f15e401230ba357d02a804a16132f90b.ppt
- Количество слайдов: 22
 Virtual Private Networks (VPN) Generic Routing Encapsulation (GRE) n. TLS (SSL-VPN) n CN 8814: Network Security 1
Virtual Private Networks (VPN) Generic Routing Encapsulation (GRE) n. TLS (SSL-VPN) n CN 8814: Network Security 1
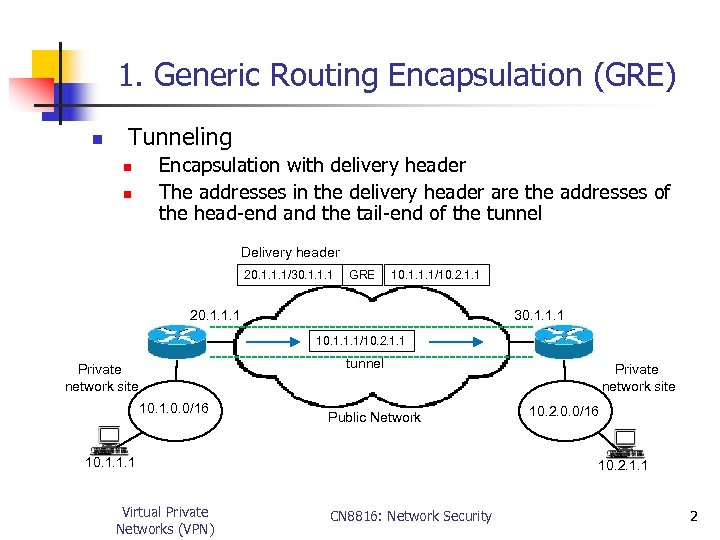 1. Generic Routing Encapsulation (GRE) n Tunneling n n Encapsulation with delivery header The addresses in the delivery header are the addresses of the head-end and the tail-end of the tunnel Delivery header 20. 1. 1. 1/30. 1. 1. 1 GRE 10. 1. 1. 1/10. 2. 1. 1 20. 1. 1. 1 30. 1. 1. 1 10. 1. 1. 1/10. 2. 1. 1 tunnel Private network site 10. 1. 0. 0/16 Public Network 10. 1. 1. 1 Virtual Private Networks (VPN) Private network site 10. 2. 0. 0/16 10. 2. 1. 1 CN 8816: Network Security 2
1. Generic Routing Encapsulation (GRE) n Tunneling n n Encapsulation with delivery header The addresses in the delivery header are the addresses of the head-end and the tail-end of the tunnel Delivery header 20. 1. 1. 1/30. 1. 1. 1 GRE 10. 1. 1. 1/10. 2. 1. 1 20. 1. 1. 1 30. 1. 1. 1 10. 1. 1. 1/10. 2. 1. 1 tunnel Private network site 10. 1. 0. 0/16 Public Network 10. 1. 1. 1 Virtual Private Networks (VPN) Private network site 10. 2. 0. 0/16 10. 2. 1. 1 CN 8816: Network Security 2
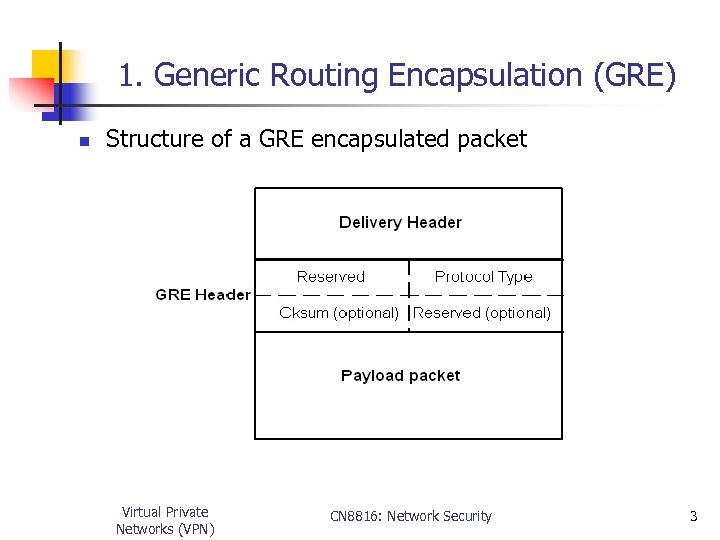 1. Generic Routing Encapsulation (GRE) n Structure of a GRE encapsulated packet Virtual Private Networks (VPN) CN 8816: Network Security 3
1. Generic Routing Encapsulation (GRE) n Structure of a GRE encapsulated packet Virtual Private Networks (VPN) CN 8816: Network Security 3
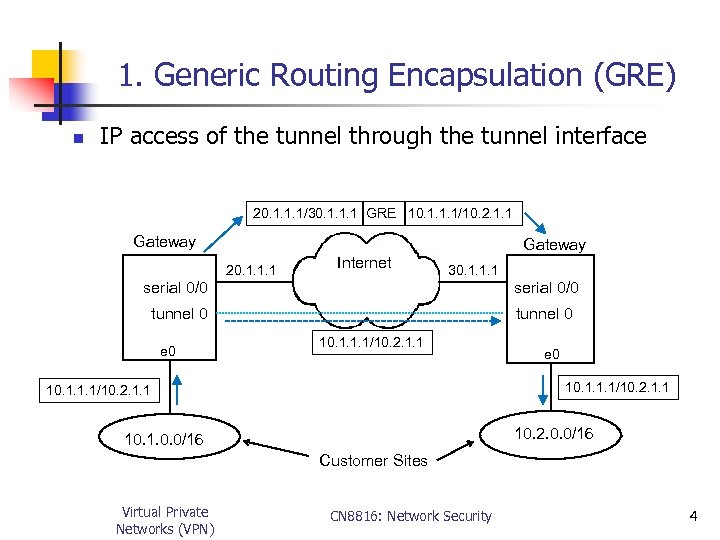 1. Generic Routing Encapsulation (GRE) n IP access of the tunnel through the tunnel interface 20. 1. 1. 1/30. 1. 1. 1 GRE 10. 1. 1. 1/10. 2. 1. 1 Gateway 20. 1. 1. 1 Internet 30. 1. 1. 1 serial 0/0 tunnel 0 e 0 10. 1. 1. 1/10. 2. 1. 1 10. 2. 0. 0/16 10. 1. 0. 0/16 Customer Sites Virtual Private Networks (VPN) CN 8816: Network Security 4
1. Generic Routing Encapsulation (GRE) n IP access of the tunnel through the tunnel interface 20. 1. 1. 1/30. 1. 1. 1 GRE 10. 1. 1. 1/10. 2. 1. 1 Gateway 20. 1. 1. 1 Internet 30. 1. 1. 1 serial 0/0 tunnel 0 e 0 10. 1. 1. 1/10. 2. 1. 1 10. 2. 0. 0/16 10. 1. 0. 0/16 Customer Sites Virtual Private Networks (VPN) CN 8816: Network Security 4
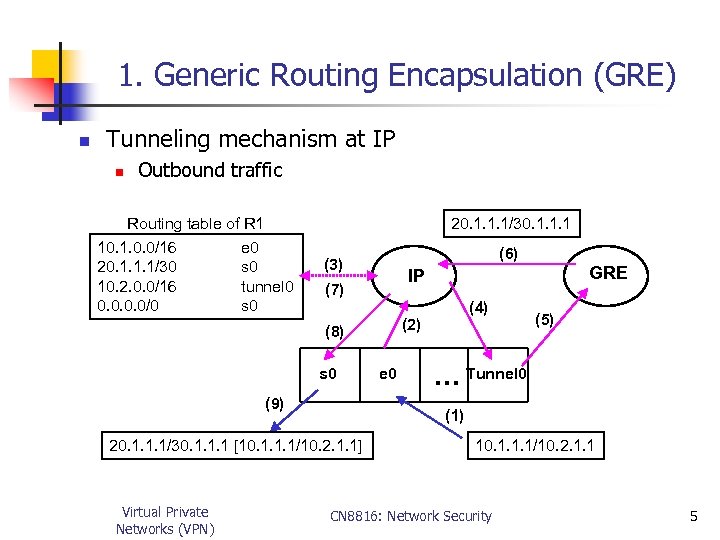 1. Generic Routing Encapsulation (GRE) n Tunneling mechanism at IP n Outbound traffic Routing table of R 1 10. 1. 0. 0/16 e 0 20. 1. 1. 1/30 s 0 10. 2. 0. 0/16 tunnel 0 0. 0/0 s 0 20. 1. 1. 1/30. 1. 1. 1 (6) (3) (7) (9) e 0 (5) … Tunnel 0 (1) 20. 1. 1. 1/30. 1. 1. 1 [10. 1. 1. 1/10. 2. 1. 1] Virtual Private Networks (VPN) (4) (2) (8) s 0 GRE IP 10. 1. 1. 1/10. 2. 1. 1 CN 8816: Network Security 5
1. Generic Routing Encapsulation (GRE) n Tunneling mechanism at IP n Outbound traffic Routing table of R 1 10. 1. 0. 0/16 e 0 20. 1. 1. 1/30 s 0 10. 2. 0. 0/16 tunnel 0 0. 0/0 s 0 20. 1. 1. 1/30. 1. 1. 1 (6) (3) (7) (9) e 0 (5) … Tunnel 0 (1) 20. 1. 1. 1/30. 1. 1. 1 [10. 1. 1. 1/10. 2. 1. 1] Virtual Private Networks (VPN) (4) (2) (8) s 0 GRE IP 10. 1. 1. 1/10. 2. 1. 1 CN 8816: Network Security 5
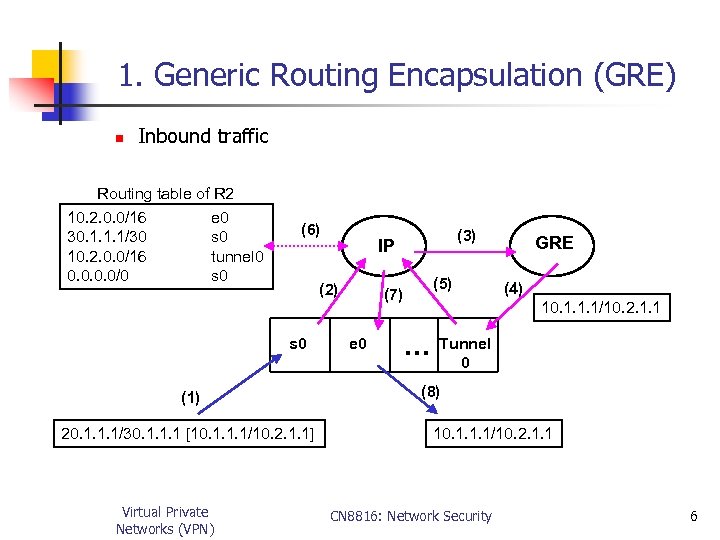 1. Generic Routing Encapsulation (GRE) n Inbound traffic Routing table of R 2 10. 2. 0. 0/16 e 0 30. 1. 1. 1/30 s 0 10. 2. 0. 0/16 tunnel 0 0. 0/0 s 0 (6) (2) s 0 (1) 20. 1. 1. 1/30. 1. 1. 1 [10. 1. 1. 1/10. 2. 1. 1] Virtual Private Networks (VPN) (3) IP (7) e 0 (5) GRE (4) 10. 1. 1. 1/10. 2. 1. 1 … Tunnel 0 (8) 10. 1. 1. 1/10. 2. 1. 1 CN 8816: Network Security 6
1. Generic Routing Encapsulation (GRE) n Inbound traffic Routing table of R 2 10. 2. 0. 0/16 e 0 30. 1. 1. 1/30 s 0 10. 2. 0. 0/16 tunnel 0 0. 0/0 s 0 (6) (2) s 0 (1) 20. 1. 1. 1/30. 1. 1. 1 [10. 1. 1. 1/10. 2. 1. 1] Virtual Private Networks (VPN) (3) IP (7) e 0 (5) GRE (4) 10. 1. 1. 1/10. 2. 1. 1 … Tunnel 0 (8) 10. 1. 1. 1/10. 2. 1. 1 CN 8816: Network Security 6
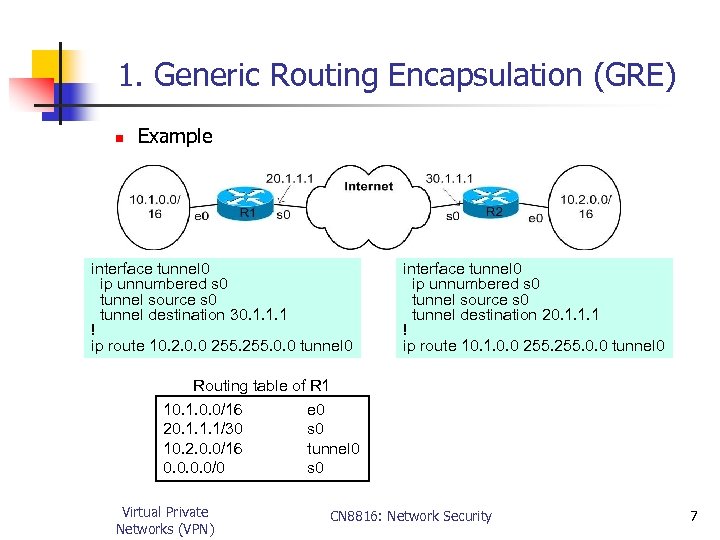 1. Generic Routing Encapsulation (GRE) n Example interface tunnel 0 ip unnumbered s 0 tunnel source s 0 tunnel destination 30. 1. 1. 1 ! ip route 10. 2. 0. 0 255. 0. 0 tunnel 0 interface tunnel 0 ip unnumbered s 0 tunnel source s 0 tunnel destination 20. 1. 1. 1 ! ip route 10. 1. 0. 0 255. 0. 0 tunnel 0 Routing table of R 1 10. 1. 0. 0/16 e 0 20. 1. 1. 1/30 s 0 10. 2. 0. 0/16 tunnel 0 0. 0/0 s 0 Virtual Private Networks (VPN) CN 8816: Network Security 7
1. Generic Routing Encapsulation (GRE) n Example interface tunnel 0 ip unnumbered s 0 tunnel source s 0 tunnel destination 30. 1. 1. 1 ! ip route 10. 2. 0. 0 255. 0. 0 tunnel 0 interface tunnel 0 ip unnumbered s 0 tunnel source s 0 tunnel destination 20. 1. 1. 1 ! ip route 10. 1. 0. 0 255. 0. 0 tunnel 0 Routing table of R 1 10. 1. 0. 0/16 e 0 20. 1. 1. 1/30 s 0 10. 2. 0. 0/16 tunnel 0 0. 0/0 s 0 Virtual Private Networks (VPN) CN 8816: Network Security 7
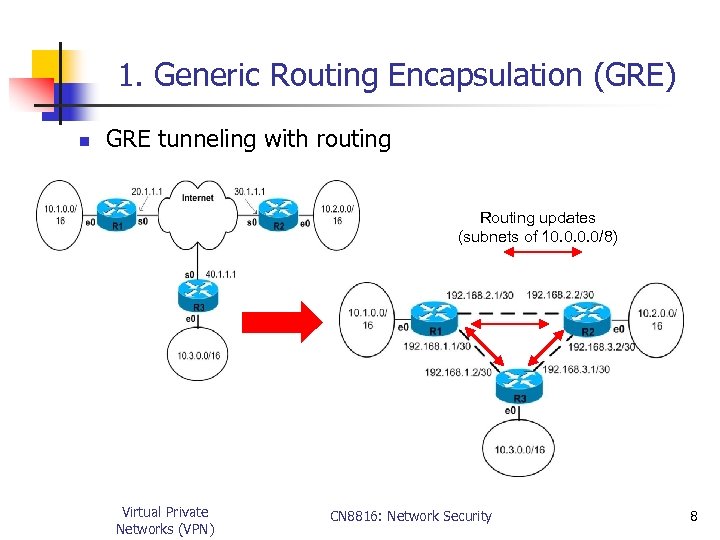 1. Generic Routing Encapsulation (GRE) n GRE tunneling with routing Routing updates (subnets of 10. 0/8) Virtual Private Networks (VPN) CN 8816: Network Security 8
1. Generic Routing Encapsulation (GRE) n GRE tunneling with routing Routing updates (subnets of 10. 0/8) Virtual Private Networks (VPN) CN 8816: Network Security 8
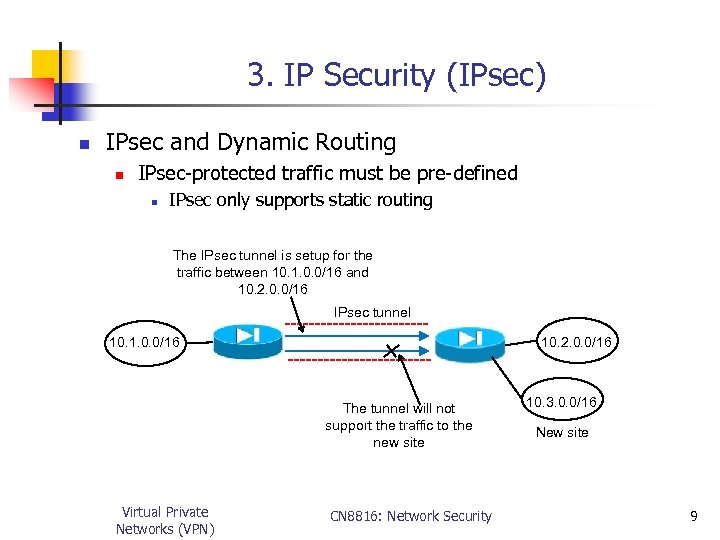 3. IP Security (IPsec) n IPsec and Dynamic Routing n IPsec-protected traffic must be pre-defined n IPsec only supports static routing The IPsec tunnel is setup for the traffic between 10. 1. 0. 0/16 and 10. 2. 0. 0/16 IPsec tunnel 10. 1. 0. 0/16 10. 2. 0. 0/16 The tunnel will not support the traffic to the new site Virtual Private Networks (VPN) CN 8816: Network Security 10. 3. 0. 0/16 New site 9
3. IP Security (IPsec) n IPsec and Dynamic Routing n IPsec-protected traffic must be pre-defined n IPsec only supports static routing The IPsec tunnel is setup for the traffic between 10. 1. 0. 0/16 and 10. 2. 0. 0/16 IPsec tunnel 10. 1. 0. 0/16 10. 2. 0. 0/16 The tunnel will not support the traffic to the new site Virtual Private Networks (VPN) CN 8816: Network Security 10. 3. 0. 0/16 New site 9
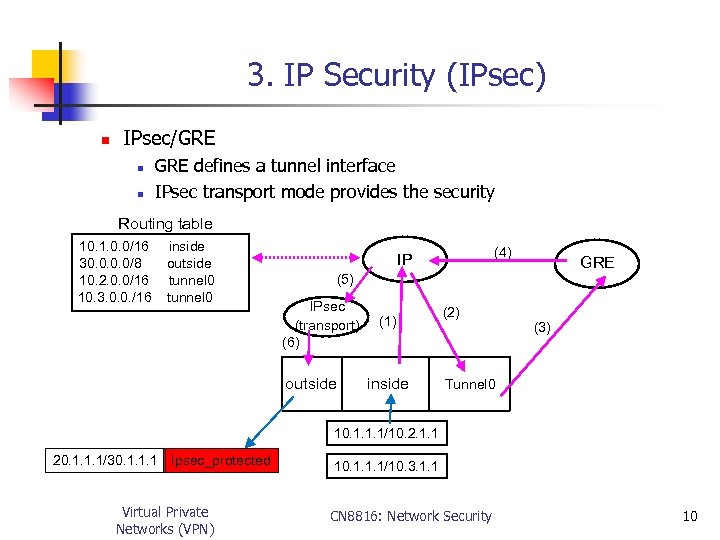 3. IP Security (IPsec) n IPsec/GRE n n GRE defines a tunnel interface IPsec transport mode provides the security Routing table 10. 1. 0. 0/16 30. 0/8 10. 2. 0. 0/16 10. 3. 0. 0. /16 inside outside tunnel 0 (4) IP GRE (5) IPsec (transport) (6) outside (1) inside (2) (3) Tunnel 0 10. 1. 1. 1/10. 2. 1. 1 20. 1. 1. 1/30. 1. 1. 1 Ipsec_protected Virtual Private Networks (VPN) 10. 1. 1. 1/10. 3. 1. 1 CN 8816: Network Security 10
3. IP Security (IPsec) n IPsec/GRE n n GRE defines a tunnel interface IPsec transport mode provides the security Routing table 10. 1. 0. 0/16 30. 0/8 10. 2. 0. 0/16 10. 3. 0. 0. /16 inside outside tunnel 0 (4) IP GRE (5) IPsec (transport) (6) outside (1) inside (2) (3) Tunnel 0 10. 1. 1. 1/10. 2. 1. 1 20. 1. 1. 1/30. 1. 1. 1 Ipsec_protected Virtual Private Networks (VPN) 10. 1. 1. 1/10. 3. 1. 1 CN 8816: Network Security 10
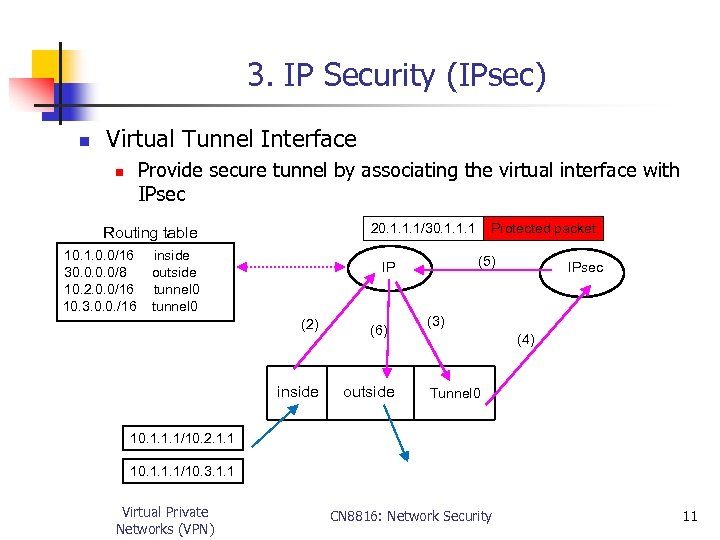 3. IP Security (IPsec) n Virtual Tunnel Interface Provide secure tunnel by associating the virtual interface with IPsec n 20. 1. 1. 1/30. 1. 1. 1 Routing table 10. 1. 0. 0/16 30. 0/8 10. 2. 0. 0/16 10. 3. 0. 0. /16 inside outside tunnel 0 (5) IP (2) inside (6) outside Protected packet IPsec (3) (4) Tunnel 0 10. 1. 1. 1/10. 2. 1. 1 10. 1. 1. 1/10. 3. 1. 1 Virtual Private Networks (VPN) CN 8816: Network Security 11
3. IP Security (IPsec) n Virtual Tunnel Interface Provide secure tunnel by associating the virtual interface with IPsec n 20. 1. 1. 1/30. 1. 1. 1 Routing table 10. 1. 0. 0/16 30. 0/8 10. 2. 0. 0/16 10. 3. 0. 0. /16 inside outside tunnel 0 (5) IP (2) inside (6) outside Protected packet IPsec (3) (4) Tunnel 0 10. 1. 1. 1/10. 2. 1. 1 10. 1. 1. 1/10. 3. 1. 1 Virtual Private Networks (VPN) CN 8816: Network Security 11
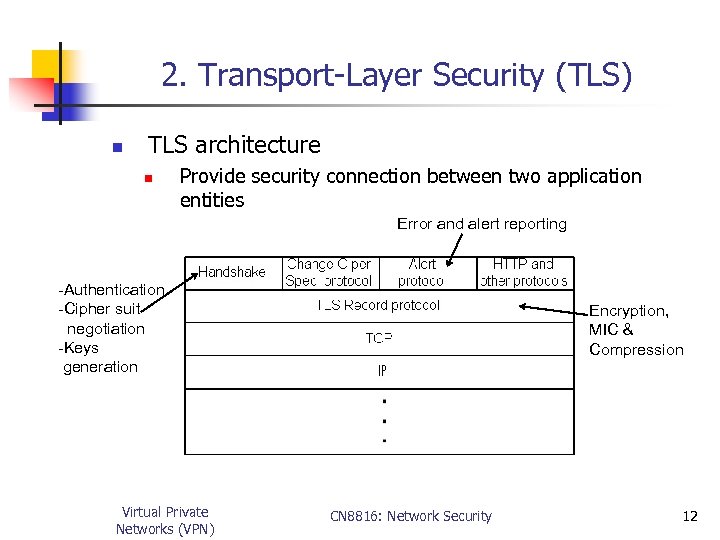 2. Transport-Layer Security (TLS) n TLS architecture n Provide security connection between two application entities Error and alert reporting -Authentication -Cipher suit negotiation -Keys generation Virtual Private Networks (VPN) Encryption, MIC & Compression CN 8816: Network Security 12
2. Transport-Layer Security (TLS) n TLS architecture n Provide security connection between two application entities Error and alert reporting -Authentication -Cipher suit negotiation -Keys generation Virtual Private Networks (VPN) Encryption, MIC & Compression CN 8816: Network Security 12
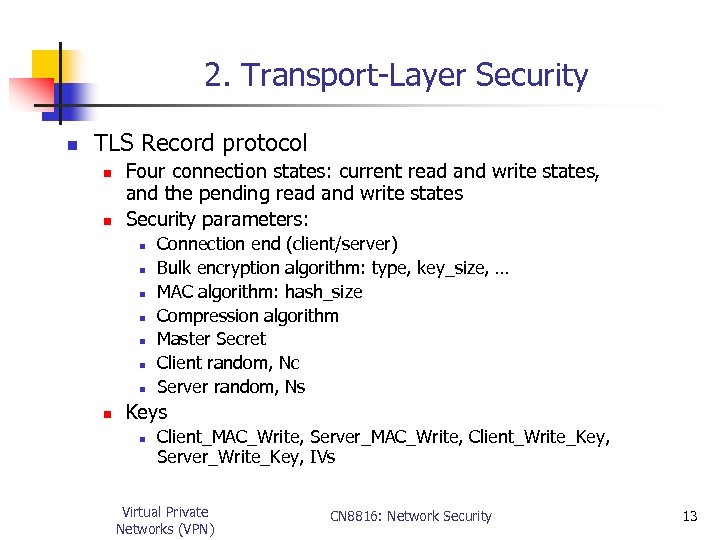 2. Transport-Layer Security n TLS Record protocol n n Four connection states: current read and write states, and the pending read and write states Security parameters: n n n n Connection end (client/server) Bulk encryption algorithm: type, key_size, … MAC algorithm: hash_size Compression algorithm Master Secret Client random, Nc Server random, Ns Keys n Client_MAC_Write, Server_MAC_Write, Client_Write_Key, Server_Write_Key, IVs Virtual Private Networks (VPN) CN 8816: Network Security 13
2. Transport-Layer Security n TLS Record protocol n n Four connection states: current read and write states, and the pending read and write states Security parameters: n n n n Connection end (client/server) Bulk encryption algorithm: type, key_size, … MAC algorithm: hash_size Compression algorithm Master Secret Client random, Nc Server random, Ns Keys n Client_MAC_Write, Server_MAC_Write, Client_Write_Key, Server_Write_Key, IVs Virtual Private Networks (VPN) CN 8816: Network Security 13
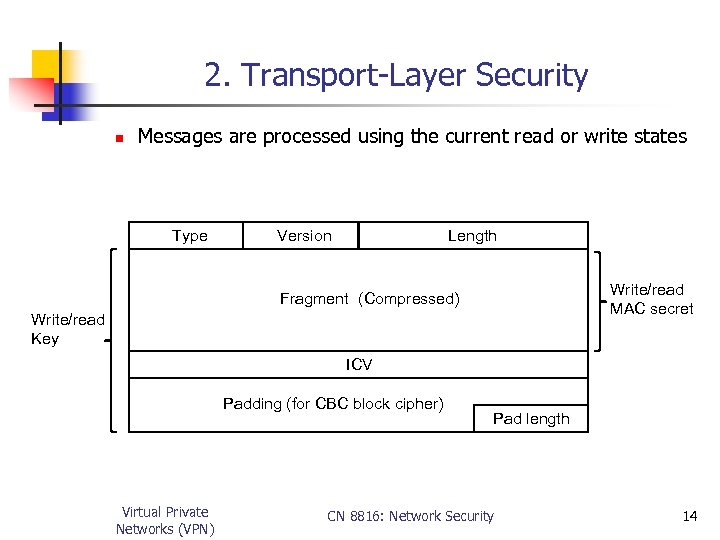 2. Transport-Layer Security n Messages are processed using the current read or write states Type Version Length Write/read MAC secret Fragment (Compressed) Write/read Key ICV Padding (for CBC block cipher) Virtual Private Networks (VPN) Pad length CN 8816: Network Security 14
2. Transport-Layer Security n Messages are processed using the current read or write states Type Version Length Write/read MAC secret Fragment (Compressed) Write/read Key ICV Padding (for CBC block cipher) Virtual Private Networks (VPN) Pad length CN 8816: Network Security 14
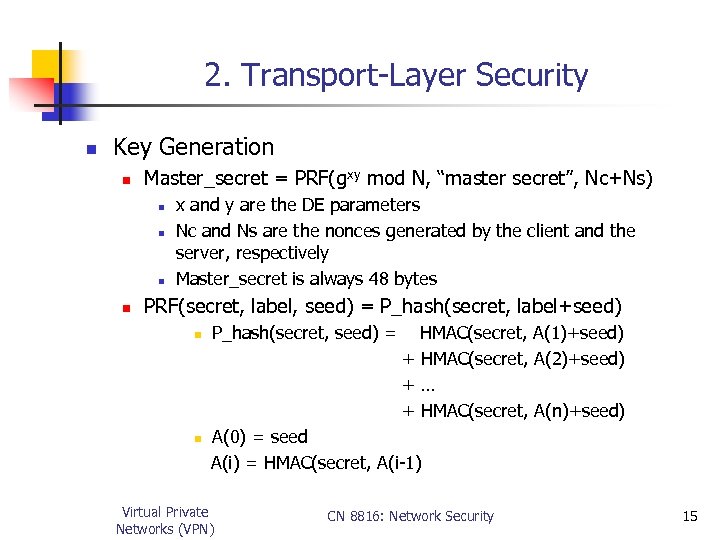 2. Transport-Layer Security n Key Generation n Master_secret = PRF(gxy mod N, “master secret”, Nc+Ns) n n x and y are the DE parameters Nc and Ns are the nonces generated by the client and the server, respectively Master_secret is always 48 bytes PRF(secret, label, seed) = P_hash(secret, label+seed) n n P_hash(secret, seed) = HMAC(secret, A(1)+seed) + HMAC(secret, A(2)+seed) +… + HMAC(secret, A(n)+seed) A(0) = seed A(i) = HMAC(secret, A(i-1) Virtual Private Networks (VPN) CN 8816: Network Security 15
2. Transport-Layer Security n Key Generation n Master_secret = PRF(gxy mod N, “master secret”, Nc+Ns) n n x and y are the DE parameters Nc and Ns are the nonces generated by the client and the server, respectively Master_secret is always 48 bytes PRF(secret, label, seed) = P_hash(secret, label+seed) n n P_hash(secret, seed) = HMAC(secret, A(1)+seed) + HMAC(secret, A(2)+seed) +… + HMAC(secret, A(n)+seed) A(0) = seed A(i) = HMAC(secret, A(i-1) Virtual Private Networks (VPN) CN 8816: Network Security 15
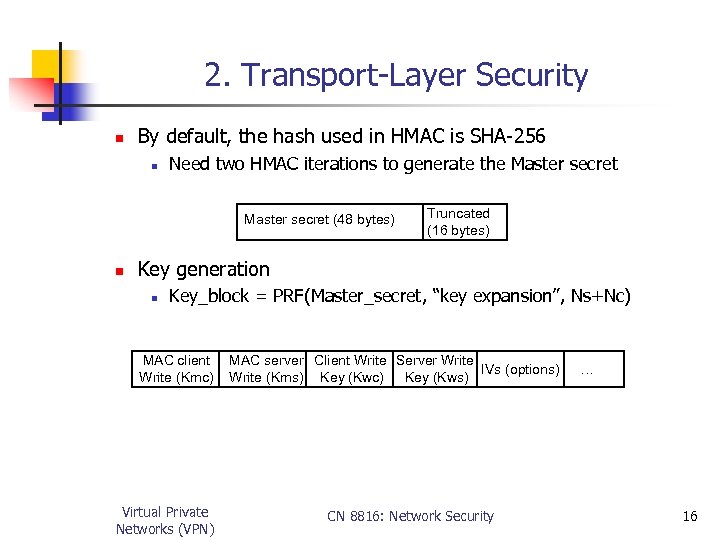 2. Transport-Layer Security n By default, the hash used in HMAC is SHA-256 n Need two HMAC iterations to generate the Master secret (48 bytes) n Truncated (16 bytes) Key generation n Key_block = PRF(Master_secret, “key expansion”, Ns+Nc) MAC client Write (Kmc) Virtual Private Networks (VPN) MAC server Client Write Server Write IVs (options) Write (Kms) Key (Kwc) Key (Kws) CN 8816: Network Security … 16
2. Transport-Layer Security n By default, the hash used in HMAC is SHA-256 n Need two HMAC iterations to generate the Master secret (48 bytes) n Truncated (16 bytes) Key generation n Key_block = PRF(Master_secret, “key expansion”, Ns+Nc) MAC client Write (Kmc) Virtual Private Networks (VPN) MAC server Client Write Server Write IVs (options) Write (Kms) Key (Kwc) Key (Kws) CN 8816: Network Security … 16
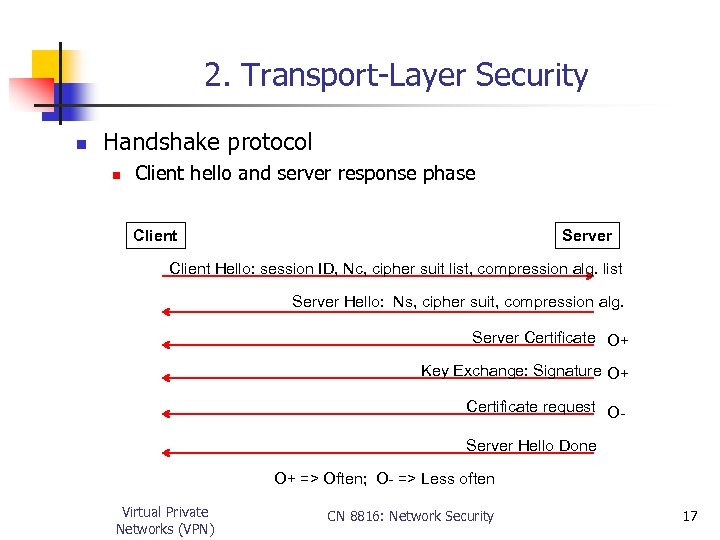 2. Transport-Layer Security n Handshake protocol n Client hello and server response phase Client Server Client Hello: session ID, Nc, cipher suit list, compression alg. list Server Hello: Ns, cipher suit, compression alg. Server Certificate O+ Key Exchange: Signature O+ Certificate request OServer Hello Done O+ => Often; O- => Less often Virtual Private Networks (VPN) CN 8816: Network Security 17
2. Transport-Layer Security n Handshake protocol n Client hello and server response phase Client Server Client Hello: session ID, Nc, cipher suit list, compression alg. list Server Hello: Ns, cipher suit, compression alg. Server Certificate O+ Key Exchange: Signature O+ Certificate request OServer Hello Done O+ => Often; O- => Less often Virtual Private Networks (VPN) CN 8816: Network Security 17
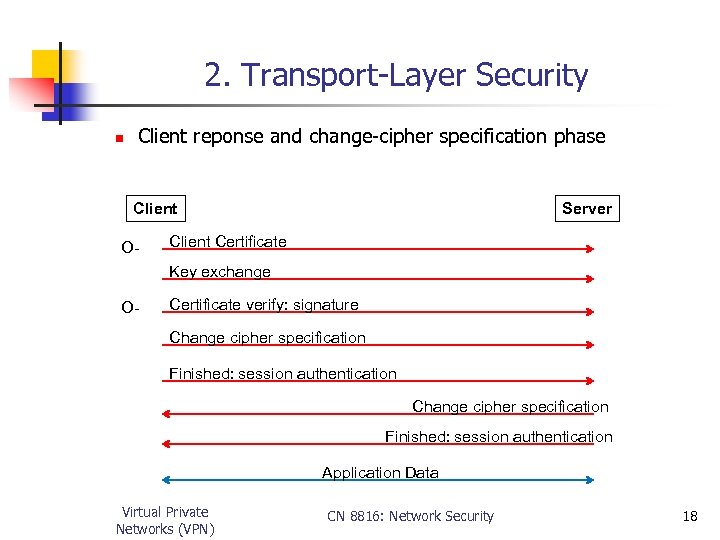 2. Transport-Layer Security n Client reponse and change-cipher specification phase Client O- Server Client Certificate Key exchange O- Certificate verify: signature Change cipher specification Finished: session authentication Application Data Virtual Private Networks (VPN) CN 8816: Network Security 18
2. Transport-Layer Security n Client reponse and change-cipher specification phase Client O- Server Client Certificate Key exchange O- Certificate verify: signature Change cipher specification Finished: session authentication Application Data Virtual Private Networks (VPN) CN 8816: Network Security 18
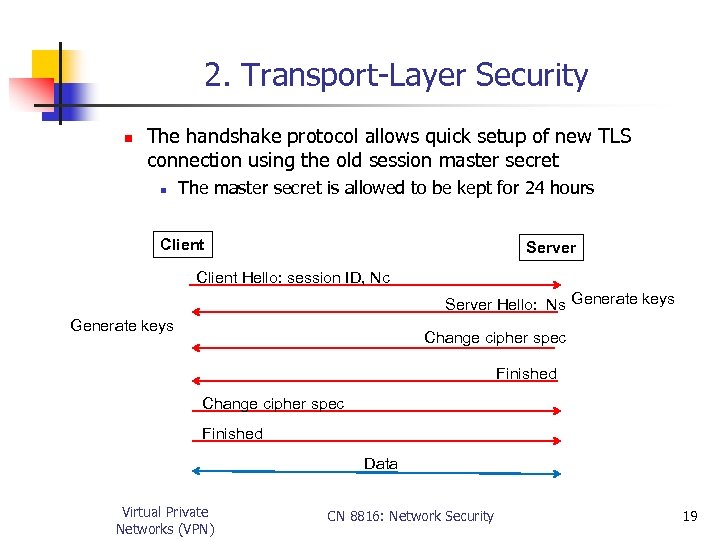 2. Transport-Layer Security n The handshake protocol allows quick setup of new TLS connection using the old session master secret n The master secret is allowed to be kept for 24 hours Client Server Client Hello: session ID, Nc Server Hello: Ns Generate keys Change cipher spec Finished Data Virtual Private Networks (VPN) CN 8816: Network Security 19
2. Transport-Layer Security n The handshake protocol allows quick setup of new TLS connection using the old session master secret n The master secret is allowed to be kept for 24 hours Client Server Client Hello: session ID, Nc Server Hello: Ns Generate keys Change cipher spec Finished Data Virtual Private Networks (VPN) CN 8816: Network Security 19
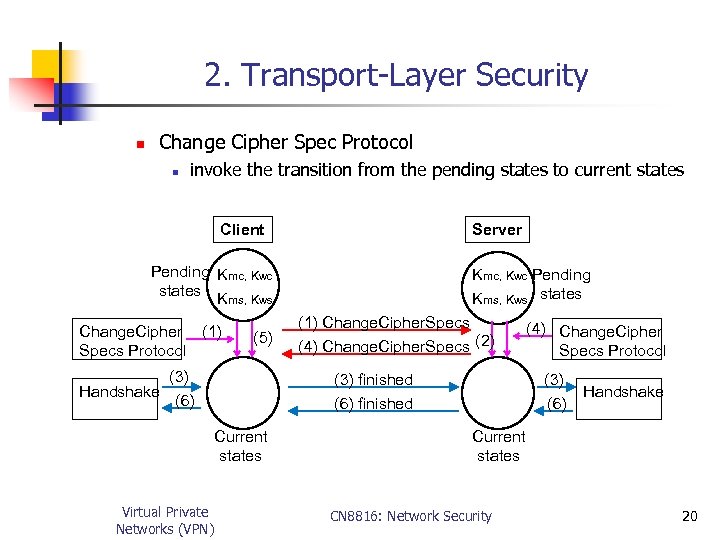 2. Transport-Layer Security n Change Cipher Spec Protocol n invoke the transition from the pending states to current states Client Server Pending Kmc, Kwc states Kms, Kws Change. Cipher (1) Specs Protocol (5) (3) Handshake (6) (1) Change. Cipher. Specs (4) Change. Cipher. Specs (2) (3) finished (6) finished Current states Virtual Private Networks (VPN) Kmc, Kwc Pending Kms, Kws states (4) Change. Cipher Specs Protocol (3) (6) Handshake Current states CN 8816: Network Security 20
2. Transport-Layer Security n Change Cipher Spec Protocol n invoke the transition from the pending states to current states Client Server Pending Kmc, Kwc states Kms, Kws Change. Cipher (1) Specs Protocol (5) (3) Handshake (6) (1) Change. Cipher. Specs (4) Change. Cipher. Specs (2) (3) finished (6) finished Current states Virtual Private Networks (VPN) Kmc, Kwc Pending Kms, Kws states (4) Change. Cipher Specs Protocol (3) (6) Handshake Current states CN 8816: Network Security 20
 2. Transport-Layer Security n Alert Protocol n n Alert messages convey the severity of the message and a description of the alert Alert levels: warning or fatal n n Alert messages with a level of fatal result in the immediate termination of the connection Alert types: n n Close notification Error alerts Virtual Private Networks (VPN) CN 8816: Network Security 21
2. Transport-Layer Security n Alert Protocol n n Alert messages convey the severity of the message and a description of the alert Alert levels: warning or fatal n n Alert messages with a level of fatal result in the immediate termination of the connection Alert types: n n Close notification Error alerts Virtual Private Networks (VPN) CN 8816: Network Security 21
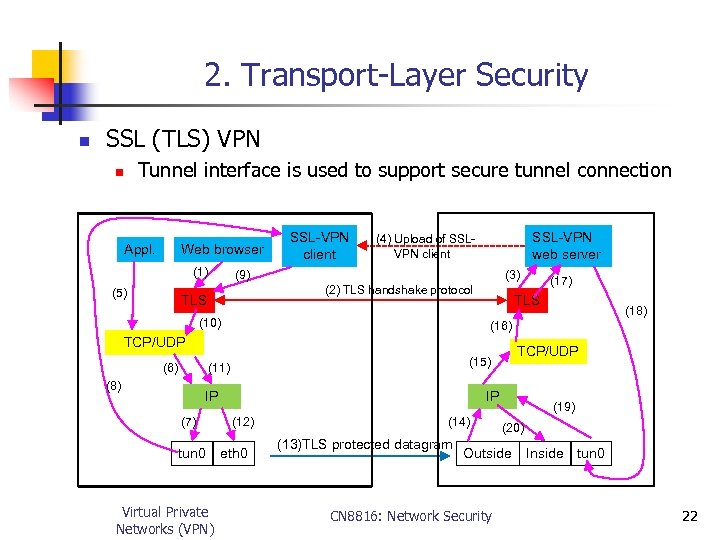 2. Transport-Layer Security n SSL (TLS) VPN Tunnel interface is used to support secure tunnel connection n Appl. Web browser (1) (5) SSL-VPN client SSL-VPN web server (4) Upload of SSLVPN client (9) (3) (2) TLS handshake protocol TLS (10) TLS IP (7) tun 0 Virtual Private Networks (VPN) TCP/UDP (15) (11) (8) (16) TCP/UDP (6) (17) IP (12) eth 0 (14) (13)TLS protected datagram (19) (20) Outside CN 8816: Network Security Inside tun 0 22
2. Transport-Layer Security n SSL (TLS) VPN Tunnel interface is used to support secure tunnel connection n Appl. Web browser (1) (5) SSL-VPN client SSL-VPN web server (4) Upload of SSLVPN client (9) (3) (2) TLS handshake protocol TLS (10) TLS IP (7) tun 0 Virtual Private Networks (VPN) TCP/UDP (15) (11) (8) (16) TCP/UDP (6) (17) IP (12) eth 0 (14) (13)TLS protected datagram (19) (20) Outside CN 8816: Network Security Inside tun 0 22


