622b3f874ee8220e03b369649ef0aa2e.ppt
- Количество слайдов: 31

Vulnerability Analysis

Vulnerability Analysis n Formal verification n Penetration testing n n n Formally (mathematically) prove certain characteristics Proves the absence of flaws in a program or design but not in a system Attempt to violate specific constrains stated in a policy Cannot prove correctness but absence of a vulnerability Review

Penetration Testing n Goals n n n Prove the existence/absence of a previously defined flaw Find vulnerabilities under given restrictions (time, resources, . . . ) Layering of tests n n n External attacker with no knowledge of the system External attacker with knowledge of the system Internal attacker with knowledge of the system

Penetration Testing Procedure n Information gathering n n Flaw hypothesis n n Verify the possible flaws (exploiting, testing) – but no harming! Flaw generalization n n Derive possible flaws from the information gathered Flaw testing n n Find problem areas in the specification Generalize the obtained insights Flaw elimination proposal n Flaws need to be fixed but sometimes this takes time and than the tester can suggest ways to prevent the exploit
Vulnerability Scanners n Automated tools to test if the network or host is vulnerable to known attacks n Run in batch mode against the system n Process n n A set of system attributes are sampled and stored The results are compared to a reference set and the deviation derived

Nessus n The Nessus Security Scanner is a security auditing tool made up of two parts: n n n The server, nessusd is in charge of the attacks The client nessus provides an interface to the user Nessusd inspect the remote hosts and attempts to list all the vulnerabilities and common misconfigurations that affects them. Nessus can be set up to use other tools such as Nmap and Hydra. New plug-ins can be downloaded or written in the nasl scripting language.

ISS n n n Internet scanner is a commercial security analysis tool similar to Nessus. It also consists of two parts a console and a sensor that is the client and server part of ISS. Runs exclusively on Windows systems. New pluggins can be downloaded or written as programs in C or Perl and added through the Flex. Check system. ISS and Nessus are the most popular security analysis tools
Network Based Analysis n Probing the system actively by n n n Looking for weaknesses Derive information from system responses Two different techniques n n Testing by exploit – really doing the attack Interference Methods – monitoring the system for vulnerable applications
Host Based Analysis n n n Assessing system data sources (file contents, configuration setting, status information) to determine vulnerabilities Passive assessment where the tool has legitimated access which mostly involves privilege escalation attacks Targets are password files, SUID, access permissions, anonymous ftp. . .

Advantage/Disadvantage + n n n Helping to document the security state of a system Regular application can spot system changes which could lead to problems A way to double-check any changes made to the system n n Host based are tightly bound to the environment Network based can harm the system and are more prone to false alarms Can misguide a running IDS system May violate legal prescriptions (privacy, others sphere of influence. . . )

Risk analysis

Terms - Risk n Risk constitutes from the expected likelihood of a hazardous event and the expected damage of the event. DIN, VDE Norm 31000, n Risks are a function of the values of the assets at risk, the likelihood of threats occurring to cause the potential adverse business impacts, the ease of exploitation of the vulnerabilities by the identified threats, and any existing or planned safeguards which might reduce the risk. ISO 13335 – Guidelines for the management of IT Security (GMITS)

Terms - Risk Analysis n The total process to identify, control, and manage the impact of uncertain harmful events, commensurate with the value of the protected assets. National Information Systems Security Glossary

Risk Analysis Approaches n Bottom up n The risk is an aggregate of lower level risks n n n e. g. The risk that a phone break is a aggregation of the risk of the consiting parts Mainly used in technical risk analysis Top down n n The risk is detailed to derive more clarity Mainly use in organizational risk analysis

Risk Analysis Approaches n Baseline Approach n n Informal Approach n n Pragmatic risk analysis Detailed Risk Analysis n n Do not analysis but apply baseline security In-depth valuation of assets, threat assessment and vulnerability assessment Combined Approach n Initial high level approach where important systems are further analysis with a detailed approach ISO 13335 – Guidelines for the management of IT Security (GMITS)

Risk Identification n Checklists/Best practices n n RA Tools (e. g. CRAMM, COBRA …) Standards n n . . . Mathematical Approaches n n ISO 17799, ISO 13335, Common criteria Basic Protection Manual (Grundschutzhandbuch) Trend Analysis, Regression Analysis. . . Creative approaches n Brainstorming, Delphi Method. .

Risk Assessment n Assess the values for a risk (per asset) n n n How likely is it ? How harmful is it? Assessment Approaches n Mathematical/Statistical Methods n n n Simulation n n Time line analysis (Trend Analysis) Regression analysis Monte Carlo Simulation Expert guesses

Risk Assessment n Severity Analysis n n Qualitative Methods n n Calculate the risk; r = p * e Abstract values for ranking (high – low effect, high – low likelihood) Quantitative Methods n Specific values indicating severity (p=0. 32, e = 1000 or e = 0. 43)

Risk countermeasures n Avoidance n n A measurement is chosen (respectively not chosen) so that the risk can not emerge. Reduction n of threat n n of vulnerability n n the cause of the risk is tried to be reduce. reducing the vulnerability of impact n reduce the effects

Risk countermeasures n Detection n n Recovery n n establish a recovery strategy Transfer n n identified when the risk is emerging – eliminating the risk source transfer the risk to a third party Acceptance n Preconditions set by the management n n Residual Risk - The maximal acceptable risk Final decision made by the management

AS/NZS: 4360 RM Process n Identify Context n n Identify Risks n n Determine Likelihood and consequences Evaluate Risk n n What can happen and how Analyze Risks n n Define the organizational context Compare against criteria and set priorities Treat Risk n Identify treatment options and decide for one

Process after ISO 17799 n n n Asset Identification Threat Assessment Vulnerability Assessment Safeguard Assessment Risk Assessment

Security Policy

Policy - Terms and definitions n As security policy is a formal statement of the rules by which people who are given access to an organization’s technology and information assets must abide. Security Policy (Site Security Handbook, B. Fraser)

Policy classification n Language n n n Formal languages (mathematics, state engines, constrain languages Natural language (normative languages, free speech) Target n n Product (mostly a technical system) Overall (mostly an organization or humans)
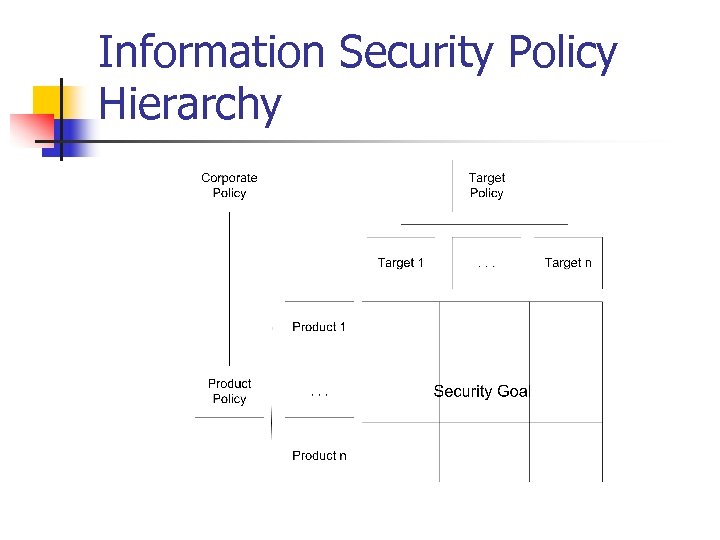
Information Security Policy Hierarchy

Overall Policy n n n Expresses policy at the highest level of abstraction A statement about the importance of information resources Management and employee responsibility Critical and subsequent security requirements As a subdocument acceptable risks and budgets

Requirements to a policy n n n Policies need to set a high enough level to guide for longer time periods Demonstrate organizational commitment to security Position of responsibility to owners, partners and public Hierarchy of policies Concordant with organizational culture and norms
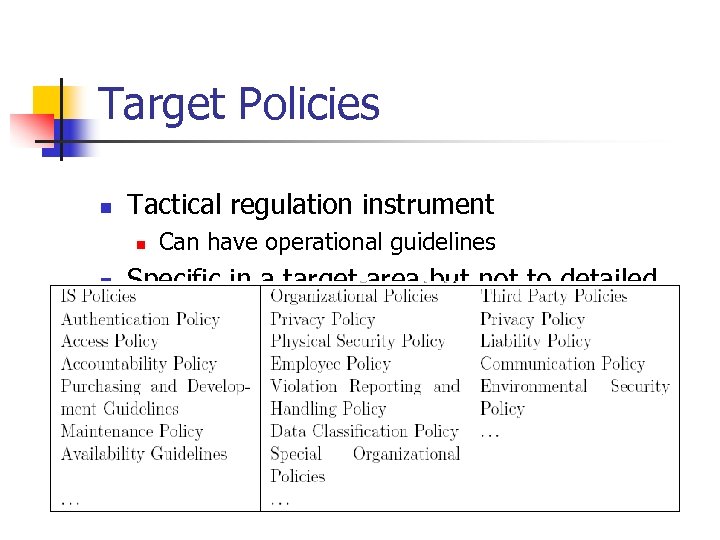
Target Policies n Tactical regulation instrument n n Can have operational guidelines Specific in a target area but not to detailed

Product policy n Requirements to the product n n n Additional Security Relaxing other policies Formulating special target policies for products n n Privacy Confidentiality statements Reliability statements. . .
Questions ?
622b3f874ee8220e03b369649ef0aa2e.ppt