1d7737dbbbe04cc00f06cb60434622f8.ppt
- Количество слайдов: 22

w. LLS, A Better Security Solution for 802. 11 b (an alternative to WEP) by Dick Hibbard VP of Engineering

Agenda 1. 2. 3. 4. 5. 6. 7. 8. Who are we and why we are here Wireless overview Solution Components Technical Specifications Ease of integration Applications Summary

Why We Are Here Fortress offers a highly secure alternative to WEP, w. LLS. Licensing w. LLS provides you with the immediate ability to proliferate the use of your 802. 11 b solutions while…. • Saving on engineering expense • Providing a time to market advantage • Increasing your market share

Experts Say …. “The Wired Equivalent Privacy system has been known from the outset not to be an end-all-be-all security system. ” Greg Ennis, Technical Director of the Wireless Ethernet Compatibility Alliance, Wall Street Journal “WEP has a loophole wide enough to sail a boatload of pirates through: Under WEP, all users of a given access point share the same encryption key. ” Network Computing “WEP’s problems are a result of misunderstanding of some cryptographic primitives and therefore combining them in in insecure ways. ” David Goldberg and David Wagner, University of California-Berkeley “Because of poor design and limitations in security features, many organizations with wireless LANs have, without knowing it, essentially installed Ethernet ports in their parking lots. ” Network Computing

WEP Security Issues • 4 Major Vulnerabilities in WEP – – Single shared static key Weak RC 4 encryption 1 in every 256 of its keys is known to be vulnerable Compromise of the checksum method can occur without detection by the use of bit swapping

Corporate Overview • Founded in 1995 by Dr. Aharon Friedman – World renowned physicist – Former Senior Scientist at Brookhaven Laboratories – Taught at the University of Maryland at the University of Tel Aviv • Fortress’ enabling technologies provide full-featured, totally ubiquitous security solutions for wired and wireless environments. • Patented and validated technologies • A privately owned company, with headquarters in Tampa Bay, Florida

Wireless Overview • Fortress’ wireless solutions are engineered on our Advanced Wireless Security Platform (AWSP). • The governing principles for AWSP include: – – small footprint computationally light simple and automated, delivering ubiquitous security modular and state driven for embedded solutions • AWSP leverages Fortress’ patented and proven technologies such as SPS and ATA

w. LLS Overview • w. LLS is a link layer security protocol that delivers point-topoint security for wireless network communications. • Seamlessly integrates with 802. 11 b, solving the security inadequacies uncovered in WEP. • Fully automates all critical security operations including encryption, authentication, data integrity checking, key exchange and data compression, eliminating human intervention. • Has a small footprint and is computationally light, making it ideal for embedded solutions or easy integration into any standard hardware platform over various operating systems.

w. LLS Solves WEP Deficiencies

w. LLS Solves WEP Deficiencies
w. LLS Components • Link layer encryption - application and network protocol independent • Encrypted Diffie-Hellman Key Exchange (prevents man-in-the-middle attacks. ) • Dynamic key regeneration - encryption keys are changed every 2 hours • Modular Encryption Algorithms - IDEA, DES, 3 DES supported
w. LLS Components continued • Frame manipulation - Utilizes a unique MAC protocol ID which is only recognized by w. LLS devices • Unique Digital Signature - to ensure communications only within the specified network. • Strong Authentication - ensures frame integrity through key encryption and hashing • Frame payload compression - disguises original length of frame and its contents
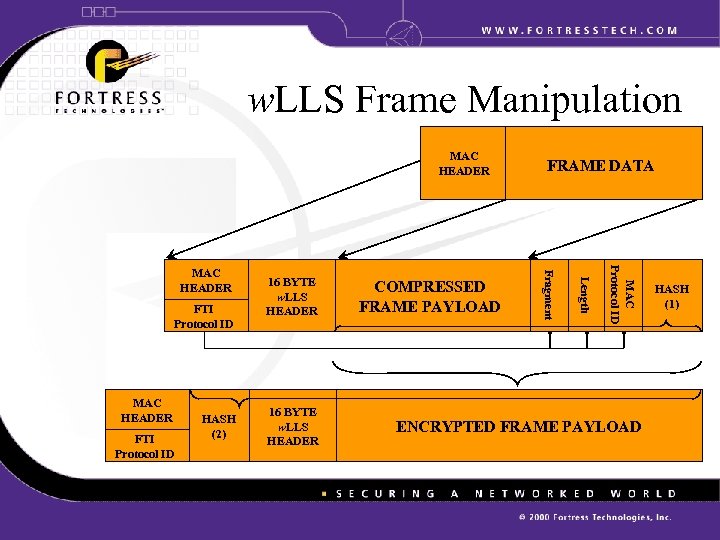
w. LLS Frame Manipulation MAC HEADER FTI Protocol ID HASH (2) 16 BYTE w. LLS HEADER MAC Protocol ID MAC HEADER COMPRESSED FRAME PAYLOAD Length FTI Protocol ID 16 BYTE w. LLS HEADER Fragment MAC HEADER FRAME DATA ENCRYPTED FRAME PAYLOAD HASH (1)
Specifications • • Co-exists transparently with WEP Layer 2 Virtual Driver Approximately 200 k in size Works in conjunction with 802. 11 b compliant NICs and networks • Works across multiple hardware platforms: PDA, laptops etc. • Currently runs on 95, 98, 2000, NT and Linux
Specifications continued • Easily ported to other OS platforms such as CE, Palm, Epoc, Opus and Vx. Works • Smart encryption enables secure communications between station-to-AP (Infrastructure Mode) or station-to-station (Ad-hoc Mode) • Uses the patented Secure Packet Shield (SPS) protocol – FIPS 140 -1 and SPOCK Validated
Simple Migration • w. LLS enabled Access Points & Clients seamlessly co-exists with WEP • w. LLS automatically attempts to negotiate a w. LLS connection with a w. LLS peer, transparent to WEP enabled/disabled devices • w. LLS provides a simple and seamless migration alternative for WEP, requiring no overlays or code replacement
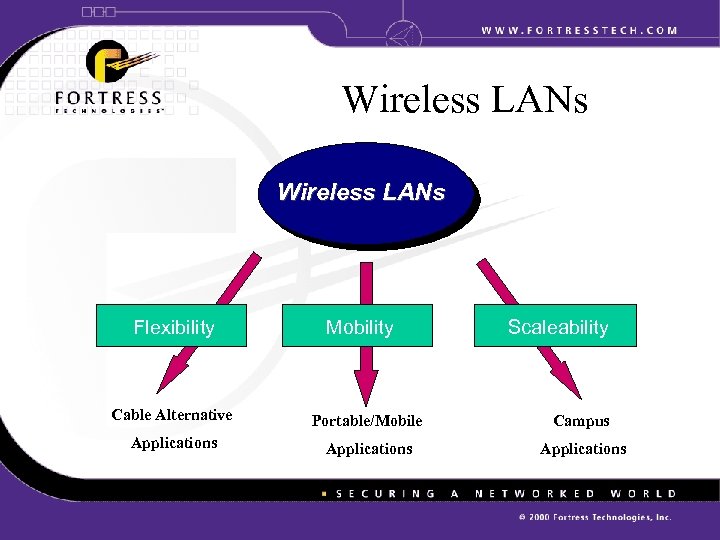
Wireless LANs Flexibility Mobility Scaleability Cable Alternative Portable/Mobile Campus Applications

Wireless LANs Ad-hoc Mode • • Departmental LAN No Wiring Cards in each PC/Server Access Point not needed
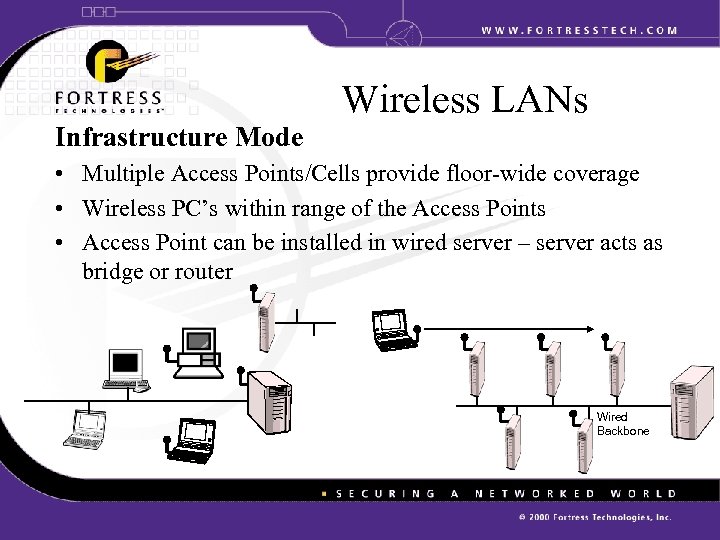
Infrastructure Mode Wireless LANs • Multiple Access Points/Cells provide floor-wide coverage • Wireless PC’s within range of the Access Points • Access Point can be installed in wired server – server acts as bridge or router Wired Backbone
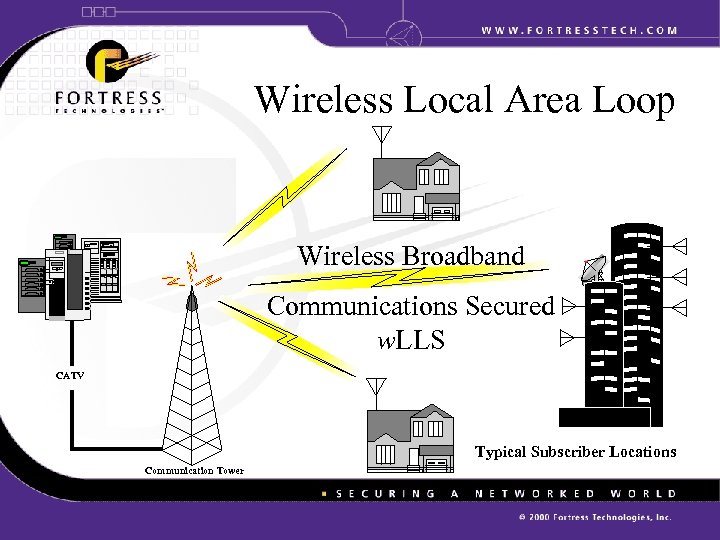
Wireless Local Area Loop Wireless Broadband IDC Communications Secured w. LLS CATV Typical Subscriber Locations Communication Tower

Conclusion • w. LLS solves the security issues inherent in 802. 11 b. • w. LLS is the only comprehensive wireless security solution available today. • w. LLS is based on proven technology.

Securing A Networked World
1d7737dbbbe04cc00f06cb60434622f8.ppt