419059f23f89cca09cb3e0b3b90f7c59.ppt
- Количество слайдов: 26

Weaving a Trust Fabric: Shibboleth & PKI & Grids Keith Hazelton, Copyright 2003 University of Wisconsin-Madison Senior IT Architect Internet 2 MACE member

Copyright Keith Hazelton 2003. This work is the intellectual property of the author. Permission is granted for this material to be shared for non-commercial, educational purposes, provided that this copyright statement appears on the reproduced materials and notice is given that the copying is by permission of the author. To disseminate otherwise or to republish requires written permission from the author. CAMP - June 4 -6, 2003 2

Two (loosely) Connected Presentations • I. Shibboleth (with Auth. N shim) as “Web. ISO plus” • II. Weaving a trust fabric – Trust agreements & architectures – …or when that gets too confusing, reframe as – Risk management agreements & architectures CAMP - June 4 -6, 2003 3

I. Shib (with Auth. N shim) as Web. ISO plus • UW-Madison’s Auth. N/Z Roadmap (Yours, too? ) – Roll out an Auth. N service for campus (web) app developers & integrators – Roll out an Authority Information (Auth. ZInfo) Management service for campus • managing biz-rule based group, affiliation & entitlement assignments • Pops, Affils & Service Entitlements (PASE) Project – Roll out a service for delivering Auth. ZInfo to apps – Decide whether to take the big step of tackling a runtime Auth. Z decision support service for campus CAMP - June 4 -6, 2003 4

UW-Madison Auth. N/Z Roadmap • Got as far as piloting Pub. Cookie as Auth. N service • Along came Shibboleth • …And local interest in PKI heated up with HIPAA • So, we’re now looking at a roadmap with two routes • And we’ll be comparing the alternative routes and making a choice CAMP - June 4 -6, 2003 5
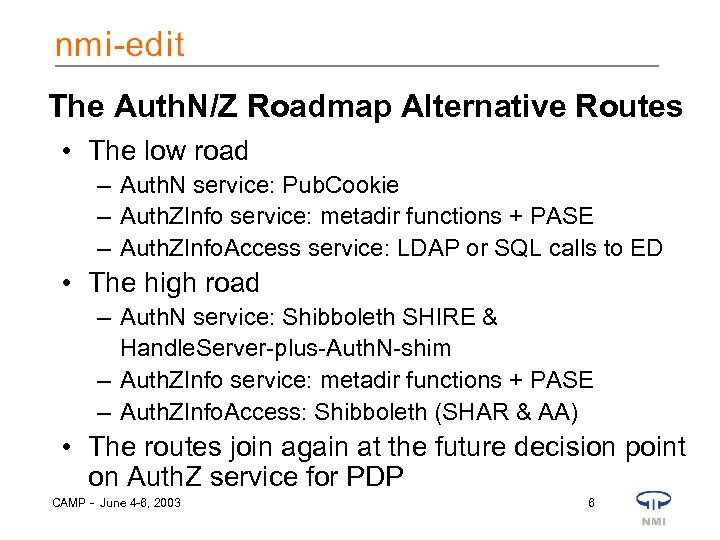
The Auth. N/Z Roadmap Alternative Routes • The low road – Auth. N service: Pub. Cookie – Auth. ZInfo service: metadir functions + PASE – Auth. ZInfo. Access service: LDAP or SQL calls to ED • The high road – Auth. N service: Shibboleth SHIRE & Handle. Server-plus-Auth. N-shim – Auth. ZInfo service: metadir functions + PASE – Auth. ZInfo. Access: Shibboleth (SHAR & AA) • The routes join again at the future decision point on Auth. Z service for PDP CAMP - June 4 -6, 2003 6

The High Road • Shibboleth Plus: Promise of a unified infrastructure for intra- as well as interdomain Auth. N/Z • Note: Shib as delivered assumes an existing Web. ISO CAMP - June 4 -6, 2003 7

The High Road • But in a pure Shib world – the only web thing that needs an authentication step is the Handle Server (HS) (!!!) – all target web apps leverage that single authentication step • So what’s the simplest Auth. N shim for the HS? • (Traditional Web. ISO solutions would have lots of redundant moving parts) CAMP - June 4 -6, 2003 8

The High Road • • • Well, getting techie, HS runs as an Apache app How do we protect Apache apps? URL/directory based auth. N schemes Use Apache config file fiddling to specify how Shib 0. 8 as shipped has way to do this with PKI – Apache Asks for client SSL authentication via apache -ssl or mod_ssl – Right environment variables get populated, presto! CAMP - June 4 -6, 2003 9
The High Road: Shib & PKI • U California System developed PKI support code (David Walker) • Adopted & adapted by UT-HSC Houston (Barry Ribbeck & Mark Jones) • . . and by Dartmouth (Bob Brentrup, Omen Wild & Mark Franklin) CAMP - June 4 -6, 2003 10

The High Road: Shib & PKI • Calif, Texas & Dartmouth pushing PKI, so happy to “force” its use for selected apps • Meanwhile, Wisconsin not there yet • We’re pushing Auth. N/Z service idea generally – For us, PKI is NYRFPT (not prime-time ready) • So, back to the drawing board • What if we could try for PKI as above, but fail over to LDAP-supported un/pw Auth. N over SSL CAMP - June 4 -6, 2003 11

The High Road: Shib & PKI • More generally: Protect the HS app the Apache way with PKI, failover to {your favorite Auth. N service here} • So, coordinating with above named culprits, Ryan Muldoon at wisc. edu is developing an Apache module-based approach • Apache config allows you to specify a list of Auth. N methods in order of preference CAMP - June 4 -6, 2003 12
The High Road: Shib HS & Auth. N Shim • Apache security directives in config allow you to specify a list of Auth. N methods in order of preference, So… • Try PKI via above approach • Second on the list is a module that does your favorite Auth. N trick & populates env. vars. Like REMOTE_USER • Ryan’s got one working at wisc. edu for un/pw with LDAP…intermittently (uses mod_perl) CAMP - June 4 -6, 2003 13

The High Road: Shib HS & Auth. N Shim • Kerberos shops could write a module for Kerberos Auth. N, etc. • Allows transparent… – migration to, or – experimentation with or – selective rollout… • …of PKI behind Shib HS for a general web app Auth. N solution CAMP - June 4 -6, 2003 14

The Journey Completed • To extent we Shibbify our target resources, this takes us all the way to the roadmap junction with the runtime Auth. Z service decision point • We’ve authenticated by choice of methods (which can be passed along to targets) • We’ve given targets controlled access to user attributes • With all the knobs for privacy & anonymity we might want CAMP - June 4 -6, 2003 15

II. Weaving a Trust Fabric CAMP - June 4 -6, 2003 16

Weaving a Trust Fabric • How do typical conversations about risks to IT resources go? – Alice: Please let my people use X – Bob: Sure, but how can I know over the ‘net that person Y really is one of your people? – Alice: Well, I’ll give them this nifty identity credential to present to you – Bob: But from what I know of your policies and procedures, I am not at all sure if I want to trust that credential for accessing my extremely valuable X. Guess I’ll just give them all accounts…. CAMP - June 4 -6, 2003 17

Weaving a Trust Fabric • Does this scale with all the conversations between all the Alices & all the Bobs about all the X’s? • So what we really want is agreement on some coarse grained, graduated scale of risk/(trust) (e. g. , low, medium, high) • And agreed-upon mappings between – an identity credential and this quantized risk/(trust) measure – a resource and this quantized risk/(trust) measure CAMP - June 4 -6, 2003 18

Weaving a Trust Fabric • So then Alice says my people have “medium” level identity credentials • And Bob says, for my valuable X resource, I really want a “high” level credential (so he just gives them each a user account on his X system) • This scales the risk/(trust) measure • How do we scale the Alice / Bob problem? • …federations or communities as the agreeing parties CAMP - June 4 -6, 2003 19
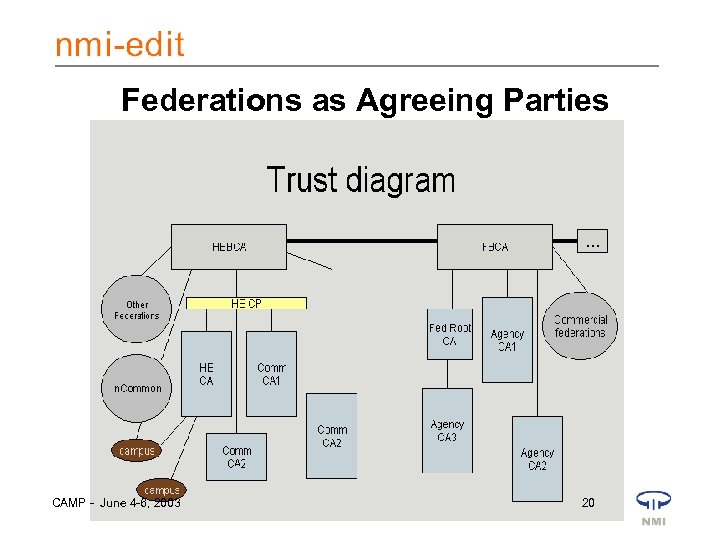
Federations as Agreeing Parties CAMP - June 4 -6, 2003 20

The Trust Diagram • In the PKI world, a Registration Authority (RA) handles – Initial identity proofing – Issuing of identity credential (X. 509 certificate) – …with level of assurance (risk measure) included • Reframe our Photo. ID offices and account creation services as RAs • Then federation partners have potential basis of agreement on risk measure CAMP - June 4 -6, 2003 21

The Trust Diagram • In the PKI world, the CA’s CP & CPS – Explain policies & procedures around identity proofing, protection of CA systems, etc. – On that basis different CAs can agree to map their respective risk measures (your “green” is my “medium”) • For GOF un/pw world, we could create CP & CPSlike things to facilitate mapping • REALITY CHECK TIME: – How have we assessed risk in our GOF un/pw worlds? ? ? – Is all this pushing too hard on the security end of the security convenience balance? CAMP - June 4 -6, 2003 22

Finding the Balance on Security vs. Convenience • Big win for members of federation if we could use the scaling benefits of agreed-upon mappings of identity credentials to risk and resources to acceptable risk • So, maybe its worth the CP/CPS-like work if we want to leverage & interoperate across – GOF un/pw – PKI certs – Grid® certs… CAMP - June 4 -6, 2003 23
Trust Weavers’ Guild • Maximum benefit if we could map as equivalent – – – Campus GOF un/pw PKI Lite certs Grid CA issued identity certs Federal Auth. N Citizen & Commerce Class Cert (C 4) Some (probably lower assurance level of Fed Bridge community certificates) – In. Common resource providers levels of acceptable risk/(trust) CAMP - June 4 -6, 2003 24

Trust Weavers’ Guild • Many, many ratholes & gotchas along the way • But even a patchy fabric with some holes would be a welcome improvement over present state of affairs CAMP - June 4 -6, 2003 25

Weaving a Trust Fabric Q & A • Do you expect to confront these issues in the next year or two? Where? • What’s your biggest point of skepticism on all this trust/risk stuff? CAMP - June 4 -6, 2003 26
419059f23f89cca09cb3e0b3b90f7c59.ppt