e68e03c1ed8d6adf75965027ebc7cec8.ppt
- Количество слайдов: 49

Web Privacy with P 3 P Lorrie Faith Cranor P 3 P Specification Working Group Chair AT&T Labs-Research July 2002 http: //lorrie. cranor. org/

Part I: The online privacy landscape Lorrie Faith Cranor • http: //lorrie. cranor. org/
Outline Part I: The online privacy landscape n Web privacy concerns «Surveys n How do they get my Data? «Browser chatter «Cookies 101 «Online and offline merging «Subpoenas «Spyware «Monitoring devices n Solutions «Privacy policies «Voluntary guidelines «Seal programs «Chief privacy officers «Laws and Regulations «Software tools n Software tools Lorrie Faith Cranor • http: //lorrie. cranor. org/ 3
The Online Privacy Landscape: Privacy concerns Web privacy concerns n Data is often collected silently «Web allows large quantities of data to be collected inexpensively and unobtrusively n Data from multiple sources may be merged «Non-identifiable information can become identifiable when merged n Data collected for business purposes may be used in civil and criminal proceedings n Users given no meaningful choice «Few sites offer alternatives Lorrie Faith Cranor • http: //lorrie. cranor. org/ 4

The Online Privacy Landscape: Privacy concerns Privacy surveys find concerns n Increasingly people say they are concerned about online privacy (80 -90% of US Net users) n Improved privacy protection is factor most likely to persuade non-Net users to go online n 27% of US Net users have abandoned online shopping carts due to privacy concerns n 64% of US Net users decided not to use a web site or make an online purchase due to privacy concerns n 34% of US Net users who do not buy online would buy online if they didn’t have privacy concerns Lorrie Faith Cranor • http: //lorrie. cranor. org/ 5
The Online Privacy Landscape: Privacy concerns Beyond concern n April 1999 Study: Beyond Concern: Understanding Net Users' Attitudes About Online Privacy by Cranor, Ackerman and Reagle (US panel results reported) http: //www. research. att. com/projects/ privacystudy/ «Internet users more likely to provide info when they are not identified «Some types of data more sensitive than others «Many factors important in decisions about information disclosure «Acceptance of persistent identifiers varies according to purpose «Internet users dislike automatic data transfer Lorrie Faith Cranor • http: //lorrie. cranor. org/ 6

The Online Privacy Landscape: Privacy concerns Few read privacy policies n 3% review online privacy policies carefully most of the time «Most likely to review policy before providing credit card info «Policies too time consuming to read and difficult to understand n 70% would prefer standard privacy policy format n Most interested in knowing about data sharing and how to get off marketing lists n People are more comfortable at sites that have privacy policies, even if they don’t read them Lorrie Faith Cranor • http: //lorrie. cranor. org/ 7

The Online Privacy Landscape: Privacy concerns Survey references n Mark S. Ackerman, Lorrie Faith Cranor and Joseph Reagle, Beyond Concern: Understanding Net Users’ Attitudes About Online Privacy, (AT&T Labs, April 1999), http: //www. research. att. com/projects/privacystudy/ n Mary J. Culnan and George R. Milne, The Culnan-Milne Survey on Consumers & Online Privacy Notices: Summary of Responses, (December 2001), http: //www. ftc. gov/bcp/workshops/glb/supporting/culnan-milne. pdf. n Cyber Dialogue, Cyber Dialogue Survey Data Reveals Lost Revenue for Retailers Due to Widespread Consumer Privacy Concerns, (Cyber Dialogue, November 7, 2001), http: //www. cyberdialogue. com/news/releases/2001/11 -07 -uco-retail. html. n Forrester Research, Privacy Issues Inhibit Online Spending, (Forrester, October 3, 2001). n Louis Harris & Associates and Alan F. Westin, Commerce, Communication and Privacy Online (Louis Harris & Associates, 1997), http: //www. privacyexchange. org/iss/surveys/computersurvey 97. html n Louis Harris & Associates and Alan F. Westin. E-Commerce and Privacy, What Net Users Want, (Sponsored by Price Waterhouse and Privacy & American Business. P & AB, June 1998). http: //www. privacyexchange. org/iss/surveys/ecommsum. html n Opinion Research Corporation and Alan F. Westin. “Freebies” and Privacy: What Net Users Think. Sponsored by Privacy & American Business. P & AB, July 1999. http: //www. privacyexchange. org/iss/surveys/sr 990714. html n Privacy Leadership Initiative, Privacy Notices Research Final Results, (Conducted by Harris Interactive, December 2001), http: //www. ftc. gov/bcp/workshops/glb/supporting/harris%20 results. pdf An extensive list of privacy surveys from around the world is available from http: //www. privacyexchange. org/iss/surveys. html. Lorrie Faith Cranor • http: //lorrie. cranor. org/ 8
The Online Privacy Landscape: How do they get my data? Browser Chatter n Browsers chatter about «IP address, domain name, organization, «Referring page «Platform: O/S, browser «What information is requested • URLs and search terms «Cookies n To anyone who might be listening «End servers «System administrators «Internet Service Providers «Other third parties • Advertising networks «Anyone who might subpoena log files later Lorrie Faith Cranor • http: //lorrie. cranor. org/ 9
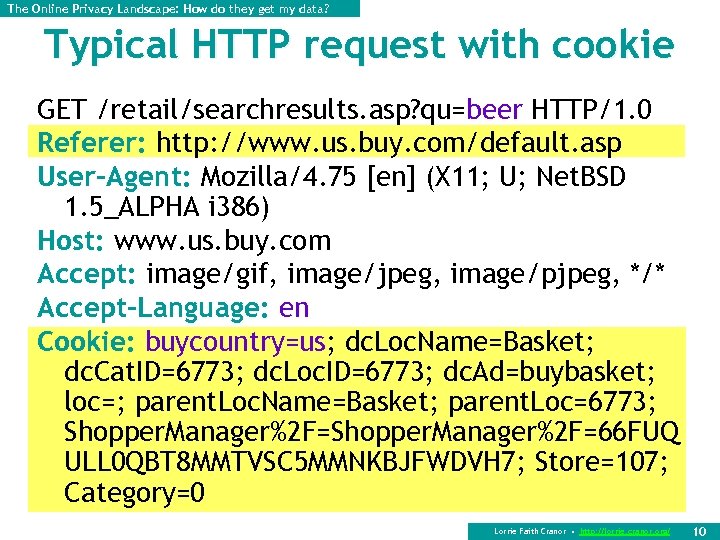
The Online Privacy Landscape: How do they get my data? Typical HTTP request with cookie GET /retail/searchresults. asp? qu=beer HTTP/1. 0 Referer: http: //www. us. buy. com/default. asp User-Agent: Mozilla/4. 75 [en] (X 11; U; Net. BSD 1. 5_ALPHA i 386) Host: www. us. buy. com Accept: image/gif, image/jpeg, image/pjpeg, */* Accept-Language: en Cookie: buycountry=us; dc. Loc. Name=Basket; dc. Cat. ID=6773; dc. Loc. ID=6773; dc. Ad=buybasket; loc=; parent. Loc. Name=Basket; parent. Loc=6773; Shopper. Manager%2 F=66 FUQ ULL 0 QBT 8 MMTVSC 5 MMNKBJFWDVH 7; Store=107; Category=0 Lorrie Faith Cranor • http: //lorrie. cranor. org/ 10
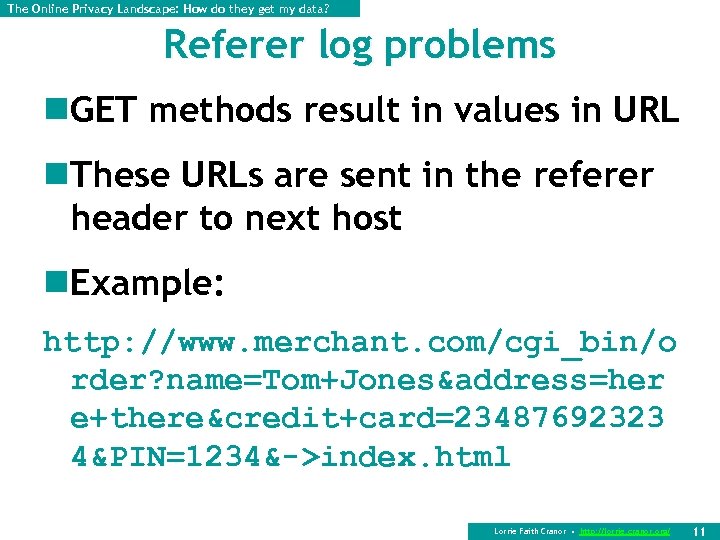
The Online Privacy Landscape: How do they get my data? Referer log problems n. GET methods result in values in URL n. These URLs are sent in the referer header to next host n. Example: http: //www. merchant. com/cgi_bin/o rder? name=Tom+Jones&address=her e+there&credit+card=23487692323 4&PIN=1234&->index. html Lorrie Faith Cranor • http: //lorrie. cranor. org/ 11

The Online Privacy Landscape: How do they get my data? Cookies 101 n Cookies can be useful «Used like a staple to attach multiple parts of a form together «Used to identify you when you return to a web site so you don’t have to remember a password «Used to help web sites understand how people use them n Cookies can do unexpected things «Used to profile users and track their activities, especially across web sites Lorrie Faith Cranor • http: //lorrie. cranor. org/ 12
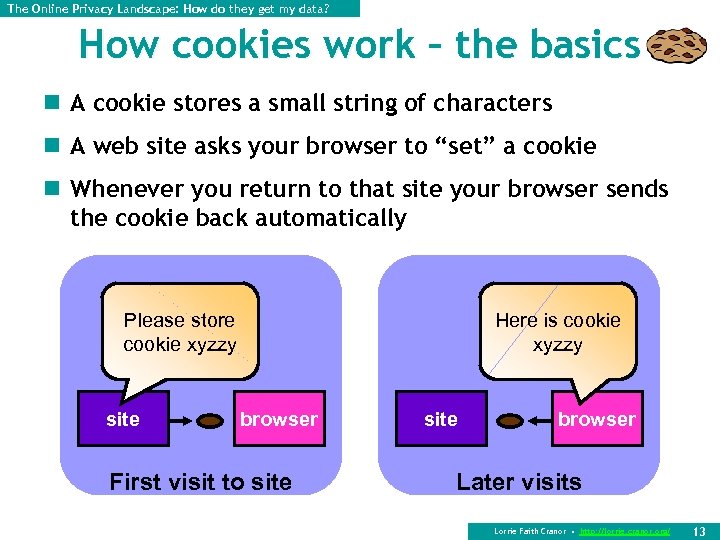
The Online Privacy Landscape: How do they get my data? How cookies work – the basics n A cookie stores a small string of characters n A web site asks your browser to “set” a cookie n Whenever you return to that site your browser sends the cookie back automatically Please store cookie xyzzy site Here is cookie xyzzy browser First visit to site browser Later visits Lorrie Faith Cranor • http: //lorrie. cranor. org/ 13
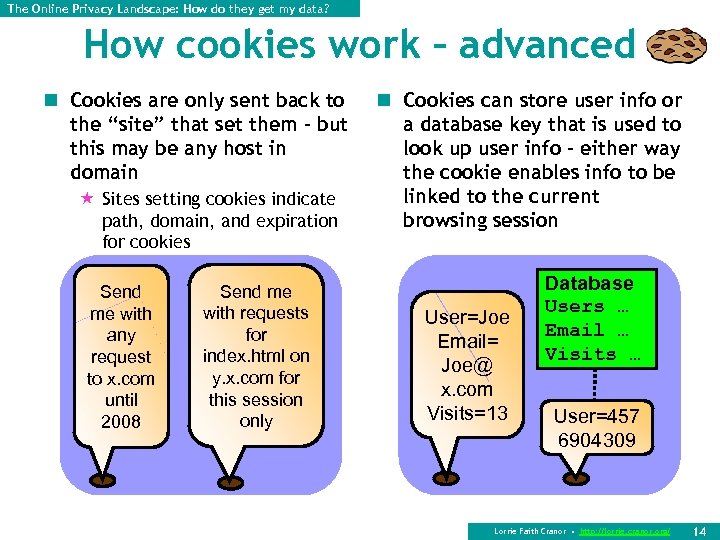
The Online Privacy Landscape: How do they get my data? How cookies work – advanced n Cookies are only sent back to the “site” that set them – but this may be any host in domain « Sites setting cookies indicate path, domain, and expiration for cookies Send me with any request to x. com until 2008 Send me with requests for index. html on y. x. com for this session only n Cookies can store user info or a database key that is used to look up user info – either way the cookie enables info to be linked to the current browsing session User=Joe Email= Joe@ x. com Visits=13 Database Users … Email … Visits … User=457 6904309 Lorrie Faith Cranor • http: //lorrie. cranor. org/ 14

The Online Privacy Landscape: How do they get my data? Cookie terminology n Cookie Replay – sending a cookie back to a site n Session cookie – cookie replayed only during current browsing session n Persistent cookie – cookie replayed until expiration date n First-party cookie – cookie associated with the site the user requested n Third-party cookie – cookie associated with an image, ad, frame, or other content from a site with a different domain name that is embedded in the site the user requested « Browser interprets third-party cookie based on domain name, even if both domains are owned by the same company Lorrie Faith Cranor • http: //lorrie. cranor. org/ 15
The Online Privacy Landscape: How do they get my data? Web bugs n Invisible “images” (1 -by-1 pixels, transparent) embedded in web pages and cause referer info and cookies to be transferred n Also called web beacons, clear gifs, tracker gifs, etc. n Work just like banner ads from ad networks, but you can’t see them unless you look at the code behind a web page n Also embedded in HTML formatted email messages, MS Word documents, etc. n For more info on web bugs see: http: //www. privacyfoundation. org/resources /webbug. asp n For software to detect web bugs see: http: //www. bugnosis. org Lorrie Faith Cranor • http: //lorrie. cranor. org/ 16

The Online Privacy Landscape: How do they get my data? How data can be linked n Every time the same cookie is replayed to a site, the site may add information to the record associated with that cookie «Number of times you visit a link, time, date «What page you visited last «Information you type into a web form n If multiple cookies are replayed together, they are usually logged together, effectively linking their data «Narrow scoped cookie might get logged with broad scoped cookie Lorrie Faith Cranor • http: //lorrie. cranor. org/ 17
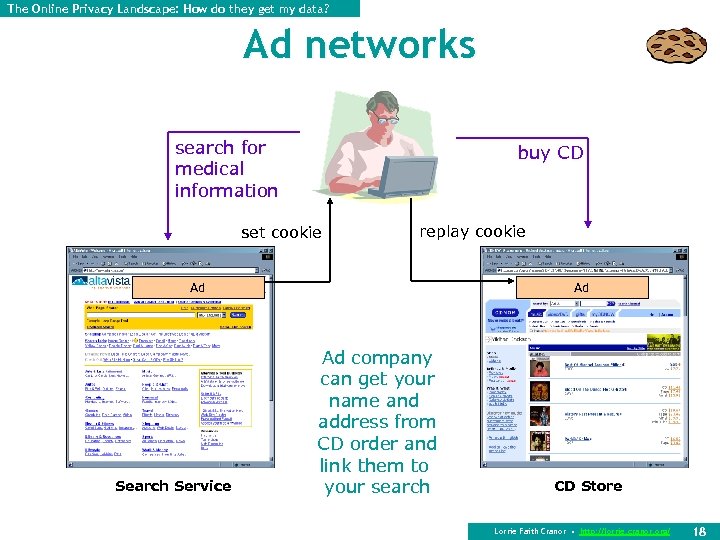
The Online Privacy Landscape: How do they get my data? Ad networks search for medical information buy CD set cookie replay cookie Ad Ad Search Service Ad company can get your name and address from CD order and link them to your search CD Store Lorrie Faith Cranor • http: //lorrie. cranor. org/ 18
The Online Privacy Landscape: How do they get my data? What ad networks may know… n Personal data: «Email address «Full name «Mailing address (street, city, state, and Zip code) «Phone number n Transactional data: «Details of plane trips «Search phrases used at search engines «Health conditions “It was not necessary for me to click on the banner ads for information to be sent to Double. Click servers. ” – Richard M. Smith Lorrie Faith Cranor • http: //lorrie. cranor. org/ 19

The Online Privacy Landscape: How do they get my data? Online and offline merging n In November 1999, Double. Click purchased Abacus Direct, a company possessing detailed consumer profiles on more than 90% of US households. n In mid-February 2000 Double. Click announced plans to merge “anonymous” online data with personal information obtained from offline databases n By the first week in March 2000 the plans were put on hold «Stock dropped from $125 (12/99) to $80 (03/00) Lorrie Faith Cranor • http: //lorrie. cranor. org/ 20
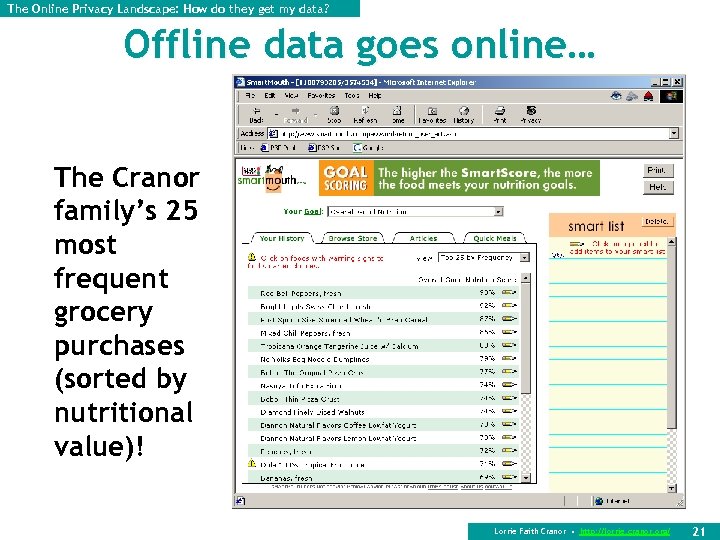
The Online Privacy Landscape: How do they get my data? Offline data goes online… The Cranor family’s 25 most frequent grocery purchases (sorted by nutritional value)! Lorrie Faith Cranor • http: //lorrie. cranor. org/ 21

The Online Privacy Landscape: How do they get my data? Subpoenas n Data on online activities is increasingly of interest in civil and criminal cases n The only way to avoid subpoenas is to not have data n In the US, your files on your computer in your home have much greater legal protection that your files stored on a server on the network Lorrie Faith Cranor • http: //lorrie. cranor. org/ 22
The Online Privacy Landscape: How do they get my data? Spyware n Spyware: Software that employs a user's Internet connection, without their knowledge or explicit permission, to collect information « Most products use pseudonymous, but unique ID n Over 800 known freeware and shareware products contain Spyware, for example: « Beeline Search Utility « Go. Zilla Download Manager « Comet Cursor n Often difficult to uninstall! n Anti-Spyware Sites: « http: //grc. com/oo/spyware. htm « http: //www. adcop. org/smallfish « http: //www. spychecker. com « http: //cexx. org/adware. htm Lorrie Faith Cranor • http: //lorrie. cranor. org/ 23

The Online Privacy Landscape: How do they get my data? Devices that monitor you Creative Labs Nomad Juke. Box Music transfer software reports all uploads to Creative Labs. Sony e. Marker Lets you figure out the artitst and title of songs you hear on the radio. And keeps a personal log of all the music you like on the emarker Web site. http: //www. nomadworld. com http: //www. emarker. com Sportbrain Monitors daily workout. Custom phone cradle uploads data to company Web site for analysis. http: //www. sportbrain. com/ : Cue. Cat Keeps personal log of advertisements you‘re interested in. http: //www. crq. com/cuecat. html See http: //www. privacyfoundation. org/ Lorrie Faith Cranor • http: //lorrie. cranor. org/ 24

The Online Privacy Landscape: Solutions Some solutions n Privacy policies n Voluntary guidelines and codes of conduct n Seal programs n Chief privacy officers n Laws and regulations n Software tools Lorrie Faith Cranor • http: //lorrie. cranor. org/ 25

The Online Privacy Landscape: Solutions Privacy policies n Policies let consumers know about site’s privacy practices n Consumers can then decide whether or not practices are acceptable, when to opt-in or opt-out, and who to do business with n The presence or privacy policies increases consumer trust Lorrie Faith Cranor • http: //lorrie. cranor. org/ 26

The Online Privacy Landscape: Solutions Privacy policy problems n BUT policies are often «difficult to understand «hard to find «take a long time to read «change without notice Lorrie Faith Cranor • http: //lorrie. cranor. org/ 27

The Online Privacy Landscape: Solutions Voluntary guidelines n Online Privacy Alliance http: //www. privacyalliance. org n Direct Marketing Association Privacy Promise http: //www. thedma. org/library/ privacy/privacypromise. shtml n Network Advertising Initiative Principles http: //www. networkadvertising. org/ Lorrie Faith Cranor • http: //lorrie. cranor. org/ 28

The Online Privacy Landscape: Solutions OECD fair information principles http: //www. oecd. org/dsti/it/secur/ prod/PRIV-en. HTM n Collection limitation n Data quality n Purpose specification n Use limitation n Security safeguards n Openness n Individual participation n Accountability Lorrie Faith Cranor • http: //lorrie. cranor. org/ 29

The Online Privacy Landscape: Solutions Simplified principles n Notice and disclosure n Choice and consent n Data security n Data quality and access n Recourse and remedies US Federal Trade Commission, Privacy Online: A Report to Congress (June 1998), http: //www. ftc. gov/reports/privacy 3/ Lorrie Faith Cranor • http: //lorrie. cranor. org/ 30

The Online Privacy Landscape: Solutions Seal programs n TRUSTe – http: //www. truste. org n BBBOnline – http: //www. bbbonline. org n CPA Web. Trust – http: //www. cpawebtrust. org/ n Japanese Privacy Mark http: //www. jipdec. or. jp/security/ privacy/ Lorrie Faith Cranor • http: //lorrie. cranor. org/ 31

The Online Privacy Landscape: Solutions Seal program problems n Certify only compliance with stated policy «Limited ability to detect non-compliance n Minimal privacy requirements n Don’t address privacy issues that go beyond the web site n Nonetheless, reporting requirements are forcing licensees to review their own policies and practices and think carefully before introducing policy changes Lorrie Faith Cranor • http: //lorrie. cranor. org/ 32
The Online Privacy Landscape: Solutions Lorrie Faith Cranor • http: //lorrie. cranor. org/ 33

The Online Privacy Landscape: Solutions Chief privacy officers n Companies are increasingly appointing CPOs to have a central point of contact for privacy concerns n Role of CPO varies in each company «Draft privacy policy «Respond to customer concerns «Educate employees about company privacy policy «Review new products and services for compliance with privacy policy «Develop new initiatives to keep company out front on privacy issue «Monitor pending privacy legislation Lorrie Faith Cranor • http: //lorrie. cranor. org/ 34

The Online Privacy Landscape: Solutions Laws and regulations n Privacy laws and regulations vary widely throughout the world n US has mostly sector-specific laws, with relatively minimal protections « Federal Trade Commission has jurisdiction over fraud and deceptive practices « Federal Communications Commission regulates telecommunications n European Data Protection Directive requires all European Union countries to adopt similar comprehensive privacy laws « Privacy commissions in each country (some countries have national and state commissions) « Many European companies non-compliant with privacy laws (2002 study found majority of UK web sites non-compliant) Lorrie Faith Cranor • http: //lorrie. cranor. org/ 35

The Online Privacy Landscape: Solutions Some US privacy laws n Bank Secrecy Act, 1970 n Fair Credit Reporting Act, 1971 n Privacy Act, 1974 n Right to Financial Privacy Act, 1978 n Cable TV Privacy Act, 1984 n Video Privacy Protection Act, 1988 n Family Educational Right to Privacy Act, 1993 n Electronic Communications Privacy Act, 1994 n Freedom of Information Act, 1966, 1991, 1996 Lorrie Faith Cranor • http: //lorrie. cranor. org/ 36
The Online Privacy Landscape: Solutions US law – recent additions n HIPAA (Health Insurance Portability and Accountability Act, 1996) «When implemented, will protect medical records and other individually identifiable health information n COPPA (Children‘s Online Privacy Protection Act, 1998) «Web sites that target children must obtain parental consent before collecting personal information from children under the age of 13 n GLB (Gramm-Leach-Bliley-Act, 1999) «Requires privacy policy disclosure and opt-out mechanisms from financial service institutions Lorrie Faith Cranor • http: //lorrie. cranor. org/ 37

The Online Privacy Landscape: Solutions Safe harbor n Membership «US companies self-certify adherance to requirements «Dept. of Commerce maintains signatory list http: //www. export. gov/safeharbor/ «Signatories must provide • notice of data collected, purposes, and recipients • choice of opt-out of 3 rd-party transfers, opt-in for sensitive data • access rights to delete or edit inaccurate information • security for storage of collected data • enforcement mechanisms for individual complaints n Approved July 26, 2000 by EU «reserves right to renegotiate if remedies for EU citizens prove to be inadequate Lorrie Faith Cranor • http: //lorrie. cranor. org/ 38

The Online Privacy Landscape: Solutions Implications of Directive for web sites n European Union Data Directive prohibits secondary uses of data without informed consent «Creating personally-identifiable online profiles will have to be opt-in in most cases «Upfront notice must be given when data is collected – no web bugs «No transfer of data to non-EU countries unless there is adequate privacy protection Lorrie Faith Cranor • http: //lorrie. cranor. org/ 39

The Online Privacy Landscape: Solutions Data protection agencies n Australia: http: //www. privacy. gov. au/ n Canada: http: //www. privcom. gc. ca/ n France: http: //www. cnil. fr/ n Germany: http: //www. bfd. bund. de/ n Hong Kong: http: //www. pco. org. hk/ n Italy: http: //www. privacy. it/ n Spain: http: //www. ag-protecciondatos. es/ n Switzerland: http: //www. edsb. ch/ n UK: http: //www. dataprotection. gov. uk/ … And many more Lorrie Faith Cranor • http: //lorrie. cranor. org/ 40
The Online Privacy Landscape: Solutions Software tools n Encryption tools – prevent others from listening in on your communications « File encryption « Email encryption « Encrypted network connections n Anonymity and pseudonymity tools – prevent your actions from being linked to you « Anonymizing proxies « Mix Networks and similar web anonymity tools « Anonymous email n Information and transparency tools – make informed choices about how your information will be used « Identity management tools « P 3 P n Filters « Cookie cutters « Child protection software n Other tools « Computer “cleaners” « Privacy suites « Personal firewalls Lorrie Faith Cranor • http: //lorrie. cranor. org/ 41
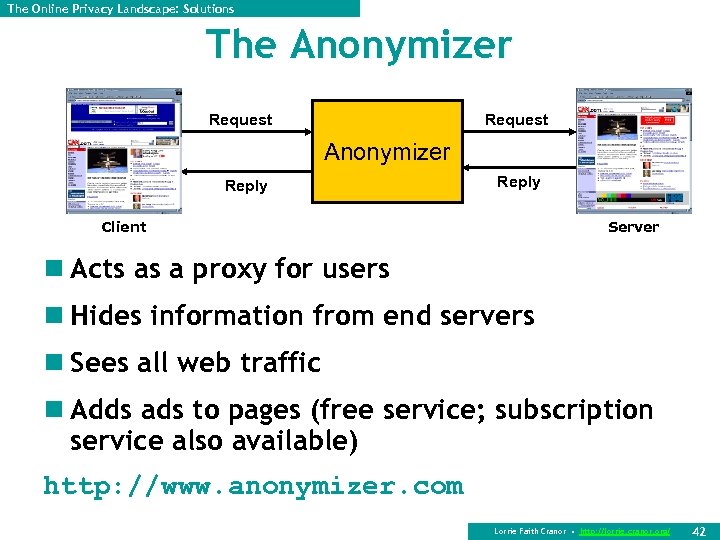
The Online Privacy Landscape: Solutions The Anonymizer Request Anonymizer Reply Client Server n Acts as a proxy for users n Hides information from end servers n Sees all web traffic n Adds ads to pages (free service; subscription service also available) http: //www. anonymizer. com Lorrie Faith Cranor • http: //lorrie. cranor. org/ 42
![The Online Privacy Landscape: Solutions Mixes [Chaum 81] Sender Destination B, C dest, msg The Online Privacy Landscape: Solutions Mixes [Chaum 81] Sender Destination B, C dest, msg](https://present5.com/presentation/e68e03c1ed8d6adf75965027ebc7cec8/image-43.jpg)
The Online Privacy Landscape: Solutions Mixes [Chaum 81] Sender Destination B, C dest, msg k. C k. B k. A Mix C msg dest, msg k. C Mix A C dest, msg k. C k. B Mix B k. X = encrypted with public key of Mix X Sender routes message randomly through network of “Mixes”, using layered public-key encryption. Lorrie Faith Cranor • http: //lorrie. cranor. org/ 43
The Online Privacy Landscape: Solutions Crowds n Users join a Crowd of other users n Web requests from the crowd cannot be linked to any individual n Protection from «end servers «other crowd members «system administrators «eavesdroppers n First system to hide data shadow on the web without trusting a central authority http: //www. research. att. com/projects/crowds/ Lorrie Faith Cranor • http: //lorrie. cranor. org/ 44

The Online Privacy Landscape: Solutions Anonymous email n Anonymous remailers allow people to send email anonymously n Similar to anonymous web proxies n Some can be chained and work like mixes http: //anon. efga. org/~rlist Lorrie Faith Cranor • http: //lorrie. cranor. org/ 45

The Online Privacy Landscape: Solutions Filters n Cookie Cutters «Block cookies, allow for more fine-grained cookie control, etc. «Some also filter ads, referer header, and browser chatter «http: //www. junkbusters. com/ht/en/ links. html#measures n Child Protection Software «Block the transmission of certain information via email, chat rooms, or web forms when child is using computer «Limit who a child can email or chat with «http: //www. getnetwise. org/ Lorrie Faith Cranor • http: //lorrie. cranor. org/ 46
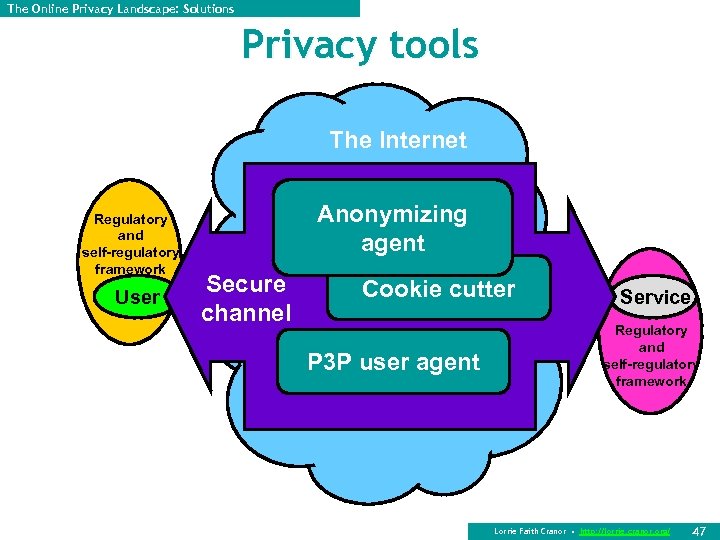
The Online Privacy Landscape: Solutions Privacy tools The Internet Regulatory and self-regulatory framework User Anonymizing agent Secure channel Cookie cutter P 3 P user agent Service Regulatory and self-regulatory framework Lorrie Faith Cranor • http: //lorrie. cranor. org/ 47
The Online Privacy Landscape Privacy web sites n http: //www. aclu. org/ n http: //www. cdt. org/ n http: //www. cpsr. org/ n http: //www. consumerprivacygui de. org/ n http: //www. vortex. com/privacy. html n http: //www. privacyfoundation. org/ n http: //www. privacy. org/pi/ n http: //www. privacyjournal. net/ n http: //www. eff. org/ n http: //www. understandingprivacy. org/ n http: //www. epic. org/ n http: //www. privacy. org/ n http: //www. healthprivacy. org/ n http: //www. privacyplace. com/ n http: //www. junkbusters. com/ n http: //www. privacyalliance. org/ n http: //www. privacyrights. org/ n http: //www. privacytimes. com/ n http: //www. pandab. org/ n http: //www. anu. edu. au/people/ Roger. Clarke/DV/index. html n http: //www. privacyexchange. org/ n http: //headlines. yahoo. com/ Full_Coverage/Tech/Internet_ Privacy/ Lorrie Faith Cranor • http: //lorrie. cranor. org/ 48

The Online Privacy Landscape Books n Web Privacy with P 3 P by Lorrie Faith Cranor n Database Nation by Simson Garfinkel n The Privacy Law Sourcebook 2001: United States Law, International Law, and Recent Developments by Marc Rotenberg Lorrie Faith Cranor • http: //lorrie. cranor. org/ 49
e68e03c1ed8d6adf75965027ebc7cec8.ppt