e47c8d408da0a0de15d72c4f28e47c93.ppt
- Количество слайдов: 22

Vulnerability Assessment Using SAINT Jane Lemmer Information Security Specialist World Wide Digital Security, Inc. lemmerj@wwdsi. com June 16, 1999

Outline The Problem The First Solution The Second Solution Other Uses for SAINT What’s Next Conclusions June 16, 1999 2
The Problem Large network y 7 Class B subnets, over 20 Class C subnets No central management Some resistance to “outsiders” How do we do a vulnerability assessment? June 16, 1999 3

The First Solution The Scanning Tool The Scanning Method Results Problems Lessons Learned June 16, 1999 4
The First Solution The Scanning Tool Conducted a comparison of several network based vulnerability assessment tools y Internet Security Scanner y Kane Security Analyst y SATAN y Nessus, and a few others June 16, 1999 5

The First Solution The Scanning Tool Chose SATAN, with COAST extensions y free y fairly easy to use y sufficient for providing a first look at overall network vulnerability June 16, 1999 6
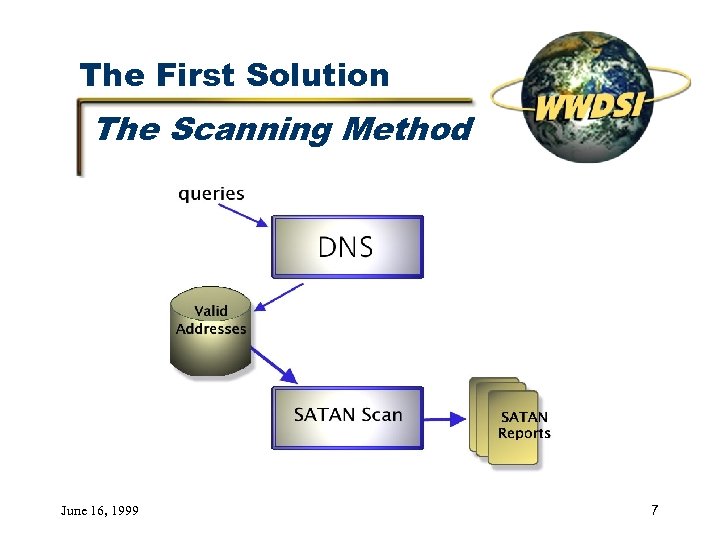
The First Solution The Scanning Method June 16, 1999 7

The First Solution Results Lasted three weeks Approximately 20, 000 potential hosts interrogated Found about 5, 000 hosts with services Inexpensive (almost automatic) June 16, 1999 8

The First Solution Problems Took almost a month to process the results into a useable format Missed many hosts (DHCP, hosts not in DNS, especially Linux boxes) Organizational problems (results not getting to the right people) Scapegoats for a host of network problems June 16, 1999 9

The First Solution Lessons Learned DNS method is not finding all the hosts SATAN is not current Report generation takes too long We need the following: ya new scanning tool y a new scanning method y a new reporting method June 16, 1999 10

The Second Solution The Scanning Tool The Scanning Method Results Problems Lessons Learned June 16, 1999 11

The Second Solution The Scanning Tool y An updated version of SATAN y Added many new tests y Added a new attack level y Changed how vulnerable services are categorized y Works in firewalled environments y Identifies Windows boxes y Developed extensive tutorials for each vulnerable service y Developed an in-house tool to help with reports June 16, 1999 12

The Second Solution The Scanning Tool y The three “r” services (rlogin, rshell, rexec) y Vulnerable CGIs y IMAP vulnerabilities y SMB open shares y Back Orifice and Net. Bus y Tool. Talk y Vulnerable DNS servers y rpc. statd service y UDP echo and/or chargen y IRC chat relays June 16, 1999 13
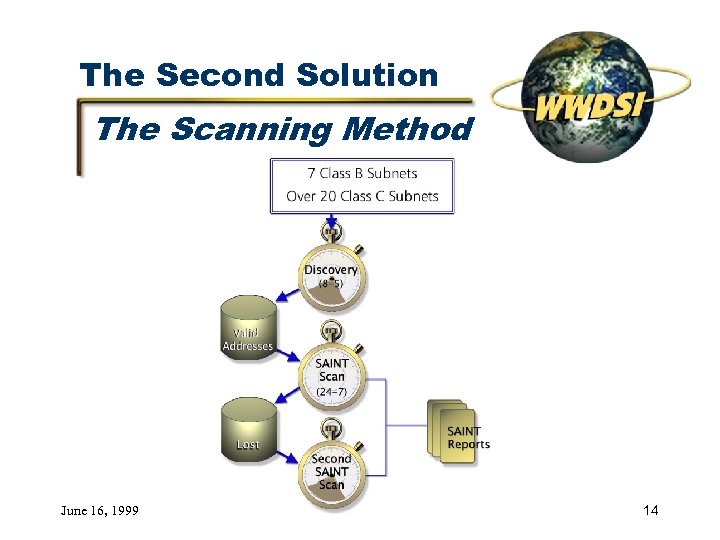
The Second Solution The Scanning Method June 16, 1999 14

The Second Solution Results Lasted two months Almost 500, 000 potential hosts interrogated Found many more hosts y approximately 7, 000 boxes with services y approximately 4, 000 boxes with no services y almost 8, 000 Windows boxes More costly (labor intensive) June 16, 1999 15

The Second Solution Problems Scanning takes longer Difficult to compare results with previous scan Organizational problems (results still not getting to the right people) Caused some problems with NT boxes Still a scapegoat for network problems June 16, 1999 16

The Second Solution Lessons Learned New method finds more hosts but takes longer SAINT needs to be continually updated Scanning can help improve the tool Still need to work on reporting results June 16, 1999 17
Other Uses for SAINT gathers a lot of information that is not reported used to produce a list of UNIX hosts by OS type y used to identify web servers y used to identify routers y Quick scans of a host or subnet June 16, 1999 18
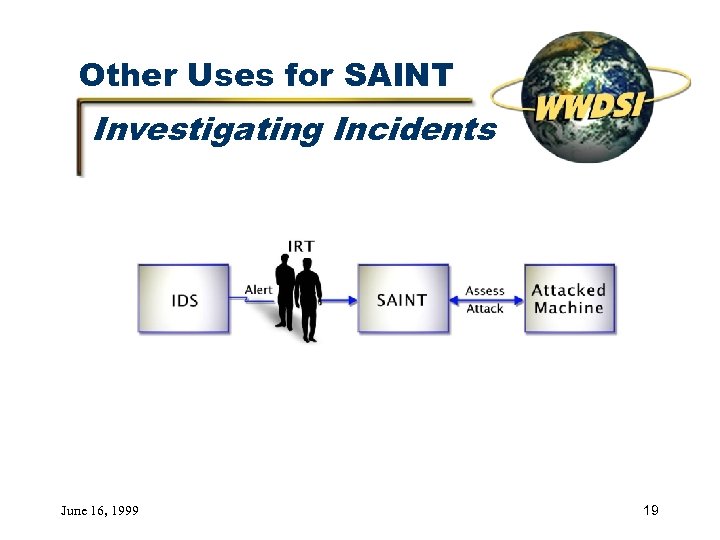
Other Uses for SAINT Investigating Incidents June 16, 1999 19
What’s Next Continue using SAINT for large scans Supplement SAINT with more robust tools Scans have led to development of an IRT defining policy y defining standard security configurations y helping users secure hosts y developing centralized site for security information y June 16, 1999 20

Conclusions SAINT is a useful tool for scanning large networks Results give a good first look at how vulnerable you are SAINT must be continually updated better OS typing y better reporting y method to compare scan results y June 16, 1999 21

Contact Information World Wide Digital Security, Inc. 11260 Roger Bacon Drive, Suite 400 Reston, VA 20910 USA PHONE: +1 703 742 -6604 FAX: +1 703 742 -6605 http: //www. wwdsi. com June 16, 1999 22
e47c8d408da0a0de15d72c4f28e47c93.ppt