aac45fb695f537324c316f59bd091904.ppt
- Количество слайдов: 66
Vulnerabilities of Cellular and Satellite-based Voice and Data Networks Dan Veeneman dan@decodesystems. com www. decodesystems. com/blackhat/bh-2. ppt Vulnerabilities of Cellular and Satellite- Black Hat Briefings July 31, 2002 based Voice & Data Networks

Focus of this talk • Practical security problems • Industry responses • Lessons (hopefully) learned from mistakes Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 2

Practical Operator Considerations • Getting paid – Prevent (limit) subscriber fraud – Ensure accurate clearing with other operators • • • Reduce churn Ensure sufficient capacity Provide CALEA compliance Maintain public perception of security Provide additional features (marketing) Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 3
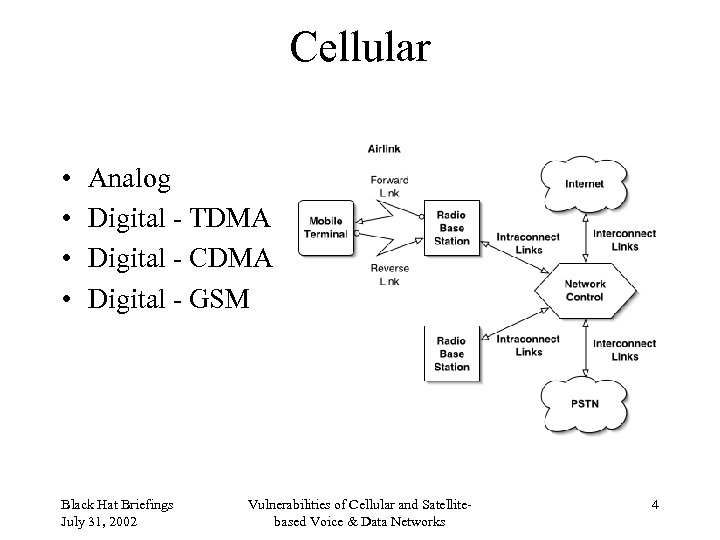
Cellular • • Analog Digital - TDMA Digital - CDMA Digital - GSM Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 4
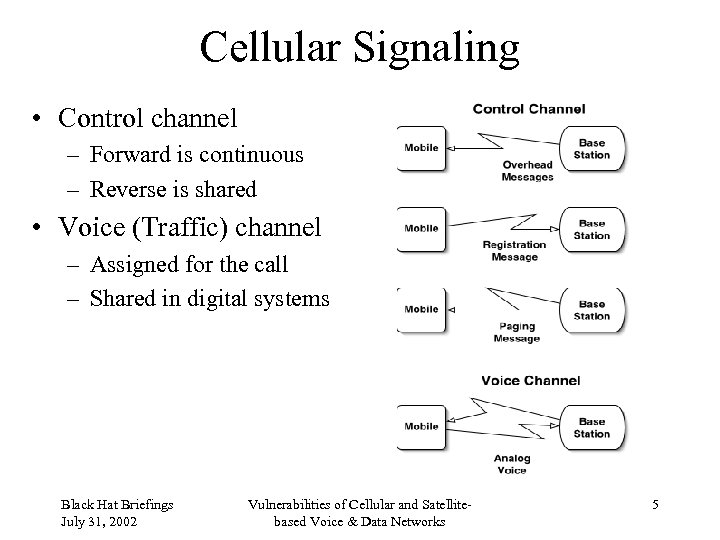
Cellular Signaling • Control channel – Forward is continuous – Reverse is shared • Voice (Traffic) channel – Assigned for the call – Shared in digital systems Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 5
Analog Cellular • Authentication is valid Electronic Serial Number (ESN) and Mobile Identification Number (MIN) pair • Sent from mobile to base in the clear • Early systems had just a “deny” list • Not all systems initially available to each other for roaming verification Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 6

Phone Theft • Automobile “smash and grab” • Use until service is canceled • Call-sell operations Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 7

Database Theft • • Dumpster diving Insider account maintenance Hack into authorization database Hack into switch maintenance port Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 8

Rogue Base Station • Forward link has no authentication • Mobiles lock to false outbound • Cell phone suppressor • Test equipment (ESN readers) Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 9
Network Interception • Read pairs on link between base station and switch • Microwave in many areas Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 10

Tumbling • • ESN/MIN pair sent to home system Pre-call validation not available First call allowed to go through “Tumble” through random ESN/MIN pairs Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 11
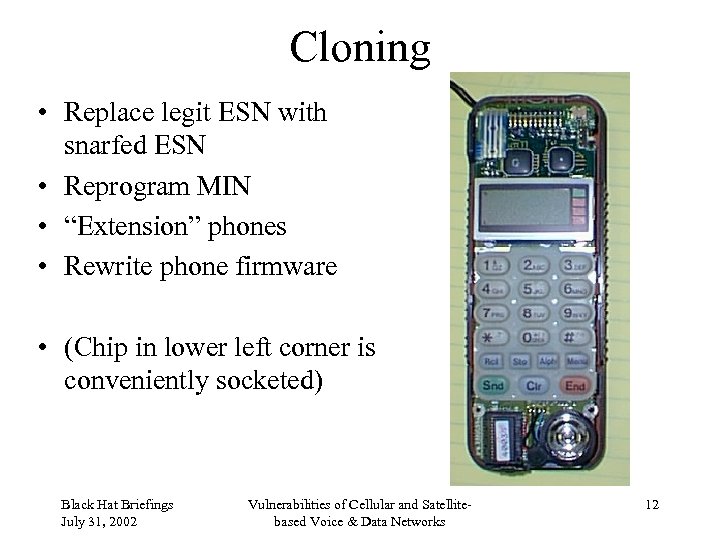
Cloning • Replace legit ESN with snarfed ESN • Reprogram MIN • “Extension” phones • Rewrite phone firmware • (Chip in lower left corner is conveniently socketed) Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 12
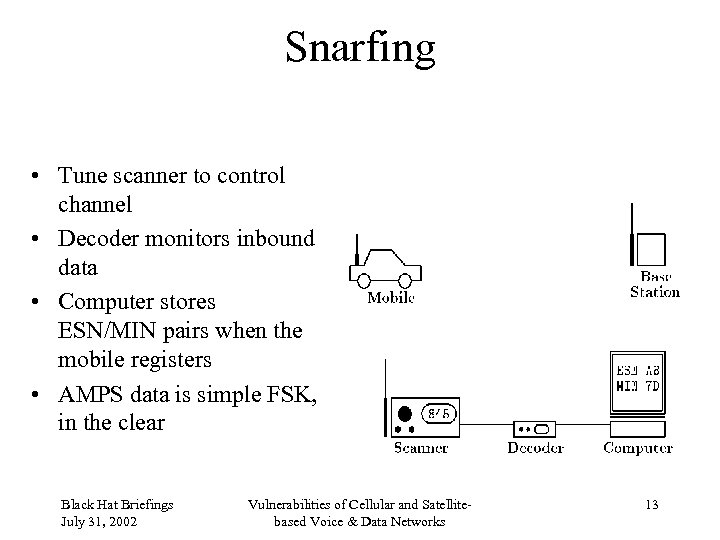
Snarfing • Tune scanner to control channel • Decoder monitors inbound data • Computer stores ESN/MIN pairs when the mobile registers • AMPS data is simple FSK, in the clear Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 13
Subscription Fraud • Sign up for service under false identity • “Identity Theft” Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 14
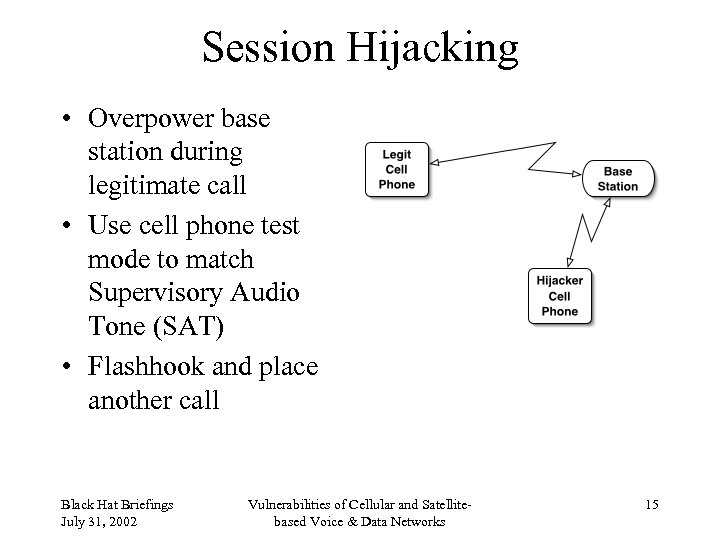
Session Hijacking • Overpower base station during legitimate call • Use cell phone test mode to match Supervisory Audio Tone (SAT) • Flashhook and place another call Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 15

Fighting Analog Fraud • Legal – Illegal to eavesdrop – Illegal to clone – Illegal to possess equipment that might be used to clone • Technical – PINs • Customers hated this – Velocity checks • Good for roaming, not great for local clones – Don’t allow more than one active at a time – RF Fingerprinting Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 16

2 G Authentication • Generally, mobile is given a challenge and network checks the response • US Digital Cellular – Cellular Authentication and Voice Encryption (CAVE) – Control Message Encryption Algorithm (CMEA) – Voice Privacy Mask (VPM) • GSM – A 3 Authentication – A 8 cipher key generation – A 5 privacy Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 17

Cellular Authentication and Voice Encryption • • A-key, 64 bits (20 digits plus 6 check digits) RANDSSD: 56 bits Electronic Serial Number (ESN): 32 bits Shared Secret Data (SSD) – SSD_A: 64 bits, for authentication – SSD_B: 64 bits, for encryption • Authentication Result, AUTHx: 18 bits • Unique Challenge – Uses voice channel during call attempts • Global Challenge – Uses control channel, checks during registration, call attempt and call delivery – All phones challenged with the same number Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 18
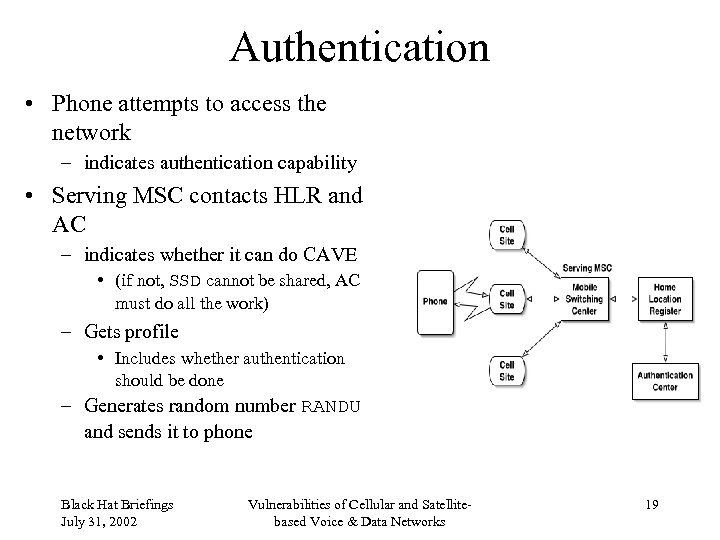
Authentication • Phone attempts to access the network – indicates authentication capability • Serving MSC contacts HLR and AC – indicates whether it can do CAVE • (if not, SSD cannot be shared, AC must do all the work) – Gets profile • Includes whether authentication should be done – Generates random number RANDU and sends it to phone Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 19
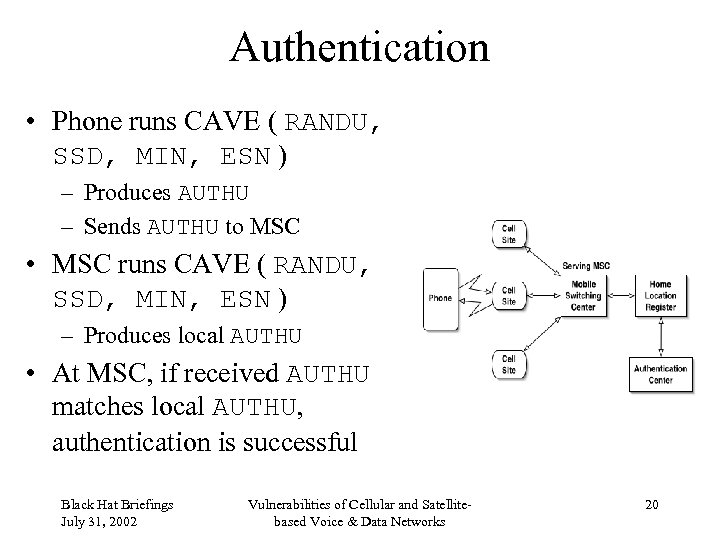
Authentication • Phone runs CAVE ( RANDU, SSD, MIN, ESN ) – Produces AUTHU – Sends AUTHU to MSC • MSC runs CAVE ( RANDU, SSD, MIN, ESN ) – Produces local AUTHU • At MSC, if received AUTHU matches local AUTHU, authentication is successful Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 20

Shared Secret Data Update • Phone and AC update their SSD – AC generates RANDSSD • Sends it to Serving MSC • Computes SSD from RANDSSD, ESN, A-key – MSC sends RANDSSD to phone – Phone generates SSD from RANDSSD, ESN, A-key • Phone authenticates Base Station (or AC) – – – – Generates RANDBS Calculates AUTHBS from RANDBS and new SSD Sends RANDBS to Serving MSC Either MSC or AC uses RANDBS and new SSD to calculate AUTHBS MSC sends AUTHBS to phone If phone AUTHBS and MSC AUTHBS match, phone stores new SSD Another authentication process is performed • If successful, AC stores new SSD Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 21

Count • Mobile maintains a 6 -bit COUNT variable • Incremented on instruction from AC • AC maintains COUNT for each mobile • COUNT values must match in order for mobile to gain access Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 22

Weaknesses • Information sent in the clear on interconnection networks (SS 7, etc) • Secret information held in vulnerable locations (HLR, VLR, etc) • CMEA “broken” • Small keysize • Poor A-keys • VPM fixed for the length of the call – XOR against known voice (e. g. silence) Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 23

Global System for Mobiles • Handsets and SIMs • International Mobile Equipment Identifier (IMEI) • International Mobile Subscriber Identity (IMSI) Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 24
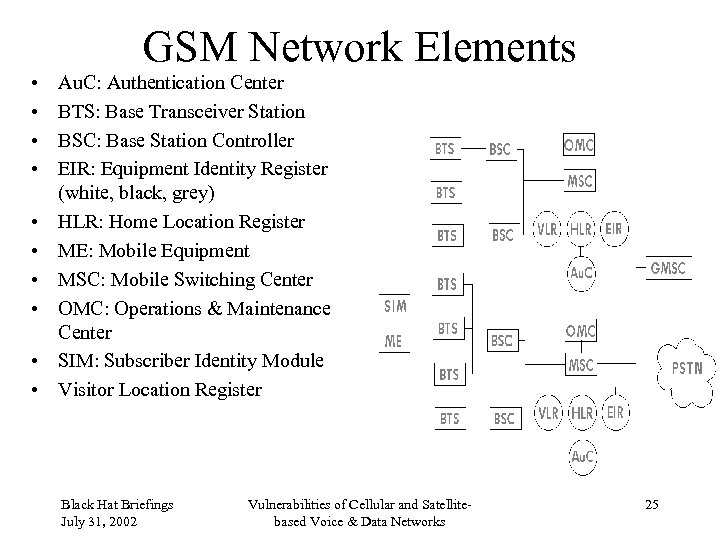
GSM Network Elements • • • Au. C: Authentication Center BTS: Base Transceiver Station BSC: Base Station Controller EIR: Equipment Identity Register (white, black, grey) HLR: Home Location Register ME: Mobile Equipment MSC: Mobile Switching Center OMC: Operations & Maintenance Center SIM: Subscriber Identity Module Visitor Location Register Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 25

GSM Security Goals The objective of security for GSM system is to make the system as secure as the public switched telephone network. The use of radio at the transmission media allows a number of potential threats from eavesdropping the transmissions. It was soon apparent in the threat analysis that the weakest part of the system was the radio path, as this can be easily intercepted. The GSM Mo. U Group produces guidance on these areas of operator interaction for members. The technical features for security are only a small part of the security requirements, the greatest threat is from simpler attacks such as disclosure of the encryption keys, insecure billing systems or corruption ! A balance is required to ensure that these security processes meet these requirements. At the same time a judgment must be made of the cost and effectiveness of the security measures. Charles Brookson Chairman GSM Mo. U Security Group Mercury one 2 one Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 26

Anonymity • Temporary identifiers. • When a user first switches on his radio set, the real identity is used, and a temporary identifier is then issued. • From then on the temporary identifier is used. Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 27
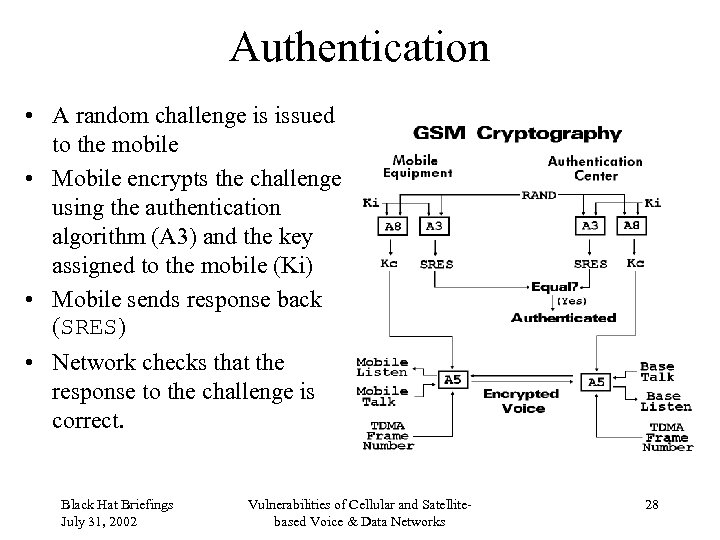
Authentication • A random challenge is issued to the mobile • Mobile encrypts the challenge using the authentication algorithm (A 3) and the key assigned to the mobile (Ki) • Mobile sends response back (SRES) • Network checks that the response to the challenge is correct. Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 28
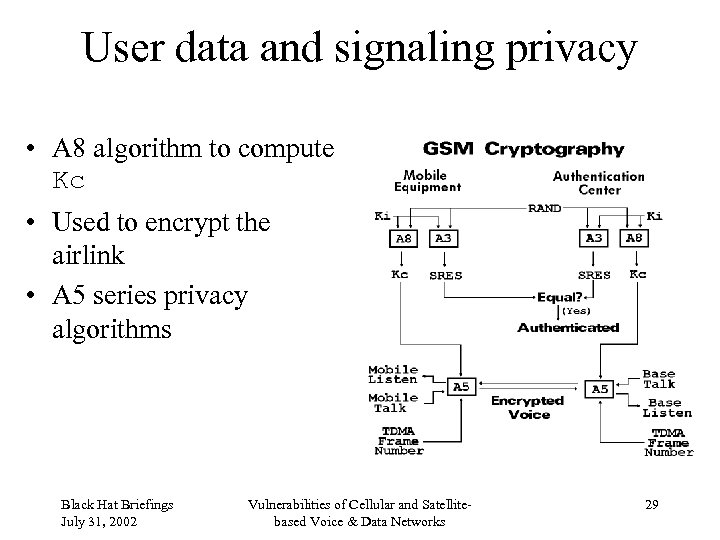
User data and signaling privacy • A 8 algorithm to compute Kc • Used to encrypt the airlink • A 5 series privacy algorithms Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 29
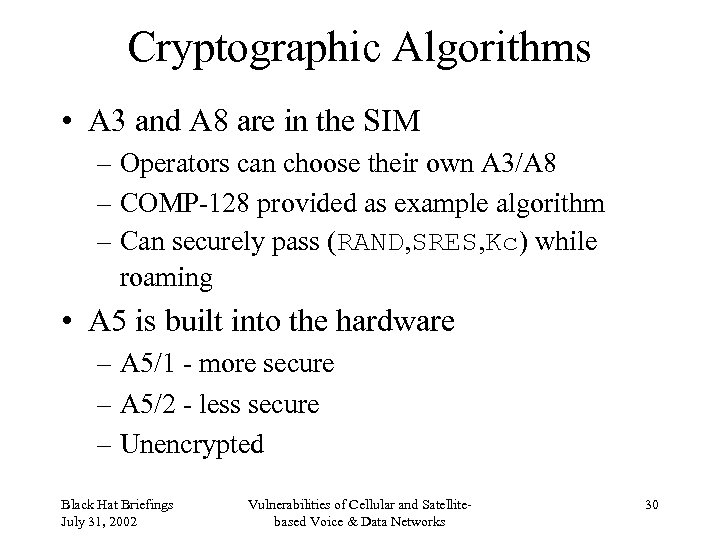
Cryptographic Algorithms • A 3 and A 8 are in the SIM – Operators can choose their own A 3/A 8 – COMP-128 provided as example algorithm – Can securely pass (RAND, SRES, Kc) while roaming • A 5 is built into the hardware – A 5/1 - more secure – A 5/2 - less secure – Unencrypted Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 30
GSM weaknesses • COMP-128 leaks Ki (April 1998) • A 8 has effective security of 54 bits – (last 10 bits set to 0) • A 5 – – 64 -bit key (Kc) and 22 -bit frame number, three shift registers A 5/1 (western Europe) A 5/2 (used in North America) A 5/0 (no encryption) • Rogue base station • Unencrypted network links – Eavesdropping – Query HLR/Au. C for new triples • Kc refreshed only occasionally Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 31
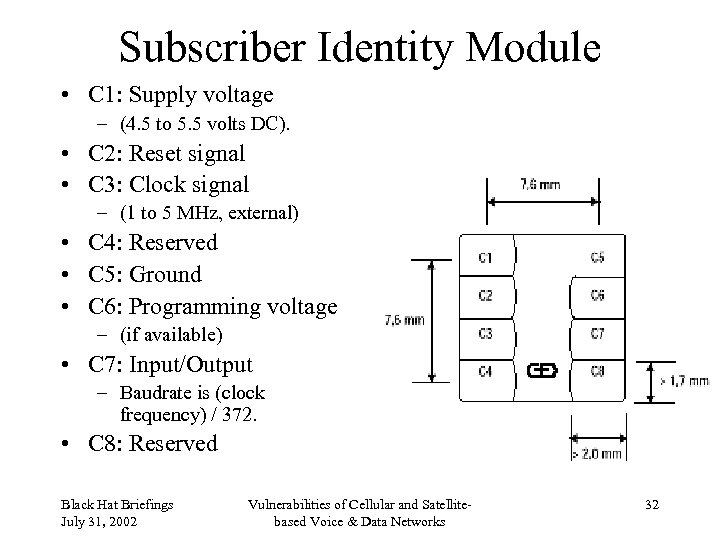
Subscriber Identity Module • C 1: Supply voltage – (4. 5 to 5. 5 volts DC). • C 2: Reset signal • C 3: Clock signal – (1 to 5 MHz, external) • C 4: Reserved • C 5: Ground • C 6: Programming voltage – (if available) • C 7: Input/Output – Baudrate is (clock frequency) / 372. • C 8: Reserved Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 32
Talking to a SIM • Defined by ETSI document GSM 11. 11 • Five bytes: – Class of instruction (CLA) • (always 0 x. A 0 for GSM) – – Instruction Code (INS) Parameter 1 (P 1) Parameter 2 (P 2) Parameter 3 (P 3) • (length of optional data segment) • SIM card readers may require additional bytes Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 33

Listening to a SIM • Three fields: – Data • (variable length) – Status Word 1 (SW 1) – Status Word 2 (SW 2) • 90 00 is normal response Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 34
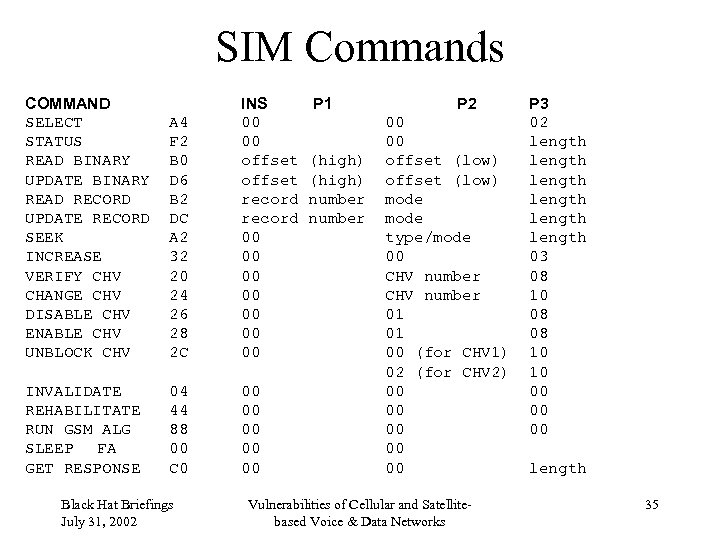
SIM Commands COMMAND SELECT STATUS READ BINARY UPDATE BINARY READ RECORD UPDATE RECORD SEEK INCREASE VERIFY CHV CHANGE CHV DISABLE CHV ENABLE CHV UNBLOCK CHV A 4 F 2 B 0 D 6 B 2 DC A 2 32 20 24 26 28 2 C INS 00 00 offset record 00 00 INVALIDATE REHABILITATE RUN GSM ALG SLEEP FA GET RESPONSE 04 44 88 00 C 0 00 00 00 Black Hat Briefings July 31, 2002 P 1 (high) number P 2 00 00 offset (low) mode type/mode 00 CHV number 01 01 00 (for CHV 1) 02 (for CHV 2) 00 00 00 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks P 3 02 length length 03 08 10 08 08 10 10 00 00 00 length 35
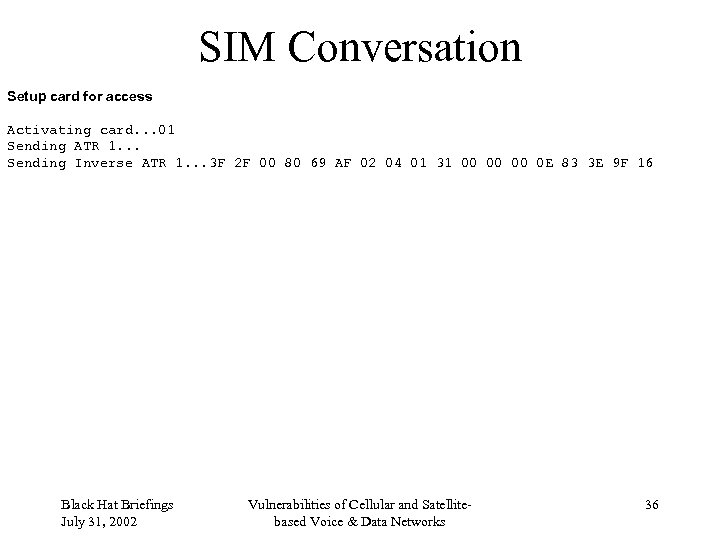
SIM Conversation Setup card for access Activating card. . . 01 Sending ATR 1. . . Sending Inverse ATR 1. . . 3 F 2 F 00 80 69 AF 02 04 01 31 00 00 00 0 E 83 3 E 9 F 16 Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 36
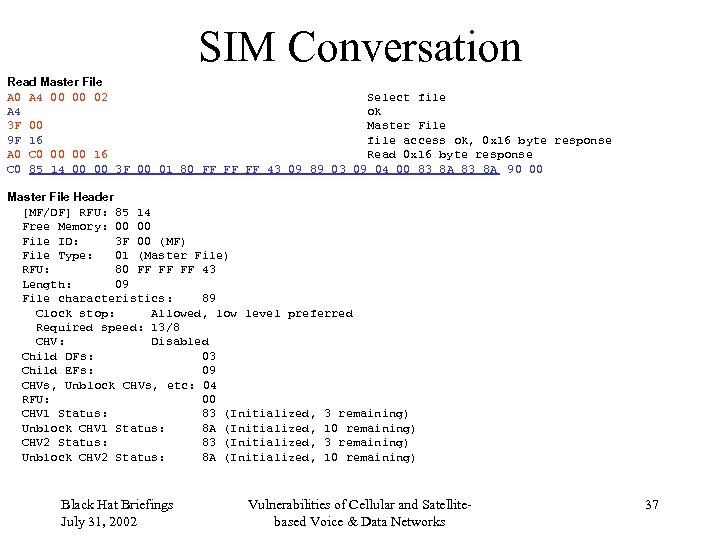
SIM Conversation Read Master File A 0 A 4 00 00 02 Select file A 4 ok 3 F 00 Master File 9 F 16 file access ok, 0 x 16 byte response A 0 C 0 00 00 16 Read 0 x 16 byte response C 0 85 14 00 00 3 F 00 01 80 FF FF FF 43 09 89 03 09 04 00 83 8 A 90 00 Master File Header [MF/DF] RFU: 85 14 Free Memory: 00 00 File ID: 3 F 00 (MF) File Type: 01 (Master File) RFU: 80 FF FF FF 43 Length: 09 File characteristics: 89 Clock stop: Allowed, low level preferred Required speed: 13/8 CHV: Disabled Child DFs: 03 Child EFs: 09 CHVs, Unblock CHVs, etc: 04 RFU: 00 CHV 1 Status: 83 (Initialized, 3 remaining) Unblock CHV 1 Status: 8 A (Initialized, 10 remaining) CHV 2 Status: 83 (Initialized, 3 remaining) Unblock CHV 2 Status: 8 A (Initialized, 10 remaining) Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 37
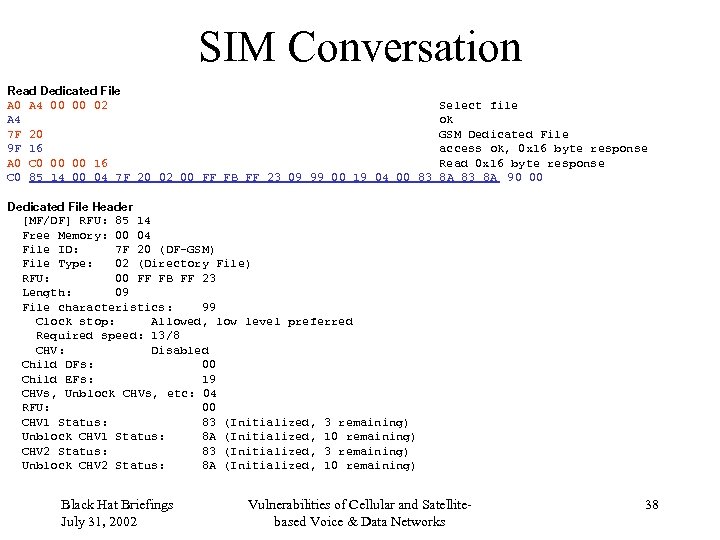
SIM Conversation Read Dedicated File A 0 A 4 00 00 02 A 4 7 F 20 9 F 16 A 0 C 0 00 00 16 C 0 85 14 00 04 7 F 20 02 00 FF FB FF 23 09 99 00 19 04 00 83 Select file ok GSM Dedicated File access ok, 0 x 16 byte response Read 0 x 16 byte response 8 A 83 8 A 90 00 Dedicated File Header [MF/DF] RFU: 85 14 Free Memory: 00 04 File ID: 7 F 20 (DF-GSM) File Type: 02 (Directory File) RFU: 00 FF FB FF 23 Length: 09 File characteristics: 99 Clock stop: Allowed, low level preferred Required speed: 13/8 CHV: Disabled Child DFs: 00 Child EFs: 19 CHVs, Unblock CHVs, etc: 04 RFU: 00 CHV 1 Status: 83 (Initialized, 3 remaining) Unblock CHV 1 Status: 8 A (Initialized, 10 remaining) CHV 2 Status: 83 (Initialized, 3 remaining) Unblock CHV 2 Status: 8 A (Initialized, 10 remaining) Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 38
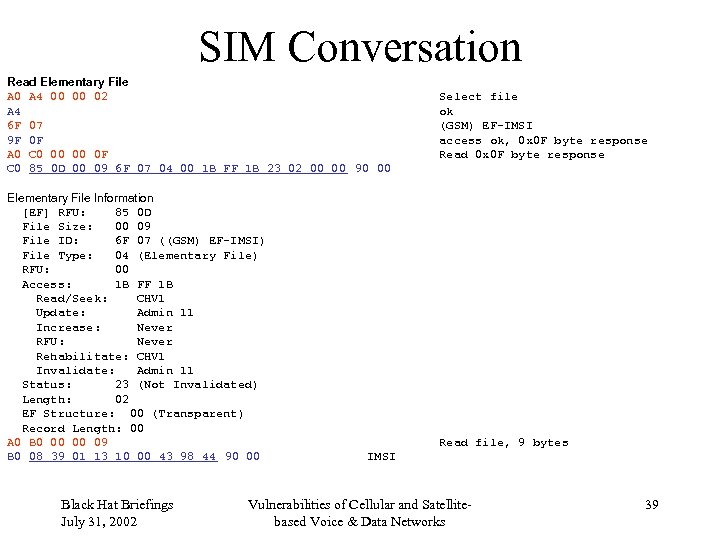
SIM Conversation Read Elementary File A 0 A 4 00 00 02 A 4 6 F 07 9 F 0 F A 0 C 0 00 00 0 F C 0 85 0 D 00 09 6 F 07 04 00 1 B FF 1 B 23 02 00 00 90 00 Elementary File Information [EF] RFU: 85 0 D File Size: 00 09 File ID: 6 F 07 ((GSM) EF-IMSI) File Type: 04 (Elementary File) RFU: 00 Access: 1 B FF 1 B Read/Seek: CHV 1 Update: Admin 11 Increase: Never RFU: Never Rehabilitate: CHV 1 Invalidate: Admin 11 Status: 23 (Not Invalidated) Length: 02 EF Structure: 00 (Transparent) Record Length: 00 A 0 B 0 00 00 09 B 0 08 39 01 13 10 00 43 98 44 90 00 Black Hat Briefings July 31, 2002 Select file ok (GSM) EF-IMSI access ok, 0 x 0 F byte response Read file, 9 bytes IMSI Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 39
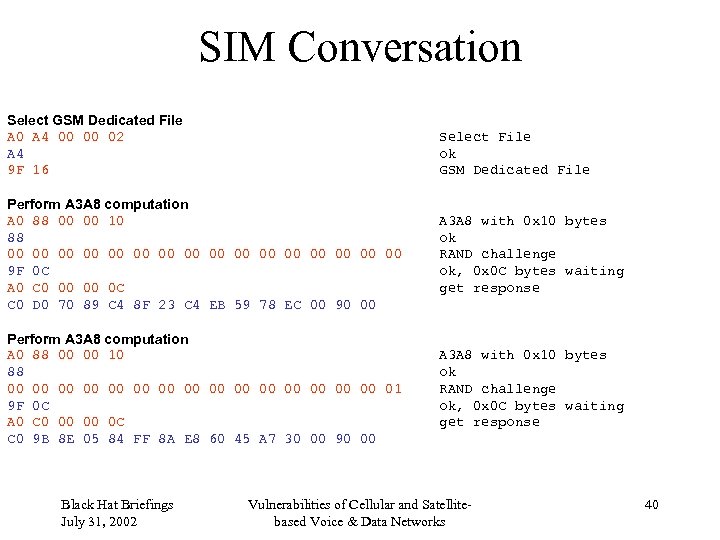
SIM Conversation Select GSM Dedicated File A 0 A 4 00 00 02 A 4 9 F 16 Select File ok GSM Dedicated File Perform A 3 A 8 computation A 0 88 00 00 10 88 00 00 00 00 9 F 0 C A 0 C 0 00 00 0 C C 0 D 0 70 89 C 4 8 F 23 C 4 EB 59 78 EC 00 90 00 A 3 A 8 with 0 x 10 bytes ok RAND challenge ok, 0 x 0 C bytes waiting get response Perform A 3 A 8 computation A 0 88 00 00 10 88 00 00 00 00 01 9 F 0 C A 0 C 0 00 00 0 C C 0 9 B 8 E 05 84 FF 8 A E 8 60 45 A 7 30 00 90 00 A 3 A 8 with 0 x 10 bytes ok RAND challenge ok, 0 x 0 C bytes waiting get response Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 40
SIM attacks • Repeated authenticate, leaks Ki – (New SIMs have a limit (about 50 k) on the number of times the authentication algorithm can be run) • Side-channel attacks – Power consumption – Timing – Electromagnetic emanations Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 41

COMP-128 Updates • COMP 128 -2 – 54 -bit Kc – Secret algorithm • COMP 128 -3 – 64 -bit Kc – Secret algorithm • Proposal for new A 3 A 8 based on MILENAGE – Milenage based on Rijndael (AES) – Algorithm will be public • New A 3 A 8 requires – Au. C software upgrade – New SIMs Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 42
A 5/3 • Based on the Kasumi algorithm – 3 GPP confidentiality and integrity algorithms. • Kasumi derived from the MISTY algorithm, created by Mitsubishi. • Specifications are publicly available on the 3 GPP web site (www. 3 gpp. org). Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 43
Cellular Jamming • Low-power private base station transmits a forward link overhead message • Mobiles register with base station • Base station never sends a page • The FCC view on this: • • The Communications Act of 1934, as amended, and the Commission's rules do not permit the use of transmitters designed to prevent or jam the operation of wireless devices in hospitals, theaters and other locations. Section 302(a) of the Communications Act, 47 USC 302(a), prohibits the manufacture, importation, sale, offer for sale, or use of devices that fail to comply with the regulations promulgated pursuant to this section. Based on the above, the operation of transmitters designed to jam wireless communications is a violation of 47 USC 301, 302(a), and 333. The manufacture, importation, sale or offer for sale, including advertising, of such transmitters is a violation of 47 USC 302(a). Parties in violations of these provisions may be subject to the penalties contained within 47 USC 501 -510. Fines for a first offense can range as high as $11, 000 for each violation or imprisonment for up to one year. The equipment can also be seized and forfeited to the U. S. Government. These regulations apply to all transmitters that are designed to cause interference to, or prevent the operation of, other radio communication systems. Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 44

Satellite Networks • Big LEOs • Little LEOs • Mobile Satellite Ventures • INTELSAT • INMARSAT • VSAT • GPS Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 45
Big LEO • Constellation of satellites in Low Earth Orbit (as opposed to geosynchronous) • Base stations in the sky • Linked to network of ground stations • Voice as primary service • 1610 to 1626. 5 MHz up • 2483. 5 to 2500 MHz down Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 46
Iridium • $5 billion • 66 satellites (plus spares) • TDMA, processing onboard • 1621. 35 to 1626. 5 up and down • 2. 4 kbps data service • Service start November 1998 • Bankruptcy in August 1999, only 55, 000 customers Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 47

Iridium Satellite LLC • • • Paid $25 M for Iridium assets Relaunched commercial service in 2001 Large government contract ($72 M/2 years via DISA) Dedicated gateway earth station in Hawaii Defense Information Systems Agency – Department of Defense – Department of State – Inter-satellite links • Enough money to replenish satellites? Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 48

Globalstar • Loral, Qualcomm • 48 satellites in LEO • Start of operations February 2000 • Currently under bankruptcy protection • Bent-pipe • CDMA service • Underpowered satellites – Recharge over oceans • 9. 6 kbps data Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 49

ICO • $4. 7 billion • Hughes-built satellites • 10 satellites in Medium Earth Orbit (MEO) • GSM-based • New ICO • Craig Mc. Caw • Merged with Teledesic Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 50

Orbcomm (Little LEO) • • • 28 satellites 14 earth stations VHF operation Data only Store and Forward if ground station not in view • “Global. Grams” = X. 400 e -mail • Latency Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 51
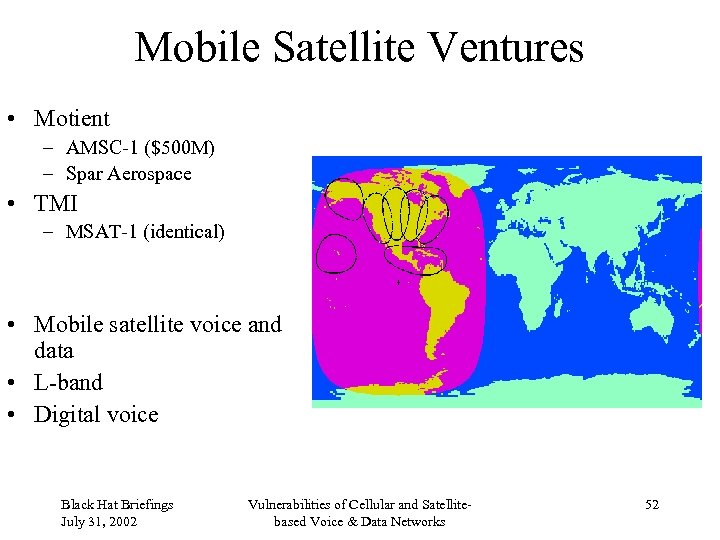
Mobile Satellite Ventures • Motient – AMSC-1 ($500 M) – Spar Aerospace • TMI – MSAT-1 (identical) • Mobile satellite voice and data • L-band • Digital voice Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 52

Interception • Gateways require tapping – FBI, CALEA requirements – Iridium agreement – Globalstar agreement – TMI on-demand access – National intelligence and police forces • Test equipment • Limited use of encryption • Modifiable phone equipment Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 53

INTELSAT • • • Was a consortium of nations as signatories Now privatized Large fleet in geostationary orbit Primarily telephone and television traffic Carries unencrypted voice, data and fax Used by US Do. D for UAV datalink Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 54

INMARSAT • International Maritime Satellite Organization • AOR, POR, IOR coverage • L-band Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 55
Global Positioning System • 24 satellites • Selective Availability turned off May 2000 • 30 meter accuracy • Can be jammed (denial of service) • Can be spoofed Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 56
GPS Frequencies L 1: 1575. 42 MHz: Coarse Acquisition (C/A) code L 2: 1227. 60 MHz: Precise (P) or Y (encrypted) code L 3: 1381. 05 MHz: Nuclear burst detectors L 4: 1841. 40 MHz: Ionospheric correction (under study) L 5: 1176. 45 MHz: Civilian safety-of-life signal (proposed) Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 57

GPS Enhancements The new architecture also requires new user equipment and an upgraded ground control segment, as well as M-Code. All of those elements should be in place by 2008, when 18 satellites with MCode - 12 IIRs and 6 IIFs - will be up. Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 58

GLONASS • Global Orbital Navigation Satellite System • 1606 to 1616 MHz • Full operational status achieved once Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 59

Satellite Failures • Pan. Am. Sat Galaxy 4 – Attitude control and backup failed – Major supplier of service to paging towers • AT&T Telstar 401 – launched 1993, failed 11 January 1997 – abrupt failure, solar activity? (large solar flare 6 January 1997) • Galaxy 7 – Primary control processor failed June 1998. Secondary processor failed November 2000. – Suspected electrical shorts in spacecraft control processor (SCP). • Solidaridad 1 – Primary SCP failed May 1999. Secondary SCP failed August 2000. • Anik E 1 – 1996, Power Subsystem Failure, Partial Loss • Echo. Star 4 – 1998, Solar Array Failed to Deploy, reduced electrical power available Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 60

Questions? Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 61
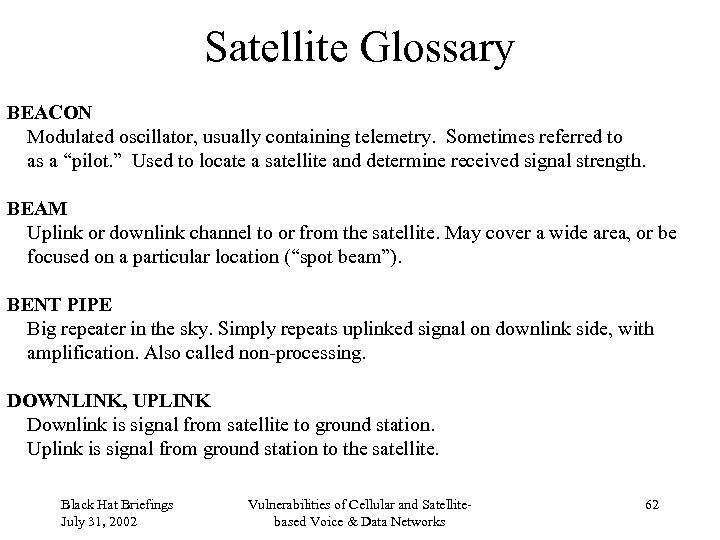
Satellite Glossary BEACON Modulated oscillator, usually containing telemetry. Sometimes referred to as a “pilot. ” Used to locate a satellite and determine received signal strength. BEAM Uplink or downlink channel to or from the satellite. May cover a wide area, or be focused on a particular location (“spot beam”). BENT PIPE Big repeater in the sky. Simply repeats uplinked signal on downlink side, with amplification. Also called non-processing. DOWNLINK, UPLINK Downlink is signal from satellite to ground station. Uplink is signal from ground station to the satellite. Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 62
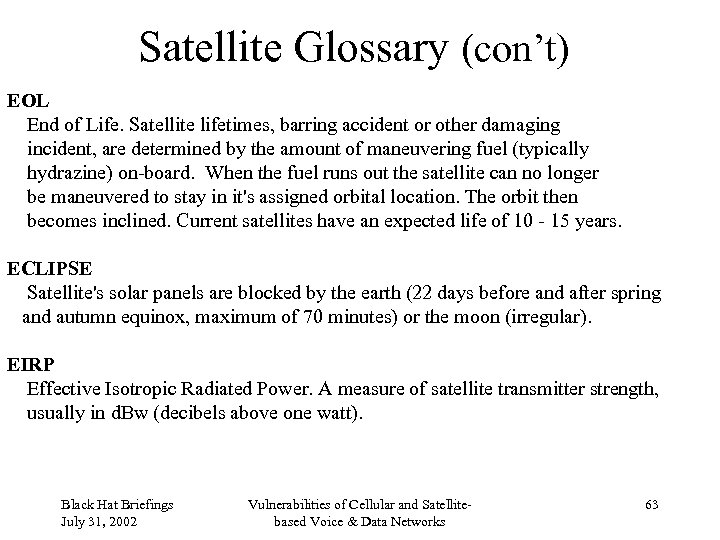
Satellite Glossary (con’t) EOL End of Life. Satellite lifetimes, barring accident or other damaging incident, are determined by the amount of maneuvering fuel (typically hydrazine) on-board. When the fuel runs out the satellite can no longer be maneuvered to stay in it's assigned orbital location. The orbit then becomes inclined. Current satellites have an expected life of 10 - 15 years. ECLIPSE Satellite's solar panels are blocked by the earth (22 days before and after spring and autumn equinox, maximum of 70 minutes) or the moon (irregular). EIRP Effective Isotropic Radiated Power. A measure of satellite transmitter strength, usually in d. Bw (decibels above one watt). Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 63
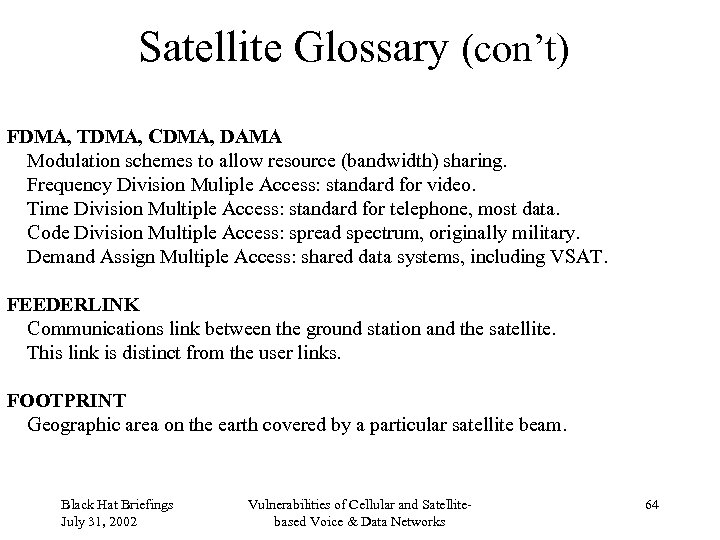
Satellite Glossary (con’t) FDMA, TDMA, CDMA, DAMA Modulation schemes to allow resource (bandwidth) sharing. Frequency Division Muliple Access: standard for video. Time Division Multiple Access: standard for telephone, most data. Code Division Multiple Access: spread spectrum, originally military. Demand Assign Multiple Access: shared data systems, including VSAT. FEEDERLINK Communications link between the ground station and the satellite. This link is distinct from the user links. FOOTPRINT Geographic area on the earth covered by a particular satellite beam. Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 64
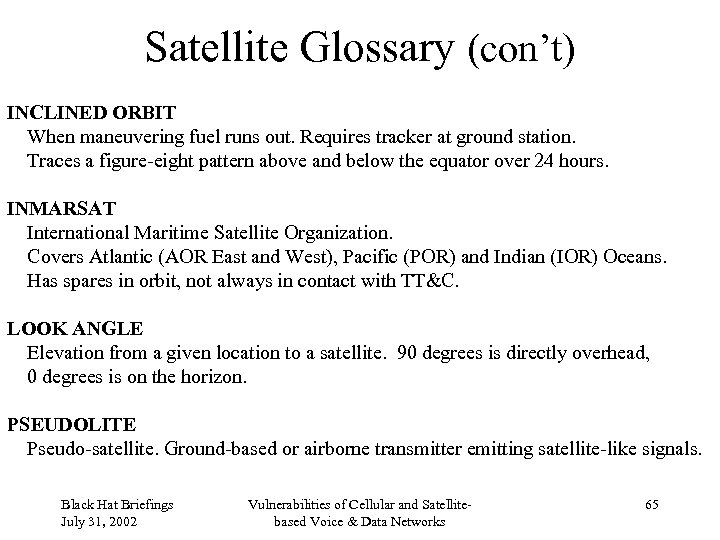
Satellite Glossary (con’t) INCLINED ORBIT When maneuvering fuel runs out. Requires tracker at ground station. Traces a figure-eight pattern above and below the equator over 24 hours. INMARSAT International Maritime Satellite Organization. Covers Atlantic (AOR East and West), Pacific (POR) and Indian (IOR) Oceans. Has spares in orbit, not always in contact with TT&C. LOOK ANGLE Elevation from a given location to a satellite. 90 degrees is directly overhead, 0 degrees is on the horizon. PSEUDOLITE Pseudo-satellite. Ground-based or airborne transmitter emitting satellite-like signals. Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 65
Satellite Glossary (con’t) TRANSPONDER Discrete frequency slot assigned to an uplink/downlink. TT&C Telemetry, Tracking and Command. Ground Station monitoring and controlling satellite operation. TWT Traveling-Wave Tube amplifier. Has nearly flat response across a wide bandwidth. Newer satellites are using solid state amplifiers. VSAT Very Small Aperture Terminal. Usually dedicated data links in a star configuration. Popular with gas stations for credit card verification; car dealers for sales information. Black Hat Briefings July 31, 2002 Vulnerabilities of Cellular and Satellitebased Voice & Data Networks 66
aac45fb695f537324c316f59bd091904.ppt