a1fd89b03286e96352e4669c9546a4a6.ppt
- Количество слайдов: 18

Web Application Security ECE 4112
What is a Web Application? • An application generally comprised of a collection of scripts that reside on a Web Server • Interacts with databases or other sources of dynamic content • Examples include: search engines, webmail, shopping carts and portal systems ECE 4112 - Internetwork Security
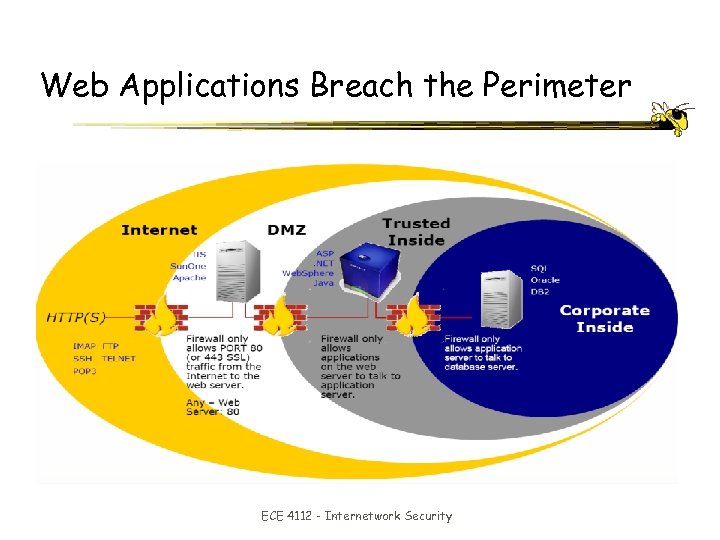
Web Applications Breach the Perimeter ECE 4112 - Internetwork Security
Web Application Vulnerabilities • Generally stem from improper handling of client requests and/or lack of input validation checking • Web applications are publicly accessible • Process data elements from within HTTP requests • Fail to identify how data elements were captured – difficult to know what kind of validation and sanity checking to use ECE 4112 - Internetwork Security
The Root of the Issue: Input Validation • Can be difficult to locate in a large code base • Penetration testing used to expose problems • Web applications subject to traditional forms of attack ECE 4112 - Internetwork Security
SQL Injection Vulnerabilities • Stems from failure of developers to strip user input of potentially “nasty” characters prior to input use • Can lead to varying levels of data/system access for attacker • May allow read in or write out to files, execution of shell commands on underlying OS ECE 4112 - Internetwork Security
Locating SQL Injection Vulnerabilities • Studying application inputs and inserting special characters • Most popular database backends give informative error messages, yielding clues about SQL syntax http: //www. abc. com/app. asp? user=jason&password=’ OR ‘ 1’=’ 1 http: //www. abc. com/app. asp? user=jason&password=’ ECE 4112 - Internetwork Security
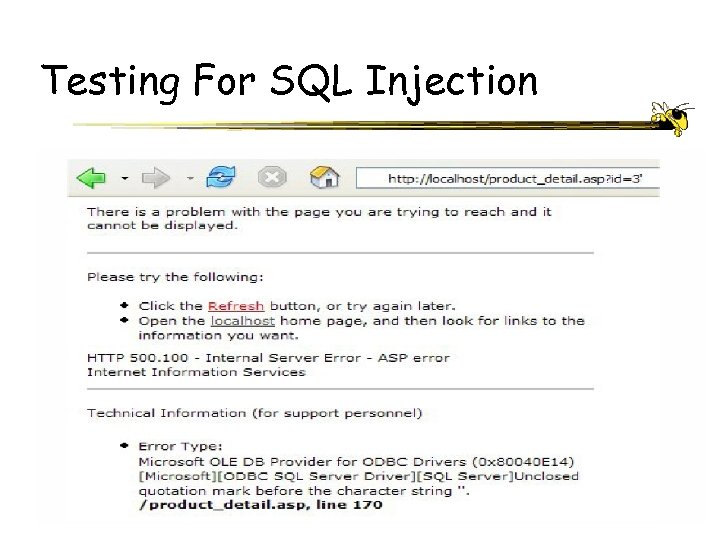
Testing For SQL Injection ECE 4112 - Internetwork Security
JSP Code Example: String username = request. get. Parameter(“user”); String password = request. get. Parameter(“password”); String SQLQuery = “SELECT Username FROM Users WHERE Username = ‘” + username + “’ AND Password = ‘” + password + “’”; Statement stmt = db. Connection. create. Statement(); Result. Set result. Set = stmt. executeuery(SQLQuery); String check. Auth = result. Set. get. String(1); boolean authenticated = false; if(check. Auth == null) authenticated = false; else authenticated = true; ECE 4112 - Internetwork Security
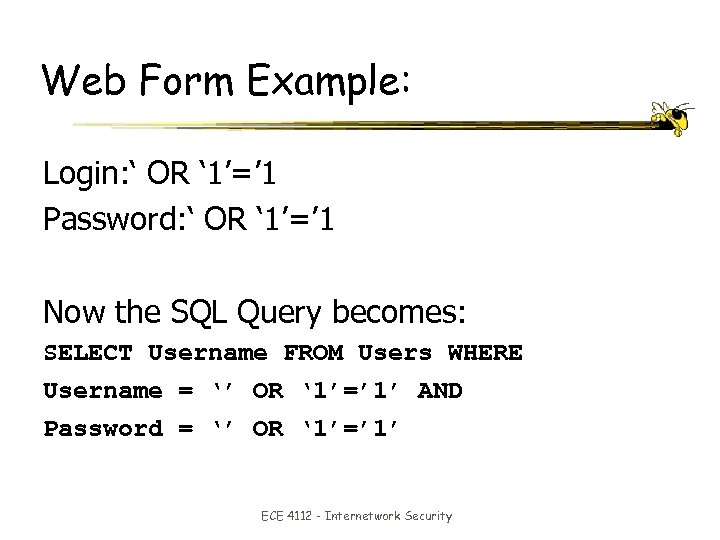
Web Form Example: Login: ‘ OR ‘ 1’=’ 1 Password: ‘ OR ‘ 1’=’ 1 Now the SQL Query becomes: SELECT Username FROM Users WHERE Username = ‘’ OR ‘ 1’=’ 1’ AND Password = ‘’ OR ‘ 1’=’ 1’ ECE 4112 - Internetwork Security

OS Commanding • If a hacker can access your cmd. exe or a copy of it, he can use it to execute arbitrary commands on your web browser. • In conjunction with tftp, a hacker could use this to download his own tools to the machine and compromise the machine further. ECE 4112 - Internetwork Security

Cross Site Scripting • Also known as XSS • Embed Javascript into page that executes on view • Commonly used to display and redirect user cookie data • Particularly vulnerable are message boards and web forms ECE 4112 - Internetwork Security

Cross Site Scripting Examples <script>alert(document. cookie)</script> Can display user’s cookie which can contain session and authentication information • Gmail XSS Vulnerability - Fixed zx variable used in authentication can contain exploitable scripts • Often the script text is converted to hex characters to hide its intent ECE 4112 - Internetwork Security

Phishing Attacks • Attacker creates replica login page that forwards information to them • Usually attack financial institutions • Spread by email that persuades users to access the fake page and login • October 2004, 1142 phishing sites up from 542 in September. ECE 4112 - Internetwork Security

Phishing Examples • Citibank recent target www. citibank. com/domain/email_scam. htm • Newer sophisticated attacks being used by organized crime groups to collect credit card and social security numbers • Email links can contain IP address instead of DNS name in email link ECE 4112 - Internetwork Security
Achilles Web Proxy • Achilles acts as a HTTP/HTTPS proxy that allows a user to intercept, log, and modify web traffic on the fly. • By modifying parameters, a user can potentially alter the contents of hidden fields or gain access to additional resources. • Can also be used to change cookie values. ECE 4112 - Internetwork Security

What you will do in this lab: • Information Gathering using nmap and netcat • SQL Injection • OS Commanding • Cross Site Scripting • Phishing Attacks • Achilles Web Proxy ECE 4112 - Internetwork Security

Resources • Lecture Slides excerpted from: http: //www. securityfocus. com/infocus/1709 http: //www. securityfocus. com/infocus/1722 http: //www. securityfocus. com/infocus/1704 “Phishing spreads the net wider. ” Computer Weekly. November 2004. http: //www. securitytracker. com/alerts/2004/Nov/1012289. html “Cross-Site Scripting. ” SPIDynamics. “Top Web App Attack Methods and How to Combat Them. ” SPIDynamics. http: //www. mavensecurity. com/achilles ECE 4112 - Internetwork Security
a1fd89b03286e96352e4669c9546a4a6.ppt