ab18723d800985a0d84db11f4668e5b5.ppt
- Количество слайдов: 22

Web Based Attacks Symantec White Paper Offense – The Other Side By AC 2 Craig, RB, Henky, Sohail

General Impression on Whitepaper • Overall the white paper was informative • Does not clearly define audience – For sophisticated users: too introductory – For novice users: lack of practical guidelines (ex: comparison of various products such as Symantec vs freeware AVG) • Somewhat outdated – rapidly changing threats

Items Missed – Other vectors: • • • Web 2. 0 vulnerabilities Webmail threats Social media sites (ex: Facebook, Twitter, etc) Online video sites (ex: Youtube, adult video sites, etc) “Black-hat” Search Engine Optimization (SEO) – Global Economics of cybercrime

Web 2. 0 Vulnerabilities • Cross Site Scripting (XSS)- Malicious input is sent by an attacker, stored by a system, and then displayed to other users. • CSRF/ CGRF- Malicious site code generates requests to a different site to which the victim is authorized, for example through a persistent cookie • Phishing- Installs a fraudulent widget or redirects to a fraudulent website to steal sensitive information from the victim • Injection Flaws- XML injection, XPath injection, Java. Script injection and JSON injection

Webmail Threats • Increasing SPAM and Unsolicited E-mail – Resurge of SPAM mails during the Obama presidency campaign (2008) – Malware that disguised as invoices from Fed-Ex and UPS (2009) – Online Pharmacy scam (2009) • Webmail Service – 10 K of accounts were leaked on Oct 09, for Hotmail, Gmail, Yahoo and other popular Webmail sites • Content and Virus filtering outside perimeter – Cloud based filtering to secure E-mail and corporate network
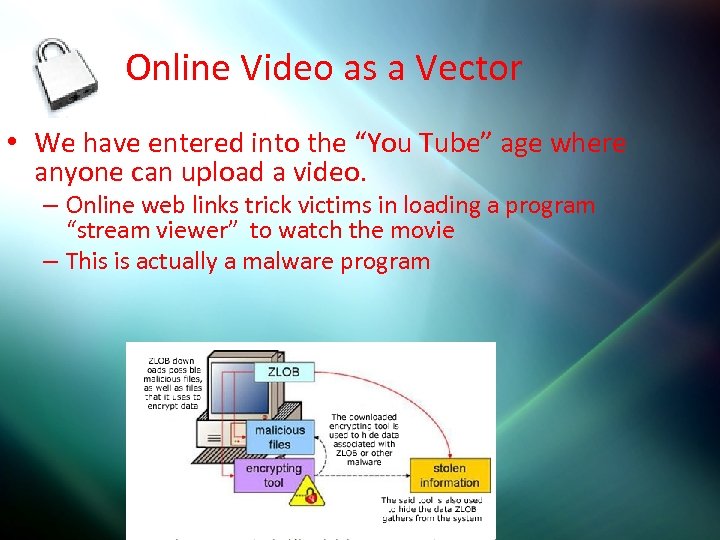
Online Video as a Vector • We have entered into the “You Tube” age where anyone can upload a video. – Online web links trick victims in loading a program “stream viewer” to watch the movie – This is actually a malware program

Social Networking • In 2009 about 2% of all online clicks going thru 4000 Cisco security devices were for Social networking sites. • Facebook was the winner with 1. 35% of all online clicks. • So who posses the most online security risk • Business cannot ignore these threats anymore (my company blocked facebook access)
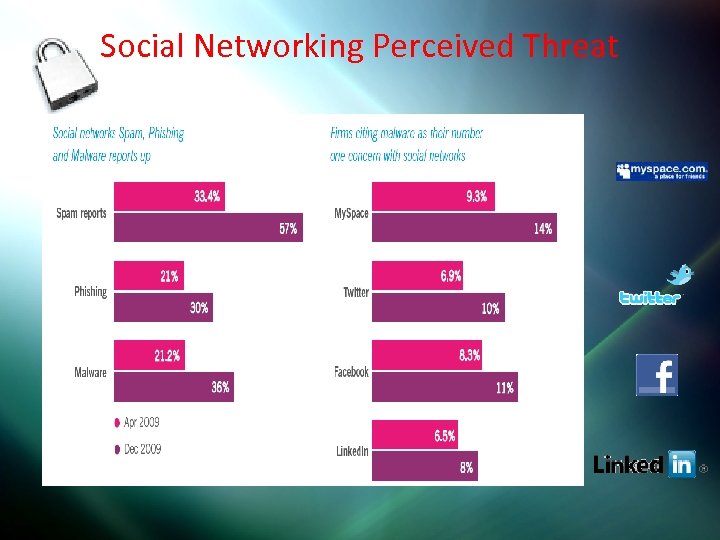
Social Networking Perceived Threat
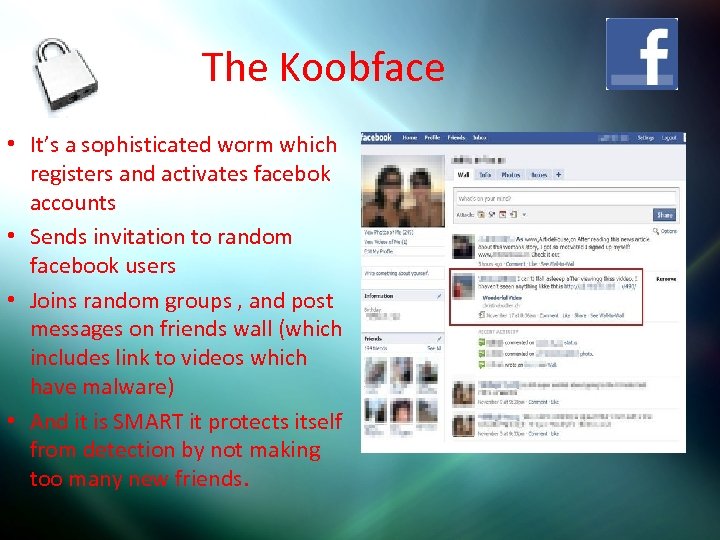
The Koobface • It’s a sophisticated worm which registers and activates facebok accounts • Sends invitation to random facebook users • Joins random groups , and post messages on friends wall (which includes link to videos which have malware) • And it is SMART it protects itself from detection by not making too many new friends.
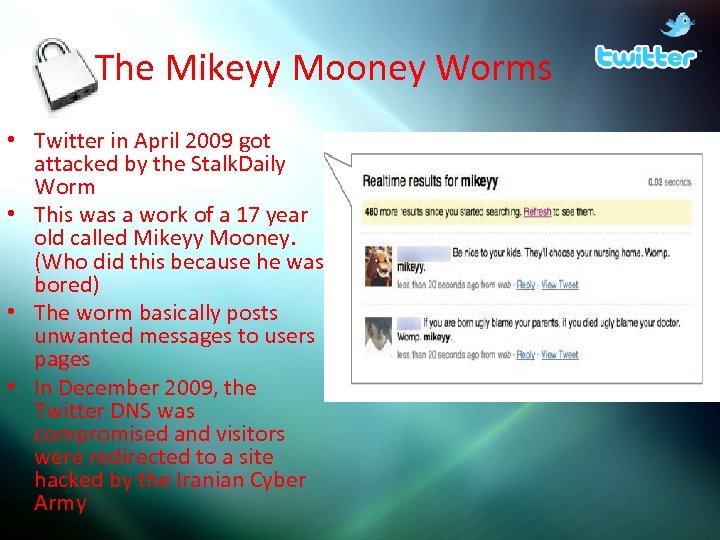
The Mikeyy Mooney Worms • Twitter in April 2009 got attacked by the Stalk. Daily Worm • This was a work of a 17 year old called Mikeyy Mooney. (Who did this because he was bored) • The worm basically posts unwanted messages to users pages • In December 2009, the Twitter DNS was compromised and visitors were redirected to a site hacked by the Iranian Cyber Army
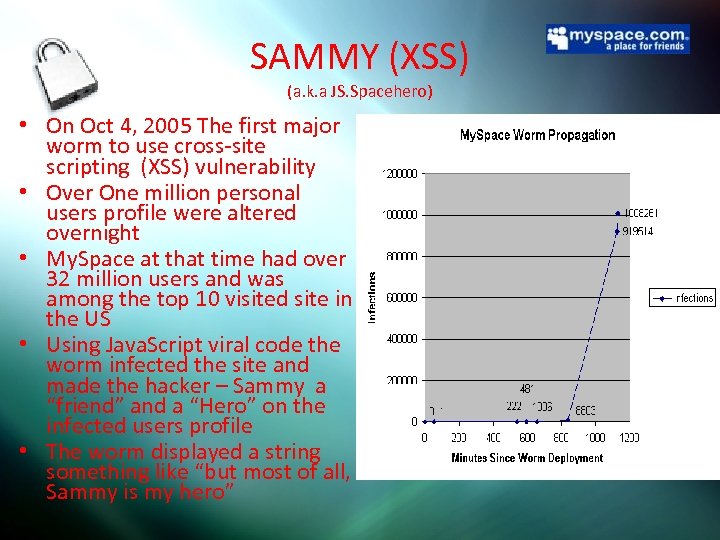
SAMMY (XSS) (a. k. a JS. Spacehero) • On Oct 4, 2005 The first major worm to use cross-site scripting (XSS) vulnerability • Over One million personal users profile were altered overnight • My. Space at that time had over 32 million users and was among the top 10 visited site in the US • Using Java. Script viral code the worm infected the site and made the hacker – Sammy a “friend” and a “Hero” on the infected users profile • The worm displayed a string something like “but most of all, Sammy is my hero”

Search Engine Optimization (SEO) • Standard marketing technique used by many legitimate firms to promote internet presence • Involves: – careful selection of keywords and topics – Manipulation of links to increase a page’s popularity • Attract visitors with SEO to push links to the top of search results

‘Black-hat’ SEO • ‘White-hat’ SEO: approved methods by search vendors: editing content to increase relevance to certain search keywords • ‘Black-hat’ SEO: spamdexing, ‘doorway’ pages, spam messages posted on blogs/forums.

‘Black-hat’ SEO Cont’d • Most popular: ‘doorway’ sites – hosting content specifically created/optimized for a particular topic & search phrases – Link to a promoted site using URL containing affiliate ID – High density of related keywords when indexed by search engine, referred site by ‘doorway’ will rank higher & placed higher in search results • Common ‘black-hat’ SEO workflow: – Mining Google Trends data for most popular search topics (ex: ‘death of david carradine’, ‘lady gaga’, etc) – Generating content related to popular search phrases & linking to a promotional site – Uploading content as a blog, forum post, Wiki article, or as a site • Most of the steps automated by SEO software tools

‘Black-hat’ SEO Cont’d • Custom tools for sale on underground black-hat forums to generate contents that seems genuine & interlink pages across domains for more exposure – A-Poster: specializing in spamming guestbooks – Xrumer: discussion forums – automated forum registrations, generate email accounts – Zenno. Poster: • generate accounts on any webmail site, social networks, blogs, free web-hosting provides, etc • Send SMS messages • Parse search results • Place spam on forums and guestbooks
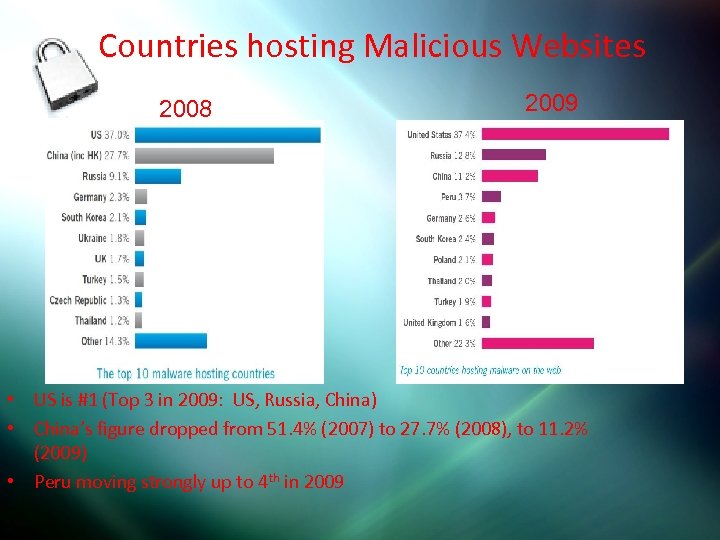
Countries hosting Malicious Websites 2008 2009 • US is #1 (Top 3 in 2009: US, Russia, China) • China’s figure dropped from 51. 4% (2007) to 27. 7% (2008), to 11. 2% (2009) • Peru moving strongly up to 4 th in 2009

Global Cybercrime • Honest money is harder to come by • People being lured into world of crime, programmers who can’t find legit jobs are more easily recruited by criminal gangs • Malware has evolved to become a major industry in itself, with complicated economic infrastructure & population of well-organized, well-funded criminal gangs, highly motivated & highly trained programmers generating massive volumes of malicious codes and exploits

Partnerka • Russian term referring to complex networks of affiliates linked by a common desire to make money from the internet. • Groups are well organized, dominated by Russians, & responsible for high proportion of spam campaigns and malware attacks • Biggest area of activity includes: online pharmacies selling illegal, off-prescription and often unsafe drugs (promoted thru spam and SEO). Ex: The Canadian Pharmacy
Top Spammers

Partnerka cont’d • Other activities: – – – ‘Scareware’ rogue/fake anti-virus Counterfeit goods (ex: fake Rolexes & high end merchandises) Online casinos (favorite method for money laundering) Adult sites Dating sites • Cash comes from: – Direct sales of fake or illegal goods – Complex affiliations with pay-per-click or pay-per-install marketing firms, who in turn get paid by often legit companies hoping to get more incoming traffic – Botnets & phishers selling data of stolen credit card information – Malware creators selling Trojans, spamming & SEO manipulation tools

Partnerka cont’d • Typical revenues: – A single Canadian Pharmacy spam campaign can net 200 purchases ($16, 000 in revenues daily) – An affiliate webmaster redirecting 10, 000 hits per day to a single scareware site can earn up to $180, 000 annually. • Not homogeneous groups – different gangs in strong competition with each other. – Allegiance: more generous commission rates, shorter ‘hold’ periods, support for wider range of payment options, hi-quality promotional, better support, etc – Perks: Expensive parties for members, generous holiday gifts, sweepstakes with prize like luxury cars, etc – Can turn ugly DDo. S attacks by competing gangs

References • • http: //us. trendmicro. com/imperia/md/content/webthreatwatch/wtw-us-0708. pdf http: //news. cnet. com/8301 -1009_3 -10217684 -83. html Sophos 2009 Security Threat Report (http: //www. sophos. com/sophos/docs/eng/marketing_material/sophos-security-threatreport-jan-2009 -na. pdf) Sophos 2010 Security Threat Report (http: //www. sophos. com/sophos/docs/eng/papers/sophos-security-threat-report-jan-2010 wpna. pdf) http: //en. wikipedia. org/wiki/Samy_(XSS) Cross –site scripting worms and viruses (http: //netsecurity. org/dl/articles/WHXSSThreats. pdf) http: //ha. ckers. org/images/samy-worm. gif Dmitry Samosseiko, “The Partnerka – What is It, and Why Should You Care? ” (http: //www. globalsecuritymag. com/Dmitry-Samosseiko-Sophos. Labs, 20091011, 13175. html)
ab18723d800985a0d84db11f4668e5b5.ppt