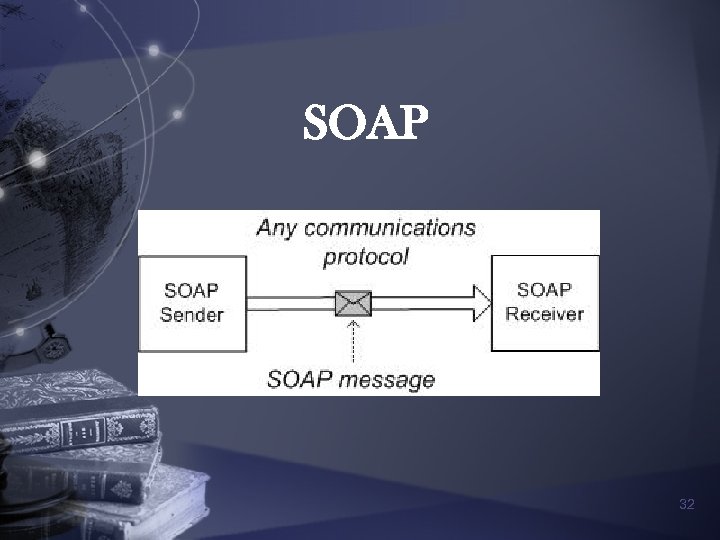
SOAP n Light-weighted protocol n Exchange structured information in a decentralized, distributed environment n Use XML as message framework n Interoperable among different system 31
SOAP 32

Why SOAP ? n Provide rich data types (more than 40) n Support various messaging schemes n Bind with other protocols/standards 33
Java APIs for XML n Document-oriented • JAXP • JAXB n Procedure-oriented • JAX-RPC • JAXM • JAXR 34
JAXP n Java APIs for XML Processing n XML Parser n Support XSLT n Include Ø SAX Parser (event-based parser) Ø DOM Parser (tree-based) 35
JAXB n Java Architecture for XML Binding n Provide mapping between XML documents and Java objects n Based on XML Schema/DTD to build Java Object 36
JAXP vs JAXB Use JAXB when • Access data in memory, but do not need tree manipulation capabilities • Process only data that is valid • Convert data to different types • Generate classes based on a DTD • Build object representations of XML data. 37
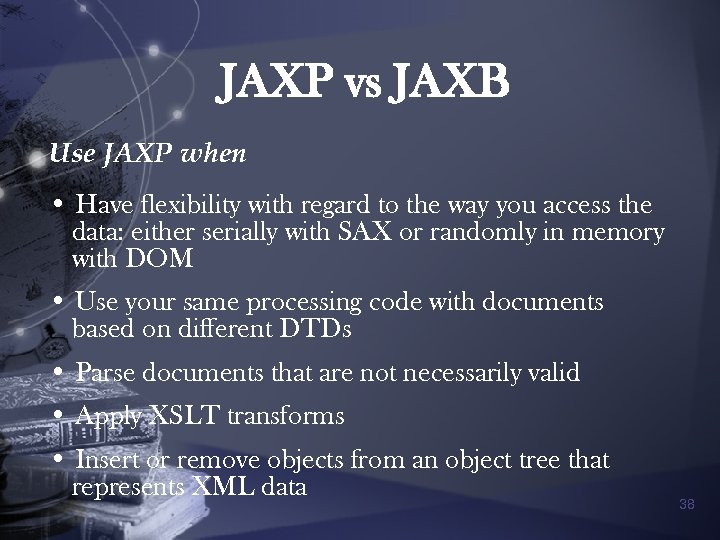
JAXP vs JAXB Use JAXP when • Have flexibility with regard to the way you access the data: either serially with SAX or randomly in memory with DOM • Use your same processing code with documents based on different DTDs • Parse documents that are not necessarily valid • Apply XSLT transforms • Insert or remove objects from an object tree that represents XML data 38

JAXM n Java API for XML Messaging n SAAJ (SOAP with Attachments API for Java) 1. 1 is the javax. xml. soap package for creating SOAP messages, adding message content, and extracting message content. n JAXM 1. 1 is the javax. xml. messaging package for using a messaging provider and to send one-way messages. It is always used in conjunction with the SAAJ 1. 1 API. 39

JAXR n Java. TM API for XML Registries n provides a convenient way to access standard business registries over the Internet. 40

JAX-RPC n Java™ API for XML-based RPC n Is a collection of procedures that can be called by a remote client over the Internet n Supports SOAP 1. 2 and WSDL 41

What you need for J 2 ME Web Service ? Server Side n Apache Axis ( for SOAP parsing) n Web Service tool kit ( e. e WSDK) Client Side n k. SOAP / JSR 172 n Wireless Toolkit 42

k. SOAP n A parser based on k. XML n k. SOAP 1. 2 supports SOAP 1. 2 43

JSR 172 n Provide subset of JAXP n Provide subset of JAX-RPC n Will be released on summer, 2003 44

Wireless Web Service Security ? n Just start n Simple XML digital signature can be done n Need to use third-party APIs 45
![Reference [1] http: //www. javaworld. com/javaworld/jw-08 -2002/jw-0823 wireless. html [2]http: //www 106. ibm. com/developerworks/webservices/library/wssec Reference [1] http: //www. javaworld. com/javaworld/jw-08 -2002/jw-0823 wireless. html [2]http: //www 106. ibm. com/developerworks/webservices/library/wssec](https://present5.com/presentation/5ae639fc92ccab2ba7df037655f6c582/image-46.jpg)
Reference [1] http: //www. javaworld. com/javaworld/jw-08 -2002/jw-0823 wireless. html [2]http: //www 106. ibm. com/developerworks/webservices/library/wssec 1. html? dwzone=webservices [3]http: //www 106. ibm. com/developerworks/webservices/library ws-secroad/? dwzone=webservices [4] http: //msdn. microsoft. com/library/default. asp? url=/library/enus/dnwssecur/html/securitywhitepaper. asp 46
5ae639fc92ccab2ba7df037655f6c582.ppt