47b0b913be967eb53bffe2d30ee9a889.ppt
- Количество слайдов: 46

Web Browser Privacy and Security Part I

Today’s Topics n Trusted Paths n Context-Sensitive Certificate Verification (optional paper) Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
Trusted Paths n Trusted paths are used to help users ensure that they are communicating with whom they think they are • Ex. Ctrl-Alt-Del in Windows systems cannot be intercepted n Trusted paths for Web are difficult because • From remote server to browser to user • Trivial to make fake UIs that look legit Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
Example Attack #1 Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
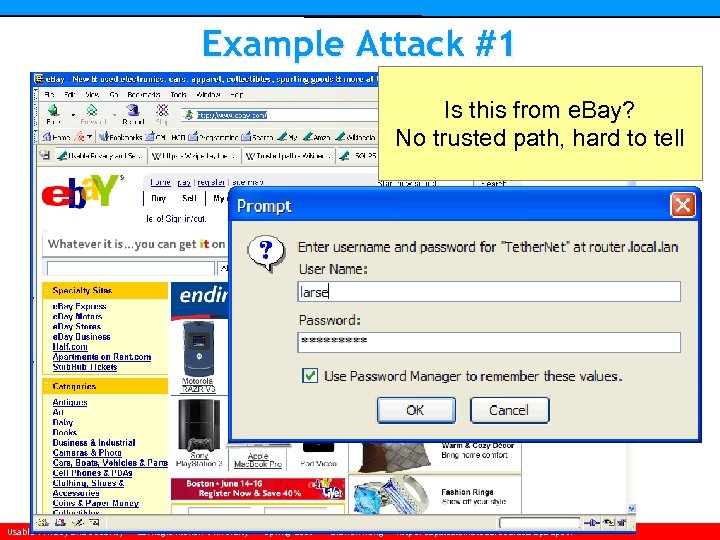
Example Attack #1 Is this from e. Bay? No trusted path, hard to tell Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
Example Attack #2 Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
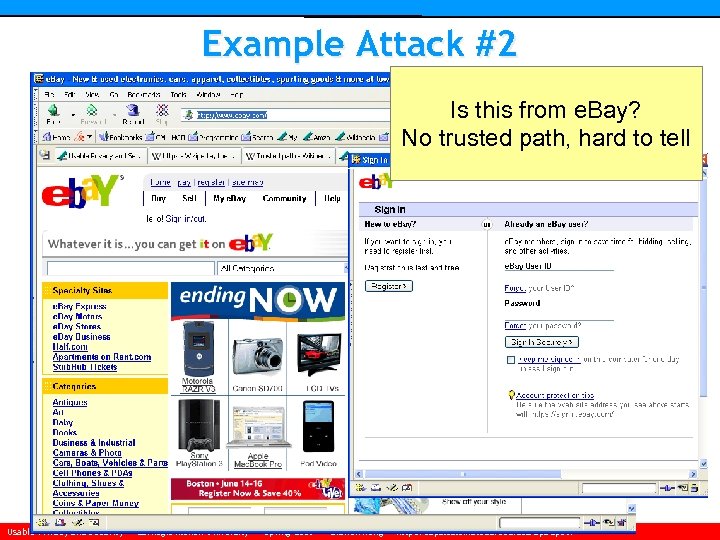
Example Attack #2 Is this from e. Bay? No trusted path, hard to tell Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
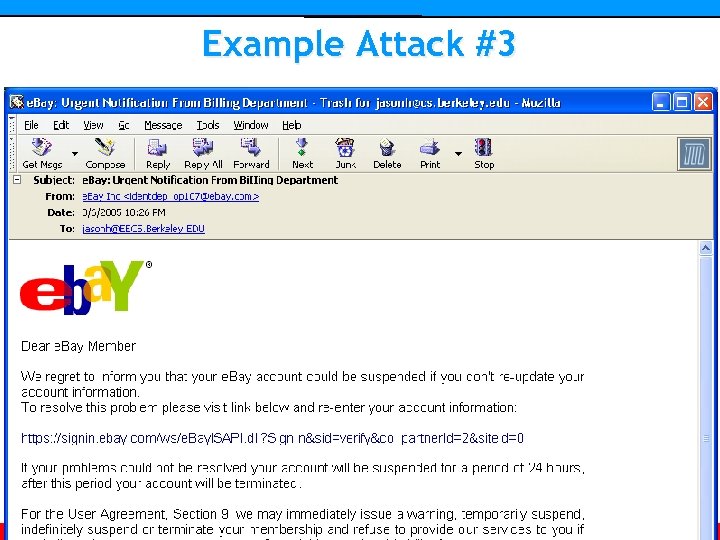
Example Attack #3 Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
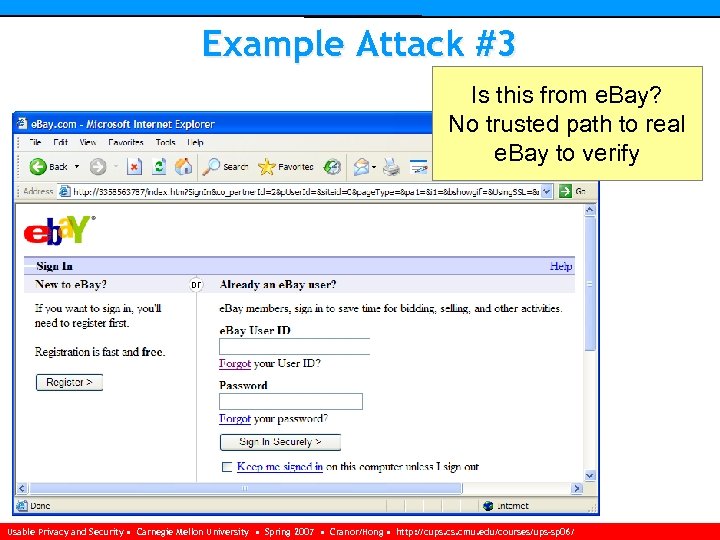
Example Attack #3 Is this from e. Bay? No trusted path to real e. Bay to verify Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/

One Idea: Dynamic Security Skins n User remembers one image • Shown in a trusted window n User remembers one password • Ease of use • Sites get hashed password only n Uses Secure Remote Password w/ server • Generated using a shared secret Dhamija and Tygar, The Battle Against Phishing: Dynamic Security Skins, SOUPS 2005 Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/

How to Show Trusted Path n Static security indicators • Ex. Secure window uses a certain color border • Ex. Secure window uses lock icon • Rejected, too predictable and easy to spoof n Custom security indicator • • Ex. One indicator per site Ex. One indicator per user Rejected, too much effort (Also too much to remember) Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
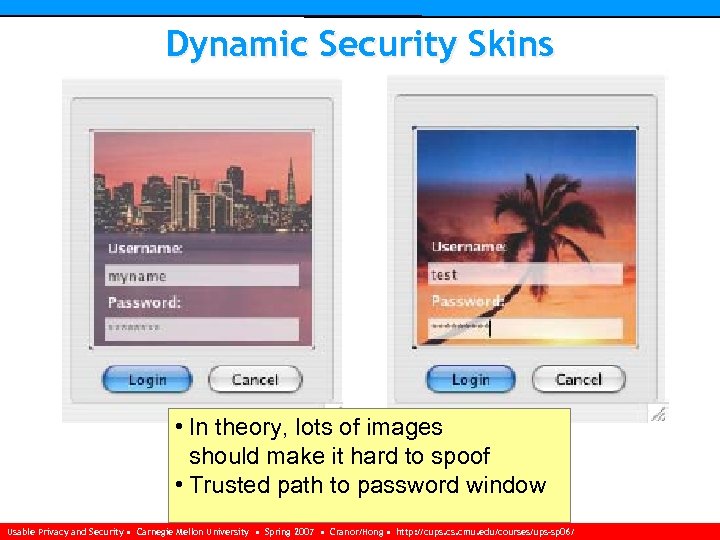
Dynamic Security Skins • In theory, lots of images should make it hard to spoof • Trusted path to password window Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
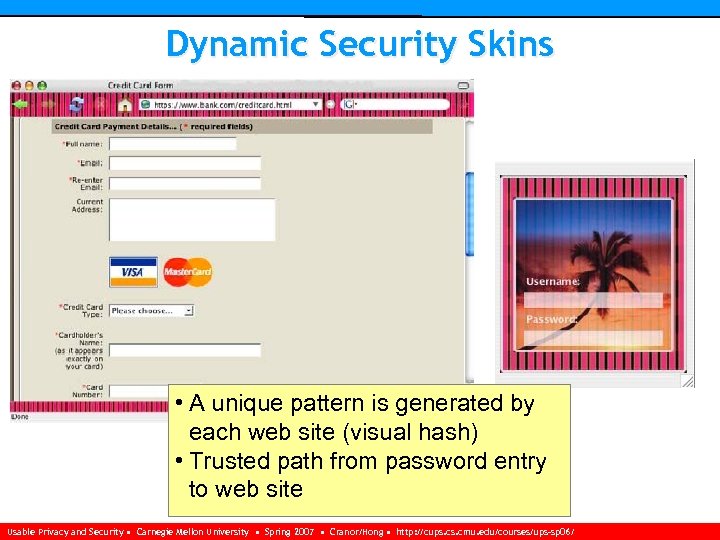
Dynamic Security Skins • A unique pattern is generated by each web site (visual hash) • Trusted path from password entry to web site Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/

Another Idea: Tokens n Two factor authentication • Something you have • Usually cryptographic n Secure. ID n Smart cards n Random cryptographic tokens n Scratch cards Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
A Third Idea: Mobile Phones n Everyone’s got a mobile phone n Client side certificates • Private keys generated/stored on phone • New key for each phone n Keys linked to domain names n Key generated upon new connection n Bluetooth from phone to PC n Very few server modifications Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/

Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
![Discussion of Trusted Path n “[O]n each launch of Firefox, paint the Firefox interface Discussion of Trusted Path n “[O]n each launch of Firefox, paint the Firefox interface](https://present5.com/presentation/47b0b913be967eb53bffe2d30ee9a889/image-17.jpg)
Discussion of Trusted Path n “[O]n each launch of Firefox, paint the Firefox interface with a nonintrusive, randomly generated pattern. Because sites wouldn’t be able to replicate this pattern, users would know when they were viewing [a] spoofed UI” n Other ideas for trusted paths? n Other barriers to adoption? Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/

Today’s Topics n Trusted Paths n Context-Sensitive Certificate Verification (optional paper) Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/

Certificates n A secure way of binding a public key with an identity • Ex. Amazon sends its certificate via https • Makes it easier to encrypt communications n How to know if this certificate is legitimate? • Certificate is also signed by a well-known certificate authority (CA) • Certificates of these CAs often included in web browser Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
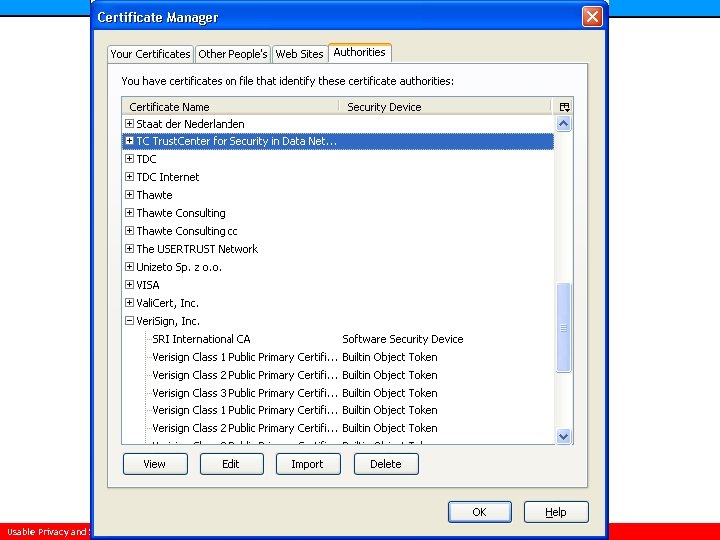
Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
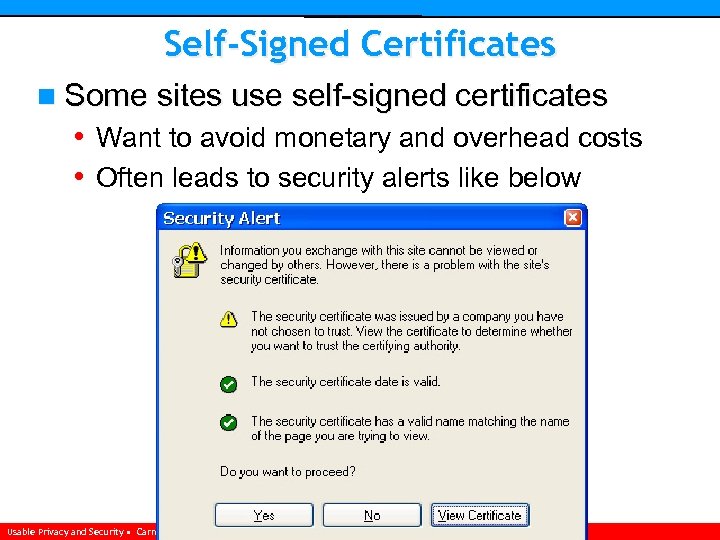
Self-Signed Certificates n Some sites use self-signed certificates • Want to avoid monetary and overhead costs • Often leads to security alerts like below Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
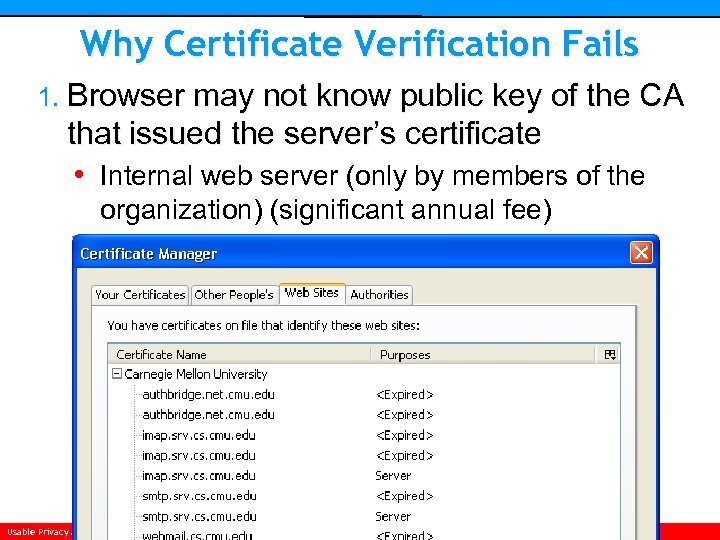
Why Certificate Verification Fails 1. Browser may not know public key of the CA that issued the server’s certificate • Internal web server (only by members of the organization) (significant annual fee) Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/

Why Certificate Verification Fails 1. Browser may not know public key of the CA that issued the server’s certificate • Internal web server (only by members of the organization) (significant annual fee) • Own CA: public key installed in browser (no verification errors), but large number of users / user owned computers means high maint 2. Issuer’s or the server’s certificate may be expired Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/

Why Certificate Verification Fails 3. Common name of certificate does not match server’s fully qualified domain name ♦ Mistake, ex. s 3. acme. com vs s 10. acme. com ♦ Might be attacker using his own identity with a CA generated certificate (difficult) Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
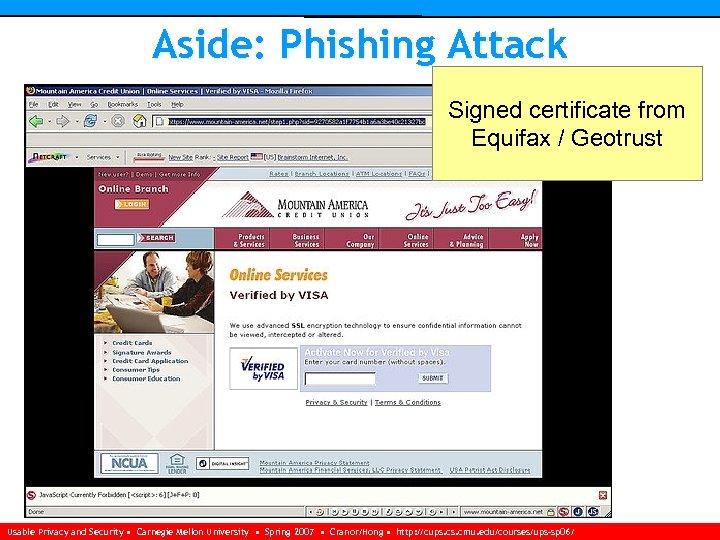
Aside: Phishing Attack Signed certificate from Equifax / Geotrust Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/

Why Certificate Verification Fails 3. Common name of certificate does not match server’s fully qualified domain name ♦ Mistake, ex. s 3. acme. com vs s 10. acme. com ♦ Might be attacker using his own identity with a CA generated certificate (easy, but expensive) ♦ Might be attacker using a stolen certificate (along with the private key) (difficult) ♦ Or might be self-signed certificate (easy) Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
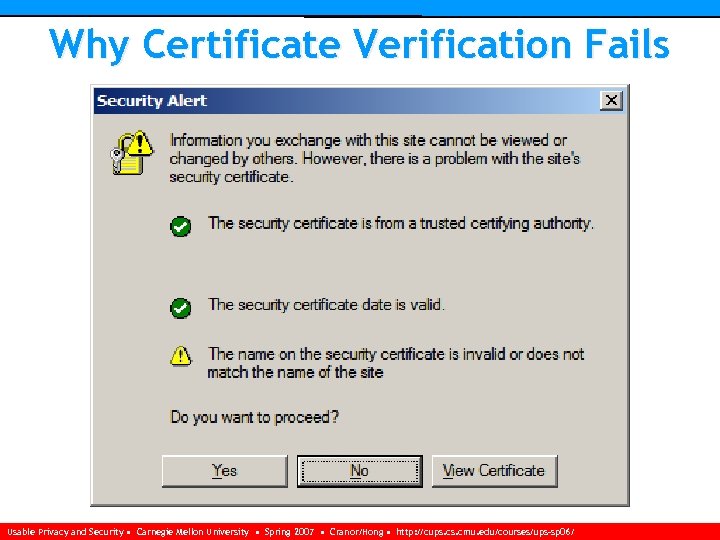
Why Certificate Verification Fails Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
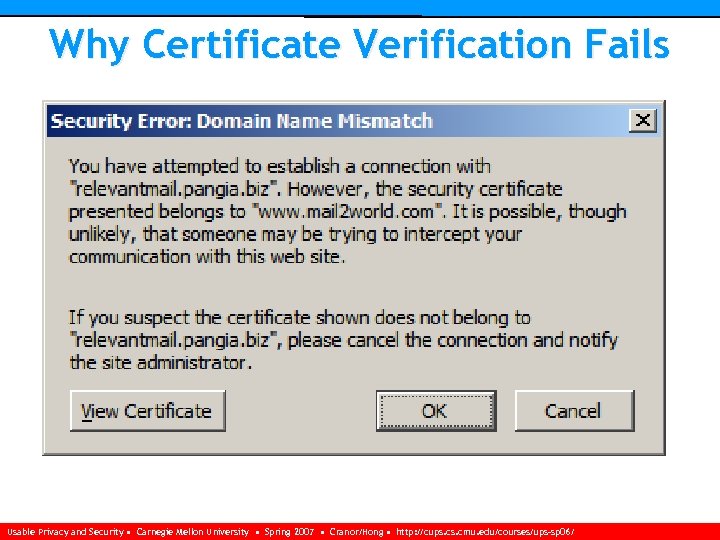
Why Certificate Verification Fails Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
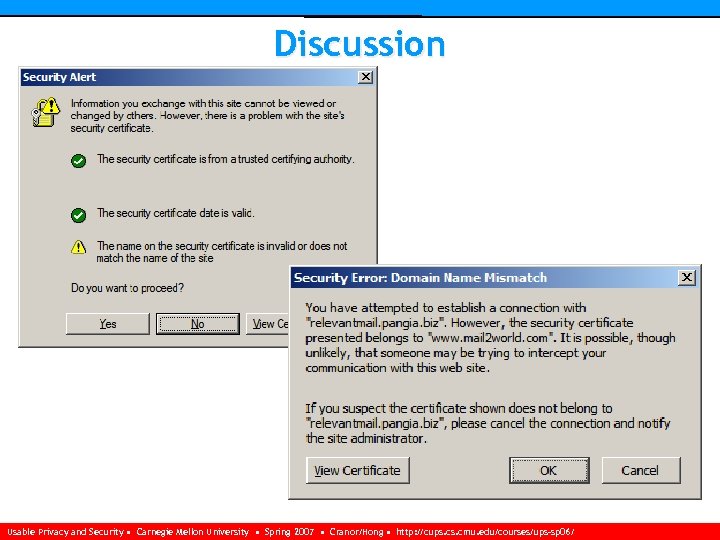
Discussion Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/

Context-Sensitive Certificate Verification n Clarify relationship between user and server’s (non verified) certificate • Not giving the user override mechanisms n Distribute signed certificates of internal servers out of band n Use typically unused certificate fields: • CA’s contact information (field: issuer alternative name) • CA administrator’s name, address, telephone and fax numbers, and work hours. Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
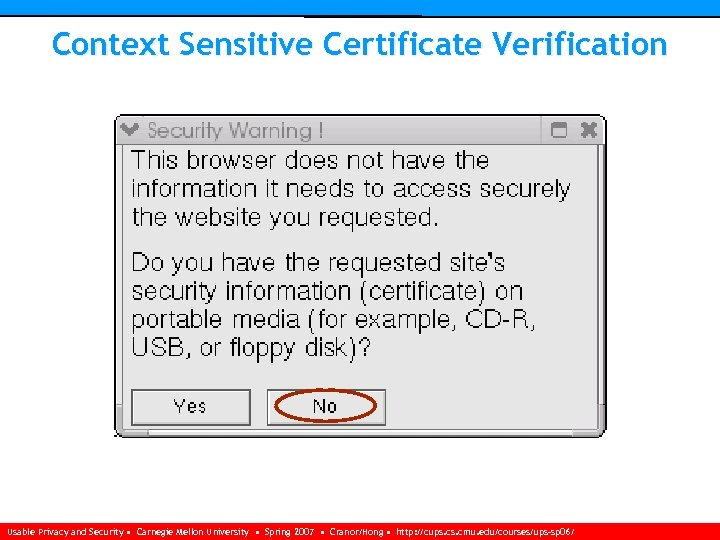
Context Sensitive Certificate Verification Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
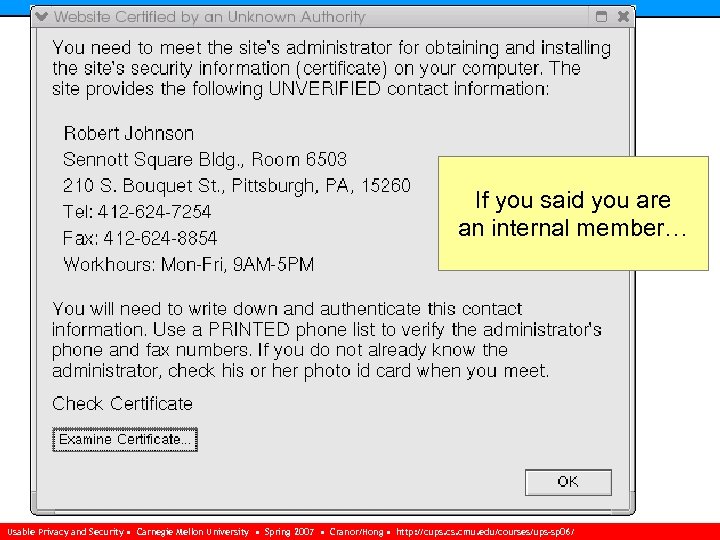
If you said you are an internal member… Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
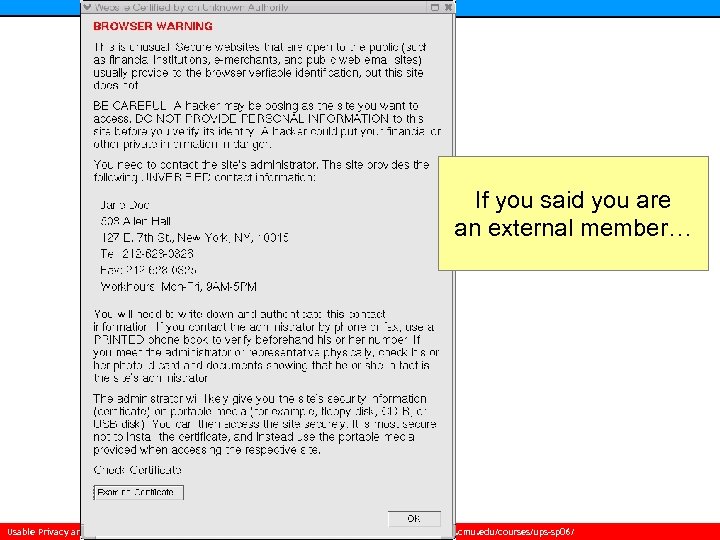
If you said you are an external member… Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
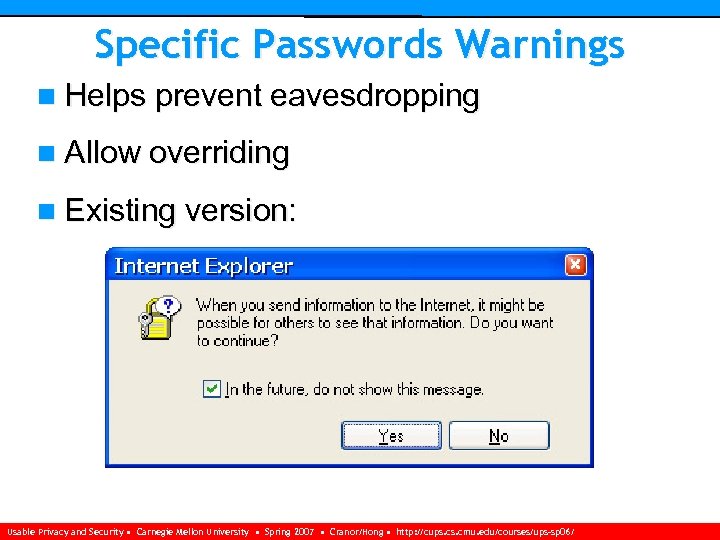
Specific Passwords Warnings n Helps prevent eavesdropping n Allow overriding n Existing version: Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
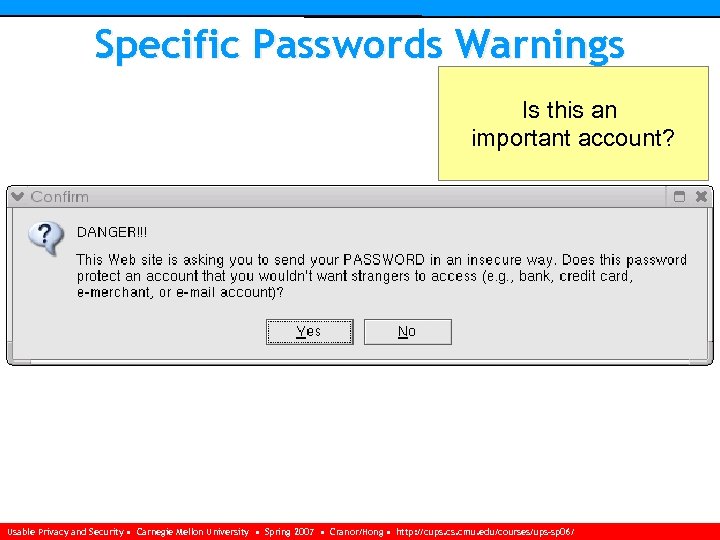
Specific Passwords Warnings Is this an important account? Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
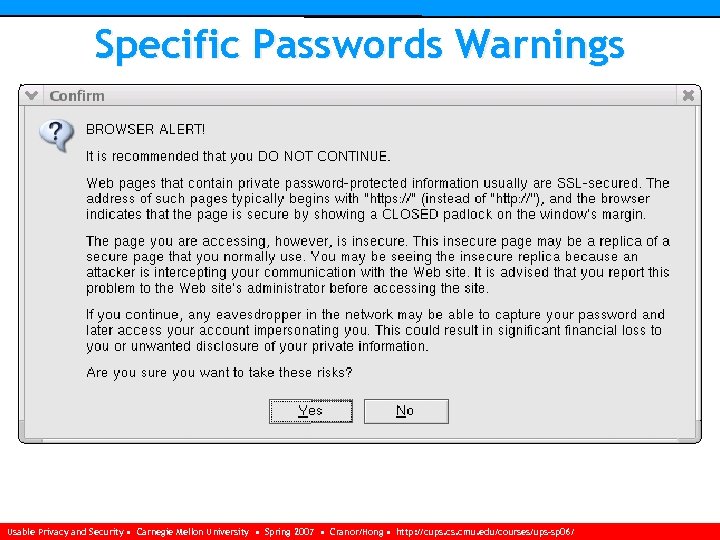
Specific Passwords Warnings Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
Discussion n Thoughts so far on designs? • Context-sensitive Certificate Verification • Specific Password Warnings Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/

User Studies n Computer literate users (CLU) n Evaluate: • Likelihood of successful attack in representative security-sensitive Web apps • Possibility of “foolproofing” browsers, so they can be used securely even by untrained CLUs • Can education about the relevant security principles, attacks, and tools improve the security of how users browse the Web? § Note: This last hypothesis is not covered in this presentation Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
Study’s Design n 17 male participants (Pitt CS seniors) n Two studies: • Unmodified browser (IE) • Modified Mozilla Firebird 0. 6. 1 with CSCV and SPW n No feedback given between these two studies • (Note: ordering not randomized) Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
Study’s Design n Visit three fictional but realistic sites • Students given password protected accounts n Site 1: “maintained by Pitt” • Monitor reward points (do well in exams, etc) • HTTPS + Certificate issued by internal CA n Site 2: “e-merchant not affiliated with Pitt” • Spend reward points on books, CDs, etc. • HTTPS + bogus certificate n Site 3: “users’ Web email accounts” • HTTP only (no certificate) Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
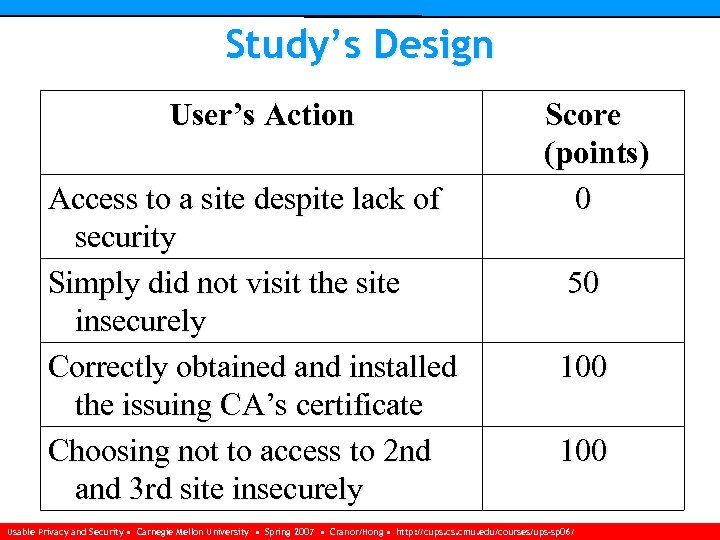
Study’s Design User’s Action Access to a site despite lack of security Simply did not visit the site insecurely Correctly obtained and installed the issuing CA’s certificate Choosing not to access to 2 nd and 3 rd site insecurely Score (points) 0 50 100 Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
Study’s Results n Guesses? Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/

Study’s Results n With current Web browsers, the mentioned attacks are alarmingly likely to succeed • More often than not, users’ behavior defeats the existing Web security mechanisms. • “um, another of those pop-ups. ” • “I always just click yes when I see these popups. ” Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
Study’s Results n CSCV blocked MITM attacks against HTTPS-based applications completely n SPW greatly reduced the insecure transmission of passwords in an HTTPbased application n Although untrained, users had little trouble using CSCV and SPW Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
Discussion n Thoughts on results? Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/

Discussion n Possible novelty effects • People might change behavior after getting used to new messages n Behavior outside of lab study • People might still not go find person to verify Usable Privacy and Security • Carnegie Mellon University • Spring 2007 • Cranor/Hong • http: //cups. cmu. edu/courses/ups-sp 06/
47b0b913be967eb53bffe2d30ee9a889.ppt