ecaa7a40476ebc5b43034b82ac01839f.ppt
- Количество слайдов: 23

Web Security Sandy Kutin CSPP 532 8/7/01

Web security: an overview z Company wants to build web site y Online purchasing y Requests for service or support y Viewing data files online z How do we make this process secure? y Confidentiality y Authentication z Usual answer: cryptography
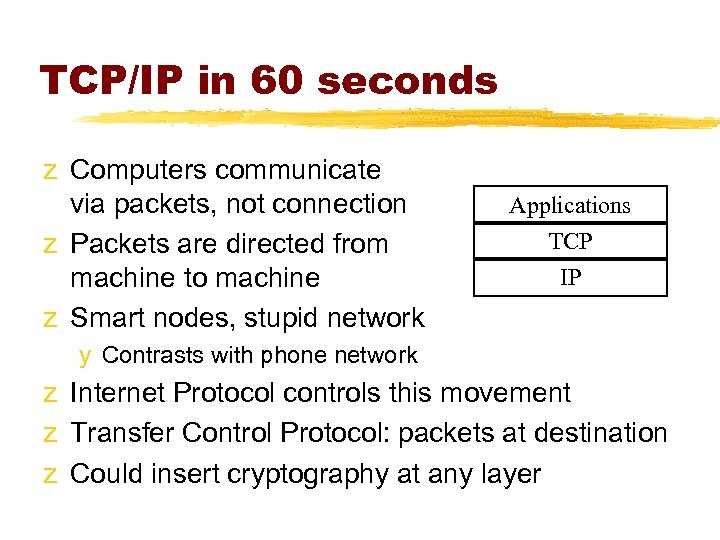
TCP/IP in 60 seconds z Computers communicate via packets, not connection z Packets are directed from machine to machine z Smart nodes, stupid network Applications TCP IP y Contrasts with phone network z Internet Protocol controls this movement z Transfer Control Protocol: packets at destination z Could insert cryptography at any layer
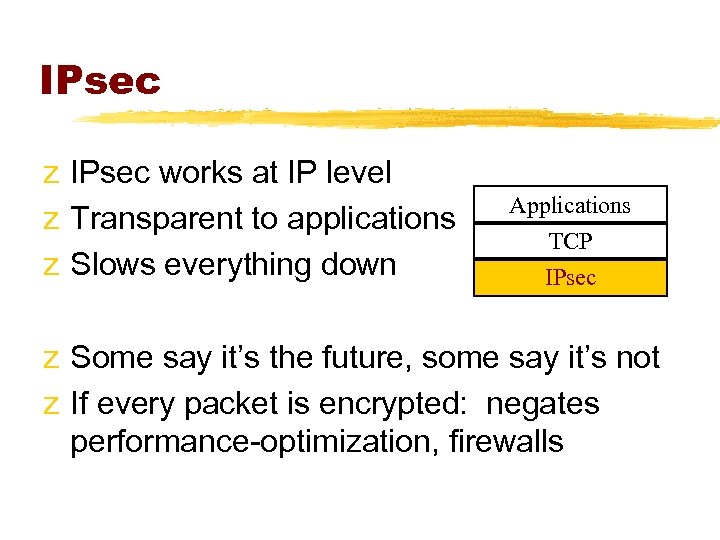
IPsec z IPsec works at IP level z Transparent to applications z Slows everything down Applications TCP IPsec z Some say it’s the future, some say it’s not z If every packet is encrypted: negates performance-optimization, firewalls
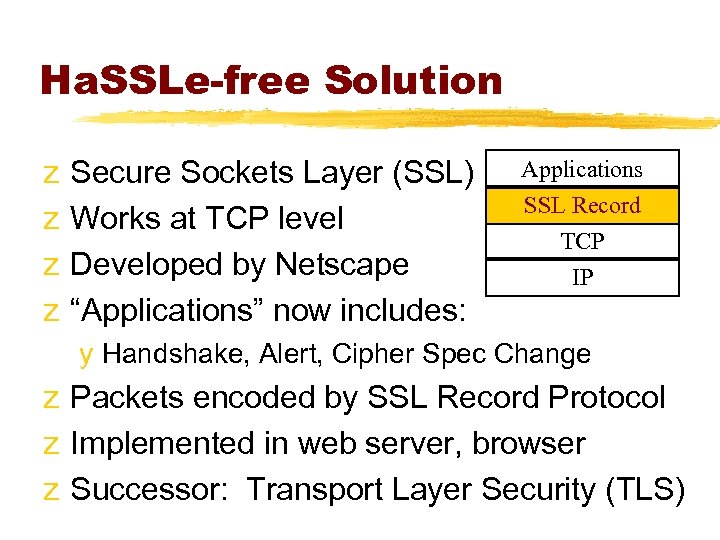
Ha. SSLe-free Solution z z Secure Sockets Layer (SSL) Works at TCP level Developed by Netscape “Applications” now includes: Applications SSL Record TCP IP y Handshake, Alert, Cipher Spec Change z Packets encoded by SSL Record Protocol z Implemented in web server, browser z Successor: Transport Layer Security (TLS)

Lo. SSLess Communication z SSL Record Protocol: y 1. Fragment data into blocks; can compress y 2. Append MAC to each block: x MAC = H(K | pad 2 | H(K | pad 1 | info | data)) x H could be MD 5 or SHA-1; similar to HMAC x info includes sequencing, length information y 3. Encrypt each block (symmetric) y 4. Append header, send fragment

Busine. SSLike Handshake z How do we establish a session key? y 1. Client says “hello”: version, random number y 2. Server says “hello”: same, includes key exchange method, optional certificate y 3. Client initiates key exchange (may just generate master, send it using RSA) y 4. Both sides compute various keys from master, random numbers in hello messages y 5. Confirmation messages

Helple. SSLy Hoping z So, does SSL secure our site? z Confidential, authenticated transactions are important, but not the only issue z Threat model: who might attack, and how y Steal customer data (credit cards) y Steal private corporate data y Deface web site y Denial of Service: prevent us from working z SSL has nothing to do with any of these

Trial Separation z How do we keep corporate data secure? z Solution: keep it separate z Only mix information when you have to: use a floppy, or a laptop z Partial solution: restrict web server’s access privileges (e. g. , firewall, DMZ) z OK if data flow is mostly to the server z What about credit card numbers?
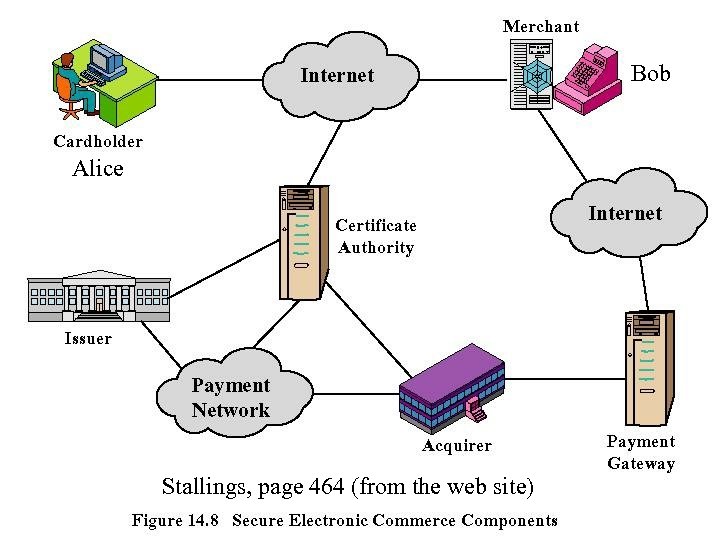
Bob Alice Stallings, page 464 (from the web site)
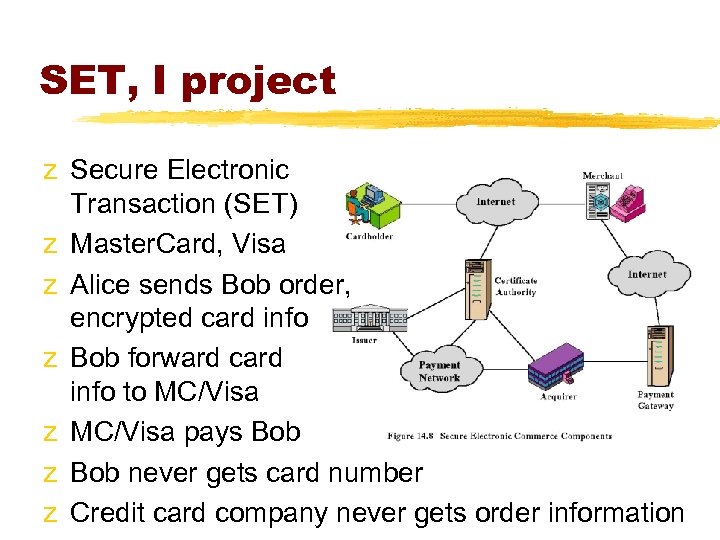
SET, I project z Secure Electronic Transaction (SET) z Master. Card, Visa z Alice sends Bob order, encrypted card info z Bob forward card info to MC/Visa z MC/Visa pays Bob z Bob never gets card number z Credit card company never gets order information

Building a Better Mou. SETrap z z z z OI = order info (include time), OIMD = H(OI) PI = payment info (& time), PIMD = H(PI) Alice signs (OIMD | PIMD) (SHA-1, RSA) Alice sends Bob OI, ECC(PI), PIMD, sig S Bob compute OIMD, checks signature S Bob sends OIMD, ECC(PI), S to MC/Visa They decrypt, check PI, check signature S They transfer funds, Bob ships item to Alice

Improving our Mind. SET z Think outside the box y Q: How do we store credit card numbers? y A: Store them so we can’t read them z Application-level solutions: harder to implement, but better targeted to problems z Cryptography is only part of the solution z Any system can be broken z Build a threat model, measure costs

Breaking and Entering z Enemy could break in y Could corrupt data (deface web site) y Could steal data (including passwords) y Could gain control of system z z Firewalls help, but there’s always a way in Keep data separate whenever possible Educate users about viruses, Trojan horses Install patches as often as you can

Intruder Alert z Home security: locks stop easy attacks z Better: door, window alarms y (as long as they don’t go through the walls) z Even better: motion detectors z Alarms don’t stop anything directly, but they alert the authorities z Fear of alarms forces criminals to hurry, make mistakes

Law and Order z Deterrent to robbery: fear of prosecution z After a crime, police gather fingerprints, DNA, eyewitnesses z Not aimed at stopping crime or recovering goods, but at punishing criminals z Hard to do in computer crime; criminals often minors or foreign nationals

Intrusion Detection z No matter what systems and protocols we use, people will break in if they want z Hard to defend against determined teenagers with nothing else to do z Solution: monitor system, detect intrusions, watch for unusual activity z Honeypots: trap intruders z Gather evidence; maybe prosecute z At the very least, close off the holes

Denial of Service Attacks z One approach: break in, crash the server z Another: flood the server with bad requests z Distributed Denial of Service (DDo. S): y Take over PCs around the country/world y Use them to overload a site z Only solution: have hardware routers detect bad packets z Almost impossible; Windows XP may make it worse

Here’s looking at you, Ki. DDo. S z In the real world: to attack, you have to put yourself at risk. Not on the Internet. z In the real world: attackers must learn skills. Not on the Internet. z One person discovers a hole, writes a script; now “script kiddies” can use it z Patches don’t work. Attackers will always be ahead of users. z Beta testing doesn’t uncover security holes

Gibson Research Corporation z Steve Gibson’s GRC. com: security z Attacked, repeatedly, by DDo. Ss. No defense. “Nothing more than the whim of a 13 -year old hacker is required to knock any user, site, or server right off the Internet. ” z Solution: Distributed Responsibility z Owners responsible for their machines z ISPs responsible for their routers z Software writers responsible for bugs

EXPensive Problem z Attackers usually spoof source IP addresses, to conceal their location z Easy to do in UNIX (as root) z Not possible in Windows 9 x/ME, but possible in Windows 2000/XP z Microsoft says: we’re fixing a bug z Gibson says: there’s no legitimate reason home users would need this feature

Bruce Schneier: Counterpane z Author of “Applied Cryptography” z Feels only monitoring, intrusion detection, active response can do any good z Counterpane. com: corporate security z Solution: Insurance z Insure against damages from attacks z Lower rates for following good practices

Recommended Reading z Secret-sharing: y Schneier, Sections 3. 7, 23. 2 z SSL, SET: Stallings, Chapter 14 z General security: y Stallings, Chapters 15 -16 y www. grc. com/dos/ y www. counterpane. com
ecaa7a40476ebc5b43034b82ac01839f.ppt