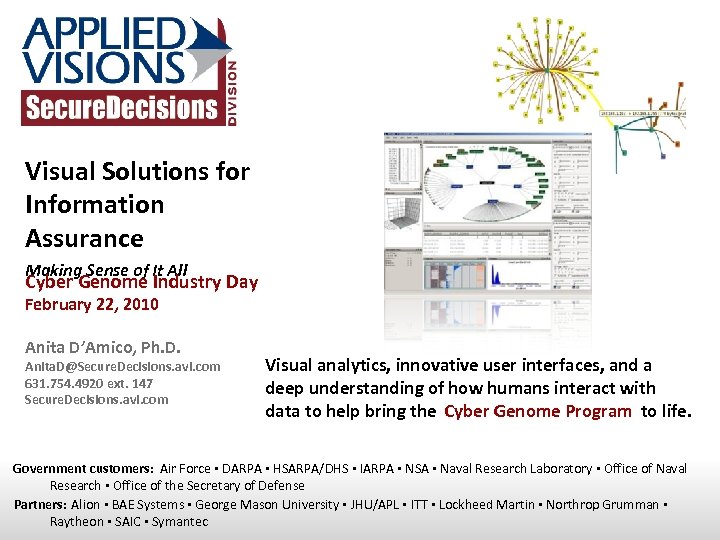
 Visual Solutions for Information Assurance Making Sense of It All Cyber Genome Industry Day February 22, 2010 Anita D’Amico, Ph. D. Anita. D@Secure. Decisions. avi. com 631. 754. 4920 ext. 147 Secure. Decisions. avi. com Visual analytics, innovative user interfaces, and a deep understanding of how humans interact with data to help bring the Cyber Genome Program to life. Government customers: Air Force ▪ DARPA ▪ HSARPA/DHS ▪ IARPA ▪ NSA ▪ Naval Research Laboratory ▪ Office of Naval Research ▪ Office of the Secretary of Defense Partners: Alion ▪ BAE Systems ▪ George Mason University ▪ JHU/APL ▪ ITT ▪ Lockheed Martin ▪ Northrop Grumman ▪ Raytheon ▪ SAIC ▪ Symantec
Visual Solutions for Information Assurance Making Sense of It All Cyber Genome Industry Day February 22, 2010 Anita D’Amico, Ph. D. Anita. D@Secure. Decisions. avi. com 631. 754. 4920 ext. 147 Secure. Decisions. avi. com Visual analytics, innovative user interfaces, and a deep understanding of how humans interact with data to help bring the Cyber Genome Program to life. Government customers: Air Force ▪ DARPA ▪ HSARPA/DHS ▪ IARPA ▪ NSA ▪ Naval Research Laboratory ▪ Office of Naval Research ▪ Office of the Secretary of Defense Partners: Alion ▪ BAE Systems ▪ George Mason University ▪ JHU/APL ▪ ITT ▪ Lockheed Martin ▪ Northrop Grumman ▪ Raytheon ▪ SAIC ▪ Symantec
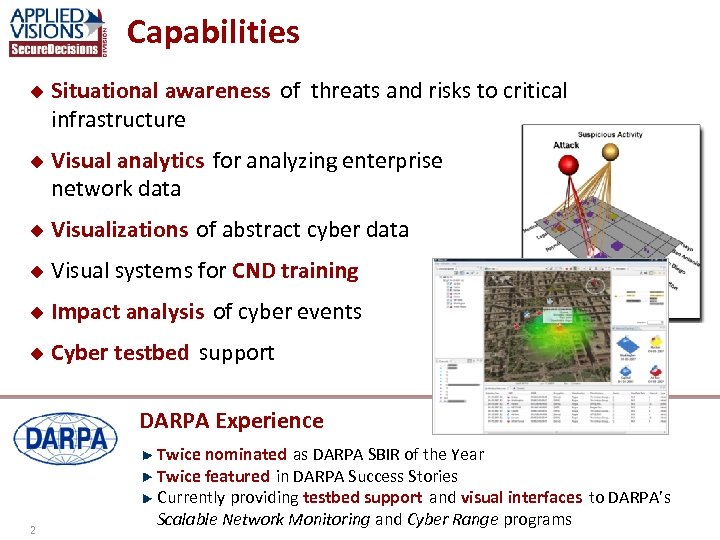 Capabilities u u Situational awareness of threats and risks to critical infrastructure Visual analytics for analyzing enterprise network data u Visualizations of abstract cyber data u Visual systems for CND training u Impact analysis of cyber events u Cyber testbed support DARPA Experience 2 Twice nominated as DARPA SBIR of the Year Twice featured in DARPA Success Stories Currently providing testbed support and visual interfaces to DARPA’s Scalable Network Monitoring and Cyber Range programs
Capabilities u u Situational awareness of threats and risks to critical infrastructure Visual analytics for analyzing enterprise network data u Visualizations of abstract cyber data u Visual systems for CND training u Impact analysis of cyber events u Cyber testbed support DARPA Experience 2 Twice nominated as DARPA SBIR of the Year Twice featured in DARPA Success Stories Currently providing testbed support and visual interfaces to DARPA’s Scalable Network Monitoring and Cyber Range programs
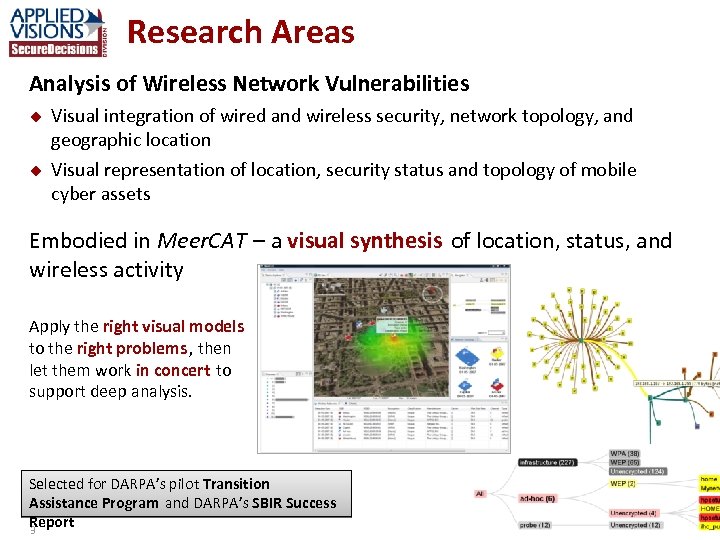 Research Areas Analysis of Wireless Network Vulnerabilities u u Visual integration of wired and wireless security, network topology, and geographic location Visual representation of location, security status and topology of mobile cyber assets Embodied in Meer. CAT – a visual synthesis of location, status, and wireless activity Apply the right visual models to the right problems , then let them work in concert to support deep analysis. Selected for DARPA’s pilot Transition Assistance Program and DARPA’s SBIR Success Report 3
Research Areas Analysis of Wireless Network Vulnerabilities u u Visual integration of wired and wireless security, network topology, and geographic location Visual representation of location, security status and topology of mobile cyber assets Embodied in Meer. CAT – a visual synthesis of location, status, and wireless activity Apply the right visual models to the right problems , then let them work in concert to support deep analysis. Selected for DARPA’s pilot Transition Assistance Program and DARPA’s SBIR Success Report 3
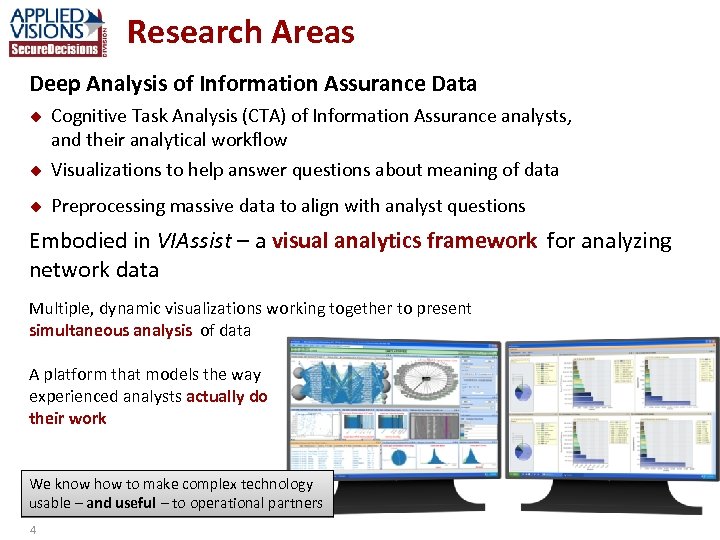 Research Areas Deep Analysis of Information Assurance Data u Cognitive Task Analysis (CTA) of Information Assurance analysts, and their analytical workflow Visualizations to help answer questions about meaning of data u Preprocessing massive data to align with analyst questions u Embodied in VIAssist – a visual analytics framework for analyzing network data Multiple, dynamic visualizations working together to present simultaneous analysis of data A platform that models the way experienced analysts actually do their work We know how to make complex technology usable – and useful – to operational partners 4
Research Areas Deep Analysis of Information Assurance Data u Cognitive Task Analysis (CTA) of Information Assurance analysts, and their analytical workflow Visualizations to help answer questions about meaning of data u Preprocessing massive data to align with analyst questions u Embodied in VIAssist – a visual analytics framework for analyzing network data Multiple, dynamic visualizations working together to present simultaneous analysis of data A platform that models the way experienced analysts actually do their work We know how to make complex technology usable – and useful – to operational partners 4
 Research Areas Visualizing Software Vulnerability u u u Swa. Viz: visual tools for analyzing software vulnerabilities TVA: visualization of cyber attack paths i. TVO: dynamic & static s/w visualization Automated analysis of software components, with visual representations of their structure, execution, and internal vulnerabilities CND Training, Impact Analysis, and Testbed Support Camus: maps Cyber Assets to Missions and Users to assess impact u SNM Command Control: Control execution and monitoring of high-speed tests of new network monitoring algorithms u Sim. BLEND: trains IA analysis through computer based training, network simulation, and a Learning Management System with a unique gaming interface u 5
Research Areas Visualizing Software Vulnerability u u u Swa. Viz: visual tools for analyzing software vulnerabilities TVA: visualization of cyber attack paths i. TVO: dynamic & static s/w visualization Automated analysis of software components, with visual representations of their structure, execution, and internal vulnerabilities CND Training, Impact Analysis, and Testbed Support Camus: maps Cyber Assets to Missions and Users to assess impact u SNM Command Control: Control execution and monitoring of high-speed tests of new network monitoring algorithms u Sim. BLEND: trains IA analysis through computer based training, network simulation, and a Learning Management System with a unique gaming interface u 5