3aa0fa3a6e6bbf84181024d4846a34f7.ppt
- Количество слайдов: 55
 Watermarking: What is the Future? Edward J. Delp Purdue University School of Electrical and Computer Engineering Purdue Multimedia Testbed Video and Image Processing Laboratory (VIPER) West Lafayette, IN 47907 -1285 +1 765 494 1740 +1 765 494 0880 (fax) email: ace@ecn. purdue. edu http: //www. ece. purdue. edu/~ace Edward J. Delp Panasonic January 13, 2000 Slide 1
Watermarking: What is the Future? Edward J. Delp Purdue University School of Electrical and Computer Engineering Purdue Multimedia Testbed Video and Image Processing Laboratory (VIPER) West Lafayette, IN 47907 -1285 +1 765 494 1740 +1 765 494 0880 (fax) email: ace@ecn. purdue. edu http: //www. ece. purdue. edu/~ace Edward J. Delp Panasonic January 13, 2000 Slide 1
 Acknowledgements • Students – Eduardo Asbun – Dan Hintz – Paul Salama – Ke Shen – Martha Saenz – Eugene Lin – Ray Wolfgang – Greg Cook – Sheng Liu Edward J. Delp Panasonic January 13, 2000 Slide 2
Acknowledgements • Students – Eduardo Asbun – Dan Hintz – Paul Salama – Ke Shen – Martha Saenz – Eugene Lin – Ray Wolfgang – Greg Cook – Sheng Liu Edward J. Delp Panasonic January 13, 2000 Slide 2
 VIPER Research Projects • Scalable Video and Color Image Compression – still image compression (CEZW) – high and low bit rate video compression (SAMCo. W) – wireless video • Error Concealment • Content Addressable Video Databases (Vi. BE) – Scene Change Detection and Identification – Pseudo-Semantic Scene Labeling • Multimedia Security: Digital Watermarking Edward J. Delp Panasonic January 13, 2000 Slide 3
VIPER Research Projects • Scalable Video and Color Image Compression – still image compression (CEZW) – high and low bit rate video compression (SAMCo. W) – wireless video • Error Concealment • Content Addressable Video Databases (Vi. BE) – Scene Change Detection and Identification – Pseudo-Semantic Scene Labeling • Multimedia Security: Digital Watermarking Edward J. Delp Panasonic January 13, 2000 Slide 3
 VIPER Research Projects • Multicast Video • Analysis of Mammograms • Embedded Image and Video Processing Edward J. Delp Panasonic January 13, 2000 Slide 4
VIPER Research Projects • Multicast Video • Analysis of Mammograms • Embedded Image and Video Processing Edward J. Delp Panasonic January 13, 2000 Slide 4
 Multimedia Security • “Everything” is digital these days - a copy of a digital media element is identical to the original • How can an owner protect their content? • Are images still “fossilized light”? • What does all of this mean in terms of law? • Does any security system really work or does it just make us feel good! Edward J. Delp Panasonic January 13, 2000 Slide 5
Multimedia Security • “Everything” is digital these days - a copy of a digital media element is identical to the original • How can an owner protect their content? • Are images still “fossilized light”? • What does all of this mean in terms of law? • Does any security system really work or does it just make us feel good! Edward J. Delp Panasonic January 13, 2000 Slide 5
 What Do We Want From a Security System? • Access Control • Copy Control Playback Control Record Control Generation Control • Auditing (fingerprinting) – Who did what and when? Edward J. Delp Panasonic January 13, 2000 Slide 6
What Do We Want From a Security System? • Access Control • Copy Control Playback Control Record Control Generation Control • Auditing (fingerprinting) – Who did what and when? Edward J. Delp Panasonic January 13, 2000 Slide 6
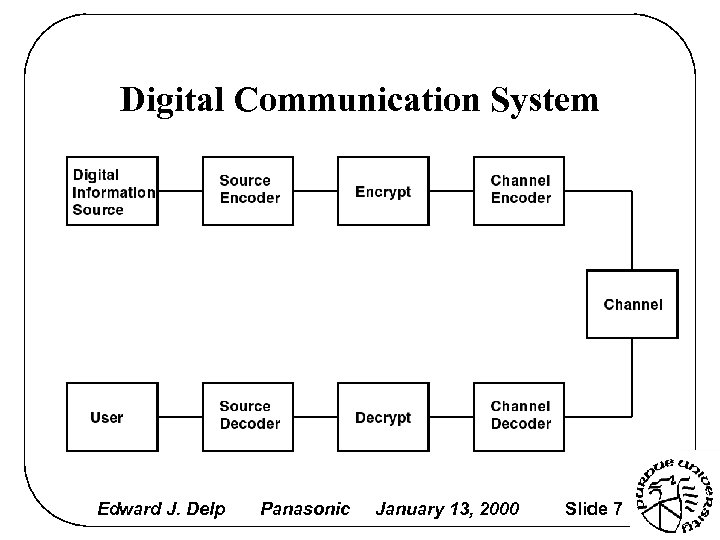 Digital Communication System Edward J. Delp Panasonic January 13, 2000 Slide 7
Digital Communication System Edward J. Delp Panasonic January 13, 2000 Slide 7
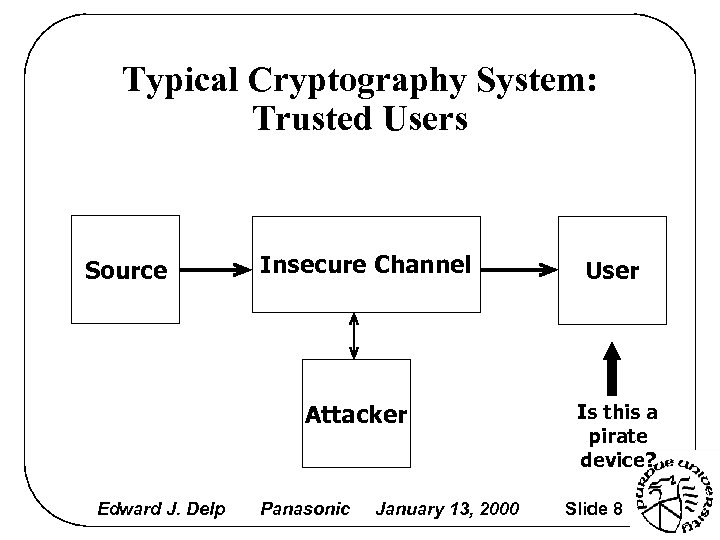 Typical Cryptography System: Trusted Users Source Insecure Channel Attacker Edward J. Delp Panasonic January 13, 2000 User Is this a pirate device? Slide 8
Typical Cryptography System: Trusted Users Source Insecure Channel Attacker Edward J. Delp Panasonic January 13, 2000 User Is this a pirate device? Slide 8
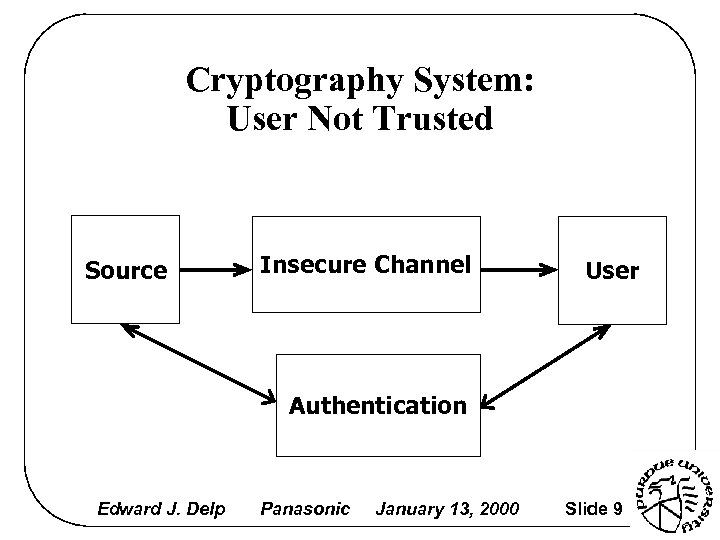 Cryptography System: User Not Trusted Source Insecure Channel User Authentication Edward J. Delp Panasonic January 13, 2000 Slide 9
Cryptography System: User Not Trusted Source Insecure Channel User Authentication Edward J. Delp Panasonic January 13, 2000 Slide 9
 What is Watermarking? • The use of perceptually invisible authentication techniques – “controlled” distortion is introduced in a multimedia element • Visible watermarks also exists Is our community mesmerized by watermarking technology? Edward J. Delp Panasonic January 13, 2000 Slide 10
What is Watermarking? • The use of perceptually invisible authentication techniques – “controlled” distortion is introduced in a multimedia element • Visible watermarks also exists Is our community mesmerized by watermarking technology? Edward J. Delp Panasonic January 13, 2000 Slide 10
 Media Elements • • Audio Video Documents (including HTML documents) Images Graphic or Scene Models Programs (executable code) Edward J. Delp Panasonic January 13, 2000 Slide 11
Media Elements • • Audio Video Documents (including HTML documents) Images Graphic or Scene Models Programs (executable code) Edward J. Delp Panasonic January 13, 2000 Slide 11
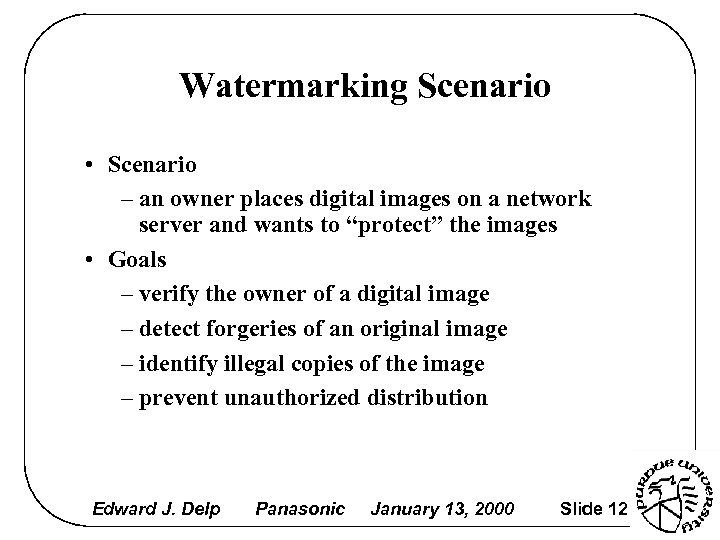 Watermarking Scenario • Scenario – an owner places digital images on a network server and wants to “protect” the images • Goals – verify the owner of a digital image – detect forgeries of an original image – identify illegal copies of the image – prevent unauthorized distribution Edward J. Delp Panasonic January 13, 2000 Slide 12
Watermarking Scenario • Scenario – an owner places digital images on a network server and wants to “protect” the images • Goals – verify the owner of a digital image – detect forgeries of an original image – identify illegal copies of the image – prevent unauthorized distribution Edward J. Delp Panasonic January 13, 2000 Slide 12
 Where are Watermarks Used? • Watermarks have been used or proposed in: – digital cameras – DVD video – audio (SDMI) – broadcast video (in US - ATSC) • visible watermarks now used – “binding” mechanism in image and video databases – key distribution systems – preventing forgery of bank notes Usually as secondary security conversion to “analog” Edward J. Delp Panasonic January 13, 2000 Slide 13
Where are Watermarks Used? • Watermarks have been used or proposed in: – digital cameras – DVD video – audio (SDMI) – broadcast video (in US - ATSC) • visible watermarks now used – “binding” mechanism in image and video databases – key distribution systems – preventing forgery of bank notes Usually as secondary security conversion to “analog” Edward J. Delp Panasonic January 13, 2000 Slide 13
 Steganography - (covered writing) techniques used to hide information within other information to conceal the very existence of the message Used much longer than cryptography Different than crytography in that an illegal user may intercept the message Edward J. Delp Panasonic January 13, 2000 Slide 14
Steganography - (covered writing) techniques used to hide information within other information to conceal the very existence of the message Used much longer than cryptography Different than crytography in that an illegal user may intercept the message Edward J. Delp Panasonic January 13, 2000 Slide 14
 Multimedia Security Applications • • • Privacy Forgery Detection watermarking Copyright Protection watermarking Proof of Purchase (non-deniable) Proof of Delivery (non-deniable) Intruder Detection Edward J. Delp Panasonic January 13, 2000 Slide 15
Multimedia Security Applications • • • Privacy Forgery Detection watermarking Copyright Protection watermarking Proof of Purchase (non-deniable) Proof of Delivery (non-deniable) Intruder Detection Edward J. Delp Panasonic January 13, 2000 Slide 15
 Multimedia Security - Tools Set • Encryption • Authentication • Hashing • Time-stamping • Watermarking Edward J. Delp Panasonic January 13, 2000 Slide 16
Multimedia Security - Tools Set • Encryption • Authentication • Hashing • Time-stamping • Watermarking Edward J. Delp Panasonic January 13, 2000 Slide 16
 Cryptographic Issues for Images • Encryption protects image until decryption • Authentication protects image ownership and content but does not conceal the image • Time stamping verifies an image’s creation date, ownership and content Copy Detection vs. Authentication – copy detection identifies copies of an original image (possibly altered) – authentication determines who owns an image – an altered copy of an image would fail an authentication test Edward J. Delp Panasonic January 13, 2000 Slide 17
Cryptographic Issues for Images • Encryption protects image until decryption • Authentication protects image ownership and content but does not conceal the image • Time stamping verifies an image’s creation date, ownership and content Copy Detection vs. Authentication – copy detection identifies copies of an original image (possibly altered) – authentication determines who owns an image – an altered copy of an image would fail an authentication test Edward J. Delp Panasonic January 13, 2000 Slide 17
 Time Stamps • Time stamps use hash functions to verify a digital work’s time of creation, ownership and content: – When was this data created or last modified? • Two procedures: – certification - the author of the data can "sign" the record, or a user can fix data in time. The result is a certificate – verification - any user can check data and its certificate to make sure it is correct • Time stamping is a form of authentication and requires a “trusted” third party escrow agent • http: //www. surety. com/ Edward J. Delp Panasonic January 13, 2000 Slide 18
Time Stamps • Time stamps use hash functions to verify a digital work’s time of creation, ownership and content: – When was this data created or last modified? • Two procedures: – certification - the author of the data can "sign" the record, or a user can fix data in time. The result is a certificate – verification - any user can check data and its certificate to make sure it is correct • Time stamping is a form of authentication and requires a “trusted” third party escrow agent • http: //www. surety. com/ Edward J. Delp Panasonic January 13, 2000 Slide 18
 Why is Watermarking Important? Edward J. Delp Panasonic January 13, 2000 Slide 19
Why is Watermarking Important? Edward J. Delp Panasonic January 13, 2000 Slide 19
 Why is Watermarking Important? Edward J. Delp Panasonic January 13, 2000 Slide 20
Why is Watermarking Important? Edward J. Delp Panasonic January 13, 2000 Slide 20
 Why Watermarking is Important? Edward J. Delp Panasonic January 13, 2000 Slide 21
Why Watermarking is Important? Edward J. Delp Panasonic January 13, 2000 Slide 21
 Why is Watermarking Important? Edward J. Delp Panasonic January 13, 2000 Slide 22
Why is Watermarking Important? Edward J. Delp Panasonic January 13, 2000 Slide 22
 Why is Watermarking Important? Edward J. Delp Panasonic January 13, 2000 Slide 23
Why is Watermarking Important? Edward J. Delp Panasonic January 13, 2000 Slide 23
 Why is Watermarking Important? Edward J. Delp Panasonic January 13, 2000 Slide 24
Why is Watermarking Important? Edward J. Delp Panasonic January 13, 2000 Slide 24
 Why is Watermarking Important? Edward J. Delp Panasonic January 13, 2000 Slide 25
Why is Watermarking Important? Edward J. Delp Panasonic January 13, 2000 Slide 25
 Why is Watermarking Important? Edward J. Delp Panasonic January 13, 2000 Slide 26
Why is Watermarking Important? Edward J. Delp Panasonic January 13, 2000 Slide 26
 A Overview of Watermarking Techniques • Spatial watermarking • Spatial Frequency (DCT or wavelet) watermarking • Visible watermarks Edward J. Delp Panasonic January 13, 2000 Slide 27
A Overview of Watermarking Techniques • Spatial watermarking • Spatial Frequency (DCT or wavelet) watermarking • Visible watermarks Edward J. Delp Panasonic January 13, 2000 Slide 27
 Components of a Watermarking Technique • The watermark, W – each owner has a unique watermark • The marking algorithm – incorporates the watermark into the image • Verification algorithm – an authentication procedure (determines the integrity / ownership of the image) Edward J. Delp Panasonic January 13, 2000 Slide 28
Components of a Watermarking Technique • The watermark, W – each owner has a unique watermark • The marking algorithm – incorporates the watermark into the image • Verification algorithm – an authentication procedure (determines the integrity / ownership of the image) Edward J. Delp Panasonic January 13, 2000 Slide 28
 Main Principles • Transparency - the watermark is not visible in the image under typical viewing conditions • Robustness to attacks - the watermark can still be detected after the image has undergone linear and/or nonlinear operations (this may not be a good property fragile watermarks) • Capacity - the technique is capable of allowing multiple watermarks to be inserted into the image with each watermark being independently verifiable Edward J. Delp Panasonic January 13, 2000 Slide 29
Main Principles • Transparency - the watermark is not visible in the image under typical viewing conditions • Robustness to attacks - the watermark can still be detected after the image has undergone linear and/or nonlinear operations (this may not be a good property fragile watermarks) • Capacity - the technique is capable of allowing multiple watermarks to be inserted into the image with each watermark being independently verifiable Edward J. Delp Panasonic January 13, 2000 Slide 29
 Attacks • • • Compression Filtering Printing and rescanning Geometric attacks - cropping, resampling, rotation Collusion - spatial and temporal Conversion to analog Edward J. Delp Panasonic January 13, 2000 Slide 30
Attacks • • • Compression Filtering Printing and rescanning Geometric attacks - cropping, resampling, rotation Collusion - spatial and temporal Conversion to analog Edward J. Delp Panasonic January 13, 2000 Slide 30
 DCT Coefficient Modulation • Fixed-length DCT watermark • Variable-length DCT watermark • Scaling of spatial watermark in DCT domain Edward J. Delp Panasonic January 13, 2000 Slide 31
DCT Coefficient Modulation • Fixed-length DCT watermark • Variable-length DCT watermark • Scaling of spatial watermark in DCT domain Edward J. Delp Panasonic January 13, 2000 Slide 31
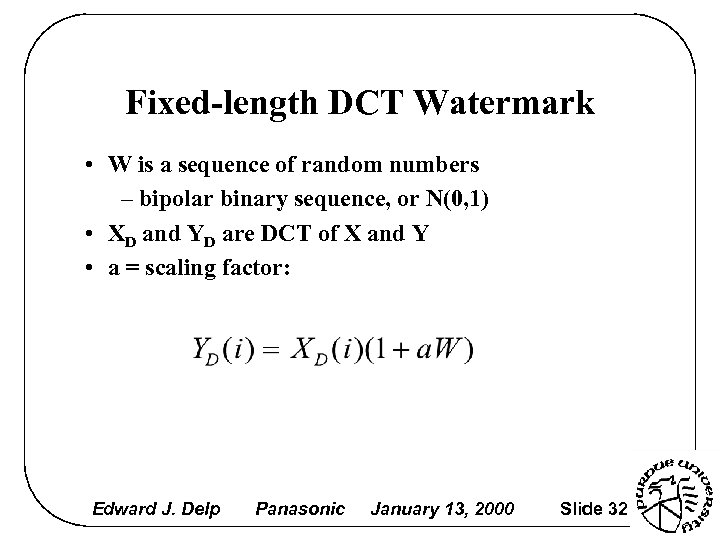 Fixed-length DCT Watermark • W is a sequence of random numbers – bipolar binary sequence, or N(0, 1) • XD and YD are DCT of X and Y • a = scaling factor: Edward J. Delp Panasonic January 13, 2000 Slide 32
Fixed-length DCT Watermark • W is a sequence of random numbers – bipolar binary sequence, or N(0, 1) • XD and YD are DCT of X and Y • a = scaling factor: Edward J. Delp Panasonic January 13, 2000 Slide 32
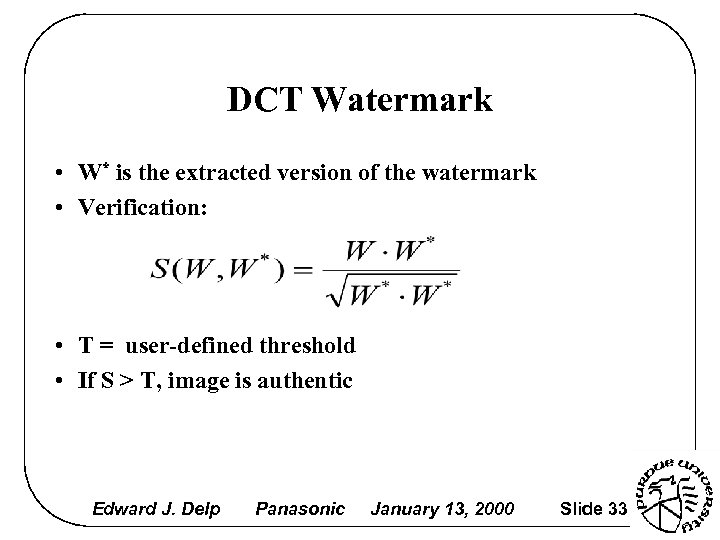 DCT Watermark • W* is the extracted version of the watermark • Verification: • T = user-defined threshold • If S > T, image is authentic Edward J. Delp Panasonic January 13, 2000 Slide 33
DCT Watermark • W* is the extracted version of the watermark • Verification: • T = user-defined threshold • If S > T, image is authentic Edward J. Delp Panasonic January 13, 2000 Slide 33
 Original Image Edward J. Delp Panasonic January 13, 2000 Slide 34
Original Image Edward J. Delp Panasonic January 13, 2000 Slide 34
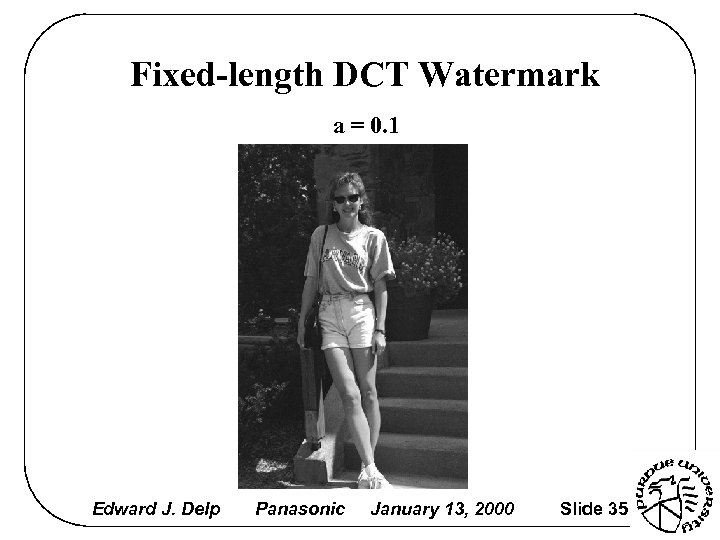 Fixed-length DCT Watermark a = 0. 1 Edward J. Delp Panasonic January 13, 2000 Slide 35
Fixed-length DCT Watermark a = 0. 1 Edward J. Delp Panasonic January 13, 2000 Slide 35
 Fixed-length DCT Watermark a = 0. 5 Edward J. Delp Panasonic January 13, 2000 Slide 36
Fixed-length DCT Watermark a = 0. 5 Edward J. Delp Panasonic January 13, 2000 Slide 36
 Fixed-length DCT Watermark a = 1. 0 Edward J. Delp Panasonic January 13, 2000 Slide 37
Fixed-length DCT Watermark a = 1. 0 Edward J. Delp Panasonic January 13, 2000 Slide 37
 Fixed-length DCT Watermark a = 5. 0 Edward J. Delp Panasonic January 13, 2000 Slide 38
Fixed-length DCT Watermark a = 5. 0 Edward J. Delp Panasonic January 13, 2000 Slide 38
 Current Research Issues • Theoretical Issues – capacity and performance bounds – models of the watermarking/detection process • Robust Watermarks – linear vs. nonlinear – scaling and other geometric attacks – watermarking analog representations of content – new detection schemes – what should be embedded (watermark structure) Edward J. Delp Panasonic January 13, 2000 Slide 39
Current Research Issues • Theoretical Issues – capacity and performance bounds – models of the watermarking/detection process • Robust Watermarks – linear vs. nonlinear – scaling and other geometric attacks – watermarking analog representations of content – new detection schemes – what should be embedded (watermark structure) Edward J. Delp Panasonic January 13, 2000 Slide 39
 Fragile Watermarks • Are we asking too much from a robust watermark? – it is a very interesting signal processing/signal detection problem but will lead to a solution or an arms race • Fragile watermarks do not have to worry about this! Edward J. Delp Panasonic January 13, 2000 Slide 40
Fragile Watermarks • Are we asking too much from a robust watermark? – it is a very interesting signal processing/signal detection problem but will lead to a solution or an arms race • Fragile watermarks do not have to worry about this! Edward J. Delp Panasonic January 13, 2000 Slide 40
 Legal Issues • When one says: “My watermarking withstands the X attack!” – What does it mean? (Has the watermark been damaged? ) – It is legally defensible? – Nearly all watermarks require statistical tests for verification Edward J. Delp Panasonic January 13, 2000 Slide 41
Legal Issues • When one says: “My watermarking withstands the X attack!” – What does it mean? (Has the watermark been damaged? ) – It is legally defensible? – Nearly all watermarks require statistical tests for verification Edward J. Delp Panasonic January 13, 2000 Slide 41
 Research at Purdue • Fragile and semi-fragile watermarks forensic imaging – are fragile watermarks better than hashing? • Extending concept of robust image adaptive watermarks to video (with Chris Podilchuk) – is there a temporal masking model that works? Edward J. Delp Panasonic January 13, 2000 Slide 42
Research at Purdue • Fragile and semi-fragile watermarks forensic imaging – are fragile watermarks better than hashing? • Extending concept of robust image adaptive watermarks to video (with Chris Podilchuk) – is there a temporal masking model that works? Edward J. Delp Panasonic January 13, 2000 Slide 42
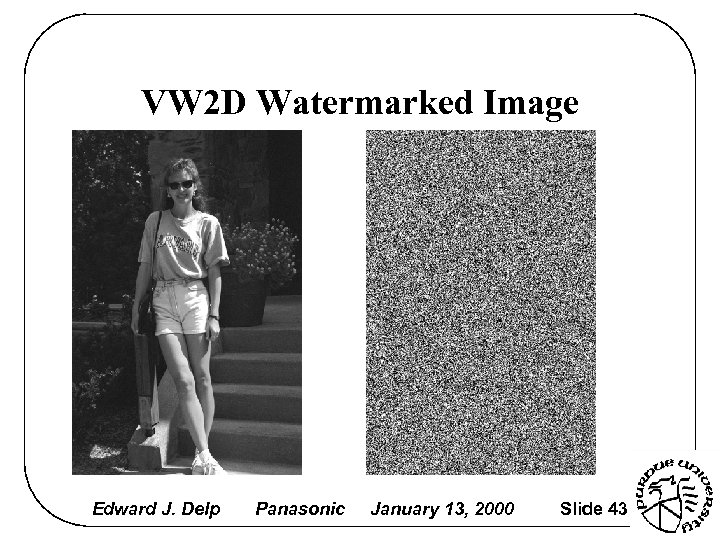 VW 2 D Watermarked Image Edward J. Delp Panasonic January 13, 2000 Slide 43
VW 2 D Watermarked Image Edward J. Delp Panasonic January 13, 2000 Slide 43
 Image Adaptive Watermarks (DCT) Edward J. Delp Panasonic January 13, 2000 Slide 44
Image Adaptive Watermarks (DCT) Edward J. Delp Panasonic January 13, 2000 Slide 44
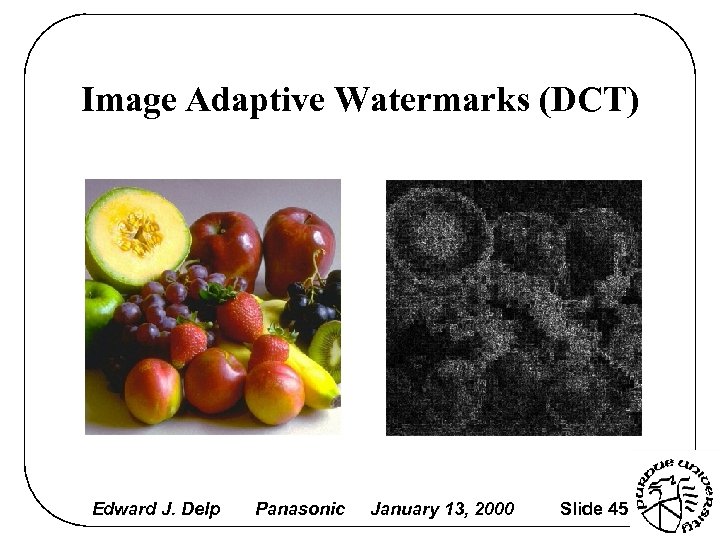 Image Adaptive Watermarks (DCT) Edward J. Delp Panasonic January 13, 2000 Slide 45
Image Adaptive Watermarks (DCT) Edward J. Delp Panasonic January 13, 2000 Slide 45
 “Watermarking” Standards • Data Hiding Subgroup (DHSG) of the Copy Protection Technical Working Group (CPTWG) – two groups have proposed systems for watermarking video used in DVD – watermark will be second level of security after encryption – the watermarks are relatively easy to defeat by difficult to remove Edward J. Delp Panasonic January 13, 2000 Slide 46
“Watermarking” Standards • Data Hiding Subgroup (DHSG) of the Copy Protection Technical Working Group (CPTWG) – two groups have proposed systems for watermarking video used in DVD – watermark will be second level of security after encryption – the watermarks are relatively easy to defeat by difficult to remove Edward J. Delp Panasonic January 13, 2000 Slide 46
 Watermarking: Legal/Political Issues • Watermarking technologies have not been tested in court – is watermarking the “feel good” technology of multimedia? • Might one be better off just doing timestamping and/or other forms of authentication? • What does it mean when a watermarking technique survives an attack (verification based on statistical tests) • Watermarking may always be the secondary security method Edward J. Delp Panasonic January 13, 2000 Slide 47
Watermarking: Legal/Political Issues • Watermarking technologies have not been tested in court – is watermarking the “feel good” technology of multimedia? • Might one be better off just doing timestamping and/or other forms of authentication? • What does it mean when a watermarking technique survives an attack (verification based on statistical tests) • Watermarking may always be the secondary security method Edward J. Delp Panasonic January 13, 2000 Slide 47
 Ownership • Copyright Ownership - Who did it first? timestamp (prevents re-watermarking attacks) Edward J. Delp Panasonic January 13, 2000 Slide 48
Ownership • Copyright Ownership - Who did it first? timestamp (prevents re-watermarking attacks) Edward J. Delp Panasonic January 13, 2000 Slide 48
 Unauthorized Distribution and Illegal Copies • Unauthorized Distribution – You took my image from my web site! – You are selling my image from the CD-ROM you bought from me! • Who owns it? hash and timestamp • Is your image the same as mine? (derived work) Edward J. Delp Panasonic January 13, 2000 Slide 49
Unauthorized Distribution and Illegal Copies • Unauthorized Distribution – You took my image from my web site! – You are selling my image from the CD-ROM you bought from me! • Who owns it? hash and timestamp • Is your image the same as mine? (derived work) Edward J. Delp Panasonic January 13, 2000 Slide 49
 Digital Millennium Copyright Act It will be illegal to remove a watermark for a multimedia element http: //lcweb. loc. gov/copyright/ http: //www. dfc. org/ Edward J. Delp Panasonic January 13, 2000 Slide 50
Digital Millennium Copyright Act It will be illegal to remove a watermark for a multimedia element http: //lcweb. loc. gov/copyright/ http: //www. dfc. org/ Edward J. Delp Panasonic January 13, 2000 Slide 50
 Conclusions • Watermarking is still an interesting research area with many interesting problems – will it be useful? (does it work? ) – will watermarking only be used a second-tier security system? – will there be significant theoretical developments? • Is watermarking the “feel good” technology of multimedia? Edward J. Delp Panasonic January 13, 2000 Slide 51
Conclusions • Watermarking is still an interesting research area with many interesting problems – will it be useful? (does it work? ) – will watermarking only be used a second-tier security system? – will there be significant theoretical developments? • Is watermarking the “feel good” technology of multimedia? Edward J. Delp Panasonic January 13, 2000 Slide 51
 Web Resources http: //www-nt. e-technik. unierlangen. de/~hartung/watermarkinglinks. html Edward J. Delp Panasonic January 13, 2000 Slide 52
Web Resources http: //www-nt. e-technik. unierlangen. de/~hartung/watermarkinglinks. html Edward J. Delp Panasonic January 13, 2000 Slide 52
 Watermarking Conference on Security and Watermarking of Multimedia Contents II (January 23 -28, 2000) in San Jose http: //www. spie. org/web/meetings/calls/pw 00/confs/ ei 23. html Edward J. Delp Panasonic January 13, 2000 Slide 53
Watermarking Conference on Security and Watermarking of Multimedia Contents II (January 23 -28, 2000) in San Jose http: //www. spie. org/web/meetings/calls/pw 00/confs/ ei 23. html Edward J. Delp Panasonic January 13, 2000 Slide 53
 Reference R. B. Wolfgang, C. I. Podilchuk, and E. J. Delp, “Perceptual watermarks for digital images and video, ” Proceedings of the IEEE, July 1999. Available at: ftp: //skynet. ecn. purdue. edu/pub/dist/delp/watermarkproceedings/ Edward J. Delp Panasonic January 13, 2000 Slide 54
Reference R. B. Wolfgang, C. I. Podilchuk, and E. J. Delp, “Perceptual watermarks for digital images and video, ” Proceedings of the IEEE, July 1999. Available at: ftp: //skynet. ecn. purdue. edu/pub/dist/delp/watermarkproceedings/ Edward J. Delp Panasonic January 13, 2000 Slide 54
 How I Spent My Summer Edward J. Delp Panasonic January 13, 2000 Slide 55
How I Spent My Summer Edward J. Delp Panasonic January 13, 2000 Slide 55


